Social media platform Parler says it will return in Q1 2024 under new owners, after its closure back in April this year This article has been indexed from Silicon UK Read the original article: Controversial Parler Platform Set For 2024…
Read more →
https://www.itsecuritynews.info/controversial-parler-platform-set-for-2024-return/?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 21, 2023
US Commerce Dept To Review Semiconductor Supply Chain
National security move, as the US Commerce Dept says it will launch survey of US semiconductor supply chain This article has been indexed from Silicon UK Read the original article: US Commerce Dept To Review Semiconductor Supply Chain
Read more →
https://www.itsecuritynews.info/us-commerce-dept-to-review-semiconductor-supply-chain/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/us-commerce-dept-to-review-semiconductor-supply-chain/?utm_source=dlvr.it&utm_medium=blogger
Weather Wonders: A Guide to Crafting a Dynamic App Using Weather APIs
By Owais Sultan Weather applications have become an integral part of our daily lives. These apps, which provide us with real-time… This is a post from HackRead.com Read the original post: Weather Wonders: A Guide to Crafting a Dynamic App…
Read more →
https://www.itsecuritynews.info/weather-wonders-a-guide-to-crafting-a-dynamic-app-using-weather-apis/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/weather-wonders-a-guide-to-crafting-a-dynamic-app-using-weather-apis/?utm_source=dlvr.it&utm_medium=blogger
Urgent: New Chrome Zero-Day Vulnerability Exploited in the Wild - Update ASAP
Google has rolled out security updates for the Chrome web browser to address a high-severity zero-day flaw that it said has been exploited in the wild.
The vulnerability, assigned the CVE identifier CVE-2023-7024, has been described as a heap-based buffer overflow bug in the WebRTC framework that could be exploited to result in program crashes or arbitrary code execution.
Clément
https://thehackernews.com/2023/12/urgent-new-chrome-zero-day.html?utm_source=dlvr.it&utm_medium=blogger
The vulnerability, assigned the CVE identifier CVE-2023-7024, has been described as a heap-based buffer overflow bug in the WebRTC framework that could be exploited to result in program crashes or arbitrary code execution.
Clément
https://thehackernews.com/2023/12/urgent-new-chrome-zero-day.html?utm_source=dlvr.it&utm_medium=blogger
What is Email Spoofing? – Email Threat Prevention Checklist 2024
A deceptive method used by malicious individuals to send emails with fictitious sender information is email spoofing. The attacker creates the impression that the email is coming from a reliable source, such as a reliable business or person, by changing the email’s header information, especially the “From” field. By convincing recipients that the email is […]
The post What is Email Spoofing? – Email Threat Prevention Checklist 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/email-spoofing/?utm_source=dlvr.it&utm_medium=blogger
The post What is Email Spoofing? – Email Threat Prevention Checklist 2024 appeared first on Cyber Security News.
https://cybersecuritynews.com/email-spoofing/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, December 20, 2023
Keeping the Lights On: Brazilian Power Utility Wins Cybersecurity Award for Securing Grid Network with Cisco
Utilities face stricter cybersecurity regulations and increasing cyberthreats. Learn how CPFL Energia’s OT and IT teams secured grid operations with Cisco Cyber Vision, built into Cisco industrial switches. This article has been indexed from Cisco Blogs Read the original article:…
Read more →
https://www.itsecuritynews.info/keeping-the-lights-on-brazilian-power-utility-wins-cybersecurity-award-for-securing-grid-network-with-cisco/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/keeping-the-lights-on-brazilian-power-utility-wins-cybersecurity-award-for-securing-grid-network-with-cisco/?utm_source=dlvr.it&utm_medium=blogger
Cisco and Nutanix Team Up in Response to Customer Demand: Another Win for Customer-Centric Innovation
At Cisco, we’re continually tuned into the demands and requirements of our customer base, and it’s this laser focus that has led to our most recent collaborative venture. We are thrilled to announce our new integration with Nutanix, a leader…
Read more →
https://www.itsecuritynews.info/cisco-and-nutanix-team-up-in-response-to-customer-demand-another-win-for-customer-centric-innovation/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/cisco-and-nutanix-team-up-in-response-to-customer-demand-another-win-for-customer-centric-innovation/?utm_source=dlvr.it&utm_medium=blogger
Okta to Acquire Israeli Startup Spera Security
Okta agreed to acquire Spera Security in a move broaden Okta’s Identity threat detection and security posture management capabilities. The post Okta to Acquire Israeli Startup Spera Security appeared first on SecurityWeek. This article has been indexed from SecurityWeek RSS…
Read more →
https://www.itsecuritynews.info/okta-to-acquire-israeli-startup-spera-security/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/okta-to-acquire-israeli-startup-spera-security/?utm_source=dlvr.it&utm_medium=blogger
Okta to Acquire Spera Security
In a landmark move, Okta, the leading Identity and Access Management (IAM) provider has announced its acquisition of Spera Security, a rising star in the Identity security space. Spera Security plays a strategic role in enhancing organizations’ cybersecurity defenses. The company focuses on unveiling threats beyond Identity Providers’ (IdPs) walls, offering insights into vulnerabilities within […]
The post Okta to Acquire Spera Security appeared first on Cyber Security News.
