By Deeba Ahmed The Russian Economic Forum was taking place in St. Petersburg when its proceedings were stalled due to a… This is a post from HackRead.com Read the original post: President Putin’s Economic Forum Speech Delayed due to DDoS…
Read more →
The post President Putin’s Economic Forum Speech Delayed due to DDoS Attack first appeared on IT Security News.
https://www.itsecuritynews.info/president-putins-economic-forum-speech-delayed-due-to-ddos-attack/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=president-putins-economic-forum-speech-delayed-due-to-ddos-attack
Tuesday, June 21, 2022
MaliBot – An Android Malware Attack Banking Victims & Steal Credentials, Cookies, and Bypass MFA Codes
Researchers from F5 Labs have recently detected a newly discovered breed of Android malware, called MaliBot. This malware has been targeting people in Spain and Italy who have access to online banking and cryptocurrency wallets. A number of distribution channels are currently used by MaliBot, most likely in order to obscure the market gap created […]
The post MaliBot – An Android Malware Attack Banking Victims & Steal Credentials, Cookies, and Bypass MFA Codes appeared first on Cyber Security News.
https://cybersecuritynews.com/malibot-android-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/malibot-android-malware/?utm_source=dlvr.it&utm_medium=blogger
Mitigate Ransomware in a Remote-First World
Ransomware has been a thorn in the side of cybersecurity teams for years. With the move to remote and hybrid work, this insidious threat has become even more of a challenge for organizations everywhere.
2021 was a case study in ransomware due to the wide variety of attacks, significant financial and economic impact, and diverse ways that organizations responded. These attacks should be seen as a
https://thehackernews.com/2022/06/mitigate-ransomware-in-remote-first.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/mitigate-ransomware-in-remote-first.html?utm_source=dlvr.it&utm_medium=blogger
Mozilla Rolls Out Total Cookie Protection On Firefox By Default
After initial release as an optional Firefox feature, Mozilla has now rolled out its ‘Total… Mozilla Rolls Out Total Cookie Protection On Firefox By Default on Latest Hacking News. This article has been indexed from Latest Hacking News Read the…
Read more →
The post Mozilla Rolls Out Total Cookie Protection On Firefox By Default first appeared on IT Security News.
https://www.itsecuritynews.info/mozilla-rolls-out-total-cookie-protection-on-firefox-by-default/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=mozilla-rolls-out-total-cookie-protection-on-firefox-by-default
https://www.itsecuritynews.info/mozilla-rolls-out-total-cookie-protection-on-firefox-by-default/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=mozilla-rolls-out-total-cookie-protection-on-firefox-by-default
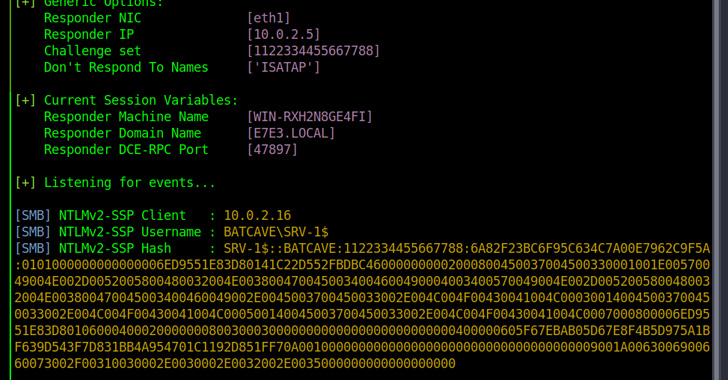
New NTLM Relay Attack Lets Attackers Take Control Over Windows Domain
A new kind of Windows NTLM relay attack dubbed DFSCoerce has been uncovered that leverages the Distributed File System (DFS): Namespace Management Protocol (MS-DFSNM) to seize control of a domain.
"Spooler service disabled, RPC filters installed to prevent PetitPotam and File Server VSS Agent Service not installed but you still want to relay [Domain Controller authentication to [Active Directory
https://thehackernews.com/2022/06/new-ntlm-relay-attack-lets-attackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/new-ntlm-relay-attack-lets-attackers.html?utm_source=dlvr.it&utm_medium=blogger
Monday, June 20, 2022
Why Paper Receipts are Money at the Drive-Thru
Check out the handmade sign posted to the front door of a shuttered Jimmy John’s sandwich chain shop in Missouri last week. See if you can tell from the store owner’s message what happened. This article has been indexed from…
Read more →
The post Why Paper Receipts are Money at the Drive-Thru first appeared on IT Security News.
