Signature-based detection has been the cornerstone of the security strategy of organizations for a long. Thanks to rapid technological advancements, attackers constantly find ways to evade and subvert defense mechanisms and traditional security tools. So, signature-based detection techniques are not enough in today’s new and constantly evolving attack landscape. Read on as we delve into […]
The post Why Signature-Based Detection Struggles to Keep Up with the New Attack Landscape? appeared first on Cyber Security News.
https://cybersecuritynews.com/signature-based-detection/?utm_source=dlvr.it&utm_medium=blogger
Monday, February 21, 2022
Hackers Exploiting Infected Android Devices to Register Disposable Accounts
An analysis of SMS phone-verified account (PVA) services has led to the discovery of a rogue platform built atop a botnet involving thousands of infected Android phones, once again underscoring the flaws with relying on SMS for account validation.
SMS PVA services, since gain prevalence in 2018, provide users with alternative mobile numbers that can be used to register for other online services
https://thehackernews.com/2022/02/hackers-exploit-bug-in-sms-verification.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/hackers-exploit-bug-in-sms-verification.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 20, 2022
New Unredacter Tool Extracts Text From Pixelized Images
This article has been indexed from Latest Hacking News Researchers have again proved why pixelation of images can be a bad idea to hide… New Unredacter Tool Extracts Text From Pixelized Images on Latest Hacking News. Read the original article:…
Read more →
The post New Unredacter Tool Extracts Text From Pixelized Images first appeared on IT Security News.
https://www.itsecuritynews.info/new-unredacter-tool-extracts-text-from-pixelized-images/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/new-unredacter-tool-extracts-text-from-pixelized-images/?utm_source=dlvr.it&utm_medium=blogger
Responding To the Ransomware Pandemic
This article has been indexed from Cyber Defense Magazine By Tom McVey, Solution Architect, Menlo Security Last year, Kaseya became the victim of the largest ransomware attack […] The post Responding To the Ransomware Pandemic appeared first on Cyber Defense…
Read more →
The post Responding To the Ransomware Pandemic first appeared on IT Security News.
https://www.itsecuritynews.info/responding-to-the-ransomware-pandemic/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/responding-to-the-ransomware-pandemic/?utm_source=dlvr.it&utm_medium=blogger
The who, what, and where of cryptography for the C-suite
This article has been indexed from Security – VentureBeat Cryptography and encryption offer many advantages, but adoption still isn’t widespread — largely due to many lingering misconceptions. Read the original article: The who, what, and where of cryptography for the…
Read more →
The post The who, what, and where of cryptography for the C-suite first appeared on IT Security News.
https://www.itsecuritynews.info/the-who-what-and-where-of-cryptography-for-the-c-suite/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-who-what-and-where-of-cryptography-for-the-c-suite/?utm_source=dlvr.it&utm_medium=blogger
PseudoManuscrypt Malware Proliferating Similarly as CryptBot Targets Koreans
This article has been indexed from CySecurity News – Latest Information Security and Hacking Incidents Since at least May 2021, a botnet known as PseudoManuscrypt has been targeting Windows workstations in South Korea, using the same delivery methods as…
Read more →
The post PseudoManuscrypt Malware Proliferating Similarly as CryptBot Targets Koreans first appeared on IT Security News.
https://www.itsecuritynews.info/pseudomanuscrypt-malware-proliferating-similarly-as-cryptbot-targets-koreans/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/pseudomanuscrypt-malware-proliferating-similarly-as-cryptbot-targets-koreans/?utm_source=dlvr.it&utm_medium=blogger
French Dad Takes nearby Town Internet Down to Prevent his Kids Going Online
A hefty fine has been imposed recently by ANFR on a French dad due to which he faced jail time. In this event, the alleged dad used a signal jammer to stop his kids from using the internet. But, the fun fact here happened accidentally is that along with his kids he also prevented the […]
The post French Dad Takes nearby Town Internet Down to Prevent his Kids Going Online appeared first on Cyber Security News.
