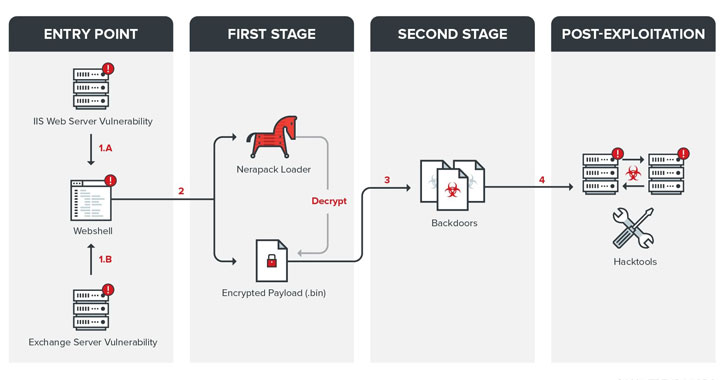
Transportation industry and government agencies related to the sector are the victims of an ongoing campaign since July 2020 by a sophisticated and well-equipped cyberespionage group in what appears to be yet another uptick in malicious activities that are "just the tip of the iceberg."
"The group tried to access some internal documents (such as flight schedules and documents for financial plans
https://thehackernews.com/2021/12/tropic-trooper-cyber-espionage-hackers.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, December 21, 2021
Meta Sues Hackers Behind Facebook, WhatsApp and Instagram Phishing Attacks
Facebook's parent company Meta Platforms on Monday said it has filed a federal lawsuit in the U.S. state of California against bad actors who operated more than 39,000 phishing websites that impersonated its digital properties to mislead unsuspecting users into divulging their login credentials.
The social engineering scheme involved the creation of rogue webpages that masqueraded as the login
https://thehackernews.com/2021/12/meta-sues-hackers-behind-facebook.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/meta-sues-hackers-behind-facebook.html?utm_source=dlvr.it&utm_medium=blogger
Monday, December 20, 2021
UK government introduces law to toughen up security of internet-connected devices
This article has been indexed from HITBSecNews – Keeping Knowledge Free for Over a Decade UK government introduces law to toughen up security of internet-connected devices l33tdawg Mon, 12/20/2021 – 23:03 Read the original article: UK government introduces law to…
Read more →
The post UK government introduces law to toughen up security of internet-connected devices first appeared on IT Security News.
https://www.itsecuritynews.info/uk-government-introduces-law-to-toughen-up-security-of-internet-connected-devices/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/uk-government-introduces-law-to-toughen-up-security-of-internet-connected-devices/?utm_source=dlvr.it&utm_medium=blogger
$30 million stolen from Grim Finance, audit firm blames new hire for vulnerability
This article has been indexed from Latest topics for ZDNet in Security Four months ago, Solidity Finance’s CTO was on vacation when a new analyst missed a crucial vulnerability during an audit of Grim Finance. Read the original article: $30…
Read more →
The post $30 million stolen from Grim Finance, audit firm blames new hire for vulnerability first appeared on IT Security News.
https://www.itsecuritynews.info/30-million-stolen-from-grim-finance-audit-firm-blames-new-hire-for-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/30-million-stolen-from-grim-finance-audit-firm-blames-new-hire-for-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
HomePod Mini Helps Apple Nearly Double Its Market Share of Smart Speakers and Screens
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Amazon continues to lead the market for smart speakers and smart screens with devices like the Echo Dot and Echo Show, but Apple has nearly doubled…
Read more →
The post HomePod Mini Helps Apple Nearly Double Its Market Share of Smart Speakers and Screens first appeared on IT Security News.
https://www.itsecuritynews.info/homepod-mini-helps-apple-nearly-double-its-market-share-of-smart-speakers-and-screens/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/homepod-mini-helps-apple-nearly-double-its-market-share-of-smart-speakers-and-screens/?utm_source=dlvr.it&utm_medium=blogger
Over 500,000+ Users Affected With Joker Malware Detected on Google Play
The security analysts at Pradeo security firm have recently detected that more than 500.000+ users were affected by the Joker malware that was detected on the Google Play store. This time Joker malware targeted the users through a messaging application, Color Message. It’s a message personalizing app that claims to improve default text messages by […]
The post Over 500,000+ Users Affected With Joker Malware Detected on Google Play appeared first on Cyber Security News.
