This article has been indexed from Latest topics for ZDNet in Security You’ll never have to worry about your online safety again while enjoying unlimited bandwidth and unrestricted access to all your favorite content no matter where you happen to…
Read more → The post For a limited time, new users can get a lifetime of VPNSecure Online Privacy for just $40 first appeared on IT Security News.
https://www.itsecuritynews.info/for-a-limited-time-new-users-can-get-a-lifetime-of-vpnsecure-online-privacy-for-just-40/?utm_source=dlvr.it&utm_medium=blogger
Sunday, November 21, 2021
5 Reasons to Hire a Cybersecurity Company for your Business
Want to launch an engineering startup and wondering whether you need to hire a team to protect data from various intrusions? Find out 5 reasons why you should do it. Daily, global cybersecurity research centers reveal more than half a million novel malicious apps floating around the Internet. A wide range of big/small businesses and […]
The post 5 Reasons to Hire a Cybersecurity Company for your Business appeared first on Cyber Security News.
https://cybersecuritynews.com/5-reasons-to-hire-a-cybersecurity-company-for-your-business/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/5-reasons-to-hire-a-cybersecurity-company-for-your-business/?utm_source=dlvr.it&utm_medium=blogger
Armorblox email security platform integrates with Microsoft Sentinel to help stop email-based BEC
This article has been indexed from Help Net Security Armorblox announced that it has joined the Microsoft Intelligent Security Association (MISA), a coalition of independent software vendors and managed security service providers that have integrated their solutions into Microsoft’s security…
Read more → The post Armorblox email security platform integrates with Microsoft Sentinel to help stop email-based BEC first appeared on IT Security News.
https://www.itsecuritynews.info/armorblox-email-security-platform-integrates-with-microsoft-sentinel-to-help-stop-email-based-bec/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/armorblox-email-security-platform-integrates-with-microsoft-sentinel-to-help-stop-email-based-bec/?utm_source=dlvr.it&utm_medium=blogger
Cyware partners with Flashpoint to empower security teams to automate threat response workflows
This article has been indexed from Help Net Security Cyware announced an expanded partnership with Flashpoint to deliver intelligent automation to security teams. The partnership now features a solution that enables customers to leverage Flashpoint’s intelligence data with Cyware’s Security…
Read more → The post Cyware partners with Flashpoint to empower security teams to automate threat response workflows first appeared on IT Security News.
https://www.itsecuritynews.info/cyware-partners-with-flashpoint-to-empower-security-teams-to-automate-threat-response-workflows/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cyware-partners-with-flashpoint-to-empower-security-teams-to-automate-threat-response-workflows/?utm_source=dlvr.it&utm_medium=blogger
11 Malicious Python Packages Downloaded Over 41,000 Times Caught Stealing Tokens & Passwords
The security engineers of the Python Package Index (PyPI) have recently detected 11 malicious Python packages that were downloaded more than 41,000 times, and these malicious Python packages were used by the threat actors to steal access tokens and passwords. But luckily all these 11 malicious Python packages were removed by them since it is […]
The post 11 Malicious Python Packages Downloaded Over 41,000 Times Caught Stealing Tokens & Passwords appeared first on Cyber Security News.
https://cybersecuritynews.com/11-malicious-python-packages-downloaded-over-41000-times/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/11-malicious-python-packages-downloaded-over-41000-times/?utm_source=dlvr.it&utm_medium=blogger
Saturday, November 20, 2021
Top Stories: Apple Self Service Repair, iOS 15.1.1 Released, and More
This article has been indexed from MacRumors: Mac News and Rumors – Front Page The biggest news item this week was Apple’s announcement of an upcoming Self Service Repair program that will allow users to obtain parts, tools, and manuals…
Read more → The post Top Stories: Apple Self Service Repair, iOS 15.1.1 Released, and More first appeared on IT Security News.
https://www.itsecuritynews.info/top-stories-apple-self-service-repair-ios-15-1-1-released-and-more/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/top-stories-apple-self-service-repair-ios-15-1-1-released-and-more/?utm_source=dlvr.it&utm_medium=blogger
SS7 Exploit Service Providers on The Dark Web are Fake
This article has been indexed from GBHackers On Security In Signalling System No. 7 or SS7 back in 2016, the cybersecurity researchers warned of vulnerabilities in it, and as a result, just a year later, the SS7 attacks turned real…
Read more → The post SS7 Exploit Service Providers on The Dark Web are Fake first appeared on IT Security News.
