Software-as-a-service (SaaS) applications have gone from novelty to business necessity in a few short years, and its positive impact on organizations is clear. It’s safe to say that most industries today run on SaaS applications, which is undoubtedly positive, but it does introduce some critical new challenges to organizations. As SaaS application use expands, as well as the number of
https://thehackernews.com/2021/10/product-overview-cynet-saas-security.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, October 21, 2021
Malicious NPM Packages Caught Running Cryptominer On Windows, Linux, macOS Devices
Three JavaScript libraries uploaded to the official NPM package repository have been unmasked as crypto-mining malware, once again demonstrating how open-source software package repositories are becoming a lucrative target for executing an array of attacks on Windows, macOS, and Linux systems. The malicious packages in question — named okhsa, klow, and klown — were published by the same
https://thehackernews.com/2021/10/malicious-npm-packages-caught-running.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/malicious-npm-packages-caught-running.html?utm_source=dlvr.it&utm_medium=blogger
U.S. Government Bans Sale of Hacking Tools to Authoritarian Regimes
The U.S. Commerce Department on Wednesday announced new rules barring the sales of hacking software and equipment to authoritarian regimes and potentially facilitate human rights abuse for national security (NS) and anti-terrorism (AT) reasons. The mandate, which is set to go into effect in 90 days, will forbid the export, reexport and transfer of "cybersecurity items" to countries of "national
https://thehackernews.com/2021/10/us-government-bans-sale-of-hacking.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/us-government-bans-sale-of-hacking.html?utm_source=dlvr.it&utm_medium=blogger
Hackers Stealing Browser Cookies to Hijack High-Profile YouTube Accounts
Since at least late 2019, a network of hackers-for-hire have been hijacking the channels of YouTube creators, luring them with bogus collaboration opportunities to broadcast cryptocurrency scams or sell the accounts to the highest bidder. That's according to a new report published by Google's Threat Analysis Group (TAG), which said it disrupted financially motivated phishing campaigns targeting
https://thehackernews.com/2021/10/hackers-stealing-browser-cookies-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/hackers-stealing-browser-cookies-to.html?utm_source=dlvr.it&utm_medium=blogger
Two Eastern Europeans Sentenced for Providing Bulletproof Hosting to Cyber Criminals
Two Eastern European nationals have been sentenced in the U.S. for offering "bulletproof hosting" services to cybercriminals, who used the technical infrastructure to distribute malware and attack financial institutions across the country between 2009 to 2015. Pavel Stassi, 30, of Estonia, and Aleksandr Shorodumov, 33, of Lithuania, have been each sentenced to 24 months and 48 months in prison,
https://thehackernews.com/2021/10/two-eastern-europeans-sentenced-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/two-eastern-europeans-sentenced-for.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, October 20, 2021
Apple Releases New Big Sur and Catalina Safari 15.1 Betas for Developers With Restored Tab Design
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Following in the footsteps of the macOS Monterey release candidate seeded earlier this week, Apple has released a fourth beta version of Safari 15.1 for macOS…
Read more → The post Apple Releases New Big Sur and Catalina Safari 15.1 Betas for Developers With Restored Tab Design first appeared on IT Security News.
https://www.itsecuritynews.info/apple-releases-new-big-sur-and-catalina-safari-15-1-betas-for-developers-with-restored-tab-design/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-releases-new-big-sur-and-catalina-safari-15-1-betas-for-developers-with-restored-tab-design/?utm_source=dlvr.it&utm_medium=blogger
Aruba CX 10000 Series Switch delivers security services for enterprise data centers
This article has been indexed from Help Net Security Aruba introduced the Distributed Services Switch enabling enterprises to deploy software-defined stateful services where data is created and processed, eliminating legacy appliances and host software needed to build the hybrid clouds…
Read more → The post Aruba CX 10000 Series Switch delivers security services for enterprise data centers first appeared on IT Security News.
