Three unpatched high-severity security flaws have been disclosed in the NGINX Ingress controller for Kubernetes that could be weaponized by a threat actor to steal secret credentials from the cluster.
The vulnerabilities are as follows -
CVE-2022-4886 (CVSS score: 8.8) - Ingress-nginx path sanitization can be bypassed to obtain the credentials of the ingress-nginx controller
CVE-2023-5043 (
https://thehackernews.com/2023/10/urgent-new-security-flaws-discovered-in.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, October 31, 2023
Monday, October 30, 2023
iLeakage – New Attack Let Hackers Steal Emails, Passwords On Apple Safari
Browser-based timerless speculative execution attacks are a security threat that exploits vulnerabilities in web browsers and CPUs. These attacks do not rely on timing measurements, making them harder to detect. Their sophistication varies, but they can be very advanced, allowing attackers to steal sensitive data or compromise system security by exploiting speculative execution mechanisms in […]
The post iLeakage – New Attack Let Hackers Steal Emails, Passwords On Apple Safari appeared first on Cyber Security News.
https://cybersecuritynews.com/ileakage-new-attack/?utm_source=dlvr.it&utm_medium=blogger
The post iLeakage – New Attack Let Hackers Steal Emails, Passwords On Apple Safari appeared first on Cyber Security News.
https://cybersecuritynews.com/ileakage-new-attack/?utm_source=dlvr.it&utm_medium=blogger
Sunday, October 29, 2023
BIG-IP Vulnerability Allows Attackers to Execute Remote Code
A critical security flaw that might allow for unauthenticated remote code execution has been identified and is categorized as CVE-2023-46747 with a 9.8 CVSS score. The F5 reports state that this problem originated in the configuration utility. The vulnerability was found and reported on October 4, 2023, by Praetorian Michael Weber and Thomas Hendrickson. BIG-IP […]
The post BIG-IP Vulnerability Allows Attackers to Execute Remote Code appeared first on Cyber Security News.
https://cybersecuritynews.com/big-ip-rce-flaw/?utm_source=dlvr.it&utm_medium=blogger
The post BIG-IP Vulnerability Allows Attackers to Execute Remote Code appeared first on Cyber Security News.
https://cybersecuritynews.com/big-ip-rce-flaw/?utm_source=dlvr.it&utm_medium=blogger
Saturday, October 28, 2023
An integrated incident response solution with Microsoft and PwC
Microsoft Incident Response and PwC have announced a new global alliance to expand their joint Incident Response and Recovery capability. In this partnership, Microsoft IR will begin the initial containment and investigation of a cyber incident, while PwC will work…
Read more →
https://www.itsecuritynews.info/an-integrated-incident-response-solution-with-microsoft-and-pwc/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/an-integrated-incident-response-solution-with-microsoft-and-pwc/?utm_source=dlvr.it&utm_medium=blogger
Friday, October 27, 2023
Why Small Businesses Need a Malware Sandbox ? – Top 3 Reasons in 2023
Running a small business can often lead to the misconception that cyber-security is not a priority due to the company’s size. This false assumption can have devastating consequences if a cyber-attack occurs. To ensure that your business remains operational in the face of any threat, it is essential to have a robust security system in […]
The post Why Small Businesses Need a Malware Sandbox ? – Top 3 Reasons in 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-sandbox-for-small-business/?utm_source=dlvr.it&utm_medium=blogger
The post Why Small Businesses Need a Malware Sandbox ? – Top 3 Reasons in 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-sandbox-for-small-business/?utm_source=dlvr.it&utm_medium=blogger
Thursday, October 26, 2023
Ransomware isn’t going away – the problem is only getting worse
As the world moves steadily to becoming more and more digital, organizations worldwide become increasingly… This article has been indexed from RedPacket Security Read the original article: Ransomware isn’t going away – the problem is only getting worse
Read more →
https://www.itsecuritynews.info/ransomware-isnt-going-away-the-problem-is-only-getting-worse/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/ransomware-isnt-going-away-the-problem-is-only-getting-worse/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, October 25, 2023
1Password Hacked – Internal Systems Compromised to Access HAR File
Recently, 1Password detected suspicious activity on their Okta instance on September 29, but no user data or sensitive systems were compromised. 1Password is widely used as a popular password manager and security tool, trusted by individuals and businesses. Users opt for 1Password due to its: These fundamental elements make storing and managing passwords, credit card […]
The post 1Password Hacked – Internal Systems Compromised to Access HAR File appeared first on Cyber Security News.
