Ransomware strikes businesses every 11 seconds. The ransomware attack volume is already at record levels, but we’re hearing it’s only getting worse. As some victims managed to take precautions and refused to pay the ransom, attackers began to add more…
Read more →
The post Triple Extortion Ransomware: How to Protect Your Organization? first appeared on IT Security News.
https://www.itsecuritynews.info/triple-extortion-ransomware-how-to-protect-your-organization/?utm_source=dlvr.it&utm_medium=blogger
Saturday, December 31, 2022
Weekly Update 328
Presently sponsored by: 1Password, a secure password manager, is building the passwordless experience you deserve. See how passkeys work We made it! That's 2022 done and dusted, and what a year it was, both professionally and personally. It feels great…
Read more →
The post Weekly Update 328 first appeared on IT Security News.
https://www.itsecuritynews.info/weekly-update-328/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/weekly-update-328/?utm_source=dlvr.it&utm_medium=blogger
Researcher Uncovers Potential Wiretapping Bugs in Google Home Smart Speakers
A security researcher was awarded a bug bounty of $107,500 for identifying security issues in Google Home smart speakers that could be exploited to install backdoors and turn them into wiretapping devices.
The flaws "allowed an attacker within wireless proximity to install a 'backdoor' account on the device, enabling them to send commands to it remotely over the internet, access its microphone
https://thehackernews.com/2022/12/researcher-uncovers-potential.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/researcher-uncovers-potential.html?utm_source=dlvr.it&utm_medium=blogger
Friday, December 30, 2022
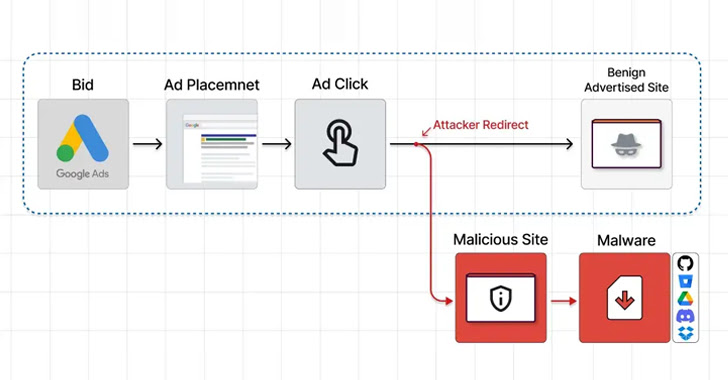
New Malvertising Campaign via Google Ads Targets Users Searching for Popular Software
Users searching for popular software are being targeted by a new malvertising campaign that abuses Google Ads to serve trojanized variants that deploy malware, such as Raccoon Stealer and Vidar.
The activity makes use of seemingly credible websites with typosquatted domain names that are surfaced on top of Google search results in the form of malicious ads by hijacking searches for specific
https://thehackernews.com/2022/12/new-malvertising-campaign-via-google.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/new-malvertising-campaign-via-google.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 29, 2022
BitKeep Confirms Cyber Attack, Loses Over $9 Million in Digital Currencies
Decentralized multi-chain crypto wallet BitKeep on Wednesday confirmed a cyberattack that allowed threat actors to distribute fraudulent versions of its Android app with the goal of stealing users' digital currencies.
"With maliciously implanted code, the altered APK led to the leak of user's private keys and enabled the hacker to move funds," BitKeep CEO Kevin Como said, describing it as a "
https://thehackernews.com/2022/12/bitkeep-confirms-cyber-attack-loses.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/bitkeep-confirms-cyber-attack-loses.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, December 28, 2022
France Fined Microsoft Over 60 Million Euros for Using Advertisement Cookies Without Consent
The French privacy regulator announced on Thursday that it had penalized Microsoft, a major US technology company, 60 million euros ($64 million) for forcing advertising cookies on customers. The National Commission for Technology and Freedoms (CNIL), which levied the biggest fine in 2022, claimed that Microsoft’s search engine Bing did not have a system in […]
The post France Fined Microsoft Over 60 Million Euros for Using Advertisement Cookies Without Consent appeared first on Cyber Security News.
https://cybersecuritynews.com/france-fined-microsoft-over-60-million-euros/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/france-fined-microsoft-over-60-million-euros/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, December 27, 2022
2022 Top Five Immediate Threats in Geopolitical Context
As we are nearing the end of 2022, looking at the most concerning threats of this turbulent year in terms of testing numbers offers a threat-based perspective on what triggers cybersecurity teams to check how vulnerable they are to specific threats. These are the threats that were most tested to validate resilience with the Cymulate security posture management platform between January 1st and
https://thehackernews.com/2022/12/2022-top-five-immediate-threats-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/2022-top-five-immediate-threats-in.html?utm_source=dlvr.it&utm_medium=blogger
PrivateLoader PPI Service Found Distributing Info-Stealing RisePro Malware
The pay-per-install (PPI) malware downloader service known as PrivateLoader is being used to distribute a previously documented information-stealing malware dubbed RisePro.
