MaaS (Malware-as-a-Service) thrives as a top choice for new cyber threats, offering easy access to powerful tools. Threat actors primarily focus on information theft under Maas, specializing in stealing and leaking sensitive data from hacked devices. This malicious behavior poses a serious risk to both individuals and businesses, with the potential to cause significant financial […]
The post LummaC2 Employs Trigonometry to Track Mouse Movements appeared first on Cyber Security News.
https://cybersecuritynews.com/lummac2-employs-trigonometry/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, November 21, 2023
Hackers Infect Linux Machines with Rootkits via Apache ActiveMQ Vulnerability
Apache ActiveMQ is a Java-based open-source protocol that allows distributed applications to exchange messages. It uses the JMS API to provide a dependable messaging platform for sharing data across systems written in diverse programming languages. It includes the following features:- Trend Micro researchers recently revealed that the Apache ActiveMQ vulnerability (CVE-2023-46604) was actively exploited for […]
The post Hackers Infect Linux Machines with Rootkits via Apache ActiveMQ Vulnerability appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-infect-linux-machines-via-apache-activemq-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
The post Hackers Infect Linux Machines with Rootkits via Apache ActiveMQ Vulnerability appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-infect-linux-machines-via-apache-activemq-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
Monday, November 20, 2023
Organizations’ serious commitment to software risk management pays off
There has been a significant decrease in vulnerabilities found in target applications – from 97% in 2020 to 83% in 2022 – an encouraging sign that code reviews, automated testing and continuous integration are helping to reduce common programming errors,…
Read more →
https://www.itsecuritynews.info/organizations-serious-commitment-to-software-risk-management-pays-off/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/organizations-serious-commitment-to-software-risk-management-pays-off/?utm_source=dlvr.it&utm_medium=blogger
Lasso Security Emerges From Stealth With $6M Seed Funding for Gen AI and Advanced LLM Cybersecurity
This post doesn’t have text content, please click on the link below to view the original article. This article has been indexed from Dark Reading Read the original article: Lasso Security Emerges From Stealth With $6M Seed Funding for Gen…
Read more →
https://www.itsecuritynews.info/lasso-security-emerges-from-stealth-with-6m-seed-funding-for-gen-ai-and-advanced-llm-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/lasso-security-emerges-from-stealth-with-6m-seed-funding-for-gen-ai-and-advanced-llm-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
Canadian government impacted by data breaches of two of its contractors
The Canadian government discloses a data breach after threat actors hacked two of its contractors. The Canadian government declared that two of its contractors,Brookfield Global Relocation Services (BGRS) and SIRVA Worldwide Relocation & Moving Services, have been hacked, resulting in…
Read more →
https://www.itsecuritynews.info/canadian-government-impacted-by-data-breaches-of-two-of-its-contractors/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/canadian-government-impacted-by-data-breaches-of-two-of-its-contractors/?utm_source=dlvr.it&utm_medium=blogger
Most OpenAI Staff Threaten To Quit After Microsoft Hires Sam Altman
This post doesn’t have text content, please click on the link below to view the original article. This article has been indexed from News ≈ Packet Storm Read the original article: Most OpenAI Staff Threaten To Quit After Microsoft Hires…
Read more →
https://www.itsecuritynews.info/most-openai-staff-threaten-to-quit-after-microsoft-hires-sam-altman/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/most-openai-staff-threaten-to-quit-after-microsoft-hires-sam-altman/?utm_source=dlvr.it&utm_medium=blogger
Indian Hack-for-Hire Group Targeted U.S., China, and More for Over 10 Years
An Indian hack-for-hire group targeted the U.S., China, Myanmar, Pakistan, Kuwait, and other countries as part of a wide-ranging espionage, surveillance, and disruptive operation for over a decade.