https://cybersecuritynews.com/dad-takes-nearby-town-internet-down/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/dad-takes-nearby-town-internet-down/?utm_source=dlvr.it&utm_medium=blogger
Saturday, February 19, 2022
IT Security News Daily Summary 2022-02-19
How assuming fraudsters are lazy can help prevent cyberattacks Versa Networks Included in Gartner® Magic Quadrant™ Millions of WordPress Sites Got a Forced Update for a Serious Bug US senators introduce the Kids Online Safety Act (KOSA) Watch out for…
Read more →
The post IT Security News Daily Summary 2022-02-19 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2022-02-19/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2022-02-19/?utm_source=dlvr.it&utm_medium=blogger
Watch out for this bump in LinkedIn phishing
This article has been indexed from Malwarebytes Labs
Read more →
The post Watch out for this bump in LinkedIn phishing first appeared on IT Security News.
https://www.itsecuritynews.info/watch-out-for-this-bump-in-linkedin-phishing/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/watch-out-for-this-bump-in-linkedin-phishing/?utm_source=dlvr.it&utm_medium=blogger
Beware of Hackers Dropping Malicious Executable Files in Teams Conversations
Cybersecurity researchers at Avanan security firm have recently detected that some threat actors are compromising Microsoft Teams. Because of the popularity of Microsoft, the threat actors are continuously targetting and aiming at Microsoft. The main motive of the threat actor is to plant malicious documents in the chat threads, which generally implement Trojans. And there […]
The post Beware of Hackers Dropping Malicious Executable Files in Teams Conversations appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-through-microsoft-teams/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/malware-through-microsoft-teams/?utm_source=dlvr.it&utm_medium=blogger
Critical Flaw Uncovered in WordPress Backup Plugin Used by Over 3 Million Sites
Patches have been issued to contain a "severe" security vulnerability in UpdraftPlus, a WordPress plugin with over three million installations, that can be weaponized to download the site's private data using an account on the vulnerable sites.
"All versions of UpdraftPlus from March 2019 onwards have contained a vulnerability caused by a missing permissions-level check, allowing untrusted users
https://thehackernews.com/2022/02/critical-flaw-uncovered-in-wordpress.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/critical-flaw-uncovered-in-wordpress.html?utm_source=dlvr.it&utm_medium=blogger
Tips to Stay Secure During the Rise of Email Fraud
Phishing protection has become increasingly important as more crooks resort to internet frauds to steal your personal information from you. We’ve all learned to avoid spam emails, but phishing emails may be deceivingly convincing in their appearance. Some of them are even customized to your unique needs. Because you will almost certainly be subjected to […]
The post Tips to Stay Secure During the Rise of Email Fraud appeared first on Cyber Security News.
https://cybersecuritynews.com/tips-to-stay-secure-during-the-rise-of-email-fraud/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/tips-to-stay-secure-during-the-rise-of-email-fraud/?utm_source=dlvr.it&utm_medium=blogger
Friday, February 18, 2022
Singapore builds National Quantum-Safe Network to enhance network security for critical infrastructure
This article has been indexed from Help Net Security Singapore’s Quantum Engineering Programme (QEP) will start conducting nationwide trials of quantum-safe communication technologies that promise robust network security for critical infrastructure and companies handling sensitive data. Supported by the National…
Read more →
The post Singapore builds National Quantum-Safe Network to enhance network security for critical infrastructure first appeared on IT Security News.
https://www.itsecuritynews.info/singapore-builds-national-quantum-safe-network-to-enhance-network-security-for-critical-infrastructure/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/singapore-builds-national-quantum-safe-network-to-enhance-network-security-for-critical-infrastructure/?utm_source=dlvr.it&utm_medium=blogger
Free Cybersecurity Tools and Services List Published by CISA
This article has been indexed from Dark Reading The Cybersecurity & Infrastructure Security Agency (CISA) says this “living repository” is a mix of popular open source and free tools and services from both the private and public sectors. Read the…
Read more →
The post Free Cybersecurity Tools and Services List Published by CISA first appeared on IT Security News.
https://www.itsecuritynews.info/free-cybersecurity-tools-and-services-list-published-by-cisa/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/free-cybersecurity-tools-and-services-list-published-by-cisa/?utm_source=dlvr.it&utm_medium=blogger
Microsoft Warns of 'Ice Phishing' Threat on Web3 and Decentralized Networks
Microsoft has warned of emerging threats in the Web3 landscape, including "ice phishing" campaigns, as a surge in adoption of blockchain and DeFi technologies emphasizes the need to build security into the decentralized web while it's still in its early stages.
