There has been a handover of patient data stolen by the notorious LockBit gang from a cloud computing company to a New York hospital alliance that is partnered with that company. There was a lawsuit filed by the North…
Read more →
https://www.itsecuritynews.info/innovative-legal-move-restores-hospitals-stolen-information/?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 21, 2024
New Bluetooth Vulnerability Let Hackers Takeover of iOS, Android, Linux, & MacOS Devices
Bluetooth vulnerabilities in Android, Linux, macOS, iOS, and Windows are critical as hackers could exploit them to gain unauthorized access to the vulnerable devices. Such flaws in Bluetooth protocols enable the threat actors to steal sensitive data, eavesdrop on communications, and execute malicious actions. A cybersecurity specialist, Marc Newlin, recently discovered a new Bluetooth vulnerability […]
The post New Bluetooth Vulnerability Let Hackers Takeover of iOS, Android, Linux, & MacOS Devices appeared first on Cyber Security News.
https://cybersecuritynews.com/bluetooth-flaw-hackers-takeover/?utm_source=dlvr.it&utm_medium=blogger
The post New Bluetooth Vulnerability Let Hackers Takeover of iOS, Android, Linux, & MacOS Devices appeared first on Cyber Security News.
https://cybersecuritynews.com/bluetooth-flaw-hackers-takeover/?utm_source=dlvr.it&utm_medium=blogger
Saturday, January 20, 2024
IT Security News Daily Summary 2024-01-20
Microsoft Executives’ Emails Breached by Russia Hackers DHS and FBI: Chinese Drones Pose Major Threat to U.S. Security Fujitsu Bugs That Sent Innocent People to Prison Were Known ‘From the Start’ USENIX Security ’23 – Unique Identification of 50,000+ Virtual…
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2024-01-20/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2024-01-20/?utm_source=dlvr.it&utm_medium=blogger
Fujitsu Bugs That Sent Innocent People to Prison Were Known ‘From the Start’
Software flaws were allegedly hidden from lawyers of wrongly convicted UK postal workers. This article has been indexed from Security Latest Read the original article: Fujitsu Bugs That Sent Innocent People to Prison Were Known ‘From the Start’
Read more →
https://www.itsecuritynews.info/fujitsu-bugs-that-sent-innocent-people-to-prison-were-known-from-the-start/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/fujitsu-bugs-that-sent-innocent-people-to-prison-were-known-from-the-start/?utm_source=dlvr.it&utm_medium=blogger
Why many CISOs consider quitting – Week in security with Tony Anscombe
The job of a CISO is becoming increasingly stressful as cybersecurity chiefs face overwhelming workloads and growing concerns over personal liability for security failings This article has been indexed from WeLiveSecurity Read the original article: Why many CISOs consider quitting…
Read more →
https://www.itsecuritynews.info/why-many-cisos-consider-quitting-week-in-security-with-tony-anscombe/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/why-many-cisos-consider-quitting-week-in-security-with-tony-anscombe/?utm_source=dlvr.it&utm_medium=blogger
1,718,000+ Apache Struts 2 Installation Open to RCE Attacks
Threat actors target Apache Struts 2 due to vulnerabilities in its code that can be exploited for unauthorized access to web applications. Exploiting these vulnerabilities allows attackers to execute arbitrary code that could lead to full system compromise. As Apache Struts 2 is widely used in web development, successful attacks can impact many applications, making […]
The post 1,718,000+ Apache Struts 2 Installation Open to RCE Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/apache-struts-2-rce-attacks/?utm_source=dlvr.it&utm_medium=blogger
The post 1,718,000+ Apache Struts 2 Installation Open to RCE Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/apache-struts-2-rce-attacks/?utm_source=dlvr.it&utm_medium=blogger
Invoice Phishing Alert: TA866 Deploys WasabiSeed & Screenshotter Malware
The threat actor tracked as TA866 has resurfaced after a nine-month hiatus with a new large-volume phishing campaign to deliver known malware families such as WasabiSeed and Screenshotter.
The campaign, observed earlier this month and blocked by Proofpoint on January 11, 2024, involved sending thousands of invoice-themed emails targeting North America bearing decoy PDF files.
"The PDFs
https://thehackernews.com/2024/01/invoice-phishing-alert-ta866-deploys.html?utm_source=dlvr.it&utm_medium=blogger
The campaign, observed earlier this month and blocked by Proofpoint on January 11, 2024, involved sending thousands of invoice-themed emails targeting North America bearing decoy PDF files.
"The PDFs
https://thehackernews.com/2024/01/invoice-phishing-alert-ta866-deploys.html?utm_source=dlvr.it&utm_medium=blogger
Friday, January 19, 2024
Canadian Man Stuck in Triangle of E-Commerce Fraud
A Canadian man who says he’s been falsely charged with orchestrating a complex e-commerce scam is seeking to clear his name. His case appears to involve “triangulation fraud,” which occurs when a consumer purchases something online — from a seller…
Read more →
https://www.itsecuritynews.info/canadian-man-stuck-in-triangle-of-e-commerce-fraud/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/canadian-man-stuck-in-triangle-of-e-commerce-fraud/?utm_source=dlvr.it&utm_medium=blogger
U.S. Cybersecurity Agency Warns of Actively Exploited Ivanti EPMM Vulnerability
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a now-patched critical flaw impacting Ivanti Endpoint Manager Mobile (EPMM) and MobileIron Core to its Known Exploited Vulnerabilities (KEV) catalog, stating it's being actively exploited in the wild.
