This article has been indexed from Help Net Security PTC and ITC Infotech announced an agreement to accelerate customer digital transformation initiatives, focused on the adoption of PTC’s Windchill product lifecycle management (PLM) software as a service (SaaS). ITC Infotech…
Read more →
The post PTC and ITC Infotech expand partnership to accelerate customer digital transformation initiatives first appeared on IT Security News.
https://www.itsecuritynews.info/ptc-and-itc-infotech-expand-partnership-to-accelerate-customer-digital-transformation-initiatives/?utm_source=dlvr.it&utm_medium=blogger
Sunday, April 24, 2022
Saturday, April 23, 2022
Dangerous malware is up 86%: Here’s how AI can help
This article has been indexed from Security – VentureBeat The need for AI-powered tools is only going to become more urgent as high-severity malware becomes more prevalent. Read the original article: Dangerous malware is up 86%: Here’s how AI can…
Read more →
The post Dangerous malware is up 86%: Here’s how AI can help first appeared on IT Security News.
https://www.itsecuritynews.info/dangerous-malware-is-up-86-heres-how-ai-can-help/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/dangerous-malware-is-up-86-heres-how-ai-can-help/?utm_source=dlvr.it&utm_medium=blogger
FBI Issues Warning as BlackCat Ransomware Targets More Than 60 Organizations Worldwide
This article has been indexed from CySecurity News – Latest Information Security and Hacking Incidents An FBI flash alert released this week suggests that the law enforcement agency has identified at least 60 ransomware attacks worldwide by the BlackCat…
Read more →
The post FBI Issues Warning as BlackCat Ransomware Targets More Than 60 Organizations Worldwide first appeared on IT Security News.
https://www.itsecuritynews.info/fbi-issues-warning-as-blackcat-ransomware-targets-more-than-60-organizations-worldwide/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/fbi-issues-warning-as-blackcat-ransomware-targets-more-than-60-organizations-worldwide/?utm_source=dlvr.it&utm_medium=blogger
Stellar Repair for Exchange – Best Exchange Recovery Tool Admins Should Use in Vulnerability
Although you try to protect the Exchange Servers as much as possible, they still become a target of cyber attacks or ransomware attack. Such attacks can be mitigated by ensuring you have the right protection on your machine and the latest Exchange Server Cumulative Updates (CU) and patches are installed. When you get hit by […]
The post Stellar Repair for Exchange – Best Exchange Recovery Tool Admins Should Use in Vulnerability appeared first on Cyber Security News.
https://cybersecuritynews.com/stellar-repair-for-exchange-best-exchange-recovery-tool-admins-should-use-in-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/stellar-repair-for-exchange-best-exchange-recovery-tool-admins-should-use-in-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
T-Mobile Admits Lapsus$ Hackers Gained Access to its Internal Tools and Source Code
This article has been indexed from The Hacker News Telecom company T-Mobile on Friday confirmed that it was the victim of a security breach in March after the LAPSUS$ mercenary gang managed to gain access to its networks. The acknowledgment…
Read more →
The post T-Mobile Admits Lapsus$ Hackers Gained Access to its Internal Tools and Source Code first appeared on IT Security News.
https://www.itsecuritynews.info/t-mobile-admits-lapsus-hackers-gained-access-to-its-internal-tools-and-source-code/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/t-mobile-admits-lapsus-hackers-gained-access-to-its-internal-tools-and-source-code/?utm_source=dlvr.it&utm_medium=blogger
Atlassian Drops Patches for Critical Jira Authentication Bypass Vulnerability
Atlassian has published a security advisory warning of a critical vulnerability in its Jira software that could be abused by a remote, unauthenticated attacker to circumvent authentication protections.