The company's Microsoft 365 Defender Research Team called out various new avenues through which malicious actors may attempt to trick
https://thehackernews.com/2022/02/microsoft-warns-of-ice-phishing-threat.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/microsoft-warns-of-ice-phishing-threat.html?utm_source=dlvr.it&utm_medium=blogger
Iranian State Broadcaster Clobbered by ‘Clumsy, Buggy’ Code
This article has been indexed from Threatpost Researchers said a Jan. 27 attack that aired footage of opposition leaders calling for assassination of Iran’s Supreme Leader was a clumsy and unsophisticated wiper attack. Read the original article: Iranian State Broadcaster…
Read more →
The post Iranian State Broadcaster Clobbered by ‘Clumsy, Buggy’ Code first appeared on IT Security News.
https://www.itsecuritynews.info/iranian-state-broadcaster-clobbered-by-clumsy-buggy-code/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/iranian-state-broadcaster-clobbered-by-clumsy-buggy-code/?utm_source=dlvr.it&utm_medium=blogger
Another Critical RCE Discovered in Adobe Commerce and Magento Platforms
Adobe on Thursday updated its advisory for an actively exploited zero-day affecting Adobe Commerce and Magento Open Source to patch a newly discovered flaw that could be weaponized to achieve arbitrary code execution.
Tracked as CVE-2022-24087, the issue – like CVE-2022-24086 – is rated 9.8 on the CVSS vulnerability scoring system and relates to an "Improper Input Validation" bug
https://thehackernews.com/2022/02/another-critical-rce-discovered-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/another-critical-rce-discovered-in.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, February 17, 2022
Philadelphia launches digital equity plan
This article has been indexed from GCN – All Content The five-year plan describes how the city will address affordability of broadband and devices and tackle the fundamental issues that contribute to the digital divide: barriers of language, race, limited…
Read more →
The post Philadelphia launches digital equity plan first appeared on IT Security News.
https://www.itsecuritynews.info/philadelphia-launches-digital-equity-plan/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/philadelphia-launches-digital-equity-plan/?utm_source=dlvr.it&utm_medium=blogger
Vulnerability in Linux program enables local privilege escalation, researchers report
This article has been indexed from Security – VentureBeat A new vulnerability in Linux software can be exploited for local privilege escalation and to gain root privileges, Qualys researchers said. Read the original article: Vulnerability in Linux program enables local…
Read more →
The post Vulnerability in Linux program enables local privilege escalation, researchers report first appeared on IT Security News.
https://www.itsecuritynews.info/vulnerability-in-linux-program-enables-local-privilege-escalation-researchers-report/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/vulnerability-in-linux-program-enables-local-privilege-escalation-researchers-report/?utm_source=dlvr.it&utm_medium=blogger
Singapore to build quantum-safe network for critical infrastructure trials
This article has been indexed from Latest topics for ZDNet in Security National network will initially comprise 10 nodes across the country and provide a testbed for public and private organisations to trial critical infrastructure applications within a quantum-safe environment.…
Read more →
The post Singapore to build quantum-safe network for critical infrastructure trials first appeared on IT Security News.
https://www.itsecuritynews.info/singapore-to-build-quantum-safe-network-for-critical-infrastructure-trials/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/singapore-to-build-quantum-safe-network-for-critical-infrastructure-trials/?utm_source=dlvr.it&utm_medium=blogger
Google Bringing Privacy Sandbox to Android to Limit Sharing of User Data
Google on Wednesday announced plans to bring its Privacy Sandbox initiatives to Android in a bid to expand its privacy-focused, but also less disruptive, advertising technology beyond the desktop web.
