In a critical security advisory, ConnectWise has alerted users of its ScreenConnect remote access software to patch their systems immediately due to two severe vulnerabilities discovered in versions 23.9.7 and earlier. These vulnerabilities, identified as CWE-288 and CWE–22, allow for authentication bypass and path traversal, posing a significant risk to the integrity and security of […]
The post ScreenConnect Security Flaw Let Attackers Bypass Authentication appeared first on Cyber Security News.
https://cybersecuritynews.com/screenconnect-security-flaw/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, February 21, 2024
Tuesday, February 20, 2024
Early adopters’ fast-tracking gen AI into production, according to new report
Healthcare, manufacturing and education industries see the greatest potential for gen AI and lead all others in their interest to become early adopters. This article has been indexed from Security News | VentureBeat Read the original article: Early adopters’ fast-tracking…
Read more →
https://www.itsecuritynews.info/early-adopters-fast-tracking-gen-ai-into-production-according-to-new-report/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/early-adopters-fast-tracking-gen-ai-into-production-according-to-new-report/?utm_source=dlvr.it&utm_medium=blogger
Singapore’s monetary authority advises banks to get busy protecting against quantum decryption
No time like the present, says central bank The Monetary Authority of Singapore (MAS) advised on Monday that financial institutions need to stay agile enough to adopt post-quantum cryptography (PQC) and quantum key distribution (QKD) technology, without significantly impacting systems…
Read more →
https://www.itsecuritynews.info/singapores-monetary-authority-advises-banks-to-get-busy-protecting-against-quantum-decryption/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/singapores-monetary-authority-advises-banks-to-get-busy-protecting-against-quantum-decryption/?utm_source=dlvr.it&utm_medium=blogger
Authentic or counterfeit? How QED Vault is using tokens to redefine asset ownership
One man’s quest to authenticate rare sneakers led to the first consumer blockchain-based tokenization platform. This article has been indexed from Latest stories for ZDNET in Security Read the original article: Authentic or counterfeit? How QED Vault is using tokens…
Read more →
https://www.itsecuritynews.info/authentic-or-counterfeit-how-qed-vault-is-using-tokens-to-redefine-asset-ownership/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/authentic-or-counterfeit-how-qed-vault-is-using-tokens-to-redefine-asset-ownership/?utm_source=dlvr.it&utm_medium=blogger
RSPAMD – Free Spam Filtering Tool to Analyse Email Threats With ANY RUN Sandbox
In a significant advancement for email security, ANY.RUN, a leader in malware analysis sandboxing, has unveiled a new module integrating RSPAMD into its Static Discovering feature. This RSPAMD integration marks a pivotal step in enhancing the detection and analysis of suspicious emails, providing users with an unparalleled toolset for identifying potential threats. ANY.RUN is a […]
The post RSPAMD – Free Spam Filtering Tool to Analyse Email Threats With ANY RUN Sandbox appeared first on Cyber Security News.
https://cybersecuritynews.com/rspamd-free-spam-filtering-tool/?utm_source=dlvr.it&utm_medium=blogger
The post RSPAMD – Free Spam Filtering Tool to Analyse Email Threats With ANY RUN Sandbox appeared first on Cyber Security News.
https://cybersecuritynews.com/rspamd-free-spam-filtering-tool/?utm_source=dlvr.it&utm_medium=blogger
Top 10 Best DDoS Protection Tools & Services – 2024
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to interrupt the regular traffic of a targeted server, service, or network by flooding the target or the area around it with Internet traffic. HTTP DDoS attacks went up by 15% from one quarter to the next, even though they went down by 35% from one […]
The post Top 10 Best DDoS Protection Tools & Services – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/ddos-protection-tools/?utm_source=dlvr.it&utm_medium=blogger
The post Top 10 Best DDoS Protection Tools & Services – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/ddos-protection-tools/?utm_source=dlvr.it&utm_medium=blogger
Monday, February 19, 2024
NSO Group’s Mysterious MOBILE & WIRELESS ‘MMS Fingerprint’ Hack Revealed
The “MMS Fingerprint” attack, a previously unidentified mobile network attack purportedly employed by spyware company NSO Group, is referenced in a single sentence in an agreement between NSO and Ghana’s telecom regulator. Because the hack is claimed to work on all three major smartphone operating systems (Blackberry, Android, and iOS), it was believed to be […]
The post NSO Group’s Mysterious MOBILE & WIRELESS ‘MMS Fingerprint’ Hack Revealed appeared first on Cyber Security News.