The vulnerability in question is CVE-2023-35082 (CVSS score: 9.8), an authentication bypass
https://thehackernews.com/2024/01/us-cybersecurity-agency-warns-of.html?utm_source=dlvr.it&utm_medium=blogger
The vulnerability in question is CVE-2023-35082 (CVSS score: 9.8), an authentication bypass
https://thehackernews.com/2024/01/us-cybersecurity-agency-warns-of.html?utm_source=dlvr.it&utm_medium=blogger
The Security Dimensions of Adopting LLMs
The incredible capabilities of LLM (Large Language Models) enable organizations to engage in various useful activities such as generating branding content, localizing content to transform customer experiences, precise demand forecasting, writing code, enhanced supplier management, spam detection, sentiment analysis, and much more. As a result, LLMs are being leveraged across a multitude of industries and […]
The post The Security Dimensions of Adopting LLMs appeared first on Cyber Security News.
https://cybersecuritynews.com/security-dimensions-llm/?utm_source=dlvr.it&utm_medium=blogger
The post The Security Dimensions of Adopting LLMs appeared first on Cyber Security News.
https://cybersecuritynews.com/security-dimensions-llm/?utm_source=dlvr.it&utm_medium=blogger
Hackers Abuse TeamViewer to Launch Ransomware Attacks
Hackers exploit TeamViewer because it gives remote access to systems and allows threat actors to control them. This can be used for several illicit purposes like illegal data access, system manipulation, and virus distribution. Besides this, the widespread use of TeamViewer makes it an attractive target for threat actors who are actively seeking to exploit […]
The post Hackers Abuse TeamViewer to Launch Ransomware Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-abuse-teamviewer/?utm_source=dlvr.it&utm_medium=blogger
The post Hackers Abuse TeamViewer to Launch Ransomware Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-abuse-teamviewer/?utm_source=dlvr.it&utm_medium=blogger
APT Hackers Exploiting Ivanti Connect Secure VPN New Zero-Day Flaw in the Wild
Hackers exploit Zero-Day flaws in VPNs as these vulnerabilities are unknown to the software vendor, making them difficult to patch immediately. This can be particularly lucrative for the threat actors seeking to exploit the growing reliance on VPNs (Virtual private networks) for secure online communication. Recently, cybersecurity researchers at Google’s Mandiant discovered that APT hackers […]
The post APT Hackers Exploiting Ivanti Connect Secure VPN New Zero-Day Flaw in the Wild appeared first on Cyber Security News.
https://cybersecuritynews.com/ivanti-connect-vpn-zero-day/?utm_source=dlvr.it&utm_medium=blogger
The post APT Hackers Exploiting Ivanti Connect Secure VPN New Zero-Day Flaw in the Wild appeared first on Cyber Security News.
https://cybersecuritynews.com/ivanti-connect-vpn-zero-day/?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 18, 2024
New iShutdown Scripts Enable Detection of Spyware On iPhones
Malware hunting on iOS devices has been extremely difficult due to the nature of the iOS ecosystem. There were only two methods for conducting forensic investigations on iOS devices: either to examine an encrypted full iOS backup or analyze the network traffic of the suspected device. However, both methods require a lot of time and […]
The post New iShutdown Scripts Enable Detection of Spyware On iPhones appeared first on Cyber Security News.
https://cybersecuritynews.com/new-ishutdown-scripts/?utm_source=dlvr.it&utm_medium=blogger
The post New iShutdown Scripts Enable Detection of Spyware On iPhones appeared first on Cyber Security News.
https://cybersecuritynews.com/new-ishutdown-scripts/?utm_source=dlvr.it&utm_medium=blogger
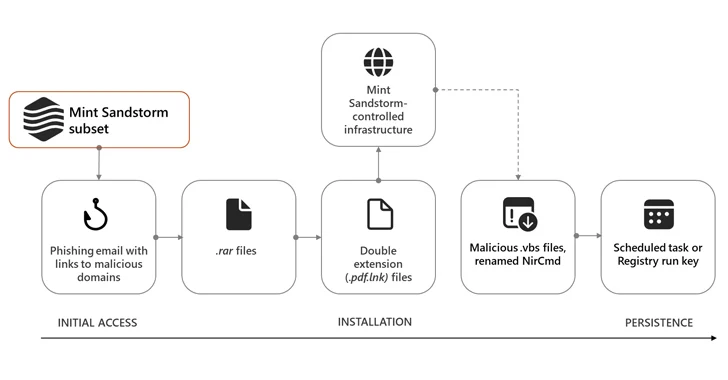
Iranian Hackers Masquerade as Journalists to Spy on Israel-Hamas War Experts
High-profile individuals working on Middle Eastern affairs at universities and research organizations in Belgium, France, Gaza, Israel, the U.K., and the U.S. have been targeted by an Iranian cyber espionage group called Mint Sandstorm since November 2023.