https://www.itsecuritynews.info/why-paper-receipts-are-money-at-the-drive-thru/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=why-paper-receipts-are-money-at-the-drive-thru
https://www.itsecuritynews.info/why-paper-receipts-are-money-at-the-drive-thru/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=why-paper-receipts-are-money-at-the-drive-thru
Interview with Guardian Digital CEO Dave Wreski: Open Source Utilization in Email Security Solutions & More
In this interview Dave Wreski, Guardian Digital CEO and Founder, discusses Guardian Digital’s utilization of Open Source in the development of cutting-edge email security solutions and the advantages of investing in these solutions to secure your business email. This article…
Read more →
The post Interview with Guardian Digital CEO Dave Wreski: Open Source Utilization in Email Security Solutions & More first appeared on IT Security News.
https://www.itsecuritynews.info/interview-with-guardian-digital-ceo-dave-wreski-open-source-utilization-in-email-security-solutions-more/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=interview-with-guardian-digital-ceo-dave-wreski-open-source-utilization-in-email-security-solutions-more
https://www.itsecuritynews.info/interview-with-guardian-digital-ceo-dave-wreski-open-source-utilization-in-email-security-solutions-more/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=interview-with-guardian-digital-ceo-dave-wreski-open-source-utilization-in-email-security-solutions-more
Do You Have Ransomware Insurance? Look at the Fine Print
Insurance exists to protect the insured party against catastrophe, but the insurer needs protection so that its policies are not abused – and that's where the fine print comes in. However, in the case of ransomware insurance, the fine print is becoming contentious and arguably undermining the usefulness of ransomware insurance.
In this article, we'll outline why, particularly given the current
https://thehackernews.com/2022/06/do-you-have-ransomware-insurance-look.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/do-you-have-ransomware-insurance-look.html?utm_source=dlvr.it&utm_medium=blogger
Mark Wrighton Appointed as Chief Revenue Officer for Heimdal™ Security
COPENHAGEN, June 20th, 2022 – Heimdal™ Security (HEIMDAL) announced a new addition to its executive team. Following a period of significant growth, the company has landed Mark Wrighton as Chief Revenue Officer. Mark will lead the sales, success, and support…
Read more →
The post Mark Wrighton Appointed as Chief Revenue Officer for Heimdal™ Security first appeared on IT Security News.
https://www.itsecuritynews.info/mark-wrighton-appointed-as-chief-revenue-officer-for-heimdal-security-8/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=mark-wrighton-appointed-as-chief-revenue-officer-for-heimdal-security-8
https://www.itsecuritynews.info/mark-wrighton-appointed-as-chief-revenue-officer-for-heimdal-security-8/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=mark-wrighton-appointed-as-chief-revenue-officer-for-heimdal-security-8
Cisco Says zero-day Flaws with end-of-life VPN Routers won’t be Fixed
The Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers have entered the end-of-life process and hence it won’t be fixed. The vulnerability is tracked as (CVE-2022-20825) and has a CVSS severity rating of 9.8. The flaw found in the web-based management interface of Cisco Small Business Routers allows an unauthenticated, remote attacker to execute […]
The post Cisco Says zero-day Flaws with end-of-life VPN Routers won’t be Fixed appeared first on Cyber Security News.
https://cybersecuritynews.com/cisco-says-zero-day-flaws/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cisco-says-zero-day-flaws/?utm_source=dlvr.it&utm_medium=blogger
Sunday, June 19, 2022
USB Forensics – Reconstruction of Digital Evidence from USB Drive
This article has been indexed from GBHackers On Security Digitial Forensics analysis of USB forensics include preservation, collection, Validation, Identification, Analysis, Interpretation, Documentation, and Presentation of digital evidence derived from digital sources for the purpose of facilitating or furthering the reconstruction…
Read more →
The post USB Forensics – Reconstruction of Digital Evidence from USB Drive first appeared on IT Security News.
https://www.itsecuritynews.info/usb-forensics-reconstruction-of-digital-evidence-from-usb-drive-2/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=usb-forensics-reconstruction-of-digital-evidence-from-usb-drive-2
https://www.itsecuritynews.info/usb-forensics-reconstruction-of-digital-evidence-from-usb-drive-2/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=usb-forensics-reconstruction-of-digital-evidence-from-usb-drive-2
Defend Your Castle with Zero Trust
This article has been indexed from Cyber Defense Magazine Protecting yourself, your company and your data from the vulnerabilities of connectivity is no longer an option, but […] The post Defend Your Castle with Zero Trust appeared first on Cyber…
Read more →
The post Defend Your Castle with Zero Trust first appeared on IT Security News.
