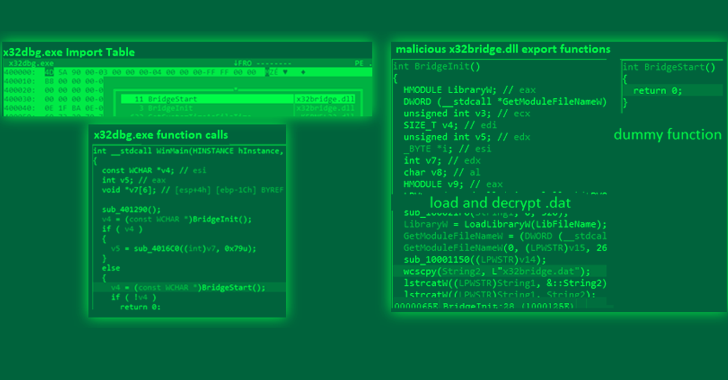
The PlugX remote access trojan has been observed masquerading as an open source Windows debugger tool called x64dbg in an attempt to circumvent security protections and gain control of a target system.
"This file is a legitimate open-source debugger tool for Windows that is generally used to examine kernel-mode and user-mode code, crash dumps, or CPU registers," Trend Micro researchers Buddy
https://thehackernews.com/2023/02/plugx-trojan-disguised-as-legitimate.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, February 28, 2023
Monday, February 27, 2023
10 Best Penetration Testing Phases & Lifecycle – A Pentesters Guide 2023
Penetration Testing Phases involves various Methods, phases, lifecycle, and scope to prepare the best checklist to perform quality penetration operations. Here we have created a complete Penetration Testing Guide with detailed step-by-step methods. Let’s take a look at how you can get better in your pentesting engagements by breaking your methodology into well-defined stages, leading […]
The post 10 Best Penetration Testing Phases & Lifecycle – A Pentesters Guide 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/penetration-testing-phases/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/penetration-testing-phases/?utm_source=dlvr.it&utm_medium=blogger
Dutch Police Arrest 3 Hackers Involved in Massive Data Theft and Extortion Scheme
The Dutch police announced the arrest of three individuals in connection with a "large-scale" criminal operation involving data theft, extortion, and money laundering.
The suspects include two 21-year-old men from Zandvoort and Rotterdam and an 18-year-old man without a permanent residence. The arrests were made on January 23, 2023.
It's estimated that the hackers stole personal data belonging
https://thehackernews.com/2023/02/dutch-police-arrest-3-hackers-involved.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/dutch-police-arrest-3-hackers-involved.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 26, 2023
Russian National Charged for Smuggling Devices Used in Counterintelligence Operations
An individual of Russian citizenship has been indicted in the United States for the offense of illegally transporting contraband items utilized in counterintelligence activities from the United States and conveying them to the Russian security services. The charges suggest that the individual in question was engaged in illicit activities aimed at compromising the security and […]
The post Russian National Charged for Smuggling Devices Used in Counterintelligence Operations appeared first on Cyber Security News.
https://cybersecuritynews.com/russian-national-charged/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/russian-national-charged/?utm_source=dlvr.it&utm_medium=blogger
Saturday, February 25, 2023
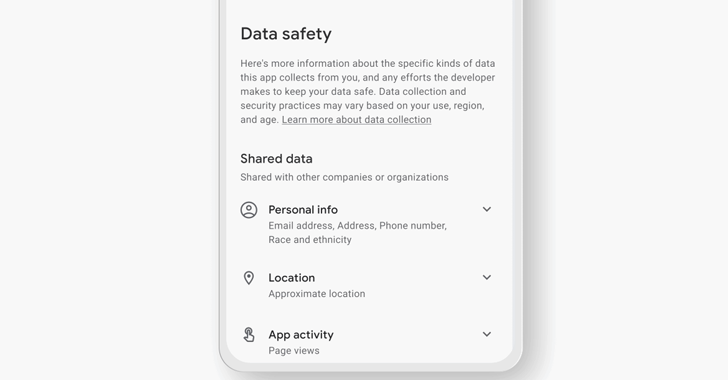
Even Top-Ranked Android Apps in Google Play Store Provide Misleading Data Safety Labels
An investigation into data safety labels for Android apps available on the Google Play Store has uncovered "serious loopholes" that allow apps to provide misleading or outright false information.
