This article has been indexed from SecurityWeek RSS Feed U.S. President Joe Biden this week signed a memorandum on boosting the cybersecurity of National Security, Department of Defense, and Intelligence Community Systems. read more Read the original article: Industry Reactions…
Read more →
The post Industry Reactions to Biden Cybersecurity Memo: Feedback Friday first appeared on IT Security News.
https://www.itsecuritynews.info/industry-reactions-to-biden-cybersecurity-memo-feedback-friday/?utm_source=dlvr.it&utm_medium=blogger
Friday, January 21, 2022
Specialized BHUNT Malware Targets Cryptocurrency Wallets to Steal User Funds
Malicious actors have been targeting cryptocurrencies ever since they start Bitcoin Boom. They have started to tune their focus towards cryptocurrency wallets since they can easily transfer funds when they gain access. Last year statistics showed a surge in cryptocurrency stealers like WeSteal and Redline Stealer Researchers at Bitdefender found a dropper with a hidden […]
The post Specialized BHUNT Malware Targets Cryptocurrency Wallets to Steal User Funds appeared first on Cyber Security News.
https://cybersecuritynews.com/bhunt-malware-crypto/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/bhunt-malware-crypto/?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 20, 2022
This 22-Year-Old Builds Chips in His Parents’ Garage
This article has been indexed from HITBSecNews – Keeping Knowledge Free for Over a Decade This 22-Year-Old Builds Chips in His Parents’ Garage l33tdawg Thu, 01/20/2022 – 23:14 Read the original article: This 22-Year-Old Builds Chips in His Parents’ Garage
Read more →
The post This 22-Year-Old Builds Chips in His Parents’ Garage first appeared on IT Security News.
https://www.itsecuritynews.info/this-22-year-old-builds-chips-in-his-parents-garage/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/this-22-year-old-builds-chips-in-his-parents-garage/?utm_source=dlvr.it&utm_medium=blogger
Reflections on the One Year Anniversary of An Inauguration
This article has been indexed from Lawfare President Joe Biden takes the oath of office as President of the United States Wednesday, Jan. 20, 2021, during the 59th Presidential Inauguration at the U.S. Capitol in Washington, D.C. (Official White House…
Read more →
The post Reflections on the One Year Anniversary of An Inauguration first appeared on IT Security News.
https://www.itsecuritynews.info/reflections-on-the-one-year-anniversary-of-an-inauguration/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/reflections-on-the-one-year-anniversary-of-an-inauguration/?utm_source=dlvr.it&utm_medium=blogger
Incident Response – Everything You Need to Know
This article has been indexed from Heimdal Security Blog You probably heard us say this before: a cybersecurity incident can happen anytime, anywhere, to anyone, with consequences that vary from data leaks to losing huge amounts of money or even…
Read more →
The post Incident Response – Everything You Need to Know first appeared on IT Security News.
https://www.itsecuritynews.info/incident-response-everything-you-need-to-know/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/incident-response-everything-you-need-to-know/?utm_source=dlvr.it&utm_medium=blogger
Google Details Two Zero-Day Bugs Reported in Zoom Clients and MMR Servers
An exploration of zero-click attack surface for the popular video conferencing solution Zoom has yielded two previously undisclosed security vulnerabilities that could be exploited to crash the service, execute malicious code, and even leak arbitrary areas of its memory.
Natalie Silvanovich of Google Project Zero, who discovered and reported the two flaws last year, said the issues impact both
https://thehackernews.com/2022/01/google-details-two-zero-day-bugs.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/google-details-two-zero-day-bugs.html?utm_source=dlvr.it&utm_medium=blogger
Telegram Increasingly Abused for Selling Stolen Financial Details
The cybercriminals are actively abusing the Telegram messenger for setting up underground channels selling stolen financial details on them and also executing their other illicit activities as well. Why are Threat Actors abusing Telegram’s Instant Messaging Service? They did so due to its feature and user base, as Telegram has an active user base of […]
The post Telegram Increasingly Abused for Selling Stolen Financial Details appeared first on Cyber Security News.
https://cybersecuritynews.com/telegram-messenger-abused/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/telegram-messenger-abused/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, January 19, 2022
Hacking attack on Red Cross exposes data of 515,000 vulnerable people
This article has been indexed from HITBSecNews – Keeping Knowledge Free for Over a Decade Hacking attack on Red Cross exposes data of 515,000 vulnerable people l33tdawg Wed, 01/19/2022 – 23:29 Read the original article: Hacking attack on Red Cross…
Read more →
The post Hacking attack on Red Cross exposes data of 515,000 vulnerable people first appeared on IT Security News.
