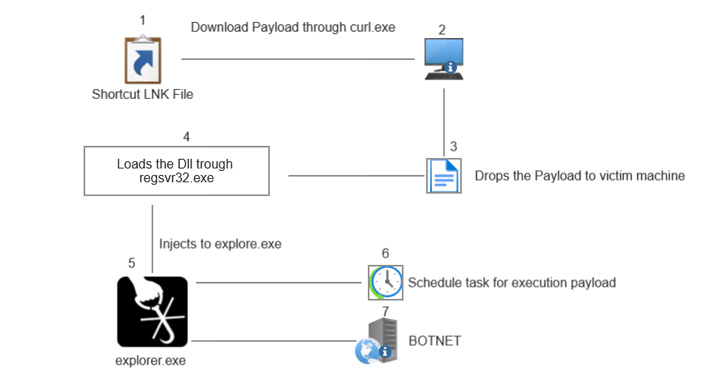
Lightning Framework is a new undetected Swiss Army Knife-like Linux malware that has modular plugins and the ability to install rootkits. Year after year Linux environments increasingly become the target of malware due to continued threat actor interest in the…
Read more →
The post Lightning Framework: New Undetected “Swiss Army Knife” Linux Malware ⚡ first appeared on IT Security News.
https://www.itsecuritynews.info/lightning-framework-new-undetected-swiss-army-knife-linux-malware-%e2%9a%a1-95/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=lightning-framework-new-undetected-swiss-army-knife-linux-malware-%25e2%259a%25a1-95
Saturday, July 23, 2022
Microsoft Resumes Blocking Office VBA Macros by Default After 'Temporary Pause'
Microsoft has officially resumed blocking Visual Basic for Applications (VBA) macros by default across Office apps, weeks after temporarily announcing plans to roll back the change.
"Based on our review of customer feedback, we've made updates to both our end user and our IT admin documentation to make clearer what options you have for different scenarios," the company said in an update on July
https://thehackernews.com/2022/07/microsoft-resumes-blocking-office-vba.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/microsoft-resumes-blocking-office-vba.html?utm_source=dlvr.it&utm_medium=blogger
Friday, July 22, 2022
Lightning Framework: New Undetected “Swiss Army Knife” Linux Malware ⚡
Lightning Framework is a new undetected Swiss Army Knife-like Linux malware that has modular plugins and the ability to install rootkits. Year after year Linux environments increasingly become the target of malware due to continued threat actor interest in the…
Read more →
The post Lightning Framework: New Undetected “Swiss Army Knife” Linux Malware ⚡ first appeared on IT Security News.
https://www.itsecuritynews.info/lightning-framework-new-undetected-swiss-army-knife-linux-malware-%e2%9a%a1-52/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=lightning-framework-new-undetected-swiss-army-knife-linux-malware-%25e2%259a%25a1-52
https://www.itsecuritynews.info/lightning-framework-new-undetected-swiss-army-knife-linux-malware-%e2%9a%a1-52/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=lightning-framework-new-undetected-swiss-army-knife-linux-malware-%25e2%259a%25a1-52
Lightning Framework: New Undetected “Swiss Army Knife” Linux Malware ⚡
Lightning Framework is a new undetected Swiss Army Knife-like Linux malware that has modular plugins and the ability to install rootkits. Year after year Linux environments increasingly become the target of malware due to continued threat actor interest in the…
Read more →
The post Lightning Framework: New Undetected “Swiss Army Knife” Linux Malware ⚡ first appeared on IT Security News.
https://www.itsecuritynews.info/lightning-framework-new-undetected-swiss-army-knife-linux-malware-%e2%9a%a1-51/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=lightning-framework-new-undetected-swiss-army-knife-linux-malware-%25e2%259a%25a1-51
https://www.itsecuritynews.info/lightning-framework-new-undetected-swiss-army-knife-linux-malware-%e2%9a%a1-51/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=lightning-framework-new-undetected-swiss-army-knife-linux-malware-%25e2%259a%25a1-51
Candiru Spyware Caught Exploiting Google Chrome Zero-Day to Target Journalists
The actively exploited but now-fixed Google Chrome zero-day flaw that came to light earlier this month was weaponized by an Israeli spyware company and used in attacks targeting journalists in the Middle East.
