Open source refers to software or technology that is made available to the public with its source code openly accessible, editable, and distributable. In other words, the source code contains the underlying programming instructions and is freely available for anyone…
Read more →
The post Open-source security challenges and complexities first appeared on IT Security News.
https://www.itsecuritynews.info/open-source-security-challenges-and-complexities/?utm_source=dlvr.it&utm_medium=blogger
Monday, July 31, 2023
20 Best Malware Protection Solutions in 2023
Malware protection solutions are combined of Antivirus Software, Endpoint Protection Platforms (EPP), Anti-Malware Software, Next-Generation Antivirus (NGAV), Internet Security Suites, Network-based Malware Protection, and Browser Extensions to defend against the cyber threats that target individuals and companies worldwide. It describes a variety of dangerous software designed to penetrate computer systems, interfere with operations, steal confidential […]
The post 20 Best Malware Protection Solutions in 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/best-malware-protection-solutions/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/best-malware-protection-solutions/?utm_source=dlvr.it&utm_medium=blogger
Sunday, July 30, 2023
New Android Malware CherryBlos Utilizing OCR to Steal Sensitive Data
A new Android malware strain called CherryBlos has been observed making use of optical character recognition (OCR) techniques to gather sensitive data stored in pictures.
CherryBlos, per Trend Micro, is distributed via bogus posts on social media platforms and comes with capabilities to steal cryptocurrency wallet-related credentials and act as a clipper to substitute wallet addresses when a
https://thehackernews.com/2023/07/new-android-malware-cherryblos.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/new-android-malware-cherryblos.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, July 29, 2023
Hackers Exploit Windows Search Feature to Execute Malware on Infected Systems
Malware authors persistently seek novel approaches to exploit unsuspecting users in the active cyber threat landscape. To easily locate all the available files, folders, and other items on your Windows system, Microsoft Windows OS offers an outstanding powerful tool known as the Windows search feature. Unexplored by many, the “search-ms” URI protocol handler in Windows […]
The post Hackers Exploit Windows Search Feature to Execute Malware on Infected Systems appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-exploit-windows-search/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-exploit-windows-search/?utm_source=dlvr.it&utm_medium=blogger
Friday, July 28, 2023
Over 60% of AWS Environments Exposed to Zenbleed Attacks
AMD Zenbleed 2 processors were found vulnerable to use-after-free flaws, enabling data theft. While the exploitation of this flaw demands local code execution, less likely in cloud setups. The Zenbleed vulnerability that is documented recently puts more than 60 percent of AWS environments at risk, impacting AMD Zen 2 processors. Cybersecurity researchers at Wiz, a […]
The post Over 60% of AWS Environments Exposed to Zenbleed Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/aws-zenbleed-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/aws-zenbleed-attacks/?utm_source=dlvr.it&utm_medium=blogger
Thursday, July 27, 2023
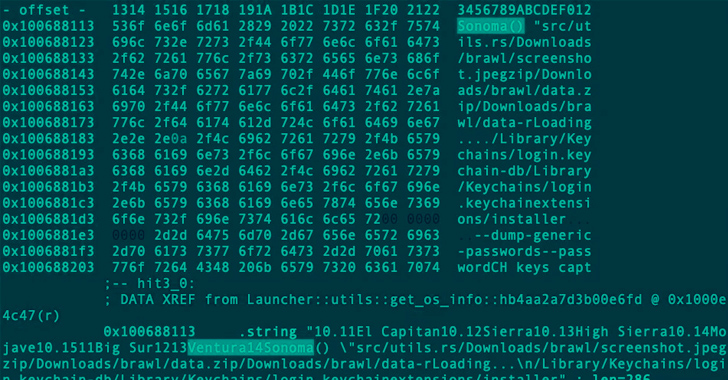
Rust-based Realst Infostealer Targeting Apple macOS Users' Cryptocurrency Wallets
A new malware family called Realst has become the latest to target Apple macOS systems, with a third of the samples already designed to infect macOS 14 Sonoma, the upcoming major release of the operating system.