Tracked as CVE-2022-0540, the flaw is rated 9.9 out of 10 on the CVSS scoring system and resides in Jira's authentication framework, Jira Seraph. Khoadha of Viettel Cyber Security has been
https://thehackernews.com/2022/04/atlassian-drops-patches-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/atlassian-drops-patches-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
Friday, April 22, 2022
Unethical vulnerability disclosures ‘a disgrace to our field’
This article has been indexed from SearchSecurity This post doesn’t have text content, please click on the link below to view the original article. Read the original article: Unethical vulnerability disclosures ‘a disgrace to our field’
Read more →
The post Unethical vulnerability disclosures ‘a disgrace to our field’ first appeared on IT Security News.
https://www.itsecuritynews.info/unethical-vulnerability-disclosures-a-disgrace-to-our-field/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/unethical-vulnerability-disclosures-a-disgrace-to-our-field/?utm_source=dlvr.it&utm_medium=blogger
China’s NFT Plans Are a Recipe for the Government’s Digital Control
This article has been indexed from Lawfare Chinese President Xi Jinping. (Official photo by UN Geneva) China is doubling down on the idea of a wholly digital economy, constructing software infrastructure to support more expansive data analysis that is likely…
Read more →
The post China’s NFT Plans Are a Recipe for the Government’s Digital Control first appeared on IT Security News.
https://www.itsecuritynews.info/chinas-nft-plans-are-a-recipe-for-the-governments-digital-control/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/chinas-nft-plans-are-a-recipe-for-the-governments-digital-control/?utm_source=dlvr.it&utm_medium=blogger
Cybersecurity Authorities Warns that Russian State-Sponsored Attack Critical Infrastructure
Russia’s invasion of Ukraine has triggered several things globally. Even cyber attacks aren’t an exception. As tensions rise over Russia and Ukraine, the U.S and its allied countries have been imposing several economic costs against Russia and the materials provided to them. Russian State-Sponsored threat actors have been conducting several cyberattacks recently which included DDoS […]
The post Cybersecurity Authorities Warns that Russian State-Sponsored Attack Critical Infrastructure appeared first on Cyber Security News.
https://cybersecuritynews.com/authorities-warns-russian-hackers/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/authorities-warns-russian-hackers/?utm_source=dlvr.it&utm_medium=blogger
Researcher Releases PoC for Recent Java Cryptographic Vulnerability
A proof-of-concept (PoC) code demonstrating a newly disclosed digital signature bypass vulnerability in Java has been shared online.
The high-severity flaw in question, CVE-2022-21449 (CVSS score: 7.5), impacts the following version of Java SE and Oracle GraalVM Enterprise Edition -
Oracle Java SE: 7u331, 8u321, 11.0.14, 17.0.2, 18
Oracle GraalVM Enterprise Edition: 20.3.5, 21.3.1, 22.0.0.2
https://thehackernews.com/2022/04/researcher-releases-poc-for-recent-java.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/researcher-releases-poc-for-recent-java.html?utm_source=dlvr.it&utm_medium=blogger
Cisco Releases Security Patches for TelePresence, RoomOS and Umbrella VA
Networking equipment maker Cisco has released security updates to address three high-severity vulnerabilities in its products that could be exploited to cause a denial-of-service (DoS) condition and take control of affected systems.
The first of the three flaws, CVE-2022-20783 (CVSS score: 7.5), affects Cisco TelePresence Collaboration Endpoint (CE) Software and Cisco RoomOS Software, and stems
https://thehackernews.com/2022/04/cisco-releases-security-patches-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/cisco-releases-security-patches-for.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, April 21, 2022
Critical bug in decoder used by popular chipsets exposes 2/3 of Android devices to hack
This article has been indexed from Security Affairs A critical RCE flaw in Android devices running on Qualcomm and MediaTek chipsets could allow access to users’ media files. Security researchers at Check Point Research have discovered a critical remote code…
Read more →
The post Critical bug in decoder used by popular chipsets exposes 2/3 of Android devices to hack first appeared on IT Security News.