https://www.itsecuritynews.info/hacking-attack-on-red-cross-exposes-data-of-515000-vulnerable-people/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hacking-attack-on-red-cross-exposes-data-of-515000-vulnerable-people/?utm_source=dlvr.it&utm_medium=blogger
Top 6 Fraud Prevention APIs For 2022
The most effective way to reduce online fraud is to collect data on its occurrence so that the necessary measures can take place. According to a study conducted in 2020, about 4.8 million identity theft complaints were filed. Moreover, this was a 113% rise only from 2019. More data is being asked for online, and […]
The post Top 6 Fraud Prevention APIs For 2022 appeared first on Cyber Security News.
https://cybersecuritynews.com/fraud-prevention-apis/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/fraud-prevention-apis/?utm_source=dlvr.it&utm_medium=blogger
European Union Takes Down VPNLab.net That Used by Hackers for Anonymity
Federal agents took footprints of major cyber-crimes which led to VPNLab.net as the service provider with which many cyber-crimes were taking place. Investigating further, they were also responsible for setting up the communication and infrastructure for ransomware campaigns and for malware distribution. Further adding up, hundreds of businesses were found to be at the risk […]
The post European Union Takes Down VPNLab.net That Used by Hackers for Anonymity appeared first on Cyber Security News.
https://cybersecuritynews.com/european-union-takes-down-vpnlab-net-that-used-by-hackers-for-anonymity/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/european-union-takes-down-vpnlab-net-that-used-by-hackers-for-anonymity/?utm_source=dlvr.it&utm_medium=blogger
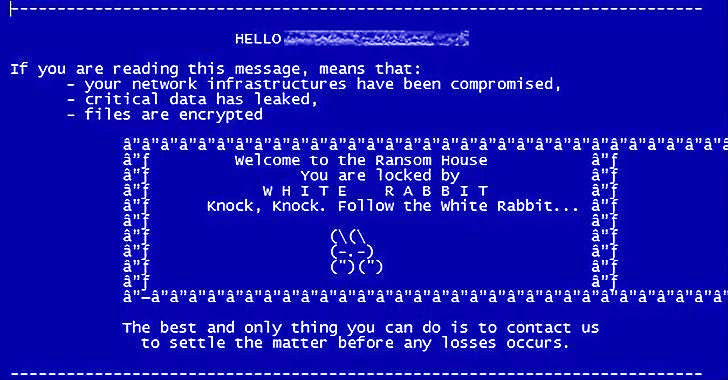
FIN8 Hackers Spotted Using New 'White Rabbit' Ransomware in Recent Attacks
The financially motivated FIN8 actor, in all likelihood, has resurfaced with a never-before-seen ransomware strain called "White Rabbit" that was recently deployed against a local bank in the U.S. in December 2021.
That's according to new findings published by Trend Micro, calling out the malware's overlaps with Egregor, which was taken down by Ukrainian law enforcement authorities in February
https://thehackernews.com/2022/01/fin8-hackers-spotted-using-new-white.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/fin8-hackers-spotted-using-new-white.html?utm_source=dlvr.it&utm_medium=blogger
DDoS IRC Bot Malware Spreading Through Korean WebHard Platforms
An IRC (Internet Relay Chat) bot strain programmed in GoLang is being used to launch distributed denial-of-service (DDoS) attacks targeting users in Korea.
"The malware is being distributed under the guise of adult games," researchers from AhnLab's Security Emergency-response Center (ASEC) said in a new report published on Wednesday. "Additionally, the DDoS malware was installed via downloader
https://thehackernews.com/2022/01/ddos-irc-bot-malware-spreading-through.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/ddos-irc-bot-malware-spreading-through.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 18, 2022
Permiso raises $10 million to scale its engineering team and expand customer footprint
This article has been indexed from Help Net Security Permiso announced a $10 million seed funding round with participation from leading institutional investors and angels. The round was led by Point72 Ventures and included Foundation Capital, Work-Bench, 11.2 Capital, Rain…
Read more →
The post Permiso raises $10 million to scale its engineering team and expand customer footprint first appeared on IT Security News.
https://www.itsecuritynews.info/permiso-raises-10-million-to-scale-its-engineering-team-and-expand-customer-footprint/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/permiso-raises-10-million-to-scale-its-engineering-team-and-expand-customer-footprint/?utm_source=dlvr.it&utm_medium=blogger
Apple Updates AirPods 3 Firmware to Version 4C170
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Apple today released a new 4C170 firmware update for the AirPods 3, an update from the prior 4C165 that was made available in December. Apple does…
Read more →
The post Apple Updates AirPods 3 Firmware to Version 4C170 first appeared on IT Security News.
