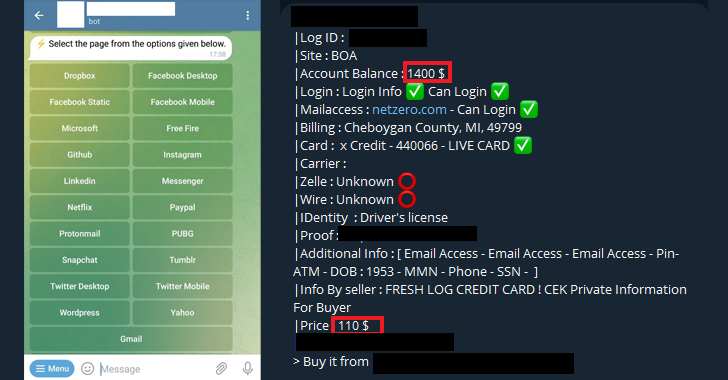
The UK Cyber Security Councilv has launched the first phase of its certification mapping tool. It has been created to map all available cyber security certifications onto the 16 specialisms identified by the Council, with the first phase now available.…
Read more →
The post UK Cyber Security Council launches certification mapping tool first appeared on IT Security News.
https://www.itsecuritynews.info/uk-cyber-security-council-launches-certification-mapping-tool/?utm_source=dlvr.it&utm_medium=blogger
Sunday, April 30, 2023
Saturday, April 29, 2023
Tonto Team Uses Anti-Malware File to Launch Attacks on South Korean Institutions
South Korean education, construction, diplomatic, and political institutions are at the receiving end of new attacks perpetrated by a China-aligned threat actor known as the Tonto Team.
"Recent cases have revealed that the group is using a file related to anti-malware products to ultimately execute their malicious attacks," the AhnLab Security Emergency Response Center (ASEC) said in a report
https://thehackernews.com/2023/04/tonto-team-uses-anti-malware-file-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/tonto-team-uses-anti-malware-file-to.html?utm_source=dlvr.it&utm_medium=blogger
Friday, April 28, 2023
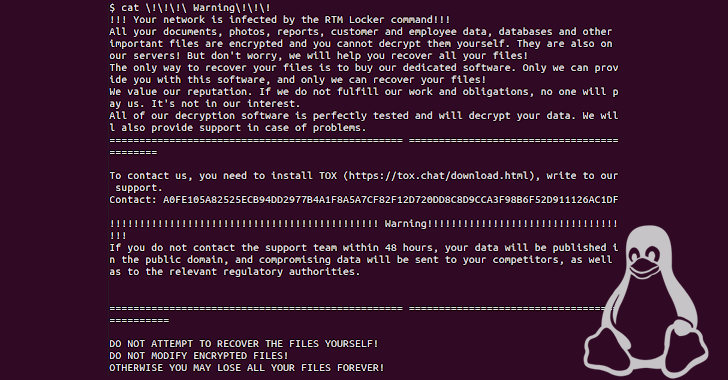
RTM Locker's First Linux Ransomware Strain Targeting NAS and ESXi Hosts
The threat actors behind RTM Locker have developed a ransomware strain that's capable of targeting Linux machines, marking the group's first foray into the open source operating system.
"Its locker ransomware infects Linux, NAS, and ESXi hosts and appears to be inspired by Babuk ransomware's leaked source code," Uptycs said in a new report published Wednesday. "It uses a combination of ECDH on
https://thehackernews.com/2023/04/rtm-lockers-first-linux-ransomware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/rtm-lockers-first-linux-ransomware.html?utm_source=dlvr.it&utm_medium=blogger
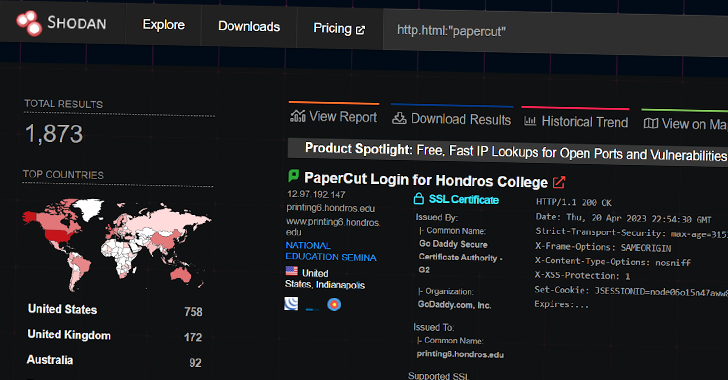
Microsoft Confirms PaperCut Servers Used to Deliver LockBit and Cl0p Ransomware
Microsoft has confirmed that the active exploitation of PaperCut servers is linked to attacks that are designed to deliver Cl0p and LockBit ransomware families.