https://www.itsecuritynews.info/critical-bug-in-decoder-used-by-popular-chipsets-exposes-2-3-of-android-devices-to-hack/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/critical-bug-in-decoder-used-by-popular-chipsets-exposes-2-3-of-android-devices-to-hack/?utm_source=dlvr.it&utm_medium=blogger
Cloud-Based Firewall for Today and The Future
In the age of cloud computing, where data and other mission-critical assets are accessed over the Internet, it’s essential to secure your digital information. Information is crucial to malicious cybercrimes, but the fact is that nefarious individuals want to undermine it for purely financial gains. Cloud comes with benefits like collaboration and benefits but protecting a […]
The post Cloud-Based Firewall for Today and The Future appeared first on Cyber Security News.
https://cybersecuritynews.com/cloud-based-firewall-for-today-and-the-future/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cloud-based-firewall-for-today-and-the-future/?utm_source=dlvr.it&utm_medium=blogger
Hackers Sneak 'More_Eggs' Malware Into Resumes Sent to Corporate Hiring Managers
A new set of phishing attacks delivering the more_eggs malware has been observed striking corporate hiring managers with bogus resumes as an infection vector, a year after potential candidates looking for work on LinkedIn were lured with weaponized job offers.
"This year the more_eggs operation has flipped the social engineering script, targeting hiring managers with fake resumes instead of
https://thehackernews.com/2022/04/hackers-sneak-moreeggs-malware-into.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/hackers-sneak-moreeggs-malware-into.html?utm_source=dlvr.it&utm_medium=blogger
Snort Flaw Let Attacker to Trigger DoS Condition & Pass Malicious Traffic
An intrusion detection system called Snort has been found to have a security vulnerability, reported by the cyber security analysts at Team82. And this could trigger the occurrence of a denial of service (DoS) condition, making the system ineffective. This security flaw has been assigned with CVE ID, “CVE-2022-20685,” and it has managed to achieve […]
The post Snort Flaw Let Attacker to Trigger DoS Condition & Pass Malicious Traffic appeared first on Cyber Security News.
https://cybersecuritynews.com/snort-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/snort-flaw/?utm_source=dlvr.it&utm_medium=blogger
New Incident Report Reveals How Hive Ransomware Targets Organizations
A recent Hive ransomware attack carried out by an affiliate involved the exploitation of "ProxyShell" vulnerabilities in the Microsoft Exchange Server that were disclosed last year to encrypt an unnamed customer's network.
"The actor managed to achieve its malicious goals and encrypt the environment in less than 72 hours from the initial compromise," Varonis security researcher, Nadav Ovadia,
https://thehackernews.com/2022/04/new-incident-report-reveals-how-hive.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/new-incident-report-reveals-how-hive.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, April 20, 2022
How SD-WANs improve security
If you haven’t heard about this technology yet, definitely you should start learning about it. Not just Enterprise network engineers, but Service Provider people as well. It helps everyone to reduce their cost, provide much more insights about their IT…
Read more →
The post How SD-WANs improve security first appeared on IT Security News.
https://www.itsecuritynews.info/how-sd-wans-improve-security/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-sd-wans-improve-security/?utm_source=dlvr.it&utm_medium=blogger
Google Project Zero Detects a Record Number of Zero-Day Exploits in 2021
Google Project Zero called 2021 a "record year for in-the-wild 0-days," as 58 security vulnerabilities were detected and disclosed during the course of the year.
The development marks more than a two-fold jump from the previous maximum when 28 0-day exploits were tracked in 2015. In contrast, only 25 0-day exploits were detected in 2020.
"The large uptick in in-the-wild 0-days in 2021 is due to
https://thehackernews.com/2022/04/google-project-zero-detects-record.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/google-project-zero-detects-record.html?utm_source=dlvr.it&utm_medium=blogger
[eBook] The Ultimate Security for Management Presentation Template
Are you a CISO, CIO, or IT Director?
In your role, you're responsible for breach protection – which means you oversee and govern the process of designing, building, maintaining, and continuously enhancing your organization's security program.
But getting buy-in from leadership can be difficult when they are a non-technical audience.