https://cybersecuritynews.com/mms-fingerprint-hack-revealed/?utm_source=dlvr.it&utm_medium=blogger
The post NSO Group’s Mysterious MOBILE & WIRELESS ‘MMS Fingerprint’ Hack Revealed appeared first on Cyber Security News.
https://cybersecuritynews.com/mms-fingerprint-hack-revealed/?utm_source=dlvr.it&utm_medium=blogger
IT Security News Daily Summary 2024-02-19
Do you need antivirus on Linux? Wyze camera breach let 13,000 strangers look into other people’s homes Anatsa Android banking Trojan expands to Slovakia, Slovenia, and Czechia Israeli El Al Alleges Hackers Targeted Flights in Mid-Air Hijack Attempt NSO Group…
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2024-02-19/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2024-02-19/?utm_source=dlvr.it&utm_medium=blogger
Do you need antivirus on Linux?
If you’ve been a Windows user for years, then you are well aware of the need for antivirus software. It’s a given. But does the same hold true for the open-source operating system? This article has been indexed from Latest…
Read more →
https://www.itsecuritynews.info/do-you-need-antivirus-on-linux/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/do-you-need-antivirus-on-linux/?utm_source=dlvr.it&utm_medium=blogger
How to Achieve the Best Risk-Based Alerting (Bye-Bye SIEM)
Did you know that Network Detection and Response (NDR) has become the most effective technology to detect cyber threats? In contrast to SIEM, NDR offers adaptive cybersecurity with reduced false alerts and efficient threat response.
Are you aware of Network Detection and Response (NDR) and how it’s become the most effective technology to detect cyber threats?
NDR massively
https://thehackernews.com/2024/02/bye-bye-siem-hello-risk-based-alerting.html?utm_source=dlvr.it&utm_medium=blogger
Are you aware of Network Detection and Response (NDR) and how it’s become the most effective technology to detect cyber threats?
NDR massively
https://thehackernews.com/2024/02/bye-bye-siem-hello-risk-based-alerting.html?utm_source=dlvr.it&utm_medium=blogger
Anatsa Android Trojan Bypasses Google Play Security, Expands Reach to New Countries
The Android banking trojan known as Anatsa has expanded its focus to include Slovakia, Slovenia, and Czechia as part of a new campaign observed in November 2023.
"Some of the droppers in the campaign successfully exploited the accessibility service, despite Google Play's enhanced detection and protection mechanisms," ThreatFabric said in a report shared with The Hacker News.
https://thehackernews.com/2024/02/anatsa-android-trojan-bypasses-google.html?utm_source=dlvr.it&utm_medium=blogger
"Some of the droppers in the campaign successfully exploited the accessibility service, despite Google Play's enhanced detection and protection mechanisms," ThreatFabric said in a report shared with The Hacker News.
https://thehackernews.com/2024/02/anatsa-android-trojan-bypasses-google.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 18, 2024
Iranian Hackers Target Middle East Policy Experts with New BASICSTAR Backdoor
The Iranian-origin threat actor known as Charming Kitten has been linked to a new set of attacks aimed at Middle East policy experts with a new backdoor called BASICSTAR by creating a fake webinar portal.
Charming Kitten, also called APT35, CharmingCypress, Mint Sandstorm, TA453, and Yellow Garuda, has a history of orchestrating a wide range of social engineering campaigns that cast a
https://thehackernews.com/2024/02/iranian-hackers-target-middle-east.html?utm_source=dlvr.it&utm_medium=blogger
Charming Kitten, also called APT35, CharmingCypress, Mint Sandstorm, TA453, and Yellow Garuda, has a history of orchestrating a wide range of social engineering campaigns that cast a
https://thehackernews.com/2024/02/iranian-hackers-target-middle-east.html?utm_source=dlvr.it&utm_medium=blogger
IT Security News Daily Summary 2024-02-18
Hackers Claim Data Breach at Staffing Giant Robert Half, Sell Sensitive Data Corporate Accountability: Tech Titans Address the Menace of Misleading AI in Elections Changing How Healthcare Works: Big News in Communication ESET fixed high-severity local privilege escalation bug in…
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2024-02-18/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2024-02-18/?utm_source=dlvr.it&utm_medium=blogger