Flashpoint spotted the newly identified stealer on December 13, 2022, after it discovered "several sets of logs" exfiltrated using the malware on an illicit cybercrime marketplace called Russian Market.
A C++-based malware,
https://thehackernews.com/2022/12/privateloader-ppi-service-found.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/privateloader-ppi-service-found.html?utm_source=dlvr.it&utm_medium=blogger
Monday, December 26, 2022
Critical Linux Kernel flaw affects SMB servers with ksmbd enabled
Experts warn of a critical Linux Kernel vulnerability (CVSS score of 10) impacting SMB servers that can lead to remote code execution. A critical Linux kernel vulnerability (CVSS score of 10) exposes SMB servers with ksmbd enabled to hack. KSMBD…
Read more →
The post Critical Linux Kernel flaw affects SMB servers with ksmbd enabled first appeared on IT Security News.
https://www.itsecuritynews.info/critical-linux-kernel-flaw-affects-smb-servers-with-ksmbd-enabled/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/critical-linux-kernel-flaw-affects-smb-servers-with-ksmbd-enabled/?utm_source=dlvr.it&utm_medium=blogger
Sunday, December 25, 2022
Godfather Android Malware Stealing Login Credentials of Over 400 Bank Users
In recent years, Android users have been experiencing a rise in the incidence of the GodFather banking trojan, mainly targeting European users. This GodFather android malware was discovered in March 2022 and was described as one of the notorious trojans by Cyble Research & Intelligence Labs (CRIL) actively targeting Android bank users all over the […]
The post Godfather Android Malware Stealing Login Credentials of Over 400 Bank Users appeared first on Cyber Security News.
https://cybersecuritynews.com/godfather-android-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/godfather-android-malware/?utm_source=dlvr.it&utm_medium=blogger
Saturday, December 24, 2022
France Fines Microsoft €60 Million for Using Advertising Cookies Without User Consent
France's privacy watchdog has imposed a €60 million ($63.88 million) fine against Microsoft's Ireland subsidiary for dropping advertising cookies in users' computers without their explicit consent in violation of data protection laws in the European Union.
The Commission nationale de l'informatique et des libertés (CNIL) noted that users visiting the home page of its Bing search engine did not
https://thehackernews.com/2022/12/france-fines-microsoft-60-million-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/france-fines-microsoft-60-million-for.html?utm_source=dlvr.it&utm_medium=blogger
Friday, December 23, 2022
New Zerobot Malware Exploiting Apache Vulnerabilities to Launch DDoS Attack
As a result of the exploitation of security vulnerabilities found on unpatched Apache servers that are exposed to the Internet, the Zerobot botnet has been recently upgraded with the capability of infecting new devices. Latest version also features new DDoS capabilities as observed by the Microsoft Defender for IoT research team. Since November at least, […]
The post New Zerobot Malware Exploiting Apache Vulnerabilities to Launch DDoS Attack appeared first on Cyber Security News.
https://cybersecuritynews.com/zerobot-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/zerobot-malware/?utm_source=dlvr.it&utm_medium=blogger
Raspberry Robin Malware Attacks Against Telecom and Government Sectors
Trend Micro researchers noticed Raspberry Robin in recent attacks on telecommunications service providers and government networks. The Raspberry Robin malware is now dropping a fake payload to evade detection when it detects it’s being run within sandboxes and debugging tools. Researchers say, due to the use of.lnk files, it appears to propagate across systems in […]
The post Raspberry Robin Malware Attacks Against Telecom and Government Sectors appeared first on Cyber Security News.
https://cybersecuritynews.com/raspberry-robin-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/raspberry-robin-malware/?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 22, 2022
Ransomware Hackers Using New Way to Bypass MS Exchange ProxyNotShell Mitigations
Threat actors affiliated with a ransomware strain known as Play are leveraging a never-before-seen exploit chain that bypasses blocking rules for ProxyNotShell flaws in Microsoft Exchange Server to achieve remote code execution (RCE) through Outlook Web Access (OWA).