https://cybersecuritynews.com/1password-hacked/?utm_source=dlvr.it&utm_medium=blogger
The post 1Password Hacked – Internal Systems Compromised to Access HAR File appeared first on Cyber Security News.
https://cybersecuritynews.com/1password-hacked/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, October 24, 2023
Hackers update Cisco IOS XE backdoor to hide infected devices
10/23/23 update added at the end explaining the cause of decreased detections. The number of… This article has been indexed from RedPacket Security Read the original article: Hackers update Cisco IOS XE backdoor to hide infected devices
Read more →
The post Hackers update Cisco IOS XE backdoor to hide infected devices first appeared on IT Security News.
https://www.itsecuritynews.info/hackers-update-cisco-ios-xe-backdoor-to-hide-infected-devices/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post Hackers update Cisco IOS XE backdoor to hide infected devices first appeared on IT Security News.
https://www.itsecuritynews.info/hackers-update-cisco-ios-xe-backdoor-to-hide-infected-devices/?utm_source=dlvr.it&utm_medium=blogger
Monday, October 23, 2023
Exposing North Korea’s IT Worker’s Eden Programming Solutions WMD-Funding IT Services and Solutions Franchise – An Overview
Jessus. This just in and I think I “did it” and I might even apply fore the Rewards for Justice program second time in a row […] This article has been indexed from Security Boulevard Read the original article: Exposing…
Read more →
The post Exposing North Korea’s IT Worker’s Eden Programming Solutions WMD-Funding IT Services and Solutions Franchise – An Overview first appeared on IT Security News.
https://www.itsecuritynews.info/exposing-north-koreas-it-workers-eden-programming-solutions-wmd-funding-it-services-and-solutions-franchise-an-overview/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post Exposing North Korea’s IT Worker’s Eden Programming Solutions WMD-Funding IT Services and Solutions Franchise – An Overview first appeared on IT Security News.
https://www.itsecuritynews.info/exposing-north-koreas-it-workers-eden-programming-solutions-wmd-funding-it-services-and-solutions-franchise-an-overview/?utm_source=dlvr.it&utm_medium=blogger
Sunday, October 22, 2023
RansomHouse Ransomware Victim: Foursquare Healthcare
NOTE: No files or stolen information are [exfiltrated/downloaded/taken/hosted/seen/reposted/disclosed] by RedPacket Security. Any legal issues… This article has been indexed from RedPacket Security Read the original article: RansomHouse Ransomware Victim: Foursquare Healthcare
Read more →
The post RansomHouse Ransomware Victim: Foursquare Healthcare first appeared on IT Security News.
https://www.itsecuritynews.info/ransomhouse-ransomware-victim-foursquare-healthcare/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post RansomHouse Ransomware Victim: Foursquare Healthcare first appeared on IT Security News.
https://www.itsecuritynews.info/ransomhouse-ransomware-victim-foursquare-healthcare/?utm_source=dlvr.it&utm_medium=blogger
Tunngle – 8,192,928 breached accounts
In 2016, the now defunct global LAN gaming network Tunngle suffered a data breach that exposed 8.2M unique email addresses. The compromised data also included usernames, IP addresses and passwords stored as salted MD5 hashes. This article has been indexed…
Read more →
The post Tunngle – 8,192,928 breached accounts first appeared on IT Security News.
