This article has been indexed from The Register – Security Boffins devise wireless tricks to dupe iPhone digital wallets into paying out arbitrary amounts when in transit mode Apple’s digital wallet Apple Pay will pay whatever amount is demanded of…
Read more → The post Revealed: How to make fraudulent contactless Apple Pay payments with Visa first appeared on IT Security News.
https://www.itsecuritynews.info/revealed-how-to-make-fraudulent-contactless-apple-pay-payments-with-visa/?utm_source=dlvr.it&utm_medium=blogger
Thursday, September 30, 2021
iPhone 13 Models Still Include EarPods in the Box in France
This article has been indexed from MacRumors: Mac News and Rumors – Front Page All four iPhone 13 models still ship with EarPods in the box in France due to a law in the country that requires all smartphones to…
Read more → The post iPhone 13 Models Still Include EarPods in the Box in France first appeared on IT Security News.
https://www.itsecuritynews.info/iphone-13-models-still-include-earpods-in-the-box-in-france/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/iphone-13-models-still-include-earpods-in-the-box-in-france/?utm_source=dlvr.it&utm_medium=blogger
How to Prevent Ransomware in the Cloud Environment
Cloud services have seen a 630% rise in cyber-attacks since the beginning of 2020. This comes as no surprise since many businesses turned to cloud services to maintain business continuity during the covid-19 pandemic. However, this means that hackers now have many new ways to access valuable information. In this article, we’ll look at how […]
The post How to Prevent Ransomware in the Cloud Environment appeared first on Cyber Security News.
https://cybersecuritynews.com/ransomware-cloud-environment/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/ransomware-cloud-environment/?utm_source=dlvr.it&utm_medium=blogger
GriftHorse – New Android Trojan Steals Millions from Over 10 Million Victims Globally
The mobile security firm Zimperium has recently detected an “aggressive” mobile campaign, that is named “GriftHorse,” and it has affected over 10 million users from nearly 70 countries. The attacks were conducted via innocuous Android apps that support the people to premium services that are costing €36 (~$42) per month. GriftHorse is targetting many users […]
The post GriftHorse – New Android Trojan Steals Millions from Over 10 Million Victims Globally appeared first on Cyber Security News.
https://cybersecuritynews.com/grifthorse-new-android-trojan/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/grifthorse-new-android-trojan/?utm_source=dlvr.it&utm_medium=blogger
Cybersecurity Firm Group-IB's CEO Arrested Over Treason Charges in Russia
Russian authorities on Wednesday arrested and detained Ilya Sachkov, the founder of cybersecurity firm Group-IB, for two months in Moscow on charges of state treason following a search of its office on September 28. The Russian company, which is headquartered in Singapore, confirmed the development but noted the "reason for the search was not yet clear," adding "The decentralized infrastructure
https://thehackernews.com/2021/09/cybersecurity-firm-group-ibs-ceo.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/cybersecurity-firm-group-ibs-ceo.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, September 29, 2021
NETSCOUT and Palo Alto Networks support SOCs in mitigating security threats in hybrid environments
This article has been indexed from Help Net Security NETSCOUT and Palo Alto Networks announced that their fully integrated security solutions are now available to support security operations centers (SOCs) in detecting, analyzing, and mitigating security threats in complex hybrid…
Read more → The post NETSCOUT and Palo Alto Networks support SOCs in mitigating security threats in hybrid environments first appeared on IT Security News.
https://www.itsecuritynews.info/netscout-and-palo-alto-networks-support-socs-in-mitigating-security-threats-in-hybrid-environments/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/netscout-and-palo-alto-networks-support-socs-in-mitigating-security-threats-in-hybrid-environments/?utm_source=dlvr.it&utm_medium=blogger
Report highlights cybersecurity dangers of Elastic Stack implementation mistakes
This article has been indexed from Latest topics for ZDNet in Security Researchers from cybersecurity firm Salt Security discovered widespread mistakes that allowed them to launch attacks where any user could extract sensitive customer and system data. Read the original…
Read more → The post Report highlights cybersecurity dangers of Elastic Stack implementation mistakes first appeared on IT Security News.