The threat actor "used bespoke phishing lures in an attempt to socially engineer targets into downloading malicious files," the
https://thehackernews.com/2024/01/iranian-hackers-masquerades-as.html?utm_source=dlvr.it&utm_medium=blogger
The threat actor "used bespoke phishing lures in an attempt to socially engineer targets into downloading malicious files," the
https://thehackernews.com/2024/01/iranian-hackers-masquerades-as.html?utm_source=dlvr.it&utm_medium=blogger
How AI-Powered Security Capabilities Implement Real-Time Cybersecurity
Palo Alto Networks and Accenture are leaders at the forefront of security technology and operations, using AI to help clients stay ahead of cyberthreats. The post How AI-Powered Security Capabilities Implement Real-Time Cybersecurity appeared first on Palo Alto Networks Blog.…
Read more →
https://www.itsecuritynews.info/how-ai-powered-security-capabilities-implement-real-time-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/how-ai-powered-security-capabilities-implement-real-time-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
LeftoverLocals Attack Let Attackers Steal AI Data From Apple, Qualcomm & AMD GPUs
An attacker may be able to steal a significant amount of data from a GPU’s memory due to a flaw known as LeftoverLocals that affects several popular GPU brands and models, including AMD, Apple, and Qualcomm. Machine learning (ML) models and large language models (LLMs) operating on affected GPU platforms are especially affected by LeftoverLocals, which […]
The post LeftoverLocals Attack Let Attackers Steal AI Data From Apple, Qualcomm & AMD GPUs appeared first on Cyber Security News.
https://cybersecuritynews.com/leftoverlocals-attack/?utm_source=dlvr.it&utm_medium=blogger
The post LeftoverLocals Attack Let Attackers Steal AI Data From Apple, Qualcomm & AMD GPUs appeared first on Cyber Security News.
https://cybersecuritynews.com/leftoverlocals-attack/?utm_source=dlvr.it&utm_medium=blogger
MyFlaw – Opera Bug Let Hackers Run ANY File on Mac or Windows
Hackers exploit Remote Code Execution (RCE) vulnerabilities as they allow them to execute arbitrary code on a target system remotely. This unauthorized access enables the threat actors to take control of the system and perform a multitude of illicit activities. Recently, cybersecurity researchers at Guardio Labs discovered an Opera bug that lets hackers run any […]
The post MyFlaw – Opera Bug Let Hackers Run ANY File on Mac or Windows appeared first on Cyber Security News.
https://cybersecuritynews.com/myflaw-opera-bug/?utm_source=dlvr.it&utm_medium=blogger
The post MyFlaw – Opera Bug Let Hackers Run ANY File on Mac or Windows appeared first on Cyber Security News.
https://cybersecuritynews.com/myflaw-opera-bug/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, January 17, 2024
Alert: Over 178,000 SonicWall Firewalls Potentially Vulnerable to Exploits - Act Now
Over 178,000 SonicWall firewalls exposed over the internet are exploitable to at least one of the two security flaws that could be potentially exploited to cause a denial-of-service (DoS) condition and remote code execution (RCE).
“The two issues are fundamentally the same but exploitable at different HTTP URI paths due to reuse of a vulnerable code pattern,” Jon Williams, a senior security
https://thehackernews.com/2024/01/alert-over-178000-sonicwall-firewalls.html?utm_source=dlvr.it&utm_medium=blogger
“The two issues are fundamentally the same but exploitable at different HTTP URI paths due to reuse of a vulnerable code pattern,” Jon Williams, a senior security
https://thehackernews.com/2024/01/alert-over-178000-sonicwall-firewalls.html?utm_source=dlvr.it&utm_medium=blogger
Remcos RAT Spreading Through Adult Games in New Attack Wave
The remote access trojan (RAT) known as Remcos RAT has been found being propagated via webhards by disguising it as adult-themed games in South Korea.
WebHard, short for web hard drive, is a popular online file storage system used to upload, download, and share files in the country.
While webhards have been used in the past to deliver njRAT, UDP RAT, and DDoS botnet malware, the
https://thehackernews.com/2024/01/remcos-rat-spreading-through-adult.html?utm_source=dlvr.it&utm_medium=blogger
WebHard, short for web hard drive, is a popular online file storage system used to upload, download, and share files in the country.
