This article has been indexed from HackRead | Latest Cyber Crime – InfoSec- Tech – Hacking News By Owais Sultan Online gaming has always been the buddy of leisure time because they allow us to bring some enjoyment… This is…
Read more →
The post 5 Casual Games You Can Play on Your Mobile Browser Now first appeared on IT Security News.
https://www.itsecuritynews.info/5-casual-games-you-can-play-on-your-mobile-browser-now/?utm_source=dlvr.it&utm_medium=blogger
Saturday, May 21, 2022
Pwn2Own 2022: Windows 11, Ubuntu, Firefox, Safari, Tesla and more hacked
This article has been indexed from Security Software news and updates The hacking event Pwn2Own took place from May 18 to May 20 of 2022. This year, security researchers managed to hack Windows 11 and Ubuntu, Firefox, Safari, Microsoft Teams,…
Read more →
The post Pwn2Own 2022: Windows 11, Ubuntu, Firefox, Safari, Tesla and more hacked first appeared on IT Security News.
https://www.itsecuritynews.info/pwn2own-2022-windows-11-ubuntu-firefox-safari-tesla-and-more-hacked/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/pwn2own-2022-windows-11-ubuntu-firefox-safari-tesla-and-more-hacked/?utm_source=dlvr.it&utm_medium=blogger
US Reclaimed $15 Million From an Ad Fraud Operation
This article has been indexed from CySecurity News – Latest Information Security and Hacking Incidents The US government has recovered more than $15 million in earnings from the 3ve digital advertising fraud enterprise, which cost firms more than $29…
Read more →
The post US Reclaimed $15 Million From an Ad Fraud Operation first appeared on IT Security News.
https://www.itsecuritynews.info/us-reclaimed-15-million-from-an-ad-fraud-operation/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/us-reclaimed-15-million-from-an-ad-fraud-operation/?utm_source=dlvr.it&utm_medium=blogger
Conti: Russian-backed rulers of Costa Rican hacktocracy?
This article has been indexed from The Register – Security Also, Chinese IT admin jailed for deleting database, and the NSA promises no more backdoors In brief The notorious Russian-aligned Conti ransomware gang has upped the ante in its attack…
Read more →
The post Conti: Russian-backed rulers of Costa Rican hacktocracy? first appeared on IT Security News.
https://www.itsecuritynews.info/conti-russian-backed-rulers-of-costa-rican-hacktocracy/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/conti-russian-backed-rulers-of-costa-rican-hacktocracy/?utm_source=dlvr.it&utm_medium=blogger
Lazarus hackers Attack VMware Servers Using Log4Shell Exploits
One of the most prominent North Korean hacking groups, Lazarus exploited the Log4J RCE vulnerability known as “NukeSped” to inject backdoors aboard VMware Horizon servers to retrieve information stealing payloads. CVE-2021-44228 (log4Shell) is the CVE ID that has been tracked and identifies this vulnerability, which affects a wide range of products, including the VMware Horizon […]
The post Lazarus hackers Attack VMware Servers Using Log4Shell Exploits appeared first on Cyber Security News.
https://cybersecuritynews.com/lazarus-log4shell-exploits/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/lazarus-log4shell-exploits/?utm_source=dlvr.it&utm_medium=blogger
Friday, May 20, 2022
All White Hat hackers exempted from US CFAA Prosecution
This article has been indexed from Cybersecurity Insiders All White Hat hackers are from now on exempted from being prosecuted under the Computer Fraud and Abuse Act (CFAA) and this is official as per the statement released by the US…
Read more →
The post All White Hat hackers exempted from US CFAA Prosecution first appeared on IT Security News.
https://www.itsecuritynews.info/all-white-hat-hackers-exempted-from-us-cfaa-prosecution/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/all-white-hat-hackers-exempted-from-us-cfaa-prosecution/?utm_source=dlvr.it&utm_medium=blogger
New Bluetooth Bug Could Let Hackers Remotely Unlock Smart Locks, Laptops & Smartphones
A vulnerability in the Bluetooth technology can be exploited to remotely unlock tens of millions of digital locks worldwide, including those on Tesla cars. Sultan Qasim Khan, a researcher at the NCC Group successfully exploited the flaw to open and drive a Tesla Model 3 and Y model using a device attached to a laptop. […]
The post New Bluetooth Bug Could Let Hackers Remotely Unlock Smart Locks, Laptops & Smartphones appeared first on Cyber Security News.