Written in the Rust programming language, the malware is distributed in the form of bogus blockchain games and is capable of "emptying crypto wallets and stealing stored password and
https://thehackernews.com/2023/07/rust-based-realst-infostealer-targeting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/rust-based-realst-infostealer-targeting.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, July 26, 2023
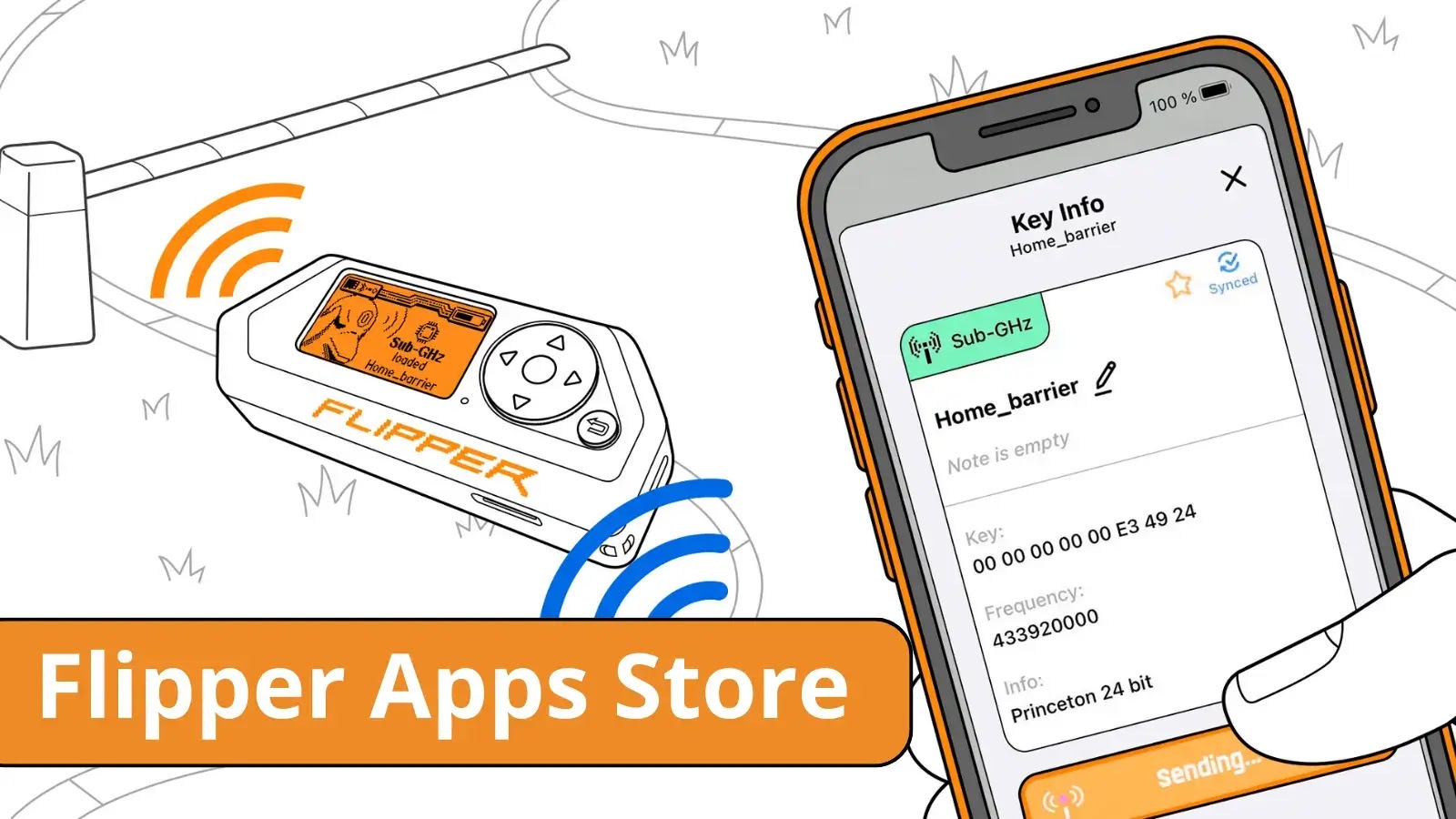
Flipper Zero – Now You Install 3rd-Party Apps With The Penetrating Testing Device
The Flipper Zero team has announced the official launch of “Flipper Apps,” a new app store enabling mobile users to download third-party apps and expand the capabilities of the well-known wireless pen-testing tool. Flipper Zero is a little, toy-like multi-tool with the inquisitive viewpoint of a cyber-dolphin. It integrates all the hardware resources required for mobile […]
The post Flipper Zero – Now You Install 3rd-Party Apps With The Penetrating Testing Device appeared first on Cyber Security News.