Czech cybersecurity firm Avast linked the exploitation to Candiru (aka Saito Tech), which has a history of leveraging previously unknown flaws to deploy a Windows malware dubbed
https://thehackernews.com/2022/07/candiru-spyware-caught-exploiting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/candiru-spyware-caught-exploiting.html?utm_source=dlvr.it&utm_medium=blogger
Hackers Steal Over 50,000 Payment Card Records Using E-Skimmer From Over 300 Restaurants
Two web-skimming Magecart campaigns that targeted three different online ordering platforms have stolen payment card details from more than 310 restaurants. It was determined that in total, 50,000 payment cards were taken, and as a result, they are already in the process of being sold on a number of dark-web marketplaces. When an online shopper […]
The post Hackers Steal Over 50,000 Payment Card Records Using E-Skimmer From Over 300 Restaurants appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-steal-over-50000-payment-card-records-using-e-skimmer/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-steal-over-50000-payment-card-records-using-e-skimmer/?utm_source=dlvr.it&utm_medium=blogger
The New Weak Link in SaaS Security: Devices
Typically, when threat actors look to infiltrate an organization's SaaS apps, they look to SaaS app misconfigurations as a means of entry. However, employees now use their personal devices, whether their phones or laptops, etc., to get their jobs done. If the device's hygiene is not up to par, it increases the risk for the organization and widens the attack surface for bad actors. And so,
https://thehackernews.com/2022/07/the-new-weak-link-in-saas-security.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/the-new-weak-link-in-saas-security.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, July 21, 2022
Atlassian Rolls Out Security Patch for Critical Confluence Vulnerability
Atlassian has rolled out fixes to remediate a critical security vulnerability pertaining to the use of hard-coded credentials affecting the Questions For Confluence app for Confluence Server and Confluence Data Center.
The flaw, tracked as CVE-2022-26138, arises when the app in question is enabled on either of two services, causing it to create a Confluence user account with the username "
https://thehackernews.com/2022/07/atlassian-releases-patch-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/atlassian-releases-patch-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
FBI Seizes $500,000 Ransomware Payments and Crypto from North Korean Hackers
The U.S. Department of Justice (DoJ) has announced the seizure of $500,000 worth of Bitcoin from North Korean hackers who extorted digital payments from several organizations by using a new ransomware strain known as Maui.
"The seized funds include ransoms paid by healthcare providers in Kansas and Colorado," the DoJ said in a press release issued Tuesday.
The recovery of the bitcoin ransoms
https://thehackernews.com/2022/07/fbi-seizes-500000-ransomware-payments.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/fbi-seizes-500000-ransomware-payments.html?utm_source=dlvr.it&utm_medium=blogger
Cynomi Automated Virtual CISO (vCISO) Platform for Service Providers
Growing cyber threats, tightening regulatory demands and strict cyber insurance requirements are driving small to medium-sized enterprises demand for strategic cybersecurity and compliance guidance and management. Since most companies this size don't have in-house CISO expertise – the demand for virtual CISO (vCISO) services is also growing. Yet current vCISO services models still rely on manual
https://thehackernews.com/2022/07/cynomi-automated-virtual-ciso-vciso.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/cynomi-automated-virtual-ciso-vciso.html?utm_source=dlvr.it&utm_medium=blogger
FBI Warns of Fake Cryptocurrency apps to Steal Funds from Investors
The US security agency, FBI (Federal Bureau of Investigation) has issued a warning today that overseas investors (specifically US-based) have been targeted by cybercriminals who are stealing funds using fraudulent cryptocurrency investment applications. It is estimated that approximately $42.7 million has already been stolen from 244 victims to date by cybercriminals, as per the US […]
The post FBI Warns of Fake Cryptocurrency apps to Steal Funds from Investors appeared first on Cyber Security News.
https://cybersecuritynews.com/fbi-warns-of-fake-cryptocurrency-apps/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/fbi-warns-of-fake-cryptocurrency-apps/?utm_source=dlvr.it&utm_medium=blogger
This Cloud Botnet Has Hijacked 30,000 Systems to Mine Cryptocurrencies
The 8220 cryptomining group has expanded in size to encompass as many as 30,000 infected hosts, up from 2,000 hosts globally in mid-2021.
"8220 Gang is one of the many low-skill crimeware gangs we continually observe infecting cloud hosts and operating a botnet and cryptocurrency miners through known vulnerabilities and remote access brute forcing infection vectors," Tom Hegel of SentinelOne
https://thehackernews.com/2022/07/this-cloud-botnet-has-hijacked-30000.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/this-cloud-botnet-has-hijacked-30000.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, July 20, 2022
Unpatched GPS Tracker Bugs Could Let Attackers Disrupt Vehicles Remotely
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning of a handful of unpatched security vulnerabilities in MiCODUS MV720 Global Positioning System (GPS) trackers outfitted in over 1.5 million vehicles that could lead to remote disruption of critical operations.