https://cybersecuritynews.com/joker-malware-detected-on-google-play/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/joker-malware-detected-on-google-play/?utm_source=dlvr.it&utm_medium=blogger
Over 500,000 Android Users Downloaded a New Joker Malware App from Play Store
A malicious Android app with more than 500,000 downloads from the Google Play app store has been found hosting malware that stealthily exfiltrates users' contact lists to an attacker-controlled server and signs up users to unwanted paid premium subscriptions without their knowledge.
The latest Joker malware was found in a messaging-focused app named Color Message ("com.guo.smscolor.amessage"),
https://thehackernews.com/2021/12/over-500000-android-users-downloaded.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/over-500000-android-users-downloaded.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, December 19, 2021
IT Security News Daily Summary 2021-12-19
Grim Finance hacked – $30 million worth of tokens stolen Ransomware Persists Even as High-Profile Attacks Have Slowed Clop ransomware gang is leaking confidential data from the UK police Overcoming 5 Challenges to Shifting AppSec Left CVE-2021-44228: Log4j2 Exploitability and…
Read more →
The post IT Security News Daily Summary 2021-12-19 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-12-19/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-12-19/?utm_source=dlvr.it&utm_medium=blogger
Clop ransomware gang is leaking confidential data from the UK police
This article has been indexed from Security Affairs Clop ransomware gang stolen confidential data from the UK police and leaked it in the dark web because the victim refused to pay the ransom Clop ransomware operators have stolen confidential information…
Read more →
The post Clop ransomware gang is leaking confidential data from the UK police first appeared on IT Security News.
https://www.itsecuritynews.info/clop-ransomware-gang-is-leaking-confidential-data-from-the-uk-police/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/clop-ransomware-gang-is-leaking-confidential-data-from-the-uk-police/?utm_source=dlvr.it&utm_medium=blogger
Security Affairs newsletter Round 345
This article has been indexed from Security Affairs A new round of the weekly Security Affairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive…
Read more →
The post Security Affairs newsletter Round 345 first appeared on IT Security News.
https://www.itsecuritynews.info/security-affairs-newsletter-round-345/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/security-affairs-newsletter-round-345/?utm_source=dlvr.it&utm_medium=blogger
Facebook Crowned ‘Worst Company of 2021’ By New Survey
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Facebook, otherwise known as Meta, has been crowned the worst company of the year, following a turbulent 12 months of controversies, public backlash, and an eventual…
Read more →
The post Facebook Crowned ‘Worst Company of 2021’ By New Survey first appeared on IT Security News.
https://www.itsecuritynews.info/facebook-crowned-worst-company-of-2021-by-new-survey/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/facebook-crowned-worst-company-of-2021-by-new-survey/?utm_source=dlvr.it&utm_medium=blogger
Apptio collaborates with Microsoft to deliver insights and business management applications for IT
This article has been indexed from Help Net Security Apptio announced a collaboration with Microsoft to deploy Apptio’s financial decisioning platform on the Microsoft Cloud to help enterprises migrate and optimize workloads. “Cloud adoption, and the wide variety of services…
Read more →
The post Apptio collaborates with Microsoft to deliver insights and business management applications for IT first appeared on IT Security News.
https://www.itsecuritynews.info/apptio-collaborates-with-microsoft-to-deliver-insights-and-business-management-applications-for-it/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apptio-collaborates-with-microsoft-to-deliver-insights-and-business-management-applications-for-it/?utm_source=dlvr.it&utm_medium=blogger
Saturday, December 18, 2021
It’s About Time: The Unappreciated Fundamental Metric for Security
This article has been indexed from Cyber Defense Magazine By Winn Schwartau During the Cold War, the US defended us poor, soon-to-be-nuked citizenry, with time. If the […] The post It’s About Time: The Unappreciated Fundamental Metric for Security appeared…
Read more →
The post It’s About Time: The Unappreciated Fundamental Metric for Security first appeared on IT Security News.