The study, conducted by the Mozilla Foundation as part of its *Privacy Not Included initiative, compared the privacy policies and labels of the 20 most popular paid apps and the 20 most popular free
https://thehackernews.com/2023/02/majority-of-android-apps-on-google-play.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/majority-of-android-apps-on-google-play.html?utm_source=dlvr.it&utm_medium=blogger
Friday, February 24, 2023
New S1deload Malware Hijacking Users' Social Media Accounts and Mining Cryptocurrency
An active malware campaign has set its sights on Facebook and YouTube users by leveraging a new information stealer to hijack the accounts and abuse the systems' resources to mine cryptocurrency.
Bitdefender is calling the malware S1deload Stealer for its use of DLL side-loading techniques to get past security defenses and execute its malicious components.
"Once infected, S1deload Stealer steals
https://thehackernews.com/2023/02/new-s1deload-malware-hijacking-users.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/new-s1deload-malware-hijacking-users.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, February 23, 2023
Hydrochasma: New Threat Actor Targets Shipping Companies and Medical Labs in Asia
Shipping companies and medical laboratories in Asia have been the subject of a suspected espionage campaign carried out by a never-before-seen threat actor dubbed Hydrochasma.
The activity, which has been ongoing since October 2022, "relies exclusively on publicly available and living-off-the-land tools," Symantec, by Broadcom Software, said in a report shared with The Hacker News.
There is no
https://thehackernews.com/2023/02/hydrochasma-new-threat-actor-targets.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/hydrochasma-new-threat-actor-targets.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, February 22, 2023
Coinbase Employee Falls for SMS Scam in Cyber Attack, Limited Data Exposed
Popular cryptocurrency exchange platform Coinbase disclosed that it experienced a cybersecurity attack that targeted its employees.
The company said its "cyber controls prevented the attacker from gaining direct system access and prevented any loss of funds or compromise of customer information."
The incident, which took place on February 5, 2023, resulted in the exposure of a "limited amount of
https://thehackernews.com/2023/02/coinbase-employee-falls-for-sms-scam-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/coinbase-employee-falls-for-sms-scam-in.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, February 21, 2023
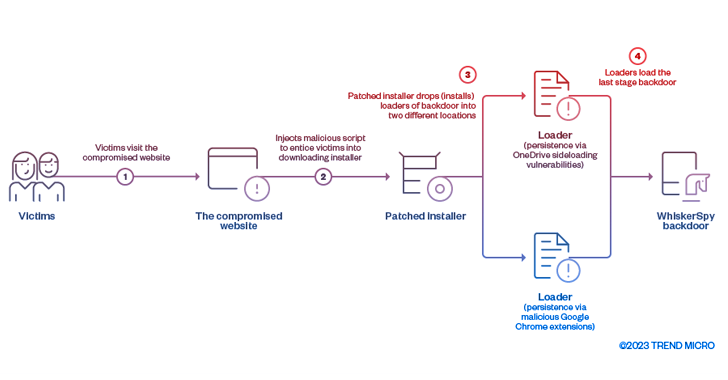
Cyber Espionage Group Earth Kitsune Deploys WhiskerSpy Backdoor in Latest Attacks
The cyber espionage threat actor tracked as Earth Kitsune has been observed deploying a new backdoor called WhiskerSpy as part of a social engineering campaign.
Earth Kitsune, active since at least 2019, is known to primarily target individuals interested in North Korea with self-developed malware such as dneSpy and agfSpy. Previously documented intrusions have entailed the use of watering holes
https://thehackernews.com/2023/02/north-korean-cyber-espionage-group.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/north-korean-cyber-espionage-group.html?utm_source=dlvr.it&utm_medium=blogger
Monday, February 20, 2023
Fortinet Critical RCE Flaws Lets Attackers Execute Arbitrary Code
FortiNAC and FortiWeb, two products that are designed to protect your network from viruses and hackers, were recently updated with new security patches by Fortinet. These updates address two vulnerabilities that are marked as critical, which, if exploited, could enable unauthorized attackers to execute arbitrary code or commands without authentication. FortiNAC is affected by the […]
The post Fortinet Critical RCE Flaws Lets Attackers Execute Arbitrary Code appeared first on Cyber Security News.
https://cybersecuritynews.com/fortinet-critical-rce-flaws/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/fortinet-critical-rce-flaws/?utm_source=dlvr.it&utm_medium=blogger
Samsung Introduces New Feature to Protect Users from Zero-Click Malware Attacks
Samsung has announced a new feature called Message Guard that comes with safeguards to protect users from malware and spyware via what's referred to as zero-click attacks.
The South Korean chaebol said the solution "preemptively" secures users' devices by "limiting exposure to invisible threats disguised as image attachments."
The security feature, available on Samsung Messages and Google
https://thehackernews.com/2023/02/samsung-introduces-new-feature-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/samsung-introduces-new-feature-to.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 19, 2023
GoDaddy Discloses Multi-Year Security Breach Causing Malware Installations and Source Code Theft
Web hosting services provider GoDaddy on Friday disclosed a multi-year security breach that enabled unknown threat actors to install malware and siphon source code related to some of its services.