Hackers Claim Data Breach at Staffing Giant Robert Half, Sell Sensitive Data
By Waqas Deja vu at Robert Half? Notorious hackers claim responsibility as the staffing giant makes headlines for yet another alleged data breach in two years. This is a post from HackRead.com Read the original post: Hackers Claim Data Breach…
Read more →
https://www.itsecuritynews.info/hackers-claim-data-breach-at-staffing-giant-robert-half-sell-sensitive-data/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/hackers-claim-data-breach-at-staffing-giant-robert-half-sell-sensitive-data/?utm_source=dlvr.it&utm_medium=blogger
Beware, iPhone Users: iOS GoldDigger Trojan can Steal Face ID and Banking Details
Numerous people pick iPhones over Android phones because they believe iPhones are more secure. However, this may no longer be the case due to the emergence of a new banking trojan designed explicitly to target iPhone users. According to…
Read more →
https://www.itsecuritynews.info/beware-iphone-users-ios-golddigger-trojan-can-steal-face-id-and-banking-details/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/beware-iphone-users-ios-golddigger-trojan-can-steal-face-id-and-banking-details/?utm_source=dlvr.it&utm_medium=blogger
Week in review: AnyDesk phishing campaign targets employees, Microsoft fixes exploited zero-days
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Integrating cybersecurity into vehicle design and manufacturing In this Help Net Security interview, Yaron Edan, CISO at REE Automotive, discusses the cybersecurity landscape of the…
Read more →
https://www.itsecuritynews.info/week-in-review-anydesk-phishing-campaign-targets-employees-microsoft-fixes-exploited-zero-days/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/week-in-review-anydesk-phishing-campaign-targets-employees-microsoft-fixes-exploited-zero-days/?utm_source=dlvr.it&utm_medium=blogger
Saturday, February 17, 2024
Lean In for Yourself
Small family farming is a labor intensive way to go broke. When I was young I spent some weeks each summer with my grandparents. As farmers and cattle ranchers, my grandparents scratched out an existence. My grandpa was up before…
Read more →
https://www.itsecuritynews.info/lean-in-for-yourself/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/lean-in-for-yourself/?utm_source=dlvr.it&utm_medium=blogger
IT Security News Daily Summary 2024-02-17
USENIX Security ’23 – Xiaoguang Li, Ninghui Li, Wenhai Sun, Neil Zhenqiang Gong, Hui Li – Fine-grained Poisoning Attack to Local Differential Privacy Protocols for Mean and Variance Estimation Enhancing PCI DSS Compliance: The Urgent Need for Risk-Based Prioritization How…
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2024-02-17/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2024-02-17/?utm_source=dlvr.it&utm_medium=blogger
Microsoft and OpenAI Reveal Hackers Weaponizing ChatGPT
In a digital landscape fraught with evolving threats, the marriage of artificial intelligence (AI) and cybercrime has become a potent concern. Recent revelations from Microsoft and OpenAI underscore the alarming trend of malicious actors harnessing advanced language models (LLMs)…
Read more →
https://www.itsecuritynews.info/microsoft-and-openai-reveal-hackers-weaponizing-chatgpt/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/microsoft-and-openai-reveal-hackers-weaponizing-chatgpt/?utm_source=dlvr.it&utm_medium=blogger
Revolutionizing Cybersecurity: Integrating UEBA for Enhanced Data Protection
There is a transformative shift taking place in cyber security, once a fortress built on rigid protocols and reactive measures. There is an increasing need for a nuanced approach to safeguarding digital assets as digital landscapes become increasingly intricate…
Read more →
https://www.itsecuritynews.info/revolutionizing-cybersecurity-integrating-ueba-for-enhanced-data-protection/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/revolutionizing-cybersecurity-integrating-ueba-for-enhanced-data-protection/?utm_source=dlvr.it&utm_medium=blogger
Google Open Sources Magika: AI-Powered File Identification Tool
Google has announced that it's open-sourcing Magika, an artificial intelligence (AI)-powered tool to identify file types, to help defenders accurately detect binary and textual file types.