https://www.itsecuritynews.info/tunngle-8192928-breached-accounts/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post Tunngle – 8,192,928 breached accounts first appeared on IT Security News.
https://www.itsecuritynews.info/tunngle-8192928-breached-accounts/?utm_source=dlvr.it&utm_medium=blogger
Saturday, October 21, 2023
How to Stay Anonymous on the Internet in 12 Secure Steps
The internet can be a fun and social experience, but it can also have a dark side. In this digital age, protecting your information is… The post How to Stay Anonymous on the Internet in 12 Secure Steps appeared first…
Read more →
The post How to Stay Anonymous on the Internet in 12 Secure Steps first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-stay-anonymous-on-the-internet-in-12-secure-steps/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post How to Stay Anonymous on the Internet in 12 Secure Steps first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-stay-anonymous-on-the-internet-in-12-secure-steps/?utm_source=dlvr.it&utm_medium=blogger
Friday, October 20, 2023
Unraveling Real-Life Attack Paths – Key Lessons Learned
In the ever-evolving landscape of cybersecurity, attackers are always searching for vulnerabilities and exploits within organizational environments. They don't just target single weaknesses; they're on the hunt for combinations of exposures and attack methods that can lead them to their desired objective.
Despite the presence of numerous security tools, organizations often have to deal with two
https://thehackernews.com/2023/10/unraveling-real-life-attack-paths-key.html?utm_source=dlvr.it&utm_medium=blogger
Despite the presence of numerous security tools, organizations often have to deal with two
https://thehackernews.com/2023/10/unraveling-real-life-attack-paths-key.html?utm_source=dlvr.it&utm_medium=blogger
Qubitstrike Targets Jupyter Notebooks with Crypto Mining and Rootkit Campaign
A threat actor, presumably from Tunisia, has been linked to a new campaign targeting exposed Jupyter Notebooks in a two-fold attempt to illicitly mine cryptocurrency and breach cloud environments.
Dubbed Qubitstrike by Cado, the intrusion set utilizes Telegram API to exfiltrate cloud service provider credentials following a successful compromise.
"The payloads for the Qubitstrike campaign are
https://thehackernews.com/2023/10/qubitstrike-targets-jupyter-notebooks.html?utm_source=dlvr.it&utm_medium=blogger
Dubbed Qubitstrike by Cado, the intrusion set utilizes Telegram API to exfiltrate cloud service provider credentials following a successful compromise.
"The payloads for the Qubitstrike campaign are
https://thehackernews.com/2023/10/qubitstrike-targets-jupyter-notebooks.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, October 19, 2023
Recently patched Citrix NetScaler bug exploited as zero-day since August
A critical vulnerability tracked as CVE-2023-4966 in Citrix NetScaler ADC/Gateway devices has been actively exploited as… This article has been indexed from RedPacket Security Read the original article: Recently patched Citrix NetScaler bug exploited as zero-day since August
Read more →
The post Recently patched Citrix NetScaler bug exploited as zero-day since August first appeared on IT Security News.
https://www.itsecuritynews.info/recently-patched-citrix-netscaler-bug-exploited-as-zero-day-since-august/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post Recently patched Citrix NetScaler bug exploited as zero-day since August first appeared on IT Security News.
https://www.itsecuritynews.info/recently-patched-citrix-netscaler-bug-exploited-as-zero-day-since-august/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, October 18, 2023
ChatGPT for Vulnerability Detection – Prompts Used and their Responses
Software vulnerabilities are essentially errors in code that malicious actors can exploit. Advanced language models such as CodeBERT, GraphCodeBERT, and CodeT5 can detect these vulnerabilities, provide detailed analysis assessments, and even recommend patches to address them. These models have proven to be highly effective in identifying and mitigating software vulnerabilities, making them an essential tool […]
The post ChatGPT for Vulnerability Detection – Prompts Used and their Responses appeared first on Cyber Security News.