https://www.itsecuritynews.info/aruba-cx-10000-series-switch-delivers-security-services-for-enterprise-data-centers/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/aruba-cx-10000-series-switch-delivers-security-services-for-enterprise-data-centers/?utm_source=dlvr.it&utm_medium=blogger
Sierra Wireless offers its customers 5G cellular wireless connectivity for their business-critical apps
This article has been indexed from Help Net Security Sierra Wireless launched its 5G managed network service in the United States, offering customers the speed and ultra-low latency of 5G cellular wireless connectivity for their business-critical applications. Sierra Wireless’ fully…
Read more → The post Sierra Wireless offers its customers 5G cellular wireless connectivity for their business-critical apps first appeared on IT Security News.
https://www.itsecuritynews.info/sierra-wireless-offers-its-customers-5g-cellular-wireless-connectivity-for-their-business-critical-apps/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/sierra-wireless-offers-its-customers-5g-cellular-wireless-connectivity-for-their-business-critical-apps/?utm_source=dlvr.it&utm_medium=blogger
2021-10-20 – Files for an ISC diary (Stolen Images Evidence –> Sliver)
This article has been indexed from Malware-Traffic-Analysis.net – Blog Entries This post doesn’t have text content, please click on the link below to view the original article. Read the original article: 2021-10-20 – Files for an ISC diary (Stolen Images…
Read more → The post 2021-10-20 – Files for an ISC diary (Stolen Images Evidence –> Sliver) first appeared on IT Security News.
https://www.itsecuritynews.info/2021-10-20-files-for-an-isc-diary-stolen-images-evidence-sliver/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/2021-10-20-files-for-an-isc-diary-stolen-images-evidence-sliver/?utm_source=dlvr.it&utm_medium=blogger
AppleCare+ for New 16-Inch MacBook Pro Costs $399
This article has been indexed from MacRumors: Mac News and Rumors – Front Page AppleCare+ for the new 16-inch MacBook Pro is priced at $399, which is a $20 increase over the cost of AppleCare for the prior-generation 16-inch model.…
Read more → The post AppleCare+ for New 16-Inch MacBook Pro Costs $399 first appeared on IT Security News.
https://www.itsecuritynews.info/applecare-for-new-16-inch-macbook-pro-costs-399/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/applecare-for-new-16-inch-macbook-pro-costs-399/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, October 19, 2021
Checkmarx Application Security Platform allows CISOs to address the growing security challenges
This article has been indexed from Help Net Security Checkmarx launched the Checkmarx Application Security Platform to help CISOs, AppSec teams, and developers address the growing and dynamic security challenges they face. With groundbreaking capabilities, the platform integrates into any…
Read more → The post Checkmarx Application Security Platform allows CISOs to address the growing security challenges first appeared on IT Security News.
https://www.itsecuritynews.info/checkmarx-application-security-platform-allows-cisos-to-address-the-growing-security-challenges/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/checkmarx-application-security-platform-allows-cisos-to-address-the-growing-security-challenges/?utm_source=dlvr.it&utm_medium=blogger
SecLytics Augur pXDR reduces risk while streamlining SOC operations
This article has been indexed from Help Net Security SecLytics unveils its Augur pXDR (Predictive Extended Detection and Response Platform). Building off SecLytics’ patented Augur predictive intelligence technology, Augur pXDR adds core TIP, SIEM, and SOAR functionalities to create a…
Read more → The post SecLytics Augur pXDR reduces risk while streamlining SOC operations first appeared on IT Security News.
https://www.itsecuritynews.info/seclytics-augur-pxdr-reduces-risk-while-streamlining-soc-operations/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/seclytics-augur-pxdr-reduces-risk-while-streamlining-soc-operations/?utm_source=dlvr.it&utm_medium=blogger
ZeroFox Physical Security Intelligence provides real-time situational awareness for security teams
This article has been indexed from Help Net Security ZeroFox announces a new Physical Security Intelligence solution, delivering visibility and intelligence on supply chain disruption, major events and public safety incidents that may impact worksites, locations, employees, customers and the…
Read more → The post ZeroFox Physical Security Intelligence provides real-time situational awareness for security teams first appeared on IT Security News.
https://www.itsecuritynews.info/zerofox-physical-security-intelligence-provides-real-time-situational-awareness-for-security-teams/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/zerofox-physical-security-intelligence-provides-real-time-situational-awareness-for-security-teams/?utm_source=dlvr.it&utm_medium=blogger
A recipe for failure: Predictably poor passwords
This article has been indexed from WeLiveSecurity Security professionals advise to never use ‘beef stew’ as a password. It just isn’t stroganoff. The post A recipe for failure: Predictably poor passwords appeared first on WeLiveSecurity Read the original article: A…
Read more → The post A recipe for failure: Predictably poor passwords first appeared on IT Security News.
