Several reports have indicated data leakage from ChatGPT ever since its release by the Microsoft-backed OpenAI in November 2022. Additionally, threat actors have been abusing the platform to gain unauthorized access or leak sensitive and confidential data. However, ChatGPT has released a new ChatGPT enterprise version, which is claimed to be SOC 2 compliant with […]
The post OpenAI Released ChatGPT Enterprise With SOC 2 Compliant & Data Encryption appeared first on Cyber Security News.
https://cybersecuritynews.com/chatgpt-enterprise-data-encryption/?utm_source=dlvr.it&utm_medium=blogger
Thursday, August 31, 2023
Wednesday, August 30, 2023
Citrix NetScaler Alert: Ransomware Hackers Exploiting Critical Vulnerability
Unpatched Citrix NetScaler systems exposed to the internet are being targeted by unknown threat actors in what's suspected to be a ransomware attack.
Cybersecurity company Sophos is tracking the activity cluster under the moniker STAC4663.
Attack chains involve the exploitation of CVE-2023-3519, a critical code injection vulnerability impacting NetScaler ADC and Gateway servers that could
https://thehackernews.com/2023/08/citrix-netscaler-alert-ransomware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/citrix-netscaler-alert-ransomware.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, August 29, 2023
Kroll Suffers Data Breach as Employee Falls Victim to SIM Swap Hack
A high-profile cyber attack targeted a prominent company, Kroll. This attack utilized a sophisticated technique known as “SIM swapping,” which allowed the threat actor to gain unauthorized access to sensitive personal information. On Saturday, August 19, 2023, Kroll was informed about the SIM swapping attack that targeted a T-Mobile US., Inc. account belonging to a Kroll […]
The post Kroll Suffers Data Breach as Employee Falls Victim to SIM Swap Hack appeared first on Cyber Security News.
https://cybersecuritynews.com/kroll-data-breach-sim-swap-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/kroll-data-breach-sim-swap-attack/?utm_source=dlvr.it&utm_medium=blogger
Monday, August 28, 2023
What true diversity in the cybersecurity industry looks like
In this Help Net Security video, Larry Whiteside, Jr., CISO at RegScale and President of Cyversity, discusses how, now more than ever, the cybersecurity industry needs the diversity of thought to address the increasingly complex and technology-driven challenges organizations face.…
Read more →
The post What true diversity in the cybersecurity industry looks like first appeared on IT Security News.
https://www.itsecuritynews.info/what-true-diversity-in-the-cybersecurity-industry-looks-like/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/what-true-diversity-in-the-cybersecurity-industry-looks-like/?utm_source=dlvr.it&utm_medium=blogger
Sunday, August 27, 2023
Threat and Vulnerability Roundup for the week of August 20th to 26th
Welcome to the Threat and Vulnerability Roundup, a weekly publication from Cyber Writes that provides the most recent news on cybersecurity. Use our wide coverage to stay up to date. Critical flaws, exploits, and recent techniques for attacking have all been highlighted. We also offer the most latest software upgrades to keep your devices safe. […]
The post Threat and Vulnerability Roundup for the week of August 20th to 26th appeared first on Cyber Security News.
https://cybersecuritynews.com/weekly-roundup-august-20th/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/weekly-roundup-august-20th/?utm_source=dlvr.it&utm_medium=blogger
Saturday, August 26, 2023
Urgent FBI Warning: Barracuda Email Gateways Vulnerable Despite Recent Patches
The U.S. Federal Bureau of Investigation (FBI) is warning that Barracuda Networks Email Security Gateway (ESG) appliances patched against a recently disclosed critical flaw continue to be at risk of potential compromise from suspected Chinese hacking groups.
It also deemed the fixes as "ineffective" and that it "continues to observe active intrusions and considers all affected Barracuda ESG
https://thehackernews.com/2023/08/urgent-fbi-warning-barracuda-email.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/urgent-fbi-warning-barracuda-email.html?utm_source=dlvr.it&utm_medium=blogger
Friday, August 25, 2023
Kali Linux 2023.3 Released – What’s New!