https://cybersecuritynews.com/new-bluetooth-bug/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/new-bluetooth-bug/?utm_source=dlvr.it&utm_medium=blogger
Two business-grade Netgear VPN routers have security vulnerabilities that can’t be fixed
This article has been indexed from Help Net Security Netgear has admitted that multiple security vulnerabilities in its business-grade BR200 and BR500 VPN routers can’t be fixed due to technical limitations outside of their control, and is offering users a…
Read more →
The post Two business-grade Netgear VPN routers have security vulnerabilities that can’t be fixed first appeared on IT Security News.
https://www.itsecuritynews.info/two-business-grade-netgear-vpn-routers-have-security-vulnerabilities-that-cant-be-fixed/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/two-business-grade-netgear-vpn-routers-have-security-vulnerabilities-that-cant-be-fixed/?utm_source=dlvr.it&utm_medium=blogger
How To Do A Virus Scan
This article has been indexed from McAfee Blog How to Check for Viruses Whether you think you might have a virus on your computer or devices, or just… The post How To Do A Virus Scan appeared first on McAfee…
Read more →
The post How To Do A Virus Scan first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-do-a-virus-scan/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-to-do-a-virus-scan/?utm_source=dlvr.it&utm_medium=blogger
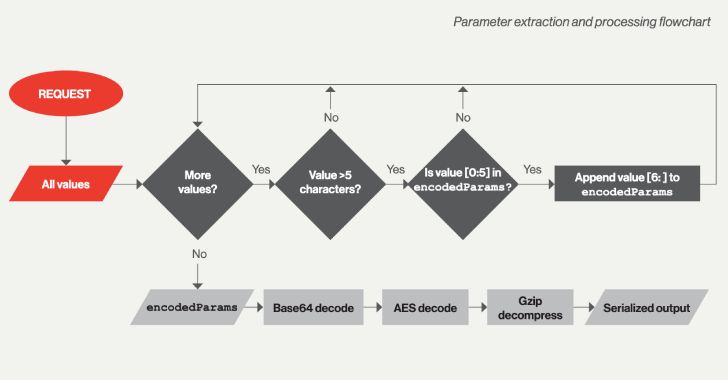
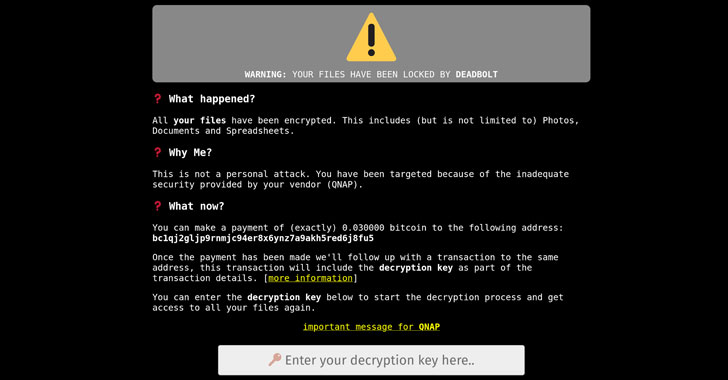
QNAP Urges Users to Update NAS Devices to Prevent Deadbolt Ransomware Attacks
Taiwanese network-attached storage (NAS) devices maker QNAP on Thursday warned its customers of a fresh wave of DeadBolt ransomware attacks.
The intrusions are said to have targeted TS-x51 series and TS-x53 series appliances running on QTS 4.3.6 and QTS 4.4.1, according to its product security incident response team.
"QNAP urges all NAS users to check and update QTS to the latest version as
https://thehackernews.com/2022/05/qnap-urges-users-to-update-nas-devices.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/qnap-urges-users-to-update-nas-devices.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, May 19, 2022
DOJ: Doctor is the Mastermind of Thanos Ransomware Design & Other Malicious Tools
The Department of Justice announced Monday that a French-Venezuelan doctor made the “Thanos” ransomware builder and other malicious tools that are used by cybercriminals. Moises Luis Zagala Gonzalez, 55, was charged in an unsealed criminal complaint filed in Brooklyn federal court last month with designing several tools to make it easier to be creative. Zargala’s […]
The post DOJ: Doctor is the Mastermind of Thanos Ransomware Design & Other Malicious Tools appeared first on Cyber Security News.
https://cybersecuritynews.com/doj-doctor-is-the-mastermind-of-ransomware-design/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/doj-doctor-is-the-mastermind-of-ransomware-design/?utm_source=dlvr.it&utm_medium=blogger
New Bluetooth Hack Could Let Attackers Remotely Unlock Smart Locks and Cars
A novel Bluetooth relay attack can let cybercriminals more easily than ever remotely unlock and operate cars, break open residential smart locks, and breach secure areas.