On top of managing your organization's breach protection
https://thehackernews.com/2022/04/ebook-ultimate-security-for-management.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/ebook-ultimate-security-for-management.html?utm_source=dlvr.it&utm_medium=blogger
Okta Says Security Breach by Lapsus$ Hackers Impacted Only Two of Its Customers
Identity and access management provider Okta on Tuesday said it concluded its probe into the breach of a third-party vendor in late January 2022 by the LAPSUS$ extortionist gang.
Stating that the "impact of the incident was significantly less than the maximum potential impact" the company had previously shared last month, Okta said the intrusion impacted only two customer tenants, down from 366
https://thehackernews.com/2022/04/okta-says-security-breach-by-lapsus.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/okta-says-security-breach-by-lapsus.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, April 19, 2022
Hackers Exploiting Recently Reported Windows Print Spooler Vulnerability in the Wild
A security flaw in the Windows Print Spooler component that was patched by Microsoft in February is being actively exploited in the wild, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has warned.
To that end, the agency has added the shortcoming to its Known Exploited Vulnerabilities Catalog, requiring Federal Civilian Executive Branch (FCEB) agencies to address the issues by
https://thehackernews.com/2022/04/hackers-exploiting-recently-reported.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/hackers-exploiting-recently-reported.html?utm_source=dlvr.it&utm_medium=blogger
New Lenovo UEFI Firmware Vulnerabilities Affect Millions of Laptops
Three high-impact Unified Extensible Firmware Interface (UEFI) security vulnerabilities have been discovered impacting various Lenovo consumer laptop models, enabling malicious actors to deploy and execute firmware implants on the affected devices.
Tracked as CVE-2021-3970, CVE-2021-3971, and CVE-2021-3972, the latter two "affect firmware drivers originally meant to be used only during the
https://thehackernews.com/2022/04/new-lenovo-uefi-firmware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/new-lenovo-uefi-firmware.html?utm_source=dlvr.it&utm_medium=blogger
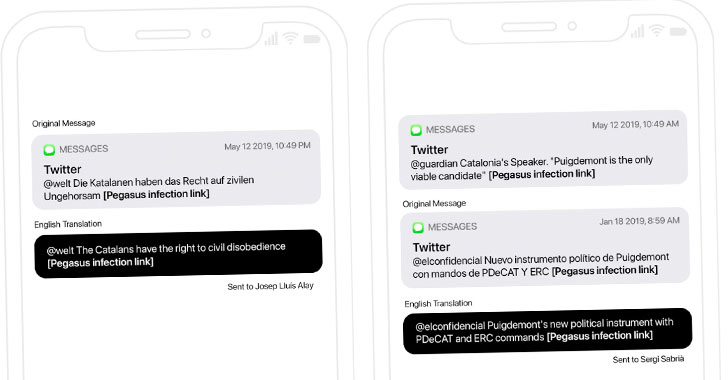
Experts Uncover Spyware Attacks Against Catalan Politicians and Activists
A previously unknown zero-click exploit in Apple's iMessage was used to install mercenary spyware from NSO Group and Candiru against at least 65 individuals as part of a "multi-year clandestine operation."
"Victims included Members of the European Parliament, Catalan Presidents, legislators, jurists, and members of civil society organizations," the University of Toronto's Citizen Lab said in a
https://thehackernews.com/2022/04/experts-uncover-spyware-attacks-against.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/experts-uncover-spyware-attacks-against.html?utm_source=dlvr.it&utm_medium=blogger
FBI, U.S. Treasury and CISA Warn of North Korean Hackers Targeting Blockchain Companies
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), along with the Federal Bureau of Investigation (FBI) and the Treasury Department, warned of a new set of ongoing cyber attacks carried out by the Lazarus Group targeting blockchain companies.
