ProxyToken, a serious security vulnerability has been detected in the Microsoft Exchange Server by the security analysts. ProxyToken vulnerability could enable unauthenticated threat actors to access and steal emails from a victim mailbox. The threat actors are using this vulnerability as a weapon to implement the attack, and this issue is tracked as CVE-2021-33766 and […]
The post Microsoft Exchange Server Flaw Let Remote Attackers Access Sensitive Information appeared first on Cyber Security News.
https://cybersecuritynews.com/microsoft-exchange-server-flaw/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, August 31, 2021
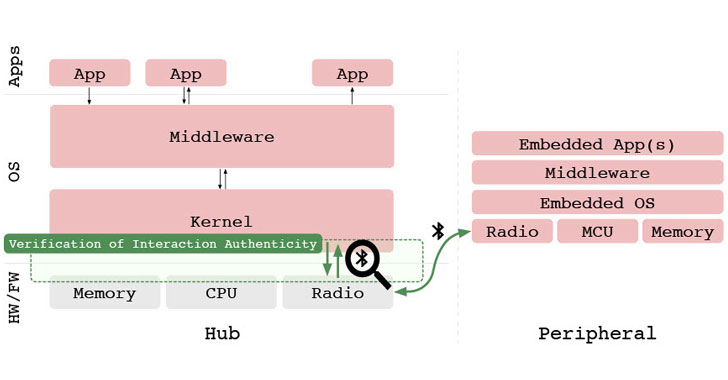
Researchers Propose Machine Learning-based Bluetooth Authentication Scheme
A group of academics has proposed a machine learning approach that uses authentic interactions between devices in Bluetooth networks as a foundation to handle device-to-device authentication reliably. Called "Verification of Interaction Authenticity" (aka VIA), the recurring authentication scheme aims to solve the problem of passive, continuous authentication and automatic deauthentication once
https://thehackernews.com/2021/08/researchers-propose-machine-learning.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/researchers-propose-machine-learning.html?utm_source=dlvr.it&utm_medium=blogger
New Microsoft Exchange 'ProxyToken' Flaw Lets Attackers Reconfigure Mailboxes
Details have emerged about a now-patched security vulnerability impacting Microsoft Exchange Server that could be weaponized by an unauthenticated attacker to modify server configurations, thus leading to the disclosure of Personally Identifiable Information (PII). The issue, tracked as CVE-2021-33766 (CVSS score: 7.3) and coined "ProxyToken," was discovered by Le Xuan Tuyen, a researcher at the
https://thehackernews.com/2021/08/new-microsoft-exchange-proxytoken-flaw.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/new-microsoft-exchange-proxytoken-flaw.html?utm_source=dlvr.it&utm_medium=blogger
Monday, August 30, 2021
iPhone 13 Satellite Support Rumor Disputed, Likely for Additional 5G Spectrum
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Over the weekend, Apple analyst Ming-Chi Kuo sent out a research note suggesting that the iPhone 13 was “likely” to support low earth orbit satellite communication,…
Read more → The post iPhone 13 Satellite Support Rumor Disputed, Likely for Additional 5G Spectrum first appeared on IT Security News.
https://www.itsecuritynews.info/iphone-13-satellite-support-rumor-disputed-likely-for-additional-5g-spectrum/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/iphone-13-satellite-support-rumor-disputed-likely-for-additional-5g-spectrum/?utm_source=dlvr.it&utm_medium=blogger
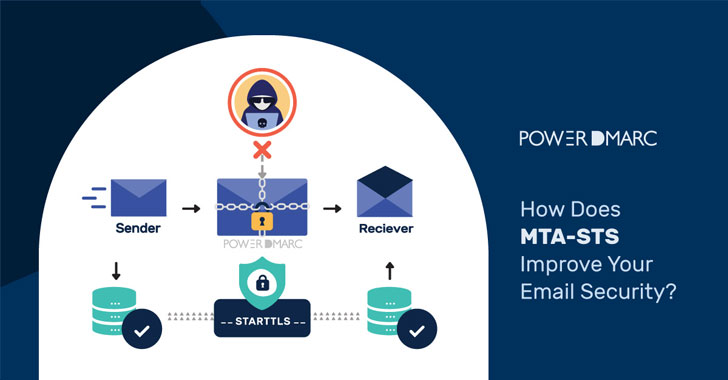
How Does MTA-STS Improve Your Email Security?
Simple Mail Transfer Protocol or SMTP has easily exploitable security loopholes. Email routing protocols were designed in a time when cryptographic technology was at a nascent stage (e.g., the de-facto protocol for email transfer, SMTP, is nearly 40 years old now), and therefore security was not an important consideration. As a result, in most email systems encryption is still opportunistic,
https://thehackernews.com/2021/08/how-does-mta-sts-improve-your-email.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/how-does-mta-sts-improve-your-email.html?utm_source=dlvr.it&utm_medium=blogger
Boston Public Library hit by Cyber Attack
This article has been indexed from Cybersecurity Insiders Boston Public Library (BPL) branches based in Massachusetts have been witnessing a digital disruption since Wednesday last week, all because of a cyber attack. And sources say that they are using pen…
Read more → The post Boston Public Library hit by Cyber Attack first appeared on IT Security News.