https://www.itsecuritynews.info/its-about-time-the-unappreciated-fundamental-metric-for-security/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/its-about-time-the-unappreciated-fundamental-metric-for-security/?utm_source=dlvr.it&utm_medium=blogger
Visualize Attack Paths in Production Environments With ThreatMapper
This article has been indexed from DZone Security Zone The huge advances in ‘Shift Left’ processes makes it possible to deliver code to production that is secure and largely free from vulnerable dependencies. Among other things, these processes typically involve…
Read more →
The post Visualize Attack Paths in Production Environments With ThreatMapper first appeared on IT Security News.
https://www.itsecuritynews.info/visualize-attack-paths-in-production-environments-with-threatmapper/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/visualize-attack-paths-in-production-environments-with-threatmapper/?utm_source=dlvr.it&utm_medium=blogger
Hardening Your Kubernetes Cluster: Guidelines (Part 2)
This article has been indexed from DZone Security Zone The NSA and CISA recently released a guide on Kubernetes hardening. Now that we explored the Threat Model and had a refresher on K8s components (see the first part), let’s dive…
Read more →
The post Hardening Your Kubernetes Cluster: Guidelines (Part 2) first appeared on IT Security News.
https://www.itsecuritynews.info/hardening-your-kubernetes-cluster-guidelines-part-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hardening-your-kubernetes-cluster-guidelines-part-2/?utm_source=dlvr.it&utm_medium=blogger
New Local Attack Vector Expands the Attack Surface of Log4j Vulnerability
Cybersecurity researchers have discovered an entirely new attack vector that enables adversaries to exploit the Log4Shell vulnerability on servers locally by using a JavaScript WebSocket connection.
"This newly-discovered attack vector means that anyone with a vulnerable Log4j version on their machine or local private network can browse a website and potentially trigger the vulnerability,"
https://thehackernews.com/2021/12/new-local-attack-vector-expands-attack.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/new-local-attack-vector-expands-attack.html?utm_source=dlvr.it&utm_medium=blogger
Apache Issues 3rd Patch to Fix New High-Severity Log4j Vulnerability
The issues with Log4j continued to stack up as the Apache Software Foundation (ASF) on Friday rolled out yet another patch — version 2.17.0 — for the widely used logging library that could be exploited by malicious actors to stage a denial-of-service (DoS) attack.
Tracked as CVE-2021-45105 (CVSS score: 7.5), the new vulnerability affects all versions of the tool from 2.0-beta9 to 2.16.0, which
https://thehackernews.com/2021/12/apache-issues-3rd-patch-to-fix-new-high.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/apache-issues-3rd-patch-to-fix-new-high.html?utm_source=dlvr.it&utm_medium=blogger
Friday, December 17, 2021
Spider-Man: No Way Home exploited to push phishing and malware scams
This article has been indexed from HackRead By Deeba Ahmed Scammers are exploiting the release of Spider-Man: No Way Home to steal credit card and banking data along with harvesting login credentials of unsuspected users. This is a post from…
Read more →
The post Spider-Man: No Way Home exploited to push phishing and malware scams first appeared on IT Security News.
https://www.itsecuritynews.info/spider-man-no-way-home-exploited-to-push-phishing-and-malware-scams/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/spider-man-no-way-home-exploited-to-push-phishing-and-malware-scams/?utm_source=dlvr.it&utm_medium=blogger
Facebook Blocked 7 Surveillance-for-hire Industries that Collect Details & Compromise User Devices
Hundreds of Facebook and Instagram accounts were recently disabled by Facebook, which is owned by Meta incorporation, in an attempt to block 7 surveillance-for-hire industries that collect details and compromise user devices. In this event, more than 50 thousand people were affected in over 100 countries by the operations of these 7 surveillance-for-hire companies. And […]
The post Facebook Blocked 7 Surveillance-for-hire Industries that Collect Details & Compromise User Devices appeared first on Cyber Security News.