"The new exploit method bypasses URL rewrite mitigations for the Autodiscover endpoint," CrowdStrike researchers Brian Pitchford,
https://thehackernews.com/2022/12/ransomware-hackers-using-new-way-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/ransomware-hackers-using-new-way-to.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, December 21, 2022
KmsdBot Botnet Suspected of Being Used as DDoS-for-Hire Service
An ongoing analysis of the KmsdBot botnet has raised the possibility that it's a DDoS-for-hire service offered to other threat actors.
This is based on the different industries and geographies that were attacked, web infrastructure company Akamai said. Among the notable targets included FiveM and RedM, which are game modifications for Grand Theft Auto V and Red Dead Redemption 2, as well as
https://thehackernews.com/2022/12/kmsdbot-botnet-suspected-of-being-used.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/kmsdbot-botnet-suspected-of-being-used.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, December 20, 2022
Facebook Cracks Down on Spyware Vendors from U.S., China, Russia, Israel, and India
Meta Platforms disclosed that it took down no less than 200 covert influence operations since 2017 spanning roughly 70 countries across 42 languages.
The social media conglomerate also took steps to disable accounts and block infrastructure operated by spyware vendors, including in China, Russia, Israel, the U.S. and India, that targeted individuals in about 200 countries.
"The global
https://thehackernews.com/2022/12/facebook-cracks-down-on-spyware-vendors.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/facebook-cracks-down-on-spyware-vendors.html?utm_source=dlvr.it&utm_medium=blogger
New DDoS Botnet Malware Infecting Windows, Linux, and IoT Devices
A cross-platform botnet, ‘MCCrash’ that starts out from malicious software downloads on Windows devices and spreads to a range of Linux-based devices was recently examined by the Microsoft Defender for IoT research team. The botnet spreads by obtaining the default credentials on Secure Shell (SSH)-capable devices that are open to the internet. Particularly, IoT devices […]
The post New DDoS Botnet Malware Infecting Windows, Linux, and IoT Devices appeared first on Cyber Security News.
https://cybersecuritynews.com/ddos-botnet-malware-infecting-windows/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/ddos-botnet-malware-infecting-windows/?utm_source=dlvr.it&utm_medium=blogger
Monday, December 19, 2022
T Mobile Retailer hacks into Company Servers
Argishti Khudaverdyan, a former retailer of T-Mobile company, received a 10-year jail imprisonment sentence at the end of last as he was found guilty of hacking into the servers of the telecom provider and gaining access to phone unlocking and…
Read more →
The post T Mobile Retailer hacks into Company Servers first appeared on IT Security News.
https://www.itsecuritynews.info/t-mobile-retailer-hacks-into-company-servers/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/t-mobile-retailer-hacks-into-company-servers/?utm_source=dlvr.it&utm_medium=blogger
Top 12 Best Open Source Intelligence Tools (OSINT Tools) for Penetration Testing 2023
We all know very well that getting or gathering any information by using various tools becomes really easy. In this article, we have discussed various OSINT tools, as if we search over the internet, then there will be many different pages to pop out. But the most problematic thing is to gather different information from […]
The post Top 12 Best Open Source Intelligence Tools (OSINT Tools) for Penetration Testing 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/osint-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/osint-tools/?utm_source=dlvr.it&utm_medium=blogger
Sunday, December 18, 2022
Hacker Halts Sale of FBI’s High-Profile InfraGard Database
By Habiba Rashid Apparently, there has been a change of heart by the hacker. This is a post from HackRead.com Read the original post: Hacker Halts Sale of FBI’s High-Profile InfraGard Database This article has been indexed from HackRead |…
Read more →
The post Hacker Halts Sale of FBI’s High-Profile InfraGard Database first appeared on IT Security News.