Kali Linux is a free and open-source Linux-based operating system that is mainly dedicated to fulfilling two prime criteria:- In short, this OS, Kali Linux, is one of the most advanced Debian-derived Linux distributions that was originally developed and maintained by Offensive Security. Offensive Security recently launched Kali Linux 2023.3 with several new mods, changes, […]
The post Kali Linux 2023.3 Released – What’s New! appeared first on Cyber Security News.
https://cybersecuritynews.com/kali-linux-2023-3/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/kali-linux-2023-3/?utm_source=dlvr.it&utm_medium=blogger
Thursday, August 24, 2023
Over a Dozen Malicious npm Packages Target Roblox Game Developers
More than a dozen malicious packages have been discovered on the npm package repository since the start of August 2023 with capabilities to deploy an open-source information stealer called Luna Token Grabber on systems belonging to Roblox developers.
The ongoing campaign, first detected on August 1 by ReversingLabs, employs modules that masquerade as the legitimate package noblox.js, an API
https://thehackernews.com/2023/08/over-dozen-malicious-npm-packages.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/over-dozen-malicious-npm-packages.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, August 23, 2023
Carderbee Attacks: Hong Kong Organizations Targeted via Malicious Software Updates
A previously undocumented threat cluster has been linked to a software supply chain attack targeting organizations primarily located in Hong Kong and other regions in Asia.
The Symantec Threat Hunter Team, part of Broadcom, is tracking the activity under its insect-themed moniker Carderbee.
The attacks, per the cybersecurity firm, leverage a trojanized version of a legitimate software called
https://thehackernews.com/2023/08/carderbee-attacks-hong-kong.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/carderbee-attacks-hong-kong.html?utm_source=dlvr.it&utm_medium=blogger
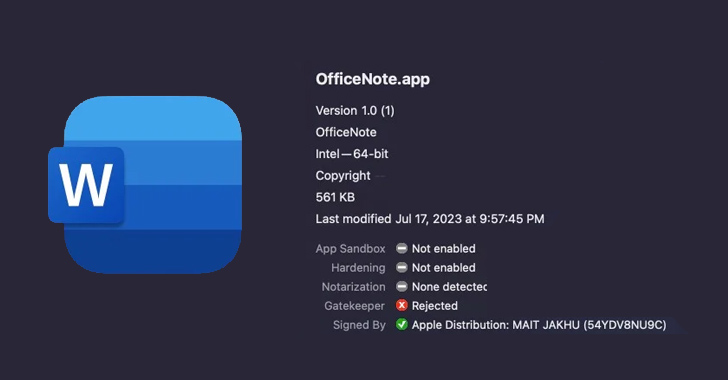
New Variant of XLoader macOS Malware Disguised as 'OfficeNote' Productivity App
A new variant of an Apple macOS malware called XLoader has surfaced in the wild, masquerading its malicious features under the guise of an office productivity app called "OfficeNote."
"The new version of XLoader is bundled inside a standard Apple disk image with the name OfficeNote.dmg," SentinelOne security researchers Dinesh Devadoss and Phil Stokes said in a Monday analysis. "The application
https://thehackernews.com/2023/08/new-variant-of-xloader-macos-malware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/new-variant-of-xloader-macos-malware.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, August 22, 2023
This Malware Turned Thousands of Hacked Windows and macOS PCs into Proxy Servers
Threat actors are leveraging access to malware-infected Windows and macOS machines to deliver a proxy server application and use them as exit nodes to reroute proxy requests.