https://cybersecuritynews.com/chatgpt-for-vulnerability-detection/?utm_source=dlvr.it&utm_medium=blogger
The post ChatGPT for Vulnerability Detection – Prompts Used and their Responses appeared first on Cyber Security News.
https://cybersecuritynews.com/chatgpt-for-vulnerability-detection/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, October 17, 2023
CISA, FBI urge admins to patch Atlassian Confluence immediately
CISA, FBI, and MS-ISAC warned network admins today to immediately patch their Atlassian Confluence servers… This article has been indexed from RedPacket Security Read the original article: CISA, FBI urge admins to patch Atlassian Confluence immediately
Read more →
The post CISA, FBI urge admins to patch Atlassian Confluence immediately first appeared on IT Security News.
https://www.itsecuritynews.info/cisa-fbi-urge-admins-to-patch-atlassian-confluence-immediately/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post CISA, FBI urge admins to patch Atlassian Confluence immediately first appeared on IT Security News.
https://www.itsecuritynews.info/cisa-fbi-urge-admins-to-patch-atlassian-confluence-immediately/?utm_source=dlvr.it&utm_medium=blogger
Monday, October 16, 2023
Node.js Multiple Vulnerabilities
Multiple vulnerabilities have been identified in Node.js. A remote attacker can exploit these vulnerabilities to… This article has been indexed from RedPacket Security Read the original article: Node.js Multiple Vulnerabilities
Read more →
The post Node.js Multiple Vulnerabilities first appeared on IT Security News.
https://www.itsecuritynews.info/node-js-multiple-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post Node.js Multiple Vulnerabilities first appeared on IT Security News.
https://www.itsecuritynews.info/node-js-multiple-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
Sunday, October 15, 2023
HackerOne Bug Bounty Disclosure: b-client-side-string-length-check-b-tomh
Company Name: b’Khan Academy’ Company HackerOne URL:
https://hackerone.com/khanacademy Submitted By:b’tomh’ Link to Submitters Profile:
https://hackerone.com/b’tomh’ Report… This article has been indexed from RedPacket Security Read the original article: HackerOne Bug Bounty Disclosure: b-client-side-string-length-check-b-tomh
Read more →
The post HackerOne Bug Bounty Disclosure: b-client-side-string-length-check-b-tomh first appeared on IT Security News.
https://www.itsecuritynews.info/hackerone-bug-bounty-disclosure-b-client-side-string-length-check-b-tomh/?utm_source=dlvr.it&utm_medium=blogger
https://hackerone.com/khanacademy Submitted By:b’tomh’ Link to Submitters Profile:
https://hackerone.com/b’tomh’ Report… This article has been indexed from RedPacket Security Read the original article: HackerOne Bug Bounty Disclosure: b-client-side-string-length-check-b-tomh
Read more →
The post HackerOne Bug Bounty Disclosure: b-client-side-string-length-check-b-tomh first appeared on IT Security News.
https://www.itsecuritynews.info/hackerone-bug-bounty-disclosure-b-client-side-string-length-check-b-tomh/?utm_source=dlvr.it&utm_medium=blogger
Saturday, October 14, 2023
Microsoft Defender Thwarts Large-Scale Akira Ransomware Attack
Microsoft on Wednesday said that a user containment feature in Microsoft Defender for Endpoint helped thwart a "large-scale remote encryption attempt" made by Akira ransomware actors targeting an unknown industrial organization in early June 2023.
The tech giant's threat intelligence team is tracking the operator as Storm-1567.
The attack leveraged devices that were not onboarded to Microsoft
https://thehackernews.com/2023/10/microsoft-defender-thwarts-akira.html?utm_source=dlvr.it&utm_medium=blogger
The tech giant's threat intelligence team is tracking the operator as Storm-1567.