To that end, the internet giant said it will work towards building solutions that prevent cross-app tracking à la Apple's App Tracking Transparency (ATT) framework, effectively limiting sharing of
https://thehackernews.com/2022/02/google-bringing-privacy-sandbox-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/google-bringing-privacy-sandbox-to.html?utm_source=dlvr.it&utm_medium=blogger
U.S. Says Russian Hackers Stealing Sensitive Data from Defense Contractors
State-sponsored actors backed by the Russian government regularly targeted the networks of several U.S. cleared defense contractors (CDCs) to acquire proprietary documents and other confidential information pertaining to the country's defense and intelligence programs and capabilities.
The sustained espionage campaign is said to have commenced at least two years ago from January 2020, according
https://thehackernews.com/2022/02/us-says-russian-hackers-stealing.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/us-says-russian-hackers-stealing.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, February 16, 2022
Best Risk Management Software for 2022
This article has been indexed from eSecurityPlanet Every organization needs visibility into the potential threats they face daily. Enterprise risk management software can provide risk monitoring, identification, analysis, assessment, and mitigation, all in one solution. While a number of solutions…
Read more →
The post Best Risk Management Software for 2022 first appeared on IT Security News.
https://www.itsecuritynews.info/best-risk-management-software-for-2022/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/best-risk-management-software-for-2022/?utm_source=dlvr.it&utm_medium=blogger
Missouri maps COVID in wastewater
This article has been indexed from GCN – All Content The Sewershed Surveillance Program gets samples from more than 100 locations – covering more than half the state’s population – to create maps that help decision-makers monitor trends in the…
Read more →
The post Missouri maps COVID in wastewater first appeared on IT Security News.
https://www.itsecuritynews.info/missouri-maps-covid-in-wastewater/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/missouri-maps-covid-in-wastewater/?utm_source=dlvr.it&utm_medium=blogger
[Webinar] When More Is Not Better: Solving Alert Overload
The increasing volume and sophistication of cyberattacks have naturally led many companies to invest in additional cybersecurity technologies. We know that expanded threat detection capabilities are necessary for protection, but they have also led to several unintended consequences. The “more is not always better” adage fits this situation perfectly.
An upcoming webinar by cybersecurity company
https://thehackernews.com/2022/02/webinar-when-more-is-not-better-solving.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/webinar-when-more-is-not-better-solving.html?utm_source=dlvr.it&utm_medium=blogger
Trickbot Malware Targeted Customers of 60 High-Profile Companies Since 2020
The notorious TrickBot malware is targeting customers of 60 financial and technology companies, including cryptocurrency firms, primarily located in the U.S., even as its operators have updated the botnet with new anti-analysis features.
"TrickBot is a sophisticated and versatile malware with more than 20 modules that can be downloaded and executed on demand," Check Point researchers Aliaksandr
https://thehackernews.com/2022/02/trickbot-malware-targeted-customers-of.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/trickbot-malware-targeted-customers-of.html?utm_source=dlvr.it&utm_medium=blogger
BlackByte Ransomware Breached US Critical Infrastructure
Ransomware threats has been on the rise with update in several technologies. Many threat actor groups have been providing RaaS based ransomware services to cybercriminals. The Federal Bureau of Investigation (FBI) and the U.S. Secret Service (USSS) posted that as of November 2021, the BlackByte Ransomware has compromised several entities in the U.S Critical infrastructure […]
The post BlackByte Ransomware Breached US Critical Infrastructure appeared first on Cyber Security News.
https://cybersecuritynews.com/blackbyte-ransomware-breached-us-critical-infrastructure/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/blackbyte-ransomware-breached-us-critical-infrastructure/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, February 15, 2022
Druva launches MSP program in Asia-Pacific and Japan to improve operational efficiency
This article has been indexed from Help Net Security Druva launched its Managed Service Provider (MSP) program in Asia-Pacific and Japan (APJ). Part of the Druva Compass Partner Program, the expanded program is designed to empower MSPs in the region…
Read more →
The post Druva launches MSP program in Asia-Pacific and Japan to improve operational efficiency first appeared on IT Security News.