https://cybersecuritynews.com/flipper-flipper-apps/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/flipper-flipper-apps/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, July 25, 2023
Akira and BlackByte ransomware group claim attack on Yamaha Music Canada
Yamaha Music of Canada that produces musical equipment and is different from Japanese Automobile maker Yamaha Motor Co has issued a statement that its servers were compromised and some of its data was accessed and stolen by hackers. The company…
Read more →
The post Akira and BlackByte ransomware group claim attack on Yamaha Music Canada first appeared on IT Security News.
https://www.itsecuritynews.info/akira-and-blackbyte-ransomware-group-claim-attack-on-yamaha-music-canada/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/akira-and-blackbyte-ransomware-group-claim-attack-on-yamaha-music-canada/?utm_source=dlvr.it&utm_medium=blogger
Apple Rolls Out Urgent Patches for Zero-Day Flaws Impacting iPhones, iPads and Macs
Apple has rolled out security updates to iOS, iPadOS, macOS, tvOS, watchOS, and Safari to address several security vulnerabilities, including one actively exploited zero-day bug in the wild. Tracked as CVE-2023-38606, the shortcoming resides in the kernel and permits a malicious app to…
Read more →
The post Apple Rolls Out Urgent Patches for Zero-Day Flaws Impacting iPhones, iPads and Macs first appeared on IT Security News.
https://www.itsecuritynews.info/apple-rolls-out-urgent-patches-for-zero-day-flaws-impacting-iphones-ipads-and-macs/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-rolls-out-urgent-patches-for-zero-day-flaws-impacting-iphones-ipads-and-macs/?utm_source=dlvr.it&utm_medium=blogger
Monday, July 24, 2023
Weekly Vulnerability Roundup: A Compiled List of Vulnerabilities and Exploits
Each week, Cyberwrites publishes a summary of cybersecurity news that compiles important vulnerabilities and exploits that may have gone unnoticed. Our weekly vulnerability roundup will provide coverage of newly discovered vulnerabilities, as well as those exploited to compromise organizations. Weekly Vulnerability Roundup Cisco Cisco has published a security advisory that states that they have discovered […]
The post Weekly Vulnerability Roundup: A Compiled List of Vulnerabilities and Exploits appeared first on Cyber Security News.
https://cybersecuritynews.com/weekly-vulnerability-roundup/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/weekly-vulnerability-roundup/?utm_source=dlvr.it&utm_medium=blogger
Sunday, July 23, 2023
ChatGPT for Digital Forensic – AI-Powered Cybercrime Investigation
OpenAI’s ChatGPT (GPT-3.5, GPT-4) and other LLMs like BERT, Bard, etc. have sparked widespread debate due to their disruptive applications across various fields. These LLM modules generate answers and solutions promptly based on comprehensive text-based training data and rapidly growing interest in the scientific community and society. Cybersecurity researchers from several universities recently published an […]
The post ChatGPT for Digital Forensic – AI-Powered Cybercrime Investigation appeared first on Cyber Security News.
