A critical security flaw has been disclosed in miniOrange's Social Login and Register plugin for WordPress that could enable a malicious actor to log in as any user-provided information about email address is already known.
Tracked as CVE-2023-2982 (CVSS score: 9.8), the authentication bypass flaw impacts all versions of the plugin, including and prior to 7.6.4. It was addressed on June 14, 2023
https://thehackernews.com/2023/06/critical-security-flaw-in-social-login.html?utm_source=dlvr.it&utm_medium=blogger
Friday, June 30, 2023
Thursday, June 29, 2023
Critical SQL Injection Flaws Expose Gentoo Soko to Remote Code Execution
Multiple SQL injection vulnerabilities have been disclosed in Gentoo Soko that could lead to remote code execution (RCE) on vulnerable systems.
"These SQL injections happened despite the use of an Object-Relational Mapping (ORM) library and prepared statements," SonarSource researcher Thomas Chauchefoin said, adding they could result in RCE on Soko because of a "misconfiguration of the database.
https://thehackernews.com/2023/06/critical-sql-injection-flaws-expose.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/critical-sql-injection-flaws-expose.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, June 28, 2023
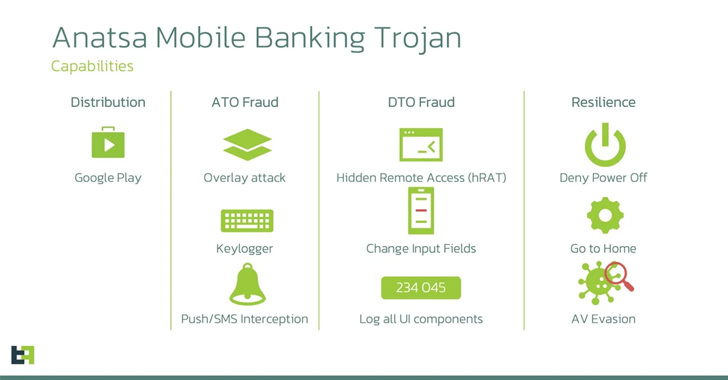
Anatsa Banking Trojan Targeting Users in US, UK, Germany, Austria, and Switzerland
A new Android malware campaign has been observed pushing the Anatsa banking trojan to target banking customers in the U.S., U.K., Germany, Austria, and Switzerland since the start of March 2023.
"The actors behind Anatsa aim to steal credentials used to authorize customers in mobile banking applications and perform Device-Takeover Fraud (DTO) to initiate fraudulent transactions," ThreatFabric
https://thehackernews.com/2023/06/anatsa-banking-trojan-targeting-users.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/anatsa-banking-trojan-targeting-users.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, June 27, 2023
Microsoft Warns of Widescale Credential Stealing Attacks by Russian Hackers
Microsoft has disclosed that it's detected a spike in credential-stealing attacks conducted by the Russian state-affiliated hacker group known as Midnight Blizzard.
The intrusions, which made use of residential proxy services to obfuscate the source IP address of the attacks, target governments, IT service providers, NGOs, defense, and critical manufacturing sectors, the tech giant's threat
https://thehackernews.com/2023/06/microsoft-warns-of-widescale-credential.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/microsoft-warns-of-widescale-credential.html?utm_source=dlvr.it&utm_medium=blogger
Monday, June 26, 2023
Chinese Hackers Using Never-Before-Seen Tactics for Critical Infrastructure Attacks
The newly discovered Chinese nation-state actor known as Volt Typhoon has been observed to be active in the wild since at least mid-2020, with the hacking crew linked to never-before-seen tradecraft to retain remote access to targets of interest.
The findings come from CrowdStrike, which is tracking the adversary under the name Vanguard Panda.
"The adversary consistently employed ManageEngine
https://thehackernews.com/2023/06/chinese-hackers-using-never-before-seen.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/chinese-hackers-using-never-before-seen.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, June 25, 2023
Twitter Hacker Sentenced to 5 Years in Prison for $120,000 Crypto Scam
A U.K. citizen who took part in the massive July 2020 hack of Twitter has been sentenced to five years in prison in the U.S.
