Over a dozen security flaws have been discovered in baseboard management controller (BMC) firmware from Lanner that could expose operational technology (OT) and internet of things (IoT) networks to remote attacks.
BMC refers to a specialized service processor, a system-on-chip (SoC), that's found in server motherboards and is used for remote monitoring and management of a host system, including
https://thehackernews.com/2022/11/over-dozen-new-bmc-firmware-flaws.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, November 30, 2022
Tuesday, November 29, 2022
Massive Twitter Breach – Over 5.4 Million users’ Data Leaked Online
It has been discovered recently that over 5.4 million personal records of Twitter users have been stolen by threat actors and publicly exposed on a hacker forum for free. While to accomplish this illicit activity threat actors exploited an API vulnerability that was fixed in January. On the popular hacking forum, Breached Forums, the threat […]
The post Massive Twitter Breach – Over 5.4 Million users’ Data Leaked Online appeared first on Cyber Security News.
https://cybersecuritynews.com/massive-twitter-breach/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/massive-twitter-breach/?utm_source=dlvr.it&utm_medium=blogger
Monday, November 28, 2022
Compromised Data of Over 9 Million Health Insurance Users Is Being Exposed On the Dark Web
After hitting Australian telecommunications company Optus, in which the information of over 9 million users has been exposed, cybercriminals have victimized another company — Medibank, one of the largest Australian insurance companies. Following the data breach on Medibank, threat actors have released the personal health information of millions of users they obtained in the attack. […]
The post Compromised Data of Over 9 Million Health Insurance Users Is Being Exposed On the Dark Web appeared first on Cyber Security News.
https://cybersecuritynews.com/health-insurance-users-is-being-exposed-on-the-dark-web/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/health-insurance-users-is-being-exposed-on-the-dark-web/?utm_source=dlvr.it&utm_medium=blogger
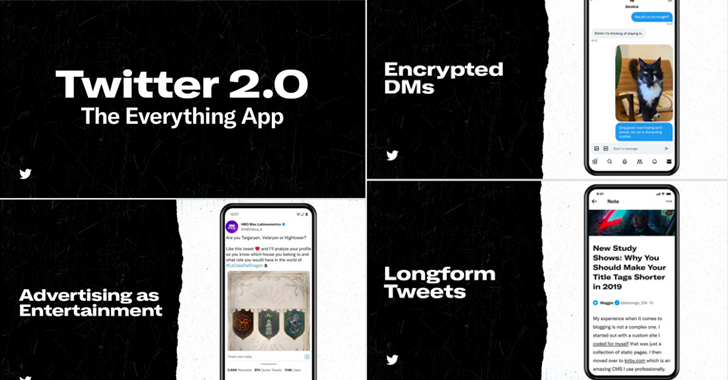
Elon Musk Confirms Twitter 2.0 will Bring End-to-End Encryption to Direct Messages
Twitter chief executive Elon Musk confirmed plans for end-to-end encryption (E2EE) for direct messages on the platform.
The feature is part of Musk's vision for Twitter 2.0, which is expected to be what's called an "everything app." Other functionalities include longform tweets and payments, according to a slide deck shared by Musk over the weekend.
The company's plans for
https://thehackernews.com/2022/11/elon-musk-confirms-twitter-20-will.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/elon-musk-confirms-twitter-20-will.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, November 27, 2022
Reasons for Being Updated ISO 27001 Crucial For Business Security
The supplier of the UK’s National Health Service, Advanced, faced a cyberattack on 4 august 2022 in the morning. It worked as a vicious example for an alerting situation: “how much a well-regulated set of rules and controls are…
Read more →
The post Reasons for Being Updated ISO 27001 Crucial For Business Security first appeared on IT Security News.
https://www.itsecuritynews.info/reasons-for-being-updated-iso-27001-crucial-for-business-security/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/reasons-for-being-updated-iso-27001-crucial-for-business-security/?utm_source=dlvr.it&utm_medium=blogger
All You Need to Know About Emotet in 2022
For 6 months, the infamous Emotet botnet has shown almost no activity, and now it's distributing malicious spam. Let's dive into details and discuss all you need to know about the notorious malware to combat it.
