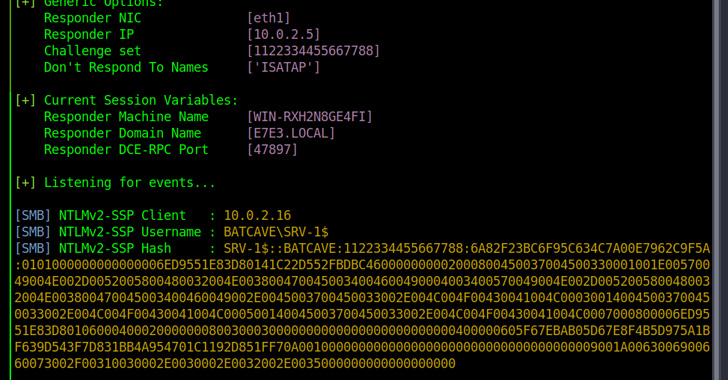
A new kind of Windows NTLM relay attack dubbed DFSCoerce has been uncovered that leverages the Distributed File System (DFS): Namespace Management Protocol (MS-DFSNM) to seize control of a domain.
"Spooler service disabled, RPC filters installed to prevent PetitPotam and File Server VSS Agent Service not installed but you still want to relay [Domain Controller authentication to [Active Directory
https://thehackernews.com/2022/06/new-ntlm-relay-attack-lets-attackers.html?utm_source=dlvr.it&utm_medium=blogger
No comments:
Post a Comment