Joseph James O'Connor (aka PlugwalkJoe), 24, was awarded the sentence on Friday in the Southern District of New York, a little over a month after he pleaded guilty to the criminal schemes. He was arrested in Spain in July 2021.
The infamous Twitter breach allowed the
https://thehackernews.com/2023/06/twitter-hacker-sentenced-to-5-years-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/twitter-hacker-sentenced-to-5-years-in.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, June 24, 2023
New Cryptocurrency Mining Campaign Targets Linux Systems and IoT Devices
Internet-facing Linux systems and Internet of Things (IoT) devices are being targeted as part of a new campaign designed to illicitly mine cryptocurrency.
"The threat actors behind the attack use a backdoor that deploys a wide array of tools and components such as rootkits and an IRC bot to steal device resources for mining operations," Microsoft threat intelligence researcher Rotem Sde-Or said.
https://thehackernews.com/2023/06/new-cryptocurrency-mining-campaign.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/new-cryptocurrency-mining-campaign.html?utm_source=dlvr.it&utm_medium=blogger
Friday, June 23, 2023
Startup Security Tactics: Friction Surveys
When we do quarterly planning, my team categorizes our goals within four evergreen outcomes:
Reduce the risk of information security incidents
Increase trust in Vanta's information security program
Reduce the friction caused by information security controls
Use security expertise to support the business
In this article, I'm going to focus on number three: reducing friction.
Declaring your
https://thehackernews.com/2023/06/startup-security-tactics-friction.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/startup-security-tactics-friction.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, June 22, 2023
Hackers Use Weaponized PDF Files to Attack Manufacturing, and Healthcare Organizations
Recently, eSentire TRU (Threat Response Unit) reported that since November 2022, it had observed the resurrection of a malicious campaign that Hackers Attack on targets explicitly the following organizations:- While cybersecurity researchers acknowledge that the campaign is being carried out by threat actors who are native Russian speakers. In this analysis, experts mainly focus on […]
The post Hackers Use Weaponized PDF Files to Attack Manufacturing, and Healthcare Organizations appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-use-weaponized-pdf-files-to-attack-organizations/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-use-weaponized-pdf-files-to-attack-organizations/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, June 21, 2023
ASUS Releases Patches to Fix Critical Security Bugs Impacting Multiple Router Models
Taiwanese company ASUS on Monday released firmware updates to address, among other issues, nine security bugs impacting a wide range of router models.
Of the nine security flaws, two are rated Critical and six are rated High in severity. One vulnerability is currently awaiting analysis.
The list of impacted products are GT6, GT-AXE16000, GT-AX11000 PRO, GT-AXE11000, GT-AX6000, GT-AX11000,
https://thehackernews.com/2023/06/asus-releases-patches-to-fix-critical.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/asus-releases-patches-to-fix-critical.html?utm_source=dlvr.it&utm_medium=blogger
Over 100,000 Stolen ChatGPT Account Credentials Sold on Dark Web Marketplaces
Over 101,100 compromised OpenAI ChatGPT account credentials have found their way on illicit dark web marketplaces between June 2022 and May 2023, with India alone accounting for 12,632 stolen credentials.
The credentials were discovered within information stealer logs made available for sale on the cybercrime underground, Group-IB said in a report shared with The Hacker News.
"The number of
https://thehackernews.com/2023/06/over-100000-stolen-chatgpt-account.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/over-100000-stolen-chatgpt-account.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, June 20, 2023
Reddit Hackers Threaten to Leak 80GB of Stolen Data
The February 5th intrusion on Reddit was allegedly carried out by the ALPHV ransomware operation, also known as BlackCat. Threat actors gained Reddit’s systems through this phishing attempt to obtain internal documents, source code, employee data, and some information about the company’s advertisers. Reddit revealed that its systems had been hacked on February 9. Threat […]
The post Reddit Hackers Threaten to Leak 80GB of Stolen Data appeared first on Cyber Security News.