"Magika outperforms conventional file identification methods providing an overall 30% accuracy boost and up to 95% higher precision on traditionally hard to identify, but potentially problematic content
https://thehackernews.com/2024/02/google-open-sources-magika-ai-powered.html?utm_source=dlvr.it&utm_medium=blogger
"Magika outperforms conventional file identification methods providing an overall 30% accuracy boost and up to 95% higher precision on traditionally hard to identify, but potentially problematic content
https://thehackernews.com/2024/02/google-open-sources-magika-ai-powered.html?utm_source=dlvr.it&utm_medium=blogger
Friday, February 16, 2024
Cybersecurity Risk Assessment: Identifying and Managing Risks
Learn the crucial steps and strategies for effective cybersecurity risk assessment, ensuring your organization is prepared to identify and manage potential risks. The post Cybersecurity Risk Assessment: Identifying and Managing Risks appeared first on Security Zap. This article has been…
Read more →
https://www.itsecuritynews.info/cybersecurity-risk-assessment-identifying-and-managing-risks/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/cybersecurity-risk-assessment-identifying-and-managing-risks/?utm_source=dlvr.it&utm_medium=blogger
Leak of Russian ‘Threat’ Part of a Bid to Kill US Surveillance Reform, Sources Say
A surprise disclosure of a national security threat by the House Intelligence chair was part of an effort to block legislation that aimed to limit cops and spies from buying Americans’ private data. This article has been indexed from Security…
Read more →
https://www.itsecuritynews.info/leak-of-russian-threat-part-of-a-bid-to-kill-us-surveillance-reform-sources-say-2/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/leak-of-russian-threat-part-of-a-bid-to-kill-us-surveillance-reform-sources-say-2/?utm_source=dlvr.it&utm_medium=blogger
Volt Typhoon Disrupts US Organizations, CISA Issues Alerts
Volt Typhoon has expanded its operations beyond illegal access and data theft in the US. Discover how they’re attacking and what you can do for protection. The post Volt Typhoon Disrupts US Organizations, CISA Issues Alerts appeared first on eSecurity…
Read more →
https://www.itsecuritynews.info/volt-typhoon-disrupts-us-organizations-cisa-issues-alerts/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/volt-typhoon-disrupts-us-organizations-cisa-issues-alerts/?utm_source=dlvr.it&utm_medium=blogger
RustDoor macOS Backdoor Targets Cryptocurrency Firms with Fake Job Offers
Multiple companies operating in the cryptocurrency sector are the target of an ongoing malware campaign that involves a newly discovered Apple macOS backdoor codenamed RustDoor.
RustDoor was first documented by Bitdefender last week, describing it as a Rust-based malware capable of harvesting and uploading files, as well as gathering information about the infected machines. It's
https://thehackernews.com/2024/02/rustdoor-macos-backdoor-targets.html?utm_source=dlvr.it&utm_medium=blogger
RustDoor was first documented by Bitdefender last week, describing it as a Rust-based malware capable of harvesting and uploading files, as well as gathering information about the infected machines. It's
https://thehackernews.com/2024/02/rustdoor-macos-backdoor-targets.html?utm_source=dlvr.it&utm_medium=blogger
New Wi-Fi Authentication Bypass Flaw Puts Enterprise and Home Networks at Risk
Security researchers Mathy Vanhoef and Héloïse Gollier, have recently uncovered several critical vulnerabilities in the Wi-Fi authentication protocols used in modern WPA2/3 networks collaborating with VPN testing company Top10VPN. The identified flaws pose a significant security risk as they could potentially enable unauthorized access to sensitive data transmitted over wireless networks and compromise the security […]
The post New Wi-Fi Authentication Bypass Flaw Puts Enterprise and Home Networks at Risk appeared first on Cyber Security News.
https://cybersecuritynews.com/new-wi-fi-authentication-bypass-flaw/?utm_source=dlvr.it&utm_medium=blogger
The post New Wi-Fi Authentication Bypass Flaw Puts Enterprise and Home Networks at Risk appeared first on Cyber Security News.
https://cybersecuritynews.com/new-wi-fi-authentication-bypass-flaw/?utm_source=dlvr.it&utm_medium=blogger
Thursday, February 15, 2024
Google, Microsoft, OpenAI make AI pledges ahead of Munich Security Conference
Google today launched an ‘AI Cyber Defense Initiative and made several AI-related commitments, following a charge by Microsoft and OpenAI. This article has been indexed from Security News | VentureBeat Read the original article: Google, Microsoft, OpenAI make AI pledges…
Read more →
https://www.itsecuritynews.info/google-microsoft-openai-make-ai-pledges-ahead-of-munich-security-conference/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/google-microsoft-openai-make-ai-pledges-ahead-of-munich-security-conference/?utm_source=dlvr.it&utm_medium=blogger
Siemens Location Intelligence
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services…
Read more →
https://www.itsecuritynews.info/siemens-location-intelligence/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/siemens-location-intelligence/?utm_source=dlvr.it&utm_medium=blogger
Russian Turla Hackers Target Polish NGOs with New TinyTurla-NG Backdoor
The Russia-linked threat actor known as Turla has been observed using a new backdoor called TinyTurla-NG as part of a three-month-long campaign targeting Polish non-governmental organizations in December 2023.