https://cybersecuritynews.com/chatgpt-for-digital-forensic/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/chatgpt-for-digital-forensic/?utm_source=dlvr.it&utm_medium=blogger
Saturday, July 22, 2023
CISA: You’ve got two weeks to patch Citrix NetScaler vulnerability CVE-2023-3519
Categories: Exploits and vulnerabilities Categories: News Tags: Citrix Tags: NetScaler Tags: CVE-2023-3519 Tags: web shell A critical unauthenticated remote code execution vulnerability in Citrix NetScaler ADC and Citrix NetScaler Gateway is being actively exploited (Read more…) The post CISA: You’ve…
Read more →
The post CISA: You’ve got two weeks to patch Citrix NetScaler vulnerability CVE-2023-3519 first appeared on IT Security News.
https://www.itsecuritynews.info/cisa-youve-got-two-weeks-to-patch-citrix-netscaler-vulnerability-cve-2023-3519/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cisa-youve-got-two-weeks-to-patch-citrix-netscaler-vulnerability-cve-2023-3519/?utm_source=dlvr.it&utm_medium=blogger
Friday, July 21, 2023
Chrome 115 Update for Windows, MacOS, and Linux – 20 Vulnerabilities Patched
Google released Chrome 115 to the stable channel for Windows, MacOS, and Linux on Tuesday, patching 20 vulnerabilities, including 11 that were discovered by external researchers. Four security issues were assessed to be of “high severity,” while six were determined to be of “medium severity.” This browser update also fixes a ‘low-severity’ issue with Themes’ insufficient […]
The post Chrome 115 Update for Windows, MacOS, and Linux – 20 Vulnerabilities Patched appeared first on Cyber Security News.
https://cybersecuritynews.com/chrome-115-update/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/chrome-115-update/?utm_source=dlvr.it&utm_medium=blogger
Thursday, July 20, 2023
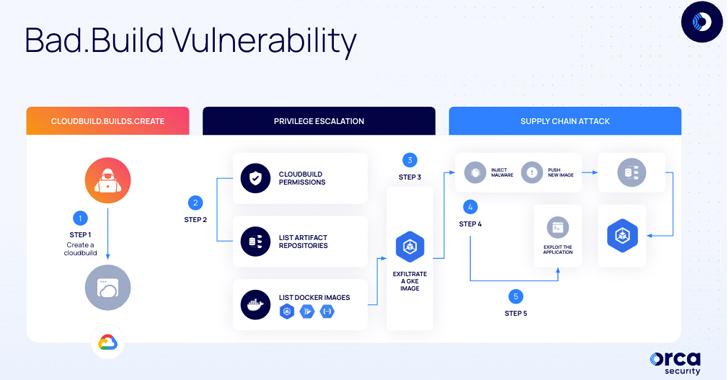
Bad.Build Flaw in Google Cloud Build Raises Concerns of Privilege Escalation
Cybersecurity researchers have uncovered a privilege escalation vulnerability in Google Cloud that could enable malicious actors tamper with application images and infect users, leading to supply chain attacks.
The issue, dubbed Bad.Build, is rooted in the Google Cloud Build service, according to cloud security firm Orca, which discovered and reported the issue.
"By abusing the flaw and enabling
https://thehackernews.com/2023/07/badbuild-flaw-in-google-cloud-build.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/badbuild-flaw-in-google-cloud-build.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, July 19, 2023
FIN8 Group Using Modified Sardonic Backdoor for BlackCat Ransomware Attacks
The financially motivated threat actor known as FIN8 has been observed using a "revamped" version of a backdoor called Sardonic to deliver the BlackCat ransomware.