The Appin Software Security (aka Appin Security Group), according to an in-depth analysis from SentinelOne, began as an educational startup offering offensive security training programs, while
https://thehackernews.com/2023/11/indian-hack-for-hire-group-targeted-us.html?utm_source=dlvr.it&utm_medium=blogger
The Appin Software Security (aka Appin Security Group), according to an in-depth analysis from SentinelOne, began as an educational startup offering offensive security training programs, while
https://thehackernews.com/2023/11/indian-hack-for-hire-group-targeted-us.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, November 19, 2023
CrowdStrike Extends AI Approach to Cybersecurity to SMBs
CrowdStrike Falcon Go enables small-to-medium businesses (SMBs) to leverage machine learning algorithms to secure their IT environments. The post CrowdStrike Extends AI Approach to Cybersecurity to SMBs appeared first on Security Boulevard. This article has been indexed from Security Boulevard…
Read more →
https://www.itsecuritynews.info/crowdstrike-extends-ai-approach-to-cybersecurity-to-smbs/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/crowdstrike-extends-ai-approach-to-cybersecurity-to-smbs/?utm_source=dlvr.it&utm_medium=blogger
IT Security News Daily Summary 2023-11-19
SSE vs. Traditional Security Models – The Variances AI/ML Tools Uncovered with 12+ Vulnerabilities Open to Exploitation Toyota Acknowledges Security Breach After Medusa Ransomware Threatens to Leak Data Android’s Privacy Boost: Google Unveils ‘Private Spaces’ Feature to Safeguard Photos and…
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2023-11-19/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/it-security-news-daily-summary-2023-11-19/?utm_source=dlvr.it&utm_medium=blogger
SSE vs. Traditional Security Models – The Variances
In today’s hyper-connected digital world, cybersecurity stands as a paramount concern, with organizations seeking robust solutions to protect… The post SSE vs. Traditional Security Models – The Variances appeared first on Hackers Online Club (HOC). This article has been indexed…
Read more →
https://www.itsecuritynews.info/sse-vs-traditional-security-models-the-variances/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/sse-vs-traditional-security-models-the-variances/?utm_source=dlvr.it&utm_medium=blogger
Security Affairs newsletter Round 446 by Pierluigi Paganini – INTERNATIONAL EDITION
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Israeli…
Read more →
https://www.itsecuritynews.info/security-affairs-newsletter-round-446-by-pierluigi-paganini-international-edition/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/security-affairs-newsletter-round-446-by-pierluigi-paganini-international-edition/?utm_source=dlvr.it&utm_medium=blogger
Dark Effects of Bot Attacks that Drive 73% of Internet Traffic
In a chilling revelation, the cybercrime economy is projected to soar to $10.5 trillion by 2025, driven by financially motivated bad actors orchestrating dark enterprises. Uncover the intricate web of these malicious activities and the alarming surge in cyber threats.…
Read more →
https://www.itsecuritynews.info/dark-effects-of-bot-attacks-that-drive-73-of-internet-traffic/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/dark-effects-of-bot-attacks-that-drive-73-of-internet-traffic/?utm_source=dlvr.it&utm_medium=blogger
Saturday, November 18, 2023
AI Demystified: Unraveling Artificial Intelligence (AI)
As the world continues to progress, so does its technology. Artificial Intelligence (AI) has become a major milestone in this advancement, bringing with it countless… The post AI Demystified: Unraveling Artificial Intelligence (AI) appeared first on Security Zap. This article…
Read more →
https://www.itsecuritynews.info/ai-demystified-unraveling-artificial-intelligence-ai/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/ai-demystified-unraveling-artificial-intelligence-ai/?utm_source=dlvr.it&utm_medium=blogger
E-commerce Security in the Cloud: Safeguarding Data in the Holiday Season
By Dan Benjamin, CEO and Co-Founder, Dig Security The holiday sales season is the most important time of year for e-commerce retailers, representing a time of heightened consumer activity and potential revenue growth. Retailers are forced to maintain security while balancing the consumer…
Read more →
https://www.itsecuritynews.info/e-commerce-security-in-the-cloud-safeguarding-data-in-the-holiday-season/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/e-commerce-security-in-the-cloud-safeguarding-data-in-the-holiday-season/?utm_source=dlvr.it&utm_medium=blogger
Unveiling LockBit: Cybercrime Gang Targeting Global Titans in Hacking Spree
Ransomware, a form of malicious software, has a history spanning over three decades. However, it only gained regular attention in popular media over the last ten years. This type of malware locks access to computer systems or encrypts files…
Read more →
https://www.itsecuritynews.info/unveiling-lockbit-cybercrime-gang-targeting-global-titans-in-hacking-spree/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/unveiling-lockbit-cybercrime-gang-targeting-global-titans-in-hacking-spree/?utm_source=dlvr.it&utm_medium=blogger
ChatGPT-Maker OpenAI Fires CEO Sam Altman, the Face of the AI Boom, for Lack of Candor With Company
Open AI pushed out its co-founder and CEO Sam Altman after a review found he was “not consistently candid in his communications” with the board of directors. The post ChatGPT-Maker OpenAI Fires CEO Sam Altman, the Face of the AI…
Read more →
https://www.itsecuritynews.info/chatgpt-maker-openai-fires-ceo-sam-altman-the-face-of-the-ai-boom-for-lack-of-candor-with-company/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/chatgpt-maker-openai-fires-ceo-sam-altman-the-face-of-the-ai-boom-for-lack-of-candor-with-company/?utm_source=dlvr.it&utm_medium=blogger
Russian Cyber Espionage Group Deploys LitterDrifter USB Worm in Targeted Attacks
Russian cyber espionage actors affiliated with the Federal Security Service (FSB) have been observed using a USB propagating worm called LitterDrifter in attacks targeting Ukrainian entities.
