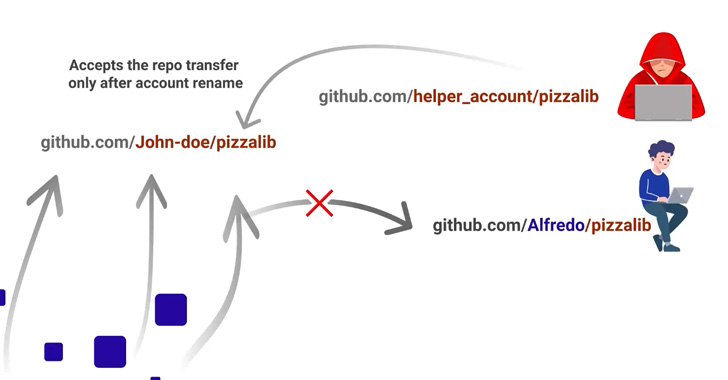
Cloud-based repository hosting service GitHub has addressed a high-severity security flaw that could have been exploited to create malicious repositories and mount supply chain attacks.
The RepoJacking technique, disclosed by Checkmarx, entails a bypass of a protection mechanism called popular repository namespace retirement, which aims to prevent developers from pulling unsafe repositories with
https://thehackernews.com/2022/10/github-repojacking-bug-couldve-allowed.html?utm_source=dlvr.it&utm_medium=blogger
Monday, October 31, 2022
Sunday, October 30, 2022
Twilio Reveals Another Breach from the Same Hackers Behind the August Hack
Communication services provider Twilio this week disclosed that it experienced another "brief security incident" in June 2022 perpetrated by the same threat actor behind the August hack that resulted in unauthorized access of customer information.
The security event occurred on June 29, 2022, the company said in an updated advisory shared this week, as part of its probe into the digital break-in
https://thehackernews.com/2022/10/twilio-reveals-another-breach-from-same.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/twilio-reveals-another-breach-from-same.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, October 29, 2022
Raspberry Robin Operators Selling Cybercriminals Access to Thousands of Endpoints
The Raspberry Robin worm is becoming an access-as-a-service malware for deploying other payloads, including IcedID, Bumblebee, TrueBot (aka Silence), and Clop ransomware.
It is "part of a complex and interconnected malware ecosystem, with links to other malware families and alternate infection methods beyond its original USB drive spread," the Microsoft Security Threat Intelligence Center (MSTIC
https://thehackernews.com/2022/10/raspberry-robin-operators-selling.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/raspberry-robin-operators-selling.html?utm_source=dlvr.it&utm_medium=blogger
Fodcha DDoS Botnet Now Capable of 1Tbps Power & Attack 100+ Targets Daily
Fodcha DDoS botnet has made a significant return with a brand new version. This updated version of the Fodcha botnet was revealed to the community for the first time by 360Netlab on April 13, 2022. Several brand-new features were found in this revamped version of the botnet. These features include ransom demands that are injected […]
The post Fodcha DDoS Botnet Now Capable of 1Tbps Power & Attack 100+ Targets Daily appeared first on Cyber Security News.
https://cybersecuritynews.com/fodcha-ddos-botnet-now-capable-of-1tbps-power/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/fodcha-ddos-botnet-now-capable-of-1tbps-power/?utm_source=dlvr.it&utm_medium=blogger
Friday, October 28, 2022
MajikPOS – A POS Malware Attack & Steal Payment Data From Credit/Debit Cards
Recently, Group-IB’s cybersecurity researchers have discovered that threat actors exploiting two vulnerabilities from point-of-sale payment devices and stolen more than 167,000 credit cards data. During a security audit conducted by Group-IB on April 19, 2022, a C2 server for the POS malware was identified, which is codenamed MajikPOS (aka MagicPOS). Experts were able to analyze […]
The post MajikPOS – A POS Malware Attack & Steal Payment Data From Credit/Debit Cards appeared first on Cyber Security News.