https://cybersecuritynews.com/reddit-hackers-threaten/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/reddit-hackers-threaten/?utm_source=dlvr.it&utm_medium=blogger
Monday, June 19, 2023
How to simplify the process of compliance with U.S. Executive Order 14028
In this Help Net Security video, Nick Mistry, SVP and CISO at Lineaje, offers tips to simplify the process of compliance with U.S. Executive Order 14028. A key part of U.S. Executive Order 14028 is for organizations that work with…
Read more →
The post How to simplify the process of compliance with U.S. Executive Order 14028 first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-simplify-the-process-of-compliance-with-u-s-executive-order-14028/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-to-simplify-the-process-of-compliance-with-u-s-executive-order-14028/?utm_source=dlvr.it&utm_medium=blogger
Goodbyes are difficult, IT offboarding processes make them harder
When employees, contractors and service providers leave an organization, they take with them knowledge, capabilities, and professional achievements. They should leave behind any proprietary or confidential data belonging to the organization, but Osterman Research found that 69% of organizations polled…
Read more →
The post Goodbyes are difficult, IT offboarding processes make them harder first appeared on IT Security News.
https://www.itsecuritynews.info/goodbyes-are-difficult-it-offboarding-processes-make-them-harder/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/goodbyes-are-difficult-it-offboarding-processes-make-them-harder/?utm_source=dlvr.it&utm_medium=blogger
Sunday, June 18, 2023
From Cryptojacking to DDoS Attacks: Diicot Expands Tactics with Cayosin Botnet
Cybersecurity researchers have discovered previously undocumented payloads associated with a Romanian threat actor named Diicot, revealing its potential for launching distributed denial-of-service (DDoS) attacks.
"The Diicot name is significant, as it's also the name of the Romanian organized crime and anti-terrorism policing unit," Cado Security said in a technical report. "In addition,
https://thehackernews.com/2023/06/from-cryptojacking-to-ddos-attacks.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/from-cryptojacking-to-ddos-attacks.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, June 17, 2023
Fake security researchers push malware files on GitHub
Categories: News Tags: GitHub Tags: malware Tags: repository Tags: security researcher Tags: fake Tags: download Tags: scam Tags: twitter Tags: social We take a look at reports of fake security researchers offering up malware downloads via GitHub repositories. (Read more…)…
Read more →
The post Fake security researchers push malware files on GitHub first appeared on IT Security News.
https://www.itsecuritynews.info/fake-security-researchers-push-malware-files-on-github/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/fake-security-researchers-push-malware-files-on-github/?utm_source=dlvr.it&utm_medium=blogger
Friday, June 16, 2023
Chinese Hackers Employed DNS-over-HTTPS for Linux Malware Communication
ChamelGang, a sophisticated threat actor believed to be based in China, has been using different tools for intrusions, as identified by the security researchers at Stairwell Threat Research in their recent investigation. While apart from this, the Threat Research team of Stairwell also found new tools for Linux intrusions that are developed by the group. […]
The post Chinese Hackers Employed DNS-over-HTTPS for Linux Malware Communication appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-employed-dns-over-https/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-employed-dns-over-https/?utm_source=dlvr.it&utm_medium=blogger
Thursday, June 15, 2023
Cyber debt levels reach tipping point
The tension between difficult economic conditions and the pace of technology innovation, including the evolution of AI, is influencing the growth of identity-led cybersecurity exposure, according to CyberArk. The CyberArk’s report details how these issues – allied to an expected…
Read more →
The post Cyber debt levels reach tipping point first appeared on IT Security News.
https://www.itsecuritynews.info/cyber-debt-levels-reach-tipping-point/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cyber-debt-levels-reach-tipping-point/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, June 14, 2023
Two Russian Nationals Charged for Masterminding Mt. Gox Crypto Exchange Hack
The U.S. Department of Justice (DoJ) has charged two Russian nationals in connection with masterminding the 2014 digital heist of the now-defunct cryptocurrency exchange Mt. Gox.
According to unsealed indictments released last week, Alexey Bilyuchenko, 43, and Aleksandr Verner, 29, have been accused of conspiring to launder approximately 647,000 bitcoins stolen from September 2011 through at
https://thehackernews.com/2023/06/two-russian-nationals-charged-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/two-russian-nationals-charged-for.html?utm_source=dlvr.it&utm_medium=blogger
Critical FortiOS and FortiProxy Vulnerability Likely Exploited - Patch Now!