The tech giant's threat intelligence team is attributing a subset of the intrusions to a financially motivated actor it tracks under the name Lace Tempest (formerly DEV-0950), which overlaps with other hacking groups like FIN11, TA505,
https://thehackernews.com/2023/04/microsoft-confirms-papercut-servers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/microsoft-confirms-papercut-servers.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, April 27, 2023
VMware Releases Critical Patches for Workstation and Fusion Software
VMware has released updates to resolve multiple security flaws impacting its Workstation and Fusion software, the most critical of which could allow a local attacker to achieve code execution.
The vulnerability, tracked as CVE-2023-20869 (CVSS score: 9.3), is described as a stack-based buffer-overflow vulnerability that resides in the functionality for sharing host Bluetooth devices with the
https://thehackernews.com/2023/04/vmware-releases-critical-patches-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/vmware-releases-critical-patches-for.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, April 26, 2023
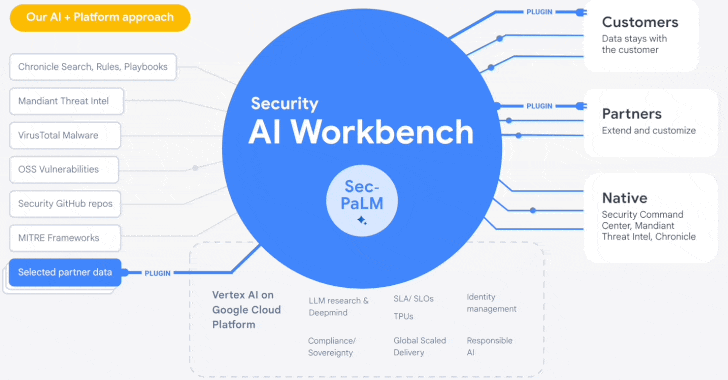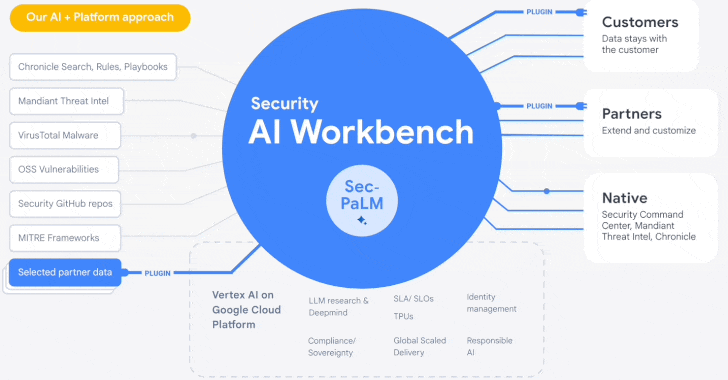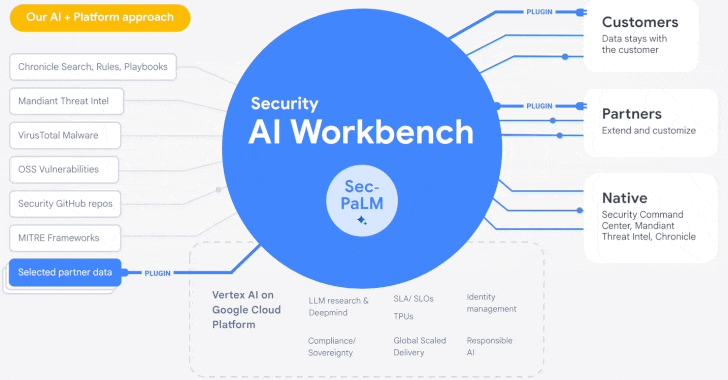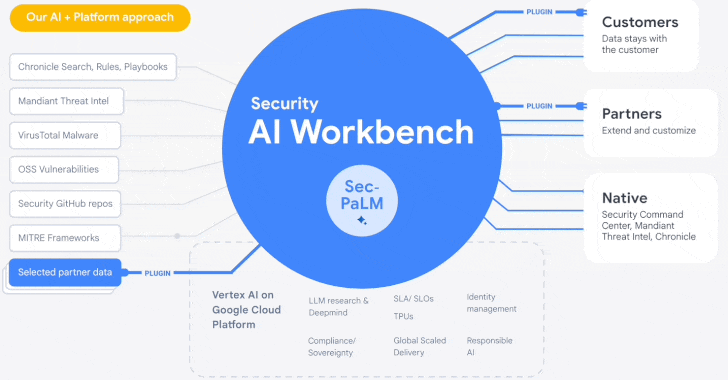
Google Cloud Introduces Security AI Workbench for Faster Threat Detection and Analysis
Google's cloud division is following in the footsteps of Microsoft with the launch of Security AI Workbench that leverages generative AI models to gain better visibility into the threat landscape.
Powering the cybersecurity suite is Sec-PaLM, a specialized large language model (LLM) that's "fine-tuned for security use cases."
The idea is to take advantage of the latest advances in AI to augment
https://thehackernews.com/2023/04/google-cloud-introduces-security-ai.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/google-cloud-introduces-security-ai.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, April 25, 2023
Hackers Exploit Outdated WordPress Plugin to Backdoor Thousands of WordPress Sites
Threat actors have been observed leveraging a legitimate but outdated WordPress plugin to surreptitiously backdoor websites as part of an ongoing campaign, Sucuri revealed in a report published last week.
The plugin in question is Eval PHP, released by a developer named flashpixx. It allows users to insert PHP code pages and posts of WordPress sites that's then executed every time the posts are