https://www.itsecuritynews.info/hacker-halts-sale-of-fbis-high-profile-infragard-database/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hacker-halts-sale-of-fbis-high-profile-infragard-database/?utm_source=dlvr.it&utm_medium=blogger
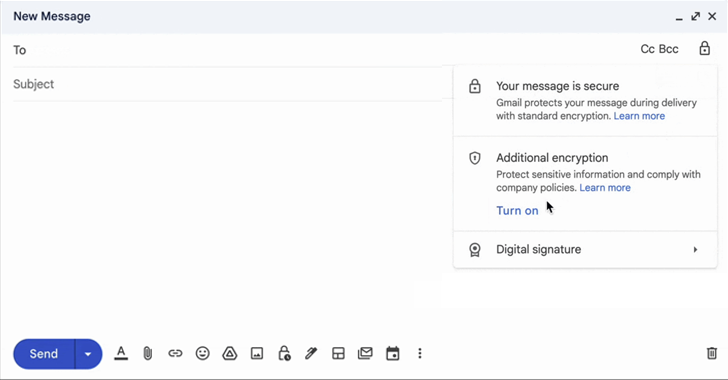
Google Takes Gmail Security to the Next Level with Client-Side Encryption
Google on Friday announced that its client-side encryption for Gmail is in beta to its Workspace and education customers to secure emails sent using the web version of the platform.
This development comes at a time when concerns about online privacy and data security are at an all-time high, and it is certainly welcomed by users who value the protection of their personal data.
To that end,
https://thehackernews.com/2022/12/gmail-encryption.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/gmail-encryption.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, December 17, 2022
Goodbye SHA-1: NIST Retires 27-Year-Old Widely Used Cryptographic Algorithm
The U.S. National Institute of Standards and Technology (NIST), an agency within the Department of Commerce, announced Thursday that it's formally retiring the SHA-1 cryptographic algorithm.
SHA-1, short for Secure Hash Algorithm 1, is a 27-year-old hash function used in cryptography and has since been deemed broken owing to the risk of collision attacks.
While hashes are designed to be
https://thehackernews.com/2022/12/goodbye-sha-1-nist-retires-27-year-old.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/goodbye-sha-1-nist-retires-27-year-old.html?utm_source=dlvr.it&utm_medium=blogger
Friday, December 16, 2022
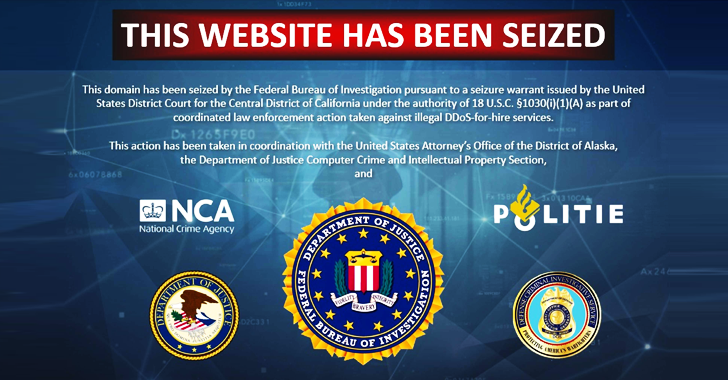
FBI Charges 6, Seizes 48 Domains Linked to DDoS-for-Hire Service Platforms
The U.S. Department of Justice (DoJ) on Wednesday announced the seizure of 48 domains that offered services to conduct distributed denial-of-service (DDoS) attacks on behalf of other threat actors, effectively lowering the barrier to entry for malicious activity.
It also charged six suspects – Jeremiah Sam Evans Miller (23), Angel Manuel Colon Jr. (37), Shamar Shattock (19), Cory Anthony Palmer
https://thehackernews.com/2022/12/fbi-charges-6-seizes-48-domains-linked.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/fbi-charges-6-seizes-48-domains-linked.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 15, 2022
Cybersecurity Experts Uncover Inner Workings of Destructive Azov Ransomware
Cybersecurity researchers have published the inner workings of a new wiper called Azov Ransomware that's deliberately designed to corrupt data and "inflict impeccable damage" to compromised systems.