Why is everyone scared of Emotet?
Emotet is by far one of the most dangerous trojans ever created. The malware became a very destructive program as it grew in scale and sophistication.
https://thehackernews.com/2022/11/all-you-need-to-know-about-emotet-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/all-you-need-to-know-about-emotet-in.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, November 26, 2022
Dell, HP, and Lenovo Devices Found Using Outdated OpenSSL Versions
An analysis of firmware images across devices from Dell, HP, and Lenovo has revealed the presence of outdated versions of the OpenSSL cryptographic library, underscoring a supply chain risk.
EFI Development Kit, aka EDK, is an open source implementation of the Unified Extensible Firmware Interface (UEFI), which functions as an interface between the operating system and the firmware embedded in
https://thehackernews.com/2022/11/dell-hp-and-lenovo-devices-found-using.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/dell-hp-and-lenovo-devices-found-using.html?utm_source=dlvr.it&utm_medium=blogger
Friday, November 25, 2022
Ducktail Malware Operation Evolves with New Malicious Capabilities
The operators of the Ducktail information stealer have demonstrated a "relentless willingness to persist" and continued to update their malware as part of an ongoing financially driven campaign.
"The malware is designed to steal browser cookies and take advantage of authenticated Facebook sessions to steal information from the victim's Facebook account," WithSecure researcher Mohammad Kazem
https://thehackernews.com/2022/11/ducktail-malware-operation-evolves-with.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/ducktail-malware-operation-evolves-with.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, November 24, 2022
King Of Malware “Emotet” Launching Aggressive Attack Via XLS Doc & New Payloads
Emotet, An infamous banking trojan-based malware family with a sophisticated attack background, returns with a new attack strain via XLS documents using targeted phishing emails and delivers the new IcedID and Bumblebee payloads. Emotet built its infrastructure over the year and started its aggressive attack in later 2021, also becoming highly active in a short […]
The post King Of Malware “Emotet” Launching Aggressive Attack Via XLS Doc & New Payloads appeared first on Cyber Security News.
https://cybersecuritynews.com/king-of-malware-emotet/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/king-of-malware-emotet/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, November 23, 2022
U.S. Authorities Seize Domains Used in 'Pig butchering' Cryptocurrency Scams
The U.S. Justice Department (DoJ) on Monday announced the takedown of seven domain names in connection to a "pig butchering" cryptocurrency scam. The fraudulent scheme, which operated from May to August 2022, netted the actors over $10 million from five victims, the DoJ said.
Pig butchering, also called Sha Zhu Pan, is a type of scam in which swindlers lure unsuspecting investors into sending
https://thehackernews.com/2022/11/us-authorities-seize-domains-used-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/us-authorities-seize-domains-used-in.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, November 22, 2022
Google Wins Lawsuit Against Russians Linked to Blockchain-based Glupteba Botnet
Google has won a lawsuit filed against two Russian nationals in connection with the operation of a botnet called Glupteba, the company said last week.
The U.S. District Court for the Southern District of New York imposed monetary sanctions against the defendants and their U.S.-based legal counsel. The defendants have also been asked to pay Google's attorney fees. The defendants' move to press
https://thehackernews.com/2022/11/google-wins-lawsuit-against-russians.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/google-wins-lawsuit-against-russians.html?utm_source=dlvr.it&utm_medium=blogger
Monday, November 21, 2022
Google Identifies 34 Cracked Versions of Popular Cobalt Strike Hacking Toolkit in the Wild
Google Cloud last week disclosed that it identified 34 different hacked release versions of the Cobalt Strike tool in the wild, the earliest of which shipped in November 2012.
The versions, spanning 1.44 to 4.7, add up to a total of 275 unique JAR files, according to findings from the Google Cloud Threat Intelligence (GCTI) team. The latest version of Cobalt Strike is version 4.7.2.