"TinyTurla-NG, just like TinyTurla, is a small 'last chance' backdoor that is left behind to be used when all other unauthorized access/backdoor mechanisms have failed or been
https://thehackernews.com/2024/02/russian-turla-hackers-target-polish.html?utm_source=dlvr.it&utm_medium=blogger
"TinyTurla-NG, just like TinyTurla, is a small 'last chance' backdoor that is left behind to be used when all other unauthorized access/backdoor mechanisms have failed or been
https://thehackernews.com/2024/02/russian-turla-hackers-target-polish.html?utm_source=dlvr.it&utm_medium=blogger
Ivanti Pulse Secure Found Using 11-Year-Old Linux Version and Outdated Libraries
A reverse engineering of the firmware running on Ivanti Pulse Secure appliances has revealed numerous weaknesses, once again underscoring the challenge of securing software supply chains.
Eclypsiusm, which acquired firmware version 9.1.18.2-24467.1 as part of the process, said the base operating system used by the Utah-based software company for the device is CentOS 6.4.
"Pulse Secure runs an
https://thehackernews.com/2024/02/ivanti-pulse-secure-found-using-11-year.html?utm_source=dlvr.it&utm_medium=blogger
Eclypsiusm, which acquired firmware version 9.1.18.2-24467.1 as part of the process, said the base operating system used by the Utah-based software company for the device is CentOS 6.4.
"Pulse Secure runs an
https://thehackernews.com/2024/02/ivanti-pulse-secure-found-using-11-year.html?utm_source=dlvr.it&utm_medium=blogger
Wireshark 4.2.3 Released: What’s New!
Wireshark, the most popular network protocol analyzer worldwide, has released version 4.2.3, which includes new features and upgrades. Wireshark, a well-known open-source network protocol analyzer, enables users to view and record network data in real time. Important features include its rich protocol support, user-friendly design, active community and updates, customizable output, powerful filtering tools, and […]
The post Wireshark 4.2.3 Released: What’s New! appeared first on Cyber Security News.
https://cybersecuritynews.com/wireshark-4-2-3-released/?utm_source=dlvr.it&utm_medium=blogger
The post Wireshark 4.2.3 Released: What’s New! appeared first on Cyber Security News.
https://cybersecuritynews.com/wireshark-4-2-3-released/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, February 14, 2024
Hackers Exploit YouTube Videos to Deliver Password Stealing Malware
Threat actors hunt for ways to exploit vulnerabilities by employing tactics from technical zero-days to broad phishing. Social engineering blends with commodity malware on high-traffic sites, like social media, that allows quick, cheap, and widespread attacks. Despite seeming trivial, these infections, such as AI-generated videos on YouTube offering malware disguised as cracked software, pose significant […]
The post Hackers Exploit YouTube Videos to Deliver Password Stealing Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/youtube-videos-deliver-malware/?utm_source=dlvr.it&utm_medium=blogger
The post Hackers Exploit YouTube Videos to Deliver Password Stealing Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/youtube-videos-deliver-malware/?utm_source=dlvr.it&utm_medium=blogger
Who’s the Boss? Teaming Up With AI in Security
“AI’s Impact in Cybersecurity” is a blog series based on interviews with a variety of experts at Palo Alto Networks and Unit 42, with roles in AI research, product management, consulting, engineering … The post Who’s the Boss? Teaming Up…
Read more →
https://www.itsecuritynews.info/whos-the-boss-teaming-up-with-ai-in-security-2/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/whos-the-boss-teaming-up-with-ai-in-security-2/?utm_source=dlvr.it&utm_medium=blogger
The Managed Services Surge: Insights from Cisco Live EMEA
Cisco Live EMEA 2024 is now in the books—what an incredible four days! The atmosphere was alive with the anticipation of the innovation and opportunity that lies ahead of us. Our partners are introducing new services to the market, customers…
Read more →
https://www.itsecuritynews.info/the-managed-services-surge-insights-from-cisco-live-emea/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/the-managed-services-surge-insights-from-cisco-live-emea/?utm_source=dlvr.it&utm_medium=blogger
South Korea Says Presumed North Korean Hackers Breached Personal Emails of Presidential Staffer
South Korean President Yoon Suk Yeol’s office said presumed North Korean hackers breached the personal emails of one of his staff members. The post South Korea Says Presumed North Korean Hackers Breached Personal Emails of Presidential Staffer appeared first on…
Read more →
https://www.itsecuritynews.info/south-korea-says-presumed-north-korean-hackers-breached-personal-emails-of-presidential-staffer/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/south-korea-says-presumed-north-korean-hackers-breached-personal-emails-of-presidential-staffer/?utm_source=dlvr.it&utm_medium=blogger
Multipurpose Glupteba Malware Controls OS Boot Process to Hide Itself
Glupteba, a decade-old malware in financial cybercrime, unveiled a new campaign in November 2023. Despite its long tenure, the undiscovered features include a UEFI bootkit that allows stealthy persistence, challenging detection, and removal. Security analysts at Palo Alto Networks recently discovered Glupteba, which is a multipurpose malware that controls the OS boot process to hide […]
The post Multipurpose Glupteba Malware Controls OS Boot Process to Hide Itself appeared first on Cyber Security News.