https://cybersecuritynews.com/okta-to-acquire-spera-security/?utm_source=dlvr.it&utm_medium=blogger
The post Okta to Acquire Spera Security appeared first on Cyber Security News.
https://cybersecuritynews.com/okta-to-acquire-spera-security/?utm_source=dlvr.it&utm_medium=blogger
How to Minimize Friction in the Cyber Compliance Certification Process
Certification has always been a great way for companies to establish trust with their customers. As modern companies gather increasing amounts of data, and as data privacy concerns mount, cyber compliance is now more important than ever. While there’s certainly an argument to be made that certification doesn’t necessarily make your company more secure, today’s […]
The post How to Minimize Friction in the Cyber Compliance Certification Process appeared first on Cyber Security News.
https://cybersecuritynews.com/cyber-compliance-certification/?utm_source=dlvr.it&utm_medium=blogger
The post How to Minimize Friction in the Cyber Compliance Certification Process appeared first on Cyber Security News.
https://cybersecuritynews.com/cyber-compliance-certification/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, December 19, 2023
The widening web of effective altruism in AI security | The AI Beat
A follow up on a VentureBeat story last week adds context about the web of effective altruism connections in AI security circles. This article has been indexed from Security News | VentureBeat Read the original article: The widening web of…
Read more →
https://www.itsecuritynews.info/the-widening-web-of-effective-altruism-in-ai-security-the-ai-beat/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/the-widening-web-of-effective-altruism-in-ai-security-the-ai-beat/?utm_source=dlvr.it&utm_medium=blogger
What Australia’s Digital ID Means to How Citizens Interact With Businesses Online
Australia is about to get a national online ID system — the Digital ID — which promises to improve the security and privacy of data online. However, concerns among Australians persist. This article has been indexed from Security | TechRepublic…
Read more →
https://www.itsecuritynews.info/what-australias-digital-id-means-to-how-citizens-interact-with-businesses-online/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/what-australias-digital-id-means-to-how-citizens-interact-with-businesses-online/?utm_source=dlvr.it&utm_medium=blogger
Partnering for Purpose: A Year in Focus
This is typically the time of year when we take time to reflect, and looking back, 2023 has been a wonderful year of fulfillment and purpose for me, specifically in my role leading Partnering for Purpose. This article has been…
Read more →
https://www.itsecuritynews.info/partnering-for-purpose-a-year-in-focus/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/partnering-for-purpose-a-year-in-focus/?utm_source=dlvr.it&utm_medium=blogger
New Windows Zero-click RCE Flaw Let Attackers Exploit Outlook Clients
Microsoft recently reported that CVE-2023-23397, a critical Outlook vulnerability, is currently being exploited in the wild by a Russian-state-sponsored threat actor known as Forrest Blizzard. This vulnerability allowed threat actors to exploit an Outlook client by extracting NTLM credentials while establishing a connection to the attacker-controlled server. Moreover, this vulnerability was also known to be […]
The post New Windows Zero-click RCE Flaw Let Attackers Exploit Outlook Clients appeared first on Cyber Security News.
https://cybersecuritynews.com/new-windows-zero-click-rce-flaw/?utm_source=dlvr.it&utm_medium=blogger
The post New Windows Zero-click RCE Flaw Let Attackers Exploit Outlook Clients appeared first on Cyber Security News.
https://cybersecuritynews.com/new-windows-zero-click-rce-flaw/?utm_source=dlvr.it&utm_medium=blogger
PikaBot Attacking Windows Machine via Malicious Search Ads
In the labyrinth of cyber threats that define the digital landscape, 2023 has witnessed the resurgence of a particularly pernicious foe — malicious advertisements, colloquially known as “malvertising.” This nefarious stratagem has set its sights on businesses, executing a sophisticated dance that sidesteps conventional security fortifications. At the forefront of this digital onslaught is the […]
The post PikaBot Attacking Windows Machine via Malicious Search Ads appeared first on Cyber Security News.
https://cybersecuritynews.com/pikabot-attacking-windows-machine/?utm_source=dlvr.it&utm_medium=blogger
The post PikaBot Attacking Windows Machine via Malicious Search Ads appeared first on Cyber Security News.
https://cybersecuritynews.com/pikabot-attacking-windows-machine/?utm_source=dlvr.it&utm_medium=blogger
Monday, December 18, 2023
Ransomware Gangs Are Collaborating To Attack Financial Services Firms
The Cyber-Extortion Trinity—the BianLian, White Rabbit, and Mario ransomware gangs—was observed by researchers working together to launch a joint extortion campaign against publicly traded financial services companies. Although these joint ransomware attacks are uncommon, they may grow more often due to Initial Access Brokers (IABs) working with various Dark Web groups. Law enforcement actions that establish networks […]
The post Ransomware Gangs Are Collaborating To Attack Financial Services Firms appeared first on Cyber Security News.
