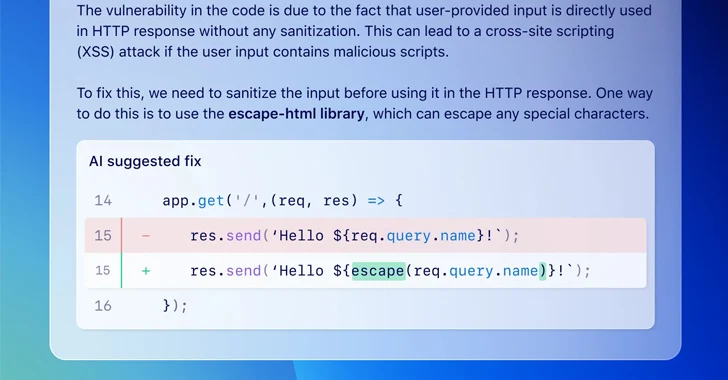
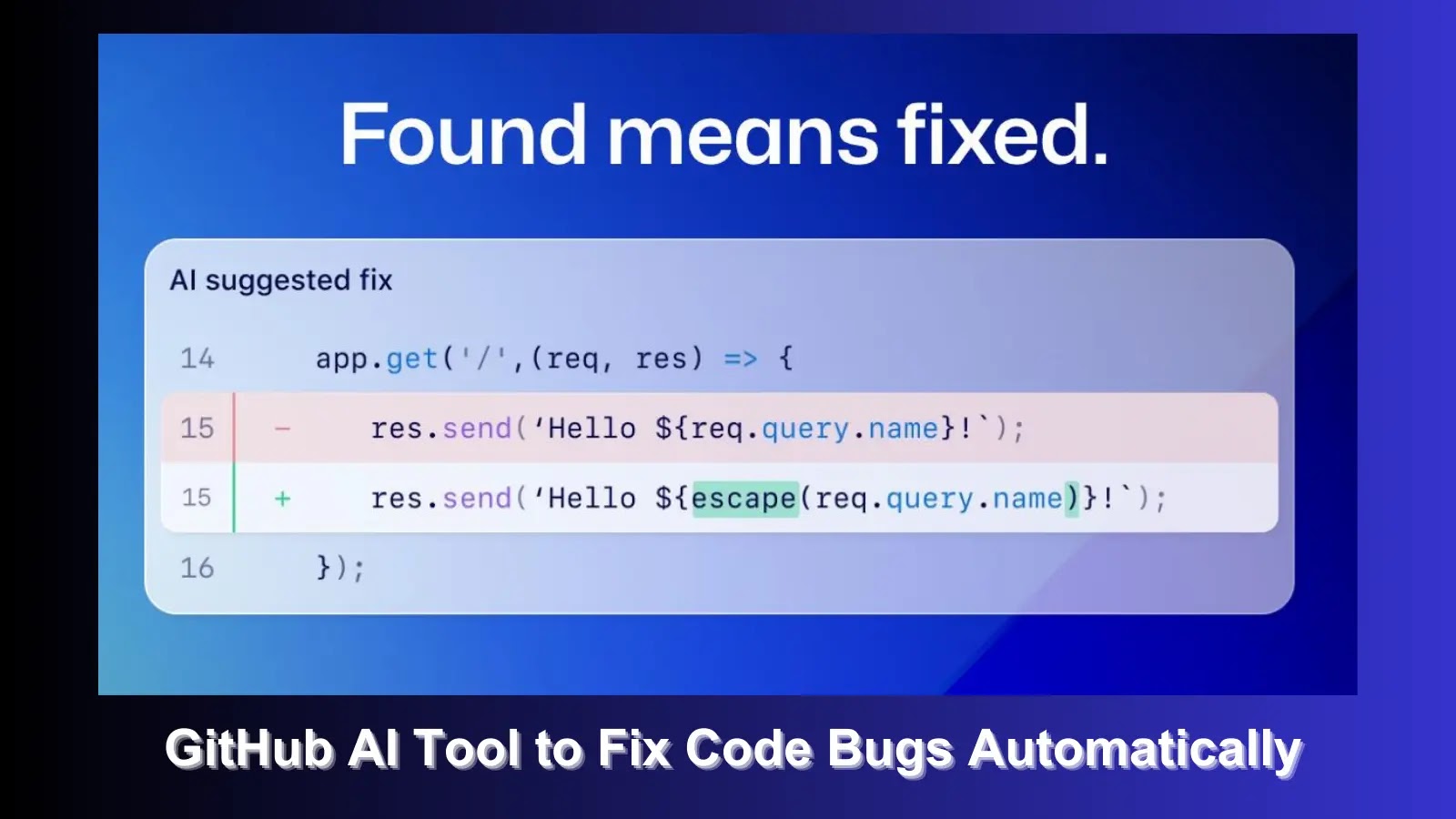
GitHub on Wednesday announced that it's making available a feature called code scanning autofix in public beta for all Advanced Security customers to provide targeted recommendations in an effort to avoid introducing new security issues.