https://www.itsecuritynews.info/report-highlights-cybersecurity-dangers-of-elastic-stack-implementation-mistakes/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/report-highlights-cybersecurity-dangers-of-elastic-stack-implementation-mistakes/?utm_source=dlvr.it&utm_medium=blogger
[eBook] Your First 90 Days as CISO — 9 Steps to Success
Chief Information Security Officers (CISOs) are an essential pillar of an organization’s defense, and they must account for a lot. Especially for new CISOs, this can be a daunting task. The first 90 days for a new CISO are crucial in setting up their security team, so there is little time to waste, and much to accomplish. Fortunately. A new guide by XDR provider Cynet (download here) looks to
https://thehackernews.com/2021/09/ebook-your-first-90-days-as-ciso-9.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/ebook-your-first-90-days-as-ciso-9.html?utm_source=dlvr.it&utm_medium=blogger
Hackers Targeting Brazil's PIX Payment System to Drain Users' Bank Accounts
Two newly discovered malicious Android applications on Google Play Store have been used to target users of Brazil's instant payment ecosystem in a likely attempt to lure victims into fraudulently transferring their entire account balances into another bank account under cybercriminals' control. "The attackers distributed two different variants of banking malware, named PixStealer and MalRhino,
https://thehackernews.com/2021/09/hackers-targeting-brazils-pix-payment.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/hackers-targeting-brazils-pix-payment.html?utm_source=dlvr.it&utm_medium=blogger
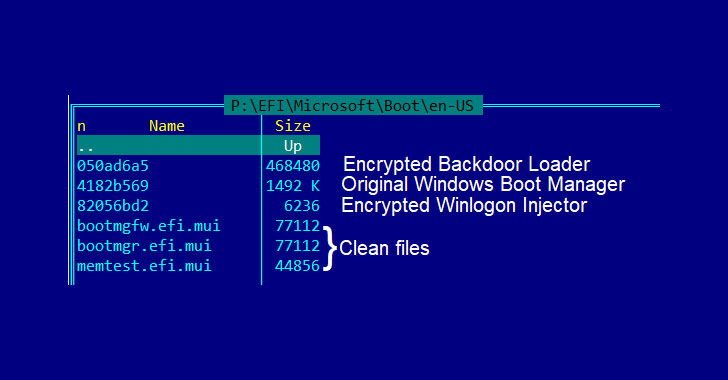
New FinSpy Malware Variant Infects Windows Systems With UEFI Bootkit
Commercially developed FinFisher surveillanceware has been upgraded to infect Windows devices using a UEFI (Unified Extensible Firmware Interface) bootkit using a trojanized Windows Boot Manager, marking a shift in infection vectors that allow it to elude discovery and analysis. Detected in the wild since 2011, FinFisher (aka FinSpy or Wingbird) is a spyware toolset for Windows, macOS, and Linux
https://thehackernews.com/2021/09/new-finspy-malware-variant-infects.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/new-finspy-malware-variant-infects.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, September 28, 2021
In U.S. v Wilson, the Ninth Circuit Reaffirms Fourth Amendment Protection for Electronic Communications
This article has been indexed from Deeplinks In a powerful new ruling for digital privacy rights, the Ninth Circuit Court of Appeals has confirmed that the police need to get a warrant before they open your email attachments—even if a…
Read more → The post In U.S. v Wilson, the Ninth Circuit Reaffirms Fourth Amendment Protection for Electronic Communications first appeared on IT Security News.
https://www.itsecuritynews.info/in-u-s-v-wilson-the-ninth-circuit-reaffirms-fourth-amendment-protection-for-electronic-communications/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/in-u-s-v-wilson-the-ninth-circuit-reaffirms-fourth-amendment-protection-for-electronic-communications/?utm_source=dlvr.it&utm_medium=blogger
Supply Chain Attack: What It Is (and What to Do About It)
This article has been indexed from Security Intelligence The past two years have delivered major disruptions for supply chains. The pandemic pushed supply chain attack issues front-and-center, with disruptions up 67% in 2020 and problems expected to persist as global…
Read more → The post Supply Chain Attack: What It Is (and What to Do About It) first appeared on IT Security News.