According to AT&T Alien Labs, the unnamed company that offers the proxy service operates more than 400,000 proxy exit nodes, although it's not immediately clear how many of them were co-opted by malware installed on
https://thehackernews.com/2023/08/this-malware-turned-thousands-of-hacked.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/this-malware-turned-thousands-of-hacked.html?utm_source=dlvr.it&utm_medium=blogger
Monday, August 21, 2023
Top 10 Privileged Users Monitoring Best Practices – 2023
Privileged users typically hold crucial positions within organizations. They usually have elevated access, authority, and permission levels in the organization’s IT systems, networks, applications, and critical data. That’s why they may pose risks to your corporate cybersecurity, and monitoring privileged users is paramount. Moreover, numerous regulations and data security standards, including GDPR, HIPAA, and NIST […]
The post Top 10 Privileged Users Monitoring Best Practices – 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/users-monitoring-best-practices/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/users-monitoring-best-practices/?utm_source=dlvr.it&utm_medium=blogger
HiatusRAT Malware Resurfaces: Taiwan Firms and U.S. Military Under Attack
The threat actors behind the HiatusRAT malware have returned from their hiatus with a new wave of reconnaissance and targeting activity aimed at Taiwan-based organizations and a U.S. military procurement system.
Besides recompiling malware samples for different architectures, the artifacts are said to have been hosted on new virtual private servers (VPSs), Lumen Black Lotus Labs said in a report
https://thehackernews.com/2023/08/hiatusrat-malware-resurfaces-taiwan.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/hiatusrat-malware-resurfaces-taiwan.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, August 20, 2023
China-Linked Bronze Starlight Group Targeting Gambling Sector with Cobalt Strike Beacons
An ongoing cyber attack campaign originating from China is targeting the Southeast Asian gambling sector to deploy Cobalt Strike beacons on compromised systems.
Cybersecurity firm SentinelOne said the tactics, techniques, and procedures point to the involvement of a threat actor tracked as Bronze Starlight (aka Emperor Dragonfly or Storm-0401), which has been linked to the use of short-lived
https://thehackernews.com/2023/08/china-linked-bronze-starlight-group.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/china-linked-bronze-starlight-group.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, August 19, 2023
Patch now! Citrix Sharefile joins the list of actively exploited file sharing software
Categories: Exploits and vulnerabilities Categories: News Tags: Citrix Tags: ShareFile Tags: CVE-2023-24489 Tags: RCE Tags: unauthenticated Tags: vulnerability Tags: PoC Citrix ShareFile can be exploited remotely by unauthenticated attackers. (Read more…) The post Patch now! Citrix Sharefile joins the list…
Read more →
The post Patch now! Citrix Sharefile joins the list of actively exploited file sharing software first appeared on IT Security News.
https://www.itsecuritynews.info/patch-now-citrix-sharefile-joins-the-list-of-actively-exploited-file-sharing-software/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/patch-now-citrix-sharefile-joins-the-list-of-actively-exploited-file-sharing-software/?utm_source=dlvr.it&utm_medium=blogger
Friday, August 18, 2023
A closer look at the new TSA oil and gas pipeline regulations
The TSA has announced updates to its Security Directive (SD) to strengthen the operational resilience of oil and natural gas pipeline owners and operators against cyber-attacks. In this Help Net Security video, Chris Warner, OT Senior Security Consultant at GuidePoint…
Read more →
The post A closer look at the new TSA oil and gas pipeline regulations first appeared on IT Security News.
https://www.itsecuritynews.info/a-closer-look-at-the-new-tsa-oil-and-gas-pipeline-regulations/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/a-closer-look-at-the-new-tsa-oil-and-gas-pipeline-regulations/?utm_source=dlvr.it&utm_medium=blogger
Thursday, August 17, 2023
2000+ Citrix NetScalers Hacked to Deploy Webshell
It has been discovered that an attacker installed web shells on susceptible Citrix NetScalers, exploiting the CVE-2023-3519 flaw to acquire persistent access. This critical zero-day vulnerability poses a significant risk as it can enable remote code execution (RCE) on both NetScaler ADC and NetScaler Gateway. Exploiting this vulnerability, malicious actors have been successful in implanting […]
The post 2000+ Citrix NetScalers Hacked to Deploy Webshell appeared first on Cyber Security News.
https://cybersecuritynews.com/2000-citrix-netscalers-hacked/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/2000-citrix-netscalers-hacked/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, August 16, 2023
Why the “voluntary AI commitments” extracted by the White House are nowhere near enough
Representatives from Amazon, Anthropic, Google, Inflection, Meta, Microsoft, and OpenAI recently convened at the White House for a meeting with President Biden with the stated mission of “ensuring the responsible development and distribution of artificial intelligence (AI) technologies”. The climate…
Read more →
The post Why the “voluntary AI commitments” extracted by the White House are nowhere near enough first appeared on IT Security News.