Check Point, which detailed Gamaredon's (aka Aqua Blizzard, Iron Tilden, Primitive Bear, Shuckworm, and Winterflounder) latest tactics, branded the group as engaging in large-scale campaigns that are
https://thehackernews.com/2023/11/russian-cyber-espionage-group-deploys.html?utm_source=dlvr.it&utm_medium=blogger
Check Point, which detailed Gamaredon's (aka Aqua Blizzard, Iron Tilden, Primitive Bear, Shuckworm, and Winterflounder) latest tactics, branded the group as engaging in large-scale campaigns that are
https://thehackernews.com/2023/11/russian-cyber-espionage-group-deploys.html?utm_source=dlvr.it&utm_medium=blogger
Friday, November 17, 2023
VicOne and Block Harbor Deliver Integrated Workflow-Based Cybersecurity System
This post doesn’t have text content, please click on the link below to view the original article. This article has been indexed from Dark Reading Read the original article: VicOne and Block Harbor Deliver Integrated Workflow-Based Cybersecurity System
Read more →
https://www.itsecuritynews.info/vicone-and-block-harbor-deliver-integrated-workflow-based-cybersecurity-system/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/vicone-and-block-harbor-deliver-integrated-workflow-based-cybersecurity-system/?utm_source=dlvr.it&utm_medium=blogger
Piloting New Ground: Expanding Scalable Cybersecurity Services to Protect the Broader Critical Infrastructure Community
This post doesn’t have text content, please click on the link below to view the original article. This article has been indexed from CISA Blog Read the original article: Piloting New Ground: Expanding Scalable Cybersecurity Services to Protect the Broader…
Read more →
https://www.itsecuritynews.info/piloting-new-ground-expanding-scalable-cybersecurity-services-to-protect-the-broader-critical-infrastructure-community/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/piloting-new-ground-expanding-scalable-cybersecurity-services-to-protect-the-broader-critical-infrastructure-community/?utm_source=dlvr.it&utm_medium=blogger
ALPHV/BlackCat Take Extortion Public
Learn more about ALPHV filing a complaint with the Security and Exchange Commission (SEC) against their victim, which appears to be an attempt to influence MeridianLink to pay the ransom sooner than later. This article has been indexed from Trend…
Read more →
https://www.itsecuritynews.info/alphv-blackcat-take-extortion-public/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/alphv-blackcat-take-extortion-public/?utm_source=dlvr.it&utm_medium=blogger
Malware Discovered in Kids’ Tablet steals sensitive data
In the ever-expanding market of Android devices, the allure of budget-friendly options can sometimes conceal unforeseen risks. Purchasing Android devices from online platforms like Amazon offers varying price points but also exposes consumers to potential security hazards. For her birthday, Alexis Hancock’s daughter received a tablet designed specifically for children. Given her profession as a […]
The post Malware Discovered in Kids’ Tablet steals sensitive data appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-kids-tablet/?utm_source=dlvr.it&utm_medium=blogger
The post Malware Discovered in Kids’ Tablet steals sensitive data appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-kids-tablet/?utm_source=dlvr.it&utm_medium=blogger
CISA Adds Three Security Flaws with Active Exploitation to KEV Catalog
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added three security flaws to its Known Exploited Vulnerabilities (KEV) catalog based on evidence of active exploitation in the wild.
The vulnerabilities are as follows -
CVE-2023-36584 (CVSS score: 5.4) - Microsoft Windows Mark-of-the-Web (MotW) Security Feature Bypass Vulnerability
CVE-2023-1671 (CVSS score: 9.8) -
https://thehackernews.com/2023/11/cisa-adds-three-security-flaws-with.html?utm_source=dlvr.it&utm_medium=blogger
The vulnerabilities are as follows -
CVE-2023-36584 (CVSS score: 5.4) - Microsoft Windows Mark-of-the-Web (MotW) Security Feature Bypass Vulnerability
CVE-2023-1671 (CVSS score: 9.8) -
https://thehackernews.com/2023/11/cisa-adds-three-security-flaws-with.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, November 16, 2023
Check Point Software Technologies Expands SecureAcademy™ Program in Canada with Eight New Universities and Colleges to Empower the Next-Generation of Cybersecurity Professionals
The cybersecurity education program provides programming to academic institutions across the country, including Sheridan College, Willis College, and, most recently, the University of Calgary. Canadian organizations across all sectors are being targeted by cyberattacks. As the incidence of cybercrime continues…
Read more →
https://www.itsecuritynews.info/check-point-software-technologies-expands-secureacademy-program-in-canada-with-eight-new-universities-and-colleges-to-empower-the-next-generation-of-cybersecurity-professionals-63/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/check-point-software-technologies-expands-secureacademy-program-in-canada-with-eight-new-universities-and-colleges-to-empower-the-next-generation-of-cybersecurity-professionals-63/?utm_source=dlvr.it&utm_medium=blogger
Check Point Software Technologies Expands SecureAcademy™ Program in Canada with Eight New Universities and Colleges to Empower the Next-Generation of Cybersecurity Professionals
The cybersecurity education program provides programming to academic institutions across the country, including Sheridan College, Willis College, and, most recently, the University of Calgary. Canadian organizations across all sectors are being targeted by cyberattacks. As the incidence of cybercrime continues…
Read more →
https://www.itsecuritynews.info/check-point-software-technologies-expands-secureacademy-program-in-canada-with-eight-new-universities-and-colleges-to-empower-the-next-generation-of-cybersecurity-professionals-60/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/check-point-software-technologies-expands-secureacademy-program-in-canada-with-eight-new-universities-and-colleges-to-empower-the-next-generation-of-cybersecurity-professionals-60/?utm_source=dlvr.it&utm_medium=blogger
Zero-Day Flaw in Zimbra Email Software Exploited by Four Hacker Groups
A zero-day flaw in the Zimbra Collaboration email software was exploited by four different groups in real-world attacks to pilfer email data, user credentials, and authentication tokens.