"Successful exploitation of these vulnerabilities may allow a remote actor to exploit access and gain control of
https://thehackernews.com/2022/07/unpatched-gps-tracker-bugs-could-let.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/unpatched-gps-tracker-bugs-could-let.html?utm_source=dlvr.it&utm_medium=blogger
Dealing With Alert Overload? There's a Guide For That
The Great Resignation – or the Great Reshuffle as some are calling it – and the growing skills gap have been dominating headlines lately. But these issues aren't new to the cybersecurity industry. While many are just now hearing about employee burnout, security teams have faced reality and serious consequences of burnout for years.
One of the biggest culprits? Alert overload.
The average
https://thehackernews.com/2022/07/dealing-with-alert-overload-theres.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/dealing-with-alert-overload-theres.html?utm_source=dlvr.it&utm_medium=blogger
Russian Hackers Tricked Ukrainians with Fake "DoS Android Apps to Target Russia"
Russian threat actors capitalized on the ongoing conflict against Ukraine to distribute Android malware camouflaged as an app for pro-Ukrainian hacktivists to launch distributed denial-of-service (DDoS) attacks against Russian sites.
Google Threat Analysis Group (TAG) attributed the malware to Turla, an advanced persistent threat also known as Krypton, Venomous Bear, Waterbug, and Uroburos, and
https://thehackernews.com/2022/07/russian-hackers-tricked-ukrainians-with.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/russian-hackers-tricked-ukrainians-with.html?utm_source=dlvr.it&utm_medium=blogger
New Air-Gap Attack Uses SATA Cable as an Antenna to Transfer Radio Signals
A new method devised to leak information and jump over air-gaps takes advantage of Serial Advanced Technology Attachment (SATA) or Serial ATA cables as a communication medium, adding to a long list of electromagnetic, magnetic, electric, optical, and acoustic methods already demonstrated to plunder data.
"Although air-gap computers have no wireless connectivity, we show that attackers can use
https://thehackernews.com/2022/07/new-air-gap-attack-uses-sata-cable-as.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/new-air-gap-attack-uses-sata-cable-as.html?utm_source=dlvr.it&utm_medium=blogger
Are You Aware of the Top Email Threats to Protect Against Today?
Given the growing volumes of emails received every day, people do not have the time to devote to every email and fall prey to email threats. This has made emails the most popular attack vector. So, what are the common email threats today? Read on to find out. 13 Email Threats to Know About and […]
The post Are You Aware of the Top Email Threats to Protect Against Today? appeared first on Cyber Security News.
https://cybersecuritynews.com/13-email-threats/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/13-email-threats/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, July 19, 2022
Several New Play Store Apps Spotted Distributing Joker, Facestealer and Coper Malware
Google has taken steps to ax dozens of fraudulent apps from the official Play Store that were spotted propagating Joker, Facestealer, and Coper malware families through the virtual marketplace.
While the Android storefront is considered to be a trusted source for discovering and installing apps, bad actors have repeatedly found ways to sneak past security barriers erected by Google in hopes of
https://thehackernews.com/2022/07/several-new-play-store-apps-spotted.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/several-new-play-store-apps-spotted.html?utm_source=dlvr.it&utm_medium=blogger
Pegasus Spyware Used to Hack Devices of Pro-Democracy Activists in Thailand
Thai activists involved in the country's pro-democracy protests have had their smartphones infected with the infamous Pegasus government-sponsored spyware.
At least 30 individuals, spanning activists, academics, lawyers, and NGO workers, are believed to have been targeted between October 2020 and November 2021, many of whom have been previously detained, arrested and imprisoned for their
https://thehackernews.com/2022/07/pegasus-spyware-used-to-hack-devices-of.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/pegasus-spyware-used-to-hack-devices-of.html?utm_source=dlvr.it&utm_medium=blogger
Experts Notice Sudden Surge in Exploitation of WordPress Page Builder Plugin Vulnerability
Researchers from Wordfence have sounded the alarm about a "sudden" spike in cyber attacks attempting to exploit an unpatched flaw in a WordPress plugin called Kaswara Modern WPBakery Page Builder Addons.