https://cybersecuritynews.com/ransomware-gangs-are-collaborating/?utm_source=dlvr.it&utm_medium=blogger
The post Ransomware Gangs Are Collaborating To Attack Financial Services Firms appeared first on Cyber Security News.
https://cybersecuritynews.com/ransomware-gangs-are-collaborating/?utm_source=dlvr.it&utm_medium=blogger
Beware: Experts Reveal New Details on Zero-Click Outlook RCE Exploits
Technical details have emerged about two now-patched security flaws in Microsoft Windows that could be chained by threat actors to achieve remote code execution on the Outlook email service sans any user interaction.
"An attacker on the internet can chain the vulnerabilities together to create a full, zero-click remote code execution (RCE) exploit against Outlook clients," Akamai security
https://thehackernews.com/2023/12/beware-experts-reveal-new-details-on.html?utm_source=dlvr.it&utm_medium=blogger
"An attacker on the internet can chain the vulnerabilities together to create a full, zero-click remote code execution (RCE) exploit against Outlook clients," Akamai security
https://thehackernews.com/2023/12/beware-experts-reveal-new-details-on.html?utm_source=dlvr.it&utm_medium=blogger
Top 7 Trends Shaping SaaS Security in 2024
Over the past few years, SaaS has developed into the backbone of corporate IT. Service businesses, such as medical practices, law firms, and financial services firms, are almost entirely SaaS based. Non-service businesses, including manufacturers and retailers, have about 70% of their software in the cloud.
These applications contain a wealth of data, from minimally sensitive general
https://thehackernews.com/2023/12/top-7-trends-shaping-saas-security-in.html?utm_source=dlvr.it&utm_medium=blogger
These applications contain a wealth of data, from minimally sensitive general
https://thehackernews.com/2023/12/top-7-trends-shaping-saas-security-in.html?utm_source=dlvr.it&utm_medium=blogger
Four U.S. Nationals Charged in $80 Million Pig Butchering Crypto Scam
Four U.S. nationals have been charged for participating in an illicit scheme that earned them more than $80 million via cryptocurrency investment scams.
The defendants – Lu Zhang, 36, of Alhambra, California; Justin Walker, 31, of Cypress, California; Joseph Wong, 32, Rosemead, California; and Hailong Zhu, 40, Naperville, Illinois – have been charged with conspiracy to commit money laundering,
https://thehackernews.com/2023/12/four-us-nationals-charged-in-80-million.html?utm_source=dlvr.it&utm_medium=blogger
The defendants – Lu Zhang, 36, of Alhambra, California; Justin Walker, 31, of Cypress, California; Joseph Wong, 32, Rosemead, California; and Hailong Zhu, 40, Naperville, Illinois – have been charged with conspiracy to commit money laundering,
https://thehackernews.com/2023/12/four-us-nationals-charged-in-80-million.html?utm_source=dlvr.it&utm_medium=blogger
CISA Urges Manufacturers Eliminate Default Passwords to Thwart Cyber Threats
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is urging manufacturers to get rid of default passwords on internet-exposed systems altogether, citing severe risks that could be exploited by malicious actors to gain initial access to, and move laterally within, organizations.
In an alert published last week, the agency called out Iranian threat actors affiliated with
https://thehackernews.com/2023/12/cisa-urges-manufacturers-eliminate.html?utm_source=dlvr.it&utm_medium=blogger
In an alert published last week, the agency called out Iranian threat actors affiliated with
https://thehackernews.com/2023/12/cisa-urges-manufacturers-eliminate.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, December 17, 2023
Hackers Steal Assets Worth $484,000 in Ledger Security Breach
Threat actors responsible for attacking Ledger’s connector library have stolen assets valued at approximately $484,000. This information was given by the blockchain analysis platform Lookonchain. Ledger has said that the security breach might have a large effect, possibly totalling hundreds…
Read more →
https://www.itsecuritynews.info/hackers-steal-assets-worth-484000-in-ledger-security-breach/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/hackers-steal-assets-worth-484000-in-ledger-security-breach/?utm_source=dlvr.it&utm_medium=blogger
Cybersecurity Incident Causes Outage at Lesotho’s Central Bank
Lesotho’s central bank is grappling with widespread disruptions following a cyberattack detected earlier this week. The landlocked country, surrounded by South Africa and home to over 2 million people, disclosed multiple statements acknowledging the impact of the recent cyber…
Read more →
https://www.itsecuritynews.info/cybersecurity-incident-causes-outage-at-lesothos-central-bank/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/cybersecurity-incident-causes-outage-at-lesothos-central-bank/?utm_source=dlvr.it&utm_medium=blogger
Microsoft Shuts Down a Criminal Ring Responsible for Creating Over 750 Million Fake Accounts
Microsoft Corp. has shut down a cybercrime group’s US-based infrastructure, which created more than 750 million fake accounts across the company’s services. Microsoft carried out the takedown with the support of Arkose Labs Inc., a venture-backed cybersecurity firm. The…
Read more →
https://www.itsecuritynews.info/microsoft-shuts-down-a-criminal-ring-responsible-for-creating-over-750-million-fake-accounts/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/microsoft-shuts-down-a-criminal-ring-responsible-for-creating-over-750-million-fake-accounts/?utm_source=dlvr.it&utm_medium=blogger
Securing Generative AI: Navigating Risks and Strategies
The introduction of generative AI has caused a paradigm change in the rapidly developing field of artificial intelligence, posing both unprecedented benefits and problems for companies. The need to strengthen security measures is becoming more and more apparent as these…
Read more →
https://www.itsecuritynews.info/securing-generative-ai-navigating-risks-and-strategies/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/securing-generative-ai-navigating-risks-and-strategies/?utm_source=dlvr.it&utm_medium=blogger
MongoDB Suffers Security Breach, Exposing Customer Data
MongoDB on Saturday disclosed it's actively investigating a security incident that has led to unauthorized access to "certain" corporate systems, resulting in the exposure of customer account metadata and contact information.