https://www.itsecuritynews.info/supply-chain-attack-what-it-is-and-what-to-do-about-it/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/supply-chain-attack-what-it-is-and-what-to-do-about-it/?utm_source=dlvr.it&utm_medium=blogger
Hackers Stealing Data From 378 Banking and Wallet Apps Using New Android Malware
A new mobile banking Trojan called ERMAC has been found recently, and this malware resembles to have been manufactured by cybercriminals at BlackRock, which is based on the roots of the infamous Cerberus. ERMAC is a code successor to a well-known Cerberus malware, and this malware uses almost indistinguishable data structures when communicating with the […]
The post Hackers Stealing Data From 378 Banking and Wallet Apps Using New Android Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-stealing-data-from-378-banking-apps/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-stealing-data-from-378-banking-apps/?utm_source=dlvr.it&utm_medium=blogger
Atlassian Confluence RCE Flaw Abused in Multiple Cyberattack Campaigns
Opportunistic threat actors have been found actively exploiting a recently disclosed critical security flaw in Atlassian Confluence deployments across Windows and Linux to deploy web shells that result in the execution of crypto miners on compromised systems. Tracked as CVE-2021-26084 (CVSS score: 9.8), the vulnerability concerns an OGNL (Object-Graph Navigation Language) injection flaw that
https://thehackernews.com/2021/09/atlassian-confluence-rce-flaw-abused-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/atlassian-confluence-rce-flaw-abused-in.html?utm_source=dlvr.it&utm_medium=blogger
Russia-linked Nobelium APT group uses custom backdoor to target Windows domains
This article has been indexed from Security Affairs Microsoft discovered new custom malware, dubbed FoggyWeb, used by the Nobelium cyberespionage group to implant backdoor in Windows domains. Microsoft Threat Intelligence Center (MSTIC) researchers have discovered a new custom malware, dubbed…
Read more → The post Russia-linked Nobelium APT group uses custom backdoor to target Windows domains first appeared on IT Security News.
https://www.itsecuritynews.info/russia-linked-nobelium-apt-group-uses-custom-backdoor-to-target-windows-domains/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/russia-linked-nobelium-apt-group-uses-custom-backdoor-to-target-windows-domains/?utm_source=dlvr.it&utm_medium=blogger
Monday, September 27, 2021
asymmetric cryptography (public key cryptography)
This article has been indexed from SearchSecurity This post doesn’t have text content, please click on the link below to view the original article. Read the original article: asymmetric cryptography (public key cryptography)
Read more → The post asymmetric cryptography (public key cryptography) first appeared on IT Security News.
https://www.itsecuritynews.info/asymmetric-cryptography-public-key-cryptography-3/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/asymmetric-cryptography-public-key-cryptography-3/?utm_source=dlvr.it&utm_medium=blogger
7 Ways to Thwart Malicious Insiders
This article has been indexed from Dark Reading Malicious insider incidents may be less frequent than inadvertent user missteps, but they can cost organizations big time. Read the original article: 7 Ways to Thwart Malicious Insiders
Read more → The post 7 Ways to Thwart Malicious Insiders first appeared on IT Security News.
https://www.itsecuritynews.info/7-ways-to-thwart-malicious-insiders/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/7-ways-to-thwart-malicious-insiders/?utm_source=dlvr.it&utm_medium=blogger
Hackers Have Figured Out a New Malware Evasion Technique to Fly Under The Radar
Google’s THREAT ANALYSIS GROUP has recently discovered a type of malware that exploits a new method to circumvent detection by security products, and this malware easily modifies the digital signature of its files. Neel Mehta one of their security researchers who has detected this malware in the Google Threat Analysis Group has claimed this method […]
The post Hackers Have Figured Out a New Malware Evasion Technique to Fly Under The Radar appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-have-figured-out-a-new-malware-evasion-technique-to-fly-under-the-radar/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-have-figured-out-a-new-malware-evasion-technique-to-fly-under-the-radar/?utm_source=dlvr.it&utm_medium=blogger
Deals: Verizon Offering Up to 30% Off MagSafe Accessory Bundles, iPhone 13 Cases, and More
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Today we’re tracking a handful of solid accessory discounts offered by Verizon, offering a chance to save on a new case or screen protector for your…
Read more → The post Deals: Verizon Offering Up to 30% Off MagSafe Accessory Bundles, iPhone 13 Cases, and More first appeared on IT Security News.