Distributed through another malware loader known as SmokeLoader, the malware has been described as an "effective, fast, and unfortunately unrecoverable data wiper," by Israeli cybersecurity company
https://thehackernews.com/2022/12/cybersecurity-experts-uncover-inner.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/cybersecurity-experts-uncover-inner.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, December 14, 2022
Key Cybersecurity Takeaways from 2022
2022 was a noteworthy year in cybersecurity. We saw a steady rise in cybercrime, continuing the trend from previous years. But we also saw a greater variety of anti-cybercrime measures, including significant cybersecurity budget increases in governments and organizations worldwide. Here are some notable events and trends from the cybersecurity world in 2022 and what […]
The post Key Cybersecurity Takeaways from 2022 appeared first on Cyber Security News.
https://cybersecuritynews.com/cybersecurity-takeaways/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cybersecurity-takeaways/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, December 13, 2022
Uber Hacked Again? – Data from Uber and Uber Eats Published on Hacking Forums
Uber has been the subject of a new cyberattack. Early on Saturday morning, a threat actor going by the name of “UberLeaks” began publishing information on a hacking forum known for revealing data breaches. Employee email addresses, company reports, and data on IT assets that were stolen from a third-party vendor are all included in […]
The post Uber Hacked Again? – Data from Uber and Uber Eats Published on Hacking Forums appeared first on Cyber Security News.
https://cybersecuritynews.com/uber-hacked-again/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/uber-hacked-again/?utm_source=dlvr.it&utm_medium=blogger
Monday, December 12, 2022
Are Deepfakes Really a Security Threat? – Member Recap from (ISC)² Security Congress 2022
A member recap of Dr. Thomas Scanlon’s session at (ISC)² Security Congress 2022 by Angus Chen, CISSP, CCSP, MBA, PMP. Dr. Scanlon started his talk by showing images of women and posing a question to the audience: Can you spot…
Read more →
The post Are Deepfakes Really a Security Threat? – Member Recap from (ISC)² Security Congress 2022 first appeared on IT Security News.
https://www.itsecuritynews.info/are-deepfakes-really-a-security-threat-member-recap-from-isc%c2%b2-security-congress-2022-5/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/are-deepfakes-really-a-security-threat-member-recap-from-isc%c2%b2-security-congress-2022-5/?utm_source=dlvr.it&utm_medium=blogger
UK arrests five for selling ‘dodgy’ point of sale software
Turns a $100 bottle of wine into a $4 soft drink to avoid tax, earns ire of international tax group Tax authorities from Australia, Canada, France, the UK and the USA have conducted a joint probe into “electronic sales suppression…
Read more →
The post UK arrests five for selling ‘dodgy’ point of sale software first appeared on IT Security News.
https://www.itsecuritynews.info/uk-arrests-five-for-selling-dodgy-point-of-sale-software/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/uk-arrests-five-for-selling-dodgy-point-of-sale-software/?utm_source=dlvr.it&utm_medium=blogger
Red Team and Blue Team Operations : How Does it Works?
Security is a multifaceted field with multiple roles for carrying out diverse operations. In this article, we demystify the concept of the red team and the blue team in security. First things first: why do we need to bifurcate security roles for two teams? Simply put, security responsibilities in a company are so wide it’s […]
The post Red Team and Blue Team Operations : How Does it Works? appeared first on Cyber Security News.
https://cybersecuritynews.com/red-team-and-blue-team/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/red-team-and-blue-team/?utm_source=dlvr.it&utm_medium=blogger
Sunday, December 11, 2022
Hack-for-Hire Group Targets Travel and Financial Entities with New Janicab Malware Variant
Travel agencies have emerged as the target of a hack-for-hire group dubbed Evilnum as part of a broader campaign aimed at legal and financial investment institutions in the Middle East and Europe.
The attacks targeting law firms throughout 2020 and 2021 involved a revamped variant of a malware called Janicab that leverages a number of public services like YouTube as dead drop resolvers,
https://thehackernews.com/2022/12/hack-for-hire-group-targets-travel-and.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/hack-for-hire-group-targets-travel-and.html?utm_source=dlvr.it&utm_medium=blogger
New MuddyWater Campaign Uses Legitimate Remote Administration Tools to Deploy Malware
Deep Instinct identified a new MuddyWater threat campaign active since at least 2017, and frequently conducts campaigns against high-value targets in American, European, and Asian countries. MuddyWater, also known as MERCURY or Static Kitten, is an APT group recently attributed to Iran’s Ministry of Intelligence and Security (MOIS) by U.S. Cyber Command. New Campaign of […]
The post New MuddyWater Campaign Uses Legitimate Remote Administration Tools to Deploy Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/muddywater-campaign-legit-remote-admin/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/muddywater-campaign-legit-remote-admin/?utm_source=dlvr.it&utm_medium=blogger
Saturday, December 10, 2022
New Dark Web Website Allows Hackers to Embed Malware to Legitimate Android Apps
ThreatFabric’s researchers found ‘Zombinder’, a third-party darknet service that was used to bind malware payloads to legitimate Android applications. In order to deceive users into installing a malicious payload, it is used to bind a malicious payload to a legitimate application. “While analyzing the activity of the Android banking Trojan Ermac, ThreatFabric’s analysts discovered a campaign […]
The post New Dark Web Website Allows Hackers to Embed Malware to Legitimate Android Apps appeared first on Cyber Security News.