Tracked as CVE-2021-24284, the issue is rated 10.0 on the CVSS vulnerability scoring system and relates to an unauthenticated arbitrary file upload that could be abused to gain code execution,
https://thehackernews.com/2022/07/experts-notice-sudden-surge-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/experts-notice-sudden-surge-in.html?utm_source=dlvr.it&utm_medium=blogger
Mind the Gap – How to Ensure Your Vulnerability Detection Methods are up to Scratch
With global cybercrime costs expected to reach $10.5 trillion annually by 2025, it comes as little surprise that the risk of attack is companies' biggest concern globally. To help businesses uncover and fix the vulnerabilities and misconfigurations affecting their systems, there is an (over)abundance of solutions available.
But beware, they may not give you a full and continuous view of your
https://thehackernews.com/2022/07/mind-gap-how-to-ensure-your.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/mind-gap-how-to-ensure-your.html?utm_source=dlvr.it&utm_medium=blogger
How To Manage Cybersecurity Risk In The Age Of Information Overload
Managing cybersecurity risk in the Information Age is no easy feat. Each day, we’re bombarded with news of increasingly sophisticated cyber threats and attacks. Nefarious actors are exploiting vulnerabilities in our systems and networks, and businesses are struggling to keep up. Now, business leaders are commonly choosing to register in a cyber security course to better prepare […]
The post How To Manage Cybersecurity Risk In The Age Of Information Overload appeared first on Cyber Security News.
https://cybersecuritynews.com/how-to-manage-cybersecurity-risk-in-the-age-of-information-overload-2/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/how-to-manage-cybersecurity-risk-in-the-age-of-information-overload-2/?utm_source=dlvr.it&utm_medium=blogger
Monday, July 18, 2022
All Free Red Teaming Tools & Simulation Toolkit For Red Team Operations 2022
We are bringing here a collection of open-source and commercial Red Team tools that aid in red team operations. This repository will help you with the majority part of red team engagement. You can also join the Certified Red Team Expert program to become a master in red team operation and understand real-world attacks. Read Team […]
The post All Free Red Teaming Tools & Simulation Toolkit For Red Team Operations 2022 appeared first on Cyber Security News.
https://cybersecuritynews.com/free-red-teaming-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/free-red-teaming-tools/?utm_source=dlvr.it&utm_medium=blogger
Software developers, how secure is your software ?
If you develop software, then a Secure Software Development Lifecycle (SSDL) process must be used starting from design, during the implementation, testing, deployment and ends when the product reaches its end of life. Do not forget also about the software…
Read more →
The post Software developers, how secure is your software ? first appeared on IT Security News.
https://www.itsecuritynews.info/software-developers-how-secure-is-your-software-8/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=software-developers-how-secure-is-your-software-8
https://www.itsecuritynews.info/software-developers-how-secure-is-your-software-8/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=software-developers-how-secure-is-your-software-8
Graff paid a $7.5M ransom and sued its insurance firm for refusing to cover this payment
The high-end British jeweler Graff paid a £6 million ransom after the ransomware attack it suffered in 2021. In September 2021, the Conti ransomware gang hit high society jeweler Graff and threatens to release private details of world leaders, actors…
Read more →
The post Graff paid a $7.5M ransom and sued its insurance firm for refusing to cover this payment first appeared on IT Security News.
https://www.itsecuritynews.info/graff-paid-a-7-5m-ransom-and-sued-its-insurance-firm-for-refusing-to-cover-this-payment/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=graff-paid-a-7-5m-ransom-and-sued-its-insurance-firm-for-refusing-to-cover-this-payment
https://www.itsecuritynews.info/graff-paid-a-7-5m-ransom-and-sued-its-insurance-firm-for-refusing-to-cover-this-payment/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=graff-paid-a-7-5m-ransom-and-sued-its-insurance-firm-for-refusing-to-cover-this-payment
New Android Malware on the Google Play Store with Over 3 Million Downloads
A new Android malware called ‘Autolycos’ installed over 3 million times is surfing on the Google Play Store by secretly subscribing users to its premium services. Maxime Ingrao, Security Researcher from Evina found the new android malware ‘Autolycos’, which is…
Read more →
The post New Android Malware on the Google Play Store with Over 3 Million Downloads first appeared on IT Security News.
https://www.itsecuritynews.info/new-android-malware-on-the-google-play-store-with-over-3-million-downloads/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=new-android-malware-on-the-google-play-store-with-over-3-million-downloads
https://www.itsecuritynews.info/new-android-malware-on-the-google-play-store-with-over-3-million-downloads/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=new-android-malware-on-the-google-play-store-with-over-3-million-downloads
Juniper Releases Patches for Critical Flaws in Junos OS and Contrail Networking
Juniper Networks has pushed security updates to address several vulnerabilities affecting multiple products, some of which could be exploited to seize control of affected systems. The most critical of the flaws affect Junos Space and Contrail Networking, with the tech company urging…
Read more →
The post Juniper Releases Patches for Critical Flaws in Junos OS and Contrail Networking first appeared on IT Security News.