https://www.itsecuritynews.info/deals-verizon-offering-up-to-30-off-magsafe-accessory-bundles-iphone-13-cases-and-more/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/deals-verizon-offering-up-to-30-off-magsafe-accessory-bundles-iphone-13-cases-and-more/?utm_source=dlvr.it&utm_medium=blogger
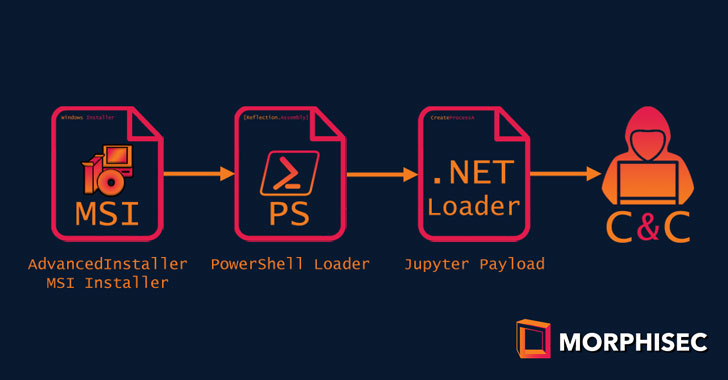
A New Jupyter Malware Version is Being Distributed via MSI Installers
Cybersecurity researchers have charted the evolution of Jupyter, a .NET infostealer known for singling out healthcare and education sectors, which make it exceptional at defeating most endpoint security scanning solutions. The new delivery chain, spotted by Morphisec on September 8, underscores that the malware has not just continued to remain active but also showcases "how threat actors
https://thehackernews.com/2021/09/a-new-jupyter-malware-version-is-being.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/a-new-jupyter-malware-version-is-being.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, September 26, 2021
IT Security News Daily Summary 2021-09-26
Online fraud causes confidence gap between customers and retailers, study finds The Importance of Adopting a Risk Management Approach to Security and Privacy Facebook Shareholders Are Suing Facebook For Protecting Zuckerberg In Data Probe SonicWall Patches Critical Flaw in SMA…
Read more → The post IT Security News Daily Summary 2021-09-26 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-09-26/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-09-26/?utm_source=dlvr.it&utm_medium=blogger
Hackers Discover Technique to Make Malware Undetectable on Windows
This article has been indexed from E Hacking News – Latest Hacker News and IT Security News Investigators within the cybersecurity industry have revealed a unique approach used by a threat actor to purposefully avoid detection using flawed digital…
Read more → The post Hackers Discover Technique to Make Malware Undetectable on Windows first appeared on IT Security News.
https://www.itsecuritynews.info/hackers-discover-technique-to-make-malware-undetectable-on-windows/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hackers-discover-technique-to-make-malware-undetectable-on-windows/?utm_source=dlvr.it&utm_medium=blogger
How to Go Passwordless on Your Microsoft Account
This article has been indexed from Security Latest You no longer need an ungainly string of characters to access your Windows PC or Xbox. Read the original article: How to Go Passwordless on Your Microsoft Account
Read more → The post How to Go Passwordless on Your Microsoft Account first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-go-passwordless-on-your-microsoft-account/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-to-go-passwordless-on-your-microsoft-account/?utm_source=dlvr.it&utm_medium=blogger
How to Protect Your CRM From a Data Breach
Cloud service providers (CSPs) are businesses that provide cloud-based network services, infrastructure, and business applications. These cloud services are housed in a data center and may be accessed through a network connection by CRM (customer relationship management) software businesses or people. Once we have selected a reputable CRM software to handle our customer relationships, safeguarding […]
The post How to Protect Your CRM From a Data Breach appeared first on Cyber Security News.
https://cybersecuritynews.com/how-to-protect-your-crm-from-a-data-breach/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/how-to-protect-your-crm-from-a-data-breach/?utm_source=dlvr.it&utm_medium=blogger
Red Box provides certified compliance recording solution for Microsoft Teams
This article has been indexed from Help Net Security Red Box announces the certification of its compliance recording solution for Microsoft Teams as part of the Microsoft Independent Software Vendor (ISV) Partner Certification Programme. Following extensive third-party approved testing, the…
Read more → The post Red Box provides certified compliance recording solution for Microsoft Teams first appeared on IT Security News.