According to the Symantec Threat Hunter Team, part of Broadcom, the development is an attempt on the part of the e-crime group to diversify its focus and maximize profits from infected entities. The intrusion attempt took place in
https://thehackernews.com/2023/07/fin8-group-using-modified-sardonic.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/fin8-group-using-modified-sardonic.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, July 18, 2023
ChatGPT For Penetration Testing – An Effective Reconnaissance Phase of Pentest
ChatGPT enhances information security by providing valuable insights for efficient reconnaissance in penetration testing and serving as an additional source of security information. Generative pre-trained transformer language models are growing rapidly with unseen and shocking capabilities. Recently GBHackers on Security Published an article about PentestGPT, a new ChatGPT-powered Penetration testing Tool that helps penetration testers […]
The post ChatGPT For Penetration Testing – An Effective Reconnaissance Phase of Pentest appeared first on Cyber Security News.
https://cybersecuritynews.com/chatgpt-for-penetration-testing/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/chatgpt-for-penetration-testing/?utm_source=dlvr.it&utm_medium=blogger
Monday, July 17, 2023
Top 10 Best Cyber Attack Simulation Tools – 2023
Cyberattack is not at all a distant threat. Any organization can be its target. This type of cyber attack simulation is a method of computer security testing. These identify the vulnerabilities and attack the technique that the malicious actors use. The Cyber Attack Simulation tools act like a continuous and automated process where it gets […]
The post Top 10 Best Cyber Attack Simulation Tools – 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/cyber-attack-simulation-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cyber-attack-simulation-tools/?utm_source=dlvr.it&utm_medium=blogger
Sunday, July 16, 2023
Microsoft Bug Allowed Hackers to Breach Over Two Dozen Organizations via Forged Azure AD Tokens
Microsoft on Friday said a validation error in its source code allowed for Azure Active Directory (Azure AD) tokens to be forged by a malicious actor known as Storm-0558 using a Microsoft account (MSA) consumer signing key to breach two dozen organizations.
"Storm-0558 acquired an inactive MSA consumer signing key and used it to forge authentication tokens for Azure AD enterprise and MSA
https://thehackernews.com/2023/07/microsoft-bug-allowed-hackers-to-breach.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/microsoft-bug-allowed-hackers-to-breach.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, July 15, 2023
Golang vulnerability checker flags Go vulnerabilities
Govulncheck, a command-line tool to help users of Google’s Go programming language find known vulnerabilities in project dependencies, has reached 1.0.0 status, the Go security team said. Unveiled July 13, Govulncheck can analyze both binaries and source code. It reduces…
Read more →
The post Golang vulnerability checker flags Go vulnerabilities first appeared on IT Security News.
https://www.itsecuritynews.info/golang-vulnerability-checker-flags-go-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/golang-vulnerability-checker-flags-go-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
Friday, July 14, 2023
Rockwell Automation ControlLogix Bugs Expose Industrial Systems to Remote Attacks
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has alerted of two security flaws impacting Rockwell Automation ControlLogix EtherNet/IP (ENIP) communication module models that could be exploited to achieve remote code execution and denial-of-service (DoS).
"The results and impact of exploiting these vulnerabilities vary depending on the ControlLogix system configuration, but
https://thehackernews.com/2023/07/rockwell-automation-controllogix-bugs.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/rockwell-automation-controllogix-bugs.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, July 13, 2023
Hackers Leverage USB Flash Drives to Attack Public and Private Sectors Globally
During the initial half of 2023, a notable surge occurred in attacks exploiting infected USB drives for secret theft. While the USB-based operation campaigns caused most incidents, impacting both public and private sectors worldwide. Cybersecurity analysts at Mandiant Managed Defense…
Read more →
The post Hackers Leverage USB Flash Drives to Attack Public and Private Sectors Globally first appeared on IT Security News.
https://www.itsecuritynews.info/hackers-leverage-usb-flash-drives-to-attack-public-and-private-sectors-globally/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hackers-leverage-usb-flash-drives-to-attack-public-and-private-sectors-globally/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, July 12, 2023
What is the Role Of Red Teaming In Cyber Security ?