https://cybersecuritynews.com/facebook-blocked-7-surveillance-for-hire-industries/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/facebook-blocked-7-surveillance-for-hire-industries/?utm_source=dlvr.it&utm_medium=blogger
DISA done with MilCloud 2.0
This article has been indexed from FCW – All Content The program, which has a contract set to expire in May 2022, was designed to help DOD users from the military services and combatant commands leverage commercial cloud services. Read…
Read more →
The post DISA done with MilCloud 2.0 first appeared on IT Security News.
https://www.itsecuritynews.info/disa-done-with-milcloud-2-0/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/disa-done-with-milcloud-2-0/?utm_source=dlvr.it&utm_medium=blogger
Facebook Bans 7 'Cyber Mercenary' Companies for Spying on 50,000 Users
Meta Platforms on Thursday revealed it took steps to deplatform seven cyber mercenaries that it said carried out "indiscriminate" targeting of journalists, dissidents, critics of authoritarian regimes, families of opposition, and human rights activists located in over 100 countries, amid mounting scrutiny of surveillance technologies.
To that end, the company said it alerted 50,000 users of
https://thehackernews.com/2021/12/facebook-bans-7-cyber-mercenaries.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/facebook-bans-7-cyber-mercenaries.html?utm_source=dlvr.it&utm_medium=blogger
New Phorpiex Botnet Variant Steals Half a Million Dollars in Cryptocurrency
Cryptocurrency users in Ethiopia, Nigeria, India, Guatemala, and the Philippines are being targeted by a new variant of the Phorpiex botnet called Twizt that has resulted in the theft of virtual coins amounting to $500,000 over the last one year.
Israeli security firm Check Point Research, which detailed the attacks, said the latest evolutionary version "enables the botnet to operate
https://thehackernews.com/2021/12/new-phorpiex-botnet-variant-steals-half.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/new-phorpiex-botnet-variant-steals-half.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 16, 2021
NSA and CISA Release Final Part IV of Guidance on Securing 5G Cloud Infrastructures
This article has been indexed from CISA All NCAS Products This post doesn’t have text content, please click on the link below to view the original article. Read the original article: NSA and CISA Release Final Part IV of Guidance…
Read more →
The post NSA and CISA Release Final Part IV of Guidance on Securing 5G Cloud Infrastructures first appeared on IT Security News.
https://www.itsecuritynews.info/nsa-and-cisa-release-final-part-iv-of-guidance-on-securing-5g-cloud-infrastructures/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/nsa-and-cisa-release-final-part-iv-of-guidance-on-securing-5g-cloud-infrastructures/?utm_source=dlvr.it&utm_medium=blogger
Privacy, Identity, and Device Protection: Why You Need to Invest in All Three
This article has been indexed from McAfee Blogs Cybercriminals make people uneasy about the safety of their identity and online accounts. McAfee is your partner who’ll work tirelessly to restore your confidence in your online activities. Check out this roundup… The post Privacy, Identity, and Device Protection: Why You Need to Invest…
Read more →
The post Privacy, Identity, and Device Protection: Why You Need to Invest in All Three first appeared on IT Security News.
https://www.itsecuritynews.info/privacy-identity-and-device-protection-why-you-need-to-invest-in-all-three/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/privacy-identity-and-device-protection-why-you-need-to-invest-in-all-three/?utm_source=dlvr.it&utm_medium=blogger
Log4Shell: The Big Picture
This article has been indexed from Dark Reading A look at why this is such a tricky vulnerability and why the industry response has been good, but not great. Read the original article: Log4Shell: The Big Picture
Read more →
The post Log4Shell: The Big Picture first appeared on IT Security News.
https://www.itsecuritynews.info/log4shell-the-big-picture/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/log4shell-the-big-picture/?utm_source=dlvr.it&utm_medium=blogger
The Guide to Automating Security Training for Lean Security Teams
Cyber threats used to be less threatening. While nobody wants their customers' credit card numbers stolen in a data breach, or to see a deranged manifesto plastered over their company website, such incidents can almost seem quaint compared to ransomware attacks that bring all of your critical information systems to a dead halt.