https://www.itsecuritynews.info/why-the-voluntary-ai-commitments-extracted-by-the-white-house-are-nowhere-near-enough/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/why-the-voluntary-ai-commitments-extracted-by-the-white-house-are-nowhere-near-enough/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, August 15, 2023
Ransomware spreading gangs start Customer Service
In recent times, the landscape of ransomware attacks has evolved, with threat actors altering their strategies. The common practice of encrypting databases and demanding ransoms has given way to a more nuanced approach. As cyber criminals have started adopting a…
Read more →
The post Ransomware spreading gangs start Customer Service first appeared on IT Security News.
https://www.itsecuritynews.info/ransomware-spreading-gangs-start-customer-service/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ransomware-spreading-gangs-start-customer-service/?utm_source=dlvr.it&utm_medium=blogger
Monday, August 14, 2023
India Passes New Digital Personal Data Protection Bill (DPDPB), Putting Users' Privacy First
The Indian President Droupadi Murmu on Friday granted assent to the Digital Personal Data Protection Bill (DPDPB) after it was unanimously passed by both houses of the parliament last week, marking a significant step towards securing people's information.
"The Bill provides for the processing of digital personal data in a manner that recognizes both the rights of the individuals to protect their
https://thehackernews.com/2023/08/india-passes-new-digital-personal-data.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/india-passes-new-digital-personal-data.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, August 13, 2023
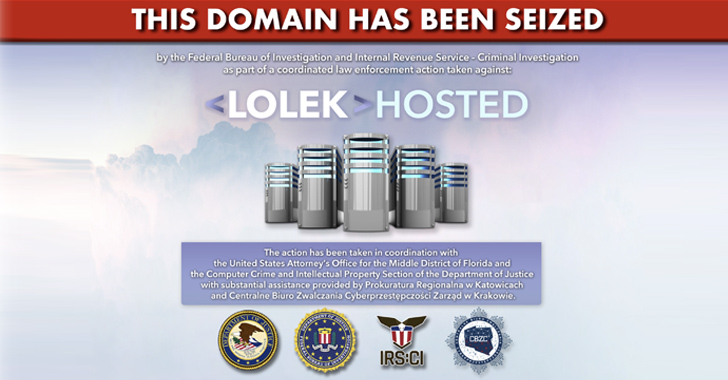
Lolek Bulletproof Hosting Servers Seized, 5 Key Operators Arrested
European and U.S. law enforcement agencies have announced the dismantling of a bulletproof hosting service provider called Lolek Hosted, which cybercriminals have used to launch cyber-attacks across the globe.
"Five of its administrators were arrested, and all of its servers seized, rendering LolekHosted.net no longer available," Europol said in a statement.
"The service facilitated the
https://thehackernews.com/2023/08/lolek-bulletproof-hosting-servers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/lolek-bulletproof-hosting-servers.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, August 12, 2023
New SystemBC Malware Variant Targets Southern African Power Company
An unknown threat actor has been linked to a cyber attack on a power generation company in southern Africa with a new variant of the SystemBC malware called DroxiDat as a precursor to a suspected ransomware attack.
"The proxy-capable backdoor was deployed alongside Cobalt Strike Beacons in a south African nation's critical infrastructure," Kurt Baumgartner, principal security researcher at
https://thehackernews.com/2023/08/new-systembc-malware-variant-targets.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/new-systembc-malware-variant-targets.html?utm_source=dlvr.it&utm_medium=blogger
Friday, August 11, 2023
UK Electoral Commission Hacked – 40 Million Britons Data Exposed
The UK Electoral Commission, entrusted with safeguarding voter information, recently faced a complex breach that triggered a vital public notification. In a digital age, securing sensitive data is paramount, yet even the most robust systems can be vulnerable to cyber-attacks. This article delves into the technical intricacies of the incident, its impact on data subjects, […]
The post UK Electoral Commission Hacked – 40 Million Britons Data Exposed appeared first on Cyber Security News.