"Most of this activity occurred after the initial fix became public on GitHub," Google Threat Analysis Group (TAG) said in a report shared with The Hacker News.
The flaw, tracked as CVE-2023-37580 (CVSS score:
https://thehackernews.com/2023/11/zero-day-flaw-in-zimbra-email-software.html?utm_source=dlvr.it&utm_medium=blogger
"Most of this activity occurred after the initial fix became public on GitHub," Google Threat Analysis Group (TAG) said in a report shared with The Hacker News.
The flaw, tracked as CVE-2023-37580 (CVSS score:
https://thehackernews.com/2023/11/zero-day-flaw-in-zimbra-email-software.html?utm_source=dlvr.it&utm_medium=blogger
Google Chrome Use-After-Free Vulnerability Leads to Browser Crash
Google Chrome Stable Channel Update for Desktop version 119.0.6.45.159 for Mac and Linux and 119.0.6045.159/.160 for Windows has been released, which will be rolling out to all users soon. There were two vulnerabilities fixed, which were CVE-2023-5997 and CVE-2023-6112. Both of these vulnerabilities were associated with Use-after-free conditions in Garbage Collection and the Navigation of […]
The post Google Chrome Use-After-Free Vulnerability Leads to Browser Crash appeared first on Cyber Security News.
https://cybersecuritynews.com/google-chrome-vulnerability-browser-crash/?utm_source=dlvr.it&utm_medium=blogger
The post Google Chrome Use-After-Free Vulnerability Leads to Browser Crash appeared first on Cyber Security News.
https://cybersecuritynews.com/google-chrome-vulnerability-browser-crash/?utm_source=dlvr.it&utm_medium=blogger
Russian Hackers Linked to 'Largest Ever Cyber Attack' on Danish Critical Infrastructure
Russian threat actors have been possibly linked to what's been described as the "largest cyber attack against Danish critical infrastructure," in which 22 companies associated with the operation of the country's energy sector were targeted in May 2023.
"22 simultaneous, successful cyberattacks against Danish critical infrastructure are not commonplace," Denmark's SektorCERT said [PDF]. "The
https://thehackernews.com/2023/11/russian-hackers-launch-largest-ever.html?utm_source=dlvr.it&utm_medium=blogger
"22 simultaneous, successful cyberattacks against Danish critical infrastructure are not commonplace," Denmark's SektorCERT said [PDF]. "The
https://thehackernews.com/2023/11/russian-hackers-launch-largest-ever.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, November 15, 2023
Microsoft Ignite: New Solutions Offer More Security and Productivity from Windows in the Cloud
Cloud PCs give you access to Windows AI tools on any device, and Windows 365 now has AI-powered tools to help IT give users the right cloud PC for their needs. This article has been indexed from Security | TechRepublic…
Read more →
https://www.itsecuritynews.info/microsoft-ignite-new-solutions-offer-more-security-and-productivity-from-windows-in-the-cloud/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/microsoft-ignite-new-solutions-offer-more-security-and-productivity-from-windows-in-the-cloud/?utm_source=dlvr.it&utm_medium=blogger
8-Point Security Checklist For Your Storage & Backups – 2024
On September 27th, Johnson Controls International announced a massive ransomware attack, that encrypted many of the company devices, including VMware ESXi servers. This impacted the company’s and its subsidiaries’ operations. The company serves clients in the government, healthcare, and naval sectors, and they believe sensitive Department of Homeland Security (DHS) information may have been compromised in […]
The post 8-Point Security Checklist For Your Storage & Backups – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/security-checklist-for-your-storage-backups/?utm_source=dlvr.it&utm_medium=blogger
The post 8-Point Security Checklist For Your Storage & Backups – 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/security-checklist-for-your-storage-backups/?utm_source=dlvr.it&utm_medium=blogger
FBI Dismantled Notorious IPStorm Botnet Infrastructure
The FBI has achieved a remarkable feat in the fight against cybercrime, dismantling the infamous IPStorm botnet network that infected tens of thousands of devices across various platforms worldwide. The brains behind this criminal operation, Sergei Makinin, a dual citizen of Russia and Moldova, has confessed to three counts of violating cybersecurity laws. The IPStorm […]
The post FBI Dismantled Notorious IPStorm Botnet Infrastructure appeared first on Cyber Security News.