The American database software company said it first detected anomalous activity on December 13, 2023, and that it immediately activated its incident response
https://thehackernews.com/2023/12/mongodb-suffers-security-breach.html?utm_source=dlvr.it&utm_medium=blogger
The American database software company said it first detected anomalous activity on December 13, 2023, and that it immediately activated its incident response
https://thehackernews.com/2023/12/mongodb-suffers-security-breach.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, December 16, 2023
How to Defend Against Digital Cyberthreats This Holiday Season
This post doesn’t have text content, please click on the link below to view the original article. This article has been indexed from Blog Read the original article: How to Defend Against Digital Cyberthreats This Holiday Season
Read more →
https://www.itsecuritynews.info/how-to-defend-against-digital-cyberthreats-this-holiday-season/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/how-to-defend-against-digital-cyberthreats-this-holiday-season/?utm_source=dlvr.it&utm_medium=blogger
Akamai?s Perspective on December?s Patch Tuesday 2023
This post doesn’t have text content, please click on the link below to view the original article. This article has been indexed from Blog Read the original article: Akamai?s Perspective on December?s Patch Tuesday 2023
Read more →
https://www.itsecuritynews.info/akamais-perspective-on-decembers-patch-tuesday-2023/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/akamais-perspective-on-decembers-patch-tuesday-2023/?utm_source=dlvr.it&utm_medium=blogger
DEF CON 31 – Joe Sullivan’s ‘A Different Uber Post Mortem’
Many thanks to DEF CON 31 for publishing their terrific DefCon Conference 31 presenters content. Originating from the conference events at Caesars Forum, Flamingo, Harrah’s and Linq in Las Vegas, Nevada; via the organizations YouTube channel. Permalink The post DEF…
Read more →
https://www.itsecuritynews.info/def-con-31-joe-sullivans-a-different-uber-post-mortem/?utm_source=dlvr.it&utm_medium=blogger
Read more →
https://www.itsecuritynews.info/def-con-31-joe-sullivans-a-different-uber-post-mortem/?utm_source=dlvr.it&utm_medium=blogger
China's MIIT Introduces Color-Coded Action Plan for Data Security Incidents
China's Ministry of Industry and Information Technology (MIIT) on Friday unveiled draft proposals detailing its plans to tackle data security events in the country using a color-coded system.
The effort is designed to "improve the comprehensive response capacity for data security incidents, to ensure timely and effective control, mitigation and elimination of hazards and losses caused
https://thehackernews.com/2023/12/chinas-miit-introduces-color-coded.html?utm_source=dlvr.it&utm_medium=blogger
The effort is designed to "improve the comprehensive response capacity for data security incidents, to ensure timely and effective control, mitigation and elimination of hazards and losses caused
https://thehackernews.com/2023/12/chinas-miit-introduces-color-coded.html?utm_source=dlvr.it&utm_medium=blogger
Microsoft Warns of Storm-0539: The Rising Threat Behind Holiday Gift Card Frauds
Microsoft is warning of an uptick in malicious activity from an emerging threat cluster it's tracking as Storm-0539 for orchestrating gift card fraud and theft via highly sophisticated email and SMS phishing attacks against retail entities during the holiday shopping season.
The goal of the attacks is to propagate booby-trapped links that direct victims to adversary-in-the-middle (AiTM
https://thehackernews.com/2023/12/microsoft-warns-of-storm-0539-rising.html?utm_source=dlvr.it&utm_medium=blogger
The goal of the attacks is to propagate booby-trapped links that direct victims to adversary-in-the-middle (AiTM
https://thehackernews.com/2023/12/microsoft-warns-of-storm-0539-rising.html?utm_source=dlvr.it&utm_medium=blogger
Friday, December 15, 2023
New Security Vulnerabilities Uncovered in pfSense Firewall Software - Patch Now
Multiple security vulnerabilities have been discovered in the open-source Netgate pfSense firewall solution called pfSense that could be chained by an attacker to execute arbitrary commands on susceptible appliances.