https://www.itsecuritynews.info/druva-launches-msp-program-in-asia-pacific-and-japan-to-improve-operational-efficiency/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/druva-launches-msp-program-in-asia-pacific-and-japan-to-improve-operational-efficiency/?utm_source=dlvr.it&utm_medium=blogger
Google has released Chrome 98 to fix active Zero-day Exploits
Google has recently released Chrome 98.0.4758.102, in which Google has fixed a critical zero-day vulnerability that is actively exploited by the threat actors. This new version of Chrome (98.0.4758.102) is released for all the major platforms, and here they are mentioned below:- Windows Mac Linux Here’s what the security team of Google has stated:- “Google […]
The post Google has released Chrome 98 to fix active Zero-day Exploits appeared first on Cyber Security News.
https://cybersecuritynews.com/google-chrome-98/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/google-chrome-98/?utm_source=dlvr.it&utm_medium=blogger
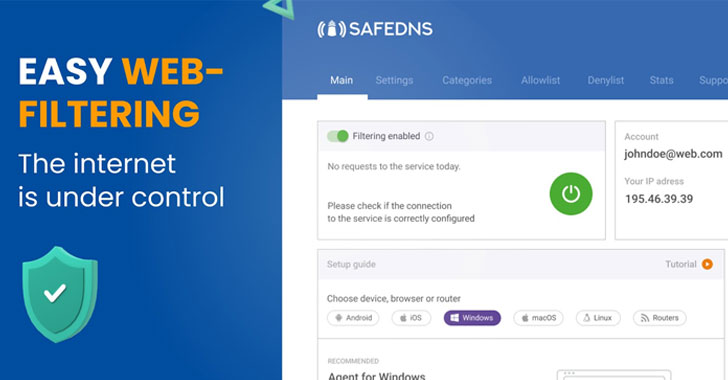
SafeDNS: Cloud-based Internet Security and Web Filtering Solution for MSPs
Remote workplace trend is getting the upper hand in 2022. A recent survey by IWG (the International Workplace Group) determined that 70% of the world's professionals work remotely at least one day a week, with 53% based outside their workplace at least half of the week.
Taking this into consideration, organizations have started looking for reliable partners that can deliver services and support
https://thehackernews.com/2022/02/safedns-cloud-based-internet-security.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/safedns-cloud-based-internet-security.html?utm_source=dlvr.it&utm_medium=blogger
SMS PVA Services’ Use of Infected Android Phones Reveals Flaws in SMS Verification
This article has been indexed from Trend Micro Research, News and Perspectives Certain SMS PVA services allow their customers to create disposable user profiles or register multiple accounts on many popular online platforms. These services can be abused by criminals…
Read more →
The post SMS PVA Services’ Use of Infected Android Phones Reveals Flaws in SMS Verification first appeared on IT Security News.
https://www.itsecuritynews.info/sms-pva-services-use-of-infected-android-phones-reveals-flaws-in-sms-verification/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/sms-pva-services-use-of-infected-android-phones-reveals-flaws-in-sms-verification/?utm_source=dlvr.it&utm_medium=blogger
New Chrome 0-Day Bug Under Active Attack – Update Your Browser ASAP!
Google on Monday rolled out fixes for eight security issues in the Chrome web browser, including a high-severity vulnerability that's being actively exploited in real-world attacks, marking the first zero-day patched by the internet giant in 2022.
The shortcoming, tracked CVE-2022-0609, is described as a use-after-free vulnerability in the Animation component that, if successfully exploited,
https://thehackernews.com/2022/02/new-chrome-0-day-bug-under-active.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/new-chrome-0-day-bug-under-active.html?utm_source=dlvr.it&utm_medium=blogger
Monday, February 14, 2022
What does a CR mean for DOD tech talent?