Cobalt
https://thehackernews.com/2022/11/google-identifies-34-cracked-versions.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/google-identifies-34-cracked-versions.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, November 20, 2022
Indian Government Publishes Draft of Digital Personal Data Protection Bill 2022
The Indian government on Friday released a draft version of the much-awaited data protection regulation, making it the fourth such effort since it was first proposed in July 2018.
The Digital Personal Data Protection Bill, 2022, as it's called, aims to secure personal data, while also seeking users' consent in what the draft claims is "clear and plain language" describing the exact kinds of
https://thehackernews.com/2022/11/indian-government-publishes-draft-of.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/indian-government-publishes-draft-of.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, November 19, 2022
Meta Fired Several Employees For Hijacking Facebook and Instagram User Accounts
As a result of hijacking the Facebook and Instagram accounts of users over the course of the last year, Meta has fired more than two dozen employees and contractors. A source familiar with the matter and internal documents indicate that some cases involved bribes being offered. On a regular basis, fraudsters target online platforms as […]
The post Meta Fired Several Employees For Hijacking Facebook and Instagram User Accounts appeared first on Cyber Security News.
https://cybersecuritynews.com/meta-fired-several-employees-for-hijacking-facebook-and-instagram-user-accounts/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/meta-fired-several-employees-for-hijacking-facebook-and-instagram-user-accounts/?utm_source=dlvr.it&utm_medium=blogger
Friday, November 18, 2022
100 Apps, Endless Security Checks
On average, organizations report using 102 business-critical SaaS applications, enabling operations of most departments across an organization, such as IT and Security, Sales, Marketing, R&D, Product Management, HR, Legal, Finance, and Enablement. An attack can come from any app, no matter how robust the app is.Without visibility and control over a critical mass of an organization’s entire SaaS
https://thehackernews.com/2022/11/100-apps-endless-security-checks.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/100-apps-endless-security-checks.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, November 17, 2022
Warning: New RapperBot Campaign Aims to Launch DDoS Attacks at Game Servers
Cybersecurity researchers have unearthed new samples of malware called RapperBot that are being used to build a botnet capable of launching Distributed Denial of Service (DDoS) attacks against game servers.
"In fact, it turns out that this campaign is less like RapperBot than an older campaign that appeared in February and then mysteriously disappeared in the middle of April," Fortinet
https://thehackernews.com/2022/11/warning-new-rapperbot-campaign-aims-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/warning-new-rapperbot-campaign-aims-to.html?utm_source=dlvr.it&utm_medium=blogger
Retesting: A Re-Pentesting Towards More Secure Products For Red & Blue Teamers
Let’s examine how rigorous retesting of products during a pentest engagement can make products more secure and what goes into performing efficient retesting. Introduction: Why Retesting? First of all, let’s clarify what retesting is. Basically, it’s the very last phase of pentesting and a quite crucial one. After the final report with all found vulnerabilities […]
The post Retesting: A Re-Pentesting Towards More Secure Products For Red & Blue Teamers appeared first on Cyber Security News.
https://cybersecuritynews.com/retesting/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/retesting/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, November 16, 2022
Researchers Say China State-backed Hackers Breached a Digital Certificate Authority
A suspected Chinese state-sponsored actor breached a digital certificate authority as well as government and defense agencies located in different countries in Asia as part of an ongoing campaign since at least March 2022.