https://www.itsecuritynews.info/defend-your-castle-with-zero-trust/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=defend-your-castle-with-zero-trust
https://www.itsecuritynews.info/defend-your-castle-with-zero-trust/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=defend-your-castle-with-zero-trust
How to Password Protect Any File
This article has been indexed from Security Latest Put a digital lock on your most important data. Read the original article: How to Password Protect Any File
Read more →
The post How to Password Protect Any File first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-password-protect-any-file/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=how-to-password-protect-any-file
https://www.itsecuritynews.info/how-to-password-protect-any-file/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=how-to-password-protect-any-file
Eclypsium expands its executive team with new appointments
This article has been indexed from Help Net Security Eclypsium announced five new appointments to its executive team with key hires across research, sales and marketing. The company also welcomed Ramy Houssaini to Eclypsium’s Strategic Advisory Board. The expansion follows…
Read more →
The post Eclypsium expands its executive team with new appointments first appeared on IT Security News.
https://www.itsecuritynews.info/eclypsium-expands-its-executive-team-with-new-appointments/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=eclypsium-expands-its-executive-team-with-new-appointments
https://www.itsecuritynews.info/eclypsium-expands-its-executive-team-with-new-appointments/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=eclypsium-expands-its-executive-team-with-new-appointments
Vesta hires Hrishi Talwar as CPO
This article has been indexed from Help Net Security Vesta announced the hiring of experienced Identity and Fraud industry leader, Hrishi Talwar as Chief Product Officer. With extensive global experience, Hrishi brings 20+ years of product management and technology expertise…
Read more →
The post Vesta hires Hrishi Talwar as CPO first appeared on IT Security News.
https://www.itsecuritynews.info/vesta-hires-hrishi-talwar-as-cpo/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=vesta-hires-hrishi-talwar-as-cpo
https://www.itsecuritynews.info/vesta-hires-hrishi-talwar-as-cpo/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=vesta-hires-hrishi-talwar-as-cpo
Saturday, June 18, 2022
How ML-powered video surveillance could improve security
This article has been indexed from Security – VentureBeat The way video is collected, processed and searched can achieve the goals of tighter security and improved safety without compromising privacy. Read the original article: How ML-powered video surveillance could improve…
Read more →
The post How ML-powered video surveillance could improve security first appeared on IT Security News.
https://www.itsecuritynews.info/how-ml-powered-video-surveillance-could-improve-security/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=how-ml-powered-video-surveillance-could-improve-security
https://www.itsecuritynews.info/how-ml-powered-video-surveillance-could-improve-security/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=how-ml-powered-video-surveillance-could-improve-security
Tinder Swindlers: How scammers steal your heart, then your money
This article has been indexed from Latest topics for ZDNet in Security Love bombing, catfishing, blackmail, and more: Here are common tactics criminals use to lure you into parting with cash or private information. Read the original article: Tinder Swindlers:…
Read more →
The post Tinder Swindlers: How scammers steal your heart, then your money first appeared on IT Security News.
https://www.itsecuritynews.info/tinder-swindlers-how-scammers-steal-your-heart-then-your-money/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=tinder-swindlers-how-scammers-steal-your-heart-then-your-money
https://www.itsecuritynews.info/tinder-swindlers-how-scammers-steal-your-heart-then-your-money/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=tinder-swindlers-how-scammers-steal-your-heart-then-your-money
Microsoft Office 365 Functionality that Allow Attackers to Encrypt Files Stored on SharePoint and OneDrive
Cybersecurity analysts at Proofpoint have recently discovered that there might be a way to encrypt files on SharePoint and OneDrive by exploiting a feature in the Microsoft 365 suite. As a result, enterprises could leave themselves open to cyber attacks such as ransomware. Attackers are going to build their hard drive campaigns on this new […]
The post Microsoft Office 365 Functionality that Allow Attackers to Encrypt Files Stored on SharePoint and OneDrive appeared first on Cyber Security News.
https://cybersecuritynews.com/microsoft-office-365-functionality/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/microsoft-office-365-functionality/?utm_source=dlvr.it&utm_medium=blogger
Authorities Shut Down Russian RSOCKS Botnet That Hacked Millions of Devices
The U.S. Department of Justice (DoJ) on Thursday disclosed that it took down the infrastructure associated with a Russian botnet known as RSOCKS in collaboration with law enforcement partners in Germany, the Netherlands, and the U.K.