https://cybersecuritynews.com/uk-electoral-commission-hacked/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/uk-electoral-commission-hacked/?utm_source=dlvr.it&utm_medium=blogger
Thursday, August 10, 2023
Mind the (Interpretation) gap: Another reason why threat modeling is important
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Where do vulnerabilities fit with respect to security…
Read more →
The post Mind the (Interpretation) gap: Another reason why threat modeling is important first appeared on IT Security News.
https://www.itsecuritynews.info/mind-the-interpretation-gap-another-reason-why-threat-modeling-is-important/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/mind-the-interpretation-gap-another-reason-why-threat-modeling-is-important/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, August 9, 2023
Microsoft Releases Patches for 74 New Vulnerabilities in August Update
Microsoft has patched a total of 74 flaws in its software as part of the company’s Patch Tuesday updates for August 2023, down from the voluminous 132 vulnerabilities the company fixed last month. This comprises six Critical and 67 Important security vulnerabilities.…
Read more →
The post Microsoft Releases Patches for 74 New Vulnerabilities in August Update first appeared on IT Security News.
https://www.itsecuritynews.info/microsoft-releases-patches-for-74-new-vulnerabilities-in-august-update/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/microsoft-releases-patches-for-74-new-vulnerabilities-in-august-update/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, August 8, 2023
Exploitation of Artificial Intelligence AI technology to facilitate password theft
In recent times, hackers have traditionally targeted databases to initiate cyber attacks, aiming to pilfer critical credentials like account passwords. However, a recent study proposes a new angle: the exploitation of Artificial Intelligence (AI) technology to facilitate password theft. A…
Read more →
The post Exploitation of Artificial Intelligence AI technology to facilitate password theft first appeared on IT Security News.
https://www.itsecuritynews.info/exploitation-of-artificial-intelligence-ai-technology-to-facilitate-password-theft/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/exploitation-of-artificial-intelligence-ai-technology-to-facilitate-password-theft/?utm_source=dlvr.it&utm_medium=blogger
Monday, August 7, 2023
Ransomware attack targets 3 hospitals in the United States
Last week, three hospitals affiliated with Prospect Medical Holdings, situated in different states across the United States, fell victim to a cyber attack, believed to be a ransomware variant. The attack occurred on Wednesday and was discovered in the early…
Read more →
The post Ransomware attack targets 3 hospitals in the United States first appeared on IT Security News.
https://www.itsecuritynews.info/ransomware-attack-targets-3-hospitals-in-the-united-states/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ransomware-attack-targets-3-hospitals-in-the-united-states/?utm_source=dlvr.it&utm_medium=blogger
Sunday, August 6, 2023
Threat and Vulnerability Roundup for the week of July 30th to August 5th
The Threat and Vulnerability Roundup for this week is out! With great pride, Cyber Writes presents a weekly overview of the most recent cybersecurity news. We highlight notable vulnerabilities and exploits, new attack tactics, and critical software patches. Both individuals and organizations can determine the criticality of an asset, its vulnerabilities, and the mitigation measures […]
The post Threat and Vulnerability Roundup for the week of July 30th to August 5th appeared first on Cyber Security News.
https://cybersecuritynews.com/threat-and-vulnerability-roundup-weekly/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/threat-and-vulnerability-roundup-weekly/?utm_source=dlvr.it&utm_medium=blogger
Saturday, August 5, 2023
The end looms for Meta’s behavioural advertising in Europe
Categories: Personal Tags: meta Tags: Facebook Tags: EU Tags: legal Tags: litigation Tags: behavioural Tags: advertising Tags: tracking We take a look at what appears to be the beginning of the end for Meta’s behavioural advertising in Europe. (Read more…)…
Read more →
The post The end looms for Meta’s behavioural advertising in Europe first appeared on IT Security News.
https://www.itsecuritynews.info/the-end-looms-for-metas-behavioural-advertising-in-europe/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-end-looms-for-metas-behavioural-advertising-in-europe/?utm_source=dlvr.it&utm_medium=blogger
Friday, August 4, 2023
Microsoft Flags Growing Cybersecurity Concerns for Major Sporting Events
Microsoft is warning of the threat malicious cyber actors pose to stadium operations, warning that the cyber risk surface of live sporting events is "rapidly expanding."