Testing your organization’s capacity to stop, identify, and respond to assaults is essential since cyber threats are developing at an unprecedented rate. Red teaming is the practice of breaking into safe systems or data while posing as a hostile actor to evaluate the security of an organization’s systems. Red teams, which are created to hack […]
The post What is the Role Of Red Teaming In Cyber Security ? appeared first on Cyber Security News.
https://cybersecuritynews.com/red-teaming-in-cyber-security/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/red-teaming-in-cyber-security/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, July 11, 2023
Revolut Faces $20 Million Loss as Attackers Exploit Payment System Weakness
Malicious actors exploited an unknown flaw in Revolut's payment systems to steal more than $20 million of the company's funds in early 2022.
The development was reported by the Financial Times, citing multiple unnamed sources with knowledge of the incident. The breach has not been disclosed publicly.
The fault stemmed from discrepancies between Revolut's U.S. and European systems, causing funds
https://thehackernews.com/2023/07/hackers-steal-20-million-by-exploiting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/hackers-steal-20-million-by-exploiting.html?utm_source=dlvr.it&utm_medium=blogger
Monday, July 10, 2023
How to Use Log Management to Retrace Your Digital Footsteps
Log management tools help IT and security teams monitor and improve a system’s performance by identifying bugs, cybersecurity breaches, and other issues that can create outages or compliance problems. This article has been indexed from Dark Reading Read the original…
Read more →
The post How to Use Log Management to Retrace Your Digital Footsteps first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-use-log-management-to-retrace-your-digital-footsteps/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-to-use-log-management-to-retrace-your-digital-footsteps/?utm_source=dlvr.it&utm_medium=blogger
Sunday, July 9, 2023
Cybersecurity Agencies Sound Alarm on Rising TrueBot Malware Attacks
Cybersecurity agencies have warned about the emergence of new variants of the TrueBot malware. This enhanced threat is now targeting companies in the U.S. and Canada with the intention of extracting confidential data from infiltrated systems.
These sophisticated attacks exploit a critical vulnerability (CVE-2022-31199) in the widely used Netwrix Auditor server and its associated agents.
This
https://thehackernews.com/2023/07/cybersecurity-agencies-sound-alarm-on.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/cybersecurity-agencies-sound-alarm-on.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, July 8, 2023
Beware of New Phishing Attacks Mimicking Booking.com and Airbnb
Beware of attackers masquerading as well-known vacation rental websites such as Airbnb and Booking.com. Scammers that prey on tourists for Phishing Attacks are more active once the summer travel season is in full force. It is recommended to double-check the website URL before entering any credentials on it to prevent being the victim of such […]
The post Beware of New Phishing Attacks Mimicking Booking.com and Airbnb appeared first on Cyber Security News.
https://cybersecuritynews.com/phishing-target-tourists/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/phishing-target-tourists/?utm_source=dlvr.it&utm_medium=blogger
Friday, July 7, 2023
INTERPOL Nabs Hacking Crew OPERA1ER's Leader Behind $11 Million Cybercrime
A suspected senior member of a French-speaking hacking crew known as OPERA1ER has been arrested as part of an international law enforcement operation codenamed Nervone, Interpol has announced.
"The group is believed to have stolen an estimated USD 11 million -- potentially as much as 30 million -- in more than 30 attacks across 15 countries in Africa, Asia, and Latin America," the agency said.
https://thehackernews.com/2023/07/interpol-nabs-hacking-crew-opera1ers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/interpol-nabs-hacking-crew-opera1ers.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, July 6, 2023
Google Authenticator – what is it and why should you use it?
An introduction to the Google Authenticator app, a clever way to protect your online accounts with multi-factor authentication. The post Google Authenticator – what is it and why should you use it? appeared first on Panda Security Mediacenter. This article…
Read more →
The post Google Authenticator – what is it and why should you use it? first appeared on IT Security News.
https://www.itsecuritynews.info/google-authenticator-what-is-it-and-why-should-you-use-it/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/google-authenticator-what-is-it-and-why-should-you-use-it/?utm_source=dlvr.it&utm_medium=blogger
TeamsPhisher Tool Exploits Microsoft Teams Flaw to Send Malware to Users
US Navy, one of the red team members, recently released “TeamsPhisher,” a tool that exploits the Microsoft Teams’ security flaw that is not fixed to bypass the incoming file restrictions from external tenants. This new tool allows attackers to deliver…
Read more →
The post TeamsPhisher Tool Exploits Microsoft Teams Flaw to Send Malware to Users first appeared on IT Security News.