https://www.itsecuritynews.info/apple-updates-airpods-3-firmware-to-version-4c170/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-updates-airpods-3-firmware-to-version-4c170/?utm_source=dlvr.it&utm_medium=blogger
UniCC – Leading Dark Web Marketplace of Stolen Credit Cards is Shutting Down
On dark web forums, UniCC, the leading dark web marketplace of stolen credit cards, has recently publicized that they are shutting down all their illegal activities, as affirmed by the blockchain forensics firm, Elliptic Enterprises. With a total of $358 million in purchases made through the marketplace since 2013 using cryptocurrencies, UniCC managed to prevail […]
The post UniCC – Leading Dark Web Marketplace of Stolen Credit Cards is Shutting Down appeared first on Cyber Security News.
https://cybersecuritynews.com/unicc/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/unicc/?utm_source=dlvr.it&utm_medium=blogger
Ukraine Government Indict Russia for The Recent Cyber Attacks
The Ukraine government has recently accused Russia of all the cyberattacks that are executed on several agencies of Ukraine. That’s why in a joint collaboration the following departments are continuing their investigation on the government websites and agencies:- The State Special Communications Service The Security Service of Ukraine The Cyber Police of Ukraine Why Russia […]
The post Ukraine Government Indict Russia for The Recent Cyber Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/ukraine-government-indict-russia-for-the-recent-cyber-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/ukraine-government-indict-russia-for-the-recent-cyber-attacks/?utm_source=dlvr.it&utm_medium=blogger
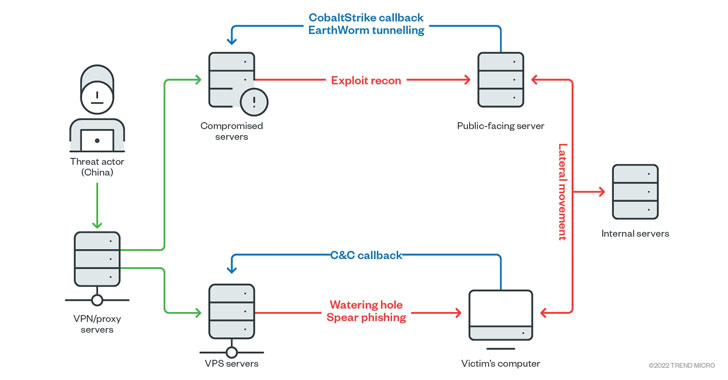
Earth Lusca Hackers Aimed at High-Value Targets in Government and Private Sectors
An elusive threat actor called Earth Lusca has been observed striking organizations across the world as part of what appears to be simultaneously an espionage campaign and an attempt to reap monetary profits.
"The list of its victims includes high-value targets such as government and educational institutions, religious movements, pro-democracy and human rights organizations in Hong Kong,
https://thehackernews.com/2022/01/earth-lusca-hackers-aimed-at-high-value.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/earth-lusca-hackers-aimed-at-high-value.html?utm_source=dlvr.it&utm_medium=blogger
Monday, January 17, 2022
Device42 aims to identify Log4j vulnerabilities
This article has been indexed from Security – VentureBeat Jen Easterly, director of the Cybersecurity and Infrastructure Security Agency (CISA), recently issued a statement to address a major security flaw in Log4j. “To be clear, this vulnerability poses a severe…
Read more →
The post Device42 aims to identify Log4j vulnerabilities first appeared on IT Security News.
https://www.itsecuritynews.info/device42-aims-to-identify-log4j-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/device42-aims-to-identify-log4j-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
Bug in WebKit’s IndexedDB implementation makes Safari 15 leak Google account info… and more
This article has been indexed from The Register – Security Glitch is spilling private data and there’s not much Apple users can do about it An improperly implemented API that stores data on browsers has caused a vulnerability in Safari…
Read more →
The post Bug in WebKit’s IndexedDB implementation makes Safari 15 leak Google account info… and more first appeared on IT Security News.
https://www.itsecuritynews.info/bug-in-webkits-indexeddb-implementation-makes-safari-15-leak-google-account-info-and-more/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/bug-in-webkits-indexeddb-implementation-makes-safari-15-leak-google-account-info-and-more/?utm_source=dlvr.it&utm_medium=blogger
Vulnerability in IDEMIA Biometric Readers Allows Hackers to Unlock Doors
This article has been indexed from SecurityWeek RSS Feed A critical vulnerability impacting multiple IDEMIA biometric identification devices can be exploited to unlock doors and turnstiles. Because of this security defect, if the TLS protocol is not activated, an attacker…
Read more →
The post Vulnerability in IDEMIA Biometric Readers Allows Hackers to Unlock Doors first appeared on IT Security News.
