Popular enterprise services provider Zoom has announced the rollout of post-quantum end-to-end encryption (E2EE) for Zoom Meetings, with support for Zoom Phone and Zoom Rooms coming in the future.
"As adversarial threats become more sophisticated, so does the need to safeguard user data," the company said in a statement. "With the launch of post-quantum E2EE, we are doubling down on
https://thehackernews.com/2024/05/zoom-adopts-nist-approved-post-quantum.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, May 22, 2024
Tuesday, May 21, 2024
Critical GitHub Enterprise Server Flaw Allows Authentication Bypass
GitHub has rolled out fixes to address a maximum severity flaw in the GitHub Enterprise Server (GHES) that could allow an attacker to bypass authentication protections.
Tracked as CVE-2024-4985 (CVSS score: 10.0), the issue could permit unauthorized access to an instance without requiring prior authentication.
"On instances that use SAML single sign-on (SSO) authentication with the
https://thehackernews.com/2024/05/critical-github-enterprise-server-flaw.html?utm_source=dlvr.it&utm_medium=blogger
Tracked as CVE-2024-4985 (CVSS score: 10.0), the issue could permit unauthorized access to an instance without requiring prior authentication.
"On instances that use SAML single sign-on (SSO) authentication with the
https://thehackernews.com/2024/05/critical-github-enterprise-server-flaw.html?utm_source=dlvr.it&utm_medium=blogger
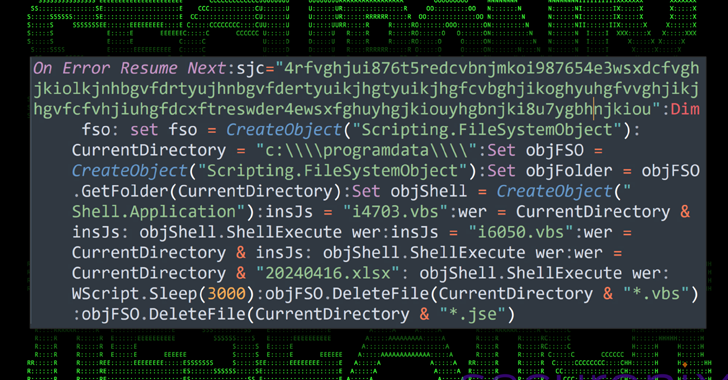
Malware Delivery via Cloud Services Exploits Unicode Trick to Deceive Users
A new attack campaign dubbed CLOUD#REVERSER has been observed leveraging legitimate cloud storage services like Google Drive and Dropbox to stage malicious payloads.
"The VBScript and PowerShell scripts in the CLOUD#REVERSER inherently involves command-and-control-like activities by using Google Drive and Dropbox as staging platforms to manage file uploads and downloads," Securonix
https://thehackernews.com/2024/05/malware-delivery-via-cloud-services.html?utm_source=dlvr.it&utm_medium=blogger
"The VBScript and PowerShell scripts in the CLOUD#REVERSER inherently involves command-and-control-like activities by using Google Drive and Dropbox as staging platforms to manage file uploads and downloads," Securonix
https://thehackernews.com/2024/05/malware-delivery-via-cloud-services.html?utm_source=dlvr.it&utm_medium=blogger
New Windows AI Feature Records All Your PC Activities
The development of AI is massively changing personal computing. AI algorithms are playing a role in computer operating systems and applications, from intelligent virtual assistants to task automation improvements. So, this blend results in better user experiences, increased productivity, and new territories for personalized human-computer intuitive interactions. Microsoft recently unveiled a new AI-powered feature dubbed […]
The post New Windows AI Feature Records All Your PC Activities appeared first on Cyber Security News.
https://cybersecuritynews.com/windows-ai-recall-feature/?utm_source=dlvr.it&utm_medium=blogger
The post New Windows AI Feature Records All Your PC Activities appeared first on Cyber Security News.
https://cybersecuritynews.com/windows-ai-recall-feature/?utm_source=dlvr.it&utm_medium=blogger
Beware of BlackPlague Malware That Steals Discord Token & Telegram Sessions
Cybersecurity experts have identified a new strain of malware named “BlackPlague” that targets explicitly popular communication platforms Discord and Telegram. This sophisticated malware is designed to steal user tokens and session data, posing a significant threat to the privacy and security of millions of users worldwide. The Rise of BlackPlague Malware According to a report […]
The post Beware of BlackPlague Malware That Steals Discord Token & Telegram Sessions appeared first on Cyber Security News.
https://cybersecuritynews.com/beware-of-blackplague-malware/?utm_source=dlvr.it&utm_medium=blogger
The post Beware of BlackPlague Malware That Steals Discord Token & Telegram Sessions appeared first on Cyber Security News.
https://cybersecuritynews.com/beware-of-blackplague-malware/?utm_source=dlvr.it&utm_medium=blogger
"Linguistic Lumberjack" Vulnerability Discovered in Popular Logging Utility Fluent Bit
Cybersecurity researchers have discovered a critical security flaw in a popular logging and metrics utility called Fluent Bit that could be exploited to achieve denial-of-service (DoS), information disclosure, or remote code execution.