https://cybersecuritynews.com/fbi-dismantled-ipstorm/?utm_source=dlvr.it&utm_medium=blogger
The post FBI Dismantled Notorious IPStorm Botnet Infrastructure appeared first on Cyber Security News.
https://cybersecuritynews.com/fbi-dismantled-ipstorm/?utm_source=dlvr.it&utm_medium=blogger
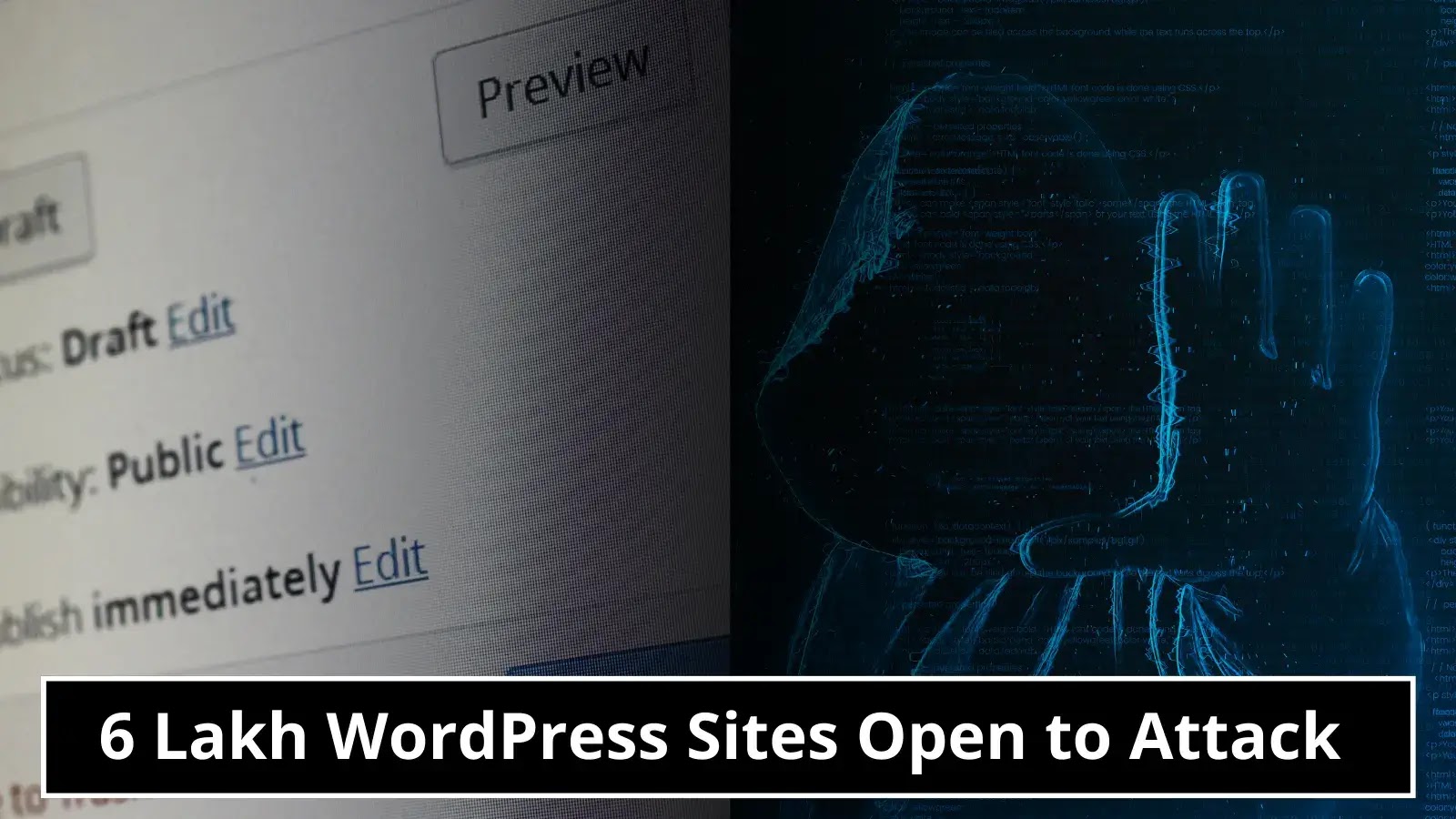
WP Fastest Cache Plugin Exposes Over 600K+ WordPress Sites to SQL Injection Attacks
In a recent development, the WPScan team has unearthed a significant security flaw within the widely-used WP Fastest Cache plugin. This vulnerability, categorized as an unauthenticated SQL injection, could potentially grant unauthorized access to sensitive data in the WordPress database. The vulnerability, identified as CVE-2023-6063, affects versions of WP Fastest Cache lower than 1.2.2. Upon […]
The post WP Fastest Cache Plugin Exposes Over 600K+ WordPress Sites to SQL Injection Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/wp-fastest-cache-plugin-exposes/?utm_source=dlvr.it&utm_medium=blogger
The post WP Fastest Cache Plugin Exposes Over 600K+ WordPress Sites to SQL Injection Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/wp-fastest-cache-plugin-exposes/?utm_source=dlvr.it&utm_medium=blogger
Hackers Deliver Weaponized LNK Files Through Legitimate Websites
LNK files are shortcut files in Windows that link to a program or file. Hackers may exploit LNK files to deliver malicious payloads by disguising them as legitimate shortcuts, taking advantage of users who unknowingly click on them, and allowing for the execution of malicious code. Over the years, malware distribution methods have evolved and […]
The post Hackers Deliver Weaponized LNK Files Through Legitimate Websites appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-deliver-weaponized-lnk-files/?utm_source=dlvr.it&utm_medium=blogger
The post Hackers Deliver Weaponized LNK Files Through Legitimate Websites appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-deliver-weaponized-lnk-files/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, November 14, 2023
Fall back…into some good digital health habits
Fall is here, and along with cozy sweaters, family gatherings, and PSLs, comes the tradition of turning the clocks back as Daylight Saving Time (DST) ends. Although we’re not certain why this practice lives on in 2023, it lends itself…