Symantec, by Broadcom Software, linked the attacks to an adversarial group it tracks under the name Billbug, citing the use of tools previously attributed to this actor. The
https://thehackernews.com/2022/11/researchers-say-china-state-backed.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/researchers-say-china-state-backed.html?utm_source=dlvr.it&utm_medium=blogger
Billbug – APT Hackers Group Attack Digital Cert Authority to Intercept The HTTPS Traffic
Researchers uncovered that State-Sponsors APT hackers called “Billbug” attacked and compromise the digital certificate authority in multiple Asian countries along with other government and defense agencies. An ongoing campaign attributed to the infamous APT group Billbug, also known as Lotus Blossom and Thrip. This APT group has been active since 2009, and it has previous […]
The post Billbug – APT Hackers Group Attack Digital Cert Authority to Intercept The HTTPS Traffic appeared first on Cyber Security News.
https://cybersecuritynews.com/billbug-apt-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/billbug-apt-malware/?utm_source=dlvr.it&utm_medium=blogger
Google to Pay $391 Million Fine For Silently Tracking User’s Location
Google is agreed to pay a $391.5 fine with 40 state attorneys general for secretly tracking users’ locations is the largest fine ever imposed as a privacy settlement led by Oregon AG Rosenblum and Nebraska AG Doug Peterson, an Attorney General, US. An allegation against Google was that it misled users to believe that they […]
The post Google to Pay $391 Million Fine For Silently Tracking User’s Location appeared first on Cyber Security News.
https://cybersecuritynews.com/google-to-pay-391-million-fine-for-silently-tracking-users-location/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/google-to-pay-391-million-fine-for-silently-tracking-users-location/?utm_source=dlvr.it&utm_medium=blogger
Beware!! King of Malware Emotet Attack Windows User Via Weaponized Excel Files
Researchers uncovered an infamous and widely distributed malware Emotet, now targeting Windows users by employing a malicious Excel File after six months after its last activity. Emotet is considered a kind of malware family among the malware research community due to its footprint and aggressive distribution method for a long while since 2014. it was developed […]
The post Beware!! King of Malware Emotet Attack Windows User Via Weaponized Excel Files appeared first on Cyber Security News.
https://cybersecuritynews.com/king-of-malware-emotet-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/king-of-malware-emotet-attack/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, November 15, 2022
What is an External Penetration Test?
A penetration test (also known as a pentest) is a security assessment that simulates the activities of real-world attackers to identify security holes in your IT systems or applications.
The aim of the test is to understand what vulnerabilities you have, how they could be exploited, and what the impact would be if an attacker was successful.
Usually performed first, an external pentest (also
https://thehackernews.com/2022/11/what-is-external-penetration-test.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/what-is-external-penetration-test.html?utm_source=dlvr.it&utm_medium=blogger
Monday, November 14, 2022
Hackers Hide Information-Stealing Malware in PNG Files Using Steganography
Experts at Avast, who built on the discoveries of ESET, the first to notice and report on the threat group known as “Worok”, conceals malware within PNG images to silently infect victims’ computers with information-stealing malware. Reports say it targets high-profile companies and local governments in Asia. Currently, they are targeting energy companies in Central […]
The post Hackers Hide Information-Stealing Malware in PNG Files Using Steganography appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-hide-malware-png-files/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-hide-malware-png-files/?utm_source=dlvr.it&utm_medium=blogger
Sunday, November 13, 2022
New Updates for ESET's Advanced Home Solutions
It's no secret that antivirus software is as essential to your computer as a power cord.
However, the threats don't stop at your devices. For example, criminals trying to steal your data can attack your Wi-Fi router, and phishing attempts can target your email.
ESET's latest consumer product release takes a comprehensive approach to security to guard against a full range of threats. All are
https://thehackernews.com/2022/11/eset-antivirus-advanced-protection.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/eset-antivirus-advanced-protection.html?utm_source=dlvr.it&utm_medium=blogger
Russian-Canadian National Charged Over Involvement in LockBit Ransomware Attacks
The U.S. Department of Justice (DoJ) has announced charges against a dual Russian and Canadian national for his alleged participation in LockBit ransomware attacks across the world.
The 33-year-old Ontario resident, Mikhail Vasiliev, has been taken into custody and is awaiting extradition to the U.S., where is likely to be sentenced for a maximum of five years in prison.