https://thehackernews.com/2023/04/hackers-exploit-outdated-wordpress.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/hackers-exploit-outdated-wordpress.html?utm_source=dlvr.it&utm_medium=blogger
Monday, April 24, 2023
Russian Hackers Suspected in Ongoing Exploitation of Unpatched PaperCut Servers
Print management software provider PaperCut said that it has "evidence to suggest that unpatched servers are being exploited in the wild," citing two vulnerability reports from cybersecurity company Trend Micro.
"PaperCut has conducted analysis on all customer reports, and the earliest signature of suspicious activity on a customer server potentially linked to this vulnerability is 14th April 01
https://thehackernews.com/2023/04/russian-hackers-suspected-in-ongoing.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/russian-hackers-suspected-in-ongoing.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, April 23, 2023
IT Security News Daily Summary 2023-04-22
The Current State of Wireless (In)security, by Bastille CTO ChatGPT Can be Tricked To Write Malware When You Act as a Developer Mode CISA adds MinIO, PaperCut, and Chrome bugs to its Known Exploited Vulnerabilities catalog DNS Malware Toolkit Discovered…
Read more →
The post IT Security News Daily Summary 2023-04-22 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2023-04-22/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2023-04-22/?utm_source=dlvr.it&utm_medium=blogger
The Current State of Wireless (In)security, by Bastille CTO
Guest Editorial by Brett T. Walkenhorst, Ph.D., CTO, Bastille From cell phones and Wi-Fi to wearables, peripherals, and IoT, the modern world is swimming in wireless devices, and their wireless data is constantly racing through the air all around us.…
Read more →
The post The Current State of Wireless (In)security, by Bastille CTO first appeared on IT Security News.
https://www.itsecuritynews.info/the-current-state-of-wireless-insecurity-by-bastille-cto/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-current-state-of-wireless-insecurity-by-bastille-cto/?utm_source=dlvr.it&utm_medium=blogger
Saturday, April 22, 2023
14 Kubernetes and Cloud Security Challenges and How to Solve Them
Recently, Andrew Martin, founder and CEO of ControlPlane, released a report entitled Cloud Native and Kubernetes Security Predictions 2023. These predictions underscore the rapidly evolving landscape of Kubernetes and cloud security, emphasizing the need for organizations to stay informed and adopt comprehensive security solutions to protect their digital assets.