https://cybersecuritynews.com/legitimate-android-apps/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/legitimate-android-apps/?utm_source=dlvr.it&utm_medium=blogger
Friday, December 9, 2022
Kali Linux 2022.4 Released With New Hacking Tools & Azure Images
The most recent Kali Linux release for 2022, Kali Linux 2022.4, from Offensive Security includes updated desktop experiences, new Azure and QEMU images, and six new tools. With the addition of 6 new tools, Kali Linux is once again available through the Microsoft Azure store. The tools include Windows NTLM relay tools, a Windows privilege […]
The post Kali Linux 2022.4 Released With New Hacking Tools & Azure Images appeared first on Cyber Security News.
https://cybersecuritynews.com/kali-linux-2022-4/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/kali-linux-2022-4/?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 8, 2022
Microsoft Alerts Cryptocurrency Industry of Targeted Cyberattacks
Cryptocurrency investment companies are the target of a developing threat cluster that uses Telegram groups to seek out potential victims.
Microsoft's Security Threat Intelligence Center (MSTIC) is tracking the activity under the name DEV-0139, and builds upon a recent report from Volexity that attributed the same set of attacks to North Korea's Lazarus Group.
"DEV-0139 joined Telegram groups
https://thehackernews.com/2022/12/microsoft-alerts-cryptocurrency.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/microsoft-alerts-cryptocurrency.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, December 7, 2022
Telcom and BPO Companies Under Attack by SIM Swapping Hackers
A persistent intrusion campaign has set its eyes on telecommunications and business process outsourcing (BPO) companies at lease since June 2022.
"The end objective of this campaign appears to be to gain access to mobile carrier networks and, as evidenced in two investigations, perform SIM swapping activity," CrowdStrike researcher Tim Parisi said in an analysis published last week.
The
https://thehackernews.com/2022/12/telcom-and-bpo-companies-under-attack.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/12/telcom-and-bpo-companies-under-attack.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, December 6, 2022
Hackers Actively Attack RDP Servers To Deploy Ransomware
Multiple ransomware groups that target open Remote Desktop Protocol (RDP) ports have been reported by Cyble Research and Intelligence Labs (CRIL). RDP enables users to connect to and manage remote computers across a network. Businesses frequently utilize it to allow remote access to corporate networks. Thus, a critical security issue might occur if an RDP […]
The post Hackers Actively Attack RDP Servers To Deploy Ransomware appeared first on Cyber Security News.
https://cybersecuritynews.com/rdp-servers-actively-targeted-by-hackers/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/rdp-servers-actively-targeted-by-hackers/?utm_source=dlvr.it&utm_medium=blogger
Monday, December 5, 2022
BlackProxies – A Criminal Proxy Services Selling a Million Access to Hackers
DomainTools analysts have recently spotted a new residential proxy market which is dubbed “BlackProxies” that is aggressively gaining huge popularity among the following entities:- During the investigation of the market in question, it was discovered that the market is providing and selling access to more than one million purported proxy IP addresses across the world. […]
The post BlackProxies – A Criminal Proxy Services Selling a Million Access to Hackers appeared first on Cyber Security News.
https://cybersecuritynews.com/blackproxies/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/blackproxies/?utm_source=dlvr.it&utm_medium=blogger
Sunday, December 4, 2022
Winter 2022 Supplement for ‘Bradley, Deeks, & Goldsmith, Foreign Relations Law: Cases and Materials’ (7th ed. 2020)
Here is the Winter 2022 Supplement for Bradley, Deeks, & Goldsmith, Foreign Relations Law: Cases and Materials (7th ed. 2020). These materials cover, among other things, foreign relations law issues implicated by the U.S. actions taken in response to Russia’s invasion of Ukraine;…
Read more →
The post Winter 2022 Supplement for ‘Bradley, Deeks, & Goldsmith, Foreign Relations Law: Cases and Materials’ (7th ed. 2020) first appeared on IT Security News.