The vulnerability has to do with weaknesses in the current implementation of Bluetooth Low Energy (BLE), a wireless technology used for authenticating Bluetooth devices that are physically located within a close range.
https://thehackernews.com/2022/05/new-bluetooth-hack-could-let-attackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/new-bluetooth-hack-could-let-attackers.html?utm_source=dlvr.it&utm_medium=blogger
7 Key Findings from the 2022 SaaS Security Survey Report
The 2022 SaaS Security Survey Report, in collaboration with CSA, examines the state of SaaS security as seen in the eyes of CISOs and security professionals in today's enterprises. The report gathers anonymous responses from 340 CSA members to examine not only the growing risks in SaaS security but also how different organizations are currently working to secure themselves.
Demographics
The
https://thehackernews.com/2022/05/7-key-findings-from-2022-saas-security.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/7-key-findings-from-2022-saas-security.html?utm_source=dlvr.it&utm_medium=blogger
New macOS Malware Dubbed UpdateAgent Spotted in Wild with Upgrade Functionalities
A new variant of macOS malware dubbed UpdateAgent has been spotted in wild with upgrade functionalities by Jamf Threat Labs researchers. AWS is the platform that hosts the malicious payloads of the new version of the malware, UpdateAgent, and it is written in Swift. As a result of the recent update to this malware, it […]
The post New macOS Malware Dubbed UpdateAgent Spotted in Wild with Upgrade Functionalities appeared first on Cyber Security News.
https://cybersecuritynews.com/macos-malware-dubbed-updateagent/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/macos-malware-dubbed-updateagent/?utm_source=dlvr.it&utm_medium=blogger
VMware Releases Patches for New Vulnerabilities Affecting Multiple Products
VMware has issued patches to contain two security flaws impacting Workspace ONE Access, Identity Manager, and vRealize Automation that could be exploited to backdoor enterprise networks.
The first of the two flaws, tracked as CVE-2022-22972 (CVSS score: 9.8), concerns an authentication bypass that could enable an actor with network access to the UI to gain administrative access without prior
https://thehackernews.com/2022/05/vmware-releases-patches-for-new.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/vmware-releases-patches-for-new.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, May 18, 2022
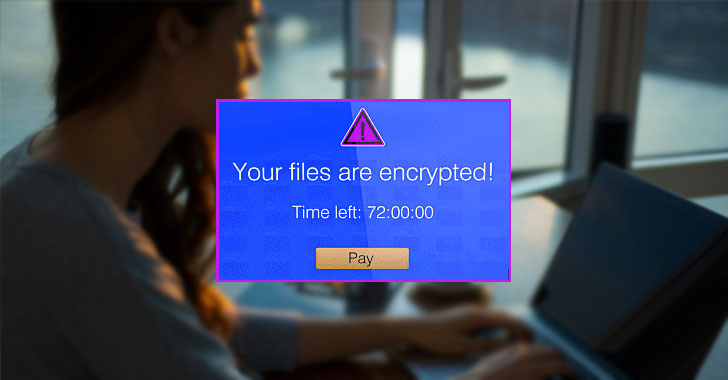
How to Protect Your Data When Ransomware Strikes
Ransomware is not a new attack vector. In fact, the first malware of its kind appeared more than 30 years ago and was distributed via 5.25-inch floppy disks. To pay the ransom, the victim had to mail money to a P.O. Box in Panama.
Fast forward to today, affordable ransomware-as-a-service (RaaS) kits are available on the dark web for anyone to purchase and deploy and attackers have an infinite
https://thehackernews.com/2022/05/how-to-protect-your-data-when.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/how-to-protect-your-data-when.html?utm_source=dlvr.it&utm_medium=blogger
Over 200 Malicious Android Apps On The Play Store Used To Steal Sensitive Data
Researchers at Trend Micro found recently that more than 200 Android applications are on the Google Play Store spreading spyware known as “Facestealer,” which aims to steal sensitive data from the compromised devices of the users. Maximum of these Android applications are found to be masquerading as the following categories of the applications:- Fitness apps […]
The post Over 200 Malicious Android Apps On The Play Store Used To Steal Sensitive Data appeared first on Cyber Security News.