The frequency of these attacks increased more than 150% in the U.S.
https://thehackernews.com/2021/12/the-guide-to-automating-security.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/the-guide-to-automating-security.html?utm_source=dlvr.it&utm_medium=blogger
A New Espionage Hacking Campaign Targeting Telecoms & IT Services Organizations
A new espionage hacking campaign has been detected by the cybersecurity experts that are continuously targeting all the telecommunication and IT service providers especially in the Middle East and Asia. After investigating the attack, the experts came to know that the threat actors are most likely connected to the Iranian threat actor team Mercury, and […]
The post A New Espionage Hacking Campaign Targeting Telecoms & IT Services Organizations appeared first on Cyber Security News.
https://cybersecuritynews.com/a-new-espionage-hacking-campaign-targeting-telecoms/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/a-new-espionage-hacking-campaign-targeting-telecoms/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, December 15, 2021
Druva hires Yogesh Badwe as CSO
This article has been indexed from Help Net Security Druva announced the appointment of Yogesh Badwe as the company’s Chief Security Officer (CSO). Bringing nearly 15 years of experience leading mature cybersecurity programs at high-growth organizations, Badwe will oversee all…
Read more →
The post Druva hires Yogesh Badwe as CSO first appeared on IT Security News.
https://www.itsecuritynews.info/druva-hires-yogesh-badwe-as-cso/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/druva-hires-yogesh-badwe-as-cso/?utm_source=dlvr.it&utm_medium=blogger
FBI’s investigation accidentally revealed the HelloKitty ransomware gang operates out of Ukraine
This article has been indexed from Security Affairs While investigating a data breach suffered by a healthcare organization, FBI accidentally revealed that it believes that the HelloKitty ransomware gang operates out of Ukraine. The investigation conducted by FBI on a…
Read more →
The post FBI’s investigation accidentally revealed the HelloKitty ransomware gang operates out of Ukraine first appeared on IT Security News.
https://www.itsecuritynews.info/fbis-investigation-accidentally-revealed-the-hellokitty-ransomware-gang-operates-out-of-ukraine/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/fbis-investigation-accidentally-revealed-the-hellokitty-ransomware-gang-operates-out-of-ukraine/?utm_source=dlvr.it&utm_medium=blogger
Facebook to Pay Hackers for Reporting Data Scraping Bugs and Scraped Datasets
Meta Platforms, the company formerly known as Facebook, has announced that it's expanding its bug bounty program to start rewarding valid reports of scraping vulnerabilities across its platforms as well as include reports of scraping data sets that are available online. "We know that automated activity designed to scrape people's public and private data targets every website or service," said
https://thehackernews.com/2021/12/facebook-to-pay-hackers-for-reporting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/facebook-to-pay-hackers-for-reporting.html?utm_source=dlvr.it&utm_medium=blogger
New Bugs that Affect Billions of WiFi Chips Let Attackers Extract Passwords & Manipulate Traffic
A new series of threat attacks has been detected by the security experts from the University of Darmstadt, Brescia, CNIT, and the Secure Mobile Networking Lab. These new bugs affect billions of WiFi Chips that allow any attackers to extract passwords and manipulate traffic from the affected devices. All the exploits that are detected are […]
The post New Bugs that Affect Billions of WiFi Chips Let Attackers Extract Passwords & Manipulate Traffic appeared first on Cyber Security News.