Vasiliev has been
https://thehackernews.com/2022/11/russian-canadian-national-charged-over.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/russian-canadian-national-charged-over.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, November 12, 2022
$70,000 Bug Let Hackers Bypass Google Pixel Lock Screen Pattern & Password
David Schütz, a security researcher, has identified a critical bug in the Google Pixel phones that allow hackers to bypass the passcode and pattern lock with the consent of having physical access to the vulnerable device. A critical Lock screen bypass bug allows anyone to bypass all formats of lock screen protections including fingerprint, pattern, […]
The post $70,000 Bug Let Hackers Bypass Google Pixel Lock Screen Pattern & Password appeared first on Cyber Security News.
https://cybersecuritynews.com/70000-bug-let-hackers-bypass-google-pixel-lock-screen-pattern-password/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/70000-bug-let-hackers-bypass-google-pixel-lock-screen-pattern-password/?utm_source=dlvr.it&utm_medium=blogger
Friday, November 11, 2022
Re-Focusing Cyber Insurance with Security Validation
The rise in the costs of data breaches, ransomware, and other cyber attacks leads to rising cyber insurance premiums and more limited cyber insurance coverage. This cyber insurance situation increases risks for organizations struggling to find coverage or facing steep increases.
Some Akin Gump Strauss Hauer & Feld LLP's law firm clients, for example, reported a three-fold increase in insurance
https://thehackernews.com/2022/11/re-focusing-cyber-insurance-with.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/re-focusing-cyber-insurance-with.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, November 10, 2022
New Laplas Clipper Malware Targeting Cryptocurrency Users via SmokeLoader
Cryptocurrency users are being targeted with a new clipper malware strain dubbed Laplas by means of another malware known as SmokeLoader.
SmokeLoader, which is delivered by means of weaponized documents sent through spear-phishing emails, further acts as a conduit for other commodity trojans like SystemBC and Raccoon Stealer 2.0, according to an analysis from Cyble.
Observed in
https://thehackernews.com/2022/11/new-laplas-clipper-malware-targeting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/new-laplas-clipper-malware-targeting.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, November 9, 2022
Path To Pentest Guide : 10 Best Penetration Testing Phases, Lifecycle, Methods – 2023
Penetration Testing Phases involves a various Methods, phases, lifecycle and scope to prepare a best checklist to perform the quality penetration operations. Here we have created a complete Penetration Testing Guide with detailed step by step methods. Let’s take a look at how you can get better in your pentesting engagements by breaking your methodology […]
The post Path To Pentest Guide : 10 Best Penetration Testing Phases, Lifecycle, Methods – 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/penetration-testing-phases/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/penetration-testing-phases/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, November 8, 2022
Robin Banks Phishing Service for Cybercriminals Returns with Russian Server
A phishing-as-a-service (PhaaS) platform known as Robin Banks has relocated its attack infrastructure to DDoS-Guard, a Russian provider of bulletproof hosting services.
The switch comes after "Cloudflare disassociated Robin Banks phishing infrastructure from its services, causing a multi-day disruption to operations," according to a report from cybersecurity company IronNet.
Robin Banks was
https://thehackernews.com/2022/11/robin-banks-phishing-service-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/robin-banks-phishing-service-for.html?utm_source=dlvr.it&utm_medium=blogger
Monday, November 7, 2022
Phishing threats are increasingly convincing and evasive
In this Help Net Security video, Tonia Dudley, VP, CISO at Cofense, provides a look at the various changes seen in the phishing threat landscape. Dudley talks about the impact of credential phishing and business email compromise (BEC), which allow…
Read more →
The post Phishing threats are increasingly convincing and evasive first appeared on IT Security News.
https://www.itsecuritynews.info/phishing-threats-are-increasingly-convincing-and-evasive/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/phishing-threats-are-increasingly-convincing-and-evasive/?utm_source=dlvr.it&utm_medium=blogger
Sunday, November 6, 2022
Chinese APT Hackers Deploy LODEINFO Malware in Windows to Open Backdoor
Cybersecurity researchers at Kaspersky’s threat research lab have recently tracked down a revised version of LODEINFO malware that has been used by APT10 (aka Stone Panda, Bronze Riverside, Cicada, and Potassium) to abuse security software and use the malware against organizations based in Japan. It targets a variety of high-privileged organizations for cyberespionage, including Japanese […]
The post Chinese APT Hackers Deploy LODEINFO Malware in Windows to Open Backdoor appeared first on Cyber Security News.