https://www.itsecuritynews.info/red-box-provides-certified-compliance-recording-solution-for-microsoft-teams/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/red-box-provides-certified-compliance-recording-solution-for-microsoft-teams/?utm_source=dlvr.it&utm_medium=blogger
Saturday, September 25, 2021
Disaster Recovery Software: How Does It Work
This article has been indexed from Latest Hacking News Disaster recovery (DR) is defined as a company s system to minimize business disruptions and… Disaster Recovery Software: How Does It Work on Latest Hacking News. Read the original article: Disaster…
Read more → The post Disaster Recovery Software: How Does It Work first appeared on IT Security News.
https://www.itsecuritynews.info/disaster-recovery-software-how-does-it-work/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/disaster-recovery-software-how-does-it-work/?utm_source=dlvr.it&utm_medium=blogger
African Bank Alerts of Data Breach With Personal Details Compromised
This article has been indexed from E Hacking News – Latest Hacker News and IT Security News South African retail bank African Bank has confirmed that one of its debt recovery partners, Debt-IN, was targeted by a ransomware attack…
Read more → The post African Bank Alerts of Data Breach With Personal Details Compromised first appeared on IT Security News.
https://www.itsecuritynews.info/african-bank-alerts-of-data-breach-with-personal-details-compromised/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/african-bank-alerts-of-data-breach-with-personal-details-compromised/?utm_source=dlvr.it&utm_medium=blogger
Threat actors are attempting to exploit VMware vCenter CVE-2021-22005 flaw
This article has been indexed from Security Affairs Immediately after the public release of the exploit code for the VMware vCenter CVE-2021-22005 flaw threat actors started using it. Researchers warn that immediately after the release of the exploit code for…
Read more → The post Threat actors are attempting to exploit VMware vCenter CVE-2021-22005 flaw first appeared on IT Security News.
https://www.itsecuritynews.info/threat-actors-are-attempting-to-exploit-vmware-vcenter-cve-2021-22005-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/threat-actors-are-attempting-to-exploit-vmware-vcenter-cve-2021-22005-flaw/?utm_source=dlvr.it&utm_medium=blogger
Windows Bug Let Hackers Install RootKits on All Windows-based Devices Since Windows 8
An unpatched vulnerability in Microsoft Windows Platform Binary Table (WPBT) has been identified by the cybersecurity researchers of Eclypsium. This bug is continuously attacking all Windows-based devices since Windows 8 could be possibly exploited to install a rootkit as well as to negotiate the integrity of devices. Moreover, these types of bugs generally make every […]
The post Windows Bug Let Hackers Install RootKits on All Windows-based Devices Since Windows 8 appeared first on Cyber Security News.
https://cybersecuritynews.com/windows-bug-let-attackers-install-rootkits/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/windows-bug-let-attackers-install-rootkits/?utm_source=dlvr.it&utm_medium=blogger
A New APT Hacker Group Spying On Hotels and Governments Worldwide
A new advanced persistent threat (APT) has been behind a string of attacks against hotels across the world, along with governments, international organizations, engineering companies, and law firms. Slovak cybersecurity firm ESET codenamed the cyber espionage group FamousSparrow, which it said has been active since at least August 2019, with victims located across Africa, Asia, Europe, the
https://thehackernews.com/2021/09/a-new-apt-hacker-group-spying-on-hotels.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/a-new-apt-hacker-group-spying-on-hotels.html?utm_source=dlvr.it&utm_medium=blogger
Friday, September 24, 2021
iPhone 13 Pro: How to Shoot Macro Photography
This article has been indexed from MacRumors: Mac News and Rumors – Front Page With the launch of the iPhone 13 Pro and Pro Max, Apple introduced Macro mode, a new camera feature that’s exclusive to the Pro models and…
Read more → The post iPhone 13 Pro: How to Shoot Macro Photography first appeared on IT Security News.