The vulnerability, tracked as CVE-2024-4323, has been codenamed Linguistic Lumberjack by Tenable Research. It impacts versions from 2.0.7 through
https://thehackernews.com/2024/05/linguistic-lumberjack-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
The vulnerability, tracked as CVE-2024-4323, has been codenamed Linguistic Lumberjack by Tenable Research. It impacts versions from 2.0.7 through
https://thehackernews.com/2024/05/linguistic-lumberjack-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
Monday, May 20, 2024
Iranian MOIS-Linked Hackers Behind Destructive Attacks on Albania and Israel
An Iranian threat actor affiliated with the Ministry of Intelligence and Security (MOIS) has been attributed as behind destructive wiping attacks targeting Albania and Israel under the personas Homeland Justice and Karma, respectively.
Cybersecurity firm Check Point is tracking the activity under the moniker Void Manticore, which is also known as Storm-0842 (formerly DEV-0842) by
https://thehackernews.com/2024/05/iranian-mois-linked-hackers-behind.html?utm_source=dlvr.it&utm_medium=blogger
Cybersecurity firm Check Point is tracking the activity under the moniker Void Manticore, which is also known as Storm-0842 (formerly DEV-0842) by
https://thehackernews.com/2024/05/iranian-mois-linked-hackers-behind.html?utm_source=dlvr.it&utm_medium=blogger
Samstealer Attacking Windows Systems To Steal Sensitive Data
Hackers mainly aim at Windows systems as they are widely adopted and dominate the market, consequently, threat actors will achieve maximum financial gain or theft of data from them compared to other operating systems. In addition, the presence of numerous entry points due to the complexity of the Windows operating system and the diversity of […]
The post Samstealer Attacking Windows Systems To Steal Sensitive Data appeared first on Cyber Security News.
https://cybersecuritynews.com/samstealer-windows-data-theft/?utm_source=dlvr.it&utm_medium=blogger
The post Samstealer Attacking Windows Systems To Steal Sensitive Data appeared first on Cyber Security News.
https://cybersecuritynews.com/samstealer-windows-data-theft/?utm_source=dlvr.it&utm_medium=blogger
Antidot Mobile Malware As Google Play Update Hijacks Device Control
Cybersecurity experts have found a new banking Trojan horse for Android smartphones. It’s called Antidot. This clever malware pretends to be a real Google Play update app so people will download it. Once installed, Antidot takes over most of the infected devices, which puts personal and financial information at great risk. ANYRUN malware sandbox’s 8th Birthday […]
The post Antidot Mobile Malware As Google Play Update Hijacks Device Control appeared first on Cyber Security News.
https://cybersecuritynews.com/antidot-mobile-malware/?utm_source=dlvr.it&utm_medium=blogger
The post Antidot Mobile Malware As Google Play Update Hijacks Device Control appeared first on Cyber Security News.
https://cybersecuritynews.com/antidot-mobile-malware/?utm_source=dlvr.it&utm_medium=blogger
Evolution of AI Technologies Fueling the Social Engineering Attacks
With the rise of AI technologies, scamming, the illegal act of tricking others in an unethical way to obtain money, steal intellectual property, or gain unauthorized access to assets, has changed a lot. Scammers, who are also sometimes called crooks or attackers, mostly use direct methods, such as calls, texts, emails, messengers, social media, and […]
The post Evolution of AI Technologies Fueling the Social Engineering Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/evolution-ai-technologies-fueling/?utm_source=dlvr.it&utm_medium=blogger
The post Evolution of AI Technologies Fueling the Social Engineering Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/evolution-ai-technologies-fueling/?utm_source=dlvr.it&utm_medium=blogger
Latrodectus Malware Loader Emerges as IcedID's Successor in Phishing Campaigns
Cybersecurity researchers have observed a spike in email phishing campaigns starting early March 2024 that delivers Latrodectus, a nascent malware loader believed to be the successor to the IcedID malware.
"These campaigns typically involve a recognizable infection chain involving oversized JavaScript files that utilize WMI's ability to invoke msiexec.exe and install a remotely-hosted MSI
https://thehackernews.com/2024/05/latrodectus-malware-loader-emerges-as.html?utm_source=dlvr.it&utm_medium=blogger
"These campaigns typically involve a recognizable infection chain involving oversized JavaScript files that utilize WMI's ability to invoke msiexec.exe and install a remotely-hosted MSI
https://thehackernews.com/2024/05/latrodectus-malware-loader-emerges-as.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, May 19, 2024
Why data breaches have become ‘normalized’ and 6 things CISOs can do to prevent them
It’s crucial that CISOs and their teams ensure employees are aware of vulnerabilities, and build a system resilient to breaches. This article has been indexed from Security News | VentureBeat Read the original article: Why data breaches have become ‘normalized’…
Read more →
https://www.itsecuritynews.info/why-data-breaches-have-become-normalized-and-6-things-cisos-can-do-to-prevent-them/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/why-data-breaches-have-become-normalized-and-6-things-cisos-can-do-to-prevent-them/?utm_source=dlvr.it&utm_medium=blogger
Cyber Security News Weekly Round-Up (Vulnerabilities, Cyber Attacks, Threats & New Stories)
The latest threats, vulnerabilities, data breaches, and defensive countermeasures are covered in the weekly cybersecurity news recap. In order to enhance your security posture and defenses, it is essential that you have up-to-date knowledge on two key things like emerging cyber risks and attack vectors. Dynamic threats may be overcome by keeping situational vigilance across […]
The post Cyber Security News Weekly Round-Up (Vulnerabilities, Cyber Attacks, Threats & New Stories) appeared first on Cyber Security News.
https://cybersecuritynews.com/cyber-security-news-weekly-round-up-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
The post Cyber Security News Weekly Round-Up (Vulnerabilities, Cyber Attacks, Threats & New Stories) appeared first on Cyber Security News.
https://cybersecuritynews.com/cyber-security-news-weekly-round-up-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
Chinese Nationals Arrested for Laundering $73 Million in Pig Butchering Crypto Scam
The U.S. Department of Justice (DoJ) has charged two arrested Chinese nationals for allegedly orchestrating a pig butchering scam that laundered at least $73 million from victims through shell companies.