This article has been indexed from FCW – All Content The Defense Department and military services often rely on pay incentives to recruit and retain tech talent, and these could be hampered by long term stopgap funding. Read the original…
Read more →
The post What does a CR mean for DOD tech talent? first appeared on IT Security News.
https://www.itsecuritynews.info/what-does-a-cr-mean-for-dod-tech-talent/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/what-does-a-cr-mean-for-dod-tech-talent/?utm_source=dlvr.it&utm_medium=blogger
Apple Updates Support App With Repair Cost Estimates in Some Locations
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Apple today updated its Apple Support app designed for the iPhone and iPad, introducing a new feature that provides price estimates for common repairs in select…
Read more →
The post Apple Updates Support App With Repair Cost Estimates in Some Locations first appeared on IT Security News.
https://www.itsecuritynews.info/apple-updates-support-app-with-repair-cost-estimates-in-some-locations/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-updates-support-app-with-repair-cost-estimates-in-some-locations/?utm_source=dlvr.it&utm_medium=blogger
Authorities Arrested SIM Swapping Hacker Group For Stealing Money
Eight alleged members of the SIM swapping hacker group were arrested recently by the Spanish National Police for stealing money by compromising the bank accounts of their victims. The primary aim of these threat actors:- Target their victims with phishing attacks. Then obtain their personal information. And then, to steal money, they proceed to rob […]
The post Authorities Arrested SIM Swapping Hacker Group For Stealing Money appeared first on Cyber Security News.
https://cybersecuritynews.com/authorities-arrested-sim-swapping-hacker-group-for-stealing-money/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/authorities-arrested-sim-swapping-hacker-group-for-stealing-money/?utm_source=dlvr.it&utm_medium=blogger
The Importance of Cybersecurity in Universities
Cybersecurity is the protection of systems, data, software, and hardware connected to the Internet. Its main objective is to protect the data, many of which are confidential, of the universities by preventing data theft, cyber-attacks, and identity theft. The accelerated process of integration of information technologies in universities has generated significant positive impacts on the […]
The post The Importance of Cybersecurity in Universities appeared first on Cyber Security News.
https://cybersecuritynews.com/the-importance-of-cybersecurity-in-universities/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/the-importance-of-cybersecurity-in-universities/?utm_source=dlvr.it&utm_medium=blogger
Critical Magento 0-Day Vulnerability Under Active Exploitation — Patch Released
Adobe on Sunday rolled out patches to contain a critical security vulnerability impacting its Commerce and Magento Open Source products that it said is being actively exploited in the wild.
Tracked as CVE-2022-24086, the shortcoming has a CVSS score of 9.8 out of 10 on the vulnerability scoring system and has been characterized as an "improper input validation" issue that could be weaponized to
https://thehackernews.com/2022/02/critical-magento-0-day-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/critical-magento-0-day-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 13, 2022
3 Opportunities for Startups Interested in the Defense Marketplace
This article has been indexed from Cyber Security – American Security Today By Jeff Decker, Program Director with Hacking for Defense Stanford University* The U.S. Defense Department (DoD) has one of the largest budgets in the world, awarding $445 billion…
Read more →
The post 3 Opportunities for Startups Interested in the Defense Marketplace first appeared on IT Security News.
https://www.itsecuritynews.info/3-opportunities-for-startups-interested-in-the-defense-marketplace/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/3-opportunities-for-startups-interested-in-the-defense-marketplace/?utm_source=dlvr.it&utm_medium=blogger
Blackbyte ransomware hits San Francisco 49ers ahead of Super Bowl
This article has been indexed from Latest topics for ZDNet in Security The team was added to the group’s list of victims this weekend. Read the original article: Blackbyte ransomware hits San Francisco 49ers ahead of Super Bowl
Read more →
The post Blackbyte ransomware hits San Francisco 49ers ahead of Super Bowl first appeared on IT Security News.
https://www.itsecuritynews.info/blackbyte-ransomware-hits-san-francisco-49ers-ahead-of-super-bowl/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/blackbyte-ransomware-hits-san-francisco-49ers-ahead-of-super-bowl/?utm_source=dlvr.it&utm_medium=blogger
Fixing Common AD Security Issues With BloodHound FOSS
This article has been indexed from DZone Security Zone Active Directory (AD) is Microsoft’s identity and access management software that controls which users have access to the systems and resources on a network. It’s a popular target for attackers because…
Read more →
The post Fixing Common AD Security Issues With BloodHound FOSS first appeared on IT Security News.