https://www.itsecuritynews.info/vulnerability-in-idemia-biometric-readers-allows-hackers-to-unlock-doors/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/vulnerability-in-idemia-biometric-readers-allows-hackers-to-unlock-doors/?utm_source=dlvr.it&utm_medium=blogger
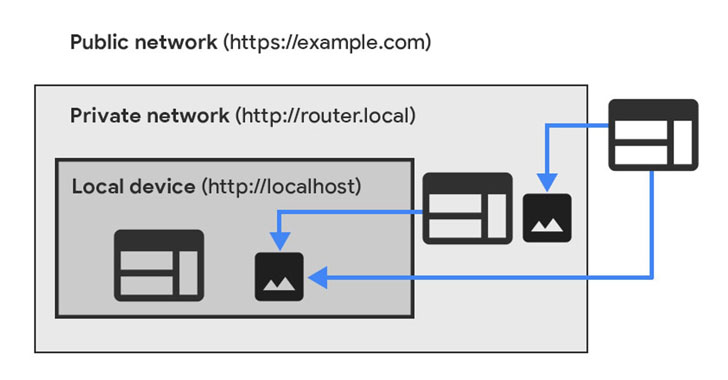
Chrome Limits Websites' Direct Access to Private Networks for Security Reasons
Google Chrome has announced plans to prohibit public websites from directly accessing endpoints located within private networks as part of an upcoming major security shakeup to prevent intrusions via the browser.
The proposed change is set to be rolled out in two phases as part of releases Chrome 98 and Chrome 101 scheduled in the coming months via a newly implemented W3C specification called
https://thehackernews.com/2022/01/chrome-limits-websites-access-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/chrome-limits-websites-access-to.html?utm_source=dlvr.it&utm_medium=blogger
Ukrainian Government Officially Accuses Russia of Recent Cyberattacks
The government of Ukraine on Sunday formally accused Russia of masterminding the attacks that targeted websites of public institutions and government agencies this past week.
"All the evidence points to the fact that Russia is behind the cyber attack," the Ministry of Digital Transformation said in a statement. "Moscow continues to wage a hybrid war and is actively building forces in the
https://thehackernews.com/2022/01/ukrainian-government-officially-accuses.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/ukrainian-government-officially-accuses.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 16, 2022
Microsoft Uncovers Destructive Malware Used in Ukraine Cyberattacks
This article has been indexed from SecurityWeek RSS Feed Newly detected WhisperGate malware being used by previously unknown threat group in cyberattacks against Ukraine read more Read the original article: Microsoft Uncovers Destructive Malware Used in Ukraine Cyberattacks
Read more →
The post Microsoft Uncovers Destructive Malware Used in Ukraine Cyberattacks first appeared on IT Security News.
https://www.itsecuritynews.info/microsoft-uncovers-destructive-malware-used-in-ukraine-cyberattacks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/microsoft-uncovers-destructive-malware-used-in-ukraine-cyberattacks/?utm_source=dlvr.it&utm_medium=blogger
Gurman: Apple Considered a Battery-Powered ‘HomePod’ Years Ago
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Earlier this month, Apple discontinued the Beats Pill+, its last battery-powered speaker. Following this news, Bloomberg‘s Mark Gurman has revealed that Apple once internally discussed and…
Read more →
The post Gurman: Apple Considered a Battery-Powered ‘HomePod’ Years Ago first appeared on IT Security News.
https://www.itsecuritynews.info/gurman-apple-considered-a-battery-powered-homepod-years-ago/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/gurman-apple-considered-a-battery-powered-homepod-years-ago/?utm_source=dlvr.it&utm_medium=blogger
Defense Contractor Hensoldt Confirms Lorenz Ransomware Attack
This article has been indexed from CySecurity News – Latest Information Security and Hacking Incidents Hensoldt, a multinational defence contractor, disclosed that Lorenz ransomware has infected part of its UK subsidiary’s systems. A spokesman for Hensholdt acknowledged the security…
Read more →
The post Defense Contractor Hensoldt Confirms Lorenz Ransomware Attack first appeared on IT Security News.