https://cybersecuritynews.com/majikpos/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/majikpos/?utm_source=dlvr.it&utm_medium=blogger
Thursday, October 27, 2022
SideWinder Hacker Group Target Government & Military Using WarHawk Tool
Zscaler ThreatLabz found a new backdoor called ‘WarHawk’ being used by the SideWinder APT threat group to target entities in Pakistan. The SideWinder group goes by the names Rattlesnake, Hardcore Nationalist, RAZOR TIGER, T-APT-04, and APT-C-17, with a history of targeting government, military, and businesses throughout Asia, particularly Pakistan. “The newly discovered WarHawk backdoor contains […]
The post SideWinder Hacker Group Target Government & Military Using WarHawk Tool appeared first on Cyber Security News.
https://cybersecuritynews.com/sidewinder-hacker-group-target-government-military-using-warhawk-tool/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/sidewinder-hacker-group-target-government-military-using-warhawk-tool/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, October 26, 2022
Chrome Extension With 1 Million Installation Stealing Data From Brower
It has recently been discovered by the security researchers at Guardio Labs that a new malvertising campaign is on the loose. This malicious campaign is intended to achieve the following objectives: Push search hacking Chrome extensions. Put affiliate links on web pages in order to earn affiliate commissions. The cybersecurity researchers titled this malvertising campaign […]
The post Chrome Extension With 1 Million Installation Stealing Data From Brower appeared first on Cyber Security News.
https://cybersecuritynews.com/chrome-extension-stealing-browser-data/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/chrome-extension-stealing-browser-data/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, October 25, 2022
Download eBook: Top virtual CISOs share 7 tips for vCISO service providers
Virtual Chief Information Security Officer (vCISO) services (also known as 'Fractional CISO' or 'CISO-as-a-Service') are growing in popularity, especially as growing cyber threats, tightening regulatory demands and strict cyber insurance requirements are driving small to medium-sized enterprises demand for strategic cybersecurity and compliance guidance and management. But vCISO services are
https://thehackernews.com/2022/10/download-ebook-top-virtual-cisos-share.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/download-ebook-top-virtual-cisos-share.html?utm_source=dlvr.it&utm_medium=blogger
Monday, October 24, 2022
CISA Warns of Daixin Team Hackers Targeting Health Organizations With Ransomware
U.S. cybersecurity and intelligence agencies have published a joint advisory warning of attacks perpetrated by a cybercrime gang known as the Daixin Team primarily targeting the healthcare sector in the country.
"The Daixin Team is a ransomware and data extortion group that has targeted the HPH Sector with ransomware and data extortion operations since at least June 2022," the agencies said.
The
https://thehackernews.com/2022/10/cisa-warns-of-daixin-team-hackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/cisa-warns-of-daixin-team-hackers.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, October 23, 2022
Why Ransomware in Education on the Rise and What That Means for 2023
The breach of LA Unified School District (LAUSD) highlights the prevalence of password vulnerabilities, as criminal hackers continue to use breached credentials in increasingly frequent ransomware attacks on education.
The Labor Day weekend breach of LAUSD brought significant districtwide disruptions to access to email, computers, and applications. It's unclear what student or employee data the
https://thehackernews.com/2022/10/why-ransomware-in-education-on-rise-and.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/why-ransomware-in-education-on-rise-and.html?utm_source=dlvr.it&utm_medium=blogger
6 Best Free Malware Analysis Tools to Break Down the Malware Samples – 2022
The malware analysis tools simply allow us to know in a quick and effective way, what actions a threat makes in the system. In this way, you can easily collect all the information about the created files, network connections, changes in the registry, etc. Hence, to achieve this goal, there are a lot of resources […]
The post 6 Best Free Malware Analysis Tools to Break Down the Malware Samples – 2022 appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-analysis-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/malware-analysis-tools/?utm_source=dlvr.it&utm_medium=blogger
Saturday, October 22, 2022
Microsoft Confirms Server Misconfiguration Led to 65,000+ Companies' Data Leak
Microsoft this week confirmed that it inadvertently exposed information related to thousands of customers following a security lapse that left an endpoint publicly accessible over the internet sans any authentication.
"This misconfiguration resulted in the potential for unauthenticated access to some business transaction data corresponding to interactions between Microsoft and prospective
https://thehackernews.com/2022/10/microsoft-confirms-server.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/microsoft-confirms-server.html?utm_source=dlvr.it&utm_medium=blogger
Friday, October 21, 2022
New Ursnif Variant Likely Shifting Focus to Ransomware and Data Theft
The Ursnif malware has become the latest malware to shed its roots as a banking trojan to revamp itself into a generic backdoor capable of delivering next-stage payloads, joining the likes of Emotet, Qakbot, and TrickBot.