"Powered by GitHub Copilot and CodeQL, code scanning autofix covers more than 90% of alert types in JavaScript, Typescript, Java, and
https://thehackernews.com/2024/03/github-launches-ai-powered-autofix-tool.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, March 21, 2024
New GitHub AI-Powered Tool Can Automatically Fix Code Vulnerabilities
In a groundbreaking move to enhance code security, GitHub has announced the launch of a new feature called “code scanning autofix,” which leverages the power of GitHub Copilot and CodeQL to resolve code vulnerabilities automatically. This innovative tool is designed to streamline the process of identifying and fixing security issues within codebases, marking a significant […]
The post New GitHub AI-Powered Tool Can Automatically Fix Code Vulnerabilities appeared first on Cyber Security News.
https://cybersecuritynews.com/github-ai-powered-tool/?utm_source=dlvr.it&utm_medium=blogger
The post New GitHub AI-Powered Tool Can Automatically Fix Code Vulnerabilities appeared first on Cyber Security News.
https://cybersecuritynews.com/github-ai-powered-tool/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, March 20, 2024
How to defend against phishing as a service and phishing kits
This post doesn’t have text content, please click on the link below to view the original article. This article has been indexed from Security Resources and Information from TechTarget Read the original article: How to defend against phishing as a…
Read more →
https://www.itsecuritynews.info/how-to-defend-against-phishing-as-a-service-and-phishing-kits/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/how-to-defend-against-phishing-as-a-service-and-phishing-kits/?utm_source=dlvr.it&utm_medium=blogger
Introducing Cisco U. Spotlight
Registration is open: Cisco U. Spotlight, a free live-streaming event on April 24, 2024. Ahead of the new virtual tech learning event’s debut, explore this year’s theme, “Connect. Secure. Observe.” and start planning your learning experience. This article has been…
Read more →
https://www.itsecuritynews.info/introducing-cisco-u-spotlight/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/introducing-cisco-u-spotlight/?utm_source=dlvr.it&utm_medium=blogger
New 'Loop DoS' Attack Impacts Hundreds of Thousands of Systems
A novel denial-of-service (DoS) attack vector has been found to target application-layer protocols based on User Datagram Protocol (UDP), putting hundreds of thousands of hosts likely at risk.
Called Loop DoS attacks, the approach pairs "servers of these protocols in such a way that they communicate with each other indefinitely," researchers from the CISPA Helmholtz-Center for
https://thehackernews.com/2024/03/new-loop-dos-attack-impacts-hundreds-of.html?utm_source=dlvr.it&utm_medium=blogger
Called Loop DoS attacks, the approach pairs "servers of these protocols in such a way that they communicate with each other indefinitely," researchers from the CISPA Helmholtz-Center for
https://thehackernews.com/2024/03/new-loop-dos-attack-impacts-hundreds-of.html?utm_source=dlvr.it&utm_medium=blogger
Researchers Detailed Red Teaming Malicious Use Cases For AI
Researchers investigated potential malicious uses of AI by threat actors and experimented with various AI models, including large language models, multimodal image models, and text-to-speech models. Importantly, they did not fine-tune or provide additional training to the models, simulating the resources threat actors might have access to and suggesting that in 2024, the most likely […]
The post Researchers Detailed Red Teaming Malicious Use Cases For AI appeared first on Cyber Security News.
https://cybersecuritynews.com/ai-malicious-use-cases-red-teaming/?utm_source=dlvr.it&utm_medium=blogger
The post Researchers Detailed Red Teaming Malicious Use Cases For AI appeared first on Cyber Security News.
https://cybersecuritynews.com/ai-malicious-use-cases-red-teaming/?utm_source=dlvr.it&utm_medium=blogger
U.S. EPA Forms Task Force to Protect Water Systems from Cyberattacks
The U.S. Environmental Protection Agency (EPA) said it's forming a new "Water Sector Cybersecurity Task Force" to devise methods to counter the threats faced by the water sector in the country.