The attack leveraged devices that were not onboarded to Microsoft
https://thehackernews.com/2023/10/microsoft-defender-thwarts-akira.html?utm_source=dlvr.it&utm_medium=blogger
Friday, October 13, 2023
Stronger ransomware protection finally pays off
60% of companies are ‘very’ to ‘extremely’ concerned about ransomware attacks, according to latest research from Hornetsecurity. Businesses acknowledge ransomware risk Hornetsecurity revealed that 92.5% businesses are aware of ransomware’s potential for negative impact. Still, just 54% of respondents said…
Read more →
The post Stronger ransomware protection finally pays off first appeared on IT Security News.
https://www.itsecuritynews.info/stronger-ransomware-protection-finally-pays-off/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post Stronger ransomware protection finally pays off first appeared on IT Security News.
https://www.itsecuritynews.info/stronger-ransomware-protection-finally-pays-off/?utm_source=dlvr.it&utm_medium=blogger
Thursday, October 12, 2023
Google Adopts Passkeys as Default Sign-in Method for All Users
Google on Tuesday announced the ability for all users to set up passkeys by default, five months after it rolled out support for the FIDO Alliance-backed passwordless standard for Google Accounts on all platforms.
"This means the next time you sign in to your account, you'll start seeing prompts to create and use passkeys, simplifying your future sign-ins," Google's Sriram Karra and Christiaan
https://thehackernews.com/2023/10/google-adopts-passkeys-as-default-sign.html?utm_source=dlvr.it&utm_medium=blogger
"This means the next time you sign in to your account, you'll start seeing prompts to create and use passkeys, simplifying your future sign-ins," Google's Sriram Karra and Christiaan
https://thehackernews.com/2023/10/google-adopts-passkeys-as-default-sign.html?utm_source=dlvr.it&utm_medium=blogger
New Report: Child Sexual Abuse Content and Online Risks to Children on the Rise
Certain online risks to children are on the rise, according to a recent report from Thorn, a technology nonprofit whose mission is to build technology to defend children from sexual abuse. Research shared in the Emerging Online Trends in Child Sexual Abuse 2023 report, indicates that minors are increasingly taking and sharing sexual images of themselves. This activity may occur consensually or
https://thehackernews.com/2023/10/new-report-child-sexual-abuse-content.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/10/new-report-child-sexual-abuse-content.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, October 11, 2023
ChatGPT, FraudGPT, and WormGPT Plays A Vital Role in Social Engineering Attacks
Generative AI models like ChatGPT, FraudGPT, and WormGPT bring innovation and new challenges in cybersecurity’s evolution. These generative AI models revolutionize cyberattacks, enabling personalized phishing, deepfakes, and cognitive bias exploitation, amplifying existing threats and introducing new risks. Generative AI boosts cybercriminals with the following abilities:- Document FREE Demo Deploy Advanced AI-Powered Email Security Solution Implementing […]
The post ChatGPT, FraudGPT, and WormGPT Plays A Vital Role in Social Engineering Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/chatgpt-fraudgpt-and-wormgpt/?utm_source=dlvr.it&utm_medium=blogger
The post ChatGPT, FraudGPT, and WormGPT Plays A Vital Role in Social Engineering Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/chatgpt-fraudgpt-and-wormgpt/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, October 10, 2023
Security Patch for Two New Flaws in Curl Library Arriving on October 11
The maintainers of the Curl library have released an advisory warning of two security vulnerabilities that are expected to be addressed as part of an forthcoming update set for release on October 11, 2023.
This includes a high-severity and a low-severity flaw tracked under the identifiers CVE-2023-38545 and CVE-2023-38546, respectively.
Additional details about the issues and the exact version
https://thehackernews.com/2023/10/security-patch-for-two-new-flaws-in.html?utm_source=dlvr.it&utm_medium=blogger
This includes a high-severity and a low-severity flaw tracked under the identifiers CVE-2023-38545 and CVE-2023-38546, respectively.