"This is a significant shift from the malware's original purpose to enable banking fraud, but is consistent with the broader threat landscape," Mandiant researchers Sandor
https://thehackernews.com/2022/10/latest-ursnif-variant-shifts-focus-from.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/latest-ursnif-variant-shifts-focus-from.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, October 20, 2022
Experts Warn of Stealthy PowerShell Backdoor Disguising as Windows Update
Details have emerged about a previously undocumented and fully undetectable (FUD) PowerShell backdoor that gains its stealth by disguising itself as part of a Windows update process.
"The covert self-developed tool and the associated C2 commands seem to be the work of a sophisticated, unknown threat actor who has targeted approximately 100 victims," Tomer Bar, director of security research at
https://thehackernews.com/2022/10/experts-warn-of-stealthy-powershell.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/experts-warn-of-stealthy-powershell.html?utm_source=dlvr.it&utm_medium=blogger
CISA Warns of Critical Flaws Affecting Industrial Appliances from Advantech and Hitachi
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday released two Industrial Control Systems (ICS) advisories pertaining to severe flaws in Advantech R-SeeNet and Hitachi Energy APM Edge appliances.
This consists of three weaknesses in the R-SeeNet monitoring solution, successful exploitation of which "could result in an unauthorized attacker remotely deleting files on the
https://thehackernews.com/2022/10/cisa-warns-of-critical-flaws-affecting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/cisa-warns-of-critical-flaws-affecting.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, October 19, 2022
European Police Arrest a Gang That Hacked Wireless Key Fobs to Steal Cars
Law enforcement authorities in France, in collaboration with Spain and Latvia, have disrupted a cybercrime ring that leveraged a hacking tool to steal cars without having to use a physical key fob.
"The criminals targeted vehicles with keyless entry and start systems, exploiting the technology to get into the car and drive away," Europol said in a press statement.
The coordinated
https://thehackernews.com/2022/10/european-police-arrest-gang-that-hacked.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/european-police-arrest-gang-that-hacked.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, October 18, 2022
Critical RCE Vulnerability Discovered in Popular Cobalt Strike Hacking Software
HelpSystems, the company behind the Cobalt Strike software platform, has released an out-of-band security update to address a remote code execution vulnerability that could allow an attacker to take control of targeted systems.
Cobalt Strike is a commercial red-team framework that's mainly used for adversary simulation, but cracked versions of the software have been actively abused by ransomware
https://thehackernews.com/2022/10/critical-rce-vulnerability-discovered.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/critical-rce-vulnerability-discovered.html?utm_source=dlvr.it&utm_medium=blogger
Monday, October 17, 2022
New Prestige Ransomware Targeting Polish and Ukrainian Organizations
A new ransomware campaign targeted the transportation and logistics sectors in Ukraine and Poland on October 11 with a previously unknown payload dubbed Prestige.
"The activity shares victimology with recent Russian state-aligned activity, specifically on affected geographies and countries, and overlaps with previous victims of the FoxBlade malware (also known as HermeticWiper)," the Microsoft
https://thehackernews.com/2022/10/new-prestige-ransomware-targeting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/new-prestige-ransomware-targeting.html?utm_source=dlvr.it&utm_medium=blogger
Zimbra Releases Patch for Actively Exploited Vulnerability in its Collaboration Suite
Zimbra has released patches to contain an actively exploited security flaw in its enterprise collaboration suite that could be leveraged to upload arbitrary files to vulnerable instances.
Tracked as CVE-2022-41352 (CVSS score: 9.8), the issue affects a component of the Zimbra suite called Amavis, an open source content filter, and more specifically, the cpio utility it uses to scan and extract
https://thehackernews.com/2022/10/zimbra-releases-patch-for-actively.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/zimbra-releases-patch-for-actively.html?utm_source=dlvr.it&utm_medium=blogger
INTERPOL-led Operation Takes Down 'Black Axe' Cyber Crime Organization
The International Criminal Police Organization, also called the Interpol, has announced the arrests of 75 individuals as part of a coordinated global operation against an organized cybercrime syndicate called Black Axe.