"In addition to considering the prevalent vulnerabilities of water systems to cyberattacks and the challenges experienced by some systems in adopting best practices, this Task Force in its deliberations
https://thehackernews.com/2024/03/us-epa-forms-task-force-to-protect.html?utm_source=dlvr.it&utm_medium=blogger
"In addition to considering the prevalent vulnerabilities of water systems to cyberattacks and the challenges experienced by some systems in adopting best practices, this Task Force in its deliberations
https://thehackernews.com/2024/03/us-epa-forms-task-force-to-protect.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, March 19, 2024
Crypto scams more costly to the US than ransomware, Feds say
Latest figures paint grim picture of how viciously the elderly are targeted The FBI says investment fraud was the form of cybercrime that incurred the greatest financial loss for Americans last year.… This article has been indexed from The Register…
Read more →
https://www.itsecuritynews.info/crypto-scams-more-costly-to-the-us-than-ransomware-feds-say-2/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/crypto-scams-more-costly-to-the-us-than-ransomware-feds-say-2/?utm_source=dlvr.it&utm_medium=blogger
Beijing-backed cyberspies attacked 70+ orgs across 23 countries
Plus potential links to I-Soon, researchers say Chinese cyberspies have compromised at least 70 organizations, mostly government entities, and targeted more than 116 victims across the globe, according to security researchers.… This article has been indexed from The Register –…
Read more →
https://www.itsecuritynews.info/beijing-backed-cyberspies-attacked-70-orgs-across-23-countries/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/beijing-backed-cyberspies-attacked-70-orgs-across-23-countries/?utm_source=dlvr.it&utm_medium=blogger
APIs Drive the Majority of Internet Traffic and Cybercriminals are Taking Advantage
Application programming interfaces (APIs) are the connective tissue behind digital modernization, helping applications and databases exchange data more effectively. The State of API Security in 2024 Report from Imperva, a Thales company, found that the majority of internet traffic (71%) in 2023 was API calls. What’s more, a typical enterprise site saw an average of 1.5 billion API
https://thehackernews.com/2024/03/apis-drive-majority-of-internet-traffic.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2024/03/apis-drive-majority-of-internet-traffic.html?utm_source=dlvr.it&utm_medium=blogger
900+ Websites Exposing 100M+ Accounts Including Plaintext Passwords
New research has revealed that more than 900 websites had a serious misconfiguration, which exposed a massive 125 million user records, including plaintext passwords and sensitive billing information. These results come after researchers scanned the entire internet for exposed PII through misconfigured Firebase instances. Moreover, these were easy misconfigurations of security rules that had zero […]
The post 900+ Websites Exposing 100M+ Accounts Including Plaintext Passwords appeared first on Cyber Security News.
https://cybersecuritynews.com/900-websites-10m-passwords-plaintext-exposed/?utm_source=dlvr.it&utm_medium=blogger
The post 900+ Websites Exposing 100M+ Accounts Including Plaintext Passwords appeared first on Cyber Security News.
https://cybersecuritynews.com/900-websites-10m-passwords-plaintext-exposed/?utm_source=dlvr.it&utm_medium=blogger
E-Root Marketplace Admin Sentenced to 42 Months for Selling 350K Stolen Credentials
A 31-year-old Moldovan national has been sentenced to 42 months in prison in the U.S. for operating an illicit marketplace called E-Root Marketplace that offered for sale hundreds of thousands of compromised credentials, the Department of Justice (DoJ) announced.
Sandu Boris Diaconu was charged with conspiracy to commit access device and computer fraud and possession of 15 or more unauthorized
https://thehackernews.com/2024/03/e-root-marketplace-admin-sentenced-to.html?utm_source=dlvr.it&utm_medium=blogger
Sandu Boris Diaconu was charged with conspiracy to commit access device and computer fraud and possession of 15 or more unauthorized
https://thehackernews.com/2024/03/e-root-marketplace-admin-sentenced-to.html?utm_source=dlvr.it&utm_medium=blogger
Monday, March 18, 2024
Exploitation activity increasing on Fortinet vulnerability
This post doesn’t have text content, please click on the link below to view the original article. This article has been indexed from Security Resources and Information from TechTarget Read the original article: Exploitation activity increasing on Fortinet vulnerability
Read more →
https://www.itsecuritynews.info/exploitation-activity-increasing-on-fortinet-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/exploitation-activity-increasing-on-fortinet-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
US Government Investigating Facebook For Role In Illegal Drug Sales
The post US Government Investigating Facebook For Role In Illegal Drug Sales appeared first on Facecrooks. Facebook has routinely been criticized for failing to stop the sale of illegal goods on Marketplace. However, the company has thus far been able…
Read more →
https://www.itsecuritynews.info/us-government-investigating-facebook-for-role-in-illegal-drug-sales/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/us-government-investigating-facebook-for-role-in-illegal-drug-sales/?utm_source=dlvr.it&utm_medium=blogger
Chinese APT Hackers Exploits Government Web & Exchange Servers
A new Advanced Persistent Threat (APT) campaign, dubbed Earth Krahang, has emerged with a focus on infiltrating government entities across the globe. This campaign, active since early 2022, has been linked to a China-nexus threat actor, previously identified as Earth Lusca. Despite similarities, Earth Krahang operates with distinct infrastructure and employs unique backdoors, suggesting it’s […]
The post Chinese APT Hackers Exploits Government Web & Exchange Servers appeared first on Cyber Security News.
https://cybersecuritynews.com/earth-krahang/?utm_source=dlvr.it&utm_medium=blogger
The post Chinese APT Hackers Exploits Government Web & Exchange Servers appeared first on Cyber Security News.
https://cybersecuritynews.com/earth-krahang/?utm_source=dlvr.it&utm_medium=blogger
What is CNAPP ? How It Benefits for Multi-Cloud & Hybrid Infrastructure Protection
Multi-cloud and hybrid infrastructures are becoming the norm among enterprises nowadays. Around 9 in 10 companies use a multi-cloud strategy, while 8 in 10 adopt a hybrid. This is not surprising, given the many advantages, including vendor independence, simplified management, and enhanced efficiency. However, maintaining multiple clouds and hybrid systems can be challenging, especially regarding […]
The post What is CNAPP ? How It Benefits for Multi-Cloud & Hybrid Infrastructure Protection appeared first on Cyber Security News.