Additional details about the issues and the exact version
https://thehackernews.com/2023/10/security-patch-for-two-new-flaws-in.html?utm_source=dlvr.it&utm_medium=blogger
Monday, October 9, 2023
Threat Actors Employ Remote Admin Tools to Gain Access over Corporate Networks
Recently, threat actors have adapted tactics, exploiting the appeal of banned apps in specific regions, making users more susceptible to cyberattacks through cleverly crafted campaigns. In a recent campaign, Chinese users were lured with a fake Telegram installer to illustrate this tactic. Cybersecurity researchers at CRIL (Cyble Research and Intelligence Labs) noted a campaign targeting […]
The post Threat Actors Employ Remote Admin Tools to Gain Access over Corporate Networks appeared first on Cyber Security News.
https://cybersecuritynews.com/threat-actors-employ-remote-admin-tools/?utm_source=dlvr.it&utm_medium=blogger
The post Threat Actors Employ Remote Admin Tools to Gain Access over Corporate Networks appeared first on Cyber Security News.
https://cybersecuritynews.com/threat-actors-employ-remote-admin-tools/?utm_source=dlvr.it&utm_medium=blogger
Sunday, October 8, 2023
Why is Skepticism the Best Protection When Adopting Generative AI?
It has become crucial for companies to implement generative artificial intelligence (AI) while minimizing potential hazards and with a healthy dose of skepticism. According to a Gartner report issued on Tuesday, 45% of firms are presently testing generative AI, while…
Read more →
The post Why is Skepticism the Best Protection When Adopting Generative AI? first appeared on IT Security News.
https://www.itsecuritynews.info/why-is-skepticism-the-best-protection-when-adopting-generative-ai/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post Why is Skepticism the Best Protection When Adopting Generative AI? first appeared on IT Security News.
https://www.itsecuritynews.info/why-is-skepticism-the-best-protection-when-adopting-generative-ai/?utm_source=dlvr.it&utm_medium=blogger
Saturday, October 7, 2023
GitHub's Secret Scanning Feature Now Covers AWS, Microsoft, Google, and Slack
GitHub has announced an improvement to its secret scanning feature that extends validity checks to popular services such as Amazon Web Services (AWS), Microsoft, Google, and Slack.
Validity checks, introduced by the Microsoft subsidiary earlier this year, alert users whether exposed tokens found by secret scanning are active, thereby allowing for effective remediation measures. It was first
https://thehackernews.com/2023/10/githubs-secret-scanning-feature-now.html?utm_source=dlvr.it&utm_medium=blogger
Validity checks, introduced by the Microsoft subsidiary earlier this year, alert users whether exposed tokens found by secret scanning are active, thereby allowing for effective remediation measures. It was first
https://thehackernews.com/2023/10/githubs-secret-scanning-feature-now.html?utm_source=dlvr.it&utm_medium=blogger
Friday, October 6, 2023
Businesses Beware: Essential Cybersecurity Best Practices
Cybersecurity is an increasingly important consideration for businesses of all sizes. It is essential to understand and implement the best practices to ensure that data… The post Businesses Beware: Essential Cybersecurity Best Practices appeared first on Security Zap. This article…
Read more →
The post Businesses Beware: Essential Cybersecurity Best Practices first appeared on IT Security News.
https://www.itsecuritynews.info/businesses-beware-essential-cybersecurity-best-practices/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post Businesses Beware: Essential Cybersecurity Best Practices first appeared on IT Security News.
https://www.itsecuritynews.info/businesses-beware-essential-cybersecurity-best-practices/?utm_source=dlvr.it&utm_medium=blogger
BlackByte Ransomware Victim: Meridian Cooperative
NOTE: No files or stolen information are [exfiltrated/downloaded/taken/hosted/seen/reposted/disclosed] by RedPacket Security. Any legal issues relating… This article has been indexed from RedPacket Security Read the original article: BlackByte Ransomware Victim: Meridian Cooperative
Read more →
The post BlackByte Ransomware Victim: Meridian Cooperative first appeared on IT Security News.
https://www.itsecuritynews.info/blackbyte-ransomware-victim-meridian-cooperative/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post BlackByte Ransomware Victim: Meridian Cooperative first appeared on IT Security News.
https://www.itsecuritynews.info/blackbyte-ransomware-victim-meridian-cooperative/?utm_source=dlvr.it&utm_medium=blogger
Thursday, October 5, 2023
Looney Tunables: New Linux Flaw Enables Privilege Escalation on Major Distributions
A new Linux security vulnerability dubbed Looney Tunables has been discovered in the GNU C library's ld.so dynamic loader that, if successfully exploited, could lead to a local privilege escalation and allow a threat actor to gain root privileges.