https://www.itsecuritynews.info/defense-contractor-hensoldt-confirms-lorenz-ransomware-attack/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/defense-contractor-hensoldt-confirms-lorenz-ransomware-attack/?utm_source=dlvr.it&utm_medium=blogger
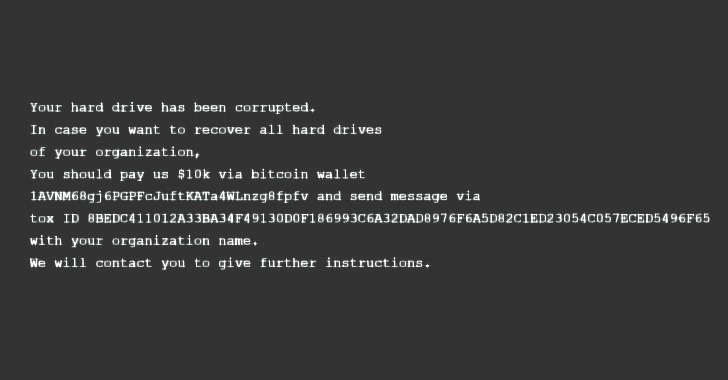
A new wave of Qlocker ransomware attacks targets QNAP NAS devices
This article has been indexed from Security Affairs QNAP NAS devices are under attack, experts warn of a new Qlocker ransomware campaign that hit devices worldwide. A new wave of Qlocker ransomware it targeting QNAP NAS devices worldwide, the new…
Read more →
The post A new wave of Qlocker ransomware attacks targets QNAP NAS devices first appeared on IT Security News.
https://www.itsecuritynews.info/a-new-wave-of-qlocker-ransomware-attacks-targets-qnap-nas-devices/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/a-new-wave-of-qlocker-ransomware-attacks-targets-qnap-nas-devices/?utm_source=dlvr.it&utm_medium=blogger
A New Destructive Malware Targeting Ukrainian Government and Business Entities
Cybersecurity teams from Microsoft on Saturday disclosed they identified evidence of a new destructive malware operation targeting government, non-profit, and information technology entities in Ukraine amid brewing geopolitical tensions between the country and Russia.
"The malware is disguised as ransomware but, if activated by the attacker, would render the infected computer system inoperable,"
https://thehackernews.com/2022/01/a-new-destructive-malware-targeting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/a-new-destructive-malware-targeting.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, January 15, 2022
Six Rumored Apple Products You’re Unlikely to See This Year
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Much has been said about what consumers could see from Apple in 2022, but the company is also working on a handful of rumored products that…
Read more →
The post Six Rumored Apple Products You’re Unlikely to See This Year first appeared on IT Security News.
https://www.itsecuritynews.info/six-rumored-apple-products-youre-unlikely-to-see-this-year/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/six-rumored-apple-products-youre-unlikely-to-see-this-year/?utm_source=dlvr.it&utm_medium=blogger
Ukraine Hacks Add to Worries of Cyber Conflict With Russia
This article has been indexed from SecurityWeek RSS Feed Hackers on Friday temporarily shut down dozens of Ukrainian government websites, causing no major damage but adding to simmering tensions while Russia amasses troops on the Ukrainian border. Separately, in a…
Read more →
The post Ukraine Hacks Add to Worries of Cyber Conflict With Russia first appeared on IT Security News.
https://www.itsecuritynews.info/ukraine-hacks-add-to-worries-of-cyber-conflict-with-russia/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ukraine-hacks-add-to-worries-of-cyber-conflict-with-russia/?utm_source=dlvr.it&utm_medium=blogger
Largest dark web market for stolen cards UniCC calls it quits
This article has been indexed from HackRead By Waqas UniCC marketplace has been active on the dark web since 2013 however its team has called its quits… This is a post from HackRead.com Read the original post: Largest dark web…
Read more →
The post Largest dark web market for stolen cards UniCC calls it quits first appeared on IT Security News.
https://www.itsecuritynews.info/largest-dark-web-market-for-stolen-cards-unicc-calls-it-quits/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/largest-dark-web-market-for-stolen-cards-unicc-calls-it-quits/?utm_source=dlvr.it&utm_medium=blogger
The GootLoader Hackers are After Law Firms and Accounting Firms
This article has been indexed from CySecurity News – Latest Information Security and Hacking Incidents GootLoader is a piece of initial access malware that allows its operators to install a variety of other malware families, including ransomware, on affected…
Read more →
The post The GootLoader Hackers are After Law Firms and Accounting Firms first appeared on IT Security News.