https://www.itsecuritynews.info/ss7-exploit-service-providers-on-the-dark-web-are-fake/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ss7-exploit-service-providers-on-the-dark-web-are-fake/?utm_source=dlvr.it&utm_medium=blogger
AT&T Alien Labs finds new Golang malware (BotenaGo) targeting millions of routers and IoT devices with more than 30 exploits
This article has been indexed from Cybersecurity Insiders Executive summary AT&T Alien Labs™ has found new malware written in the open source programming language Golang. Deployed with more than 30 exploits, it has the potential of targeting millions of routers…
Read more → The post AT&T Alien Labs finds new Golang malware (BotenaGo) targeting millions of routers and IoT devices with more than 30 exploits first appeared on IT Security News.
https://www.itsecuritynews.info/att-alien-labs-finds-new-golang-malware-botenago-targeting-millions-of-routers-and-iot-devices-with-more-than-30-exploits-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/att-alien-labs-finds-new-golang-malware-botenago-targeting-millions-of-routers-and-iot-devices-with-more-than-30-exploits-2/?utm_source=dlvr.it&utm_medium=blogger
Enhancing AT&T SASE with Palo Alto Networks ‘as a Service’
This article has been indexed from Cybersecurity Insiders A few months ago, I wrote a blog on “SASE as a Service” that described how managed services providers (MSPs) can be a catalyzing force for transforming to SASE and bridging the…
Read more → The post Enhancing AT&T SASE with Palo Alto Networks ‘as a Service’ first appeared on IT Security News.
https://www.itsecuritynews.info/enhancing-att-sase-with-palo-alto-networks-as-a-service-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/enhancing-att-sase-with-palo-alto-networks-as-a-service-2/?utm_source=dlvr.it&utm_medium=blogger
U.S. Charged 2 Iranian Hackers for Threatening Voters During 2020 Presidential Election
The U.S. government on Thursday unsealed an indictment that accused two Iranian nationals of their involvement in cyber-enabled disinformation and threat campaign orchestrated to interfere in the 2020 presidential elections by gaining access to confidential voter information from at least one state election website. The two defendants in question — Seyyed Mohammad Hosein Musa Kazemi, 24, and
https://thehackernews.com/2021/11/us-charged-2-iranians-hackers-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/us-charged-2-iranians-hackers-for.html?utm_source=dlvr.it&utm_medium=blogger
Friday, November 19, 2021
How to Design IoT Security From the Ground Up
This article has been indexed from Security Intelligence The Internet of Things (IoT) is a powerful boon to business. But it also represents a massive potential expansion of the cybersecurity attack surface. So far, IoT inclusion in many organizations has…
Read more → The post How to Design IoT Security From the Ground Up first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-design-iot-security-from-the-ground-up/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-to-design-iot-security-from-the-ground-up/?utm_source=dlvr.it&utm_medium=blogger
California Pizza Kitchen Says Employee Data Stolen in Breach
This article has been indexed from SecurityWeek RSS Feed American pizza chain California Pizza Kitchen (CPK) is notifying employees of a data breach that might have resulted in some of their personal information being accessed by hackers. read more Read…
Read more → The post California Pizza Kitchen Says Employee Data Stolen in Breach first appeared on IT Security News.
https://www.itsecuritynews.info/california-pizza-kitchen-says-employee-data-stolen-in-breach/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/california-pizza-kitchen-says-employee-data-stolen-in-breach/?utm_source=dlvr.it&utm_medium=blogger
New Side Channel Attacks Re-Enable Serious DNS Cache Poisoning Attacks
Researchers have demonstrated yet another variant of the SAD DNS cache poisoning attack that leaves about 38% of the domain name resolvers vulnerable, enabling attackers to redirect traffic originally destined to legitimate websites to a server under their control. "The attack allows an off-path attacker to inject a malicious DNS record into a DNS cache," University of California researchers
https://thehackernews.com/2021/11/new-side-channel-attacks-re-enable.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/new-side-channel-attacks-re-enable.html?utm_source=dlvr.it&utm_medium=blogger
Experts Expose Secrets of Conti Ransomware Group That Made 25 Million from Victims
The clearnet and dark web payment portals operated by the Conti ransomware group have gone down in what appears to be an attempt to shift to new infrastructure after details about the gang's inner workings and its members were made public. According to MalwareHunterTeam, "while both the clearweb and Tor domains of the leak site of the Conti ransomware gang is online and working, both their
https://thehackernews.com/2021/11/experts-expose-secrets-of-conti.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/experts-expose-secrets-of-conti.html?utm_source=dlvr.it&utm_medium=blogger
What Is Endpoint Security?