https://cybersecuritynews.com/over-200-malicious-android-apps/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/over-200-malicious-android-apps/?utm_source=dlvr.it&utm_medium=blogger
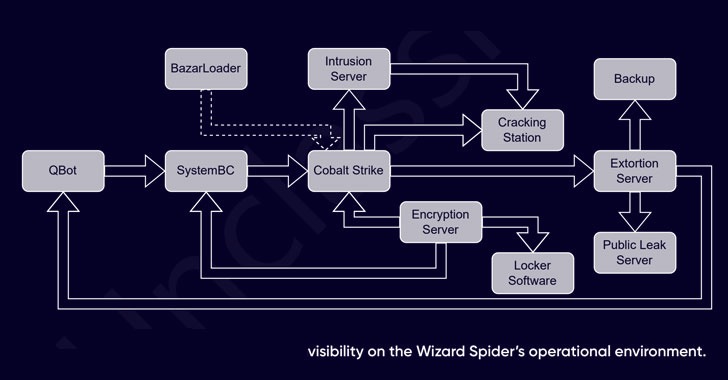
Researchers Expose Inner Workings of Billion-Dollar Wizard Spider Cybercrime Gang
The inner workings of a cybercriminal group known as the Wizard Spider have been exposed, shedding light on its organizational structure and motivations.
"Most of Wizard Spider's efforts go into hacking European and U.S. businesses, with a special cracking tool used by some of their attackers to breach high-value targets," Swiss cybersecurity company PRODAFT said in a new report shared with The
https://thehackernews.com/2022/05/researchers-expose-inner-working-of.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/researchers-expose-inner-working-of.html?utm_source=dlvr.it&utm_medium=blogger
NVIDIA Patches Code Execution Vulnerabilities in Graphics Driver
This article has been indexed from SecurityWeek RSS Feed NVIDIA has announced the roll-out of updates for its graphics drivers to address multiple vulnerabilities, including four CVEs rated “high severity.” read more Read the original article: NVIDIA Patches Code Execution…
Read more →
The post NVIDIA Patches Code Execution Vulnerabilities in Graphics Driver first appeared on IT Security News.
https://www.itsecuritynews.info/nvidia-patches-code-execution-vulnerabilities-in-graphics-driver/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/nvidia-patches-code-execution-vulnerabilities-in-graphics-driver/?utm_source=dlvr.it&utm_medium=blogger
Researchers Find a New Way to Execute Malware Even While The iPhone is Switched off
The iPhone does not completely shut down when you turn it off because it is not completely powered down. Researchers have devised a new kind of malware that can run even when the phone’s power is not on. This new type of malware was spotted by researchers at the Technical University of Darmstadt. It is […]
The post Researchers Find a New Way to Execute Malware Even While The iPhone is Switched off appeared first on Cyber Security News.
https://cybersecuritynews.com/execute-malware-iphone/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/execute-malware-iphone/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, May 17, 2022
Apple Releases Security Updates for Multiple Products
This article has been indexed from CISA All NCAS Products This post doesn’t have text content, please click on the link below to view the original article. Read the original article: Apple Releases Security Updates for Multiple Products
Read more →
The post Apple Releases Security Updates for Multiple Products first appeared on IT Security News.
https://www.itsecuritynews.info/apple-releases-security-updates-for-multiple-products-17/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-releases-security-updates-for-multiple-products-17/?utm_source=dlvr.it&utm_medium=blogger
In hot pursuit of ‘cryware’: Defending hot wallets from attacks
This article has been indexed from Microsoft Security Blog The rise in cryptocurrency market capitalization paved the way to the emergence of threats Microsoft security researchers are referring to as “cryware”—information stealers focused on gathering and exfiltrating data from non-custodial…
Read more →
The post In hot pursuit of ‘cryware’: Defending hot wallets from attacks first appeared on IT Security News.
https://www.itsecuritynews.info/in-hot-pursuit-of-cryware-defending-hot-wallets-from-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/in-hot-pursuit-of-cryware-defending-hot-wallets-from-attacks/?utm_source=dlvr.it&utm_medium=blogger
Are You Investing in Securing Your Data in the Cloud?
Traditional businesses migrating to the cloud need robust information security mechanisms. Gartner predicts that more than 95% of new digital workloads will continue to be deployed on cloud-native platforms by 2025.