https://www.itsecuritynews.info/iphone-13-pro-how-to-shoot-macro-photography/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/iphone-13-pro-how-to-shoot-macro-photography/?utm_source=dlvr.it&utm_medium=blogger
Microsoft Exchange Autodiscover Bug Leaks 372,072 Windows Domain Credentials
A bug in the Microsoft Exchange mail server has been detected recently by the security researchers of the Guardicore. This issue has occurred in the leaking of domain credentials and Windows applications all over the world. However, the main difficulty lazes in the protocol of the Microsoft Autodiscover characteristic of the Microsoft Exchange mail servers, […]
The post Microsoft Exchange Autodiscover Bug Leaks 372,072 Windows Domain Credentials appeared first on Cyber Security News.
https://cybersecuritynews.com/microsoft-exchange-autodiscover/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/microsoft-exchange-autodiscover/?utm_source=dlvr.it&utm_medium=blogger
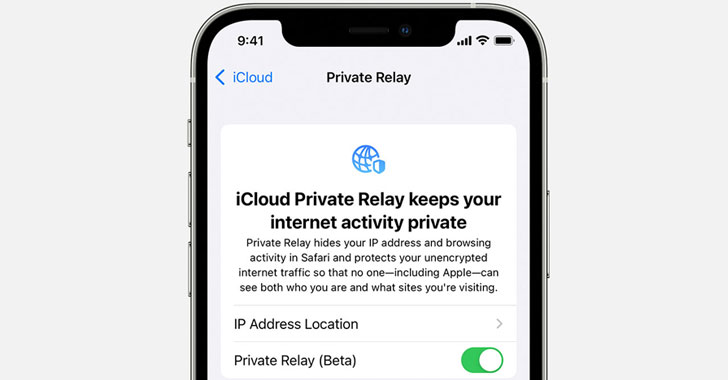
Apple's New iCloud Private Relay Service Leaks Users' Real IP Addresses
A new as-yet unpatched weakness in Apple's iCloud Private Relay feature could be circumvented to leak users' true IP addresses from iOS devices running the latest version of the operating system. Introduced with iOS 15, which was officially released this week, iCloud Private Relay aims to improve anonymity on the web by employing a dual-hop architecture that effectively shields users' IP address
https://thehackernews.com/2021/09/apples-new-icloud-private-relay-service.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/apples-new-icloud-private-relay-service.html?utm_source=dlvr.it&utm_medium=blogger
Google Warns of a New Way Hackers Can Make Malware Undetectable on Windows
Cybersecurity researchers have disclosed a novel technique adopted by threat actors to deliberately evade detection with the help of malformed digital signatures of its malware payloads. "Attackers created malformed code signatures that are treated as valid by Windows but are not able to be decoded or checked by OpenSSL code — which is used in a number of security scanning products," Google
https://thehackernews.com/2021/09/google-warns-of-new-way-hackers-can.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/google-warns-of-new-way-hackers-can.html?utm_source=dlvr.it&utm_medium=blogger
Urgent Apple iOS and macOS Updates Released to Fix Actively Exploited Zero-Days
Apple on Thursday released security updates to fix multiple security vulnerabilities in older versions of iOS and macOS that it says have been detected in exploits in the wild, in addition to expanding patches for a previously plugged security weakness abused by NSO Group's Pegasus surveillance tool to target iPhone users. Chief among them is CVE-2021-30869, a type confusion flaw
https://thehackernews.com/2021/09/urgent-apple-ios-and-macos-updates.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/urgent-apple-ios-and-macos-updates.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, September 23, 2021
New OffSec Training Library Subscriptions: Learn One and Learn Unlimited
This article has been indexed from Offensive Security The OffSec Training Library is a subscription-based cybersecurity training platform. Discover more about our Learn One and Learn Unlimited subscriptions. The post New OffSec Training Library Subscriptions: Learn One and Learn Unlimited…
Read more → The post New OffSec Training Library Subscriptions: Learn One and Learn Unlimited first appeared on IT Security News.