This article has been indexed from Heimdal Security Blog A significant portion of cyberattacks target endpoints, either individually or as gateways to the larger company network. Unfortunately, this is not a singular threat, but a layered issue: hackers exploit software…
Read more → The post What Is Endpoint Security? first appeared on IT Security News.
https://www.itsecuritynews.info/what-is-endpoint-security-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/what-is-endpoint-security-2/?utm_source=dlvr.it&utm_medium=blogger
Thursday, November 18, 2021
Critical Root RCE Bug Affects Multiple Netgear SOHO Router Models
Networking equipment company Netgear has released yet another round of patches to remediate a high-severity remote code execution vulnerability affecting multiple routers that could be exploited by remote attackers to take control of an affected system. Tracked as CVE-2021-34991 (CVSS score: 8.8), the pre-authentication buffer overflow flaw in small office and home office (SOHO) routers can lead
https://thehackernews.com/2021/11/critical-root-rce-bug-affects-multiple.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/critical-root-rce-bug-affects-multiple.html?utm_source=dlvr.it&utm_medium=blogger
How to Build a Security Awareness Training Program that Yields Measurable Results
Organizations have been worrying about cyber security since the advent of the technological age. Today, digital transformation coupled with the rise of remote work has made the need for security awareness all the more critical. Cyber security professionals are continuously thinking about how to prevent cyber security breaches from happening, with employees and contractors often proving to be the
https://thehackernews.com/2021/11/how-to-build-security-awareness.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/how-to-build-security-awareness.html?utm_source=dlvr.it&utm_medium=blogger
Phishing campaign targets Tiktok influencer accounts
This article has been indexed from Security Affairs Threat actors have launched a phishing campaign targeting more than 125 TikTok ‘Influencer’ accounts in an attempt to hijack them. Researchers from Abnormal Security uncovered a phishing scam aimed at hijacking at…
Read more → The post Phishing campaign targets Tiktok influencer accounts first appeared on IT Security News.
https://www.itsecuritynews.info/phishing-campaign-targets-tiktok-influencer-accounts/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/phishing-campaign-targets-tiktok-influencer-accounts/?utm_source=dlvr.it&utm_medium=blogger
Threat Actors Discuss Leasing Zero-Day Exploits
This article has been indexed from http://www.infosecurity-magazine.com/rss/news/76/application-security/ Exploit-as-a-service model mooted in the cybercrime underground Read the original article: Threat Actors Discuss Leasing Zero-Day Exploits
Read more → The post Threat Actors Discuss Leasing Zero-Day Exploits first appeared on IT Security News.
https://www.itsecuritynews.info/threat-actors-discuss-leasing-zero-day-exploits/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/threat-actors-discuss-leasing-zero-day-exploits/?utm_source=dlvr.it&utm_medium=blogger
Hackers Hijacked Alibaba Servers to Install Cryptominer Malware
Hackers have recently targeted and hacked the Alibaba Elastic Computing Service (ECS) instances. All this is being done with the motive to install crypto-miner malware so that the threat actors can secure the available server resources for their own personal benefit. The hacker “AgainstTheWest” on the RaidForums forum had proclaimed that they have hacked into […]
The post Hackers Hijacked Alibaba Servers to Install Cryptominer Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/alibaba-servers-cryptominer/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/alibaba-servers-cryptominer/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, November 17, 2021
Bugcrowd correlates $27bn risk reduction with ethical hacking to find vulnerabilities
This article has been indexed from IT Security Guru Bugcrowd, the crowdsourced cybersecurity platform, has published its Inside the Mind of a Hacker ’21 report, which it says provides CIOs and CISOs valuable insight on ethical hackers and the economics…
Read more → The post Bugcrowd correlates $27bn risk reduction with ethical hacking to find vulnerabilities first appeared on IT Security News.
https://www.itsecuritynews.info/bugcrowd-correlates-27bn-risk-reduction-with-ethical-hacking-to-find-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/bugcrowd-correlates-27bn-risk-reduction-with-ethical-hacking-to-find-vulnerabilities/?utm_source=dlvr.it&utm_medium=blogger
Protecting Against Ransomware: Zero Trust Security For a Modern Workforce
This article has been indexed from The Duo Blog One of the worst outcomes of a lack of a strong zero trust security foundation is a ransomware attack. The modernization of ransomware, coupled with Ransomware-as-a-Service (RaaS), has made it incredibly…
Read more → The post Protecting Against Ransomware: Zero Trust Security For a Modern Workforce first appeared on IT Security News.