"Information on athletic performance, competitive advantage, and personal information is a lucrative target," the company said in a Cyber Signals report shared with The Hacker News. "Sports teams, major league and global
https://thehackernews.com/2023/08/microsoft-flags-growing-cybersecurity.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/microsoft-flags-growing-cybersecurity.html?utm_source=dlvr.it&utm_medium=blogger
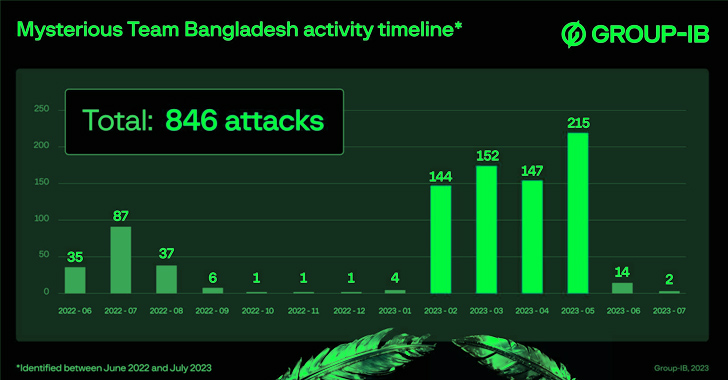
"Mysterious Team Bangladesh" Targeting India with DDoS Attacks and Data Breaches
A hacktivist group known as Mysterious Team Bangladesh has been linked to over 750 distributed denial-of-service (DDoS) attacks and 78 website defacements since June 2022.
"The group most frequently attacks logistics, government, and financial sector organizations in India and Israel," Singapore-headquartered cybersecurity firm Group-IB said in a report shared with The Hacker News. "The group is
https://thehackernews.com/2023/08/mysterious-team-bangladesh-targeting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/mysterious-team-bangladesh-targeting.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, August 3, 2023
Iranian Company Cloudzy Accused of Aiding Cybercriminals and Nation-State Hackers
Services offered by an obscure Iranian company known as Cloudzy are being leveraged by multiple threat actors, including cybercrime groups and nation-state crews.
"Although Cloudzy is incorporated in the United States, it almost certainly operates out of Tehran, Iran – in possible violation of U.S. sanctions – under the direction of someone going by the name Hassan Nozari," Halcyon said in a new
https://thehackernews.com/2023/08/iranian-company-cloudzy-accused-of.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/08/iranian-company-cloudzy-accused-of.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, August 2, 2023
Splunk SOAR Unauthenticated Log Injection Let attackers Execute Malicious Code
Splunk has discovered a vulnerability that allows unauthenticated log injection, which could enable malicious actors to run harmful code on the system. Splunk SOAR (Security Orchestration, Automation, and Response) is an application that can be used to automate repetitive tasks and respond to security incidents rapidly, which leads to higher productivity. It can also be […]
The post Splunk SOAR Unauthenticated Log Injection Let attackers Execute Malicious Code appeared first on Cyber Security News.
https://cybersecuritynews.com/splunk-soar-log-injection/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/splunk-soar-log-injection/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, August 1, 2023
Multiple Flaws Found in Ninja Forms Plugin Leave 800,000 Sites Vulnerable
Multiple security vulnerabilities have been disclosed in the Ninja Forms plugin for WordPress that could be exploited by threat actors to escalate privileges and steal sensitive data.
The flaws, tracked as CVE-2023-37979, CVE-2023-38386, and CVE-2023-38393, impact versions 3.6.25 and below, Patchstack said in a report last week. Ninja Forms is installed on over 800,000 sites.
A brief description
https://thehackernews.com/2023/07/multiple-flaws-found-in-ninja-forms.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/multiple-flaws-found-in-ninja-forms.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)















-1.webp)