The botnet, operated by a sophisticated cybercrime organization, is believed to have ensnared millions of internet-connected devices, including Internet of Things (
https://thehackernews.com/2022/06/authorities-shut-down-russian-rsocks.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/authorities-shut-down-russian-rsocks.html?utm_source=dlvr.it&utm_medium=blogger
Atlassian Confluence Flaw Being Used to Deploy Ransomware and Crypto Miners
A recently patched critical security flaw in Atlassian Confluence Server and Data Center products is being actively weaponized in real-world attacks to drop cryptocurrency miners and ransomware payloads.
In at least two of the Windows-related incidents observed by cybersecurity vendor Sophos, adversaries exploited the vulnerability to deliver Cerber ransomware and a crypto miner called z0miner
https://thehackernews.com/2022/06/atlassian-confluence-flaw-being-used-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/atlassian-confluence-flaw-being-used-to.html?utm_source=dlvr.it&utm_medium=blogger
Friday, June 17, 2022
Panchan Peer-to-Peer Botnet
This article has been indexed from Information Security Buzz Akamai security researchers have released discovery on Panchan, a new peer-to-peer botnet and SSH worm that emerged in March and has been actively breaching Linux servers since. Panchan, written in Golang,…
Read more →
The post Panchan Peer-to-Peer Botnet first appeared on IT Security News.
https://www.itsecuritynews.info/panchan-peer-to-peer-botnet/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/panchan-peer-to-peer-botnet/?utm_source=dlvr.it&utm_medium=blogger
Sophos Zero-day Flaw by Chinese Hackers to Implement Backdoor
The Chinese hackers exploited Sophos firewall’s zero-day flaw to target South Asian companies and breached cloud-hosted web servers. Previously, Volexity noticed a sophisticated attack against a customer that is seriously targeted by multiple Chinese advanced persistent threat (APT) groups. This attack leveraged a zero-day exploit to compromise the customer’s firewall. The cybersecurity company, Volexity said […]
The post Sophos Zero-day Flaw by Chinese Hackers to Implement Backdoor appeared first on Cyber Security News.
https://cybersecuritynews.com/sophos-zero-day-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/sophos-zero-day-flaw/?utm_source=dlvr.it&utm_medium=blogger
Researchers Uncover 'Hermit' Android Spyware Used in Kazakhstan, Syria, and Italy
An enterprise-grade surveillanceware dubbed Hermit has been put to use by entities operating from within Kazakhstan, Syria, and Italy over the years since 2019, new research has revealed.
Lookout attributed the spy software, which is equipped to target both Android and iOS, to an Italian company named RCS Lab S.p.A and Tykelab Srl, a telecom services provider which it suspects to be a front
https://thehackernews.com/2022/06/researchers-uncover-hermit-android.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/researchers-uncover-hermit-android.html?utm_source=dlvr.it&utm_medium=blogger
Beware!! BlackCat Ransomware Gang Attack Unpatched Microsoft Exchange Servers
This article has been indexed from GBHackers On Security In a recent Microsoft advisory, the company warned that the operators of BlackCat ransomware (aka ALPHV) is using exploits to gain access to target networks by exploiting unpatched Exchange server vulnerabilities.…
Read more →
The post Beware!! BlackCat Ransomware Gang Attack Unpatched Microsoft Exchange Servers first appeared on IT Security News.
https://www.itsecuritynews.info/beware-blackcat-ransomware-gang-attack-unpatched-microsoft-exchange-servers/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/beware-blackcat-ransomware-gang-attack-unpatched-microsoft-exchange-servers/?utm_source=dlvr.it&utm_medium=blogger
Over a Million WordPress Sites Forcibly Updated to Patch a Critical Plugin Vulnerability
WordPress websites using a widely used plugin named Ninja Forms have been updated automatically to remediate a critical security vulnerability that's suspected of having been actively exploited in the wild.
The issue, which relates to a case of code injection, is rated 9.8 out of 10 for severity and affects multiple versions starting from 3.0. It has been fixed in 3.0.34.2, 3.1.10, 3.2.28,
https://thehackernews.com/2022/06/over-million-wordpress-sites-forcibly.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/over-million-wordpress-sites-forcibly.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, June 16, 2022
Cloudflare Mitigates a Record-Breaking DDoS Assault Peaking at 26 Million RPS
This article has been indexed from CySecurity News – Latest Information Security and Hacking Incidents Last week, Cloudflare thwarted the largest HTTPS DDoS attack ever recorded. The attack amassed 26 million HTTPS requests per second, breaking the previous record…
Read more →
The post Cloudflare Mitigates a Record-Breaking DDoS Assault Peaking at 26 Million RPS first appeared on IT Security News.