https://www.itsecuritynews.info/protecting-against-ransomware-zero-trust-security-for-a-modern-workforce/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/protecting-against-ransomware-zero-trust-security-for-a-modern-workforce/?utm_source=dlvr.it&utm_medium=blogger
New Blacksmith Exploit Bypasses Current Rowhammer Attack Defenses
Cybersecurity researchers have demonstrated yet another variation of the Rowhammer attack affecting all DRAM (dynamic random-access memory) chips that bypasses currently deployed mitigations, thereby effectively compromising the security of the devices. The new technique — dubbed "Blacksmith" (CVE-2021-42114, CVSS score: 9.0) — is designed to trigger bit flips on target refresh rate-enabled DRAM
https://thehackernews.com/2021/11/new-blacksmith-exploit-bypasses-current.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/new-blacksmith-exploit-bypasses-current.html?utm_source=dlvr.it&utm_medium=blogger
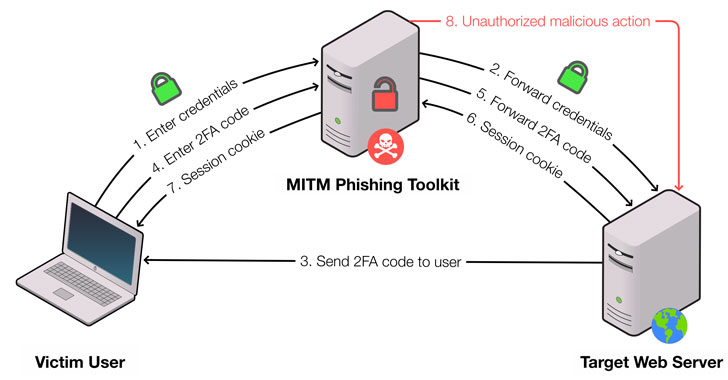
Researchers Demonstrate New Way to Detect MitM Phishing Kits in the Wild
No fewer than 1,220 Man-in-the-Middle (MitM) phishing websites have been discovered as targeting popular online services like Instagram, Google, PayPal, Apple, Twitter, and LinkedIn with the goal of hijacking users' credentials and carrying out further follow-on attacks. The findings come from a new study undertaken by a group of researchers from Stony Brook University and Palo Alto Networks,
https://thehackernews.com/2021/11/researchers-demonstrate-new-way-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/researchers-demonstrate-new-way-to.html?utm_source=dlvr.it&utm_medium=blogger
FCW Insider: November 17, 2021
This article has been indexed from FCW: The business of federal technology The latest news and analysis from FCW’s reporters and editors. Read the original article: FCW Insider: November 17, 2021
Read more → The post FCW Insider: November 17, 2021 first appeared on IT Security News.
https://www.itsecuritynews.info/fcw-insider-november-17-2021/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/fcw-insider-november-17-2021/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, November 16, 2021
As cloud threats inundate businesses, Cado Security aims for rapid expansion
This article has been indexed from Security – VentureBeat Cado Security reports big demand for its cloud-native digital forensics platform, supporting cloud security investigations for AWS and Azure. Read the original article: As cloud threats inundate businesses, Cado Security aims…
Read more → The post As cloud threats inundate businesses, Cado Security aims for rapid expansion first appeared on IT Security News.
https://www.itsecuritynews.info/as-cloud-threats-inundate-businesses-cado-security-aims-for-rapid-expansion/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/as-cloud-threats-inundate-businesses-cado-security-aims-for-rapid-expansion/?utm_source=dlvr.it&utm_medium=blogger
Palo Alto Networks updates Prisma Cloud to secure the full app lifecycle
This article has been indexed from Latest topics for ZDNet in Security The latest version of Prisma Cloud offers cloud code security, agentless security and other enhancements to embed security into the entire application lifecycle. Read the original article: Palo…
Read more → The post Palo Alto Networks updates Prisma Cloud to secure the full app lifecycle first appeared on IT Security News.
https://www.itsecuritynews.info/palo-alto-networks-updates-prisma-cloud-to-secure-the-full-app-lifecycle/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/palo-alto-networks-updates-prisma-cloud-to-secure-the-full-app-lifecycle/?utm_source=dlvr.it&utm_medium=blogger
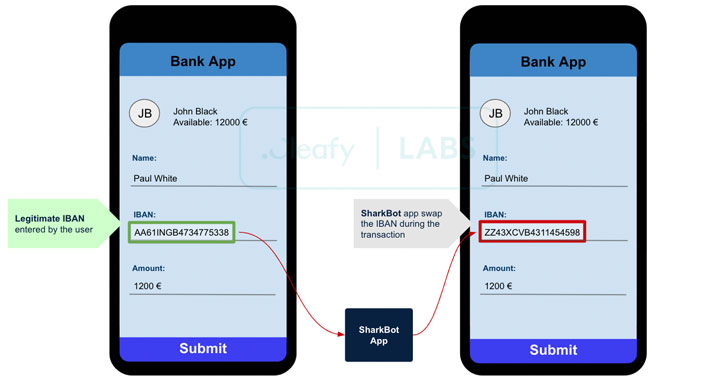
SharkBot — A New Android Trojan Stealing Banking and Cryptocurrency Accounts
Cybersecurity researchers on Monday took the wraps off a new Android trojan that takes advantage of accessibility features on the devices to siphon credentials from banking and cryptocurrency services in Italy, the U.K., and the U.S. Dubbed "SharkBot" by Cleafy, the malware is designed to strike a total of 27 targets — counting 22 unnamed international banks in Italy and the U.K. as well as five