https://cybersecuritynews.com/cnapp/?utm_source=dlvr.it&utm_medium=blogger
The post What is CNAPP ? How It Benefits for Multi-Cloud & Hybrid Infrastructure Protection appeared first on Cyber Security News.
https://cybersecuritynews.com/cnapp/?utm_source=dlvr.it&utm_medium=blogger
Malware Alert! Hackers Attacking Indian Android users With Malware-as-a-Service
A new malware campaign has been identified targeting Android users in India. This sophisticated attack distributes malicious APK packages to compromise personal and financial information. The malware, available as a Malware-as-a-Service (MaaS) offering, underscores the evolving threat landscape in the digital age. Symantec, a global leader in cybersecurity, has stepped up to protect users from […]
The post Malware Alert! Hackers Attacking Indian Android users With Malware-as-a-Service appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-alert-hackers-android/?utm_source=dlvr.it&utm_medium=blogger
The post Malware Alert! Hackers Attacking Indian Android users With Malware-as-a-Service appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-alert-hackers-android/?utm_source=dlvr.it&utm_medium=blogger
Sunday, March 17, 2024
Fraudulent Antivirus Software Faces FTC Lawsuit After Raking in Millions
The US Federal Trade Commission filed a lawsuit alleging that two antivirus software packages, Restoro and Reimage, are counterfeit goods that have defrauded customers out of “ten of millions” of dollars. FTC investigators apparently went undercover and purchased the…
Read more →
https://www.itsecuritynews.info/fraudulent-antivirus-software-faces-ftc-lawsuit-after-raking-in-millions/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/fraudulent-antivirus-software-faces-ftc-lawsuit-after-raking-in-millions/?utm_source=dlvr.it&utm_medium=blogger
Private AI Chatbot Not Safe From Hackers With Encryption
AI helpers have assimilated into our daily lives in over a year and gained access to our most private information and worries. Sensitive information, such as personal health questions and professional consultations, is entrusted to these digital companions. While providers…
Read more →
https://www.itsecuritynews.info/private-ai-chatbot-not-safe-from-hackers-with-encryption/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/private-ai-chatbot-not-safe-from-hackers-with-encryption/?utm_source=dlvr.it&utm_medium=blogger
Cyber Attacks Threaten Essential Services
As per a recent report by BlackBerry, it was revealed that critical infrastructure providers faced a surge in cyberattacks during the latter part of 2023. Shockingly, these providers bore the brunt of 62% of all industry-related cyberattacks tracked from…
Read more →
https://www.itsecuritynews.info/cyber-attacks-threaten-essential-services/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/cyber-attacks-threaten-essential-services/?utm_source=dlvr.it&utm_medium=blogger
In the rush to build AI apps, please, please don’t leave security behind
Supply-chain attacks are definitely possible and could lead to data theft, system hijacking, and more Feature While in a rush to understand, build, and ship AI products, developers and data scientists are being urged to be mindful of security and…
Read more →
https://www.itsecuritynews.info/in-the-rush-to-build-ai-apps-please-please-dont-leave-security-behind/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/in-the-rush-to-build-ai-apps-please-please-dont-leave-security-behind/?utm_source=dlvr.it&utm_medium=blogger
Scranton School District in Pennsylvania suffered a ransomware attack
School districts continue to be under attack, schools in Scranton, Pennsylvania, are suffering a ransomware attack. This week, schools in Scranton, Pennsylvania, experienced a ransomware attack, resulting in IT outages. The Scranton School District is working with third-party forensic specialists…
Read more →
https://www.itsecuritynews.info/scranton-school-district-in-pennsylvania-suffered-a-ransomware-attack/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/scranton-school-district-in-pennsylvania-suffered-a-ransomware-attack/?utm_source=dlvr.it&utm_medium=blogger
Saturday, March 16, 2024
Decoding the data dilemma: Strategies for effective data deletion in the age of AI
Why navigating the intricacies of data deletion requires a strategic approach around legal, cybersecurity and financial implications. This article has been indexed from Security News | VentureBeat Read the original article: Decoding the data dilemma: Strategies for effective data deletion…
Read more →
https://www.itsecuritynews.info/decoding-the-data-dilemma-strategies-for-effective-data-deletion-in-the-age-of-ai/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/decoding-the-data-dilemma-strategies-for-effective-data-deletion-in-the-age-of-ai/?utm_source=dlvr.it&utm_medium=blogger
USENIX Security ’23 – Pushed By Accident: A Mixed-Methods Study On Strategies Of Handling Secret Information In Source Code Repositories
Authors/Presenters: Alexander Krause, Jan H. Klemmer, Nicolas Huaman, Dominik Wermke, Yasemin Acar, Sascha Fahl Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open Access. Originating from the conference’s events…
Read more →
https://www.itsecuritynews.info/usenix-security-23-pushed-by-accident-a-mixed-methods-study-on-strategies-of-handling-secret-information-in-source-code-repositories/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/usenix-security-23-pushed-by-accident-a-mixed-methods-study-on-strategies-of-handling-secret-information-in-source-code-repositories/?utm_source=dlvr.it&utm_medium=blogger
How to Identify & Monitor Insider Threat Indicators [A Guide]
How Your Life Events Invite Cyber & Physical Threats The post How to Identify & Monitor Insider Threat Indicators [A Guide] appeared first on Security Boulevard. This article has been indexed from Security Boulevard Read the original article: How to…
Read more →
https://www.itsecuritynews.info/how-to-identify-monitor-insider-threat-indicators-a-guide/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/how-to-identify-monitor-insider-threat-indicators-a-guide/?utm_source=dlvr.it&utm_medium=blogger
Hackers Using Cracked Software on GitHub to Spread RisePro Info Stealer
Cybersecurity researchers have found a number of GitHub repositories offering cracked software that are used to deliver an information stealer called RisePro.