https://cybersecuritynews.com/lodeinfo-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/lodeinfo-malware/?utm_source=dlvr.it&utm_medium=blogger
Saturday, November 5, 2022
CISA Warns of Critical Vulnerabilities in 3 Industrial Control System Software
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published three Industrial Control Systems (ICS) advisories about multiple vulnerabilities in software from ETIC Telecom, Nokia, and Delta Industrial Automation.
Prominent among them is a set of three flaws affecting ETIC Telecom's Remote Access Server (RAS), which "could allow an attacker to obtain sensitive information and
https://thehackernews.com/2022/11/cisa-warns-of-critical-vulnerabilities.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/cisa-warns-of-critical-vulnerabilities.html?utm_source=dlvr.it&utm_medium=blogger
Friday, November 4, 2022
New TikTok Privacy Policy Confirms Chinese Staff Can Access European Users' Data
Popular short-form video-sharing service TikTok is revising its privacy policy for European users to make it explicitly clear that user data can be accessed by some employees from across the world, including China.
The ByteDance-owned platform, which currently stores European user data in the U.S. and Singapore, said the revision is part of its ongoing data governance efforts to limit employee
https://thehackernews.com/2022/11/new-tiktok-privacy-policy-confirms.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/new-tiktok-privacy-policy-confirms.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, November 3, 2022
Experts Warn of SandStrike Android Spyware Infecting Devices via Malicious VPN App
A previously undocumented Android spyware campaign has been found striking Persian-speaking individuals by masquerading as a seemingly harmless VPN application.
Russian cybersecurity firm Kaspersky is tracking the campaign under the moniker SandStrike. It has not been attributed to any particular threat group.
"SandStrike is distributed as a means to access resources about the Bahá'í religion
https://thehackernews.com/2022/11/experts-warn-of-sandstrike-android.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/experts-warn-of-sandstrike-android.html?utm_source=dlvr.it&utm_medium=blogger
Dropbox Breach: Hackers Unauthorizedly Accessed 130 GitHub Source Code Repositories
File hosting service Dropbox on Tuesday disclosed that it was the victim of a phishing campaign that allowed unidentified threat actors to gain unauthorized access to 130 of its source code repositories on GitHub.
"These repositories included our own copies of third-party libraries slightly modified for use by Dropbox, internal prototypes, and some tools and configuration files used by the
https://thehackernews.com/2022/11/dropbox-breach-hackers-unauthorizedly.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/dropbox-breach-hackers-unauthorizedly.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, November 2, 2022
GitHub Repojacking Bug Let Hackers Take Control Over a GitHub Repository
A high-severity security flaw has been patched recently by GitHub on September 19, 2022, and it’s a cloud-based repository hosting service. By exploiting this vulnerability, malicious repositories could have been created and attacks on the supply chain could have been mounted. This vulnerability has been named “RepoJacking” and was discovered by the experts at Checkmarx […]
The post GitHub Repojacking Bug Let Hackers Take Control Over a GitHub Repository appeared first on Cyber Security News.
https://cybersecuritynews.com/github-repojacking-bug/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/github-repojacking-bug/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, November 1, 2022
Unofficial Patch Released for New Actively Exploited Windows MotW Vulnerability
An unofficial patch has been made available for an actively exploited security flaw in Microsoft Windows that makes it possible for files signed with malformed signatures to sneak past Mark-of-the-Web (MotW) protections.
The fix, released by 0patch, arrives weeks after HP Wolf Security disclosed a Magniber ransomware campaign that targets users with fake security updates which employ a
https://thehackernews.com/2022/10/unofficial-patch-released-for-new.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/unofficial-patch-released-for-new.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)