https://thehackernews.com/2021/11/sharkbot-new-android-trojan-stealing.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/sharkbot-new-android-trojan-stealing.html?utm_source=dlvr.it&utm_medium=blogger
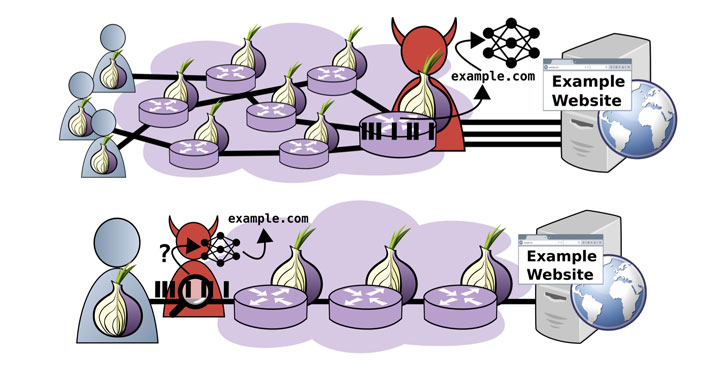
Researchers Demonstrate New Fingerprinting Attack on Tor Encrypted Traffic
A new analysis of website fingerprinting (WF) attacks aimed at the Tor web browser has revealed that it's possible for an adversary to glean a website frequented by a victim, but only in scenarios where the threat actor is interested in a specific subset of the websites visited by users. "While attacks can exceed 95% accuracy when monitoring a small set of five popular websites, indiscriminate (
https://thehackernews.com/2021/11/researchers-demonstrate-new.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/researchers-demonstrate-new.html?utm_source=dlvr.it&utm_medium=blogger
Peloton bike, Amazon Halo Band and Facebook Portal featured on Mozilla list of holiday gifts lacking privacy features
This article has been indexed from Latest topics for ZDNet in Security Mozilla researchers spent over 950 hours examining 151 popular connected gifts, identifying 47 that had what they called “problematic privacy practices.” Read the original article: Peloton bike, Amazon…
Read more → The post Peloton bike, Amazon Halo Band and Facebook Portal featured on Mozilla list of holiday gifts lacking privacy features first appeared on IT Security News.
https://www.itsecuritynews.info/peloton-bike-amazon-halo-band-and-facebook-portal-featured-on-mozilla-list-of-holiday-gifts-lacking-privacy-features/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/peloton-bike-amazon-halo-band-and-facebook-portal-featured-on-mozilla-list-of-holiday-gifts-lacking-privacy-features/?utm_source=dlvr.it&utm_medium=blogger
Monday, November 15, 2021
Cisco Secure Cloud Insights is your Eye in the Sky
This article has been indexed from Security – Cisco Blogs This blog introduces Cisco Secure Cloud Insights, which provides hybrid cloud asset inventory, security posture management and continuous monitoring. Read the original article: Cisco Secure Cloud Insights is your Eye…
Read more → The post Cisco Secure Cloud Insights is your Eye in the Sky first appeared on IT Security News.
https://www.itsecuritynews.info/cisco-secure-cloud-insights-is-your-eye-in-the-sky/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cisco-secure-cloud-insights-is-your-eye-in-the-sky/?utm_source=dlvr.it&utm_medium=blogger
1-15 October 2021 Cyber Attacks Timeline
This article has been indexed from HACKMAGEDDON The first cyber attacks timeline of October 2021 is here and let me say that, at least in terms of numbers, I have recorded the lower value for this year: Read the original…
Read more → The post 1-15 October 2021 Cyber Attacks Timeline first appeared on IT Security News.
https://www.itsecuritynews.info/1-15-october-2021-cyber-attacks-timeline/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/1-15-october-2021-cyber-attacks-timeline/?utm_source=dlvr.it&utm_medium=blogger
Cloudflare Blocks an Almost 2 Tbps Multi-vector DDoS Attack
Cloudflare mitigated a multi-vector DDoS attack of almost 2 Tbps recently with the help of its automated defense mechanism and Cloudflare remarked this multi-vector DDoS attack as one of the largest till now. A multi-vector DDoS attack is a combination of DNS amplification attacks and UDP floods, and this entire multi-vector DDoS attack served for […]
The post Cloudflare Blocks an Almost 2 Tbps Multi-vector DDoS Attack appeared first on Cyber Security News.
https://cybersecuritynews.com/cloudflare-blocks-an-almost-2-tbps-multi-vector-ddos-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cloudflare-blocks-an-almost-2-tbps-multi-vector-ddos-attack/?utm_source=dlvr.it&utm_medium=blogger
What Do You Need to Proactively Identify Cyber-Security Threats?