https://www.itsecuritynews.info/cloudflare-mitigates-a-record-breaking-ddos-assault-peaking-at-26-million-rps/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cloudflare-mitigates-a-record-breaking-ddos-assault-peaking-at-26-million-rps/?utm_source=dlvr.it&utm_medium=blogger
New Malware On Google Play With Over Two Million Downloads
As a result of the recent investigation into the Google Play Store, researchers discovered adware and malware that steals information from users. At least five of the apps were still available when they were discovered last month, and have more than two million downloads. Infections of adware can produce a variety of unwanted advertisements that […]
The post New Malware On Google Play With Over Two Million Downloads appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-on-google-play/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/malware-on-google-play/?utm_source=dlvr.it&utm_medium=blogger
BlackCat Ransomware Gang Targeting Unpatched Microsoft Exchange Servers
Microsoft is warning that the BlackCat ransomware crew is leveraging exploits for unpatched Exchange server vulnerabilities to gain access to targeted networks.
Upon gaining an entry point, the attackers swiftly moved to gather information about the compromised machines, followed by carrying out credential theft and lateral movement activities, before harvesting intellectual property and
https://thehackernews.com/2022/06/blackcat-ransomware-gang-targeting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/blackcat-ransomware-gang-targeting.html?utm_source=dlvr.it&utm_medium=blogger
How to Increase Sales With Sales Automation Software?
This article has been indexed from NorseCorp Possessing a private venture is definitely not a simple errand in the present business climate. Finance is to meet you, to keep clients blissful, bills … Read more The post How to Increase…
Read more →
The post How to Increase Sales With Sales Automation Software? first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-increase-sales-with-sales-automation-software/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-to-increase-sales-with-sales-automation-software/?utm_source=dlvr.it&utm_medium=blogger
Largest HTTPS DDoS Attack on Record – 26 million Request per Second
Recently, Cloudflare noticed and mitigated a 26 million request per second DDoS attack, the largest HTTPS DDoS attack on record. This attack targeted customer websites using Cloudflare’s free plan. In this case, the attackers used hijacked servers and virtual machines seeing that the attack originated from Cloud Service Providers instead of weaker Internet of Things […]
The post Largest HTTPS DDoS Attack on Record – 26 million Request per Second appeared first on Cyber Security News.
https://cybersecuritynews.com/largest-https-ddos-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/largest-https-ddos-attack/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, June 15, 2022
Can global recruitment solve the cybersecurity hiring problem?
This article has been indexed from Cybersecurity Insiders This blog was written by an independent guest blogger. It’s well known that there’s a pervasive cybersecurity skills shortage. The problem has multiple ramifications. Current cybersecurity teams often deal with consistently heavy…
Read more →
The post Can global recruitment solve the cybersecurity hiring problem? first appeared on IT Security News.
https://www.itsecuritynews.info/can-global-recruitment-solve-the-cybersecurity-hiring-problem/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/can-global-recruitment-solve-the-cybersecurity-hiring-problem/?utm_source=dlvr.it&utm_medium=blogger
BeanVPN leaks 25 million user records
This article has been indexed from http://www.infosecurity-magazine.com/rss/news/76/application-security/ The cache of 18.5GB connection logs allegedly contained more than 25 million records Read the original article: BeanVPN leaks 25 million user records
Read more →
The post BeanVPN leaks 25 million user records first appeared on IT Security News.
https://www.itsecuritynews.info/beanvpn-leaks-25-million-user-records/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/beanvpn-leaks-25-million-user-records/?utm_source=dlvr.it&utm_medium=blogger
Press Release: Perimeter 81 Adds Secure Web Gateway to its Scalable SSE Solution
Cybersecurity: Going Beyond the Enterprise Cloud Perimeter 81 recently announced the addition of a new Secure Web Gateway (SWG) to its growing list of cloud and network security solutions. The new solution provides an extra layer of protection for organizations by preventing malicious web traffic and content from ever reaching devices or applications. The Secure […]
The post Press Release: Perimeter 81 Adds Secure Web Gateway to its Scalable SSE Solution appeared first on Cyber Security News.
https://cybersecuritynews.com/secure-web-gateway/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/secure-web-gateway/?utm_source=dlvr.it&utm_medium=blogger
Email compromise leads to healthcare data breach at Kaiser Permanente
This article has been indexed from Malwarebytes Labs We take a look at the latest healthcare breach, an email compromise of a healthcare employee and explore the fallout. The post Email compromise leads to healthcare data breach at Kaiser Permanente…
Read more →
The post Email compromise leads to healthcare data breach at Kaiser Permanente first appeared on IT Security News.