The individuals, Daren Li, 41, and Yicheng Zhang, 38, were arrested in Atlanta and Los Angeles on April 12 and May 16, respectively.
The foreign nationals have been "charged for leading a scheme
https://thehackernews.com/2024/05/chinese-nationals-arrested-for.html?utm_source=dlvr.it&utm_medium=blogger
The individuals, Daren Li, 41, and Yicheng Zhang, 38, were arrested in Atlanta and Los Angeles on April 12 and May 16, respectively.
The foreign nationals have been "charged for leading a scheme
https://thehackernews.com/2024/05/chinese-nationals-arrested-for.html?utm_source=dlvr.it&utm_medium=blogger
Quantum Navigation Systems: Safeguarding Against GPS Spoofing
Britain has achieved a world-first with a series of test flights that show the key technologies of a future quantum navigation system meant to counter one of the most potentially dangerous, yet little discussed, dangers to transportation: GPS jamming and…
Read more →
https://www.itsecuritynews.info/quantum-navigation-systems-safeguarding-against-gps-spoofing/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/quantum-navigation-systems-safeguarding-against-gps-spoofing/?utm_source=dlvr.it&utm_medium=blogger
Grandoreiro Banking Trojan Resurfaces, Targeting Over 1,500 Banks Worldwide
The threat actors behind the Windows-based Grandoreiro banking trojan have returned in a global campaign since March 2024 following a law enforcement takedown in January.
The large-scale phishing attacks, likely facilitated by other cybercriminals via a malware-as-a-service (MaaS) model, target over 1,500 banks across the world, spanning more than 60 countries in Central and South
https://thehackernews.com/2024/05/grandoreiro-banking-trojan-resurfaces.html?utm_source=dlvr.it&utm_medium=blogger
The large-scale phishing attacks, likely facilitated by other cybercriminals via a malware-as-a-service (MaaS) model, target over 1,500 banks across the world, spanning more than 60 countries in Central and South
https://thehackernews.com/2024/05/grandoreiro-banking-trojan-resurfaces.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, May 18, 2024
LATRODECTUS Loader Getting Popular Among Cybercriminals, Is It Replacing ICEDID!
Hackers use loaders to bypass security measures and run harmful code in a genuine process’s memory themselves. This makes it possible for malware payloads to be quietly loaded into the system without being discovered by any of the many file execution monitoring security solutions. Cybersecurity researchers at Elastic Security Labs recently discovered that LATRODECTUS loader […]
The post LATRODECTUS Loader Getting Popular Among Cybercriminals, Is It Replacing ICEDID! appeared first on Cyber Security News.
https://cybersecuritynews.com/latrodectus-loader-rising-threat/?utm_source=dlvr.it&utm_medium=blogger
The post LATRODECTUS Loader Getting Popular Among Cybercriminals, Is It Replacing ICEDID! appeared first on Cyber Security News.
https://cybersecuritynews.com/latrodectus-loader-rising-threat/?utm_source=dlvr.it&utm_medium=blogger
Friday, May 17, 2024
Kinsing Hacker Group Exploits More Flaws to Expand Botnet for Cryptojacking
The cryptojacking group known as Kinsing has demonstrated its ability to continuously evolve and adapt, proving to be a persistent threat by swiftly integrating newly disclosed vulnerabilities to exploit arsenal and expand its botnet.
The findings come from cloud security firm Aqua, which described the threat actor as actively orchestrating illicit cryptocurrency mining
https://thehackernews.com/2024/05/kinsing-hacker-group-exploits-more.html?utm_source=dlvr.it&utm_medium=blogger
The findings come from cloud security firm Aqua, which described the threat actor as actively orchestrating illicit cryptocurrency mining
https://thehackernews.com/2024/05/kinsing-hacker-group-exploits-more.html?utm_source=dlvr.it&utm_medium=blogger
How to Use Threat Intelligence Feeds for SOC/DFIR Teams
Threat intelligence feeds provide real-time updates on indicators of compromise (IOCs), such as malicious IPs and URLs. Security researchers and organizations share IOCs with feed vendors, who then analyze and validate them before distributing the information to subscribers. Security systems can then ingest these IOCs to identify and block potential threats, which essentially grants organizations […]
The post How to Use Threat Intelligence Feeds for SOC/DFIR Teams appeared first on Cyber Security News.
https://cybersecuritynews.com/how-to-use-threat-intelligence-feeds/?utm_source=dlvr.it&utm_medium=blogger
The post How to Use Threat Intelligence Feeds for SOC/DFIR Teams appeared first on Cyber Security News.
https://cybersecuritynews.com/how-to-use-threat-intelligence-feeds/?utm_source=dlvr.it&utm_medium=blogger
New Cyber Attack Targeting Facebook Business Accounts
The email campaign impersonates the Facebook Ads Team to trick users into clicking a malicious link, as the email leverages social engineering tactics like sender name spoofing and urgency to appear legitimate. Grammatical errors and a suspicious link embedded in a button are giveaways of the phishing attempt. Hovering over the button reveals the true […]
The post New Cyber Attack Targeting Facebook Business Accounts appeared first on Cyber Security News.