Read more →
https://www.itsecuritynews.info/fall-back-into-some-good-digital-health-habits/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/fall-back-into-some-good-digital-health-habits/?utm_source=dlvr.it&utm_medium=blogger
CacheWarp Attack: New Vulnerability in AMD SEV Exposes Encrypted VMs
A group of academics has disclosed a new "software fault attack" on AMD's Secure Encrypted Virtualization (SEV) technology that could be potentially exploited by threat actors to infiltrate encrypted virtual machines (VMs) and even perform privilege escalation.
The attack has been codenamed CacheWarp (CVE-2023-20592) by researchers from the CISPA Helmholtz Center for Information Security. It
https://thehackernews.com/2023/11/cachewarp-attack-new-vulnerability-in.html?utm_source=dlvr.it&utm_medium=blogger
The attack has been codenamed CacheWarp (CVE-2023-20592) by researchers from the CISPA Helmholtz Center for Information Security. It
https://thehackernews.com/2023/11/cachewarp-attack-new-vulnerability-in.html?utm_source=dlvr.it&utm_medium=blogger
8 New Metasploit Exploit Modules Released Targeting Critical Vulnerabilities
Metasploit is an open-source penetration testing framework created by Rapid7 that enables security professionals to simulate attacks against computer systems, networks, and applications. It includes several tools and modules that can be used to test the target system’s security, detect vulnerabilities, and use them to gain access to the system. Two recent noteworthy vulnerabilities that have […]
The post 8 New Metasploit Exploit Modules Released Targeting Critical Vulnerabilities appeared first on Cyber Security News.
https://cybersecuritynews.com/new-metasploit-modules/?utm_source=dlvr.it&utm_medium=blogger
The post 8 New Metasploit Exploit Modules Released Targeting Critical Vulnerabilities appeared first on Cyber Security News.
https://cybersecuritynews.com/new-metasploit-modules/?utm_source=dlvr.it&utm_medium=blogger
Alert: OracleIV DDoS Botnet Targets Public Docker Engine APIs to Hijack Containers
Publicly-accessible Docker Engine API instances are being targeted by threat actors as part of a campaign designed to co-opt the machines into a distributed denial-of-service (DDoS) botnet dubbed OracleIV.