https://www.itsecuritynews.info/fixing-common-ad-security-issues-with-bloodhound-foss/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/fixing-common-ad-security-issues-with-bloodhound-foss/?utm_source=dlvr.it&utm_medium=blogger
The Hacking Group ‘ModifiedElephant’ Remained Undetected
This article has been indexed from CySecurity News – Latest Information Security and Hacking Incidents SentinelLabs’ IT security researchers have discovered information of growing cyber-attacks (APT) wherein the threat actors have been targeting human rights activists, free speech advocates,…
Read more →
The post The Hacking Group ‘ModifiedElephant’ Remained Undetected first appeared on IT Security News.
https://www.itsecuritynews.info/the-hacking-group-modifiedelephant-remained-undetected/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-hacking-group-modifiedelephant-remained-undetected/?utm_source=dlvr.it&utm_medium=blogger
Organizations are addressing zero-day vulnerabilities more quickly, says Google
This article has been indexed from Security Affairs Organizations are addressing zero-day vulnerabilities more quickly, compared to last year, Google’s Project Zero reported. According to Google’s Project Zero researchers, organizations are addressing zero-day vulnerabilities more quickly, compared to last year.…
Read more →
The post Organizations are addressing zero-day vulnerabilities more quickly, says Google first appeared on IT Security News.
https://www.itsecuritynews.info/organizations-are-addressing-zero-day-vulnerabilities-more-quickly-says-google/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/organizations-are-addressing-zero-day-vulnerabilities-more-quickly-says-google/?utm_source=dlvr.it&utm_medium=blogger
Saturday, February 12, 2022
Decision Trees in Case of a Ransomware Attack
This article has been indexed from Cyber Defense Magazine Does Your Organization Have a Procedure to Handle a Ransomware? Is It Worth Paying the Attackers? By Zsolt […] The post Decision Trees in Case of a Ransomware Attack appeared first…
Read more →
The post Decision Trees in Case of a Ransomware Attack first appeared on IT Security News.
https://www.itsecuritynews.info/decision-trees-in-case-of-a-ransomware-attack/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/decision-trees-in-case-of-a-ransomware-attack/?utm_source=dlvr.it&utm_medium=blogger
The CIA Has Secretly Run a “Bulk Collection” Program
This article has been indexed from Security Latest Plus: Vulnerability fixes, the return of EARN IT, and more of the week’s top security news. Read the original article: The CIA Has Secretly Run a “Bulk Collection” Program
Read more →
The post The CIA Has Secretly Run a “Bulk Collection” Program first appeared on IT Security News.
https://www.itsecuritynews.info/the-cia-has-secretly-run-a-bulk-collection-program/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-cia-has-secretly-run-a-bulk-collection-program/?utm_source=dlvr.it&utm_medium=blogger
Croatian phone carrier A1 Hrvatska discloses data breach
This article has been indexed from Security Affairs Croatian phone carrier A1 Hrvatska has disclosed a data breach that has impacted roughly 200,000 customers. Croatian phone carrier A1 Hrvatska has disclosed a data breach that has impacted 10% of its…
Read more →
The post Croatian phone carrier A1 Hrvatska discloses data breach first appeared on IT Security News.
https://www.itsecuritynews.info/croatian-phone-carrier-a1-hrvatska-discloses-data-breach/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/croatian-phone-carrier-a1-hrvatska-discloses-data-breach/?utm_source=dlvr.it&utm_medium=blogger
Cloudflare acquires Vectrix to help businesses gain control of their SaaS applications
This article has been indexed from Help Net Security Cloudflare announced that it has acquired Vectrix, a company that provides businesses one-click visibility and control across all of their SaaS applications. Vectrix enhances Cloudflare’s existing Zero Trust platform, Cloudflare One,…
Read more →
The post Cloudflare acquires Vectrix to help businesses gain control of their SaaS applications first appeared on IT Security News.