The issues relate to two reflected cross-site scripting (XSS) bugs and one command injection flaw, according to new findings from Sonar.
"Security inside a local network is often
https://thehackernews.com/2023/12/new-security-vulnerabilities-uncovered.html?utm_source=dlvr.it&utm_medium=blogger
The issues relate to two reflected cross-site scripting (XSS) bugs and one command injection flaw, according to new findings from Sonar.
"Security inside a local network is often
https://thehackernews.com/2023/12/new-security-vulnerabilities-uncovered.html?utm_source=dlvr.it&utm_medium=blogger
Rhadamanthys – A Fast-evolving Multi-layer Malware Sold on The Dark Web
Threat actors make use of fast-evolving multi-layer malware for their complexity and sophistication, as they offer the ability to rapidly adapt and change their code. To make analysis and countermeasures more difficult, this sophisticated type of malware often employs the following key things:- Cybersecurity researchers at Check Point recently discovered the Rhadamanthys, an information stealer […]
The post Rhadamanthys – A Fast-evolving Multi-layer Malware Sold on The Dark Web appeared first on Cyber Security News.
https://cybersecuritynews.com/rhadamanthys-malware-sold-dark-web/?utm_source=dlvr.it&utm_medium=blogger
The post Rhadamanthys – A Fast-evolving Multi-layer Malware Sold on The Dark Web appeared first on Cyber Security News.
https://cybersecuritynews.com/rhadamanthys-malware-sold-dark-web/?utm_source=dlvr.it&utm_medium=blogger
Research Discovered 116 Malicious PyPI Packages Downloaded Over 10,000 Times
A cluster of malicious Python projects has been identified in PyPI, the official Python PyPI package repository, which targets both Windows and Linux systems and often deploys a custom backdoor. In certain instances, the ultimate payload consists of a simplified clipboard monitor designed to steal cryptocurrencies, a version of the notorious W4SP Stealer, or both. In 53 […]
The post Research Discovered 116 Malicious PyPI Packages Downloaded Over 10,000 Times appeared first on Cyber Security News.
https://cybersecuritynews.com/116-malicious-pypi-packages/?utm_source=dlvr.it&utm_medium=blogger
The post Research Discovered 116 Malicious PyPI Packages Downloaded Over 10,000 Times appeared first on Cyber Security News.
https://cybersecuritynews.com/116-malicious-pypi-packages/?utm_source=dlvr.it&utm_medium=blogger
Multiple Flaws in Dell PowerProtect Products Let Attackers Execute OS Commands
Multiple vulnerabilities have been discovered in Dell’s PowerProtect, which were associated with SQL injection, cross-site scripting (XSS), privilege escalation, command injection, and path tracing. The severity for these vulnerabilities ranges between 4.3 (Medium) and 8.8 (High). Relevant CVEs have been assigned to all these vulnerabilities, with CVE-2023-44286 associated with Cross-Site Scripting having the highest severity […]
The post Multiple Flaws in Dell PowerProtect Products Let Attackers Execute OS Commands appeared first on Cyber Security News.
https://cybersecuritynews.com/dell-powerprotect-products-flaw/?utm_source=dlvr.it&utm_medium=blogger
The post Multiple Flaws in Dell PowerProtect Products Let Attackers Execute OS Commands appeared first on Cyber Security News.
https://cybersecuritynews.com/dell-powerprotect-products-flaw/?utm_source=dlvr.it&utm_medium=blogger
New Hacker Group Uses SQL Injection to Hack Companies in APAC Region
A new threat actor has been discovered to be using SQL injection attacks to gain unauthorized access to organizations in the APAC region. This threat actor has been named “GambleForce” and is using publicly available open-source instruments that are generally used by penetration testers. The threat actor has targeted more than 20 websites, including government, […]
The post New Hacker Group Uses SQL Injection to Hack Companies in APAC Region appeared first on Cyber Security News.
https://cybersecuritynews.com/hacker-group-uses-sql-injection/?utm_source=dlvr.it&utm_medium=blogger
The post New Hacker Group Uses SQL Injection to Hack Companies in APAC Region appeared first on Cyber Security News.
https://cybersecuritynews.com/hacker-group-uses-sql-injection/?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 14, 2023
New Pierogi++ Malware by Gaza Cyber Gang Targeting Palestinian Entities
A pro-Hamas threat actor known as Gaza Cyber Gang is targeting Palestinian entities using an updated version of a backdoor dubbed Pierogi.
The findings come from SentinelOne, which has given the malware the name Pierogi++ owing to the fact that it's implemented in the C++ programming language unlike its Delphi- and Pascal-based predecessor.