https://cybersecuritynews.com/wifi-chips/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/wifi-chips/?utm_source=dlvr.it&utm_medium=blogger
Microsoft Issues Windows Update to Patch 0-Day Used to Spread Emotet Malware
Microsoft has rolled out Patch Tuesday updates to address multiple security vulnerabilities in Windows and other software, including one actively exploited flaw that's being abused to deliver Emotet, TrickBot, or Bazaloader malware payloads. The latest monthly release for December fixes a total of 67 flaws, bringing the total number of bugs patched by the company this year to 887, according to
https://thehackernews.com/2021/12/microsoft-issues-windows-update-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/microsoft-issues-windows-update-to.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, December 14, 2021
Khonsari ransomware, Nemesis Kitten are exploiting Log4j vulnerability
This article has been indexed from Latest topics for ZDNet in Security Security researchers are discovering that attacks are evolving beyond crypto miners. Read the original article: Khonsari ransomware, Nemesis Kitten are exploiting Log4j vulnerability
Read more → The post Khonsari ransomware, Nemesis Kitten are exploiting Log4j vulnerability first appeared on IT Security News.
https://www.itsecuritynews.info/khonsari-ransomware-nemesis-kitten-are-exploiting-log4j-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/khonsari-ransomware-nemesis-kitten-are-exploiting-log4j-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
Emergency Chrome Update to Fix zero-day Exploited in the Wild
Google recently updated the Chrome browser and released the latest version Chrome 96.0.4664.110 with the patch for a critical zero-day vulnerability that was exploited in the wild and other four security flaws. This latest version of Chrome is released for all the major platforms:- Windows Mac Linux To reach all the users at this moment […]
The post Emergency Chrome Update to Fix zero-day Exploited in the Wild appeared first on Cyber Security News.
https://cybersecuritynews.com/chrome-zero-day-2/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/chrome-zero-day-2/?utm_source=dlvr.it&utm_medium=blogger
State CIOs focusing on cyber, digital services, connectivity in 2022
This article has been indexed from GCN: News, Explainers, Insights Cloud services, identity and access management and app modernization led NASCIO’s list of top tech tools. Read the original article: State CIOs focusing on cyber, digital services, connectivity in 2022
Read more → The post State CIOs focusing on cyber, digital services, connectivity in 2022 first appeared on IT Security News.
https://www.itsecuritynews.info/state-cios-focusing-on-cyber-digital-services-connectivity-in-2022/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/state-cios-focusing-on-cyber-digital-services-connectivity-in-2022/?utm_source=dlvr.it&utm_medium=blogger
Hackers Attacked 1.6 Million WordPress Sites Via Four Different Vulnerable Plugins
This article has been indexed from Latest Hacking News In a recent wave of attacks, hackers targeted 1.6 million WordPress sites by exploiting unpatched… Hackers Attacked 1.6 Million WordPress Sites Via Four Different Vulnerable Plugins on Latest Hacking News. Read…
Read more → The post Hackers Attacked 1.6 Million WordPress Sites Via Four Different Vulnerable Plugins first appeared on IT Security News.
https://www.itsecuritynews.info/hackers-attacked-1-6-million-wordpress-sites-via-four-different-vulnerable-plugins/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hackers-attacked-1-6-million-wordpress-sites-via-four-different-vulnerable-plugins/?utm_source=dlvr.it&utm_medium=blogger
Update Google Chrome to Patch New Zero-Day Exploit Detected in the Wild
Google has rolled out fixes for five security vulnerabilities in its Chrome web browser, including one which it says is being exploited in the wild, making it the 17th such weakness to be disclosed since the start of the year. Tracked as CVE-2021-4102, the flaw relates to a use-after-free bug in the V8 JavaScript and WebAssembly engine, which could have severe consequences ranging from
https://thehackernews.com/2021/12/update-google-chrome-to-patch-new-zero.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/update-google-chrome-to-patch-new-zero.html?utm_source=dlvr.it&utm_medium=blogger
Monday, December 13, 2021
Dream Job Alert: Senior Fellow for Decentralization at EFF
This article has been indexed from Deeplinks We have an amazing opportunity to join the EFF team. We are hiring a Senior Fellow of Decentralization, a position that is a public advocate helping to establish EFF as a leader in…
Read more → The post Dream Job Alert: Senior Fellow for Decentralization at EFF first appeared on IT Security News.