https://www.itsecuritynews.info/winter-2022-supplement-for-bradley-deeks-goldsmith-foreign-relations-law-cases-and-materials-7th-ed-2020/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/winter-2022-supplement-for-bradley-deeks-goldsmith-foreign-relations-law-cases-and-materials-7th-ed-2020/?utm_source=dlvr.it&utm_medium=blogger
Saturday, December 3, 2022
10 Best Bot Protection Software – 2023
Bot protection software or bot mitigation software plays a vital role in protecting websites and web apps from malicious traffic. A ‘bot’ (short for robot), is a software program that performs automated, repetitious, pre-defined tasks. Bots typically imitate or replace human behavior. Because they’re automated, operate important faster than human users. The Bot Detection software […]
The post 10 Best Bot Protection Software – 2023 appeared first on Cyber Security News.
https://cybersecuritynews.com/bot-protection-software/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/bot-protection-software/?utm_source=dlvr.it&utm_medium=blogger
Friday, December 2, 2022
Critical RCE Flaw With 2M Downloaded Android Remote Keyboard Apps Let Attackers Access keystrokes
Multiple critical vulnerabilities were found by the security researchers at Synopsys in three Android apps that enable users to control computer systems with Android devices. Furthermore, these critical vulnerabilities could be exploited by threat actors to expose key presses and to perform RCE (Remote Code Execution). The three apps are quite popular and have more […]
The post Critical RCE Flaw With 2M Downloaded Android Remote Keyboard Apps Let Attackers Access keystrokes appeared first on Cyber Security News.
https://cybersecuritynews.com/rce-flaw-with-2m-downloaded-app/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/rce-flaw-with-2m-downloaded-app/?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 1, 2022
New Flaw in Acer Laptops Let Attackers Disable Boot Protection
Experts from Acer observed multiple Acer laptop models have vulnerabilities that might let hackers disable the ‘Secure Boot’ function and security checks to install malware. The vulnerability, tracked as CVE-2022-4020 (CVSS score of 8.1), was found in the HQSwSmiDxe DXE driver, which examines to see if the NVRAM variable “BootOrderSecureBootDisable” is present to disable Secure Boot. […]
The post New Flaw in Acer Laptops Let Attackers Disable Boot Protection appeared first on Cyber Security News.
https://cybersecuritynews.com/flaw-in-acer-laptops/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/flaw-in-acer-laptops/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, November 30, 2022
Over a Dozen New BMC Firmware Flaws Expose OT and IoT Devices to Remote Attacks
Over a dozen security flaws have been discovered in baseboard management controller (BMC) firmware from Lanner that could expose operational technology (OT) and internet of things (IoT) networks to remote attacks.
BMC refers to a specialized service processor, a system-on-chip (SoC), that's found in server motherboards and is used for remote monitoring and management of a host system, including
https://thehackernews.com/2022/11/over-dozen-new-bmc-firmware-flaws.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/over-dozen-new-bmc-firmware-flaws.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, November 29, 2022
Massive Twitter Breach – Over 5.4 Million users’ Data Leaked Online
It has been discovered recently that over 5.4 million personal records of Twitter users have been stolen by threat actors and publicly exposed on a hacker forum for free. While to accomplish this illicit activity threat actors exploited an API vulnerability that was fixed in January. On the popular hacking forum, Breached Forums, the threat […]
The post Massive Twitter Breach – Over 5.4 Million users’ Data Leaked Online appeared first on Cyber Security News.
https://cybersecuritynews.com/massive-twitter-breach/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/massive-twitter-breach/?utm_source=dlvr.it&utm_medium=blogger
Monday, November 28, 2022
Compromised Data of Over 9 Million Health Insurance Users Is Being Exposed On the Dark Web
After hitting Australian telecommunications company Optus, in which the information of over 9 million users has been exposed, cybercriminals have victimized another company — Medibank, one of the largest Australian insurance companies. Following the data breach on Medibank, threat actors have released the personal health information of millions of users they obtained in the attack. […]
The post Compromised Data of Over 9 Million Health Insurance Users Is Being Exposed On the Dark Web appeared first on Cyber Security News.