https://www.itsecuritynews.info/the-gootloader-hackers-are-after-law-firms-and-accounting-firms/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-gootloader-hackers-are-after-law-firms-and-accounting-firms/?utm_source=dlvr.it&utm_medium=blogger
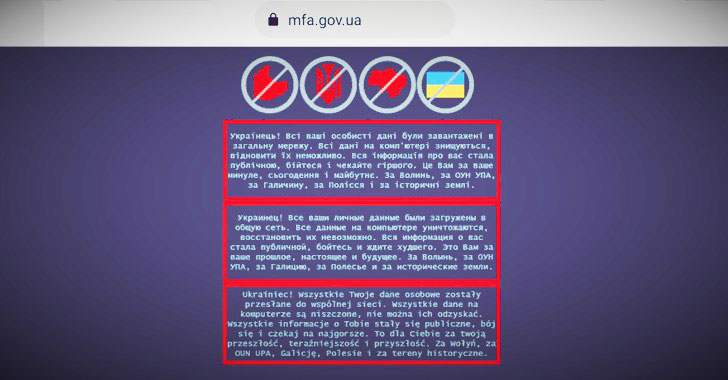
Massive Cyber Attack Knocks Down Ukrainian Government Websites
No fewer than 70 websites operated by the Ukrainian government went offline on Friday for hours in what appears to be a coordinated cyber attack amid heightened tensions with Russia.
"As a result of a massive cyber attack, the websites of the Ministry of Foreign Affairs and a number of other government agencies are temporarily down," Oleg Nikolenko, MFA spokesperson, tweeted.
The Security
https://thehackernews.com/2022/01/massive-cyber-attack-knocks-down.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/massive-cyber-attack-knocks-down.html?utm_source=dlvr.it&utm_medium=blogger
Friday, January 14, 2022
Russian government claims to have dismantled REvil ransomware gang
This article has been indexed from Security Affairs Russia’s FSB announced to have dismantled the REvil ransomware gang, the infamous group behind Kaseya and JBS USA. The Russian Federal Security Service (FSB) announced to have shut down the REvil ransomware…
Read more →
The post Russian government claims to have dismantled REvil ransomware gang first appeared on IT Security News.
https://www.itsecuritynews.info/russian-government-claims-to-have-dismantled-revil-ransomware-gang/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/russian-government-claims-to-have-dismantled-revil-ransomware-gang/?utm_source=dlvr.it&utm_medium=blogger
Today’s Trends: People Feel More Exposed to Online Threats, Want Stronger Protection
This article has been indexed from McAfee Blogs People have made it clear. They’re feeling more exposed to online threats and want stronger protection. Our 2022 Trends Study… The post Today’s Trends: People Feel More Exposed to Online Threats, Want…
Read more →
The post Today’s Trends: People Feel More Exposed to Online Threats, Want Stronger Protection first appeared on IT Security News.
https://www.itsecuritynews.info/todays-trends-people-feel-more-exposed-to-online-threats-want-stronger-protection/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/todays-trends-people-feel-more-exposed-to-online-threats-want-stronger-protection/?utm_source=dlvr.it&utm_medium=blogger
North Korean Hackers Stole Millions from Cryptocurrency Startups Worldwide
Operators associated with the Lazarus sub-group BlueNoroff have been linked to a series of cyberattacks targeting small and medium-sized companies worldwide with an aim to drain their cryptocurrency funds, in what's yet another financially motivated operation mounted by the prolific North Korean state-sponsored actor.
Russian cybersecurity company Kaspersky, which is tracking the intrusions
https://thehackernews.com/2022/01/north-korean-hackers-stole-millions.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/north-korean-hackers-stole-millions.html?utm_source=dlvr.it&utm_medium=blogger
The Great Resignation: How to Acquire and Retain Cybersecurity Talent
This article has been indexed from Security Intelligence If you’ve been following reports and whispering with industry colleagues, you know what’s going on: the cybersecurity skills gap is difficult to close, and the Great Resignation is here. The 2021 (ISC)2…
Read more →
The post The Great Resignation: How to Acquire and Retain Cybersecurity Talent first appeared on IT Security News.
https://www.itsecuritynews.info/the-great-resignation-how-to-acquire-and-retain-cybersecurity-talent/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-great-resignation-how-to-acquire-and-retain-cybersecurity-talent/?utm_source=dlvr.it&utm_medium=blogger
Cisco Releases Patch for Critical Bug Affecting Unified CCMP and Unified CCDM
Cisco Systems has rolled out security updates for a critical security vulnerability affecting Unified Contact Center Management Portal (Unified CCMP) and Unified Contact Center Domain Manager (Unified CCDM) that could be exploited by a remote attacker to take control of an affected system.