The campaign, codenamed gitgub, includes 17 repositories associated with 11 different accounts, according to G DATA. The repositories in question have since been taken down by the Microsoft-owned subsidiary.
"The repositories look
https://thehackernews.com/2024/03/hackers-using-cracked-software-on.html?utm_source=dlvr.it&utm_medium=blogger
The campaign, codenamed gitgub, includes 17 repositories associated with 11 different accounts, according to G DATA. The repositories in question have since been taken down by the Microsoft-owned subsidiary.
"The repositories look
https://thehackernews.com/2024/03/hackers-using-cracked-software-on.html?utm_source=dlvr.it&utm_medium=blogger
How to Set Up a Network Research Laboratory for Malware Analysis (SOC & DFIR Teams)
To analyze a security vulnerability (CVE-2024-21413) in Outlook, a controlled environment can be set up using a virtual machine (ANY.RUN) within a local virtual private network (VPN). Researchers can learn more about the exploit by making a proof-of-concept (PoC) and testing its functionality in a separate environment. During the PoC execution, tools like Impacket can […]
The post How to Set Up a Network Research Laboratory for Malware Analysis (SOC & DFIR Teams) appeared first on Cyber Security News.
https://cybersecuritynews.com/how-to-set-up-a-network-research-laboratory/?utm_source=dlvr.it&utm_medium=blogger
The post How to Set Up a Network Research Laboratory for Malware Analysis (SOC & DFIR Teams) appeared first on Cyber Security News.
https://cybersecuritynews.com/how-to-set-up-a-network-research-laboratory/?utm_source=dlvr.it&utm_medium=blogger
Friday, March 15, 2024
Location Data Tracks Abortion Clinic Visits. Here’s What to Know
< div class=”field field–name-body field–type-text-with-summary field–label-hidden”> < div class=”field__items”> < div class=”field__item even”> Our concerns about the selling and misuse of location data for those seeking reproductive and gender healthcare are escalating amid a recent wave of cases and incidents…
Read more →
https://www.itsecuritynews.info/location-data-tracks-abortion-clinic-visits-heres-what-to-know/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/location-data-tracks-abortion-clinic-visits-heres-what-to-know/?utm_source=dlvr.it&utm_medium=blogger
Cloudflare loses 22% of its domains in Freenom .tk shutdown
A staggering 12.6 million domains on TLDs controlled by Freenom (.tk, .cf and .gq) have been shut down and no longer resolve, leading to a significant reduction in the number of websites hosted by Cloudflare. The disappearance of these websites…
Read more →
https://www.itsecuritynews.info/cloudflare-loses-22-of-its-domains-in-freenom-tk-shutdown/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/cloudflare-loses-22-of-its-domains-in-freenom-tk-shutdown/?utm_source=dlvr.it&utm_medium=blogger
GhostRace – New Data Leak Vulnerability Affects Modern CPUs
A group of researchers has discovered a new data leakage attack impacting modern CPU architectures supporting speculative execution.
Dubbed GhostRace (CVE-2024-2193), it is a variation of the transient execution CPU vulnerability known as Spectre v1 (CVE-2017-5753). The approach combines speculative execution and race conditions.
"All the common synchronization primitives implemented
https://thehackernews.com/2024/03/ghostrace-new-data-leak-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
Dubbed GhostRace (CVE-2024-2193), it is a variation of the transient execution CPU vulnerability known as Spectre v1 (CVE-2017-5753). The approach combines speculative execution and race conditions.
"All the common synchronization primitives implemented
https://thehackernews.com/2024/03/ghostrace-new-data-leak-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
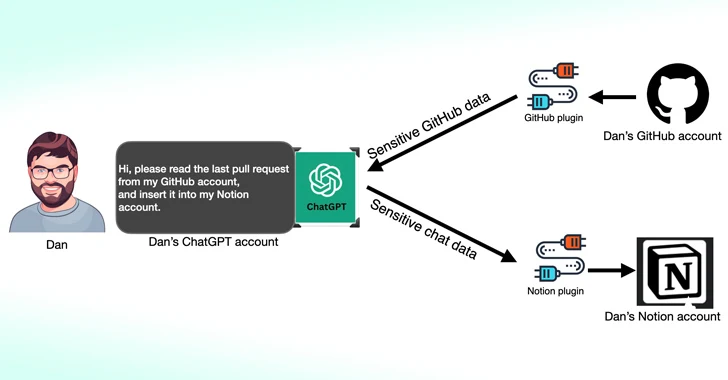
Third-Party ChatGPT Plugins Could Lead to Account Takeovers
Cybersecurity researchers have found that third-party plugins available for OpenAI ChatGPT could act as a new attack surface for threat actors looking to gain unauthorized access to sensitive data.