Robust cloud data security is imperative for businesses adopting rapid digital transformation to the cloud. While a traditional hosting model could be considered more secure, not all
https://thehackernews.com/2022/05/are-you-investing-in-securing-your-data.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/are-you-investing-in-securing-your-data.html?utm_source=dlvr.it&utm_medium=blogger
How To Establish SAP Security
This article has been indexed from Cyber Defense Magazine By Christoph Nagy, CEO, SecurityBridge Malicious external cyber-threats certainly grab the headlines and leave businesses with no doubt […] The post How To Establish SAP Security appeared first on Cyber Defense…
Read more →
The post How To Establish SAP Security first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-establish-sap-security/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-to-establish-sap-security/?utm_source=dlvr.it&utm_medium=blogger
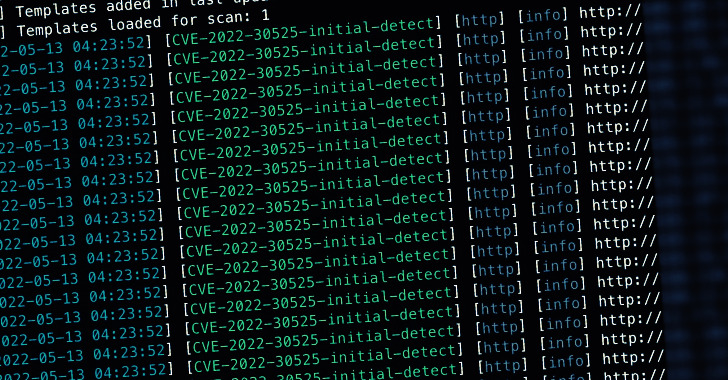
Watch Out! Hackers Begin Exploiting Recent Zyxel Firewalls RCE Vulnerability
Image source: z3r00t
The U.S. Cybersecurity and Infrastructure Security Agency on Monday added two security flaws, including the recently disclosed remote code execution bug affecting Zyxel firewalls, to its Known Exploited Vulnerabilities Catalog, citing evidence of active exploitation.
Tracked as CVE-2022-30525, the vulnerability is rated 9.8 for severity and relates to a command injection flaw
https://thehackernews.com/2022/05/watch-out-hackers-begin-exploiting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/watch-out-hackers-begin-exploiting.html?utm_source=dlvr.it&utm_medium=blogger
Monday, May 16, 2022
US Courts Are Coming After Crypto Exchanges That Skirt Sanctions
This article has been indexed from Security Latest A newly unsealed opinion is likely the first decision from a US federal court to find that cryptocurrencies can’t be used to evade sanctions. Read the original article: US Courts Are Coming…
Read more →
The post US Courts Are Coming After Crypto Exchanges That Skirt Sanctions first appeared on IT Security News.
https://www.itsecuritynews.info/us-courts-are-coming-after-crypto-exchanges-that-skirt-sanctions/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/us-courts-are-coming-after-crypto-exchanges-that-skirt-sanctions/?utm_source=dlvr.it&utm_medium=blogger
Microsoft showcases the future of comprehensive security at RSA 2022
This article has been indexed from Microsoft Security Blog RSA 2022 is happening in person—find out about Microsoft-sponsored sessions, pre-day events, speakers, awards, and more. The post Microsoft showcases the future of comprehensive security at RSA 2022 appeared first on…
Read more →
The post Microsoft showcases the future of comprehensive security at RSA 2022 first appeared on IT Security News.
https://www.itsecuritynews.info/microsoft-showcases-the-future-of-comprehensive-security-at-rsa-2022/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/microsoft-showcases-the-future-of-comprehensive-security-at-rsa-2022/?utm_source=dlvr.it&utm_medium=blogger
SonicWall Strongly Urges Organizations to Patch SSLVPN SMA1000 Bugs
SonicWall issued a security notice urging customers to immediately patch several vulnerabilities that are considered high-risk affecting its Secure Mobile Access (SMA) 1000 Series line of products. This can allow attackers to bypass authorization and, potentially, compromise unpatched appliances. The flaw tracked as CVE-2022-22282 in an unauthenticated access control bypass flaw affects SMA1000 series firmware […]
The post SonicWall Strongly Urges Organizations to Patch SSLVPN SMA1000 Bugs appeared first on Cyber Security News.
https://cybersecuritynews.com/sslvpn-sma1000-bugs/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/sslvpn-sma1000-bugs/?utm_source=dlvr.it&utm_medium=blogger
UK announces nuclear cybersecurity strategy
This article has been indexed from IT Security Guru The UK government has announced cybersecurity plans for the country’s civil nuclear sector in the newly published 2022 Civil Nuclear Cyber Security Strategy. The country’s nuclear program is growing into one…
Read more →
The post UK announces nuclear cybersecurity strategy first appeared on IT Security News.
https://www.itsecuritynews.info/uk-announces-nuclear-cybersecurity-strategy/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/uk-announces-nuclear-cybersecurity-strategy/?utm_source=dlvr.it&utm_medium=blogger
Ukrainian Hacker Jailed for 4-Years in U.S. for Selling Access to Hacked Servers
A 28-year-old Ukrainian national has been sentenced to four years in prison for siphoning thousands of server login credentials and selling them on the dark web for monetary gain as part of a credential theft scheme.