In today’s world, almost all businesses are running online with different software. Every company in the world sometimes encounters a security threat. The threats may fluctuate and vary every day, every hour, every minute, every second. So if the organizations want to feel secure from cyber-threats, they have to update their security protocols. What is […]
The post What Do You Need to Proactively Identify Cyber-Security Threats? appeared first on Cyber Security News.
https://cybersecuritynews.com/what-do-you-need-to-proactively-identify-cyber-security-threats/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/what-do-you-need-to-proactively-identify-cyber-security-threats/?utm_source=dlvr.it&utm_medium=blogger
How to Tackle SaaS Security Misconfigurations
Whether it's Office 365, Salesforce, Slack, GitHub or Zoom, all SaaS apps include a host of security features designed to protect the business and its data. The job of ensuring these apps' security settings are properly configured falls on the security team. The challenge lies within how burdensome this responsibility is — each app has tens or hundreds of security settings to configure, in
https://thehackernews.com/2021/11/how-to-tackle-saas-security.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/how-to-tackle-saas-security.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, November 14, 2021
Weekly Update 269
This article has been indexed from Troy Hunt’s Blog Presently sponsored by: 1Password is a secure password manager and digital wallet that keeps you safe online Where does the time go? The video is an hour and 35 mins today,…
Read more → The post Weekly Update 269 first appeared on IT Security News.
https://www.itsecuritynews.info/weekly-update-269/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/weekly-update-269/?utm_source=dlvr.it&utm_medium=blogger
Report: 99% of federal security pros want the government to increase data protection
This article has been indexed from Security – VentureBeat Federal security professionals cite common challenges to cybersecurity, like a lack of leadership, internal expertise, and resources. Read the original article: Report: 99% of federal security pros want the government to…
Read more → The post Report: 99% of federal security pros want the government to increase data protection first appeared on IT Security News.
https://www.itsecuritynews.info/report-99-of-federal-security-pros-want-the-government-to-increase-data-protection/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/report-99-of-federal-security-pros-want-the-government-to-increase-data-protection/?utm_source=dlvr.it&utm_medium=blogger
Ransomware attacks are getting more complex and even harder to prevent
This article has been indexed from Security – VentureBeat Ransomware attackers are making attacks more complex and costly by acting on potential targets’ weaknesses faster than enterprises can react. Read the original article: Ransomware attacks are getting more complex and…
Read more → The post Ransomware attacks are getting more complex and even harder to prevent first appeared on IT Security News.
https://www.itsecuritynews.info/ransomware-attacks-are-getting-more-complex-and-even-harder-to-prevent/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ransomware-attacks-are-getting-more-complex-and-even-harder-to-prevent/?utm_source=dlvr.it&utm_medium=blogger
NINJIO appoints Brett Wahlin to Board of Directors
This article has been indexed from Help Net Security NINJIO announced the appointment of Brett Wahlin to their board of directors. Brett will advise the company on its continued development and implementation of cyber security solutions. He brings decades of…
Read more → The post NINJIO appoints Brett Wahlin to Board of Directors first appeared on IT Security News.
https://www.itsecuritynews.info/ninjio-appoints-brett-wahlin-to-board-of-directors/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ninjio-appoints-brett-wahlin-to-board-of-directors/?utm_source=dlvr.it&utm_medium=blogger
TrickBot Operators Abusing Windows 10 App Installer To Install BazarLoader Malware
The Principal Researcher of the SophosLabs security firm, Andrew Brandt spotted that to deploy BazarLoader malware on the victim’s systems the TrickBot gang operators are now abusing the Windows 10 App Installer in their malicious campaign. BazarLoader is an enigmatic Trojan and it has several names like:- BazarBackdoor BazaLoader BEERBOT KEGTAP Team9Backdoor This stealthy Trojan, […]
The post TrickBot Operators Abusing Windows 10 App Installer To Install BazarLoader Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/trickbot-operators-abusing-windows-10-app-installer/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/trickbot-operators-abusing-windows-10-app-installer/?utm_source=dlvr.it&utm_medium=blogger
Saturday, November 13, 2021
OPM updates decade-old telework guide
This article has been indexed from FCW: The business of federal technology The Office of Personnel Management is asking agencies to rethink their approach to work in light of lessons learned during the COVID-19 pandemic. Read the original article: OPM…
Read more → The post OPM updates decade-old telework guide first appeared on IT Security News.
https://www.itsecuritynews.info/opm-updates-decade-old-telework-guide/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/opm-updates-decade-old-telework-guide/?utm_source=dlvr.it&utm_medium=blogger
Week in security with Tony Anscombe
This article has been indexed from WeLiveSecurity Steps to take right after a data breach – What to consider before going passwordless – 7 million people hit by Robinhood data breach The post Week in security with Tony Anscombe appeared…
Read more → The post Week in security with Tony Anscombe first appeared on IT Security News.