In response, Uptycs, the first
https://thehackernews.com/2023/04/14-kubernetes-and-cloud-security.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/14-kubernetes-and-cloud-security.html?utm_source=dlvr.it&utm_medium=blogger
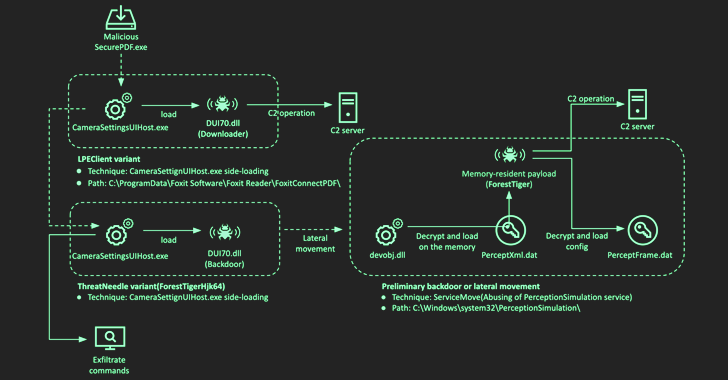
N.K. Hackers Employ Matryoshka Doll-Style Cascading Supply Chain Attack on 3CX
The supply chain attack targeting 3CX was the result of a prior supply chain compromise associated with a different company, demonstrating a new level of sophistication with North Korean threat actors.
Google-owned Mandiant, which is tracking the attack event under the moniker UNC4736, said the incident marks the first time it has seen a "software supply chain attack lead to another software
https://thehackernews.com/2023/04/nk-hackers-employ-matryoshka-doll-style.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/nk-hackers-employ-matryoshka-doll-style.html?utm_source=dlvr.it&utm_medium=blogger
Friday, April 21, 2023
NSO Group Used 3 Zero-Click iPhone Exploits Against Human Rights Defenders
Israeli spyware maker NSO Group deployed at least three novel "zero-click" exploits against iPhones in 2022 to infiltrate defenses erected by Apple and deploy Pegasus, according to the latest findings from Citizen Lab.
"NSO Group customers widely deployed at least three iOS 15 and iOS 16 zero-click exploit chains against civil society targets around the world," the interdisciplinary laboratory
https://thehackernews.com/2023/04/nso-group-used-3-zero-click-iphone.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/nso-group-used-3-zero-click-iphone.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, April 20, 2023
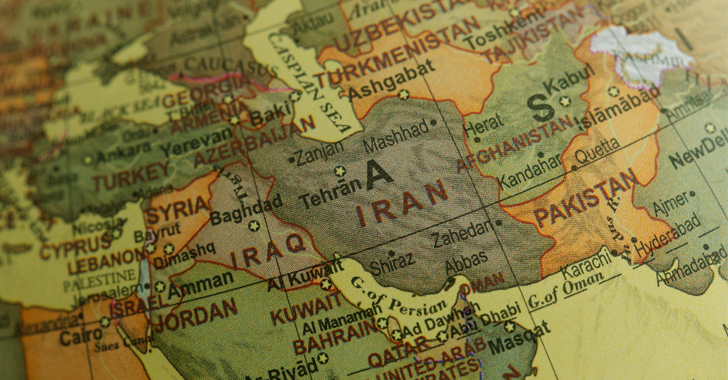
Iranian Government-Backed Hackers Targeting U.S. Energy and Transit Systems
An Iranian government-backed actor known as Mint Sandstorm has been linked to attacks aimed at critical infrastructure in the U.S. between late 2021 to mid-2022.