Glib Oleksandr Ivanov-Tolpintsev, who pleaded guilty to his offenses earlier this February, was arrested in Poland in October 2020, before being extradited to the U.S. in September
https://thehackernews.com/2022/05/ukrainian-hacker-jailed-for-4-years-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/ukrainian-hacker-jailed-for-4-years-in.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, May 15, 2022
How Education Decreases the Fear of Terrorism
This article has been indexed from Lawfare A person waits at a TSA checkpoint at John Glenn Columbus International Airport in Columbus, Ohio, on March 11, 2019. Photo credit: Michael Ball via Wikimedia; CC0 1.0. Editor’s Note: The gap between…
Read more →
The post How Education Decreases the Fear of Terrorism first appeared on IT Security News.
https://www.itsecuritynews.info/how-education-decreases-the-fear-of-terrorism/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-education-decreases-the-fear-of-terrorism/?utm_source=dlvr.it&utm_medium=blogger
Security Affairs newsletter Round 365 by Pierluigi Paganini
This article has been indexed from Security Affairs A new round of the weekly Security Affairs newsletter arrived! Every week the best security articles from Security Affairs for free in your email box. If you want to also receive for…
Read more →
The post Security Affairs newsletter Round 365 by Pierluigi Paganini first appeared on IT Security News.
https://www.itsecuritynews.info/security-affairs-newsletter-round-365-by-pierluigi-paganini/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/security-affairs-newsletter-round-365-by-pierluigi-paganini/?utm_source=dlvr.it&utm_medium=blogger
Sysrv-K, a new variant of the Sysrv botnet includes new exploits
This article has been indexed from Security Affairs Microsoft reported that the Sysrv botnet is targeting Windows and Linux servers exploiting flaws in the Spring Framework and WordPress. Microsoft Security Intelligence team Microsoft reported that a new variant of the Sysrv botnet, tracked…
Read more →
The post Sysrv-K, a new variant of the Sysrv botnet includes new exploits first appeared on IT Security News.
https://www.itsecuritynews.info/sysrv-k-a-new-variant-of-the-sysrv-botnet-includes-new-exploits/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/sysrv-k-a-new-variant-of-the-sysrv-botnet-includes-new-exploits/?utm_source=dlvr.it&utm_medium=blogger
Willyama Services launches a new cybersecurity subsidiary
This article has been indexed from Help Net Security Willyama Services a sovereign Australian, Indigenous and veteran owned technology company has launched a new subsidiary business named Willyama Cyber. Willyama Cyber was launched today at their Canberra headquarters by Andrew…
Read more →
The post Willyama Services launches a new cybersecurity subsidiary first appeared on IT Security News.
https://www.itsecuritynews.info/willyama-services-launches-a-new-cybersecurity-subsidiary/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/willyama-services-launches-a-new-cybersecurity-subsidiary/?utm_source=dlvr.it&utm_medium=blogger
Votiro completes SOC 2 Type II compliance for Votiro Cloud
This article has been indexed from Help Net Security Votiro announced that it has successfully completed a Service Organization Controls (SOC) 2 Type II compliance audit for the entire Votiro Cloud product line, demonstrating the company’s commitment to maintaining all…
Read more →
The post Votiro completes SOC 2 Type II compliance for Votiro Cloud first appeared on IT Security News.
https://www.itsecuritynews.info/votiro-completes-soc-2-type-ii-compliance-for-votiro-cloud/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/votiro-completes-soc-2-type-ii-compliance-for-votiro-cloud/?utm_source=dlvr.it&utm_medium=blogger
Saturday, May 14, 2022
The NSA Swears It Has ‘No Backdoors’ in Next-Gen Encryption
This article has been indexed from Security Latest Plus: New details of ICE’s dragnet surveillance in the US, Clearview AI agrees to limit sales of its faceprint database, and more. Read the original article: The NSA Swears It Has ‘No…
Read more →
The post The NSA Swears It Has ‘No Backdoors’ in Next-Gen Encryption first appeared on IT Security News.