The company attributed the campaign to a "sophisticated and organized group targeting hosting services."
GoDaddy said in December 2022, it received an unspecified number of customer complaints about
https://thehackernews.com/2023/02/godaddy-discloses-multi-year-security.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/godaddy-discloses-multi-year-security.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, February 18, 2023
New Mirai Botnet Variant 'V3G4' Exploiting 13 Flaws to Target Linux and IoT Devices
A new variant of the notorious Mirai botnet has been found leveraging several security vulnerabilities to propagate itself to Linux and IoT devices.
Observed during the second half of 2022, the new version has been dubbed V3G4 by Palo Alto Networks Unit 42, which identified three different campaigns likely conducted by the same threat actor.
"Once the vulnerable devices are compromised, they
https://thehackernews.com/2023/02/new-mirai-botnet-variant-v3g4.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/new-mirai-botnet-variant-v3g4.html?utm_source=dlvr.it&utm_medium=blogger
Friday, February 17, 2023
Parrot Security OS 5.2 Release – What’s New!
Recently, Parrot Security announced the latest release of Parrot Security OS 5.2. This new version of Parrot Security OS is now available to the public as the latest stable version. The primary focus of this operating system is ethical hacking and penetration testing, making it an essential tool for cybersecurity professionals and enthusiasts alike. The […]
The post Parrot Security OS 5.2 Release – What’s New! appeared first on Cyber Security News.
https://cybersecuritynews.com/parrot-security-os-5-2/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/parrot-security-os-5-2/?utm_source=dlvr.it&utm_medium=blogger
Thursday, February 16, 2023
RedEyes Hacking Group Uses Steganography Technique to Deploy Malware on PC & Mobile Phones
RedEyes Hacking Group (aka APT37), a threat group known for its cyber espionage activities, has recently adopted a new tactic in its efforts to collect intelligence from targeted individuals. This group is now using a sophisticated malware called “M2RAT,” which is specifically designed to evade detection by security software. In addition to using M2RAT, APT37 […]
The post RedEyes Hacking Group Uses Steganography Technique to Deploy Malware on PC & Mobile Phones appeared first on Cyber Security News.
https://cybersecuritynews.com/redeyes-hacking-group/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/redeyes-hacking-group/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, February 15, 2023
Patch Now: Apple's iOS, iPadOS, macOS, and Safari Under Attack with New Zero-Day Flaw
Apple on Monday rolled out security updates for iOS, iPadOS, macOS, and Safari to address a zero-day flaw that it said has been actively exploited in the wild.
Tracked as CVE-2023-23529, the issue relates to a type confusion bug in the WebKit browser engine that could be activated when processing maliciously crafted web content, culminating in arbitrary code execution.
The iPhone maker said the
https://thehackernews.com/2023/02/patch-now-apples-ios-ipados-macos-and.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/patch-now-apples-ios-ipados-macos-and.html?utm_source=dlvr.it&utm_medium=blogger
Hackers Create Malicious Dota 2 Game Modes to Secretly Access Players' Systems
An unknown threat actor created malicious game modes for the Dota 2 multiplayer online battle arena (MOBA) video game that could have been exploited to establish backdoor access to players' systems.
The modes exploited a high-severity flaw in the V8 JavaScript engine tracked as CVE-2021-38003 (CVSS score: 8.8), which was exploited as a zero-day and addressed by Google in October 2021.
"Since V8
https://thehackernews.com/2023/02/hackers-create-malicious-dota-2-game.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/hackers-create-malicious-dota-2-game.html?utm_source=dlvr.it&utm_medium=blogger
Honeypot-Factory: The Use of Deception in ICS/OT Environments
The recently published Security Navigator report of Orange Cyberdefense shows there has been a rapid increase of attacks on industrial control systems (ICS) in the past few years. Looking a bit closer, most of the attacks seem to have spilt over from traditional IT. That's to be expected, as production systems are commonly connected to ordinary corporate networks at this point. Though the data
https://thehackernews.com/2023/02/honeypot-factory-use-of-deception-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/honeypot-factory-use-of-deception-in.html?utm_source=dlvr.it&utm_medium=blogger
Chinese Tonto Team Hackers' Second Attempt to Target Cybersecurity Firm Group-IB Fails
The advanced persistent threat (APT) actor known as Tonto Team carried out an unsuccessful attack on cybersecurity company Group-IB in June 2022.