https://www.itsecuritynews.info/a-recipe-for-failure-predictably-poor-passwords/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/a-recipe-for-failure-predictably-poor-passwords/?utm_source=dlvr.it&utm_medium=blogger
$5.2 billion worth of Bitcoin transactions possibly tied to ransomware
This article has been indexed from WeLiveSecurity Threat actors are increasingly using advanced tactics to obfuscate and launder their illicit gains, a report by the US Government finds The post $5.2 billion worth of Bitcoin transactions possibly tied to ransomware…
Read more → The post $5.2 billion worth of Bitcoin transactions possibly tied to ransomware first appeared on IT Security News.
https://www.itsecuritynews.info/5-2-billion-worth-of-bitcoin-transactions-possibly-tied-to-ransomware/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/5-2-billion-worth-of-bitcoin-transactions-possibly-tied-to-ransomware/?utm_source=dlvr.it&utm_medium=blogger
Monday, October 18, 2021
ManageEngine adds anti-ransomware capabilities to its UEM solution to combat evolving cyberthreats
This article has been indexed from Help Net Security ManageEngine announced the addition of data loss prevention for endpoints, anti-ransomware and endpoint compliance capabilities to its unified endpoint management (UEM) solution, Desktop Central. Since the prevalent adoption of remote work,…
Read more → The post ManageEngine adds anti-ransomware capabilities to its UEM solution to combat evolving cyberthreats first appeared on IT Security News.
https://www.itsecuritynews.info/manageengine-adds-anti-ransomware-capabilities-to-its-uem-solution-to-combat-evolving-cyberthreats/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/manageengine-adds-anti-ransomware-capabilities-to-its-uem-solution-to-combat-evolving-cyberthreats/?utm_source=dlvr.it&utm_medium=blogger
SecurID Governance and Lifecycle Cloud helps organizations secure the hybrid workforce
This article has been indexed from Help Net Security SecurID announced innovations that empower security-sensitive organizations to work dynamically, accelerate their cloud journeys and advance zero-trust security with the launch of SecurID Governance and Lifecycle (G&L) Cloud. Businesses everywhere are…
Read more → The post SecurID Governance and Lifecycle Cloud helps organizations secure the hybrid workforce first appeared on IT Security News.
https://www.itsecuritynews.info/securid-governance-and-lifecycle-cloud-helps-organizations-secure-the-hybrid-workforce/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/securid-governance-and-lifecycle-cloud-helps-organizations-secure-the-hybrid-workforce/?utm_source=dlvr.it&utm_medium=blogger
macOS Monterey and iPadOS 15.1 Release Candidates Limit Safari Color Tab Bar Option to Compact View
This article has been indexed from MacRumors: Mac News and Rumors – Front Page With the macOS Monterey and iPadOS 15 release candidates that were seeded to developers today, Apple has eliminated the option to use the Color Tab Bar…
Read more → The post macOS Monterey and iPadOS 15.1 Release Candidates Limit Safari Color Tab Bar Option to Compact View first appeared on IT Security News.
https://www.itsecuritynews.info/macos-monterey-and-ipados-15-1-release-candidates-limit-safari-color-tab-bar-option-to-compact-view/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/macos-monterey-and-ipados-15-1-release-candidates-limit-safari-color-tab-bar-option-to-compact-view/?utm_source=dlvr.it&utm_medium=blogger
New MacBook Pros Feature 3.5mm Headphone Jack With Advanced Support for High-Impedance Headphones, Six-Speaker Sound System
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Apple’s new MacBook Pro models are equipped with the “best audio system in a notebook,” according to Apple, with upgrades to the headphone jack and the…
Read more → The post New MacBook Pros Feature 3.5mm Headphone Jack With Advanced Support for High-Impedance Headphones, Six-Speaker Sound System first appeared on IT Security News.