Tracked as CVE-2022-20658, the vulnerability has been rated 9.6 in severity on the CVSS scoring system, and
https://thehackernews.com/2022/01/cisco-releases-patch-for-critical-bug.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/cisco-releases-patch-for-critical-bug.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 13, 2022
How Cybercriminals Are Cashing in on the Culture of ‘Yes’
This article has been indexed from Dark Reading The reward is always front of mind, while the potential harm of giving out a phone number doesn’t immediately reveal itself. Read the original article: How Cybercriminals Are Cashing in on the…
Read more →
The post How Cybercriminals Are Cashing in on the Culture of ‘Yes’ first appeared on IT Security News.
https://www.itsecuritynews.info/how-cybercriminals-are-cashing-in-on-the-culture-of-yes/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-cybercriminals-are-cashing-in-on-the-culture-of-yes/?utm_source=dlvr.it&utm_medium=blogger
DoorLock Bug That Disables iPhones & iPads Running HomeKit on iOS 14.7
On 10th August, a new report was published in which Apple declared that they had released security updates to address a persistent denial of service (DoS) dubbed “DoorLock.” This DoorLock bug disables the iPhones and iPads running the HomeKit on iOS 14.7; that’s why it was very important to release security updates so that users […]
The post DoorLock Bug That Disables iPhones & iPads Running HomeKit on iOS 14.7 appeared first on Cyber Security News.
https://cybersecuritynews.com/doorlock-bug/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/doorlock-bug/?utm_source=dlvr.it&utm_medium=blogger
Adobe Cloud Abused to Steal Office 365, Gmail Credentials
This article has been indexed from Threatpost Threat actors are creating accounts within the Adobe Cloud suite and sending images and PDFs that appear legitimate to target Office 365 and Gmail users, researchers from Avanan discovered. Read the original article:…
Read more →
The post Adobe Cloud Abused to Steal Office 365, Gmail Credentials first appeared on IT Security News.
https://www.itsecuritynews.info/adobe-cloud-abused-to-steal-office-365-gmail-credentials/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/adobe-cloud-abused-to-steal-office-365-gmail-credentials/?utm_source=dlvr.it&utm_medium=blogger
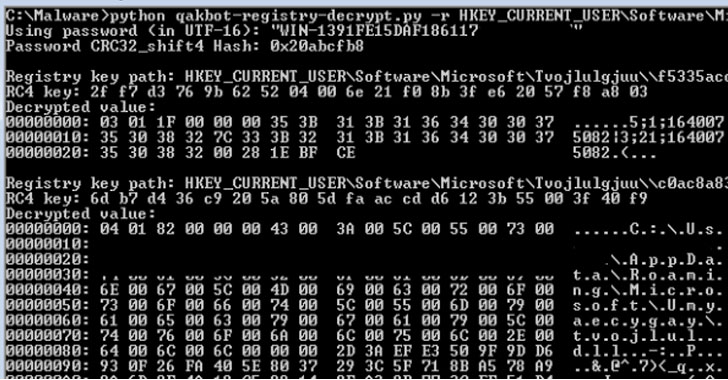
Researchers Decrypted Qakbot Banking Trojan’s Encrypted Registry Keys
Cybersecurity researchers have decoded the mechanism by which the versatile Qakbot banking trojan handles the insertion of encrypted configuration data into the Windows Registry.
Qakbot, also known as QBot, QuackBot and Pinkslipbot, has been observed in the wild since 2007. Although mainly fashioned as an information-stealing malware, Qakbot has since shifted its goals and acquired new
https://thehackernews.com/2022/01/researchers-decrypted-qakbot-banking.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/researchers-decrypted-qakbot-banking.html?utm_source=dlvr.it&utm_medium=blogger
Beware of Fake RedLine Stealer That Distributed As Fake Omicron Stats Counter
The latest version of the RedLine info-stealer is roaming in the wild, and this time it was distributed as a fake COVID-19 Omicron Stats Counter app by threat actors through emails with a malicious attachment. For a couple of hundred USD, the threat actors sold the RedLine malware on dark web markets since it is […]
The post Beware of Fake RedLine Stealer That Distributed As Fake Omicron Stats Counter appeared first on Cyber Security News.
https://cybersecuritynews.com/beware-of-fake-redline-stealer-that-distributed-as-fake-omicron-stats-counter/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/beware-of-fake-redline-stealer-that-distributed-as-fake-omicron-stats-counter/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, January 12, 2022
U.S. Cyber Command Operation Targets ‘Real-life Cyber Threats’
This article has been indexed from (ISC)² Blog A U.S. Cyber Command (USCYBERCOM) task force has conducted “its first offensive cyber effect operation against real-life cyber threats.” Details of the operation have not been published, but the military says offensive…
Read more →
The post U.S. Cyber Command Operation Targets ‘Real-life Cyber Threats’ first appeared on IT Security News.