https://www.itsecuritynews.info/juniper-releases-patches-for-critical-flaws-in-junos-os-and-contrail-networking/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=juniper-releases-patches-for-critical-flaws-in-junos-os-and-contrail-networking
https://www.itsecuritynews.info/juniper-releases-patches-for-critical-flaws-in-junos-os-and-contrail-networking/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=juniper-releases-patches-for-critical-flaws-in-junos-os-and-contrail-networking
Sunday, July 17, 2022
Week in review: Kali Linux gets on Linode, facial recognition defeated, Log4j exploitation
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Dealing with threats and preventing sensitive data loss Recently, Normalyze, a data-first cloud security platform, came out of stealth with $22.2M in Series A funding.…
Read more →
The post Week in review: Kali Linux gets on Linode, facial recognition defeated, Log4j exploitation first appeared on IT Security News.
https://www.itsecuritynews.info/week-in-review-kali-linux-gets-on-linode-facial-recognition-defeated-log4j-exploitation/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=week-in-review-kali-linux-gets-on-linode-facial-recognition-defeated-log4j-exploitation
https://www.itsecuritynews.info/week-in-review-kali-linux-gets-on-linode-facial-recognition-defeated-log4j-exploitation/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=week-in-review-kali-linux-gets-on-linode-facial-recognition-defeated-log4j-exploitation
Pakistani APT Hackers Attack Indian Education Institutes & Students With New Malware
Recently, Cisco Talos discovered that the Transparent Tribe APT group is engaged in an ongoing malicious campaign. APT hackers from Pakistan have carried out a malicious campaign against several educational institutions located throughout India in order to inflict harm on students. In this ongoing active campaign, the APT is also targeting civilian users within its […]
The post Pakistani APT Hackers Attack Indian Education Institutes & Students With New Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/pakistani-apt-hackers-attack-indian-education-institutes-students-with-new-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/pakistani-apt-hackers-attack-indian-education-institutes-students-with-new-malware/?utm_source=dlvr.it&utm_medium=blogger
Saturday, July 16, 2022
Eskimi – 1,197,620 breached accounts
In late 2020, the AdTech platform Eskimi suffered a data breach that exposed 26M records with 1.2M unique email addresses. The data included usernames, dates of birth, genders and passwords stored as unsalted MD5 hashes. This article has been indexed…
Read more →
The post Eskimi – 1,197,620 breached accounts first appeared on IT Security News.
https://www.itsecuritynews.info/eskimi-1197620-breached-accounts/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=eskimi-1197620-breached-accounts
https://www.itsecuritynews.info/eskimi-1197620-breached-accounts/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=eskimi-1197620-breached-accounts
Four Steps to Using Metrics to Defend Your Security Budget
By Diana-Lynn Contesti (Chief Architect, CISSP-ISSAP, ISSMP, CSSLP, SSCP), and Richard Nealon (Senior Security Consultant, CISSP-ISSMP, SSCP, SABSA SCF) Ever find yourself in a struggle to defend your security budget or to introduce a change? This guide is a baseline to help…
Read more →
The post Four Steps to Using Metrics to Defend Your Security Budget first appeared on IT Security News.
https://www.itsecuritynews.info/four-steps-to-using-metrics-to-defend-your-security-budget-3/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=four-steps-to-using-metrics-to-defend-your-security-budget-3
https://www.itsecuritynews.info/four-steps-to-using-metrics-to-defend-your-security-budget-3/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=four-steps-to-using-metrics-to-defend-your-security-budget-3
Haystack Secure Delivery protects sensitive and proprietary internal communications
Haystack announced Secure Delivery, a feature that deters unattributed, unauthorized sharing of sensitive information and keeps internal communications internal. “Taking an email out of context can be disastrous. Leaking company information can be even more damaging. Organizations can now rest…
Read more →
The post Haystack Secure Delivery protects sensitive and proprietary internal communications first appeared on IT Security News.
https://www.itsecuritynews.info/haystack-secure-delivery-protects-sensitive-and-proprietary-internal-communications/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=haystack-secure-delivery-protects-sensitive-and-proprietary-internal-communications
https://www.itsecuritynews.info/haystack-secure-delivery-protects-sensitive-and-proprietary-internal-communications/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=haystack-secure-delivery-protects-sensitive-and-proprietary-internal-communications
Keysight Cyber Training Simulator enables students to develop their skills in a realistic environment
Keysight Technologies has introduced Keysight Cyber Training Simulator (KCTS), a comprehensive, turnkey cyber range that simulates real-world traffic using the company’s BreakingPoint solution. With cybercrime on the rise and cybersecurity professionals difficult to find, organizations are at risk. Consequently, cybersecurity…
Read more →
The post Keysight Cyber Training Simulator enables students to develop their skills in a realistic environment first appeared on IT Security News.