"Recent Gaza Cybergang activities show
https://thehackernews.com/2023/12/new-pierogi-malware-by-gaza-cyber-gang.html?utm_source=dlvr.it&utm_medium=blogger
The findings come from SentinelOne, which has given the malware the name Pierogi++ owing to the fact that it's implemented in the C++ programming language unlike its Delphi- and Pascal-based predecessor.
"Recent Gaza Cybergang activities show
https://thehackernews.com/2023/12/new-pierogi-malware-by-gaza-cyber-gang.html?utm_source=dlvr.it&utm_medium=blogger
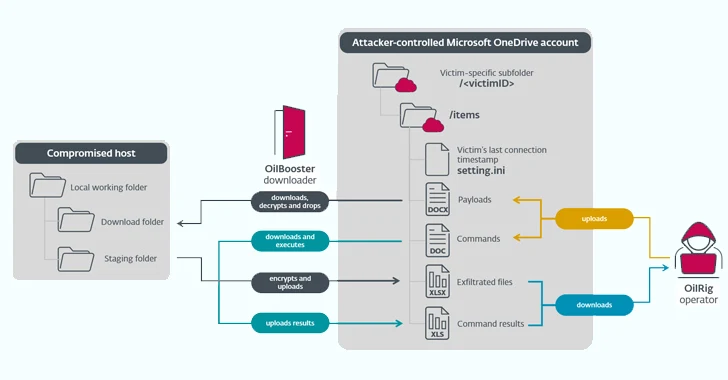
Iranian State-Sponsored OilRig Group Deploys 3 New Malware Downloaders
The Iranian state-sponsored threat actor known as OilRig deployed three different downloader malware throughout 2022 to maintain persistent access to victim organizations located in Israel.
The three new downloaders have been named ODAgent, OilCheck, and OilBooster by Slovak cybersecurity company ESET. The attacks also involved the use of an updated version of a known OilRig downloader
https://thehackernews.com/2023/12/iranian-state-sponsored-oilrig-group.html?utm_source=dlvr.it&utm_medium=blogger
The three new downloaders have been named ODAgent, OilCheck, and OilBooster by Slovak cybersecurity company ESET. The attacks also involved the use of an updated version of a known OilRig downloader
https://thehackernews.com/2023/12/iranian-state-sponsored-oilrig-group.html?utm_source=dlvr.it&utm_medium=blogger
Reimagining Network Pentesting With Automation
Network penetration testing plays a crucial role in protecting businesses in the ever-evolving world of cybersecurity. Yet, business leaders and IT pros have misconceptions about this process, which impacts their security posture and decision-making.
This blog acts as a quick guide on network penetration testing, explaining what it is, debunking common myths and reimagining its role in
https://thehackernews.com/2023/12/reimagining-network-pentesting-with.html?utm_source=dlvr.it&utm_medium=blogger
This blog acts as a quick guide on network penetration testing, explaining what it is, debunking common myths and reimagining its role in
https://thehackernews.com/2023/12/reimagining-network-pentesting-with.html?utm_source=dlvr.it&utm_medium=blogger
Microsoft Takes Legal Action to Crack Down on Storm-1152's Cybercrime Network
Microsoft on Wednesday said it obtained a court order to seize infrastructure set up by a group called Storm-1152 that peddled roughly 750 million fraudulent Microsoft accounts and tools through a network of bogus websites and social media pages to other criminal actors, netting them millions of dollars in illicit revenue.
"Fraudulent online accounts act as the gateway to a host of cybercrime,
https://thehackernews.com/2023/12/microsoft-takes-legal-action-to-crack.html?utm_source=dlvr.it&utm_medium=blogger
"Fraudulent online accounts act as the gateway to a host of cybercrime,
https://thehackernews.com/2023/12/microsoft-takes-legal-action-to-crack.html?utm_source=dlvr.it&utm_medium=blogger
BazaCall Phishing Scammers Now Leveraging Google Forms for Deception
The threat actors behind the BazaCall call back phishing attacks have been observed leveraging Google Forms to lend the scheme a veneer of credibility.
The method is an "attempt to elevate the perceived authenticity of the initial malicious emails," cybersecurity firm Abnormal Security said in a report published today.
BazaCall (aka BazarCall), which was first
https://thehackernews.com/2023/12/bazacall-phishing-scammers-now.html?utm_source=dlvr.it&utm_medium=blogger
The method is an "attempt to elevate the perceived authenticity of the initial malicious emails," cybersecurity firm Abnormal Security said in a report published today.