https://www.itsecuritynews.info/new-offsec-training-library-subscriptions-learn-one-and-learn-unlimited-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/new-offsec-training-library-subscriptions-learn-one-and-learn-unlimited-2/?utm_source=dlvr.it&utm_medium=blogger
Why You Should Consider QEMU Live Patching
Sysadmins know what the risks are of running unpatched services. Given the choice, and unlimited resources, most hardworking administrators will ensure that all systems and services are patched consistently. But things are rarely that simple. Technical resources are limited, and patching can often be more complicated than it appears at first glance. Worse, some services are so hidden in the
https://thehackernews.com/2021/09/why-you-should-consider-qemu-live.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/why-you-should-consider-qemu-live.html?utm_source=dlvr.it&utm_medium=blogger
Colombian Real Estate Agency Leak Exposes Records of Over 100,000 Buyers
More than one terabyte of data containing 5.5 million files has been left exposed, leaking personal information of over 100,000 customers of a Colombian real estate firm, according to cybersecurity company WizCase. The breach was discovered by Ata Hakçıl and his team in a database owned by Coninsa Ramon H, a company that specializes in architecture, engineering, construction, and real estate
https://thehackernews.com/2021/09/colombian-real-estate-agency-leak.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/colombian-real-estate-agency-leak.html?utm_source=dlvr.it&utm_medium=blogger
China-Linked Group TAG-28 Attack Indian Government Agency With Winnti Malware
The police department of India recently discovered that an Indian media conglomerate, Bennett Coleman And Co Ltd, (BCCL), and the Unique Identification Authority of India (UIDAI) database have been hacked probably by a Chinese hacking group. They were given a temporary name TAG-28 and it was also detected that the threat actors of this group […]
The post China-Linked Group TAG-28 Attack Indian Government Agency With Winnti Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/china-linked-group-tag-28/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/china-linked-group-tag-28/?utm_source=dlvr.it&utm_medium=blogger
LG acquires Israeli automotive cybersecurity startup Cybellum
This article has been indexed from Latest topics for ZDNet in Security The South Korean company has acquired startup Cybellum, which offers risk assessment software that scans vehicles for security vulnerabilities. Read the original article: LG acquires Israeli automotive cybersecurity…
Read more → The post LG acquires Israeli automotive cybersecurity startup Cybellum first appeared on IT Security News.
https://www.itsecuritynews.info/lg-acquires-israeli-automotive-cybersecurity-startup-cybellum/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/lg-acquires-israeli-automotive-cybersecurity-startup-cybellum/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, September 22, 2021
APT-C-36 Hacking Group Uses Wide Range of Trojans (RATs) To Target Organizations
A hacking group from Columbia which is dubbed as “APT-C-36” is running a phishing campaign that represents emails and attempts to accumulate victims in South America. In this campaign, the threat actors have used a wide range of malware and geolocation filters to affect computers and to avoid different kinds of detection. Initially, this phishing […]
The post APT-C-36 Hacking Group Uses Wide Range of Trojans (RATs) To Target Organizations appeared first on Cyber Security News.
https://cybersecuritynews.com/apt-c-36-hacking-group/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/apt-c-36-hacking-group/?utm_source=dlvr.it&utm_medium=blogger
How Cynet's Response Automation Helps Organizations Mitigate Cyber Threats
One of the determining factors of how much damage a cyber-attack cause is how fast organizations can respond to it. Time to response is critical for security teams, and it is a major hurdle for leaner teams. To help improve this metric and enhance organizations’ ability to respond to attacks quickly, many endpoint detection and response (EDR) and extended detection and response (XDR) vendors
https://thehackernews.com/2021/09/how-cynets-response-automation-helps.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/how-cynets-response-automation-helps.html?utm_source=dlvr.it&utm_medium=blogger
VMware Warns of Critical File Upload Vulnerability Affecting vCenter Server
VMware on Tuesday published a new bulletin warning of as many as 19 vulnerabilities in vCenter Server and Cloud Foundation appliances that a remote attacker could exploit to take control of an affected system. The most urgent among them is an arbitrary file upload vulnerability in the Analytics service (CVE-2021-22005) that impacts vCenter Server 6.7 and 7.0 deployments. "A malicious actor with
https://thehackernews.com/2021/09/vmware-warns-of-critical-file-upload.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/vmware-warns-of-critical-file-upload.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, September 21, 2021
Turla APT group used a new backdoor in attacks against Afghanistan, Germany and the US
This article has been indexed from Security Affairs Russia-linked cyber espionage group Turla made the headlines again, the APT has employed a new backdoor in a recent wave of attacks Cisco Talos researchers reported that the Russia-linked Turla APT group…
Read more → The post Turla APT group used a new backdoor in attacks against Afghanistan, Germany and the US first appeared on IT Security News.