https://www.itsecuritynews.info/the-nsa-swears-it-has-no-backdoors-in-next-gen-encryption/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-nsa-swears-it-has-no-backdoors-in-next-gen-encryption/?utm_source=dlvr.it&utm_medium=blogger
Pro-Russian hacktivists target Italy government websites
This article has been indexed from Security Affairs Pro-Russian hacker group Killnet targeted the websites of several Italian institutions, including the senate and the National Institute of Health. A group of Pro-Russian hackers known as “Killnet” launched an attack against…
Read more →
The post Pro-Russian hacktivists target Italy government websites first appeared on IT Security News.
https://www.itsecuritynews.info/pro-russian-hacktivists-target-italy-government-websites/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/pro-russian-hacktivists-target-italy-government-websites/?utm_source=dlvr.it&utm_medium=blogger
Threat Actors Using Telegram To Build & Spread ‘Eternity’ Malware-as-a-Service
The cybersecurity experts at Cyble Research Labs detected a new malware-as-a-service called ‘Eternity Project,’ where threat actors can buy custom malware tools according to their needs and purpose. In addition to being modular, the malware toolkit includes a range of other items and all these items can be purchased separately. Here we have mentioned all […]
The post Threat Actors Using Telegram To Build & Spread ‘Eternity’ Malware-as-a-Service appeared first on Cyber Security News.
https://cybersecuritynews.com/eternity-malware-as-a-service/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/eternity-malware-as-a-service/?utm_source=dlvr.it&utm_medium=blogger
Cyber Agencies: Beware of State Actors Levelling up Attacks on Managed Service Providers
This article has been indexed from CySecurity News – Latest Information Security and Hacking Incidents The United States, the United Kingdom, Australia, and Canada’s cybersecurity agencies issued a second advisory this week, stating that cyberattacks against managed service providers…
Read more →
The post Cyber Agencies: Beware of State Actors Levelling up Attacks on Managed Service Providers first appeared on IT Security News.
https://www.itsecuritynews.info/cyber-agencies-beware-of-state-actors-levelling-up-attacks-on-managed-service-providers/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cyber-agencies-beware-of-state-actors-levelling-up-attacks-on-managed-service-providers/?utm_source=dlvr.it&utm_medium=blogger
SonicWall Releases Patches for New Flaws Affecting SSLVPN SMA1000 Devices
SonicWall has published an advisory warning of a trio of security flaws in its Secure Mobile Access (SMA) 1000 appliances, including a high-severity authentication bypass vulnerability.
The weaknesses in question impact SMA 6200, 6210, 7200, 7210, 8000v running firmware versions 12.4.0 and 12.4.1. The list of vulnerabilities is below -
CVE-2022-22282 (CVSS score: 8.2) - Unauthenticated Access
https://thehackernews.com/2022/05/sonicwall-releases-patches-for-new.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/sonicwall-releases-patches-for-new.html?utm_source=dlvr.it&utm_medium=blogger
Friday, May 13, 2022
Google Created 'Open-Source Maintenance Crew' to Help Secure Critical Projects
Google on Thursday announced the creation of a new "Open Source Maintenance Crew" to focus on bolstering the security of critical open source projects.
Additionally, the tech giant pointed out Open Source Insights as a tool for analyzing packages and their dependency graphs, using it to determine "whether a vulnerability in a dependency might affect your code."
"With this information, developers
https://thehackernews.com/2022/05/google-created-open-source-maintenance.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/google-created-open-source-maintenance.html?utm_source=dlvr.it&utm_medium=blogger
Top 10 Best SysAdmin Tools For 2022
Running a system network is not so easy, and for this, you need to select the right sysadmin tools so that work can happen peacefully. Right tools do their job perfectly, so it does not make much difference. As an IT admin, you need to balance the needs regarding the network where the user needs […]
The post Top 10 Best SysAdmin Tools For 2022 appeared first on Cyber Security News.
https://cybersecuritynews.com/sysadmin-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/sysadmin-tools/?utm_source=dlvr.it&utm_medium=blogger
FluBot Financial Malware Delivered Through SMS and MMS
Flubot malware sends text messages to both Androids and iPhones. There are a large number of different types of Flubot text messages and scammers are updating them all the time. In Finland, the FluBot malware campaign has been activated again. This malware steals data from the user’s device and is distributed via SMS and MMS. […]
The post FluBot Financial Malware Delivered Through SMS and MMS appeared first on Cyber Security News.
https://cybersecuritynews.com/flubot-financial-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/flubot-financial-malware/?utm_source=dlvr.it&utm_medium=blogger
New Saitama backdoor Targeted Official from Jordan's Foreign Ministry
A spear-phishing campaign targeting Jordan's foreign ministry has been observed dropping a new stealthy backdoor dubbed Saitama.