"Attackers are exploiting this misconfiguration to deliver a malicious Docker container, built from an image named 'oracleiv_latest' and containing Python malware compiled as an ELF executable
https://thehackernews.com/2023/11/alert-oracleiv-ddos-botnet-targets.html?utm_source=dlvr.it&utm_medium=blogger
"Attackers are exploiting this misconfiguration to deliver a malicious Docker container, built from an image named 'oracleiv_latest' and containing Python malware compiled as an ELF executable
https://thehackernews.com/2023/11/alert-oracleiv-ddos-botnet-targets.html?utm_source=dlvr.it&utm_medium=blogger
Cyber Attack on DP World Halted Container Movements
DP World Australia, a leading provider of landside freight operations, issued an update on Friday, November 10, regarding its efforts to address a cybersecurity incident that affected its systems. The company has collaborated with cybersecurity experts to restore its terminal operations securely and safely. Security and continuity The company has placed security as its utmost […]
The post Cyber Attack on DP World Halted Container Movements appeared first on Cyber Security News.
https://cybersecuritynews.com/dp-world-cyber-attack/?utm_source=dlvr.it&utm_medium=blogger
The post Cyber Attack on DP World Halted Container Movements appeared first on Cyber Security News.
https://cybersecuritynews.com/dp-world-cyber-attack/?utm_source=dlvr.it&utm_medium=blogger
Monday, November 13, 2023
‘Hunters International’ Cyberattackers Take Over Hive Ransomware
Hunters International appears to have acquired Hive ransomware from its original operators and may be seeking to cash in on the malware’s reputation. This article has been indexed from Dark Reading Read the original article: ‘Hunters International’ Cyberattackers Take Over…
Read more →
https://www.itsecuritynews.info/hunters-international-cyberattackers-take-over-hive-ransomware/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/hunters-international-cyberattackers-take-over-hive-ransomware/?utm_source=dlvr.it&utm_medium=blogger
Information-Stealing Malware Escalates in Online Gaming
A report by Sekoia.io shed light on a targeted campaign using Discord and fake download websites This article has been indexed from www.infosecurity-magazine.com Read the original article: Information-Stealing Malware Escalates in Online Gaming
Read more →
https://www.itsecuritynews.info/information-stealing-malware-escalates-in-online-gaming/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/information-stealing-malware-escalates-in-online-gaming/?utm_source=dlvr.it&utm_medium=blogger
Multiple Vulnerabilities Found In PureVPN – One Remains Unpatched
Researchers spotted a couple of security vulnerabilities in PureVPN Desktop clients for Linux that impact… Multiple Vulnerabilities Found In PureVPN – One Remains Unpatched on Latest Hacking News | Cyber Security News, Hacking Tools and Penetration Testing Courses. This article…
Read more →
https://www.itsecuritynews.info/multiple-vulnerabilities-found-in-purevpn-one-remains-unpatched/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/multiple-vulnerabilities-found-in-purevpn-one-remains-unpatched/?utm_source=dlvr.it&utm_medium=blogger
BiBi Wiper Attacking Windows Machine to Cause Data Destruction
The ongoing conflict between Israel and Hamas has taken a new turn as cyberattacks have become a prominent weapon for both sides. A new wiper malware, dubbed the BiBi-Linux Wiper, has been discovered by an Israeli security firm, targeting Linux systems and causing irreversible data loss. The malware is believed to be deployed by pro-Hamas […]
The post BiBi Wiper Attacking Windows Machine to Cause Data Destruction appeared first on Cyber Security News.
https://cybersecuritynews.com/bibi-wiper-attacking-windows/?utm_source=dlvr.it&utm_medium=blogger
The post BiBi Wiper Attacking Windows Machine to Cause Data Destruction appeared first on Cyber Security News.
https://cybersecuritynews.com/bibi-wiper-attacking-windows/?utm_source=dlvr.it&utm_medium=blogger
New BiBi-Windows Wiper Targets Windows Systems in Pro-Hamas Attacks
Cybersecurity researchers have warned about a Windows version of a wiper malware that was previously observed targeting Linux systems in cyber attacks aimed at Israel.
Dubbed BiBi-Windows Wiper by BlackBerry, the wiper is the Windows counterpart of BiBi-Linux Wiper, which has been put to use by a pro-Hamas hacktivist group in the wake of the Israel-Hamas war last month.
"The Windows variant [...
https://thehackernews.com/2023/11/new-bibi-windows-wiper-targets-windows.html?utm_source=dlvr.it&utm_medium=blogger
Dubbed BiBi-Windows Wiper by BlackBerry, the wiper is the Windows counterpart of BiBi-Linux Wiper, which has been put to use by a pro-Hamas hacktivist group in the wake of the Israel-Hamas war last month.
"The Windows variant [...
https://thehackernews.com/2023/11/new-bibi-windows-wiper-targets-windows.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, November 12, 2023
Apple Co-founder Says AI Could Make Cyber Scams ‘Harder to Spot’
Apple co-founder Steve Wozniak recently cautioned that artificial intelligence (AI) could result in making cyber scams and misinformation more challenging to recognize. Speaking to BBC, he further notes that technology may as well be harnessed by “bad actors.” According to…
Read more →
https://www.itsecuritynews.info/apple-co-founder-says-ai-could-make-cyber-scams-harder-to-spot/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/apple-co-founder-says-ai-could-make-cyber-scams-harder-to-spot/?utm_source=dlvr.it&utm_medium=blogger
What is the threat landscape, and why should you care?