"This Mint Sandstorm subgroup is technically and operationally mature, capable of developing bespoke tooling and quickly weaponizing N-day vulnerabilities, and has demonstrated agility in its operational focus, which appears to align
https://thehackernews.com/2023/04/iranian-government-backed-hackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/iranian-government-backed-hackers.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, April 19, 2023
LockBit Ransomware Now Targeting Apple macOS Devices
Threat actors behind the LockBit ransomware operation have developed new artifacts that can encrypt files on devices running Apple's macOS operating system.
The development, which was reported by the MalwareHunterTeam over the weekend, appears to be the first time a big-game ransomware crew has created a macOS-based payload.
Additional samples identified by vx-underground show that the macOS
https://thehackernews.com/2023/04/lockbit-ransomware-now-targeting-apple.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/lockbit-ransomware-now-targeting-apple.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, April 18, 2023
New Zaraza Bot Credential-Stealer Sold on Telegram Targeting 38 Web Browsers
A novel credential-stealing malware called Zaraza bot is being offered for sale on Telegram while also using the popular messaging service as a command-and-control (C2).
"Zaraza bot targets a large number of web browsers and is being actively distributed on a Russian Telegram hacker channel popular with threat actors," cybersecurity company Uptycs said in a report published last week.
"Once the
https://thehackernews.com/2023/04/new-zaraza-bot-credential-stealer-sold.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/new-zaraza-bot-credential-stealer-sold.html?utm_source=dlvr.it&utm_medium=blogger
Monday, April 17, 2023
ChatGPT Account Take Over Vulnerability Let Hackers Gain User’s Online Account
A renowned security analyst and bug hunter, Nagli (@naglinagli), recently uncovered a critical security vulnerability in ChatGPT. With just a single click, a threat actor could easily exploit the vulnerability and gain complete control of any ChatGPT user’s account. As a result, opening the doors to sensitive data let attackers execute unauthorized actions; the whole […]
The post ChatGPT Account Take Over Vulnerability Let Hackers Gain User’s Online Account appeared first on Cyber Security News.
https://cybersecuritynews.com/chatgpt-account-take-over-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/chatgpt-account-take-over-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
Sunday, April 16, 2023
Top 30 Best Penetration Testing Tools – 2023
In this article, security experts from Cyber security News have extensively researched and listed the top 30 best penetration testing tools. When we talk about penetration Testing, we all know very well that the first thing that comes to mind is the threat. These tools allow penetration testers to perform scans, reconnaissance, information gathering, analysis, […]
The post Top 30 Best Penetration Testing Tools – 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/penetration-testing-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/penetration-testing-tools/?utm_source=dlvr.it&utm_medium=blogger
Saturday, April 15, 2023
Webinar: Tips from MSSPs to MSSPs – Building a Profitable vCISO Practice
In today's fast-paced and ever-changing digital landscape, businesses of all sizes face a myriad of cybersecurity threats. Putting in place the right people, technological tools and services, MSSPs are in a great position to ensure their customers' cyber resilience.
The growing need of SMEs and SMBs for structured cybersecurity services can be leveraged by MSPs and MSSPs to provide strategic
https://thehackernews.com/2023/04/webinar-tips-from-mssps-to-mssps.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/webinar-tips-from-mssps-to-mssps.html?utm_source=dlvr.it&utm_medium=blogger
Friday, April 14, 2023
Lazarus Hacker Group Evolves Tactics, Tools, and Targets in DeathNote Campaign
The North Korean threat actor known as the Lazarus Group has been observed shifting its focus and rapidly evolving its tools and tactics as part of a long-running campaign called DeathNote.