https://www.itsecuritynews.info/teamsphisher-tool-exploits-microsoft-teams-flaw-to-send-malware-to-users/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/teamsphisher-tool-exploits-microsoft-teams-flaw-to-send-malware-to-users/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, July 5, 2023
Neo_Net Hackers Group Targeting Users of Prominent Banks Globally
A Spanish-based threat actor Neo_Net has conducted campaigns against financial institutions and banks and achieved the highest success rate in spite of its unsophisticated tools. The campaign has compromised a significant amount of Personally Identifiable Information (PII), including telephone numbers, national identity numbers, and names of thousands of victims. Neo_Net has established and rented out […]
The post Neo_Net Hackers Group Targeting Users of Prominent Banks Globally appeared first on Cyber Security News.
https://cybersecuritynews.com/neo_net-targeting-bank-users/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/neo_net-targeting-bank-users/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, July 4, 2023
Evasive Meduza Stealer Targets 19 Password Managers and 76 Crypto Wallets
In yet another sign of a lucrative crimeware-as-a-service (CaaS) ecosystem, cybersecurity researchers have discovered a new Windows-based information stealer called Meduza Stealer that's actively being developed by its author to evade detection by software solutions.
"The Meduza Stealer has a singular objective: comprehensive data theft," Uptycs said in a new report. "It pilfers users' browsing
https://thehackernews.com/2023/07/evasive-meduza-stealer-targets-19.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/evasive-meduza-stealer-targets-19.html?utm_source=dlvr.it&utm_medium=blogger
Monday, July 3, 2023
BlackCat Operators Distributing Ransomware Disguised as WinSCP via Malvertising
Threat actors associated with the BlackCat ransomware have been observed employing malvertising tricks to distribute rogue installers of the WinSCP file transfer application.
"Malicious actors used malvertising to distribute a piece of malware via cloned webpages of legitimate organizations," Trend Micro researchers said in an analysis published last week. "In this case, the distribution
https://thehackernews.com/2023/07/blackcat-operators-distributing.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/07/blackcat-operators-distributing.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, July 2, 2023
The High School Changed Every Student’s Password to ‘Ch@ngeme!’
In an attempt to reset the student’s passwords after a mistake in a cybersecurity audit, the Oak Park and River Forest (OPRF) High School reset all the students’ passwords to ‘Ch@ngeme!’ During a cybersecurity audit on the school’s systems, an unexpected vendor error resettled all the students’ passwords that prevented all the 3000+ students from […]
The post The High School Changed Every Student’s Password to ‘Ch@ngeme!’ appeared first on Cyber Security News.
https://cybersecuritynews.com/school-changed-students-password/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/school-changed-students-password/?utm_source=dlvr.it&utm_medium=blogger
Saturday, July 1, 2023
Top 10 Best AWS Security Tools – 2023
To store the data with high standard security, there several AWS security tools are available to manage, scan, and audit the data that’s been stored. AWS is nothing but Amazon Web Services, which is undoubtedly revolutionary and implemented by millions of businesses around the world to store and manage data. It has the ability to […]
The post Top 10 Best AWS Security Tools – 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/aws-security-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/aws-security-tools/?utm_source=dlvr.it&utm_medium=blogger
University of Manchester Hack – Over One Million NHS patient data Exposed
It has come to light that the University of Manchester fell victim to a Ransomware Hack, which resulted in the breach of 1.1 million NHS patients’ information from 200 hospitals. This event has caused great concern and raised important questions about data security. Ransomware is malicious software (malware) designed to lock devices and prevent users […]
The post University of Manchester Hack – Over One Million NHS patient data Exposed appeared first on Cyber Security News.
https://cybersecuritynews.com/nhs-patient-data-exposed/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/nhs-patient-data-exposed/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)