https://cybersecuritynews.com/multipurpose-glupteba-malware/?utm_source=dlvr.it&utm_medium=blogger
The post Multipurpose Glupteba Malware Controls OS Boot Process to Hide Itself appeared first on Cyber Security News.
https://cybersecuritynews.com/multipurpose-glupteba-malware/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, February 13, 2024
What Is Packet Filtering? Definition, Advantages & How It Works
Packet filtering is a function used today in most firewalls. Discover how packet filtering works, plus advantages, disadvantages, types, and use cases. The post What Is Packet Filtering? Definition, Advantages & How It Works appeared first on eSecurity Planet. This…
Read more →
https://www.itsecuritynews.info/what-is-packet-filtering-definition-advantages-how-it-works/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/what-is-packet-filtering-definition-advantages-how-it-works/?utm_source=dlvr.it&utm_medium=blogger
10 Best Secure Network As a Service for MSP Providers – 2024
Secure Network as a Service (SNaaS) for Managed Service Providers (MSPs) delivers networking and security services to clients via the cloud, integrating networking advantages with complete protection. This strategy allows MSPs to provide clients with scalable, adaptable, and secure networking solutions without investing in physical infrastructure or security expertise. Unlike traditional models that require significant […]
The post 10 Best Secure Network As a Service for MSP Providers – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/secure-network-as-a-service-for-msp/?utm_source=dlvr.it&utm_medium=blogger
The post 10 Best Secure Network As a Service for MSP Providers – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/secure-network-as-a-service-for-msp/?utm_source=dlvr.it&utm_medium=blogger
ANY.RUN Threat Intelligence Lookup Tool – A Repository of Millions of Malware IOCs
Malware sandbox leader ANY.RUN introduced the Threat Intelligence Lookup platform that helps security researchers find the relevant threat data from the sandbox tasks of ANY.RUN. The platform aids in identifying and studying various types of malware by improving the incident response and overall cybersecurity measures. In a controlled environment, ANY.RUN allows security analysts to execute […]
The post ANY.RUN Threat Intelligence Lookup Tool – A Repository of Millions of Malware IOCs appeared first on Cyber Security News.
https://cybersecuritynews.com/any-run-threat-intelligence-lookup/?utm_source=dlvr.it&utm_medium=blogger
The post ANY.RUN Threat Intelligence Lookup Tool – A Repository of Millions of Malware IOCs appeared first on Cyber Security News.
https://cybersecuritynews.com/any-run-threat-intelligence-lookup/?utm_source=dlvr.it&utm_medium=blogger
10 Best Network Security Providers for Education Sectors – 2024
Network security providers for education safeguard schools, colleges, and educational institutions against cyberattacks. These providers protect student, research, and administrative data, comply with legal and regulatory requirements, and provide a secure learning environment. In education, digital learning tools, online courses, and remote education emphasize the necessity for strong network security. With the growing number of […]
The post 10 Best Network Security Providers for Education Sectors – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/network-security-providers-for-education/?utm_source=dlvr.it&utm_medium=blogger
The post 10 Best Network Security Providers for Education Sectors – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/network-security-providers-for-education/?utm_source=dlvr.it&utm_medium=blogger
Alert: CISA Warns of Active 'Roundcube' Email Attacks - Patch Now
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a medium-severity security flaw impacting Roundcube email software to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The issue, tracked as CVE-2023-43770 (CVSS score: 6.1), relates to a cross-site scripting (XSS) flaw that stems from the handling of
https://thehackernews.com/2024/02/alert-cisa-warns-of-active-roundcube.html?utm_source=dlvr.it&utm_medium=blogger
The issue, tracked as CVE-2023-43770 (CVSS score: 6.1), relates to a cross-site scripting (XSS) flaw that stems from the handling of
https://thehackernews.com/2024/02/alert-cisa-warns-of-active-roundcube.html?utm_source=dlvr.it&utm_medium=blogger
Monday, February 12, 2024
CISA adds Roundcube Webmail Persistent XSS bug to its Known Exploited Vulnerabilities catalog
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Roundcube Webmail Persistent Cross-Site Scripting (XSS) Vulnerability to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a Roundcube Webmail Persistent Cross-Site Scripting (XSS) vulnerability, tracked as CVE-2023-43770,…
Read more →
https://www.itsecuritynews.info/cisa-adds-roundcube-webmail-persistent-xss-bug-to-its-known-exploited-vulnerabilities-catalog/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/cisa-adds-roundcube-webmail-persistent-xss-bug-to-its-known-exploited-vulnerabilities-catalog/?utm_source=dlvr.it&utm_medium=blogger
Do Any HTTP Clients Not Support SNI?