Tracked as CVE-2023-4911 (CVSS score: 7.8), the issue is a buffer overflow that resides in the dynamic loader's processing of the GLIBC_TUNABLES
https://thehackernews.com/2023/10/looney-tunables-new-linux-flaw-enables.html?utm_source=dlvr.it&utm_medium=blogger
Tracked as CVE-2023-4911 (CVSS score: 7.8), the issue is a buffer overflow that resides in the dynamic loader's processing of the GLIBC_TUNABLES
https://thehackernews.com/2023/10/looney-tunables-new-linux-flaw-enables.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, October 4, 2023
Researcher Reveals New Techniques to Bypass Cloudflare's Firewall and DDoS Protection
Firewall and distributed denial-of-service (DDoS) attack prevention mechanisms in Cloudflare can be circumvented by exploiting gaps in cross-tenant security controls, defeating the very purpose of these safeguards, it has emerged.
"Attackers can utilize their own Cloudflare accounts to abuse the per-design trust-relationship between Cloudflare and the customers' websites, rendering the
https://thehackernews.com/2023/10/researcher-reveal-new-technique-to.html?utm_source=dlvr.it&utm_medium=blogger
"Attackers can utilize their own Cloudflare accounts to abuse the per-design trust-relationship between Cloudflare and the customers' websites, rendering the
https://thehackernews.com/2023/10/researcher-reveal-new-technique-to.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, October 3, 2023
LUCR-3: Scattered Spider Getting SaaS-y in the Cloud
LUCR-3 overlaps with groups such as Scattered Spider, Oktapus, UNC3944, and STORM-0875 and is a financially motivated attacker that leverages the Identity Provider (IDP) as initial access into an environment with the goal of stealing Intellectual Property (IP) for extortion. LUCR-3 targets Fortune 2000 companies across various sectors, including but not limited to Software, Retail, Hospitality,
https://thehackernews.com/2023/10/lucr-3-scattered-spider-getting-saas-y.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/10/lucr-3-scattered-spider-getting-saas-y.html?utm_source=dlvr.it&utm_medium=blogger
Silent Skimmer: A Year-Long Web Skimming Campaign Targeting Online Payment Businesses
A financially motivated campaign has been targeting online payment businesses in the Asia Pacific, North America, and Latin America with web skimmers for more than a year.
The BlackBerry Research and Intelligence Team is tracking the activity under the name Silent Skimmer, attributing it to an actor who is knowledgeable in the Chinese language. Prominent victims include online businesses and
https://thehackernews.com/2023/10/silent-skimmer-year-long-web-skimming.html?utm_source=dlvr.it&utm_medium=blogger
The BlackBerry Research and Intelligence Team is tracking the activity under the name Silent Skimmer, attributing it to an actor who is knowledgeable in the Chinese language. Prominent victims include online businesses and
https://thehackernews.com/2023/10/silent-skimmer-year-long-web-skimming.html?utm_source=dlvr.it&utm_medium=blogger
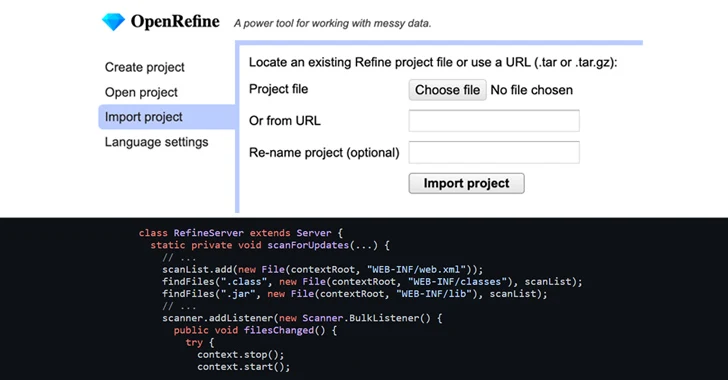
OpenRefine's Zip Slip Vulnerability Could Let Attackers Execute Malicious Code
A high-severity security flaw has been disclosed in the open-source OpenRefine data cleanup and transformation tool that could result in arbitrary code execution on affected systems.