https://www.itsecuritynews.info/new-macbook-pros-feature-3-5mm-headphone-jack-with-advanced-support-for-high-impedance-headphones-six-speaker-sound-system/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/new-macbook-pros-feature-3-5mm-headphone-jack-with-advanced-support-for-high-impedance-headphones-six-speaker-sound-system/?utm_source=dlvr.it&utm_medium=blogger
New MacBook Pro Keyboard Has All-Black Design, Full-Size Function Keys, and Touch ID Ring
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Apple’s new MacBook Pro models unveiled today feature a redesigned keyboard with an all-black design, a row of full-size function keys, and a Touch ID ring…
Read more → The post New MacBook Pro Keyboard Has All-Black Design, Full-Size Function Keys, and Touch ID Ring first appeared on IT Security News.
https://www.itsecuritynews.info/new-macbook-pro-keyboard-has-all-black-design-full-size-function-keys-and-touch-id-ring/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/new-macbook-pro-keyboard-has-all-black-design-full-size-function-keys-and-touch-id-ring/?utm_source=dlvr.it&utm_medium=blogger
Sunday, October 17, 2021
IT Security News Daily Summary 2021-10-17
Application Modernization and Other Best Practices of Securing Legacy Infrastructures Is the Edge Really Secure? Cloud security is an ongoing struggle to keep sensitive data safe. Is it getting any easier? Microsoft October Patch Tuesday Addresses 4 Zero-Day Vulnerabilities MacBook…
Read more → The post IT Security News Daily Summary 2021-10-17 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-10-17/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-10-17/?utm_source=dlvr.it&utm_medium=blogger
Application Modernization and Other Best Practices of Securing Legacy Infrastructures
This article has been indexed from Cyber Defense Magazine By Roman Davydov, Technology Observer, Itransition Legacy systems continue to play a vital role in the operations of […] The post Application Modernization and Other Best Practices of Securing Legacy Infrastructures…
Read more → The post Application Modernization and Other Best Practices of Securing Legacy Infrastructures first appeared on IT Security News.
https://www.itsecuritynews.info/application-modernization-and-other-best-practices-of-securing-legacy-infrastructures/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/application-modernization-and-other-best-practices-of-securing-legacy-infrastructures/?utm_source=dlvr.it&utm_medium=blogger
Is the Edge Really Secure?
This article has been indexed from Cyber Defense Magazine By Chetan Venkatesh, CEO and Co-Founder of Macrometa The simplest answer is… No. But, if history has taught […] The post Is the Edge Really Secure? appeared first on Cyber Defense…
Read more → The post Is the Edge Really Secure? first appeared on IT Security News.
https://www.itsecuritynews.info/is-the-edge-really-secure/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/is-the-edge-really-secure/?utm_source=dlvr.it&utm_medium=blogger
Cloud security is an ongoing struggle to keep sensitive data safe. Is it getting any easier?
This article has been indexed from HackRead By Owais Sultan The latest cloud security breaches show that we have miles to go as we keep fighting to keep our sensitive data safe. This is a post from HackRead.com Read the…
Read more → The post Cloud security is an ongoing struggle to keep sensitive data safe. Is it getting any easier? first appeared on IT Security News.
https://www.itsecuritynews.info/cloud-security-is-an-ongoing-struggle-to-keep-sensitive-data-safe-is-it-getting-any-easier/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cloud-security-is-an-ongoing-struggle-to-keep-sensitive-data-safe-is-it-getting-any-easier/?utm_source=dlvr.it&utm_medium=blogger
Google Tracking 270 Government-backed Hacker Groups From Over 50 Countries
Google’s Threat Analysis Group (TAG) has tracked more than 270 government-backed cybercriminal associations in over 50 countries. From the beginning of 2021, they have noted that the attack rate of phishing campaigns is increasing and that’s why they have clients with about 50,000 alerts regarding phishing attempts or malware installations. Soon after detecting such attacks, […]
The post Google Tracking 270 Government-backed Hacker Groups From Over 50 Countries appeared first on Cyber Security News.
https://cybersecuritynews.com/google-tracking-270-government-backed-hacker-groups/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/google-tracking-270-government-backed-hacker-groups/?utm_source=dlvr.it&utm_medium=blogger
Saturday, October 16, 2021
Data Governance Trends Report Reveals Securing Customer Data is Top IT Priority, Content Sprawl is Major Concern
This article has been indexed from Cybersecurity Insiders Companies are struggling with how to get a handle on the vast amounts of unstructured data they generate, and this is going to continue as the new hybrid work model proceeds into…
Read more → The post Data Governance Trends Report Reveals Securing Customer Data is Top IT Priority, Content Sprawl is Major Concern first appeared on IT Security News.