https://www.itsecuritynews.info/email-compromise-leads-to-healthcare-data-breach-at-kaiser-permanente/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/email-compromise-leads-to-healthcare-data-breach-at-kaiser-permanente/?utm_source=dlvr.it&utm_medium=blogger
Metasploit 6.2 Released – 138 New modules, 148 New Enhancements & 150+ Bugs Fixed
The company Rapid7 has released a brand-new version of Metasploit, Metasploit 6.2.0, which has a lot of improvements and enhanced features. In addition to the existing features, this new version offers the following things:- 138 New modules 148 Enhancements and features 156 Bug fixes With 864 payloads and 2,227 exploits, Metasploit is one of the […]
The post Metasploit 6.2 Released – 138 New modules, 148 New Enhancements & 150+ Bugs Fixed appeared first on Cyber Security News.
https://cybersecuritynews.com/metasploit-6-2/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/metasploit-6-2/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, June 14, 2022
Journey Into Cybersecurity – Conversations with Cyber Newcomers, Part 2
This article has been indexed from Cybersecurity Insiders In the second portion of this blog series, we are sharing member stories from those with four to six years of experience in cybersecurity. We asked members about their entry into cyber…
Read more →
The post Journey Into Cybersecurity – Conversations with Cyber Newcomers, Part 2 first appeared on IT Security News.
https://www.itsecuritynews.info/journey-into-cybersecurity-conversations-with-cyber-newcomers-part-2-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/journey-into-cybersecurity-conversations-with-cyber-newcomers-part-2-2/?utm_source=dlvr.it&utm_medium=blogger
What is the Essential Eight (And Why Non-Aussies Should Care)
In 2017, The Australian Cyber Security Center (ACSC) published a set of mitigation strategies that were designed to help organizations to protect themselves against cyber security incidents. These strategies, which became known as the Essential Eight, are designed specifically for use on Windows networks, although variations of these strategies are commonly applied to other platforms.
What is
https://thehackernews.com/2022/06/what-is-essential-eight-and-why-non.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/what-is-essential-eight-and-why-non.html?utm_source=dlvr.it&utm_medium=blogger
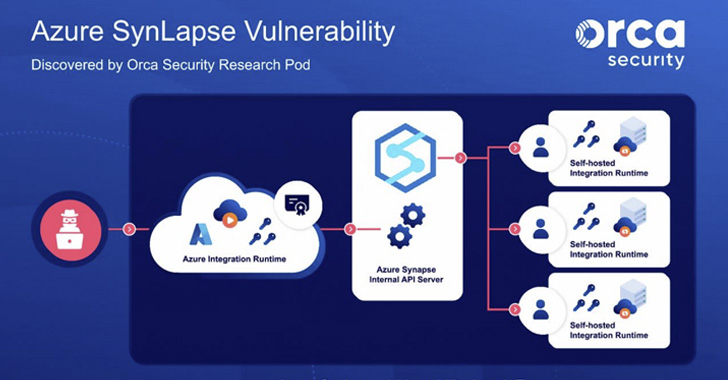
Technical Details Released for 'SynLapse' RCE Vulnerability Reported in Microsoft Azure
Microsoft has incorporated additional improvements to address the recently disclosed SynLapse security vulnerability in order to meet comprehensive tenant isolation requirements in Azure Data Factory and Azure Synapse Pipelines.
The latest safeguards include moving the shared integration runtimes to sandboxed ephemeral instances and using scoped tokens to prevent adversaries from using a client
https://thehackernews.com/2022/06/technical-details-released-for-synlapse.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/technical-details-released-for-synlapse.html?utm_source=dlvr.it&utm_medium=blogger
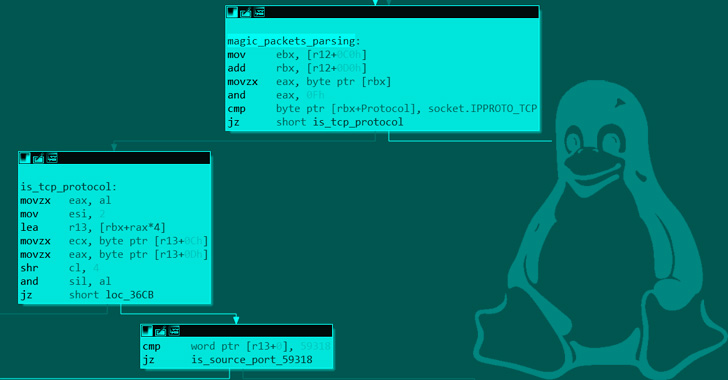
New Syslogk Linux Rootkit Lets Attackers Remotely Command It Using "Magic Packets"
A new covert Linux kernel rootkit named Syslogk has been spotted under development in the wild and cloaking a malicious payload that can be remotely commandeered by an adversary using a magic network traffic packet.