While the nation-state adversary is known for persistently singling out the cryptocurrency sector, recent attacks have also targeted automotive, academic, and defense sectors in Eastern Europe and other parts
https://thehackernews.com/2023/04/lazarus-hacker-group-evolves-tactics.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/lazarus-hacker-group-evolves-tactics.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, April 13, 2023
Urgent: Microsoft Issues Patches for 97 Flaws, Including Active Ransomware Exploit
It's the second Tuesday of the month, and Microsoft has released another set of security updates to fix a total of 97 flaws impacting its software, one of which has been actively exploited in ransomware attacks in the wild.
Seven of the 97 bugs are rated Critical and 90 are rated Important in severity. Interestingly, 45 of the shortcomings are remote code execution flaws, followed by 20
https://thehackernews.com/2023/04/urgent-microsoft-issues-patches-for-97.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/urgent-microsoft-issues-patches-for-97.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, April 12, 2023
Cryptocurrency Stealer Malware Distributed via 13 NuGet Packages
Cybersecurity researchers have detailed the inner workings of the cryptocurrency stealer malware that was distributed via 13 malicious NuGet packages as part of a supply chain attack targeting .NET developers.
The sophisticated typosquatting campaign, which was uncovered by JFrog late last month, impersonated legitimate packages to execute PowerShell code designed to retrieve a follow-on binary
https://thehackernews.com/2023/04/cryptocurrency-stealer-malware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/cryptocurrency-stealer-malware.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, April 11, 2023
Protecting your business with Wazuh: The open source security platform
Today, businesses face a variety of security challenges like cyber attacks, compliance requirements, and endpoint security administration. The threat landscape constantly evolves, and it can be overwhelming for businesses to keep up with the latest security trends. Security teams use processes and security solutions to curb these challenges. These solutions include firewalls, antiviruses, data
https://thehackernews.com/2023/04/protecting-your-business-with-wazuh.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/protecting-your-business-with-wazuh.html?utm_source=dlvr.it&utm_medium=blogger
Monday, April 10, 2023
CISA Warns of 5 Actively Exploited Security Flaws: Urgent Action Required
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added five security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild.
This includes three high-severity flaws in the Veritas Backup Exec Agent software (CVE-2021-27876, CVE-2021-27877, and CVE-2021-27878) that could lead to the execution of privileged commands
https://thehackernews.com/2023/04/cisa-warns-of-5-actively-exploited.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/cisa-warns-of-5-actively-exploited.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, April 9, 2023
Iran-Based Hackers Caught Carrying Out Destructive Attacks Under Ransomware Guise
The Iranian nation-state group known as MuddyWater has been observed carrying out destructive attacks on hybrid environments under the guise of a ransomware operation.
That's according to new findings from the Microsoft Threat Intelligence team, which discovered the threat actor targeting both on-premises and cloud infrastructures in partnership with another emerging activity cluster dubbed
https://thehackernews.com/2023/04/iran-based-hackers-caught-carrying-out.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/iran-based-hackers-caught-carrying-out.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, April 8, 2023
Researchers Uncover Thriving Phishing Kit Market on Telegram Channels
In yet another sign that Telegram is increasingly becoming a thriving hub for cybercrime, researchers have found that threat actors are using the messaging platform to peddle phishing kits and help set up phishing campaigns.
"To promote their 'goods,' phishers create Telegram channels through which they educate their audience about phishing and entertain subscribers with polls like, 'What type
https://thehackernews.com/2023/04/researchers-uncover-thriving-phishing.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/researchers-uncover-thriving-phishing.html?utm_source=dlvr.it&utm_medium=blogger
Friday, April 7, 2023
Supply Chain Attacks and Critical Infrastructure: How CISA Helps Secure a Nation's Crown Jewels
Critical infrastructure attacks are a preferred target for cyber criminals. Here's why and what's being done to protect them.
What is Critical Infrastructure and Why is It Attacked?
Critical infrastructure is the physical and digital assets, systems and networks that are vital to national security, the economy, public health, or safety. It can be government- or privately-owned.
According to Etay
https://thehackernews.com/2023/04/supply-chain-attacks-and-critical.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/supply-chain-attacks-and-critical.html?utm_source=dlvr.it&utm_medium=blogger
FBI Cracks Down on Genesis Market: 119 Arrested in Cybercrime Operation
A joint international law enforcement operation has dismantled Genesis Market, an illegal online marketplace that specialized in the sale of stolen credentials associated with email, bank accounts, and social media platforms.