According to new research published by Salt Labs, security flaws found directly in ChatGPT and within the ecosystem could allow attackers to install malicious plugins without users' consent
https://thehackernews.com/2024/03/third-party-chatgpt-plugins-could-lead.html?utm_source=dlvr.it&utm_medium=blogger
According to new research published by Salt Labs, security flaws found directly in ChatGPT and within the ecosystem could allow attackers to install malicious plugins without users' consent
https://thehackernews.com/2024/03/third-party-chatgpt-plugins-could-lead.html?utm_source=dlvr.it&utm_medium=blogger
Malicious Ads Targeting Chinese Users with Fake Notepad++ and VNote Installers
Chinese users looking for legitimate software such as Notepad++ and VNote on search engines like Baidu are being targeted with malicious ads and bogus links to distribute trojanized versions of the software and ultimately deploy Geacon, a Golang-based implementation of Cobalt Strike.
“The malicious site found in the notepad++ search is distributed through an advertisement block,” Kaspersky
https://thehackernews.com/2024/03/malicious-ads-targeting-chinese-users.html?utm_source=dlvr.it&utm_medium=blogger
“The malicious site found in the notepad++ search is distributed through an advertisement block,” Kaspersky
https://thehackernews.com/2024/03/malicious-ads-targeting-chinese-users.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, March 14, 2024
Privacy Perils: Experts Warn of Pitfalls in Sharing Pregnancy Photos Online
Taking pregnancy pictures online can even lead to the creation of a digital identity for your child that could be exploited, according to data scientists. When a child appears online, experts say it puts them at risk of identity…
Read more →
https://www.itsecuritynews.info/privacy-perils-experts-warn-of-pitfalls-in-sharing-pregnancy-photos-online/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/privacy-perils-experts-warn-of-pitfalls-in-sharing-pregnancy-photos-online/?utm_source=dlvr.it&utm_medium=blogger
Not everything has to be a massive, global cyber attack
There are a few reasons why we’re so ready to jump to the “it’s a cyber attack!” This article has been indexed from Cisco Talos Blog Read the original article: Not everything has to be a massive, global cyber attack
Read more →
https://www.itsecuritynews.info/not-everything-has-to-be-a-massive-global-cyber-attack/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/not-everything-has-to-be-a-massive-global-cyber-attack/?utm_source=dlvr.it&utm_medium=blogger
LockBit Ransomware Hacker Ordered to Pay $860,000 After Guilty Plea in Canada
A 34-year-old Russian-Canadian national has been sentenced to nearly four years in jail in Canada for his participation in the LockBit global ransomware operation.
Mikhail Vasiliev, an Ontario resident, was originally arrested in November 2022 and charged by the U.S. Department of Justice (DoJ) with "conspiring with others to intentionally damage protected computers and to transmit
https://thehackernews.com/2024/03/lockbit-ransomware-hacker-ordered-to.html?utm_source=dlvr.it&utm_medium=blogger
Mikhail Vasiliev, an Ontario resident, was originally arrested in November 2022 and charged by the U.S. Department of Justice (DoJ) with "conspiring with others to intentionally damage protected computers and to transmit
https://thehackernews.com/2024/03/lockbit-ransomware-hacker-ordered-to.html?utm_source=dlvr.it&utm_medium=blogger
Researchers Uncover SnakeKeylogger Attacks, Techniques & Tactics
Threat actors use keyloggers to capture sensitive information by recording keystrokes on infected devices, as covert techniques and tactics allow them to steal valuable information without the victim’s knowledge. Governments or threat actors can deploy Keyloggers as espionage tools to gather intelligence or monitor their targets. Recently, the cybersecurity researchers at Splunk Threat Research Team […]
The post Researchers Uncover SnakeKeylogger Attacks, Techniques & Tactics appeared first on Cyber Security News.
https://cybersecuritynews.com/researchers-uncover-snakekeylogger/?utm_source=dlvr.it&utm_medium=blogger
The post Researchers Uncover SnakeKeylogger Attacks, Techniques & Tactics appeared first on Cyber Security News.
https://cybersecuritynews.com/researchers-uncover-snakekeylogger/?utm_source=dlvr.it&utm_medium=blogger
Fortinet Warns of Severe SQLi Vulnerability in FortiClientEMS Software
Fortinet has warned of a critical security flaw impacting its FortiClientEMS software that could allow attackers to achieve code execution on affected systems.