While webhards have been used in the past to deliver njRAT, UDP RAT, and DDoS botnet malware, the
https://thehackernews.com/2024/01/remcos-rat-spreading-through-adult.html?utm_source=dlvr.it&utm_medium=blogger
Salt Security Delivers another Technology Breakthrough with Industry’s only API Posture Governance Engine
Today, API security company Salt Security has announced multiple advancements in discovery, posture management and AI-based threat protection to the industry leading Salt Security API Protection Platform. Salt leapfrogs traditional posture management by providing the industry’s first API posture governance…
Read more →
https://www.itsecuritynews.info/salt-security-delivers-another-technology-breakthrough-with-industrys-only-api-posture-governance-engine/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/salt-security-delivers-another-technology-breakthrough-with-industrys-only-api-posture-governance-engine/?utm_source=dlvr.it&utm_medium=blogger
Google Chrome Browser Zero-Day Vulnerability Exploited in Wild
Google Chrome released the first security update in 2024 with a fix for the zero-day bug actively exploited in Wild. An update to Google Chrome 120.0.6099.234 for Mac, 120.0.6099.224 for Linux, and 120.0.6099.224/225 for Windows will be released in the next days or weeks. Hackers exploit zero-day flaws as these vulnerabilities are unknown to software […]
The post Google Chrome Browser Zero-Day Vulnerability Exploited in Wild appeared first on Cyber Security News.
https://cybersecuritynews.com/google-chrome-browser-zero-day-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
The post Google Chrome Browser Zero-Day Vulnerability Exploited in Wild appeared first on Cyber Security News.
https://cybersecuritynews.com/google-chrome-browser-zero-day-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
Hackers Exploiting Windows Defender SmartScreen Flaw to Hijack Computers
Hackers actively target and exploit Windows Defender SmartScreen to deceive users and deliver malicious content by creating convincing, misleading websites or applications. By evading SmartScreen, the threat actors increase the chances of their malicious content being executed on users’ systems to compromise security. This exploitation often involves the use of social engineering tactics to deceive […]
The post Hackers Exploiting Windows Defender SmartScreen Flaw to Hijack Computers appeared first on Cyber Security News.
https://cybersecuritynews.com/windows-defender-smartscreen-flaw/?utm_source=dlvr.it&utm_medium=blogger
The post Hackers Exploiting Windows Defender SmartScreen Flaw to Hijack Computers appeared first on Cyber Security News.
https://cybersecuritynews.com/windows-defender-smartscreen-flaw/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 16, 2024
Hackers Weaponize Windows Flaw to Deploy Crypto-Siphoning Phemedrone Stealer
Threat actors have been observed leveraging a now-patched security flaw in Microsoft Windows to deploy an open-source information stealer called Phemedrone Stealer.
“Phemedrone targets web browsers and data from cryptocurrency wallets and messaging apps such as Telegram, Steam, and Discord,” Trend Micro researchers Peter Girnus, Aliakbar Zahravi, and Simon Zuckerbraun said.
“It also
https://thehackernews.com/2024/01/hackers-weaponize-windows-flaw-to.html?utm_source=dlvr.it&utm_medium=blogger
“Phemedrone targets web browsers and data from cryptocurrency wallets and messaging apps such as Telegram, Steam, and Discord,” Trend Micro researchers Peter Girnus, Aliakbar Zahravi, and Simon Zuckerbraun said.
“It also
https://thehackernews.com/2024/01/hackers-weaponize-windows-flaw-to.html?utm_source=dlvr.it&utm_medium=blogger
Opera MyFlaw Bug Could Let Hackers Run ANY File on Your Mac or Windows
Cybersecurity researchers have disclosed a now-patched security flaw in the Opera web browser for Microsoft Windows and Apple macOS that could be exploited to execute any file on the underlying operating system.
The remote code execution vulnerability has been codenamed MyFlaw by the Guardio Labs research team owing to the fact that it takes advantage of a feature called My Flow that
https://thehackernews.com/2024/01/opera-myflaw-bug-could-let-hackers-run.html?utm_source=dlvr.it&utm_medium=blogger
The remote code execution vulnerability has been codenamed MyFlaw by the Guardio Labs research team owing to the fact that it takes advantage of a feature called My Flow that
https://thehackernews.com/2024/01/opera-myflaw-bug-could-let-hackers-run.html?utm_source=dlvr.it&utm_medium=blogger
3 Ransomware Group Newcomers to Watch in 2024
The ransomware industry surged in 2023 as it saw an alarming 55.5% increase in victims worldwide, reaching a staggering 4,368 cases.
Figure 1: Year over year victims per quarter
The rollercoaster ride from explosive growth in 2021 to a momentary dip in 2022 was just a teaser—2023 roared back with the same fervor as 2021, propelling existing groups and ushering in a wave of formidable
https://thehackernews.com/2024/01/3-ransomware-group-newcomers-to-watch.html?utm_source=dlvr.it&utm_medium=blogger
Figure 1: Year over year victims per quarter
The rollercoaster ride from explosive growth in 2021 to a momentary dip in 2022 was just a teaser—2023 roared back with the same fervor as 2021, propelling existing groups and ushering in a wave of formidable
https://thehackernews.com/2024/01/3-ransomware-group-newcomers-to-watch.html?utm_source=dlvr.it&utm_medium=blogger
10 Best Firewall as a Service (FWaaS) Providers – 2024
Firewall as a Service (FWaaS) is an emerging security model in cloud computing and network security. It represents a shift from traditional, on-premise firewall solutions to cloud-based firewall services. Firewalls as Service Providers (FWaaS) are pillars of enterprise network security. It keeps an eye on both incoming and outgoing network traffic, allowing or blocking data […]
The post 10 Best Firewall as a Service (FWaaS) Providers – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/best-firewall-as-a-service-providers/?utm_source=dlvr.it&utm_medium=blogger
The post 10 Best Firewall as a Service (FWaaS) Providers – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/best-firewall-as-a-service-providers/?utm_source=dlvr.it&utm_medium=blogger
Framework Hacked – Hackers Compromised The Network Using Phishing Email
Recently, Framework’s primary external accounting partner, Keating Consulting, discovered at 8:13 am PST on January 11th, 2024, that the network of Frame Work had been hacked by an attacker using a phishing email. Hackers use phishing emails to trick individuals into providing sensitive information. By posing as trustworthy entities, hackers exploit human psychology to trick […]
The post Framework Hacked – Hackers Compromised The Network Using Phishing Email appeared first on Cyber Security News.