Calling the activity cluster TraderTraitor, the infiltrations involve the North Korean state-sponsored advanced persistent threat (APT)
https://thehackernews.com/2022/04/fbi-us-treasury-and-cisa-warns-of-north.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/fbi-us-treasury-and-cisa-warns-of-north.html?utm_source=dlvr.it&utm_medium=blogger
Github Notifies Victims Whose Private Data Was Accessed Using OAuth Tokens
GitHub on Monday noted that it had notified all victims of an attack campaign, which involved an unauthorized party downloading private repository contents by taking advantage of third-party OAuth user tokens maintained by Heroku and Travis CI.
"Customers should also continue to monitor Heroku and Travis CI for updates on their own investigations into the affected OAuth applications," the
https://thehackernews.com/2022/04/github-notifies-victims-whose-private.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/github-notifies-victims-whose-private.html?utm_source=dlvr.it&utm_medium=blogger
Monday, April 18, 2022
The Importance of Cyber Education in College
Cybersecurity is one of the most popular terms in the digital world. How to define it? Basically, cybersecurity is the practice of protecting computer systems, networks and programs from cyberattacks aimed at accessing, altering, or deleting sensitive information. The final goal of cyberattacks may be stealing money or interrupting business processes. Nowadays, it’s quite challenging […]
The post The Importance of Cyber Education in College appeared first on Cyber Security News.
https://cybersecuritynews.com/the-importance-of-cyber-education-in-college/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/the-importance-of-cyber-education-in-college/?utm_source=dlvr.it&utm_medium=blogger
New SolarMarker Malware Variant Using Updated Techniques to Stay Under the Radar
Cybersecurity researchers have disclosed a new version of the SolarMarker malware that packs in new improvements with the goal of updating its defense evasion abilities and staying under the radar.
"The recent version demonstrated an evolution from Windows Portable Executables (EXE files) to working with Windows installer package files (MSI files)," Palo Alto Networks Unit 42 researchers said in
https://thehackernews.com/2022/04/new-solarmarker-malware-variant-using.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/new-solarmarker-malware-variant-using.html?utm_source=dlvr.it&utm_medium=blogger
New Hacking Campaign Targeting Ukrainian Government with IcedID Malware
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new wave of social engineering campaigns delivering IcedID malware and leveraging Zimbra exploits with the goal of stealing sensitive information.
Attributing the IcedID phishing attacks to a threat cluster named UAC-0041, the agency said the infection sequence begins with an email containing a Microsoft Excel document (
https://thehackernews.com/2022/04/new-hacking-campaign-targeting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/new-hacking-campaign-targeting.html?utm_source=dlvr.it&utm_medium=blogger
Critical RCE Flaw Reported in WordPress Elementor Website Builder Plugin
Elementor, a WordPress website builder plugin with over five million active installations, has been found to be vulnerable to an authenticated remote code execution flaw that could be abused to take over affected websites.
Plugin Vulnerabilities, which disclosed the flaw last week, said the bug was introduced in version 3.6.0 that was released on March 22, 2022. Roughly 37% of users of the
https://thehackernews.com/2022/04/critical-rce-flaw-reported-in-wordpress.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/critical-rce-flaw-reported-in-wordpress.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, April 17, 2022
Top 10 Best Free Penetration Testing Tools 2022
When we talk about the penetration Testing tools, we all know very well that the first thing that comes up to our mind is the threat. As we all know very well that we use penetration testing and hacking tools for recognizing security vulnerabilities in a network, server, or in a web application. Generally, all […]
The post Top 10 Best Free Penetration Testing Tools 2022 appeared first on Cyber Security News.
https://cybersecuritynews.com/penetration-testing-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/penetration-testing-tools/?utm_source=dlvr.it&utm_medium=blogger
Saturday, April 16, 2022
Get Lifetime Access to This 60-Hour Java Programming Training Bundle @ 97% Discount
Java is a very versatile programming language. From Android apps to Oracle databases, it can be used to power a wide range of software and systems. As with most technical skills, the best way to learn Java is through building your own projects. But you can definitely speed things up with high-quality training.