"An improper neutralization of special elements used in an SQL Command ('SQL Injection') vulnerability [CWE-89] in FortiClientEMS may allow an unauthenticated attacker to execute unauthorized code or commands via specifically crafted
https://thehackernews.com/2024/03/fortinet-warns-of-severe-sqli.html?utm_source=dlvr.it&utm_medium=blogger
"An improper neutralization of special elements used in an SQL Command ('SQL Injection') vulnerability [CWE-89] in FortiClientEMS may allow an unauthenticated attacker to execute unauthorized code or commands via specifically crafted
https://thehackernews.com/2024/03/fortinet-warns-of-severe-sqli.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, March 13, 2024
Microsoft Patch Tuesday March 2024 includes critical Hyper-V flaws
Microsoft patched 61 vulnerabilities in the March 2024 Patch Tuesday round, including two critical flaws in Hyper-V. This article has been indexed from Malwarebytes Read the original article: Microsoft Patch Tuesday March 2024 includes critical Hyper-V flaws
Read more →
https://www.itsecuritynews.info/microsoft-patch-tuesday-march-2024-includes-critical-hyper-v-flaws/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/microsoft-patch-tuesday-march-2024-includes-critical-hyper-v-flaws/?utm_source=dlvr.it&utm_medium=blogger
Demystifying a Common Cybersecurity Myth
One of the most common misconceptions in file upload cybersecurity is that certain tools are “enough” on their own—this is simply not the case. In our latest whitepaper OPSWAT CEO and Founder, Benny Czarny, takes a comprehensive look at what it takes to prevent malware threats in today’s ever-evolving file upload security landscape, and a big part of that is understanding where the
https://thehackernews.com/2024/03/demystifying-common-cybersecurity-myth.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2024/03/demystifying-common-cybersecurity-myth.html?utm_source=dlvr.it&utm_medium=blogger
PixPirate Android Banking Trojan Using New Evasion Tactic to Target Brazilian Users
The threat actors behind the PixPirate Android banking trojan are leveraging a new trick to evade detection on compromised devices and harvest sensitive information from users in Brazil.
The approach allows it to hide the malicious app’s icon from the home screen of the victim’s device, IBM said in a technical report published today.
“Thanks to this new technique, during PixPirate reconnaissance
https://thehackernews.com/2024/03/pixpirate-android-banking-trojan-using.html?utm_source=dlvr.it&utm_medium=blogger
The approach allows it to hide the malicious app’s icon from the home screen of the victim’s device, IBM said in a technical report published today.
“Thanks to this new technique, during PixPirate reconnaissance
https://thehackernews.com/2024/03/pixpirate-android-banking-trojan-using.html?utm_source=dlvr.it&utm_medium=blogger
Microsoft Patch Tuesday – Major Flaws In Office, Exchange And SQL Server
Microsoft published its March 2024 Patch Tuesday, which addressed almost 59 vulnerabilities in its products and none of them were Zero-day or publicly known vulnerabilities. Out of the newly released patches, two are classified as Critical and 57 are classified as Important in severity. The vulnerabilities in Skype, Microsoft Components for Android, Microsoft Windows and Windows […]
The post Microsoft Patch Tuesday – Major Flaws In Office, Exchange And SQL Server appeared first on Cyber Security News.
https://cybersecuritynews.com/microsoft-patch-tuesday-march-2024/?utm_source=dlvr.it&utm_medium=blogger
The post Microsoft Patch Tuesday – Major Flaws In Office, Exchange And SQL Server appeared first on Cyber Security News.
https://cybersecuritynews.com/microsoft-patch-tuesday-march-2024/?utm_source=dlvr.it&utm_medium=blogger
New Rust-based Backdoor Attacking Windows and Linux Systems
Rust’s strong focus on memory safety, which prevents common vulnerabilities such as buffer overflows, makes it a choice for threat actors to use Rust-based backdoors. Moreover, the performance of this language is appealing to many, and due to this, they prefer using it when creating malware that is both efficient and stealthy. Not only that, […]
The post New Rust-based Backdoor Attacking Windows and Linux Systems appeared first on Cyber Security News.
https://cybersecuritynews.com/new-rust-based-backdoor-attacking/?utm_source=dlvr.it&utm_medium=blogger
The post New Rust-based Backdoor Attacking Windows and Linux Systems appeared first on Cyber Security News.