BazaCall (aka BazarCall), which was first
https://thehackernews.com/2023/12/bazacall-phishing-scammers-now.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, December 13, 2023
Recruiters Beware! Hackers Deliver Malware Posing as Job Applicant
Threat actors have been targeting recruiters disguised as job applicants to deliver their malware. Though this method is not unique, the technique and attack vectors have been noted to have changed from their previous methods. TA4557 is a highly skilled, financially motivated threat actor who primarily uses sophisticated social engineering to lure victims. This threat […]
The post Recruiters Beware! Hackers Deliver Malware Posing as Job Applicant appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-targeting-recruiters/?utm_source=dlvr.it&utm_medium=blogger
The post Recruiters Beware! Hackers Deliver Malware Posing as Job Applicant appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-targeting-recruiters/?utm_source=dlvr.it&utm_medium=blogger
Google Using Clang Sanitizers to Protect Android Against Cellular Baseband Vulnerabilities
Google is highlighting the role played by Clang sanitizers in hardening the security of the cellular baseband in the Android operating system and preventing specific kinds of vulnerabilities.
This comprises Integer Overflow Sanitizer (IntSan) and BoundsSanitizer (BoundSan), both of which are part of UndefinedBehaviorSanitizer (UBSan), a tool designed to catch various kinds of
https://thehackernews.com/2023/12/google-using-clang-sanitizers-to.html?utm_source=dlvr.it&utm_medium=blogger
This comprises Integer Overflow Sanitizer (IntSan) and BoundsSanitizer (BoundSan), both of which are part of UndefinedBehaviorSanitizer (UBSan), a tool designed to catch various kinds of
https://thehackernews.com/2023/12/google-using-clang-sanitizers-to.html?utm_source=dlvr.it&utm_medium=blogger
How to Analyze Malware’s Network Traffic in A Sandbox
Malware analysis encompasses a broad range of activities, including examining the malware's network traffic. To be effective at it, it's crucial to understand the common challenges and how to overcome them. Here are three prevalent issues you may encounter and the tools you'll need to address them.
Decrypting HTTPS traffic
Hypertext Transfer Protocol Secure (HTTPS), the protocol for secure
https://thehackernews.com/2023/12/how-to-analyze-malwares-network-traffic.html?utm_source=dlvr.it&utm_medium=blogger
Decrypting HTTPS traffic
Hypertext Transfer Protocol Secure (HTTPS), the protocol for secure
https://thehackernews.com/2023/12/how-to-analyze-malwares-network-traffic.html?utm_source=dlvr.it&utm_medium=blogger
Hackers Planting Credit Card Skimmers Inside Google Tag Manager Scripts
Recently, it has been reported that Magecart Veteran ATMZOW has found 40 new domains of Google Tag Manager. As a result, thousands of websites have been affected by this security breach. Hackers enjoy Google Tag Manager because millions of websites use it, and it allows them to insert HTML code and custom scripts using a […]
The post Hackers Planting Credit Card Skimmers Inside Google Tag Manager Scripts appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-planting-credit-card-skimmers/?utm_source=dlvr.it&utm_medium=blogger
The post Hackers Planting Credit Card Skimmers Inside Google Tag Manager Scripts appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-planting-credit-card-skimmers/?utm_source=dlvr.it&utm_medium=blogger
New Editbot Stealer in Action; Stealing Browser Passwords & Cookies
A new malicious campaign, Editbot Stealer, was discovered in which threat actors use WinRAR archive files with minimal detection to perform a multi-stage attack. Threat actors have been utilizing the theme of “defective product to be sent back” to lure users to their deceptive websites. However, the malicious WinRAR archive used by the threat actors […]
The post New Editbot Stealer in Action; Stealing Browser Passwords & Cookies appeared first on Cyber Security News.
https://cybersecuritynews.com/new-editbot-stealer/?utm_source=dlvr.it&utm_medium=blogger
The post New Editbot Stealer in Action; Stealing Browser Passwords & Cookies appeared first on Cyber Security News.
https://cybersecuritynews.com/new-editbot-stealer/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, December 12, 2023
Apple Releases Security Updates to Patch Critical iOS and macOS Security Flaws
Apple on Monday released security patches for iOS, iPadOS, macOS, tvOS, watchOS, and Safari web browser to address multiple security flaws, in addition to backporting fixes for two recently disclosed zero-days to older devices.
This includes updates for 12 security vulnerabilities in iOS and iPadOS spanning AVEVideoEncoder, ExtensionKit, Find My, ImageIO, Kernel, Safari
https://thehackernews.com/2023/12/apple-releases-security-updates-to.html?utm_source=dlvr.it&utm_medium=blogger
This includes updates for 12 security vulnerabilities in iOS and iPadOS spanning AVEVideoEncoder, ExtensionKit, Find My, ImageIO, Kernel, Safari
https://thehackernews.com/2023/12/apple-releases-security-updates-to.html?utm_source=dlvr.it&utm_medium=blogger
New Critical RCE Vulnerability Discovered in Apache Struts 2 - Patch Now
Apache has released a security advisory warning of a critical security flaw in the Struts 2 open-source web application framework that could result in remote code execution.