"The Syslogk rootkit is heavily based on Adore-Ng but incorporates new functionalities making the user-mode application and the kernel rootkit hard to detect," Avast security
https://thehackernews.com/2022/06/new-syslogk-linux-rootkit-lets.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/new-syslogk-linux-rootkit-lets.html?utm_source=dlvr.it&utm_medium=blogger
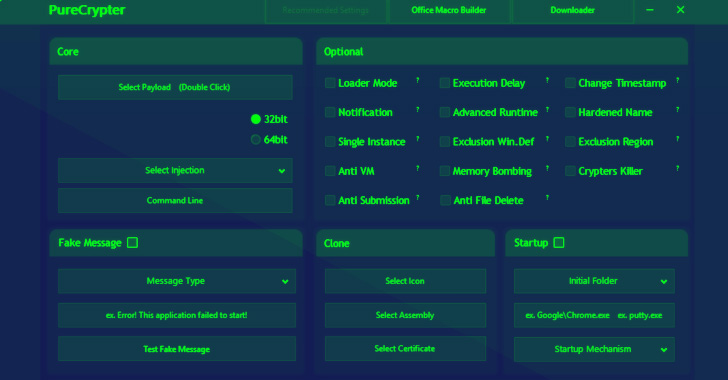
Researchers Detail PureCrypter Loader Cyber Criminals Using to Distribute Malware
Cybersecurity researchers have detailed the workings of a fully-featured malware loader dubbed PureCrypter that's being purchased by cyber criminals to deliver remote access trojans (RATs) and information stealers.
"The loader is a .NET executable obfuscated with SmartAssembly and makes use of compression, encryption, and obfuscation to evade antivirus software products," Zscaler's Romain Dumont
https://thehackernews.com/2022/06/researchers-detail-purecrypter-loader.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/researchers-detail-purecrypter-loader.html?utm_source=dlvr.it&utm_medium=blogger
Monday, June 13, 2022
You’re invited! Join us for a live walkthrough of the “Follina” story…
This article has been indexed from Naked Security – Sophos Live demo, plain English, no sales pitch, just a chance to watch an attack dissected in safety. Join us if you can! Read the original article: You’re invited! Join us…
Read more →
The post You’re invited! Join us for a live walkthrough of the “Follina” story… first appeared on IT Security News.
https://www.itsecuritynews.info/youre-invited-join-us-for-a-live-walkthrough-of-the-follina-story/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/youre-invited-join-us-for-a-live-walkthrough-of-the-follina-story/?utm_source=dlvr.it&utm_medium=blogger
Nearly-Impossible-to-Detect Linux Malware Used to Target Financial Sectors
As a result of a collaborative effort between BlackBerry Research & Intelligence Team and Intezer Security Researcher, Symbiote was discovered. Unlike most types of Linux malware, Symbiote is a brand new and hard-to-detect form of Linux malware. Several months ago, Symbiote was discovered by the security team. Malware in general compromises Linux processes and acts […]
The post Nearly-Impossible-to-Detect Linux Malware Used to Target Financial Sectors appeared first on Cyber Security News.
https://cybersecuritynews.com/impossible-to-detect-linux-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/impossible-to-detect-linux-malware/?utm_source=dlvr.it&utm_medium=blogger
Chinese 'Gallium' Hackers Using New PingPull Malware in Cyberespionage Attacks
A Chinese advanced persistent threat (APT) known as Gallium has been observed using a previously undocumented remote access trojan in its espionage attacks targeting companies operating in Southeast Asia, Europe, and Africa.
Called PingPull, the "difficult-to-detect" backdoor is notable for its use of the Internet Control Message Protocol (ICMP) for command-and-control (C2) communications,
https://thehackernews.com/2022/06/chinese-gallium-hackers-using-new.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/chinese-gallium-hackers-using-new.html?utm_source=dlvr.it&utm_medium=blogger
Hello XD Ransomware Installing Backdoor on Targeted Windows and Linux Systems
Windows and Linux systems are being targeted by a ransomware variant called HelloXD, with the infections also involving the deployment of a backdoor to facilitate persistent remote access to infected hosts.