https://www.itsecuritynews.info/data-governance-trends-report-reveals-securing-customer-data-is-top-it-priority-content-sprawl-is-major-concern/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/data-governance-trends-report-reveals-securing-customer-data-is-top-it-priority-content-sprawl-is-major-concern/?utm_source=dlvr.it&utm_medium=blogger
The Importance of Correctly Scoping Your Information Systems
This article has been indexed from Cybersecurity Insiders The decision to authorize (or not) an information system to operate within an organization is the result of an on-going project that needs to be dealt effectively to be successful and prevent…
Read more → The post The Importance of Correctly Scoping Your Information Systems first appeared on IT Security News.
https://www.itsecuritynews.info/the-importance-of-correctly-scoping-your-information-systems-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-importance-of-correctly-scoping-your-information-systems-2/?utm_source=dlvr.it&utm_medium=blogger
Securing the edge with Zero Trust
This article has been indexed from Cybersecurity Insiders The proliferation of cloud computing, mobile device use, and the Internet of Things has dissolved traditional network boundaries. Today, the network perimeter has evolved as workloads have moved to the cloud while…
Read more → The post Securing the edge with Zero Trust first appeared on IT Security News.
https://www.itsecuritynews.info/securing-the-edge-with-zero-trust-3/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/securing-the-edge-with-zero-trust-3/?utm_source=dlvr.it&utm_medium=blogger
Russia-Linked TA505 targets financial institutions in a new malspam campaign
This article has been indexed from Security Affairs Russia-linked TA505 group leverages a lightweight Office file to spread malware in a campaign, tracked as MirrorBlast, aimed at financial institutions. Russia-linked APT group TA505 (e.g. Evil Corp) is leveraging a lightweight…
Read more → The post Russia-Linked TA505 targets financial institutions in a new malspam campaign first appeared on IT Security News.
https://www.itsecuritynews.info/russia-linked-ta505-targets-financial-institutions-in-a-new-malspam-campaign/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/russia-linked-ta505-targets-financial-institutions-in-a-new-malspam-campaign/?utm_source=dlvr.it&utm_medium=blogger
Whatsapp Announces End-to-End Backup to Protect 100 billion users Every day
The CEO of Facebook Mark Zuckerberg has recently announced on Thursday that WhatsApp will start rolling out the end-to-end encrypted chat backups for iOS and Android users globally. This end-to-end encryption has put a lot of importance on security, and that’s why it is one of the USPs of the app. It’s was being stated […]
The post Whatsapp Announces End-to-End Backup to Protect 100 billion users Every day appeared first on Cyber Security News.
https://cybersecuritynews.com/whatsapp-announces-end-to-end-backup/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/whatsapp-announces-end-to-end-backup/?utm_source=dlvr.it&utm_medium=blogger
Friday, October 15, 2021
China’s Hackers Crack Devices at Tianfu Cup for $1.5M in Prizes
This article has been indexed from Dark Reading China’s premier hackers will target web browsers, operating systems, mobile devices, and even a car at Tianfu Cup. Read the original article: China’s Hackers Crack Devices at Tianfu Cup for $1.5M in…
Read more → The post China’s Hackers Crack Devices at Tianfu Cup for $1.5M in Prizes first appeared on IT Security News.
https://www.itsecuritynews.info/chinas-hackers-crack-devices-at-tianfu-cup-for-1-5m-in-prizes/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/chinas-hackers-crack-devices-at-tianfu-cup-for-1-5m-in-prizes/?utm_source=dlvr.it&utm_medium=blogger
Weekly Update 265
This article has been indexed from Troy Hunt’s Blog Presently sponsored by: Axonius provides an always up-to-date asset inventory, helping IT and security uncover gaps and automate action. Learn more and try it free. I had a bunch of false…
Read more → The post Weekly Update 265 first appeared on IT Security News.