https://www.itsecuritynews.info/turla-apt-group-used-a-new-backdoor-in-attacks-against-afghanistan-germany-and-the-us/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/turla-apt-group-used-a-new-backdoor-in-attacks-against-afghanistan-germany-and-the-us/?utm_source=dlvr.it&utm_medium=blogger
New Capoae Malware Infiltrates WordPress Sites and Installs Backdoored Plugin
A recently discovered wave of malware attacks has been spotted using a variety of tactics to enslave susceptible machines with easy-to-guess administrative credentials to co-opt them into a network with the goal of illegally mining cryptocurrency. "The malware's primary tactic is to spread by taking advantage of vulnerable systems and weak administrative credentials. Once they've been infected,
https://thehackernews.com/2021/09/new-capoae-malware-infiltrates.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/new-capoae-malware-infiltrates.html?utm_source=dlvr.it&utm_medium=blogger
Android 11 to come with auto-resets Permissions for Unused Android Apps
A maximum of users spends time with their smartphones. Sometimes they are working, connecting with friends, playing games, etc. this has become their primary gateway for digital lives. To work correctly, the app needs specific permission, and for that, they need to send a request to the given device. Permission can be automatically granted if […]
The post Android 11 to come with auto-resets Permissions for Unused Android Apps appeared first on Cyber Security News.
https://cybersecuritynews.com/android-11/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/android-11/?utm_source=dlvr.it&utm_medium=blogger
Monday, September 20, 2021
iMovie and Clips Apps for iOS Gain Support for iPhone 13 Features
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Apple today updated iMovie and Clips with support for several new features that are set to be introduced alongside the iPhone 13 models. iMovie now supports…
Read more → The post iMovie and Clips Apps for iOS Gain Support for iPhone 13 Features first appeared on IT Security News.
https://www.itsecuritynews.info/imovie-and-clips-apps-for-ios-gain-support-for-iphone-13-features/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/imovie-and-clips-apps-for-ios-gain-support-for-iphone-13-features/?utm_source=dlvr.it&utm_medium=blogger
Numando – A Trojan Abuses YouTube & Pastebin to Spread & Hack Windows Users
A Latin American banking Trojan named Numando has been detected recently by the ESET researchers, and it’s targetting Brazil, some areas of Mexico, and Spain. Numando banking trojan is comparable to the other malware families that are being described in the series of Latin American Trojan. This trojan generally uses the miscreant browser overlays, backdoor […]
The post Numando – A Trojan Abuses YouTube & Pastebin to Spread & Hack Windows Users appeared first on Cyber Security News.
https://cybersecuritynews.com/numando/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/numando/?utm_source=dlvr.it&utm_medium=blogger
Numando: A New Banking Trojan Targeting Latin American Users
A newly spotted banking trojan has been caught leveraging legitimate platforms like YouTube and Pastebin to store its encrypted, remote configuration and commandeer infected Windows systems, making it the latest to join the long list of malware targeting Latin America (LATAM) after Guildma, Javali, Melcoz, Grandoreiro, Mekotio, Casbaneiro, Amavaldo, Vadokrist, and Janeleiro. The threat actor
https://thehackernews.com/2021/09/numando-new-banking-trojan-targeting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/09/numando-new-banking-trojan-targeting.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, September 19, 2021
Hackers Using MSHTML 0-Days Exploit To Deploy Cobalt Strike Beacon On Windows
Microsoft announced a targeted phishing campaign that they have detected recently, and this campaign is exploiting MSHTML 0-Days exploit to deploy Cobalt Strike Beacon on Windows. But, right now at this moment, they have already patched the zero-day vulnerability in the MSHTML platform. In this campaign, the threat actors used especially configured Office documents to […]
The post Hackers Using MSHTML 0-Days Exploit To Deploy Cobalt Strike Beacon On Windows appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-using-mshtml-0-days-exploit-to-deploy-cobalt-strike/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-using-mshtml-0-days-exploit-to-deploy-cobalt-strike/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)