"'Black Axe' and other West African organized crime groups have developed transnational networks, defrauding victims of millions while channeling their profits into lavish
https://thehackernews.com/2022/10/interpol-led-operation-takes-down-black.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/interpol-led-operation-takes-down-black.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, October 16, 2022
Node JS Authentication: Role Based vs Attribute-Based Access Control
NodeJS is categorized as a power full platform for developing event-driven web applications that need to offer a low latency experience to its users. While being cross-platform capable and mobile-friendly, the most significant reason it has become so popular is that it utilizes JavaScript, allowing developers to develop applications inside the web browser. NodeJS comes […]
The post Node JS Authentication: Role Based vs Attribute-Based Access Control appeared first on Cyber Security News.
https://cybersecuritynews.com/node-js-authentication-role-based-vs-attribute-based-access-control/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/node-js-authentication-role-based-vs-attribute-based-access-control/?utm_source=dlvr.it&utm_medium=blogger
Saturday, October 15, 2022
Mirai Botnet Hits Wynncraft Minecraft Server with 2.5 Tbps DDoS Attack
Web infrastructure and security company Cloudflare disclosed this week that it halted a 2.5 Tbps distributed denial-of-service (DDoS) attack launched by a Mirai botnet.
Characterizing it as a "multi-vector attack consisting of UDP and TCP floods," researcher Omer Yoachimik said the DDoS attack targeted the Minecraft server Wynncraft in Q3 2022.
"The entire 2.5 Tbps attack lasted about 2 minutes,
https://thehackernews.com/2022/10/mirai-botnet-hits-wynncraft-minecraft.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/mirai-botnet-hits-wynncraft-minecraft.html?utm_source=dlvr.it&utm_medium=blogger
Friday, October 14, 2022
Researchers Uncover Custom Backdoors and Spying Tools Used by Polonium Hackers
A threat actor tracked as Polonium has been linked to over a dozen highly targeted attacks aimed at Israelian entities with seven different custom backdoors since at least September 2021.
The intrusions were aimed at organizations in various verticals, such as engineering, information technology, law, communications, branding and marketing, media, insurance, and social services, cybersecurity
https://thehackernews.com/2022/10/researchers-uncover-custom-backdoors.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/researchers-uncover-custom-backdoors.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, October 13, 2022
Microsoft Patch Tuesday Fixes New Windows Zero-Day; No Patch for Exchange Server Bugs
Microsoft's Patch Tuesday update for the month of October has addressed a total of 85 security vulnerabilities, including fixes for an actively exploited zero-day flaw in the wild.
Of the 85 bugs, 15 are rated Critical, 69 are rated Important, and one is rated Moderate in severity. The update, however, does not include mitigations for the actively exploited ProxyNotShell flaws in Exchange Server
https://thehackernews.com/2022/10/microsoft-patch-tuesday-fixes-new.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/microsoft-patch-tuesday-fixes-new.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, October 12, 2022
Hackers Exploiting Unpatched RCE Flaw in Zimbra Collaboration Suite
A severe remote code execution vulnerability in Zimbra's enterprise collaboration software and email platform is being actively exploited, with no patch currently available to remediate the issue.
The shortcoming, assigned CVE-2022-41352, carries a critical-severity rating of CVSS 9.8, providing a pathway for attackers to upload arbitrary files and carry out malicious actions on affected
https://thehackernews.com/2022/10/hackers-exploiting-unpatched-rce-flaw.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/10/hackers-exploiting-unpatched-rce-flaw.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, October 11, 2022
Cheerscrypt Linux-based Ransomware Encrypt Both Linux & Windows Systems
In a recent investigation, the Sygnia security firm found Linux-based ransomware, Cheerscrypt. This ransomware was found using the TTPs of Night Sky ransomware. There is a common threat group called Emperor Dragonfly (A.K.A. DEV-0401/BRONZE STARLIGHT) that is behind both Cheerscrypt and Night Sky. There were several open-source tools deployed by Emperor Dragonfly. In order to […]
The post Cheerscrypt Linux-based Ransomware Encrypt Both Linux & Windows Systems appeared first on Cyber Security News.
https://cybersecuritynews.com/cheerscrypt-linux-based-ransomware-encrypt-linux-windows-systems/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cheerscrypt-linux-based-ransomware-encrypt-linux-windows-systems/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)