https://www.itsecuritynews.info/dream-job-alert-senior-fellow-for-decentralization-at-eff/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/dream-job-alert-senior-fellow-for-decentralization-at-eff/?utm_source=dlvr.it&utm_medium=blogger
Apple Patches 42 Security Flaws in Latest iOS Refresh
This article has been indexed from SecurityWeek RSS Feed Apple has released a major point-update to its flagship iOS mobile operating system, beefing up app privacy protections and patching at least 42 security defects that expose users to malicious hacker…
Read more → The post Apple Patches 42 Security Flaws in Latest iOS Refresh first appeared on IT Security News.
https://www.itsecuritynews.info/apple-patches-42-security-flaws-in-latest-ios-refresh/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-patches-42-security-flaws-in-latest-ios-refresh/?utm_source=dlvr.it&utm_medium=blogger
Hackers Exploiting Log4j 0-day Flaw to deploy Malware on Vulnerable Servers
A new 0-day exploit with the popular Java logging library log4j lets attackers execute remote code and gain full control over the server. Log4j is a part of Apache Logging Services that is Widely used by both enterprise apps and cloud services. A security researcher published the 0-day flaw published on Twitter and also the […]
The post Hackers Exploiting Log4j 0-day Flaw to deploy Malware on Vulnerable Servers appeared first on Cyber Security News.
https://cybersecuritynews.com/log4j-0-day/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/log4j-0-day/?utm_source=dlvr.it&utm_medium=blogger
Top 3 SaaS Security Threats for 2022
With 2021 drawing to a close and many closing their plans and budgets for 2022, the time has come to do a brief wrap-up of the SaaS Security challenges on the horizon. Here are the top 3 SaaS security posture challenges as we see them. 1 — The Mess of Misconfiguration Management The good news is that more businesses than ever are using SaaS apps such as GitHub, Microsoft 365, Salesforce, Slack,
https://thehackernews.com/2021/12/top-3-saas-security-threats-for-2022.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/top-3-saas-security-threats-for-2022.html?utm_source=dlvr.it&utm_medium=blogger
Microsoft Details Building Blocks of Widely Active Qakbot Banking Trojan
Infection chains associated with the multi-purpose Qakbot malware have been broken down into "distinct building blocks," an effort that Microsoft said will help to detect and block the threat in an effective manner proactively. The Microsoft 365 Defender Threat Intelligence Team dubbed Qakbot a "customizable chameleon that adapts to suit the needs of the multiple threat actor groups that utilize
https://thehackernews.com/2021/12/microsoft-details-building-blocks-of.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/12/microsoft-details-building-blocks-of.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, December 12, 2021
The Best Ways to Secure Communication Channels in The Enterprise Environment
This article has been indexed from Cybersecurity Insiders Data security is an important factor in every enterprise and organization. Every day lots of confidential information is sent and received. And any compromise in security can harm the company’s reputation. Sometimes,…
Read more → The post The Best Ways to Secure Communication Channels in The Enterprise Environment first appeared on IT Security News.
https://www.itsecuritynews.info/the-best-ways-to-secure-communication-channels-in-the-enterprise-environment/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-best-ways-to-secure-communication-channels-in-the-enterprise-environment/?utm_source=dlvr.it&utm_medium=blogger
Anticipating Future Directions of Tech-Enabled Terror
This article has been indexed from Lawfare A U.S. Marine pilots a DJI Phantom 3 drone during a training exercise at Camp Lejeune, NC, on Jan. 17, 2018. Photo credit: U.S. Marine Corps photo by Lance Cpl. Tojyea G. Matally…
Read more → The post Anticipating Future Directions of Tech-Enabled Terror first appeared on IT Security News.
https://www.itsecuritynews.info/anticipating-future-directions-of-tech-enabled-terror/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/anticipating-future-directions-of-tech-enabled-terror/?utm_source=dlvr.it&utm_medium=blogger
Russian nation sentenced to 48 months in prison for helping Kelihos Botnet to evade detection
This article has been indexed from Security Affairs A United States court has sentenced to four years in prison for the Russian citizen Oleg Koshkin for his role in Kelihos Botnet development. Oleg Koshkin (41) has been sentenced to 48…
Read more → The post Russian nation sentenced to 48 months in prison for helping Kelihos Botnet to evade detection first appeared on IT Security News.