https://cybersecuritynews.com/facebook-ad-phishing-attack/?utm_source=dlvr.it&utm_medium=blogger
The post New Cyber Attack Targeting Facebook Business Accounts appeared first on Cyber Security News.
https://cybersecuritynews.com/facebook-ad-phishing-attack/?utm_source=dlvr.it&utm_medium=blogger
CISA Warns of Actively Exploited D-Link Router Vulnerabilities - Patch Now
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added two security flaws impacting D-Link routers to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The list of vulnerabilities is as follows -
CVE-2014-100005 - A cross-site request forgery (CSRF) vulnerability impacting D-Link DIR-600 routers that allows an
https://thehackernews.com/2024/05/cisa-warns-of-actively-exploited-d-link.html?utm_source=dlvr.it&utm_medium=blogger
The list of vulnerabilities is as follows -
CVE-2014-100005 - A cross-site request forgery (CSRF) vulnerability impacting D-Link DIR-600 routers that allows an
https://thehackernews.com/2024/05/cisa-warns-of-actively-exploited-d-link.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, May 16, 2024
Exabeam Recognized as a Leader in the 2024 Gartner® Magic Quadrant™ for SIEM, for the Fifth Year
Global cybersecurity leader that delivers AI-driven security operations and has been recognized as a Leader in the Gartner Magic Quadrant Exabeam, a leading global entity in AI-driven security operations, today announced its designation as a Leader in the 2024 Gartner®…
Read more →
https://www.itsecuritynews.info/exabeam-recognized-as-a-leader-in-the-2024-gartner-magic-quadrant-for-siem-for-the-fifth-year-19/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/exabeam-recognized-as-a-leader-in-the-2024-gartner-magic-quadrant-for-siem-for-the-fifth-year-19/?utm_source=dlvr.it&utm_medium=blogger
CrowdStrike launches advanced SIEM to power the AI-native SOC at RSAC 2024
With attackers setting speed records for breakouts and tool download times, every security operations center (SOC) team needs to consider how AI can help bend time in their favor. It takes just two minutes and seven seconds to move laterally…
Read more →
https://www.itsecuritynews.info/crowdstrike-launches-advanced-siem-to-power-the-ai-native-soc-at-rsac-2024/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/crowdstrike-launches-advanced-siem-to-power-the-ai-native-soc-at-rsac-2024/?utm_source=dlvr.it&utm_medium=blogger
North Korean Hackers Exploit Facebook Messenger in Targeted Malware Campaign
The North Korea-linked Kimsuky hacking group has been attributed to a new social engineering attack that employs fictitious Facebook accounts to targets via Messenger and ultimately delivers malware.
"The threat actor created a Facebook account with a fake identity disguised as a public official working in the North Korean human rights field," South Korean cybersecurity company Genians
https://thehackernews.com/2024/05/north-korean-hackers-exploit-facebook.html?utm_source=dlvr.it&utm_medium=blogger
"The threat actor created a Facebook account with a fake identity disguised as a public official working in the North Korean human rights field," South Korean cybersecurity company Genians
https://thehackernews.com/2024/05/north-korean-hackers-exploit-facebook.html?utm_source=dlvr.it&utm_medium=blogger
PoC Exploit Released for Ivanti EPMM MobileIron Core
A newly disclosed vulnerability, CVE-2024-22026, has been found in Ivanti Endpoint Manager Mobile (EPMM), formerly MobileIron Core. This vulnerability allows a local attacker to gain root access to affected systems. The severity of this vulnerability is currently undetermined. CVE-2024-22026: Local Privilege Escalation Vulnerability The attack vector for CVE-2024-22026 is local, meaning the attacker must have […]
The post PoC Exploit Released for Ivanti EPMM MobileIron Core appeared first on Cyber Security News.
https://cybersecuritynews.com/poc-exploit-released/?utm_source=dlvr.it&utm_medium=blogger
The post PoC Exploit Released for Ivanti EPMM MobileIron Core appeared first on Cyber Security News.
https://cybersecuritynews.com/poc-exploit-released/?utm_source=dlvr.it&utm_medium=blogger
Researchers Uncover 11 Security Flaws in GE HealthCare Ultrasound Machines
Security researchers have disclosed almost a dozen security flaws impacting the GE HealthCare Vivid Ultrasound product family that could be exploited by malicious actors to tamper with patient data and even install ransomware under certain circumstances.
"The impacts enabled by these flaws are manifold: from the implant of ransomware on the ultrasound machine to the access and manipulation of
https://thehackernews.com/2024/05/researchers-uncover-11-security-flaws.html?utm_source=dlvr.it&utm_medium=blogger
"The impacts enabled by these flaws are manifold: from the implant of ransomware on the ultrasound machine to the access and manipulation of
https://thehackernews.com/2024/05/researchers-uncover-11-security-flaws.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, May 15, 2024
Google Patches Yet Another Actively Exploited Chrome Zero-Day Vulnerability
Google has rolled out fixes to address a set of nine security issues in its Chrome browser, including a new zero-day that has been exploited in the wild.