https://www.itsecuritynews.info/weekly-update-265/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/weekly-update-265/?utm_source=dlvr.it&utm_medium=blogger
Attackers Behind Trickbot Expanding Malware Distribution Channels
The operators behind the pernicious TrickBot malware have resurfaced with new tricks that aim to increase its foothold by expanding its distribution channels, ultimately leading to the deployment of ransomware such as Conti. The threat actor, tracked under the monikers ITG23 and Wizard Spider, has been found to partner with other cybercrime gangs known Hive0105, Hive0106 (aka TA551 or Shathak),
https://thehackernews.com/2021/10/attackers-behind-trickbot-expanding.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/attackers-behind-trickbot-expanding.html?utm_source=dlvr.it&utm_medium=blogger
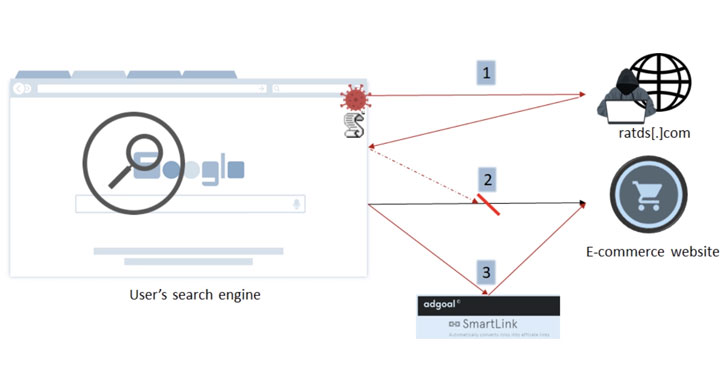
Ad-Blocking Chrome Extension Caught Injecting Ads in Google Search Pages
A new deceptive ad injection campaign has been found leveraging an ad blocker extension for Google Chrome and Opera web browsers to sneakily insert ads and affiliate codes on websites, according to new research from cybersecurity firm Imperva. The findings come following the discovery of rogue domains distributing an ad injection script in late August 2021 that the researchers connected to an
https://thehackernews.com/2021/10/ad-blocking-chrome-extension-caught.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/ad-blocking-chrome-extension-caught.html?utm_source=dlvr.it&utm_medium=blogger
CISA Issues Warning On Cyber Threats Targeting Water and Wastewater Systems
The U.S. Cybersecurity Infrastructure and Security Agency (CISA) on Thursday warned of continued ransomware attacks aimed at disrupting water and wastewater facilities (WWS), highlighting five incidents that occurred between March 2019 and August 2021. "This activity—which includes attempts to compromise system integrity via unauthorized access—threatens the ability of WWS facilities to provide
https://thehackernews.com/2021/10/cisa-issues-warning-on-cyber-threats.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/cisa-issues-warning-on-cyber-threats.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, October 14, 2021
The Ultimate SaaS Security Posture Management (SSPM) Checklist
Cloud security is the umbrella that holds within it: IaaS, PaaS and SaaS. Gartner created the SaaS Security Posture Management (SSPM) category for solutions that continuously assess security risk and manage the SaaS applications’ security posture. With enterprises having 1,000 or more employees relying on dozens to hundreds of apps, the need for deep visibility and remediation for SaaS security
https://thehackernews.com/2021/10/the-ultimate-saas-security-posture.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/the-ultimate-saas-security-posture.html?utm_source=dlvr.it&utm_medium=blogger
Google: We're Tracking 270 State-Sponsored Hacker Groups From Over 50 Countries
Google's Threat Analysis Group (TAG) on Thursday said it's tracking more than 270 government-backed threat actors from more than 50 countries, adding it has approximately sent 50,000 alerts of state-sponsored phishing or malware attempts to customers since the start of 2021. The warnings mark a 33% increase from 2020, the internet giant said, with the spike largely stemming from "blocking an