https://www.itsecuritynews.info/keysight-cyber-training-simulator-enables-students-to-develop-their-skills-in-a-realistic-environment/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=keysight-cyber-training-simulator-enables-students-to-develop-their-skills-in-a-realistic-environment
https://www.itsecuritynews.info/keysight-cyber-training-simulator-enables-students-to-develop-their-skills-in-a-realistic-environment/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=keysight-cyber-training-simulator-enables-students-to-develop-their-skills-in-a-realistic-environment
New Cache Side Channel Attack Can De-Anonymize Targeted Online Users
A group of academics from the New Jersey Institute of Technology (NJIT) has warned of a novel technique that could be used to defeat anonymity protections and identify a unique website visitor.
"An attacker who has complete or partial control over a website can learn whether a specific target (i.e., a unique individual) is browsing the website," the researchers said. "The attacker knows this
https://thehackernews.com/2022/07/new-cache-side-channel-attack-can-de.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/new-cache-side-channel-attack-can-de.html?utm_source=dlvr.it&utm_medium=blogger
Friday, July 15, 2022
North Korean Hackers Targeting Small and Midsize Businesses with H0lyGh0st Ransomware
An emerging threat cluster originating from North Korea has been linked to developing and using ransomware in cyberattacks targeting small businesses since September 2021.
The group, which calls itself H0lyGh0st after the ransomware payload of the same name, is being tracked by the Microsoft Threat Intelligence Center under the moniker DEV-0530, a designation assigned for unknown, emerging, or a
https://thehackernews.com/2022/07/north-korean-hackers-targeting-small.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/north-korean-hackers-targeting-small.html?utm_source=dlvr.it&utm_medium=blogger
Meet Mantis – the tiny shrimp that launched 3,000 DDoS attacks
Watch out for deadly pinchers after that record-breaking attack The botnet behind the largest-ever HTTPS-based distributed-denial-of-service (DDoS) attack has been named after a tiny shrimp.… This article has been indexed from The Register – Security Read the original article: Meet…
Read more →
The post Meet Mantis – the tiny shrimp that launched 3,000 DDoS attacks first appeared on IT Security News.
https://www.itsecuritynews.info/meet-mantis-the-tiny-shrimp-that-launched-3000-ddos-attacks-2/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=meet-mantis-the-tiny-shrimp-that-launched-3000-ddos-attacks-2
https://www.itsecuritynews.info/meet-mantis-the-tiny-shrimp-that-launched-3000-ddos-attacks-2/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=meet-mantis-the-tiny-shrimp-that-launched-3000-ddos-attacks-2
Mantis Botnet Behind the Largest HTTPS DDoS Attack Targeting Cloudflare Customers
The botnet behind the largest HTTPS distributed denial-of-service (DDoS) attack in June 2022 has been linked to a spate of attacks aimed at nearly 1,000 Cloudflare customers. Calling the powerful botnet Mantis, the web performance and security company attributed it to…
Read more →
The post Mantis Botnet Behind the Largest HTTPS DDoS Attack Targeting Cloudflare Customers first appeared on IT Security News.
https://www.itsecuritynews.info/mantis-botnet-behind-the-largest-https-ddos-attack-targeting-cloudflare-customers/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=mantis-botnet-behind-the-largest-https-ddos-attack-targeting-cloudflare-customers
https://www.itsecuritynews.info/mantis-botnet-behind-the-largest-https-ddos-attack-targeting-cloudflare-customers/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=mantis-botnet-behind-the-largest-https-ddos-attack-targeting-cloudflare-customers
New infosec products of the week: July 15, 2022
Here’s a look at the most interesting products from the past week, featuring releases from Deloitte, Flashpoint, CertiK, CyberArk, and N-able. Flashpoint Automate accelerates repeatable security-related processes Combined with the Flashpoint Intelligence Platform, Flashpoint Automate’s capabilities provide security teams with…
Read more →
The post New infosec products of the week: July 15, 2022 first appeared on IT Security News.
https://www.itsecuritynews.info/new-infosec-products-of-the-week-july-15-2022/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=new-infosec-products-of-the-week-july-15-2022
https://www.itsecuritynews.info/new-infosec-products-of-the-week-july-15-2022/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=new-infosec-products-of-the-week-july-15-2022
Mantis Botnet Behind the Largest HTTPS DDoS Attack Targeting Cloudflare Customers
The botnet behind the largest HTTPS distributed denial-of-service (DDoS) attack in June 2022 has been linked to a spate of attacks aimed at nearly 1,000 Cloudflare customers.