https://www.itsecuritynews.info/week-in-security-with-tony-anscombe-142/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/week-in-security-with-tony-anscombe-142/?utm_source=dlvr.it&utm_medium=blogger
Threat from Organized Cybercrime Syndicates Is Rising
This article has been indexed from Threatpost Europol reports that criminal groups are undermining the EU’s economy and its society, offering everything from murder-for-hire to kidnapping, torture and mutilation. Read the original article: Threat from Organized Cybercrime Syndicates Is Rising
Read more → The post Threat from Organized Cybercrime Syndicates Is Rising first appeared on IT Security News.
https://www.itsecuritynews.info/threat-from-organized-cybercrime-syndicates-is-rising/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/threat-from-organized-cybercrime-syndicates-is-rising/?utm_source=dlvr.it&utm_medium=blogger
Hackers Increasingly Using HTML Smuggling in Malware and Phishing Attacks
Threat actors are increasingly banking on the technique of HTML smuggling in phishing campaigns as a means to gain initial access and deploy an array of threats, including banking malware, remote administration trojans (RATs), and ransomware payloads. Microsoft 365 Defender Threat Intelligence Team, in a new report published Thursday, disclosed that it identified infiltrations distributing the
https://thehackernews.com/2021/11/hackers-increasingly-using-html.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/hackers-increasingly-using-html.html?utm_source=dlvr.it&utm_medium=blogger
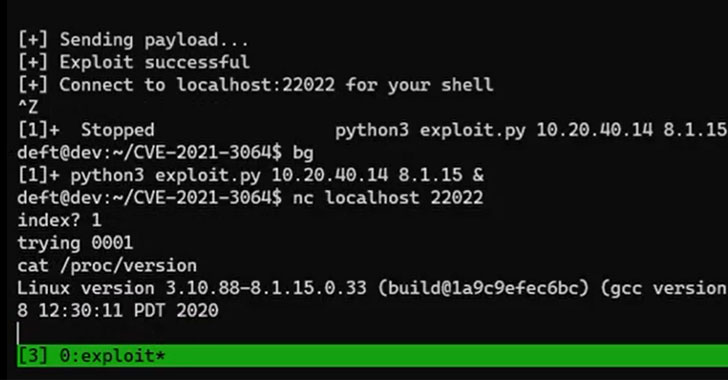
Palo Alto Warns of Zero-Day Bug in Firewalls Let Hackers Execute an Arbitrary Code Remotely
A Zero-Day vulnerability has been identified by the Massachusetts-based cybersecurity firm Randori in Palo Alto Networks firewalls using GlobalProtect VPN. This Zero-Day flaw could be exploited by an unauthorized attacker to execute arbitrary code remotely on vulnerable devices with superuser privileges. This Zero-Day bug was tracked as CVE-2021-3064 scored 9.8 on the CVSS and affects […]
The post Palo Alto Warns of Zero-Day Bug in Firewalls Let Hackers Execute an Arbitrary Code Remotely appeared first on Cyber Security News.
https://cybersecuritynews.com/palo-alto-warns-of-zero-day-bug/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/palo-alto-warns-of-zero-day-bug/?utm_source=dlvr.it&utm_medium=blogger
Friday, November 12, 2021
Iran's Lyceum Hackers Target Telecoms, ISPs in Israel, Saudi Arabia, and Africa
A state-sponsored threat actor allegedly affiliated with Iran has been linked to a series of targeted attacks aimed at internet service providers (ISPs) and telecommunication operators in Israel, Morocco, Tunisia, and Saudi Arabia, as well as a ministry of foreign affairs (MFA) in Africa, new findings reveal. The intrusions, staged by a group tracked as Lyceum, are believed to have occurred
https://thehackernews.com/2021/11/irans-lyceum-hackers-target-telecoms.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/irans-lyceum-hackers-target-telecoms.html?utm_source=dlvr.it&utm_medium=blogger
Palo Alto Warns of Zero-Day Bug in Firewalls Using GlobalProtect Portal VPN
A new zero-day vulnerability has been disclosed in Palo Alto Networks GlobalProtect VPN that could be abused by an unauthenticated network-based attacker to execute arbitrary code on affected devices with root user privileges. Tracked as CVE-2021-3064 (CVSS score: 9.8), the security weakness impacts PAN-OS 8.1 versions earlier than PAN-OS 8.1.17. Massachusetts-based cybersecurity firm Randori
https://thehackernews.com/2021/11/palo-alto-warns-of-zero-day-bug-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/palo-alto-warns-of-zero-day-bug-in.html?utm_source=dlvr.it&utm_medium=blogger
Researchers Discover PhoneSpy Malware Spying on South Korean Citizens
An ongoing mobile spyware campaign has been uncovered snooping on South Korean residents using a family of 23 malicious Android apps to siphon sensitive information and gain remote control of the devices. "With more than a thousand South Korean victims, the malicious group behind this invasive campaign has had access to all the data, communications, and services on their devices," Zimperium
https://thehackernews.com/2021/11/researchers-discover-phonespy-malware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/researchers-discover-phonespy-malware.html?utm_source=dlvr.it&utm_medium=blogger
13 New Flaws in Siemens Nucleus TCP/IP Stack Impact Safety-Critical Equipment
As many as 13 security vulnerabilities have been discovered in the Nucleus TCP/IP stack, a software library now maintained by Siemens and used in three billion operational technology and IoT devices that could allow for remote code execution, denial-of-service (DoS), and information leak. Collectively called "NUCLEUS:13," successful attacks abusing the flaws can "result in devices going offline