Fortinet on Monday disclosed that a newly patched critical flaw impacting FortiOS and FortiProxy may have been "exploited in a limited number of cases" in attacks targeting government, manufacturing, and critical infrastructure sectors.
The vulnerability, tracked as CVE-2023-27997 (CVSS score: 9.2), concerns a heap-based buffer overflow vulnerability in FortiOS and FortiProxy SSL-VPN that could
https://thehackernews.com/2023/06/critical-fortios-and-fortiproxy.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/critical-fortios-and-fortiproxy.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, June 13, 2023
China’s cyber now aimed at infrastructure, warns CISA boss
Resilience against threats needs a boost China’s cyber-ops against the US have shifted from espionage activities to targeting infrastructure and societal disruption, the director of the Cybersecurity and Infrastructure Security Agency (CISA) Jen Easterly told an Aspen Institute event on…
Read more →
The post China’s cyber now aimed at infrastructure, warns CISA boss first appeared on IT Security News.
https://www.itsecuritynews.info/chinas-cyber-now-aimed-at-infrastructure-warns-cisa-boss/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/chinas-cyber-now-aimed-at-infrastructure-warns-cisa-boss/?utm_source=dlvr.it&utm_medium=blogger
Monday, June 12, 2023
Apple’s Safari Private Browsing Now Automatically Removes Tracking Parameters in URLs
Apple is introducing major updates to Safari Private Browsing, offering users better protections against third-party trackers as they browse the web. “Advanced tracking and fingerprinting protections go even further to help prevent websites from using the latest techniques to track or…
Read more →
The post Apple’s Safari Private Browsing Now Automatically Removes Tracking Parameters in URLs first appeared on IT Security News.
https://www.itsecuritynews.info/apples-safari-private-browsing-now-automatically-removes-tracking-parameters-in-urls/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apples-safari-private-browsing-now-automatically-removes-tracking-parameters-in-urls/?utm_source=dlvr.it&utm_medium=blogger
Sunday, June 11, 2023
What is SYN Attack? How Does the Attack Works ?
TCP SYN Flood attacks are the most popular ones among DDOS attacks. Here we will discuss, in detail, the basis of the TCP SYN attack and to stop it before it reaches those servers. It’s been more than two decades since the first DDOS attack was attempted at the University of Minnesota, knocking it down […]
The post What is SYN Attack? How Does the Attack Works ? appeared first on Cyber Security News.
https://cybersecuritynews.com/syn-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/syn-attack/?utm_source=dlvr.it&utm_medium=blogger
Saturday, June 10, 2023
Update your Cisco System Secure Client now to fix this AnyConnect bug
Categories: Exploits and vulnerabilities Categories: News Tags: Cisco Tags: anyconnect Tags: system secure client Tags: VPN Tags: bug Tags: patch Tags: update Tags: vulnerability Tags: SYSTEM We take a look at a recent update for Cisco Secure System Client and…
Read more →
The post Update your Cisco System Secure Client now to fix this AnyConnect bug first appeared on IT Security News.
https://www.itsecuritynews.info/update-your-cisco-system-secure-client-now-to-fix-this-anyconnect-bug/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/update-your-cisco-system-secure-client-now-to-fix-this-anyconnect-bug/?utm_source=dlvr.it&utm_medium=blogger
Ransomware review: June 2023
Categories: Ransomware Categories: Threat Intelligence May saw a record number of 556 reported ransomware victims, the unusual emergence of Italy and Russia as major targets, and a significant rise in attacks on the education sector. (Read more…) The post Ransomware…
Read more →
The post Ransomware review: June 2023 first appeared on IT Security News.