The Complete 2022 Java Coder Bundle provides plenty of that — nine full-length video
https://thehackernews.com/2022/04/get-lifetime-access-to-this-60-hour.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/get-lifetime-access-to-this-60-hour.html?utm_source=dlvr.it&utm_medium=blogger
Lazarus Group Behind $540 Million Axie Infinity Crypto Hack and Attacks on Chemical Sector
The U.S. Treasury Department has implicated the North Korea-backed Lazarus Group (aka Hidden Cobra) in the theft of $540 million from video game Axie Infinity's Ronin Network last month.
On Thursday, the Treasury tied the Ethereum wallet address that received the stolen funds to the threat actor and sanctioned the funds by adding the address to the Office of Foreign Assets Control's (OFAC)
https://thehackernews.com/2022/04/lazarus-hackers-behind-540-million-axie.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/lazarus-hackers-behind-540-million-axie.html?utm_source=dlvr.it&utm_medium=blogger
Friday, April 15, 2022
FBI Warns that Hackers Attack Users of Digital Payment Apps to Make Instant Money Transfers
Hackers targeting money are not something new. The way they target differs with improvements in technology. To alert users during a fraudulent transaction from a stolen credit card, Banks used to send a message alert to the victims to confirm whether the transaction was initiated by the users. Threat actors are now spoofing these message […]
The post FBI Warns that Hackers Attack Users of Digital Payment Apps to Make Instant Money Transfers appeared first on Cyber Security News.
https://cybersecuritynews.com/fbi-warns-that-hackers-attack-users-of-digital-payment-apps-to-make-instant-money-transfers/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/fbi-warns-that-hackers-attack-users-of-digital-payment-apps-to-make-instant-money-transfers/?utm_source=dlvr.it&utm_medium=blogger
US Warns of APT Hackers Attacking Industrial Control Systems
The security agencies of the US government, “CISA, FBI, DOE, and NSA,” have recently released a joint security advisory that alerts about the ongoing attacks against the industrial control systems (ICS) and SCADA devices using malware by the state-sponsored hacking groups. Here’s what the security agencies have stated:- “The APT actors have developed custom-made tools […]
The post US Warns of APT Hackers Attacking Industrial Control Systems appeared first on Cyber Security News.
https://cybersecuritynews.com/us-warns-of-apt-hackers/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/us-warns-of-apt-hackers/?utm_source=dlvr.it&utm_medium=blogger
JekyllBot:5 Flaws Let Attackers Take Control of Aethon TUG Hospital Robots
As many as five security vulnerabilities have been addressed in Aethon Tug hospital robots that could enable remote attackers to seize control of the devices and interfere with the timely distribution of medication and lab samples.
"Successful exploitation of these vulnerabilities could cause a denial-of-service condition, allow full control of robot functions, or expose sensitive information,"
https://thehackernews.com/2022/04/new-jekyllbot5-flaws-let-attackers-take.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/new-jekyllbot5-flaws-let-attackers-take.html?utm_source=dlvr.it&utm_medium=blogger
As State-Backed Cyber Threats Grow, Here's How the World Is Reacting
With the ongoing conflict in Eurasia, cyberwarfare is inevitably making its presence felt. The fight is not only being fought on the fields. There is also a big battle happening in cyberspace. Several cyber-attacks have been reported over the past months.
Notably, cyber attacks backed by state actors are becoming prominent. There have been reports of a rise of ransomware and other malware
https://thehackernews.com/2022/04/as-state-backed-cyber-threats-grow.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/as-state-backed-cyber-threats-grow.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, April 14, 2022
Google Releases Urgent Chrome Update to Patch Actively Exploited Zero-Day Flaw
Google on Thursday shipped emergency patches to address two security issues in its Chrome web browser, one of which it says is being actively exploited in the wild.