The Singapore-headquartered firm said that it detected and blocked malicious phishing emails originating from the group targeting its employees. It's also the second attack aimed at Group-IB, the first of which took place in March 2021.
Tonto Team,
https://thehackernews.com/2023/02/chinese-tonto-team-hackers-second.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/chinese-tonto-team-hackers-second.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, February 14, 2023
Hackers Targeting Telecommunications Industry – Over 74 Million Clients’ Data Leaked
Among the most crucial industries to any nation’s infrastructure is the one based on telecommunications. It serves as the foundation for communication and coordination, providing the necessary connectivity for people to stay connected and for businesses to operate efficiently. The year 2023 is projected to have an impressive increase in the number of internet users, […]
The post Hackers Targeting Telecommunications Industry – Over 74 Million Clients’ Data Leaked appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-telecommunications-industry/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-telecommunications-industry/?utm_source=dlvr.it&utm_medium=blogger
Monday, February 13, 2023
The City of Oakland Targeted by Ransomware Attack – Severity Unknown
The City of Oakland has revealed that a ransomware attack recently targeted it. Their essential functions remain in place. There is no impact on 911, financial data, or emergency resources. “Our core functions are intact. 911, financial data, and fire and emergency resources are not impacted”, in a statement released on Friday, by the City stated. […]
The post The City of Oakland Targeted by Ransomware Attack – Severity Unknown appeared first on Cyber Security News.
https://cybersecuritynews.com/city-of-oakland-targeted/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/city-of-oakland-targeted/?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 12, 2023
Enigma, Vector, and TgToxic: The New Threats to Cryptocurrency Users
Suspected Russian threat actors have been targeting Eastern European users in the crypto industry with fake job opportunities as bait to install information-stealing malware on compromised hosts.
The attackers "use several highly obfuscated and under-development custom loaders in order to infect those involved in the cryptocurrency industry with Enigma stealer," Trend Micro researchers Aliakbar
https://thehackernews.com/2023/02/enigma-vector-and-tgtoxic-new-threats.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/enigma-vector-and-tgtoxic-new-threats.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, February 11, 2023
Reddit Hacked – Attackers Steal Internal Documents and Source Code
A sophisticated and highly targeted phishing attack led to the hacking of the Reddit systems. Reports say attackers were given access to some internal business systems, code, and documentation. In an effort to acquire credentials and two-factor tokens, the attacker, as with other phishing attacks, sent out plausible-sounding prompts directing employees to a website that mimicked […]
The post Reddit Hacked – Attackers Steal Internal Documents and Source Code appeared first on Cyber Security News.
https://cybersecuritynews.com/reddit-hacked/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/reddit-hacked/?utm_source=dlvr.it&utm_medium=blogger
Friday, February 10, 2023
OpenSSL Fixes Multiple New Security Flaws with Latest Update
The OpenSSL Project has released fixes to address several security flaws, including a high-severity bug in the open source encryption toolkit that could potentially expose users to malicious attacks.
Tracked as CVE-2023-0286, the issue relates to a case of type confusion that may permit an adversary to "read memory contents or enact a denial-of-service," the maintainers said in an advisory.
The
https://thehackernews.com/2023/02/openssl-fixes-multiple-new-security.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/openssl-fixes-multiple-new-security.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, February 9, 2023
Russian Hacker Pleads Guilty to Money Laundering Linked to Ryuk Ransomware
A Russian national on February 7, 2023, pleaded guilty in the U.S. to money laundering charges and for attempting to conceal the source of funds obtained in connection with Ryuk ransomware attacks.
Denis Mihaqlovic Dubnikov, 30, was arrested in Amsterdam in November 2021 before he was extradited from the Netherlands in August 2022. He is awaiting sentencing on April 11, 2023.
"Between at least
https://thehackernews.com/2023/02/russian-hacker-pleads-guilty-to-money.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/russian-hacker-pleads-guilty-to-money.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, February 8, 2023
Google to Announce Chat-GPT Rival On February 8 Event
There seems to be a lot of consternation on Google’s part at the prospect of a showdown with ChatGPT on the February 8 event. The search giant has been making moves that suggest it is preparing to enter the market for large language models, where ChatGPT is currently a dominant player. With its extensive resources […]
The post Google to Announce Chat-GPT Rival On February 8 Event appeared first on Cyber Security News.
https://cybersecuritynews.com/google-chat-gpt-rival/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/google-chat-gpt-rival/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, February 7, 2023
OpenSSH Releases Patch for New Pre-Auth Double Free Vulnerability
The maintainers of OpenSSH have released OpenSSH 9.2 to address a number of security bugs, including a memory safety vulnerability in the OpenSSH server (sshd).