https://thehackernews.com/2021/10/google-were-tracking-270-state.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/google-were-tracking-270-state.html?utm_source=dlvr.it&utm_medium=blogger
Critical Remote Hacking Flaws Disclosed in Linphone and MicroSIP Softphones
Multiple security vulnerabilities have been disclosed in softphone software from Linphone and MicroSIP that could be exploited by an unauthenticated remote adversary to crash the client and even extract sensitive information like password hashes by simply making a malicious call. The vulnerabilities, which were discovered by Moritz Abrell of German pen-testing firm SySS GmbH, have since been
https://thehackernews.com/2021/10/critical-remote-hacking-flaws-disclosed.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/critical-remote-hacking-flaws-disclosed.html?utm_source=dlvr.it&utm_medium=blogger
VirusTotal Releases Ransomware Report Based on Analysis of 80 Million Samples
As many as 130 different ransomware families have been found to be active in 2020 and the first half of 2021, with Israel, South Korea, Vietnam, China, Singapore, India, Kazakhstan, Philippines, Iran, and the U.K. emerging as the most affected territories, a comprehensive analysis of 80 million ransomware-related samples has revealed. Google's cybersecurity arm VirusTotal attributed a
https://thehackernews.com/2021/10/virustotal-releases-ransomware-report.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/virustotal-releases-ransomware-report.html?utm_source=dlvr.it&utm_medium=blogger
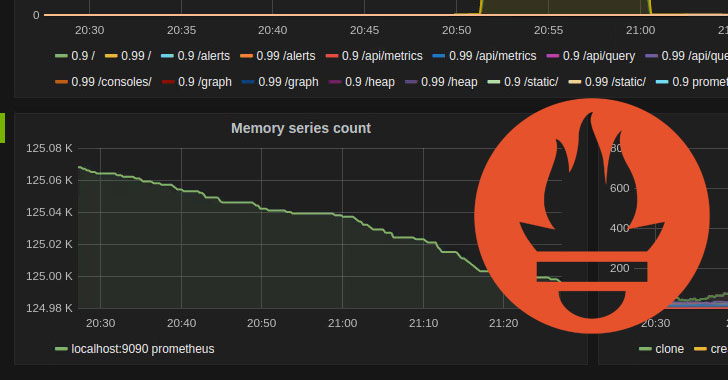
Experts Warn of Unprotected Prometheus Endpoints Exposing Sensitive Information
A large-scale unauthenticated scraping of publicly available and non-secured endpoints from older versions of Prometheus event monitoring and alerting solution could be leveraged to inadvertently leak sensitive information, according to the latest research. "Due to the fact that authentication and encryption support is relatively new, many organizations that use Prometheus haven't yet enabled
https://thehackernews.com/2021/10/experts-warn-of-unprotected-prometheus.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/experts-warn-of-unprotected-prometheus.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, October 13, 2021
Microsoft Hit with 2.4 Tbps DDoS Attack – 2nd Largest Attack Ever Recorded
Microsoft recently proclaimed that they have witnessed a 2.4 Tbps DDoS attack in August this year, and it’s the largest attack ever recorded till now. Since the early one was recorded with a volume of 2.3 Tbps, which was already mitigated by AWS. This huge attack was targeted on Microsoft Azure clients in Europe and […]
The post Microsoft Hit with 2.4 Tbps DDoS Attack – 2nd Largest Attack Ever Recorded appeared first on Cyber Security News.
https://cybersecuritynews.com/microsoft-hit-with-2-4-tbps-ddos-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/microsoft-hit-with-2-4-tbps-ddos-attack/?utm_source=dlvr.it&utm_medium=blogger
Indian Made Spyware That Linked With Notorious Hacker Group Attacking Activist
Researchers from Amnesty International have uncovered a new wave of spyware that is believed to be developed from an India-based cybersecurity company and utilized by the notorious hacker group to target human rights activists in Tago. The threat group is known as Donot Team that was connected to various attacks in south Asia, now linked […]
The post Indian Made Spyware That Linked With Notorious Hacker Group Attacking Activist appeared first on Cyber Security News.