Assigned the CVE identifier CVE-2024-4947, the vulnerability relates to a type confusion bug in the V8 JavaScript and WebAssembly engine. It was reported by Kaspersky researchers Vasily Berdnikov and Boris
https://thehackernews.com/2024/05/google-patches-yet-another-actively.html?utm_source=dlvr.it&utm_medium=blogger
Assigned the CVE identifier CVE-2024-4947, the vulnerability relates to a type confusion bug in the V8 JavaScript and WebAssembly engine. It was reported by Kaspersky researchers Vasily Berdnikov and Boris
https://thehackernews.com/2024/05/google-patches-yet-another-actively.html?utm_source=dlvr.it&utm_medium=blogger
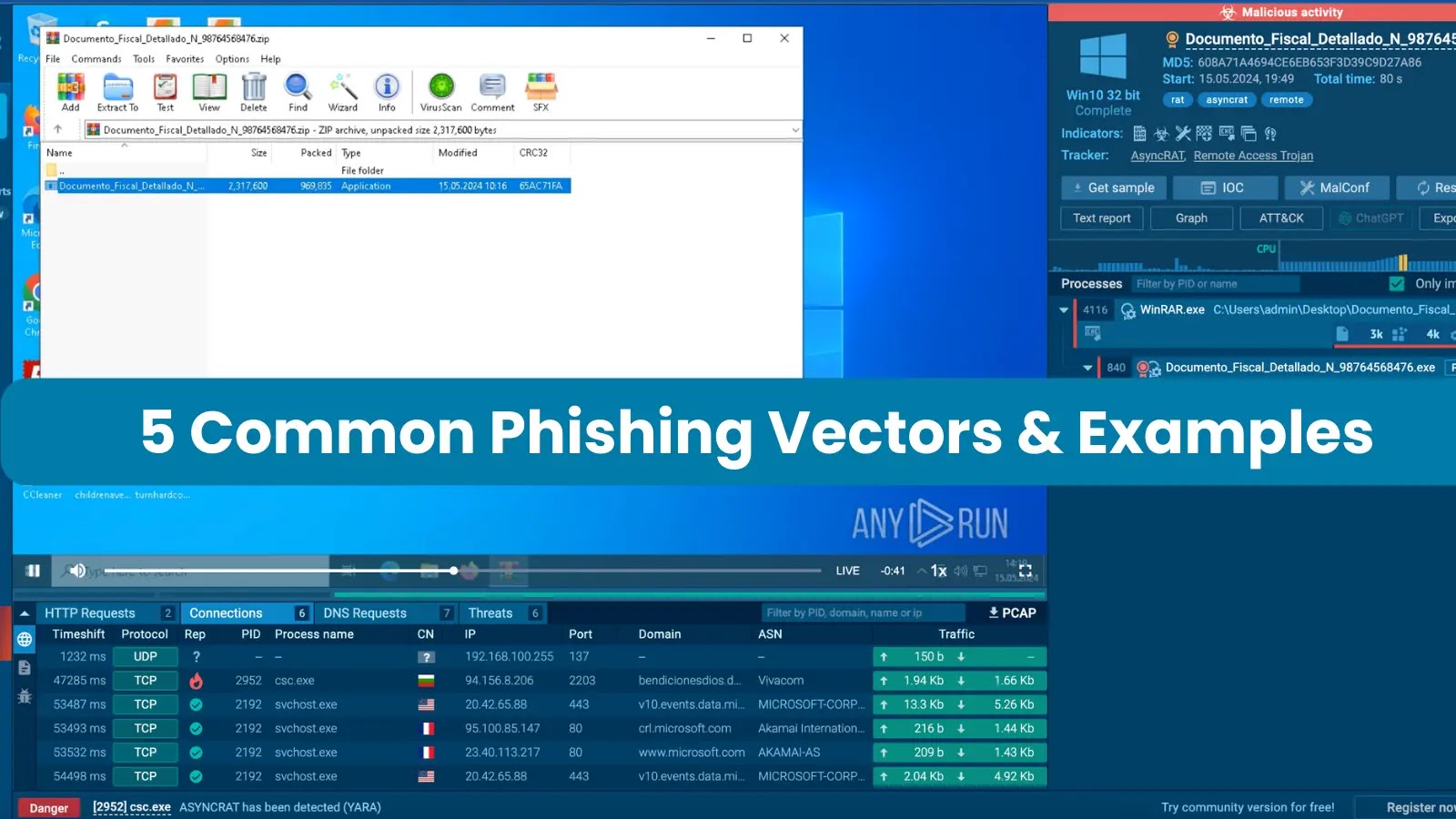
5 Common Phishing Vectors and Examples – 2024
Phishing attacks can be executed through various means, such as SMS and phone calls, but the most prevalent method involves sending victims emails containing malicious attachments. These may come in various forms, but they most often belong to one of the following categories: executable files, office documents, archives, PDFs, or links. Let’s take a closer […]
The post 5 Common Phishing Vectors and Examples – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/5-common-phishing-vectors/?utm_source=dlvr.it&utm_medium=blogger
The post 5 Common Phishing Vectors and Examples – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/5-common-phishing-vectors/?utm_source=dlvr.it&utm_medium=blogger
New Wi-Fi ‘SSID Confusion’ Attack Let Attackers connecting To Malicious Network
A design flaw in the IEEE 802.11 standard allows for SSID spoofing in WPA2 and WPA3 networks. While authentication protocols prevent unauthorized access points, they don’t guarantee that the SSID displayed on the client device matches the actual network’s SSID. The vulnerability enables attackers to create a rogue access point with a spoofed SSID, tricking […]
The post New Wi-Fi ‘SSID Confusion’ Attack Let Attackers connecting To Malicious Network appeared first on Cyber Security News.