https://cybersecuritynews.com/frame-work-hacked/?utm_source=dlvr.it&utm_medium=blogger
The post Framework Hacked – Hackers Compromised The Network Using Phishing Email appeared first on Cyber Security News.
https://cybersecuritynews.com/frame-work-hacked/?utm_source=dlvr.it&utm_medium=blogger
Monday, January 15, 2024
High-Severity Flaws Uncovered in Bosch Thermostats and Smart Nutrunners
Multiple security vulnerabilities have been disclosed in Bosch BCC100 thermostats and Rexroth NXA015S-36V-B smart nutrunners that, if successfully exploited, could allow attackers to execute arbitrary code on affected systems.
Romanian cybersecurity firm Bitdefender, which discovered the flaw in Bosch BCC100 thermostats last August, said the issue could be weaponized by an attacker to
https://thehackernews.com/2024/01/high-severity-flaws-uncovered-in-bosch.html?utm_source=dlvr.it&utm_medium=blogger
Romanian cybersecurity firm Bitdefender, which discovered the flaw in Bosch BCC100 thermostats last August, said the issue could be weaponized by an attacker to
https://thehackernews.com/2024/01/high-severity-flaws-uncovered-in-bosch.html?utm_source=dlvr.it&utm_medium=blogger
Balada Injector Infects Over 7,100 WordPress Sites Using Plugin Vulnerability
Thousands of WordPress sites using a vulnerable version of the Popup Builder plugin have been compromised with a malware called Balada Injector.
First documented by Doctor Web in January 2023, the campaign takes place in a series of periodic attack waves, weaponizing security flaws WordPress plugins to inject backdoor designed to redirect visitors of infected sites to bogus tech
https://thehackernews.com/2024/01/balada-injector-infects-over-7100.html?utm_source=dlvr.it&utm_medium=blogger
First documented by Doctor Web in January 2023, the campaign takes place in a series of periodic attack waves, weaponizing security flaws WordPress plugins to inject backdoor designed to redirect visitors of infected sites to bogus tech
https://thehackernews.com/2024/01/balada-injector-infects-over-7100.html?utm_source=dlvr.it&utm_medium=blogger
DDoS Attacks on the Environmental Services Industry Surge by 61,839% in 2023
The environmental services industry witnessed an “unprecedented surge” in HTTP-based distributed denial-of-service (DDoS) attacks, accounting for half of all its HTTP traffic.
This marks a 61,839% increase in DDoS attack traffic year-over-year, web infrastructure and security company Cloudflare said in its DDoS threat report for 2023 Q4 published last week.
“This surge in cyber attacks coincided
https://thehackernews.com/2024/01/ddos-attacks-on-environmental-services.html?utm_source=dlvr.it&utm_medium=blogger
This marks a 61,839% increase in DDoS attack traffic year-over-year, web infrastructure and security company Cloudflare said in its DDoS threat report for 2023 Q4 published last week.
“This surge in cyber attacks coincided
https://thehackernews.com/2024/01/ddos-attacks-on-environmental-services.html?utm_source=dlvr.it&utm_medium=blogger
Living-off-Trusted-Sites (LOTS) – APT Hackers Abusing GitHub To Deliver Malware Payload
Hackers use GitHub to access and manipulate source code repositories. GitHub hosts open-source projects, and unauthorized access allows hackers to inject malicious code, steal sensitive information, and exploit vulnerabilities in software development pipelines. Cybersecurity researchers at Recorded Future recently discovered that APT hackers actively exploit the GitHub platform to deliver malware payloads. Over 94 million […]
The post Living-off-Trusted-Sites (LOTS) – APT Hackers Abusing GitHub To Deliver Malware Payload appeared first on Cyber Security News.
https://cybersecuritynews.com/living-off-trusted-sites-lots-apt-hackers/?utm_source=dlvr.it&utm_medium=blogger
The post Living-off-Trusted-Sites (LOTS) – APT Hackers Abusing GitHub To Deliver Malware Payload appeared first on Cyber Security News.