Researchers from Malwarebytes and Fortinet FortiGuard Labs attributed the campaign to an Iranian cyber espionage threat actor tracked under the moniker APT34, citing resemblances to past campaigns staged by the group.
"Like many of these attacks, the email contained a
https://thehackernews.com/2022/05/new-saitama-backdoor-targeted-official.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/new-saitama-backdoor-targeted-official.html?utm_source=dlvr.it&utm_medium=blogger
Zyxel Releases Patch for Critical Firewall OS Command Injection Vulnerability
Zyxel has moved to address a critical security vulnerability affecting Zyxel firewall devices that enables unauthenticated and remote attackers to gain arbitrary code execution.
"A command injection vulnerability in the CGI program of some firewall versions could allow an attacker to modify specific files and then execute some OS commands on a vulnerable device," the company said in an advisory
https://thehackernews.com/2022/05/zyxel-releases-patch-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/zyxel-releases-patch-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, May 12, 2022
E.U. Proposes New Rules for Tech Companies to Combat Online Child Sexual Abuse
The European Commission on Wednesday proposed new regulation that would require tech companies to scan for child sexual abuse material (CSAM) and grooming behavior, raising worries that it could undermine end-to-end encryption (E2EE).
To that end, online service providers, including hosting services and communication apps, are expected to proactively scan their platforms for CSAM as well as
https://thehackernews.com/2022/05/eu-proposes-new-rules-for-tech.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/eu-proposes-new-rules-for-tech.html?utm_source=dlvr.it&utm_medium=blogger
CISA Urges Organizations to Patch Actively Exploited F5 BIG-IP Vulnerability
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added the recently disclosed F5 BIG-IP flaw to its Known Exploited Vulnerabilities Catalog following reports of active abuse in the wild.
The flaw, assigned the identifier CVE-2022-1388 (CVSS score: 9.8), concerns a critical bug in the BIG-IP iControl REST endpoint that provides an unauthenticated adversary with a method to
https://thehackernews.com/2022/05/cisa-urges-organizations-to-patch.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/cisa-urges-organizations-to-patch.html?utm_source=dlvr.it&utm_medium=blogger
Hackers Deploy IceApple Exploitation Framework on Hacked MS Exchange Servers
Researchers have detailed a previously undocumented .NET-based post-exploitation framework called IceApple that has been deployed on Microsoft Exchange server instances to facilitate reconnaissance and data exfiltration.
"Suspected to be the work of a state-nexus adversary, IceApple remains under active development, with 18 modules observed in use across a number of enterprise environments, as
https://thehackernews.com/2022/05/hackers-deploy-iceapple-exploitation.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/hackers-deploy-iceapple-exploitation.html?utm_source=dlvr.it&utm_medium=blogger
Bitter APT Hackers Add Bangladesh to Their List of Targets in South Asia
An espionage-focused threat actor known for targeting China, Pakistan, and Saudi Arabia has expanded to set its sights on Bangladeshi government organizations as part of an ongoing campaign that commenced in August 2021.
Cybersecurity firm Cisco Talos attributed the activity with moderate confidence to a hacking group dubbed the Bitter APT based on overlaps in the command-and-control (C2)
https://thehackernews.com/2022/05/bitter-apt-hackers-add-bangladesh-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/bitter-apt-hackers-add-bangladesh-to.html?utm_source=dlvr.it&utm_medium=blogger
[White Paper] Social Engineering: What You Need to Know to Stay Resilient
Security and IT teams are losing sleep as would-be intruders lay siege to the weakest link in any organization's digital defense: employees. By preying on human emotion, social engineering scams inflict billions of dollars of damage with minimal planning or expertise. Cybercriminals find it easier to manipulate people before resorting to technical "hacking" tactics. Recent research reveals that
https://thehackernews.com/2022/05/white-paper-social-engineering-what-you.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/05/white-paper-social-engineering-what-you.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)



.png)
















.jpg)