https://www.itsecuritynews.info/russian-nation-sentenced-to-48-months-in-prison-for-helping-kelihos-botnet-to-evade-detection/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/russian-nation-sentenced-to-48-months-in-prison-for-helping-kelihos-botnet-to-evade-detection/?utm_source=dlvr.it&utm_medium=blogger
How to Guard Against Smishing Attacks on Your Phone
This article has been indexed from Security Latest “Smishing” is an attempt to collect logins or other sensitive information with a malicious text message—and it’s on the rise. Read the original article: How to Guard Against Smishing Attacks on Your…
Read more → The post How to Guard Against Smishing Attacks on Your Phone first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-guard-against-smishing-attacks-on-your-phone/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-to-guard-against-smishing-attacks-on-your-phone/?utm_source=dlvr.it&utm_medium=blogger
300,000 MikroTik Devices Still Vulnerable To Botnets For Remote Hacking
Security experts of Eclypsium have recently detected more than 300,000 vulnerable Internet-accessible MikroTik routers. These routers are being targeted by the threat actors, as the owners forgot to install firmware updates for four-year-old vulnerabilities. After investigating the attack, it become known that the most influenced devices were discovered in the following countries:- China Brazil Russia […]
The post 300,000 MikroTik Devices Still Vulnerable To Botnets For Remote Hacking appeared first on Cyber Security News.
https://cybersecuritynews.com/300000-mikrotik-devices-still-vulnerable/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/300000-mikrotik-devices-still-vulnerable/?utm_source=dlvr.it&utm_medium=blogger
Saturday, December 11, 2021
Canadian Citizen Charged for Ransomware Attacks in Alaska
This article has been indexed from HackRead By Deeba Ahmed The accused became a suspect when the FBI contacted Canadian intelligence after observing a surge in ransomware attacks in Alaska in 2018. This is a post from HackRead.com Read the…
Read more → The post Canadian Citizen Charged for Ransomware Attacks in Alaska first appeared on IT Security News.
https://www.itsecuritynews.info/canadian-citizen-charged-for-ransomware-attacks-in-alaska/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/canadian-citizen-charged-for-ransomware-attacks-in-alaska/?utm_source=dlvr.it&utm_medium=blogger
Update on Apache Log4j Zero-Day Vulnerability
This article has been indexed from Security Intelligence IBM Security is following a recent disclosure regarding an Apache vulnerability in the Log4j Java library dubbed Log4Shell (or LogJam). X-Force Exchange has further details on the exploit. Millions of applications use…
Read more → The post Update on Apache Log4j Zero-Day Vulnerability first appeared on IT Security News.
https://www.itsecuritynews.info/update-on-apache-log4j-zero-day-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/update-on-apache-log4j-zero-day-vulnerability/?utm_source=dlvr.it&utm_medium=blogger
Cyber Pandemic Update – Protect yourself against a widely exploited vulnerability CVE-2021-44228 (Apache Log4j2 versions 2.14.1)
This article has been indexed from Check Point Software What happened? On December 9th, an acute remote code execution (RCE) vulnerability was reported in the Apache logging package Log4j2 versions 2.14.1 and below (CVE-2021-44228). Apache Log4j is the most popular java…
Read more → The post Cyber Pandemic Update – Protect yourself against a widely exploited vulnerability CVE-2021-44228 (Apache Log4j2 versions 2.14.1) first appeared on IT Security News.
https://www.itsecuritynews.info/cyber-pandemic-update-protect-yourself-against-a-widely-exploited-vulnerability-cve-2021-44228-apache-log4j2-versions-2-14-1/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cyber-pandemic-update-protect-yourself-against-a-widely-exploited-vulnerability-cve-2021-44228-apache-log4j2-versions-2-14-1/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)