https://cybersecuritynews.com/living-off-trusted-sites-lots-apt-hackers/?utm_source=dlvr.it&utm_medium=blogger
10 Best Zero Trust Security Vendors – 2024
Zero Trust Security is a strategic approach to cybersecurity that centers on the principle of “never trust, always verify.” This model questions the standard security paradigm that previously assumed complete trust in everything within an organization’s network. Zero Trust is a security framework that mandates that all users, whether inside or outside the organization’s network, […]
The post 10 Best Zero Trust Security Vendors – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/zero-trust-security-vendors/?utm_source=dlvr.it&utm_medium=blogger
The post 10 Best Zero Trust Security Vendors – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/zero-trust-security-vendors/?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 14, 2024
Classic Baggie: A Delaware BEC Case calls him the leader of an International Criminal Organization
The U.S. Attorney’s office in Delaware charged Olugbenga Lawal with being a major money launderer for a Nigerian-based international criminal organization that specialized in Business Email Compromise (#BEC) and Romance Scam. Lawal was charged with receiving more than $3 million…
Read more →
https://www.itsecuritynews.info/classic-baggie-a-delaware-bec-case-calls-him-the-leader-of-an-international-criminal-organization/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/classic-baggie-a-delaware-bec-case-calls-him-the-leader-of-an-international-criminal-organization/?utm_source=dlvr.it&utm_medium=blogger
Who’s Behind GoatRAT?
In this brief analysis I’ll take a look at who’s behind GoatRAT in terms of social media activity C&C servers and actual personally identifiable information. Personally identifiable information: hxxp://bit[.]ly/nubankmodulo hxxp://goatrat[.]com/apks/apk20[.]apk Sample MD5s: 6583a9b6b83738e0bf2a261fc04483e18772da3241e467fdef37a8e27b1869a7 9a8e85cf1bbd32c71f0efa42ffedf1a0 hxxp://api[.]goatrat[.]com:3008 Social Media: hxxp://t[.]me/sickoDevz hxxp://t[.]me/goatmalware Web site: …
Read more →
https://www.itsecuritynews.info/whos-behind-goatrat/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/whos-behind-goatrat/?utm_source=dlvr.it&utm_medium=blogger
Top 11 Best Enterprise Remote Access Software – 2024
Enterprise remote access software is an incredible innovation that eliminates the need for physical presence by allowing for the remote management and operation of computers and other electronic devices. Remote work, technical support, and effective system management are all made more accessible by this program in today’s increasingly interconnected world. Users can access remote resources, […]
The post Top 11 Best Enterprise Remote Access Software – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/enterprise-remote-access-software/?utm_source=dlvr.it&utm_medium=blogger
The post Top 11 Best Enterprise Remote Access Software – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/enterprise-remote-access-software/?utm_source=dlvr.it&utm_medium=blogger
Babuk Ransomware Decryptor Updated to Recover Files Infected by Latest Variant
Hackers use ransomware to encrypt victims’ files and render them inaccessible until a ransom is paid. This forces the victims to pay a ransom to regain access to compromised systems and data. This tactic leads to financial gains for the threat actors. While ransomware attacks can be conducted at scale and threat actors can target […]
The post Babuk Ransomware Decryptor Updated to Recover Files Infected by Latest Variant appeared first on Cyber Security News.
https://cybersecuritynews.com/babuk-ransomware-decryptor-updated/?utm_source=dlvr.it&utm_medium=blogger
The post Babuk Ransomware Decryptor Updated to Recover Files Infected by Latest Variant appeared first on Cyber Security News.
https://cybersecuritynews.com/babuk-ransomware-decryptor-updated/?utm_source=dlvr.it&utm_medium=blogger
New Findings Challenge Attribution in Denmark's Energy Sector Cyberattacks
The cyber attacks targeting the energy sector in Denmark last year may not have had the involvement of the Russia-linked Sandworm hacking group, new findings from Forescout show.
The intrusions, which targeted around 22 Danish energy organizations in May 2023, occurred in two distinct waves, one which exploited a security flaw in Zyxel firewall (CVE-2023-28771) and a
https://thehackernews.com/2024/01/new-findings-challenge-attribution-in.html?utm_source=dlvr.it&utm_medium=blogger
The intrusions, which targeted around 22 Danish energy organizations in May 2023, occurred in two distinct waves, one which exploited a security flaw in Zyxel firewall (CVE-2023-28771) and a
https://thehackernews.com/2024/01/new-findings-challenge-attribution-in.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, January 13, 2024
Nation-State Actors Weaponize Ivanti VPN Zero-Days, Deploying 5 Malware Families
As many as five different malware families were deployed by suspected nation-state actors as part of post-exploitation activities leveraging two zero-day vulnerabilities in Ivanti Connect Secure (ICS) VPN appliances since early December 2023.