The threat landscape is the entirety of potential and identified cyber threats affecting a particular sector, group of users, time period, and so forth. It includes a wide range of threats, such as malware, phishing attacks, ransomware, and social engineering…
Read more →
https://www.itsecuritynews.info/what-is-the-threat-landscape-and-why-should-you-care/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/what-is-the-threat-landscape-and-why-should-you-care/?utm_source=dlvr.it&utm_medium=blogger
The State of Maine disclosed a data breach that impacted 1.3M people
The State of Maine disclosed a data breach that impacted about 1.3 million people after an attack hit its MOVEit file transfer install. The State of Maine was the victim of the large-scale hacking campaign that targeted organizations using the MOVEit file transfer…
Read more →
https://www.itsecuritynews.info/the-state-of-maine-disclosed-a-data-breach-that-impacted-1-3m-people/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/the-state-of-maine-disclosed-a-data-breach-that-impacted-1-3m-people/?utm_source=dlvr.it&utm_medium=blogger
Cyber Insurance Roundup: What’s Happening Now?
From the roller-coaster ride in rates to new generative AI uses to dramatic changes in underwriting rules, cyber insurance is evolving fast. Here are some of the latest trends. The post Cyber Insurance Roundup: What’s Happening Now? appeared first on…
Read more →
https://www.itsecuritynews.info/cyber-insurance-roundup-whats-happening-now/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/cyber-insurance-roundup-whats-happening-now/?utm_source=dlvr.it&utm_medium=blogger
Microsoft Warns of Fake Skills Assessment Portals Targeting IT Job Seekers
A sub-cluster within the infamous Lazarus Group has established new infrastructure that impersonates skills assessment portals as part of its social engineering campaigns.
Microsoft attributed the activity to a threat actor it calls Sapphire Sleet, describing it as a "shift in the persistent actor's tactics."
Sapphire Sleet, also called APT38, BlueNoroff, CageyChameleon, and CryptoCore, has a
https://thehackernews.com/2023/11/microsoft-warns-of-fake-skills.html?utm_source=dlvr.it&utm_medium=blogger
Microsoft attributed the activity to a threat actor it calls Sapphire Sleet, describing it as a "shift in the persistent actor's tactics."
Sapphire Sleet, also called APT38, BlueNoroff, CageyChameleon, and CryptoCore, has a
https://thehackernews.com/2023/11/microsoft-warns-of-fake-skills.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, November 11, 2023
Zero-Day Alert: Lace Tempest Exploits SysAid IT Support Software Vulnerability
The threat actor known as Lace Tempest has been linked to the exploitation of a zero-day flaw in SysAid IT support software in limited attacks, according to new findings from Microsoft.
Lace Tempest, which is known for distributing the Cl0p ransomware, has in the past leveraged zero-day flaws in MOVEit Transfer and PaperCut servers.
The issue, tracked as CVE-2023-47246, concerns a path traversal
https://thehackernews.com/2023/11/zero-day-alert-lace-tempest-exploits.html?utm_source=dlvr.it&utm_medium=blogger
Lace Tempest, which is known for distributing the Cl0p ransomware, has in the past leveraged zero-day flaws in MOVEit Transfer and PaperCut servers.
The issue, tracked as CVE-2023-47246, concerns a path traversal
https://thehackernews.com/2023/11/zero-day-alert-lace-tempest-exploits.html?utm_source=dlvr.it&utm_medium=blogger
New Malvertising Campaign Uses Fake Windows News Portal to Distribute Malicious Installers
A new malvertising campaign has been found to employ fake sites that masquerade as legitimate Windows news portal to propagate a malicious installer for a popular system profiling tool called CPU-Z.
"This incident is a part of a larger malvertising campaign that targets other utilities like Notepad++, Citrix, and VNC Viewer as seen in its infrastructure (domain names) and cloaking templates used
https://thehackernews.com/2023/11/new-malvertising-campaign-uses-fake.html?utm_source=dlvr.it&utm_medium=blogger
"This incident is a part of a larger malvertising campaign that targets other utilities like Notepad++, Citrix, and VNC Viewer as seen in its infrastructure (domain names) and cloaking templates used
https://thehackernews.com/2023/11/new-malvertising-campaign-uses-fake.html?utm_source=dlvr.it&utm_medium=blogger
When Email Security Meets SaaS Security: Uncovering Risky Auto-Forwarding Rules
While intended for convenience and efficient communication, email auto-forwarding rules can inadvertently lead to the unauthorized dissemination of sensitive information to external entities, putting confidential data at risk of exposure to unauthorized parties. Wing Security (Wing), a SaaS security company, announced yesterday that their SaaS shadow IT discovery methods now include a solution
https://thehackernews.com/2023/11/when-email-security-meets-saas-security.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/11/when-email-security-meets-saas-security.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)





-1-1.webp)