"Unlike other ransomware groups, this ransomware family doesn't have an active leak site; instead it prefers to direct the impacted victim to negotiations through Tox chat and onion-based
https://thehackernews.com/2022/06/hello-xd-ransomware-installing-backdoor.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/hello-xd-ransomware-installing-backdoor.html?utm_source=dlvr.it&utm_medium=blogger
Iranian Hackers Spotted Using a new DNS Hijacking Malware in Recent Attacks
The Iranian state-sponsored threat actor tracked under the moniker Lyceum has turned to using a new custom .NET-based backdoor in recent campaigns directed against the Middle East.
"The new malware is a .NET based DNS Backdoor which is a customized version of the open source tool 'DIG.net,'" Zscaler ThreatLabz researchers Niraj Shivtarkar and Avinash Kumar said in a report published last week.
"
https://thehackernews.com/2022/06/iranian-hackers-spotted-using-new-dns.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/06/iranian-hackers-spotted-using-new-dns.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, June 12, 2022
A Complete Malware Analysis Tutorials, Cheatsheet & Tools list for Security Professionals
This article has been indexed from GBHackers On Security Analyzing the malware to breakdown its function and infection routine is a kind of tough job. here we describing the complete Malware Analysis Tutorials, tools, and elaborate cheatsheet. You can also…
Read more →
The post A Complete Malware Analysis Tutorials, Cheatsheet & Tools list for Security Professionals first appeared on IT Security News.
https://www.itsecuritynews.info/a-complete-malware-analysis-tutorials-cheatsheet-tools-list-for-security-professionals-4/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/a-complete-malware-analysis-tutorials-cheatsheet-tools-list-for-security-professionals-4/?utm_source=dlvr.it&utm_medium=blogger
Ransomware gangs are exploiting CVE-2022-26134 RCE in Atlassian Confluence servers
This article has been indexed from Security Affairs Ransomware gangs are actively exploiting CVE-2022-26134 remote code execution (RCE) flaw in Atlassian Confluence Server and Data Center. Multiple ransomware groups are actively exploiting the recently disclosed remote code execution (RCE) vulnerability,…
Read more →
The post Ransomware gangs are exploiting CVE-2022-26134 RCE in Atlassian Confluence servers first appeared on IT Security News.
https://www.itsecuritynews.info/ransomware-gangs-are-exploiting-cve-2022-26134-rce-in-atlassian-confluence-servers/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ransomware-gangs-are-exploiting-cve-2022-26134-rce-in-atlassian-confluence-servers/?utm_source=dlvr.it&utm_medium=blogger
Conti’s Attack Against Costa Rica Sparks a New Ransomware Era
This article has been indexed from Security Latest A pair of ransomware attacks crippled parts of the country—and rewrote the rules of cybercrime. Read the original article: Conti’s Attack Against Costa Rica Sparks a New Ransomware Era
Read more →
The post Conti’s Attack Against Costa Rica Sparks a New Ransomware Era first appeared on IT Security News.
https://www.itsecuritynews.info/contis-attack-against-costa-rica-sparks-a-new-ransomware-era/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/contis-attack-against-costa-rica-sparks-a-new-ransomware-era/?utm_source=dlvr.it&utm_medium=blogger
Steve Prodger joins Arcules as CRO
This article has been indexed from Help Net Security Arcules has expanded its leadership team to drive growth, and accelerate industry change. Steve Prodger, a vanguard and results-oriented technology executive, joins Arcules as Chief Revenue Officer. He will catalyze the…
Read more →
The post Steve Prodger joins Arcules as CRO first appeared on IT Security News.
https://www.itsecuritynews.info/steve-prodger-joins-arcules-as-cro/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/steve-prodger-joins-arcules-as-cro/?utm_source=dlvr.it&utm_medium=blogger
Researchers Found that Bluetooth Devices Can Be Used to Track Location of Mobile Phones
Using Bluetooth signals generated by smartphones, security researchers at the University of California San Diego have developed a method of identifying and tracking them via their smartphones. During the team’s research, they found that Bluetooth signals, which are continuously being sent by phone, have a unique fingerprint that can be identified. In addition, they also […]
The post Researchers Found that Bluetooth Devices Can Be Used to Track Location of Mobile Phones appeared first on Cyber Security News.
https://cybersecuritynews.com/bluetooth-devices-location-tracking/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/bluetooth-devices-location-tracking/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)