"These families allow the threat actors to circumvent authentication and provide backdoor access to these devices," Mandiant said in an
https://thehackernews.com/2024/01/nation-state-actors-weaponize-ivanti.html?utm_source=dlvr.it&utm_medium=blogger
"These families allow the threat actors to circumvent authentication and provide backdoor access to these devices," Mandiant said in an
https://thehackernews.com/2024/01/nation-state-actors-weaponize-ivanti.html?utm_source=dlvr.it&utm_medium=blogger
Medusa Ransomware on the Rise: From Data Leaks to Multi-Extortion
The threat actors associated with the Medusa ransomware have ramped up their activities following the debut of a dedicated data leak site on the dark web in February 2023 to publish sensitive data of victims who are unwilling to agree to their demands.
“As part of their multi-extortion strategy, this group will provide victims with multiple options when their data is posted on their
https://thehackernews.com/2024/01/medusa-ransomware-on-rise-from-data.html?utm_source=dlvr.it&utm_medium=blogger
“As part of their multi-extortion strategy, this group will provide victims with multiple options when their data is posted on their
https://thehackernews.com/2024/01/medusa-ransomware-on-rise-from-data.html?utm_source=dlvr.it&utm_medium=blogger
Applying the Tyson Principle to Cybersecurity: Why Attack Simulation is Key to Avoiding a KO
Picture a cybersecurity landscape where defenses are impenetrable, and threats are nothing more than mere disturbances deflected by a strong shield. Sadly, this image of fortitude remains a pipe dream despite its comforting nature. In the security world, preparedness is not just a luxury but a necessity. In this context, Mike Tyson's famous adage, "Everyone has a plan until they get punched in
https://thehackernews.com/2024/01/applying-tyson-principle-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2024/01/applying-tyson-principle-to.html?utm_source=dlvr.it&utm_medium=blogger
Urgent: GitLab Releases Patch for Critical Vulnerabilities - Update ASAP
GitLab has released security updates to address two critical vulnerabilities, including one that could be exploited to take over accounts without requiring any user interaction.
Tracked as CVE-2023-7028, the flaw has been awarded the maximum severity of 10.0 on the CVSS scoring system and could facilitate account takeover by sending password reset emails to an unverified email address.
The
https://thehackernews.com/2024/01/urgent-gitlab-releases-patch-for.html?utm_source=dlvr.it&utm_medium=blogger
Tracked as CVE-2023-7028, the flaw has been awarded the maximum severity of 10.0 on the CVSS scoring system and could facilitate account takeover by sending password reset emails to an unverified email address.
The
https://thehackernews.com/2024/01/urgent-gitlab-releases-patch-for.html?utm_source=dlvr.it&utm_medium=blogger
What is the Difference Between ISO 27001 & 27002 Compliance? – A Detailed Guide
ISO 27001 and ISO 27002 are international standards that provide a framework for managing information security within an organization. In an increasingly interconnected world, where organizations rely heavily on technology and digital systems, safeguarding sensitive information and maintaining robust security measures is paramount. Perimeter81 Providers ISO 27001 and ISO 27002 compliance offer a systematic approach […]
The post What is the Difference Between ISO 27001 & 27002 Compliance? – A Detailed Guide appeared first on Cyber Security News.
https://cybersecuritynews.com/iso-27001-27002-compliance/?utm_source=dlvr.it&utm_medium=blogger
The post What is the Difference Between ISO 27001 & 27002 Compliance? – A Detailed Guide appeared first on Cyber Security News.
https://cybersecuritynews.com/iso-27001-27002-compliance/?utm_source=dlvr.it&utm_medium=blogger
Friday, January 12, 2024
Threat Actors Increasingly Abusing GitHub for Malicious Purposes
The ubiquity of GitHub in information technology (IT) environments has made it a lucrative choice for threat actors to host and deliver malicious payloads and act as dead drop resolvers, command-and-control, and data exfiltration points.
“Using GitHub services for malicious infrastructure allows adversaries to blend in with legitimate network traffic, often bypassing traditional security
https://thehackernews.com/2024/01/threat-actors-increasingly-abusing.html?utm_source=dlvr.it&utm_medium=blogger
“Using GitHub services for malicious infrastructure allows adversaries to blend in with legitimate network traffic, often bypassing traditional security
https://thehackernews.com/2024/01/threat-actors-increasingly-abusing.html?utm_source=dlvr.it&utm_medium=blogger
New PoC Exploit for Apache OfBiz Vulnerability Poses Risk to ERP Systems
Cybersecurity researchers have developed a proof-of-concept (PoC) code that exploits a recently disclosed critical flaw in the Apache OfBiz open-source Enterprise Resource Planning (ERP) system to execute a memory-resident payload.
The vulnerability in question is CVE-2023-51467 (CVSS score: 9.8), a bypass for another severe shortcoming in the same software (
https://thehackernews.com/2024/01/new-poc-exploit-for-apache-ofbiz.html?utm_source=dlvr.it&utm_medium=blogger
The vulnerability in question is CVE-2023-51467 (CVSS score: 9.8), a bypass for another severe shortcoming in the same software (
https://thehackernews.com/2024/01/new-poc-exploit-for-apache-ofbiz.html?utm_source=dlvr.it&utm_medium=blogger
New Python-based FBot Hacking Toolkit Aims at Cloud and SaaS Platforms
A new Python-based hacking tool called FBot has been uncovered targeting web servers, cloud services, content management systems (CMS), and SaaS platforms such as Amazon Web Services (AWS), Microsoft 365, PayPal, Sendgrid, and Twilio.