Tracked as CVE-2023-25136, the shortcoming has been classified as a pre-authentication double free vulnerability that was introduced in version 9.1.
"This is not believed to be exploitable, and it occurs in the unprivileged pre-auth
https://thehackernews.com/2023/02/openssh-releases-patch-for-new-pre-auth.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/openssh-releases-patch-for-new-pre-auth.html?utm_source=dlvr.it&utm_medium=blogger
FormBook Malware Spreads via Malvertising Using MalVirt Loader to Evade Detection
An ongoing malvertising campaign is being used to distribute virtualized .NET loaders that are designed to deploy the FormBook information-stealing malware.
"The loaders, dubbed MalVirt, use obfuscated virtualization for anti-analysis and evasion along with the Windows Process Explorer driver for terminating processes," SentinelOne researchers Aleksandar Milenkoski and Tom Hegel said in a
https://thehackernews.com/2023/02/formbook-malware-spreads-via.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/formbook-malware-spreads-via.html?utm_source=dlvr.it&utm_medium=blogger
Monday, February 6, 2023
Secure Your CI/CD Pipeline with Secret Management Best Practices
CI/CD pipelines require a number of permissions to function, and they handle infrastructure and application secrets in most organizations. As a result, whoever manages to gain unauthorized access to your CI/CD pipeline gains virtually absolute power to compromise your entire infrastructure or introduce malicious code. Therefore, you should give safeguarding CI/CD pipelines top priority. What […]
The post Secure Your CI/CD Pipeline with Secret Management Best Practices appeared first on Cyber Security News.
https://cybersecuritynews.com/secure-your-ci-cd-pipeline/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/secure-your-ci-cd-pipeline/?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 5, 2023
PixPirate: New Android Banking Trojan Targeting Brazilian Financial Institutions
A new Android banking trojan has set its eyes on Brazilian financial institutions to commit fraud by leveraging the PIX payments platform.
Italian cybersecurity company Cleafy, which discovered the malware between the end of 2022 and the beginning of 2023, is tracking it under the name PixPirate.
"PixPirate belongs to the newest generation of Android banking trojan, as it can perform ATS (
https://thehackernews.com/2023/02/pixpirate-new-android-banking-trojan.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/pixpirate-new-android-banking-trojan.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, February 4, 2023
Atlassian's Jira Service Management Found Vulnerable to Critical Vulnerability
Atlassian has released fixes to resolve a critical security flaw in Jira Service Management Server and Data Center that could be abused by an attacker to pass off as another user and gain unauthorized access to susceptible instances.
The vulnerability is tracked as CVE-2023-22501 (CVSS score: 9.4) and has been described as a case of broken authentication with low attack complexity.
"An
https://thehackernews.com/2023/02/atlassians-jira-software-found.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/atlassians-jira-software-found.html?utm_source=dlvr.it&utm_medium=blogger
Friday, February 3, 2023
North Korean Hackers Exploit Unpatched Zimbra Devices in 'No Pineapple' Campaign
A new intelligence gathering campaign linked to the prolific North Korean state-sponsored Lazarus Group leveraged known security flaws in unpatched Zimbra devices to compromise victim systems.
That's according to Finnish cybersecurity company WithSecure (formerly F-Secure), which codenamed the incident No Pineapple in reference to an error message that's used in one of the backdoors.
Targets of
https://thehackernews.com/2023/02/north-korean-hackers-exploit-unpatched.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/north-korean-hackers-exploit-unpatched.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, February 2, 2023
Prilex PoS Malware Evolves to Block Contactless Payments to Steal from NFC Cards
The Brazilian threat actors behind an advanced and modular point-of-sale (PoS) malware known as Prilex have reared their head once again with new updates that allow it to block contactless payment transactions.
Russian cybersecurity firm Kaspersky said it detected three versions of Prilex (06.03.8080, 06.03.8072, and 06.03.8070) that are capable of targeting NFC-enabled credit cards, taking its
https://thehackernews.com/2023/02/prilex-pos-malware-evolves-to-block.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/02/prilex-pos-malware-evolves-to-block.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, February 1, 2023
Researchers Uncover Packer Used by Several Malware to Evade Detection for 6 Years
A shellcode-based packer dubbed TrickGate has been successfully operating without attracting notice for over six years, while enabling threat actors to deploy a wide range of malware such as TrickBot, Emotet, AZORult, Agent Tesla, FormBook, Cerber, Maze, and REvil over the years.
"TrickGate managed to stay under the radar for years because it is transformative – it undergoes changes periodically
https://thehackernews.com/2023/01/researchers-uncover-packer-that-helped.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/researchers-uncover-packer-that-helped.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)