https://cybersecuritynews.com/indian-made-spyware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/indian-made-spyware/?utm_source=dlvr.it&utm_medium=blogger
Critical Flaw in OpenSea Could Have Let Hackers Steal Cryptocurrency From Wallets
A now-patched critical vulnerability in OpenSea, the world's largest non-fungible token (NFT) marketplace, could've been abused by malicious actors to drain cryptocurrency funds from a victim by sending a specially-crafted token, opening a new attack vector for exploitation. The findings come from cybersecurity firm Check Point Research, which began an investigation into the platform following
https://thehackernews.com/2021/10/critical-flaw-in-opensea-could-have-let.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/critical-flaw-in-opensea-could-have-let.html?utm_source=dlvr.it&utm_medium=blogger
[eBook] The Guide for Reducing SaaS Applications Risk for Lean IT Security Teams
The Software-as-a-service (SaaS) industry has gone from novelty to an integral part of today’s business world in just a few years. While the benefits to most organizations are clear – more efficiency, greater productivity, and accessibility – the risks that the SaaS model poses are starting to become visible. It’s not an overstatement to say that most companies today run on SaaS. This poses an
https://thehackernews.com/2021/10/ebook-guide-for-reducing-saas.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/ebook-guide-for-reducing-saas.html?utm_source=dlvr.it&utm_medium=blogger
Update Your Windows PCs Immediately to Patch New 0-Day Under Active Attack
Microsoft on Tuesday rolled out security patches to contain a total of 71 vulnerabilities in Microsoft Windows and other software, including a fix for an actively exploited privilege escalation vulnerability that could be exploited in conjunction with remote code execution bugs to take control over vulnerable systems. Two of the addressed security flaws are rated Critical, 68 are rated Important
https://thehackernews.com/2021/10/update-your-windows-pcs-immediately-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/update-your-windows-pcs-immediately-to.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, October 12, 2021
GitHub Revoked Insecure SSH Keys Generated by a Popular git Client
Code hosting platform GitHub has revoked weak SSH authentication keys that were generated via the GitKraken git GUI client due to a vulnerability in a third-party library that increased the likelihood of duplicated SSH keys. As an added precautionary measure, the Microsoft-owned company also said it's building safeguards to prevent vulnerable versions of GitKraken from adding newly generated
https://thehackernews.com/2021/10/github-revoked-insecure-ssh-keys.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/github-revoked-insecure-ssh-keys.html?utm_source=dlvr.it&utm_medium=blogger
Microsoft Fended Off a Record 2.4 Tbps DDoS Attack Targeting Azure Customers
Microsoft on Monday revealed that its Azure cloud platform mitigated a 2.4 Tbps distributed denial-of-service (DDoS) attack in the last week of August targeting an unnamed customer in Europe, surpassing a 2.3 Tbps attack stopped by Amazon Web Services in February 2020. "This is 140 percent higher than 2020's 1 Tbps attack and higher than any network volumetric event previously detected on Azure,
https://thehackernews.com/2021/10/microsoft-fended-off-record-24-tbps.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/microsoft-fended-off-record-24-tbps.html?utm_source=dlvr.it&utm_medium=blogger
Microsoft Warns of Iran-Linked Hackers Targeting US and Israeli Defense Firms
An emerging threat actor likely supporting Iranian national interests has been behind a password spraying campaign targeting US, EU, and Israeli defense technology companies, with additional activity observed against regional ports of entry in the Persian Gulf as well as maritime and cargo transportation companies focused in the Middle East. Microsoft is tracking the hacking crew under the
https://thehackernews.com/2021/10/microsoft-warns-of-iran-linked-hackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/microsoft-warns-of-iran-linked-hackers.html?utm_source=dlvr.it&utm_medium=blogger
Ukraine Arrests Operator of DDoS Botnet with 100,000 Compromised Devices
Ukrainian law enforcement authorities on Monday disclosed the arrest of a hacker responsible for the creation and management of a "powerful botnet" consisting of over 100,000 enslaved devices that was used to carry out distributed denial-of-service (DDoS) and spam attacks on behalf of paid customers. The unnamed individual, from the Ivano-Frankivsk region of the country, is also said to have
https://thehackernews.com/2021/10/ukraine-arrests-operator-of-ddos-botnet.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/ukraine-arrests-operator-of-ddos-botnet.html?utm_source=dlvr.it&utm_medium=blogger
Verify End-Users at the Helpdesk to Prevent Social Engineering Cyber Attack
Although organizations commonly go to great lengths to address security vulnerabilities that may exist within their IT infrastructure, an organization's helpdesk might pose a bigger threat due to social engineering attacks. Social engineering is "the art of manipulating people so they give up confidential information," according to Webroot. There are many different types of social engineering
https://thehackernews.com/2021/10/verify-end-users-at-helpdesk-to-prevent.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/10/verify-end-users-at-helpdesk-to-prevent.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)