Calling the powerful botnet Mantis, the web performance and security company attributed it to more than 3,000 HTTP DDoS attacks against its users.
The most attacked industry verticals include internet and telecom, media,
https://thehackernews.com/2022/07/mantis-botnet-behind-largest-https-ddos.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/mantis-botnet-behind-largest-https-ddos.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, July 14, 2022
Pakistani Hackers Targeting Indian Students in Latest Malware Campaign
The advanced persistent threat (APT) group known as Transparent Tribe has been attributed to a new ongoing phishing campaign targeting students at various educational institutions in India at least since December 2021.
"This new campaign also suggests that the APT is actively expanding its network of victims to include civilian users," Cisco Talos said in a report shared with The Hacker News.
https://thehackernews.com/2022/07/pakistani-hackers-targeting-indian.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/pakistani-hackers-targeting-indian.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, July 13, 2022
New 'Retbleed' Speculative Execution Attack Affects AMD and Intel CPUs
Security researchers have uncovered yet another vulnerability affecting numerous older AMD and Intel microprocessors that could bypass current defenses and result in Spectre-based speculative-execution attacks.
Dubbed Retbleed by ETH Zurich researchers Johannes Wikner and Kaveh Razavi, the issues are tracked as CVE-2022-29900 (AMD) and CVE-2022-29901 (Intel), with the chipmakers releasing
https://thehackernews.com/2022/07/new-retbleed-speculative-execution.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/new-retbleed-speculative-execution.html?utm_source=dlvr.it&utm_medium=blogger
Large-Scale Phishing Campaign Bypasses MFA
Attackers used adversary-in-the-middle attacks to steal passwords, hijack sign-in sessions and skip authentication and then use victim mailboxes to launch BEC attacks against other targets. This article has been indexed from Threatpost Read the original article: Large-Scale Phishing Campaign Bypasses…
Read more →
The post Large-Scale Phishing Campaign Bypasses MFA first appeared on IT Security News.
https://www.itsecuritynews.info/large-scale-phishing-campaign-bypasses-mfa/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=large-scale-phishing-campaign-bypasses-mfa
https://www.itsecuritynews.info/large-scale-phishing-campaign-bypasses-mfa/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=large-scale-phishing-campaign-bypasses-mfa
New UEFI Firmware Vulnerabilities Impact Several Lenovo Notebook Models
Consumer electronics maker Lenovo on Tuesday rolled out fixes to contain three security flaws in its UEFI firmware affecting over 70 product models.
"The vulnerabilities can be exploited to achieve arbitrary code execution in the early phases of the platform boot, possibly allowing the attackers to hijack the OS execution flow and disable some important security features," Slovak cybersecurity
https://thehackernews.com/2022/07/new-uefi-firmware-vulnerabilities.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/new-uefi-firmware-vulnerabilities.html?utm_source=dlvr.it&utm_medium=blogger
Researchers Uncover New Attempts by Qakbot Malware to Evade Detection
The operators behind the Qakbot malware are transforming their delivery vectors in an attempt to sidestep detection.
"Most recently, threat actors have transformed their techniques to evade detection by using ZIP file extensions, enticing file names with common formats, and Excel (XLM) 4.0 to trick victims into downloading malicious attachments that install Qakbot," Zscaler Threatlabz
https://thehackernews.com/2022/07/researchers-uncover-new-attempts-by.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/researchers-uncover-new-attempts-by.html?utm_source=dlvr.it&utm_medium=blogger
Microsoft Releases Fix for Zero-Day Flaw in July 2022 Security Patch Rollout
Microsoft released its monthly round of Patch Tuesday updates to address 84 new security flaws spanning multiple product categories, counting a zero-day vulnerability that's under active attack in the wild.