https://cybersecuritynews.com/wi-fi-ssid-confusion-attack/?utm_source=dlvr.it&utm_medium=blogger
The post New Wi-Fi ‘SSID Confusion’ Attack Let Attackers connecting To Malicious Network appeared first on Cyber Security News.
https://cybersecuritynews.com/wi-fi-ssid-confusion-attack/?utm_source=dlvr.it&utm_medium=blogger
(Cyber) Risk = Probability of Occurrence x Damage
Here’s How to Enhance Your Cyber Resilience with CVSS
In late 2023, the Common Vulnerability Scoring System (CVSS) v4.0 was unveiled, succeeding the eight-year-old CVSS v3.0, with the aim to enhance vulnerability assessment for both industry and the public. This latest version introduces additional metrics like safety and automation to address criticism of lacking granularity
https://thehackernews.com/2024/05/get-cyber-resilient-with-cvss.html?utm_source=dlvr.it&utm_medium=blogger
In late 2023, the Common Vulnerability Scoring System (CVSS) v4.0 was unveiled, succeeding the eight-year-old CVSS v3.0, with the aim to enhance vulnerability assessment for both industry and the public. This latest version introduces additional metrics like safety and automation to address criticism of lacking granularity
https://thehackernews.com/2024/05/get-cyber-resilient-with-cvss.html?utm_source=dlvr.it&utm_medium=blogger
Microsoft Patches 61 Flaws, Including Two Actively Exploited Zero-Days
Microsoft has addressed a total of 61 new security flaws in its software as part of its Patch Tuesday updates for May 2024, including two zero-days which have been actively exploited in the wild.
Of the 61 flaws, one is rated Critical, 59 are rated Important, and one is rated Moderate in severity. This is in addition to 30 vulnerabilities&
https://thehackernews.com/2024/05/microsoft-patches-61-flaws-including.html?utm_source=dlvr.it&utm_medium=blogger
Of the 61 flaws, one is rated Critical, 59 are rated Important, and one is rated Moderate in severity. This is in addition to 30 vulnerabilities&
https://thehackernews.com/2024/05/microsoft-patches-61-flaws-including.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, May 14, 2024
Microsoft is again named a Leader in the 2024 Gartner® Magic Quadrant™ for Security Information and Event Management
Microsoft is named a Leader in the 2024 Gartner® Magic Quadrant™ for Security Information and Event Management and positioned based on our Ability to Execute Completeness of vision. The post Microsoft is again named a Leader in the 2024 Gartner®…
Read more →
https://www.itsecuritynews.info/microsoft-is-again-named-a-leader-in-the-2024-gartner-magic-quadrant-for-security-information-and-event-management-39/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/microsoft-is-again-named-a-leader-in-the-2024-gartner-magic-quadrant-for-security-information-and-event-management-39/?utm_source=dlvr.it&utm_medium=blogger
Alert! Microsoft Fixes 60 Vulnerabilities With 2 Actively Exploited Zero-Days
In its May 2024 Patch Tuesday release, Microsoft addressed 60 vulnerabilities, including 2 zero-day vulnerabilities actively exploited in the wild. The updates cover a range of vulnerability categories. Zero-Day Vulnerabilities Addressed Microsoft has patched two actively exploited zero-day vulnerabilities in this update: CVE-2024-30040 – Windows MSHTML Platform Security Feature Bypass Vulnerability This flaw could enable […]
The post Alert! Microsoft Fixes 60 Vulnerabilities With 2 Actively Exploited Zero-Days appeared first on Cyber Security News.
https://cybersecuritynews.com/microsoft-security-update-may-2024/?utm_source=dlvr.it&utm_medium=blogger
The post Alert! Microsoft Fixes 60 Vulnerabilities With 2 Actively Exploited Zero-Days appeared first on Cyber Security News.
https://cybersecuritynews.com/microsoft-security-update-may-2024/?utm_source=dlvr.it&utm_medium=blogger
New Chrome Zero-Day Vulnerability CVE-2024-4761 Under Active Exploitation
Google on Monday shipped emergency fixes to address a new zero-day flaw in the Chrome web browser that has come under active exploitation in the wild.
The high-severity vulnerability, tracked as CVE-2024-4761, is an out-of-bounds write bug impacting the V8 JavaScript and WebAssembly engine. It was reported anonymously on May 9, 2024.
Out-of-bounds write bugs could be typically
https://thehackernews.com/2024/05/new-chrome-zero-day-vulnerability-cve.html?utm_source=dlvr.it&utm_medium=blogger
The high-severity vulnerability, tracked as CVE-2024-4761, is an out-of-bounds write bug impacting the V8 JavaScript and WebAssembly engine. It was reported anonymously on May 9, 2024.
Out-of-bounds write bugs could be typically
https://thehackernews.com/2024/05/new-chrome-zero-day-vulnerability-cve.html?utm_source=dlvr.it&utm_medium=blogger
Ongoing Campaign Bombards Enterprises with Spam Emails and Phone Calls
Cybersecurity researchers have uncovered an ongoing social engineering campaign that bombards enterprises with spam emails with the goal of obtaining initial access to their environments for follow-on exploitation.