https://cybersecuritynews.com/health-insurance-users-is-being-exposed-on-the-dark-web/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/health-insurance-users-is-being-exposed-on-the-dark-web/?utm_source=dlvr.it&utm_medium=blogger
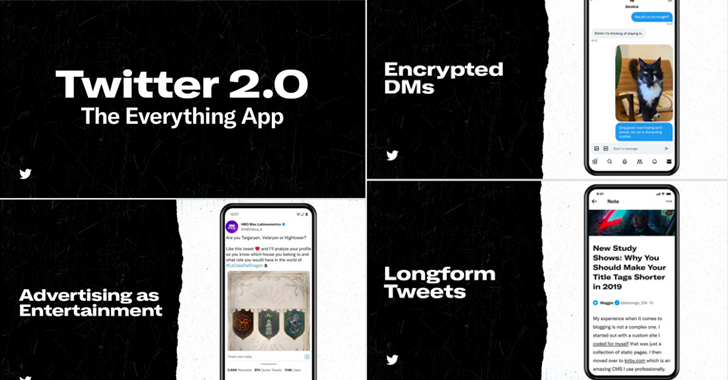
Elon Musk Confirms Twitter 2.0 will Bring End-to-End Encryption to Direct Messages
Twitter chief executive Elon Musk confirmed plans for end-to-end encryption (E2EE) for direct messages on the platform.
The feature is part of Musk's vision for Twitter 2.0, which is expected to be what's called an "everything app." Other functionalities include longform tweets and payments, according to a slide deck shared by Musk over the weekend.
The company's plans for
https://thehackernews.com/2022/11/elon-musk-confirms-twitter-20-will.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/elon-musk-confirms-twitter-20-will.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, November 27, 2022
Reasons for Being Updated ISO 27001 Crucial For Business Security
The supplier of the UK’s National Health Service, Advanced, faced a cyberattack on 4 august 2022 in the morning. It worked as a vicious example for an alerting situation: “how much a well-regulated set of rules and controls are…
Read more →
The post Reasons for Being Updated ISO 27001 Crucial For Business Security first appeared on IT Security News.
https://www.itsecuritynews.info/reasons-for-being-updated-iso-27001-crucial-for-business-security/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/reasons-for-being-updated-iso-27001-crucial-for-business-security/?utm_source=dlvr.it&utm_medium=blogger
All You Need to Know About Emotet in 2022
For 6 months, the infamous Emotet botnet has shown almost no activity, and now it's distributing malicious spam. Let's dive into details and discuss all you need to know about the notorious malware to combat it.
Why is everyone scared of Emotet?
Emotet is by far one of the most dangerous trojans ever created. The malware became a very destructive program as it grew in scale and sophistication.
https://thehackernews.com/2022/11/all-you-need-to-know-about-emotet-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/all-you-need-to-know-about-emotet-in.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, November 26, 2022
Dell, HP, and Lenovo Devices Found Using Outdated OpenSSL Versions
An analysis of firmware images across devices from Dell, HP, and Lenovo has revealed the presence of outdated versions of the OpenSSL cryptographic library, underscoring a supply chain risk.
EFI Development Kit, aka EDK, is an open source implementation of the Unified Extensible Firmware Interface (UEFI), which functions as an interface between the operating system and the firmware embedded in
https://thehackernews.com/2022/11/dell-hp-and-lenovo-devices-found-using.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/dell-hp-and-lenovo-devices-found-using.html?utm_source=dlvr.it&utm_medium=blogger
Friday, November 25, 2022
Ducktail Malware Operation Evolves with New Malicious Capabilities
The operators of the Ducktail information stealer have demonstrated a "relentless willingness to persist" and continued to update their malware as part of an ongoing financially driven campaign.
"The malware is designed to steal browser cookies and take advantage of authenticated Facebook sessions to steal information from the victim's Facebook account," WithSecure researcher Mohammad Kazem
https://thehackernews.com/2022/11/ducktail-malware-operation-evolves-with.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2022/11/ducktail-malware-operation-evolves-with.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, November 24, 2022
King Of Malware “Emotet” Launching Aggressive Attack Via XLS Doc & New Payloads
Emotet, An infamous banking trojan-based malware family with a sophisticated attack background, returns with a new attack strain via XLS documents using targeted phishing emails and delivers the new IcedID and Bumblebee payloads. Emotet built its infrastructure over the year and started its aggressive attack in later 2021, also becoming highly active in a short […]
The post King Of Malware “Emotet” Launching Aggressive Attack Via XLS Doc & New Payloads appeared first on Cyber Security News.
https://cybersecuritynews.com/king-of-malware-emotet/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/king-of-malware-emotet/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)













.webp)