Tracked as CVE-2022-1364, the tech giant described the high-severity bug as a case of type confusion in the V8 JavaScript engine. Clément Lecigne of Google's Threat Analysis Group has been credited with reporting the flaw on April 13
https://thehackernews.com/2022/04/google-releases-urgent-chrome-update-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/google-releases-urgent-chrome-update-to.html?utm_source=dlvr.it&utm_medium=blogger
Ethereum Developer Jailed 63 Months for Helping North Korea Evade Sanctions
A U.S. court has sentenced former Ethereum developer Virgil Griffith to five years and three months in prison and pay a $100,000 fine for conspiring with North Korea to help use cryptocurrencies to circumvent sanctions imposed on the country.
"There is no question North Korea poses a national security threat to our nation, and the regime has shown time and again it will stop at nothing to ignore
https://thehackernews.com/2022/04/ethereum-developer-jailed-63-months-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/ethereum-developer-jailed-63-months-for.html?utm_source=dlvr.it&utm_medium=blogger
New EnemyBot DDoS Botnet Borrows Exploit Code from Mirai and Gafgyt
A threat group that pursues crypto mining and distributed denial-of-service (DDoS) attacks has been linked to a new botnet called Enemybot, which has been discovered enslaving routers and Internet of Things (IoT) devices since last month.
"This botnet is mainly derived from Gafgyt's source code but has been observed to borrow several modules from Mirai's original source code," Fortinet
https://thehackernews.com/2022/04/new-enemybot-ddos-botnet-borrows.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/new-enemybot-ddos-botnet-borrows.html?utm_source=dlvr.it&utm_medium=blogger
Microsoft Disrupts ZLoader Cybercrime Botnet in Global Operation
Microsoft and a consortium of cybersecurity companies took legal and technical steps to disrupt the ZLoader botnet, seizing control of 65 domains that were used to control and communicate with the infected hosts.
"ZLoader is made up of computing devices in businesses, hospitals, schools, and homes around the world and is run by a global internet-based organized crime gang operating malware as a
https://thehackernews.com/2022/04/microsoft-disrupts-zloader-cybercrime.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/microsoft-disrupts-zloader-cybercrime.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, April 13, 2022
Critical VMware Workspace ONE Access Flaw Under Active Exploitation in the Wild
A week after VMware released patches to remediate eight security vulnerabilities in VMware Workspace ONE Access, threat actors have begun to actively exploit one of the critical flaws in the wild.
Tracked as CVE-2022-22954, the critical issue relates to a remote code execution vulnerability that stems from server-side template injection in VMware Workspace ONE Access and Identity Manager. The
https://thehackernews.com/2022/04/vmware-releases-patches-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/vmware-releases-patches-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
Facebook Blocked Russia and Belarus Hackers Targeting Ukraine
Ever since 2018, Facebook (now called Meta) has been sharing its open findings through adversary reports. Recently, Meta has released a report which has the following information. Three cyber-espionage networks from Iran and Azerbaijan removed Ukraine security update Removing four networks for coordinated inauthentic behavior Removing a mass reporting network in Russia Removing a coordinated […]
The post Facebook Blocked Russia and Belarus Hackers Targeting Ukraine appeared first on Cyber Security News.
https://cybersecuritynews.com/facebook-blocked-russia-and-belarus-hackers/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/facebook-blocked-russia-and-belarus-hackers/?utm_source=dlvr.it&utm_medium=blogger
Windows Autopatch – A New Feature for Organizations to Keep Endpoints up-to-date
IT professionals suffer a lot when trying to update operating systems and software. Usually, every second Tuesday of the month will be a huge struggle for IT admins as they have to check and update every software. Microsoft came up with a new solution for this. They have introduced a new feature called “Windows Autopatch” […]
The post Windows Autopatch – A New Feature for Organizations to Keep Endpoints up-to-date appeared first on Cyber Security News.
https://cybersecuritynews.com/windows-autopatch/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/windows-autopatch/?utm_source=dlvr.it&utm_medium=blogger
Russian Hackers Tried Attacking Ukraine's Power Grid with Industroyer2 Malware
The Computer Emergency Response Team of Ukraine (CERT-UA) on Tuesday disclosed that it thwarted a cyberattack by Sandworm, a hacking group affiliated with Russia's military intelligence, to sabotage the operations of an unnamed energy provider in the country.