"The incident involves a threat actor overwhelming a user's email with junk and calling the user, offering assistance," Rapid7 researchers Tyler McGraw, Thomas Elkins, and
https://thehackernews.com/2024/05/ongoing-campaign-bombarded-enterprises.html?utm_source=dlvr.it&utm_medium=blogger
"The incident involves a threat actor overwhelming a user's email with junk and calling the user, offering assistance," Rapid7 researchers Tyler McGraw, Thomas Elkins, and
https://thehackernews.com/2024/05/ongoing-campaign-bombarded-enterprises.html?utm_source=dlvr.it&utm_medium=blogger
Apple and Google Launch Cross-Platform Feature to Detect Unwanted Bluetooth Tracking Devices
Apple and Google on Monday officially announced the rollout of a new feature that notifies users across both iOS and Android if a Bluetooth tracking device is being used to stealthily keep tabs on them without their knowledge or consent.
"This will help mitigate the misuse of devices designed to help keep track of belongings," the companies said in a joint statement, adding it aims to address "
https://thehackernews.com/2024/05/apple-and-google-launch-cross-platform.html?utm_source=dlvr.it&utm_medium=blogger
"This will help mitigate the misuse of devices designed to help keep track of belongings," the companies said in a joint statement, adding it aims to address "
https://thehackernews.com/2024/05/apple-and-google-launch-cross-platform.html?utm_source=dlvr.it&utm_medium=blogger
Monday, May 13, 2024
‘Got that boomer!’: How cybercriminals steal one-time passcodes for SIM swap attacks and raiding bank accounts
Estate is an invite-only website that has helped hundreds of attackers make thousands of phone calls aimed at stealing account passcodes, according to its leaked database. © 2024 TechCrunch. All rights reserved. For personal use only. This article has been…
Read more →
https://www.itsecuritynews.info/got-that-boomer-how-cybercriminals-steal-one-time-passcodes-for-sim-swap-attacks-and-raiding-bank-accounts/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/got-that-boomer-how-cybercriminals-steal-one-time-passcodes-for-sim-swap-attacks-and-raiding-bank-accounts/?utm_source=dlvr.it&utm_medium=blogger
Russian hackers defaced local British news sites
A group of hackers that defines itself as “first-class Russian hackers” claims the defacement of hundreds of local and regional British newspaper websites. A group claiming to be “first-class Russian hackers” defaced numerous local and regional British newspaper websites owned…
Read more →
https://www.itsecuritynews.info/russian-hackers-defaced-local-british-news-sites/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/russian-hackers-defaced-local-british-news-sites/?utm_source=dlvr.it&utm_medium=blogger
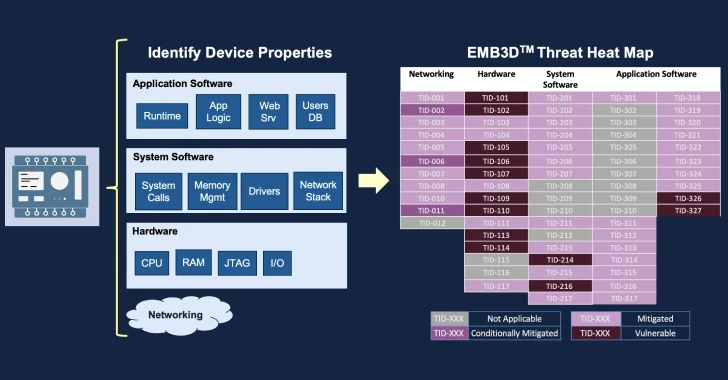
MITRE Unveils EMB3D: A Threat-Modeling Framework for Embedded Devices
The MITRE Corporation has officially made available a new threat-modeling framework called EMB3D for makers of embedded devices used in critical infrastructure environments.
"The model provides a cultivated knowledge base of cyber threats to embedded devices, providing a common understanding of these threats with the security mechanisms required to mitigate them," the non-profit said
https://thehackernews.com/2024/05/mitre-unveils-emb3d-threat-modeling.html?utm_source=dlvr.it&utm_medium=blogger
"The model provides a cultivated knowledge base of cyber threats to embedded devices, providing a common understanding of these threats with the security mechanisms required to mitigate them," the non-profit said
https://thehackernews.com/2024/05/mitre-unveils-emb3d-threat-modeling.html?utm_source=dlvr.it&utm_medium=blogger
The 2024 Browser Security Report Uncovers How Every Web Session Could be a Security Minefield
With the browser becoming the most prevalent workspace in the enterprise, it is also turning into a popular attack vector for cyber attackers. From account takeovers to malicious extensions to phishing attacks, the browser is a means for stealing sensitive data and accessing organizational systems.
Security leaders who are planning their security architecture
https://thehackernews.com/2024/05/the-2024-browser-security-report.html?utm_source=dlvr.it&utm_medium=blogger
Security leaders who are planning their security architecture
https://thehackernews.com/2024/05/the-2024-browser-security-report.html?utm_source=dlvr.it&utm_medium=blogger
Malicious Python Package Hides Sliver C2 Framework in Fake Requests Library Logo
Cybersecurity researchers have identified a malicious Python package that purports to be an offshoot of the popular requests library and has been found concealing a Golang-version of the Sliver command-and-control (C2) framework within a PNG image of the project's logo.