“Key features include credential harvesting for spamming attacks, AWS account hijacking tools, and functions to enable attacks against PayPal and various
https://thehackernews.com/2024/01/new-python-based-fbot-hacking-toolkit.html?utm_source=dlvr.it&utm_medium=blogger
“Key features include credential harvesting for spamming attacks, AWS account hijacking tools, and functions to enable attacks against PayPal and various
https://thehackernews.com/2024/01/new-python-based-fbot-hacking-toolkit.html?utm_source=dlvr.it&utm_medium=blogger
There is a Ransomware Armageddon Coming for Us All
Generative AI will enable anyone to launch sophisticated phishing attacks that only Next-generation MFA devices can stop
The least surprising headline from 2023 is that ransomware again set new records for a number of incidents and the damage inflicted. We saw new headlines every week, which included a who’s-who of big-name organizations. If MGM, Johnson Controls, Chlorox, Hanes Brands, Caesars
https://thehackernews.com/2024/01/there-is-ransomware-armageddon-coming.html?utm_source=dlvr.it&utm_medium=blogger
The least surprising headline from 2023 is that ransomware again set new records for a number of incidents and the damage inflicted. We saw new headlines every week, which included a who’s-who of big-name organizations. If MGM, Johnson Controls, Chlorox, Hanes Brands, Caesars
https://thehackernews.com/2024/01/there-is-ransomware-armageddon-coming.html?utm_source=dlvr.it&utm_medium=blogger
Atomic Stealer Gets an Upgrade - Targeting Mac Users with Encrypted Payload
Cybersecurity researchers have identified an updated version of a macOS information stealer called Atomic (or AMOS), indicating that the threat actors behind the malware are actively enhancing its capabilities.
"It looks like Atomic Stealer was updated around mid to late December 2023, where its developers introduced payload encryption in an effort to bypass detection rules,"
https://thehackernews.com/2024/01/atomic-stealer-gets-upgrade-targeting.html?utm_source=dlvr.it&utm_medium=blogger
"It looks like Atomic Stealer was updated around mid to late December 2023, where its developers introduced payload encryption in an effort to bypass detection rules,"
https://thehackernews.com/2024/01/atomic-stealer-gets-upgrade-targeting.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 11, 2024
Free Decryptor Released for Black Basta and Babuk's Tortilla Ransomware Victims
A decryptor for the Tortilla variant of the Babuk ransomware has been released by Cisco Talos, allowing victims targeted by the malware to regain access to their files.
The cybersecurity firm said the threat intelligence it shared with Dutch law enforcement authorities made it possible to arrest the threat actor behind the operations.
The encryption key has also been shared with Avast,
https://thehackernews.com/2024/01/free-decryptor-released-for-black-basta.html?utm_source=dlvr.it&utm_medium=blogger
The cybersecurity firm said the threat intelligence it shared with Dutch law enforcement authorities made it possible to arrest the threat actor behind the operations.
The encryption key has also been shared with Avast,
https://thehackernews.com/2024/01/free-decryptor-released-for-black-basta.html?utm_source=dlvr.it&utm_medium=blogger
FTC Bans Outlogic (X-Mode) From Selling Sensitive Location Data
The U.S. Federal Trade Commission (FTC) on Tuesday prohibited data broker Outlogic, which was previously known as X-Mode Social, from sharing or selling any sensitive location data with third-parties.
The ban is part of a settlement over allegations that the company "sold precise location data that could be used to track people's visits to sensitive locations such as medical and
https://thehackernews.com/2024/01/ftc-bans-outlogic-x-mode-from-selling.html?utm_source=dlvr.it&utm_medium=blogger
The ban is part of a settlement over allegations that the company "sold precise location data that could be used to track people's visits to sensitive locations such as medical and
https://thehackernews.com/2024/01/ftc-bans-outlogic-x-mode-from-selling.html?utm_source=dlvr.it&utm_medium=blogger
Microsoft's January 2024 Windows Update Patches 48 New Vulnerabilities
Microsoft has addressed a total of 48 security flaws spanning its software as part of its Patch Tuesday updates for January 2024.
Of the 48 bugs, two are rated Critical and 46 are rated Important in severity. There is no evidence that any of the issues are publicly known or under active attack at the time of release, making it the second consecutive Patch Tuesday with no zero-days.
The
https://thehackernews.com/2024/01/microsofts-january-2024-windows-update.html?utm_source=dlvr.it&utm_medium=blogger
Of the 48 bugs, two are rated Critical and 46 are rated Important in severity. There is no evidence that any of the issues are publicly known or under active attack at the time of release, making it the second consecutive Patch Tuesday with no zero-days.
The
https://thehackernews.com/2024/01/microsofts-january-2024-windows-update.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)






















%20-%20APT%20Hackers%20Abusing%20GitHub%20To%20Deliver%20Malware%20Payload.webp)