In this blog post, we’ll share the results of an internal research project we conducted on our CDN customers focused on websites that are getting non-Server Name Indication (SNI) traffic. The goal of our research was to answer the following…
Read more →
https://www.itsecuritynews.info/do-any-http-clients-not-support-sni/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/do-any-http-clients-not-support-sni/?utm_source=dlvr.it&utm_medium=blogger
Beware of Stealthy Raspberry Robin That Delivered as a Windows Component
Raspberry Robin is a malicious worm that spreads through USB drives, and it’s been actively used by the threat actors to download and install hidden malware on Windows systems. Besides this, the threat actors exploit it for various reasons like initial access, data theft, espionage, and deploying other malware. Cybersecurity researchers at Check Point recently […]
The post Beware of Stealthy Raspberry Robin That Delivered as a Windows Component appeared first on Cyber Security News.
https://cybersecuritynews.com/beware-of-stealthy-raspberry-robin/?utm_source=dlvr.it&utm_medium=blogger
The post Beware of Stealthy Raspberry Robin That Delivered as a Windows Component appeared first on Cyber Security News.
https://cybersecuritynews.com/beware-of-stealthy-raspberry-robin/?utm_source=dlvr.it&utm_medium=blogger
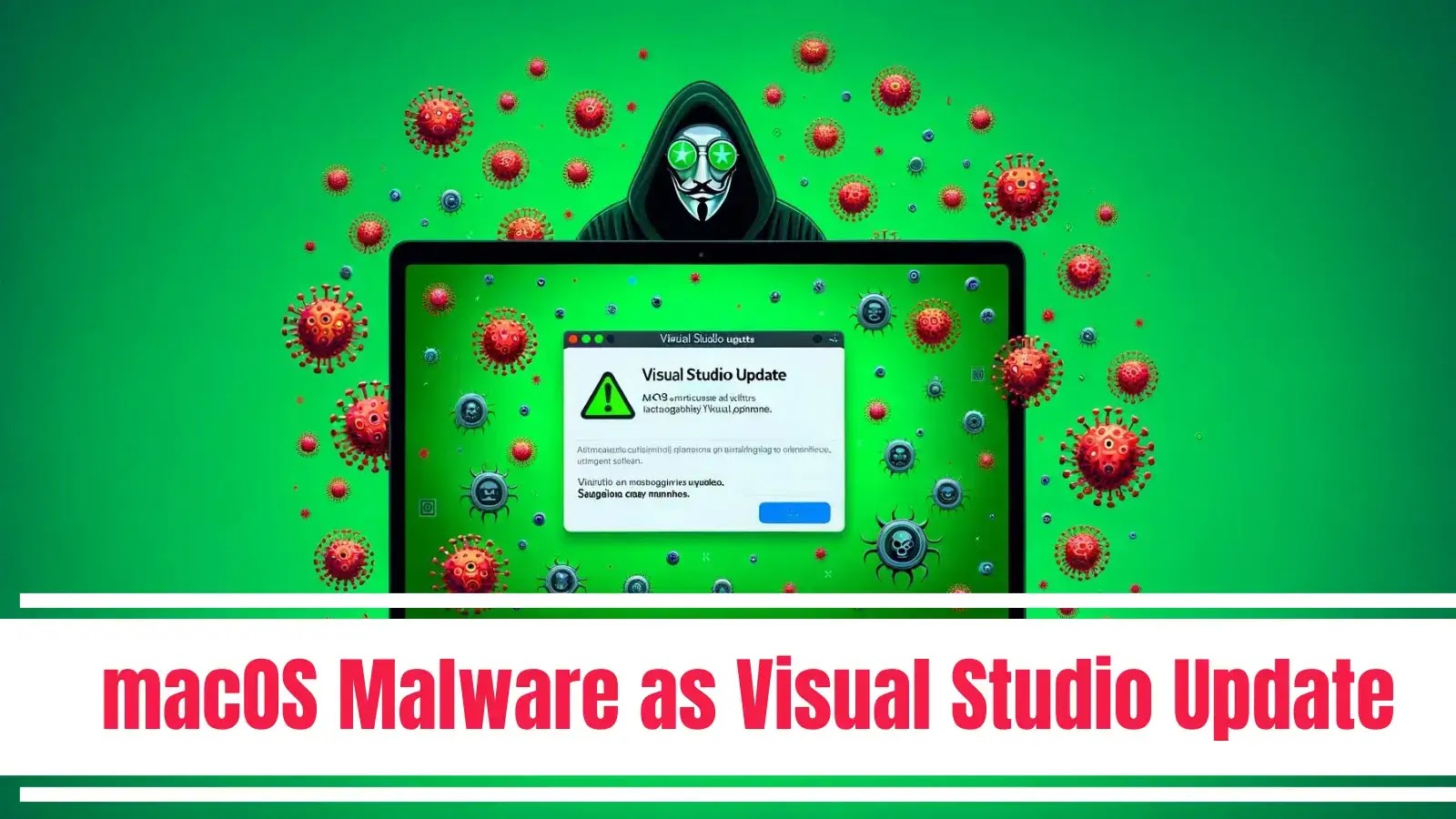
New Malware Mimic as Visual Studio Update to Attack macOS users
A new backdoor written in Rust has been discovered to target macOS users with several interesting features. Moreover, there have been 3 variants of backdoor found masquerading under the name of Visual Studio Update. The backdoor is distributed as FAT binaries with Mach-O files for x84_64 Intel and ARM architectures. In addition to this, the […]
The post New Malware Mimic as Visual Studio Update to Attack macOS users appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-visual-studio-macos/?utm_source=dlvr.it&utm_medium=blogger
The post New Malware Mimic as Visual Studio Update to Attack macOS users appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-visual-studio-macos/?utm_source=dlvr.it&utm_medium=blogger
Benefits of a vCISO for Small Businesses
Cybersecurity is of critical concern for every company, no matter their headcount or yearly revenue; in fact, many hackers target small and midsize companies, knowing that they likely don’t have the budget for sophisticated threat monitoring. With the tight profit margins that come with more compact operations, it can be difficult to manage the day-to-day […]
The post Benefits of a vCISO for Small Businesses appeared first on Cyber Security News.