The package employing this steganographic trickery is requests-darwin-lite, which has been
https://thehackernews.com/2024/05/malicious-python-package-hides-sliver.html?utm_source=dlvr.it&utm_medium=blogger
The package employing this steganographic trickery is requests-darwin-lite, which has been
https://thehackernews.com/2024/05/malicious-python-package-hides-sliver.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, May 12, 2024
Stemming the Tide: Solving the Challenge of Password Reuse and Password-Stealing Malware
Password stealing malware is again rising with several attacks making the news cycle in recent months. For instance, a new password-stealing malware named Ov3r_Stealer was discovered on Facebook Ads, spreading by way of fake job opportunities. Further analysis into password-stealing…
Read more →
https://www.itsecuritynews.info/stemming-the-tide-solving-the-challenge-of-password-reuse-and-password-stealing-malware/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/stemming-the-tide-solving-the-challenge-of-password-reuse-and-password-stealing-malware/?utm_source=dlvr.it&utm_medium=blogger
WordPress Vulnerabilities, Exploiting LiteSpeed Cache and Email Subscribers Plugins
In recent cybersecurity developments, hackers have been leveraging a critical vulnerability within the LiteSpeed Cache plugin for WordPress to exploit websites running outdated versions. LiteSpeed Cache, a popular caching plugin utilized by over five million WordPress sites, is designed…
Read more →
https://www.itsecuritynews.info/wordpress-vulnerabilities-exploiting-litespeed-cache-and-email-subscribers-plugins/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/wordpress-vulnerabilities-exploiting-litespeed-cache-and-email-subscribers-plugins/?utm_source=dlvr.it&utm_medium=blogger
Cyber Crime Wave: Chinese Scammers Target Europe with Fake Designer Brands
In the last couple of weeks, there has been an increase in the number of people who have been duped into sharing their card details and other personal information with a network of fake online designer shops that are…
Read more →
https://www.itsecuritynews.info/cyber-crime-wave-chinese-scammers-target-europe-with-fake-designer-brands/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/cyber-crime-wave-chinese-scammers-target-europe-with-fake-designer-brands/?utm_source=dlvr.it&utm_medium=blogger
Cyber Security News Weekly Round-Up (Vulnerabilities, Cyber Attacks, Threats & New Stories)
Staying informed is the key in this dynamic battle of cybersecurity, and due to this, the weekly news recap provides you with the newest trends, weaknesses, infringements found, and some possible defense mechanisms. Quickly knowing about new cyber risks and attack vectors lets you immediately strengthen your defenses and preventive measures. Keeping alert situational awareness […]
The post Cyber Security News Weekly Round-Up (Vulnerabilities, Cyber Attacks, Threats & New Stories) appeared first on Cyber Security News.
https://cybersecuritynews.com/cyber-security-news-weekly-may/?utm_source=dlvr.it&utm_medium=blogger
The post Cyber Security News Weekly Round-Up (Vulnerabilities, Cyber Attacks, Threats & New Stories) appeared first on Cyber Security News.
https://cybersecuritynews.com/cyber-security-news-weekly-may/?utm_source=dlvr.it&utm_medium=blogger
IT Security News Daily Summary 2024-05-11
Ohio Lottery data breach impacted over 538,000 individuals Ascension Cyber Attack Heightens Focus on Healthcare Cybersecurity Measures Microsoft Introduces Innovative AI Model for Intelligence Analysis Critical infrastructure security will stay poor unless everyone pulls together USENIX Security ’23 – Don’t…
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2024-05-11/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2024-05-11/?utm_source=dlvr.it&utm_medium=blogger
Saturday, May 11, 2024
In it to win it! WeLiveSecurity shortlisted for European Security Blogger Awards
We’re thrilled to announce that WeLiveSecurity has been named a finalist in the Corporates – Best Cybersecurity Vendor Blog category of the European Security Blogger Awards 2024 This article has been indexed from WeLiveSecurity Read the original article: In it…
Read more →
https://www.itsecuritynews.info/in-it-to-win-it-welivesecurity-shortlisted-for-european-security-blogger-awards/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/in-it-to-win-it-welivesecurity-shortlisted-for-european-security-blogger-awards/?utm_source=dlvr.it&utm_medium=blogger
How to talk about climate change – and what motivates people to action: An interview with Katharine Hayhoe
We spoke to climate scientist Katharine Hayhoe about intersections between climate action, human psychology and spirituality, and how to channel anxiety about the state of our planet into meaningful action This article has been indexed from WeLiveSecurity Read the original…
Read more →
https://www.itsecuritynews.info/how-to-talk-about-climate-change-and-what-motivates-people-to-action-an-interview-with-katharine-hayhoe/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/how-to-talk-about-climate-change-and-what-motivates-people-to-action-an-interview-with-katharine-hayhoe/?utm_source=dlvr.it&utm_medium=blogger
Unpatchable VPN Vulnerability Exposes Data to Attackers: What You Need to Know
In a recent revelation that has sent shockwaves through the cybersecurity community, researchers have unearthed a significant vulnerability in virtual private networks (VPNs) dubbed TunnelVision. This flaw, described as deep and unpatchable, poses a substantial threat to data security,…
Read more →
https://www.itsecuritynews.info/unpatchable-vpn-vulnerability-exposes-data-to-attackers-what-you-need-to-know/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/unpatchable-vpn-vulnerability-exposes-data-to-attackers-what-you-need-to-know/?utm_source=dlvr.it&utm_medium=blogger
Microsoft Deploys Generative AI for US Spies
Plus: China is suspected in a hack targeting the UK’s military, the US Marines are testing gun-toting robotic dogs, and Dell suffers a data breach impacting 49 million customers. This article has been indexed from Security Latest Read the original…
Read more →
https://www.itsecuritynews.info/microsoft-deploys-generative-ai-for-us-spies/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/microsoft-deploys-generative-ai-for-us-spies/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)



.webp)



.webp)
.webp)


.png)








%20(1)%20(1).webp)


.webp)








.png)