https://www.itsecuritynews.info/ransomware-review-june-2023/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ransomware-review-june-2023/?utm_source=dlvr.it&utm_medium=blogger
Friday, June 9, 2023
How to Improve Your API Security Posture
APIs, more formally known as application programming interfaces, empower apps and microservices to communicate and share data. However, this level of connectivity doesn't come without major risks. Hackers can exploit vulnerabilities in APIs to gain unauthorized access to sensitive data or even take control of the entire system. Therefore, it's essential to have a robust API security posture to
https://thehackernews.com/2023/06/how-to-improve-your-api-security-posture.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/how-to-improve-your-api-security-posture.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, June 8, 2023
20 cybersecurity projects on GitHub you should check out
Open-source GitHub cybersecurity projects, developed and maintained by dedicated contributors, provide valuable tools, frameworks, and resources to enhance security practices. From vulnerability scanning and network monitoring to encryption and incident response, the following collection encompasses a diverse range of projects…
Read more →
The post 20 cybersecurity projects on GitHub you should check out first appeared on IT Security News.
https://www.itsecuritynews.info/20-cybersecurity-projects-on-github-you-should-check-out/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/20-cybersecurity-projects-on-github-you-should-check-out/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, June 7, 2023
‘Triangulation’ Malware- New Tool to Find iPhones & iOS Devices Infection
Kaspersky reported earlier this month that they have discovered a new Zero-click iOS exploit currently being exploited by threat actors. The exploitation involves using iMessage as the delivery channel to gain root privileges. Threat actors were using Command and Control (C2) servers to manage and control the compromised iOS devices. Recent reports suggest that a […]
The post ‘Triangulation’ Malware- New Tool to Find iPhones & iOS Devices Infection appeared first on Cyber Security News.
https://cybersecuritynews.com/triangle-check/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/triangle-check/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, June 6, 2023
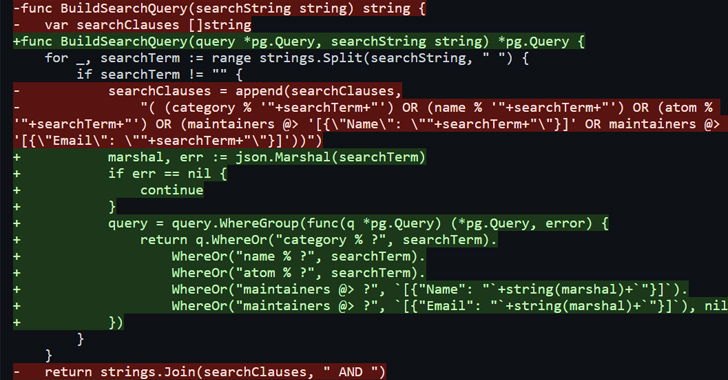
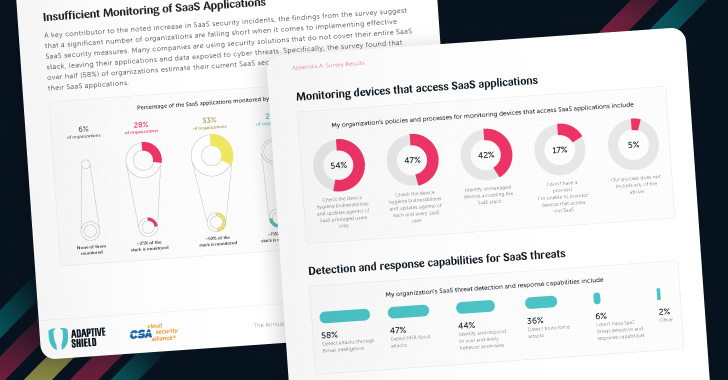
The Annual Report: 2024 Plans and Priorities for SaaS Security
Over 55% of security executives report that they have experienced a SaaS security incident in the past two years — ranging from data leaks and data breaches to SaaS ransomware and malicious apps (as seen in figures 1 and 2).