Tracked as CVE-2023-37476 (CVSS score: 7.8), the vulnerability is a Zip Slip vulnerability that could have adverse impacts when importing a specially crafted project in versions 3.7.3 and below.
"Although OpenRefine
https://thehackernews.com/2023/10/openrefines-zip-slip-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
Tracked as CVE-2023-37476 (CVSS score: 7.8), the vulnerability is a Zip Slip vulnerability that could have adverse impacts when importing a specially crafted project in versions 3.7.3 and below.
"Although OpenRefine
https://thehackernews.com/2023/10/openrefines-zip-slip-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
Monday, October 2, 2023
Zanubis Android Banking Trojan Poses as Peruvian Government App to Target Users
An emerging Android banking trojan called Zanubis is now masquerading as a Peruvian government app to trick unsuspecting users into installing the malware.
"Zanubis's main infection path is through impersonating legitimate Peruvian Android applications and then tricking the user into enabling the Accessibility permissions in order to take full control of the device," Kaspersky said in an
https://thehackernews.com/2023/10/zanubis-android-banking-trojan-poses-as.html?utm_source=dlvr.it&utm_medium=blogger
"Zanubis's main infection path is through impersonating legitimate Peruvian Android applications and then tricking the user into enabling the Accessibility permissions in order to take full control of the device," Kaspersky said in an
https://thehackernews.com/2023/10/zanubis-android-banking-trojan-poses-as.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, October 1, 2023
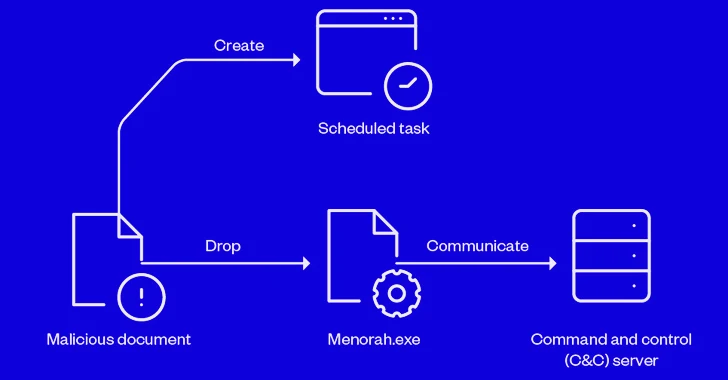
Iranian APT Group OilRig Using New Menorah Malware for Covert Operations
Sophisticated cyber actors backed by Iran known as OilRig have been linked to a spear-phishing campaign that infects victims with a new strain of malware called Menorah.
"The malware was designed for cyberespionage, capable of identifying the machine, reading and uploading files from the machine, and downloading another file or malware," Trend Micro researchers Mohamed Fahmy and Mahmoud Zohdy
https://thehackernews.com/2023/09/iranian-apt-group-oilrig-using-new.html?utm_source=dlvr.it&utm_medium=blogger
"The malware was designed for cyberespionage, capable of identifying the machine, reading and uploading files from the machine, and downloading another file or malware," Trend Micro researchers Mohamed Fahmy and Mahmoud Zohdy
https://thehackernews.com/2023/09/iranian-apt-group-oilrig-using-new.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)