Tracked as CVE-2023-50164, the vulnerability is rooted in a flawed "file upload logic" that could enable unauthorized path traversal and could be exploited under the circumstances to upload a malicious file
https://thehackernews.com/2023/12/new-critical-rce-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
Tracked as CVE-2023-50164, the vulnerability is rooted in a flawed "file upload logic" that could enable unauthorized path traversal and could be exploited under the circumstances to upload a malicious file
https://thehackernews.com/2023/12/new-critical-rce-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
Researchers Unmask Sandman APT's Hidden Link to China-Based KEYPLUG Backdoor
Tactical and targeting overlaps have been discovered between the enigmatic advanced persistent threat (APT) called Sandman and a China-based threat cluster that's known to use a backdoor known as KEYPLUG.
The assessment comes jointly from SentinelOne, PwC, and the Microsoft Threat Intelligence team based on the fact that the adversary's Lua-based malware LuaDream and KEYPLUG have been
https://thehackernews.com/2023/12/researchers-unmask-sandman-apts-hidden.html?utm_source=dlvr.it&utm_medium=blogger
The assessment comes jointly from SentinelOne, PwC, and the Microsoft Threat Intelligence team based on the fact that the adversary's Lua-based malware LuaDream and KEYPLUG have been
https://thehackernews.com/2023/12/researchers-unmask-sandman-apts-hidden.html?utm_source=dlvr.it&utm_medium=blogger
Lazarus Group Using Log4j Exploits to Deploy Remote Access Trojans
The notorious North Korea-linked threat actor known as the Lazarus Group has been attributed to a new global campaign that involves the opportunistic exploitation of security flaws in Log4j to deploy previously undocumented remote access trojans (RATs) on compromised hosts.
Cisco Talos is tracking the activity under the name Operation Blacksmith, noting the use of three DLang-based
https://thehackernews.com/2023/12/lazarus-group-using-log4j-exploits-to.html?utm_source=dlvr.it&utm_medium=blogger
Cisco Talos is tracking the activity under the name Operation Blacksmith, noting the use of three DLang-based
https://thehackernews.com/2023/12/lazarus-group-using-log4j-exploits-to.html?utm_source=dlvr.it&utm_medium=blogger
Playbook: Your First 100 Days as a vCISO - 5 Steps to Success
In an increasingly digital world, no organization is spared from cyber threats. Yet, not every organization has the luxury of hiring a full-time, in-house CISO. This gap in cybersecurity leadership is where you, as a vCISO, come in. You are the person who will establish, develop, and solidify the organization's cybersecurity infrastructure, blending strategic guidance with actionable
https://thehackernews.com/2023/12/playbook-your-first-100-days-as-vciso-5.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/12/playbook-your-first-100-days-as-vciso-5.html?utm_source=dlvr.it&utm_medium=blogger
Monday, December 11, 2023
New 5G Modem Flaws Affect iOS Devices and Android Models from Major Brands
A collection of security flaws in the firmware implementation of 5G mobile network modems from major chipset vendors such as MediaTek and Qualcomm impact USB and IoT modems as well as hundreds of smartphone models running Android and iOS.
Of the 14 flaws – collectively called 5Ghoul (a combination of "5G" and "Ghoul") – 10 affect 5G modems from the two companies, out of which three
https://thehackernews.com/2023/12/new-5g-modems-flaws-affect-ios-devices.html?utm_source=dlvr.it&utm_medium=blogger
Of the 14 flaws – collectively called 5Ghoul (a combination of "5G" and "Ghoul") – 10 affect 5G modems from the two companies, out of which three
https://thehackernews.com/2023/12/new-5g-modems-flaws-affect-ios-devices.html?utm_source=dlvr.it&utm_medium=blogger
N. Korea's Kimsuky Targeting South Korean Research Institutes with Backdoor Attacks
The North Korean threat actor known as Kimsuky has been observed targeting research institutes in South Korea as part of a spear-phishing campaign with the ultimate goal of distributing backdoors on compromised systems.
"The threat actor ultimately uses a backdoor to steal information and execute commands," the AhnLab Security Emergency Response Center (ASEC) said in an
https://thehackernews.com/2023/12/n-korean-kimsuky-targeting-south-korean.html?utm_source=dlvr.it&utm_medium=blogger
"The threat actor ultimately uses a backdoor to steal information and execute commands," the AhnLab Security Emergency Response Center (ASEC) said in an
https://thehackernews.com/2023/12/n-korean-kimsuky-targeting-south-korean.html?utm_source=dlvr.it&utm_medium=blogger
Ransomware-as-a-Service: The Growing Threat You Can't Ignore
Ransomware attacks have become a significant and pervasive threat in the ever-evolving realm of cybersecurity. Among the various iterations of ransomware, one trend that has gained prominence is Ransomware-as-a-Service (RaaS). This alarming development has transformed the cybercrime landscape, enabling individuals with limited technical expertise to carry out devastating attacks.
https://thehackernews.com/2023/12/ransomware-as-service-growing-threat.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2023/12/ransomware-as-service-growing-threat.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)