https://thehackernews.com/2021/11/13-new-flaws-in-siemens-nucleus-tcpip.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/13-new-flaws-in-siemens-nucleus-tcpip.html?utm_source=dlvr.it&utm_medium=blogger
14 New Security Flaws Found in BusyBox Linux Utility for Embedded Devices
Cybersecurity researchers on Tuesday disclosed 14 critical vulnerabilities in the BusyBox Linux utility that could be exploited to result in a denial-of-service (DoS) condition and, in select cases, even lead to information leaks and remote code execution. The security weaknesses, tracked from CVE-2021-42373 through CVE-2021-42386, affect multiple versions of the tool ranging from 1.16-1.33.1,
https://thehackernews.com/2021/11/14-new-security-flaws-found-in-busybox.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/11/14-new-security-flaws-found-in-busybox.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, November 11, 2021
Trojan Source – A new method Let Hackers inject vulnerabilities into the source code
A new type of vulnerability has been identified by the security researchers of Cambridge University, Nicholas Boucher and Ross Anderson, and this vulnerability enables threat actors to insert visually deceptive malware into the source code in such a way that is semantically correct. Not only this, but at the same time, this vulnerability also modifies […]
The post Trojan Source – A new method Let Hackers inject vulnerabilities into the source code appeared first on Cyber Security News.
https://cybersecuritynews.com/trojan-source/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/trojan-source/?utm_source=dlvr.it&utm_medium=blogger
The Increasing Need for Application Security During Covid-19
The Covid-19 pandemic shook businesses all over the world, unleashing massive disruption on the global economy. Trying to develop responses to the crisis almost overnight, many businesses were left exposed and vulnerable in terms of application security, and cybercriminals began to up their game with the massive increase of people working from home. According to a recent survey […]
The post The Increasing Need for Application Security During Covid-19 appeared first on Cyber Security News.
https://cybersecuritynews.com/application-security-during-covid-19/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/application-security-during-covid-19/?utm_source=dlvr.it&utm_medium=blogger
How to Keep Your Customer Relationship Management Software Secure
Having great customer relationship managementsoftware is absolutely essential if you are a business that is looking to plan and execute a successful marketing plan. Nonetheless, when you have so much information regarding your customers’ personal data, the difficulty can be keeping it secure. This is especially true when it comes to the rise of hackers, […]
The post How to Keep Your Customer Relationship Management Software Secure appeared first on Cyber Security News.
https://cybersecuritynews.com/how-to-keep-your-customer-relationship-management-software-secure/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/how-to-keep-your-customer-relationship-management-software-secure/?utm_source=dlvr.it&utm_medium=blogger
Hackers Attacking Windows Using Infostealer Malware by Mimics as Legitimate Win 10 App
A new malicious campaign has been detected recently by Rapid7’s Managed Detection and Response (MDR) team and Threat Intelligence and Detection Engineering (TIDE) team in which the hackers are targeting Windows using infostealer malware and delivering fake legitimate-looking Win 10 app. In this malicious campaign, the threat actors infect the users’ systems by using a […]
The post Hackers Attacking Windows Using Infostealer Malware by Mimics as Legitimate Win 10 App appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-attacking-windows-using-infostealer-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-attacking-windows-using-infostealer-malware/?utm_source=dlvr.it&utm_medium=blogger
How Can Small Businesses Protect Against Cyber Threats?
In the modern era of working from home and agile workplaces, cyber threats are becoming more dangerous to business continuity than physical threats such as vandalism and theft. However, whilst it may seem difficult to avoid cyber threats, there are some steps you can take to stay safe in the digital landscape. Read on to […]
The post How Can Small Businesses Protect Against Cyber Threats? appeared first on Cyber Security News.
https://cybersecuritynews.com/how-can-small-businesses-protect-against-cyber-threats/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/how-can-small-businesses-protect-against-cyber-threats/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)