"The attackers attempted to take down several infrastructure components of their target, namely: Electrical substations, Windows-operated
https://thehackernews.com/2022/04/russian-hackers-tried-attacking.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/russian-hackers-tried-attacking.html?utm_source=dlvr.it&utm_medium=blogger
FBI, Europol Seize RaidForums Hacker Forum and Arrest Admin
An international law enforcement operation raided and took down RaidForums, one of the world's largest hacking forums notorious for selling access to hacked personal information belonging to users.
Dubbed Tourniquet, the seizure of the cybercrime website involved authorities from the U.S., U.K., Sweden, Portugal, and Romania, with the criminal investigation resulting in the arrest of the forum's
https://thehackernews.com/2022/04/fbi-europol-seize-raidforums-hacker.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/fbi-europol-seize-raidforums-hacker.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, April 12, 2022
Cross-Regional Disaster Recovery with Elasticsearch
Unsurprisingly, here at Rewind, we've got a lot of data to protect (over 2 petabytes worth). One of the databases we use is called Elasticsearch (ES or Opensearch, as it is currently known in AWS). To put it simply, ES is a document database that facilitates lightning-fast search results. Speed is essential when customers are looking for a particular file or item that they need to restore using
https://thehackernews.com/2022/04/cross-regional-disaster-recovery-with.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/cross-regional-disaster-recovery-with.html?utm_source=dlvr.it&utm_medium=blogger
Critical LFI Vulnerability Reported in Hashnode Blogging Platform
Researchers have disclosed a previously undocumented local file inclusion (LFI) vulnerability in Hashnode, a developer-oriented blogging platform, that could be abused to access sensitive data such as SSH keys, server's IP address, and other network information.
"The LFI originates in a Bulk Markdown Import feature that can be manipulated to provide attackers with unimpeded ability to download
https://thehackernews.com/2022/04/critical-lfi-vulnerability-reported-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/critical-lfi-vulnerability-reported-in.html?utm_source=dlvr.it&utm_medium=blogger
Google Sues Scammer for Running 'Puppy Fraud Scheme' Website
Google on Monday disclosed that it's taking legal action against a nefarious actor who has been spotted operating fraudulent websites to defraud unsuspecting people into buying non-existent puppies.
"The actor used a network of fraudulent websites that claimed to sell basset hound puppies — with alluring photos and fake customer testimonials — in order to take advantage of people during the
https://thehackernews.com/2022/04/google-sues-scammer-for-running-puppy.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/04/google-sues-scammer-for-running-puppy.html?utm_source=dlvr.it&utm_medium=blogger
Monday, April 11, 2022
What is SQL injection and How Can You Protect Your Business From It?
With more businesses using the web, there is more space for online hackers to attack new sites that aren’t adequately protected. Moreover, it seems to be a preferred method of attack by hackers as 51% of them use it to attack an organization’s sensitive data! The use of web applications will continue to expand in […]
The post What is SQL injection and How Can You Protect Your Business From It? appeared first on Cyber Security News.
https://cybersecuritynews.com/what-is-sql-injection-and-how-can-you-protect-your-business-from-it/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/what-is-sql-injection-and-how-can-you-protect-your-business-from-it/?utm_source=dlvr.it&utm_medium=blogger
Beware of New Android Banking Malware that Completely Controls Your Device
Octo, a new Android banking malware that employs remote access capabilities to enable attackers to commit on-device fraud, has been identified in the wild and is designed to prey on vulnerable Android devices. The Octo malware that strikes Android is a variation of ExoCompact, an Exo trojan-based malware that was used by cybercriminals before it […]
The post Beware of New Android Banking Malware that Completely Controls Your Device appeared first on Cyber Security News.
https://cybersecuritynews.com/new-android-banking-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/new-android-banking-malware/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)
























.png)