https://www.itsecuritynews.info/u-s-cyber-command-operation-targets-real-life-cyber-threats/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/u-s-cyber-command-operation-targets-real-life-cyber-threats/?utm_source=dlvr.it&utm_medium=blogger
‘Powerdir’ New macOS Bug Let Hackers Accessed Unauthorized User Data Access
A new macOS vulnerability has been detected recently by the security team of Microsoft that is tracked as “powerdir,” and this vulnerability is identified as CVE-2021-30970. This security flaw allows any threat actors to bypass one of the crucial technologies of macOS, Transparency, Consent, and Control (TCC). Evading the Transparency, Consent, and Control (TCC) technology […]
The post ‘Powerdir’ New macOS Bug Let Hackers Accessed Unauthorized User Data Access appeared first on Cyber Security News.
https://cybersecuritynews.com/powerdir-new-macos-bug/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/powerdir-new-macos-bug/?utm_source=dlvr.it&utm_medium=blogger
Log4j: How hackers are using the flaw to deliver this new ‘modular’ backdoor
This article has been indexed from Latest topics for ZDNet in Security Some state-backed hackers go to great lengths to cover their tracks. This Iran-backed group does not, according to Check Point. Read the original article: Log4j: How hackers are…
Read more →
The post Log4j: How hackers are using the flaw to deliver this new ‘modular’ backdoor first appeared on IT Security News.
https://www.itsecuritynews.info/log4j-how-hackers-are-using-the-flaw-to-deliver-this-new-modular-backdoor/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/log4j-how-hackers-are-using-the-flaw-to-deliver-this-new-modular-backdoor/?utm_source=dlvr.it&utm_medium=blogger
Hackers Use Cloud Services to Distribute Nanocore, Netwire, and AsyncRAT Malware
Threat actors are actively incorporating public cloud services from Amazon and Microsoft into their malicious campaigns to deliver commodity remote access trojans (RATs) such as Nanocore, Netwire, and AsyncRAT to siphon sensitive information from compromised systems.
The spear-phishing attacks, which commenced in October 2021, have primarily targeted entities located in the U.S., Canada, Italy,
https://thehackernews.com/2022/01/hackers-use-cloud-services-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/hackers-use-cloud-services-to.html?utm_source=dlvr.it&utm_medium=blogger
How Can You Leave Log4J in 2021?
With the last month of 2021 dominated by the log4J vulnerabilities discovery, publication, and patches popping up in rapid succession, odds are you have patched your system against Log4J exploitation attempts. At least some systems, if not all. You might even have installed the latest patch – at the time of writing, that is 2.17.1, but, if the last rapid patching cycle persists, it might have
https://thehackernews.com/2022/01/how-can-you-leave-log4j-in-2021.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/how-can-you-leave-log4j-in-2021.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 11, 2022
Public-Key Cryptography Standards (PKCS)
This article has been indexed from SearchSecurity This post doesn’t have text content, please click on the link below to view the original article. Read the original article: Public-Key Cryptography Standards (PKCS)
Read more →
The post Public-Key Cryptography Standards (PKCS) first appeared on IT Security News.
https://www.itsecuritynews.info/public-key-cryptography-standards-pkcs/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/public-key-cryptography-standards-pkcs/?utm_source=dlvr.it&utm_medium=blogger
The Facebook Pixel Hunt aims to unravel Facebook’s tracking methods. Will you join?
This article has been indexed from Malwarebytes Labs
Read more →
The post The Facebook Pixel Hunt aims to unravel Facebook’s tracking methods. Will you join? first appeared on IT Security News.
https://www.itsecuritynews.info/the-facebook-pixel-hunt-aims-to-unravel-facebooks-tracking-methods-will-you-join/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-facebook-pixel-hunt-aims-to-unravel-facebooks-tracking-methods-will-you-join/?utm_source=dlvr.it&utm_medium=blogger
New KCodes NetUSB Bug Affect Millions of Routers from Different Vendors
Cybersecurity researchers have detailed a high severity flaw in KCodes NetUSB component that's integrated into millions of end-user router devices from Netgear, TP-Link, Tenda, EDiMAX, D-Link, and Western Digital, among others.
KCodes NetUSB is a Linux kernel module that enables devices on a local network to provide USB-based services over IP. Printers, external hard drives, and flash drives
https://thehackernews.com/2022/01/new-kcodes-netusb-bug-affect-millions.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/01/new-kcodes-netusb-bug-affect-millions.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)