https://cybersecuritynews.com/benefits-of-a-vciso-for-small-businesses/?utm_source=dlvr.it&utm_medium=blogger
The post Benefits of a vCISO for Small Businesses appeared first on Cyber Security News.
https://cybersecuritynews.com/benefits-of-a-vciso-for-small-businesses/?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 11, 2024
Cyber Mayday and My Journey to Oz
When we persevere through difficulties our results are often better than initially expected. Here’s a story of how pandemic disappointments and travel problems led to new professional opportunities. The post Cyber Mayday and My Journey to Oz appeared first…
Read more →
https://www.itsecuritynews.info/cyber-mayday-and-my-journey-to-oz/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/cyber-mayday-and-my-journey-to-oz/?utm_source=dlvr.it&utm_medium=blogger
Should I get CISA Certified?
< p class=””>CISA is possibly the one ‘pure’ Information systems audit qualification that is recognised anywhere. It is balanced between technical IT knowledge and business understanding. And it has lovely exam questions – and I should know, as I wrote…
Read more →
https://www.itsecuritynews.info/should-i-get-cisa-certified/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/should-i-get-cisa-certified/?utm_source=dlvr.it&utm_medium=blogger
South Staffs Water Faces a Group Action Following Clop Ransomware Attack
Following the theft and disclosure of their data by the Clop/Cl0p ransomware group, nearly one thousand victims recently filed a class action lawsuit against South Staffordshire Plc. South Staffordshire Plc, which owns South Staffordshire Water and Cambridge Water, served…
Read more →
https://www.itsecuritynews.info/south-staffs-water-faces-a-group-action-following-clop-ransomware-attack/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/south-staffs-water-faces-a-group-action-following-clop-ransomware-attack/?utm_source=dlvr.it&utm_medium=blogger
China Caught Deploying Remote Access Trojan Tailored for FortiGate Devices
The Military Intelligence and Security Service (MIVD) of the Netherlands has issued a warning regarding the discovery of a new strain of malware believed to be orchestrated by the Chinese government. Named “Coathanger,” this persistent and highly elusive malware…
Read more →
https://www.itsecuritynews.info/china-caught-deploying-remote-access-trojan-tailored-for-fortigate-devices/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/china-caught-deploying-remote-access-trojan-tailored-for-fortigate-devices/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)














.webp)