Coinciding with the infrastructure seizure, the major crackdown, which involved authorities from 17 countries, culminated in 119 arrests and 208 property searches in 13
https://thehackernews.com/2023/04/fbi-cracks-down-on-genesis-market-119.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/fbi-cracks-down-on-genesis-market-119.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, April 6, 2023
Typhon Reborn Stealer Malware Resurfaces with Advanced Evasion Techniques
The threat actor behind the information-stealing malware known as Typhon Reborn has resurfaced with an updated version (V2) that packs in improved capabilities to evade detection and resist analysis.
The new version is offered for sale on the criminal underground for $59 per month, $360 per year, or alternatively, for $540 for a lifetime subscription.
"The stealer can harvest and exfiltrate
https://thehackernews.com/2023/04/typhon-reborn-stealer-malware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/typhon-reborn-stealer-malware.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, April 5, 2023
Think Before You Share the Link: SaaS in the Real World
Collaboration sits at the essence of SaaS applications. The word, or some form of it, appears in the top two headlines on Google Workspace’s homepage. It can be found six times on Microsoft 365’s homepage, three times on Box, and once on Workday. Visit nearly any SaaS site, and odds are ‘collaboration’ will appear as part of the app’s key selling point.
By sitting on the cloud, content within
https://thehackernews.com/2023/04/think-before-you-share-link-saas-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/think-before-you-share-link-saas-in.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, April 4, 2023
Crypto-Stealing OpcJacker Malware Targets Users with Fake VPN Service
A piece of new information-stealing malware called OpcJacker has been spotted in the wild since the second half of 2022 as part of a malvertising campaign.
"OpcJacker's main functions include keylogging, taking screenshots, stealing sensitive data from browsers, loading additional modules, and replacing cryptocurrency addresses in the clipboard for hijacking purposes," Trend Micro researchers
https://thehackernews.com/2023/04/crypto-stealing-opcjacker-malware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/crypto-stealing-opcjacker-malware.html?utm_source=dlvr.it&utm_medium=blogger
Monday, April 3, 2023
Hackers Exploiting WordPress Plugin with Over 11M Installs
One of the most popular WordPress plugins, Elementor Pro, used by over eleven million websites, is vulnerable to a high-severity vulnerability that hackers have actively exploited. More than 12 million sites powered by WordPress have been affected by the vulnerability, which carries a severity rating of 8.8 out of 10. Elementor Pro is a plugin […]
The post Hackers Exploiting WordPress Plugin with Over 11M Installs appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-exploiting-wordpress-plugin/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-exploiting-wordpress-plugin/?utm_source=dlvr.it&utm_medium=blogger
Sunday, April 2, 2023
Microsoft Fixes New Azure AD Vulnerability Impacting Bing Search and Major Apps
Microsoft has patched a misconfiguration issue impacting the Azure Active Directory (AAD) identity and access management service that exposed several "high-impact" applications to unauthorized access.
"One of these apps is a content management system (CMS) that powers Bing.com and allowed us to not only modify search results, but also launch high-impact XSS attacks on Bing users," cloud security
https://thehackernews.com/2023/04/microsoft-fixes-new-azure-ad.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/04/microsoft-fixes-new-azure-ad.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, April 1, 2023
3CX Supply Chain Attack — Here's What We Know So Far
Enterprise communications software maker 3CX on Thursday confirmed that multiple versions of its desktop app for Windows and macOS are affected by a supply chain attack.
The version numbers include 18.12.407 and 18.12.416 for Windows and 18.11.1213, 18.12.402, 18.12.407, and 18.12.416 for macOS.
The company said it's engaging the services of Google-owned Mandiant to review the incident. In the
https://thehackernews.com/2023/03/3cx-supply-chain-attack-heres-what-we.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/03/3cx-supply-chain-attack-heres-what-we.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)


.jpg)