https://cybersecuritynews.com/new-rust-based-backdoor-attacking/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, March 12, 2024
White House Summons UnitedHealth CEO Over Hack
This post doesn’t have text content, please click on the link below to view the original article. This article has been indexed from News ≈ Packet Storm Read the original article: White House Summons UnitedHealth CEO Over Hack
Read more →
https://www.itsecuritynews.info/white-house-summons-unitedhealth-ceo-over-hack/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/white-house-summons-unitedhealth-ceo-over-hack/?utm_source=dlvr.it&utm_medium=blogger
Reject Nevada’s Attack on Encrypted Messaging, EFF Tells Court
Nevada Makes Backward Argument That Insecure Communication Makes Children Safer < div class=”field field–name-body field–type-text-with-summary field–label-hidden”> < div class=”field__items”> < div class=”field__item even”> LAS VEGAS — The Electronic Frontier Foundation (EFF) and a coalition of partners urged a federal court…
Read more →
https://www.itsecuritynews.info/reject-nevadas-attack-on-encrypted-messaging-eff-tells-court/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/reject-nevadas-attack-on-encrypted-messaging-eff-tells-court/?utm_source=dlvr.it&utm_medium=blogger
ICS Patch Tuesday: Siemens Ruggedcom Devices Impacted by 45 Fortinet Vulnerabilities
Siemens and Schneider Electric publish March 2024 Patch Tuesday advisories to inform customers about over 200 vulnerabilities. The post ICS Patch Tuesday: Siemens Ruggedcom Devices Impacted by 45 Fortinet Vulnerabilities appeared first on SecurityWeek. This article has been indexed from…
Read more →
https://www.itsecuritynews.info/ics-patch-tuesday-siemens-ruggedcom-devices-impacted-by-45-fortinet-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/ics-patch-tuesday-siemens-ruggedcom-devices-impacted-by-45-fortinet-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
Remcos Everywhere! Attacking From a Weaponized Zip File
Cybersecurity circles are abuzz with the latest campaign involving the notorious Remote Control System (RAT), Remcos. This sophisticated malware has been making headlines for its widespread and targeted attacks, particularly in Eastern Europe. The recent surge in activities has seen Romania, Moldova, and neighboring countries falling victim to a cleverly disguised threat, masquerading as a […]
The post Remcos Everywhere! Attacking From a Weaponized Zip File appeared first on Cyber Security News.
https://cybersecuritynews.com/remcos-everywhere/?utm_source=dlvr.it&utm_medium=blogger
The post Remcos Everywhere! Attacking From a Weaponized Zip File appeared first on Cyber Security News.
https://cybersecuritynews.com/remcos-everywhere/?utm_source=dlvr.it&utm_medium=blogger
Guide: On-Prem is Dead. Have You Adjusted Your Web DLP Plan?
As the shift of IT infrastructure to cloud-based solutions celebrates its 10-year anniversary, it becomes clear that traditional on-premises approaches to data security are becoming obsolete. Rather than protecting the endpoint, DLP solutions need to refocus their efforts to where corporate data resides - in the browser.
A new guide by LayerX titled "On-Prem is Dead. Have You Adjusted Your Web
https://thehackernews.com/2024/03/data-leakage-prevention-in-age-of-cloud.html?utm_source=dlvr.it&utm_medium=blogger
A new guide by LayerX titled "On-Prem is Dead. Have You Adjusted Your Web
https://thehackernews.com/2024/03/data-leakage-prevention-in-age-of-cloud.html?utm_source=dlvr.it&utm_medium=blogger
Monday, March 11, 2024
Secrets Sensei: Conquering Secrets Management Challenges
In the realm of cybersecurity, the stakes are sky-high, and at its core lies secrets management — the foundational pillar upon which your security infrastructure rests. We're all familiar with the routine: safeguarding those API keys, connection strings, and certificates is non-negotiable. However, let's dispense with the pleasantries; this isn't a simple 'set it and forget it' scenario. It's
https://thehackernews.com/2024/03/secrets-sensei-conquering-secrets.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2024/03/secrets-sensei-conquering-secrets.html?utm_source=dlvr.it&utm_medium=blogger
Cisco Issues Patch for High-Severity VPN Hijacking Bug in Secure Client
Cisco has released patches to address a high-severity security flaw impacting its Secure Client software that could be exploited by a threat actor to open a VPN session with that of a targeted user.
The networking equipment company described the vulnerability, tracked as CVE-2024-20337 (CVSS score: 8.2), as allowing an unauthenticated, remote attacker to conduct a carriage return line feed (CRLF
https://thehackernews.com/2024/03/cisco-issues-patch-for-high-severity.html?utm_source=dlvr.it&utm_medium=blogger
The networking equipment company described the vulnerability, tracked as CVE-2024-20337 (CVSS score: 8.2), as allowing an unauthenticated, remote attacker to conduct a carriage return line feed (CRLF
https://thehackernews.com/2024/03/cisco-issues-patch-for-high-severity.html?utm_source=dlvr.it&utm_medium=blogger
QEMU Emulator Exploited as Tunneling Tool to Breach Company Network
Threat actors have been observed leveraging the QEMU open-source hardware emulator as tunneling software during a cyber attack targeting an unnamed "large company" to connect to their infrastructure.
While a number of legitimate tunneling tools like Chisel, FRP, ligolo, ngrok, and Plink have been used by adversaries to their advantage, the development marks the first QEMU that has been
https://thehackernews.com/2024/03/cybercriminals-utilize-qemu-emulator-as.html?utm_source=dlvr.it&utm_medium=blogger
While a number of legitimate tunneling tools like Chisel, FRP, ligolo, ngrok, and Plink have been used by adversaries to their advantage, the development marks the first QEMU that has been
https://thehackernews.com/2024/03/cybercriminals-utilize-qemu-emulator-as.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)







.webp)
%20(1).webp)










%20(1)%20(1).jpg)
.webp)