Of the 84 shortcomings, four are rated Critical, and 80 are rated Important in severity. Also separately resolved by the tech giant are two other bugs in the Chromium-based Edge browser, one
https://thehackernews.com/2022/07/microsoft-releases-fix-for-zero-day.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/microsoft-releases-fix-for-zero-day.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, July 12, 2022
Out of Date Risk Assessment Intel is Damaging Company Security says Armis
With results from more than 100 professionals in cybersecurity, Armis released a survey that explored the risks and struggles within the industry as the environment changes. As the landscape of cybersecurity changes rapidly, security intel being reported to companies may…
Read more →
The post Out of Date Risk Assessment Intel is Damaging Company Security says Armis first appeared on IT Security News.
https://www.itsecuritynews.info/out-of-date-risk-assessment-intel-is-damaging-company-security-says-armis/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=out-of-date-risk-assessment-intel-is-damaging-company-security-says-armis
https://www.itsecuritynews.info/out-of-date-risk-assessment-intel-is-damaging-company-security-says-armis/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=out-of-date-risk-assessment-intel-is-damaging-company-security-says-armis
TikTok Postpones Privacy Policy Update in Europe After Italy Warns of GDPR Breach
Popular video-sharing platform TikTok on Tuesday agreed to pause a controversial privacy policy update that could have allowed it to serve targeted ads based on users' activity on the social video platform without their permission to do so.
The reversal, reported by TechCrunch, comes a day after the Italian data protection authority — the Garante per la Protezione dei Dati Personali — warned the
https://thehackernews.com/2022/07/tiktok-postpones-privacy-policy-update.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/tiktok-postpones-privacy-policy-update.html?utm_source=dlvr.it&utm_medium=blogger
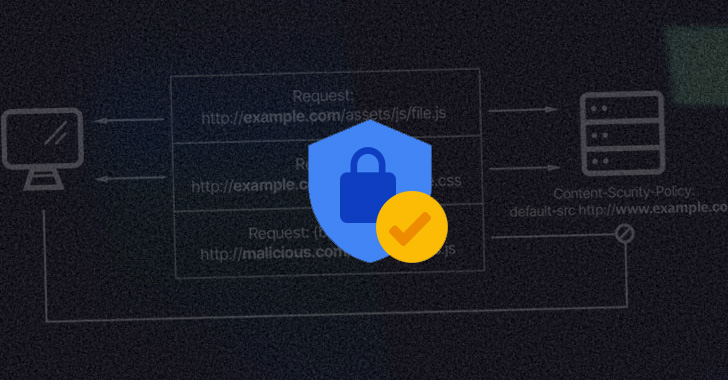
Avoiding Death by a Thousand Scripts: Using Automated Content Security Policies
Businesses know they need to secure their client-side scripts. Content security policies (CSPs) are a great way to do that. But CSPs are cumbersome. One mistake and you have a potentially significant client-side security gap. Finding those gaps means long and tedious hours (or days) in manual code reviews through thousands of lines of script on your web applications. Automated content security
https://thehackernews.com/2022/07/avoiding-death-by-thousand-scripts.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/07/avoiding-death-by-thousand-scripts.html?utm_source=dlvr.it&utm_medium=blogger
🚀 Launching Autonomous SecOps (Your Virtual, Algorithm-Driven Tier 1 SOC Team)
We are helping security teams go beyond individual file analysis to automate their entire Endpoint and Email alert triage processes with our new dashboard. Autonomous SecOps provides a better, more affordable alternative to in-house Tier 1 teams or external Managed…
Read more →
The post 🚀 Launching Autonomous SecOps (Your Virtual, Algorithm-Driven Tier 1 SOC Team) first appeared on IT Security News.
https://www.itsecuritynews.info/%f0%9f%9a%80-launching-autonomous-secops-your-virtual-algorithm-driven-tier-1-soc-team-33/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=%25f0%259f%259a%2580-launching-autonomous-secops-your-virtual-algorithm-driven-tier-1-soc-team-33
https://www.itsecuritynews.info/%f0%9f%9a%80-launching-autonomous-secops-your-virtual-algorithm-driven-tier-1-soc-team-33/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=%25f0%259f%259a%2580-launching-autonomous-secops-your-virtual-algorithm-driven-tier-1-soc-team-33
Rozena Backdoor Malware Uses a Fileless Attack to Injecting Remote shell on Windows
In order to distribute a previously undocumented backdoor named Rozena on Windows systems, an phishing campaign has recently been observed that leverages the recently disclosed Follina vulnerability. The Microsoft Windows Support Diagnostic Tool (MSDT) is an application that is designed for remote code execution, resulting in a CVE-2022-30190 vulnerability that was published in May 2022. […]
The post Rozena Backdoor Malware Uses a Fileless Attack to Injecting Remote shell on Windows appeared first on Cyber Security News.
https://cybersecuritynews.com/rozena-backdoor-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/rozena-backdoor-malware/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)