Figure 1. How many organizations have experienced a SaaS security incident within the past two years
The SaaS Security Survey Report: Plans and Priorities for 2024,
https://thehackernews.com/2023/06/the-annual-report-2024-plans-and.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/the-annual-report-2024-plans-and.html?utm_source=dlvr.it&utm_medium=blogger
Monday, June 5, 2023
10 Best SIEM Tools for SOC Operations – 2023
SIEM is now a fundamental security component of modern enterprises. The major reason is that each customer or tracker creates a virtual footprint in the log data of a network. SIEM systems leverage these log data to get knowledge into past incidents and events. A SIEM system not only determines that an attack has occurred […]
The post 10 Best SIEM Tools for SOC Operations – 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/best-siem-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/best-siem-tools/?utm_source=dlvr.it&utm_medium=blogger
Sunday, June 4, 2023
Kimsuky APT poses as journalists and broadcast writers in its attacks
North Korea-linked APT group Kimsuky is posing as journalists to gather intelligence, a joint advisory from NSA and FBI warns. A joint advisory from the FBI, the U.S. Department of State, the National Security Agency (NSA), South Korea’s National Intelligence Service…
Read more →
The post Kimsuky APT poses as journalists and broadcast writers in its attacks first appeared on IT Security News.
https://www.itsecuritynews.info/kimsuky-apt-poses-as-journalists-and-broadcast-writers-in-its-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/kimsuky-apt-poses-as-journalists-and-broadcast-writers-in-its-attacks/?utm_source=dlvr.it&utm_medium=blogger
Saturday, June 3, 2023
Camaro Dragon Strikes with New TinyNote Backdoor for Intelligence Gathering
The Chinese nation-state group known as Camaro Dragon has been linked to yet another backdoor that's designed to meet its intelligence-gathering goals.
Israeli cybersecurity firm Check Point, which dubbed the Go-based malware TinyNote, said it functions as a first-stage payload capable of "basic machine enumeration and command execution via PowerShell or Goroutines."
What the malware lacks in
https://thehackernews.com/2023/06/camaro-dragon-strikes-with-new-tinynote.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/06/camaro-dragon-strikes-with-new-tinynote.html?utm_source=dlvr.it&utm_medium=blogger
Friday, June 2, 2023
How defense contractors can move from cybersecurity to cyber resilience
As the world’s most powerful military and economic power, the United States also holds another, less impressive distinction: Cyber threat actors target the US more than any other country in the world. In 2022 alone, the FBI received more than…
Read more →
The post How defense contractors can move from cybersecurity to cyber resilience first appeared on IT Security News.
https://www.itsecuritynews.info/how-defense-contractors-can-move-from-cybersecurity-to-cyber-resilience/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-defense-contractors-can-move-from-cybersecurity-to-cyber-resilience/?utm_source=dlvr.it&utm_medium=blogger
Thursday, June 1, 2023
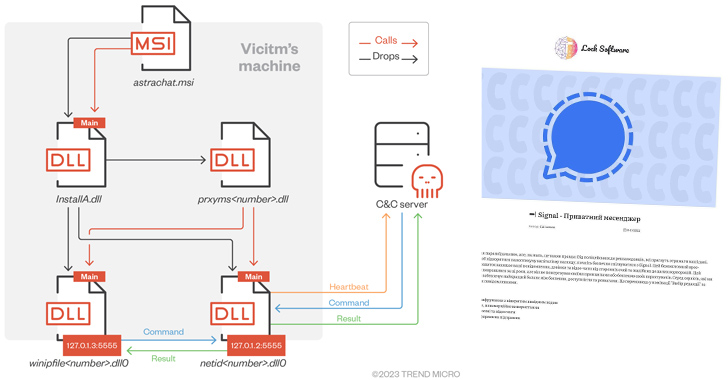
RomCom RAT Using Deceptive Web of Rogue Software Sites for Covert Attacks
The threat actors behind RomCom RAT are leveraging a network of fake websites advertising rogue versions of popular software at least since July 2022 to infiltrate targets.
Cybersecurity firm Trend Micro is tracking the activity cluster under the name Void Rabisu, which is also known as Tropical Scorpius (Unit 42) and UNC2596 (Mandiant).
"These lure sites are most likely only meant for a small
https://thehackernews.com/2023/05/romcom-rat-using-deceptive-web-of-rogue.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/romcom-rat-using-deceptive-web-of-rogue.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)















.webp)