https://www.itsecuritynews.info/cloudflare-acquires-vectrix-to-help-businesses-gain-control-of-their-saas-applications/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cloudflare-acquires-vectrix-to-help-businesses-gain-control-of-their-saas-applications/?utm_source=dlvr.it&utm_medium=blogger
Russia Seizes Four Major Dark Web Carding Estimated $263M in Crypto Sales
Recently, Four Major Illicit DarkWeb sites have been taken down by the Russian Ministry. Sky-Fraud Trump’s Dumps UAS Store Ferum Shop Millions of payment card details are stolen from retailers and payment companies every day and are sold in the Darkweb market for crypto assets. Cybercriminals use these cards to purchase items online which can […]
The post Russia Seizes Four Major Dark Web Carding Estimated $263M in Crypto Sales appeared first on Cyber Security News.
https://cybersecuritynews.com/fall-of-stolen-credit-card-market/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/fall-of-stolen-credit-card-market/?utm_source=dlvr.it&utm_medium=blogger
Friday, February 11, 2022
iPhone 13 is Significantly Faster Than Samsung’s New Galaxy S22 in Benchmarks
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Samsung’s new Galaxy S22 models are some of the fastest Android smartphones ever, but Apple still has the world’s fastest mobile processor by a considerable margin.…
Read more →
The post iPhone 13 is Significantly Faster Than Samsung’s New Galaxy S22 in Benchmarks first appeared on IT Security News.
https://www.itsecuritynews.info/iphone-13-is-significantly-faster-than-samsungs-new-galaxy-s22-in-benchmarks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/iphone-13-is-significantly-faster-than-samsungs-new-galaxy-s22-in-benchmarks/?utm_source=dlvr.it&utm_medium=blogger
CISA Adds One Known Exploited Vulnerability to Catalog
This article has been indexed from CISA All NCAS Products This post doesn’t have text content, please click on the link below to view the original article. Read the original article: CISA Adds One Known Exploited Vulnerability to Catalog
Read more →
The post CISA Adds One Known Exploited Vulnerability to Catalog first appeared on IT Security News.
https://www.itsecuritynews.info/cisa-adds-one-known-exploited-vulnerability-to-catalog-3/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cisa-adds-one-known-exploited-vulnerability-to-catalog-3/?utm_source=dlvr.it&utm_medium=blogger
FritzFrog Botnet Is Back and Focuses on Education, Healthcare, and Government Entities
This article has been indexed from Heimdal Security Blog The FritzFrog botnet, which has been operative for more than two years, has reemerged with a concerning infection rate, having grodawn tenfold in just a month after compromising medical, education, and…
Read more →
The post FritzFrog Botnet Is Back and Focuses on Education, Healthcare, and Government Entities first appeared on IT Security News.
https://www.itsecuritynews.info/fritzfrog-botnet-is-back-and-focuses-on-education-healthcare-and-government-entities/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/fritzfrog-botnet-is-back-and-focuses-on-education-healthcare-and-government-entities/?utm_source=dlvr.it&utm_medium=blogger
23 UEFI Flaws Impact Millions of Devices From Several Vendors
The cybersecurity analysts have recently identified 23 critical UEFI vulnerabilities impacting millions of several well-renowned vendors, and here we have mentioned all the major ones below:- HP Lenovo Fujitsu Microsoft Intel Dell Bull Siemens These flaws concern the products of more than 25 suppliers, and due to these critical vulnerabilities, millions of devices were affected […]
The post 23 UEFI Flaws Impact Millions of Devices From Several Vendors appeared first on Cyber Security News.
https://cybersecuritynews.com/23-uefi-flaws/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/23-uefi-flaws/?utm_source=dlvr.it&utm_medium=blogger
U.S. Arrests Two and Seizes $3.6 Billion Cryptocurrency Stolen in 2016 Bitfinex Hack
The U.S. Justice Department (DoJ) on Tuesday announced the arrest of a married couple in connection with conspiring to launder cryptocurrency worth $4.5 billion that was siphoned during the hack of the virtual currency exchange Bitfinex in 2016.
Ilya Lichtenstein, 34, and his wife, Heather Morgan, 31, both of New York, are alleged to have "stolen funds through a labyrinth of cryptocurrency
https://thehackernews.com/2022/02/us-arrests-two-and-seizes-36-million-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/02/us-arrests-two-and-seizes-36-million-in.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)