https://www.itsecuritynews.info/boston-public-library-hit-by-cyber-attack/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/boston-public-library-hit-by-cyber-attack/?utm_source=dlvr.it&utm_medium=blogger
Sunday, August 29, 2021
T-Mobile hacker used brute force attack to steal customers’ data
This article has been indexed from HackRead By Saad Rajpoot A 21-year-old US citizen named John Binns has claimed responsibility for the T-Mobile data breach and labeled the carrier’s “security is awful.” This is a post from HackRead.com Read the…
Read more → The post T-Mobile hacker used brute force attack to steal customers’ data first appeared on IT Security News.
https://www.itsecuritynews.info/t-mobile-hacker-used-brute-force-attack-to-steal-customers-data/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/t-mobile-hacker-used-brute-force-attack-to-steal-customers-data/?utm_source=dlvr.it&utm_medium=blogger
Universal Control Works in macOS Monterey Beta 5, But Terminal Commands Required to Enable It
This article has been indexed from MacRumors: Mac News and Rumors – Front Page One of the most highly anticipated features coming to macOS Monterey and iPadOS 15 is Universal Control. Universal Control enables users to use a single Mac’s…
Read more → The post Universal Control Works in macOS Monterey Beta 5, But Terminal Commands Required to Enable It first appeared on IT Security News.
https://www.itsecuritynews.info/universal-control-works-in-macos-monterey-beta-5-but-terminal-commands-required-to-enable-it/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/universal-control-works-in-macos-monterey-beta-5-but-terminal-commands-required-to-enable-it/?utm_source=dlvr.it&utm_medium=blogger
Get Lifetime Access to 24 Professional Cybersecurity Certification Prep Courses
Not all heroes wear capes. Cybersecurity professionals are digital warriors who use their knowledge and skill to battle malicious hackers. Sounds like an exciting career, right? If the comic-book comparisons aren’t working for you, perhaps some figures will. According to ZipRecruiter, the average salary of a cybersecurity professional is just over $100,000 a year. The Complete 2021
https://thehackernews.com/2021/08/get-lifetime-access-to-24-professional.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/get-lifetime-access-to-24-professional.html?utm_source=dlvr.it&utm_medium=blogger
Saturday, August 28, 2021
Five iPhone 13 Rumors You May Have Missed
This article has been indexed from MacRumors: Mac News and Rumors – Front Page We’re just weeks away from when Apple will announce the iPhone 13, which we’re expecting to feature some considerable upgrades, including design, performance, cameras, and more.…
Read more → The post Five iPhone 13 Rumors You May Have Missed first appeared on IT Security News.
https://www.itsecuritynews.info/five-iphone-13-rumors-you-may-have-missed/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/five-iphone-13-rumors-you-may-have-missed/?utm_source=dlvr.it&utm_medium=blogger
Critical Vulnerability in Microsoft Azure Platform Let Attackers Takeover Remotely
Recently, Microsoft has informed all its customers about a critical vulnerability in its Azure cloud platform. Here, the security company, Wiz has reported this data leak to Microsoft, and even they have also published the information on their official blog. After investigating the attack, the experts of Wiz security firm claimed that the issue correlates […]
The post Critical Vulnerability in Microsoft Azure Platform Let Attackers Takeover Remotely appeared first on Cyber Security News.
https://cybersecuritynews.com/chaosdb-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/chaosdb-flaw/?utm_source=dlvr.it&utm_medium=blogger
Beyond the pandemic: Why are data breach costs at an all‑time high?
This article has been indexed from WeLiveSecurity It might be tempting to blame the record-high costs of data breaches on the COVID-19 pandemic alone. But dig deeper and a more nuanced picture emerges. The post Beyond the pandemic: Why are…
Read more → The post Beyond the pandemic: Why are data breach costs at an all‑time high? first appeared on IT Security News.
https://www.itsecuritynews.info/beyond-the-pandemic-why-are-data-breach-costs-at-an-all%e2%80%91time-high/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/beyond-the-pandemic-why-are-data-breach-costs-at-an-all%e2%80%91time-high/?utm_source=dlvr.it&utm_medium=blogger
Friday, August 27, 2021
Building tomorrow’s network today
This article has been indexed from GCN: News, Explainers, Insights Agencies investing Technology Modernization Fund money into modernizing their networks should consider rapidly evolving wireless technologies, security and network and data center infrastructures. Read the original article: Building tomorrow’s network…
Read more → The post Building tomorrow’s network today first appeared on IT Security News.
https://www.itsecuritynews.info/building-tomorrows-network-today/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/building-tomorrows-network-today/?utm_source=dlvr.it&utm_medium=blogger
IoT Botnet Attack Hundreds of Thousands of Realtek Chipset Based Devices
The IoT security firm, SAM has recently discovered a dangerous botnet attacking devices using the Realtek chipsets. Not only this even this chipset is used by more than 65 vendors, which implies hundreds of thousands of smart devices are vulnerable to this security flaw. Last week all these attacks were initiated which were reported and […]
The post IoT Botnet Attack Hundreds of Thousands of Realtek Chipset Based Devices appeared first on Cyber Security News.
https://cybersecuritynews.com/iot-botnet-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/iot-botnet-attack/?utm_source=dlvr.it&utm_medium=blogger
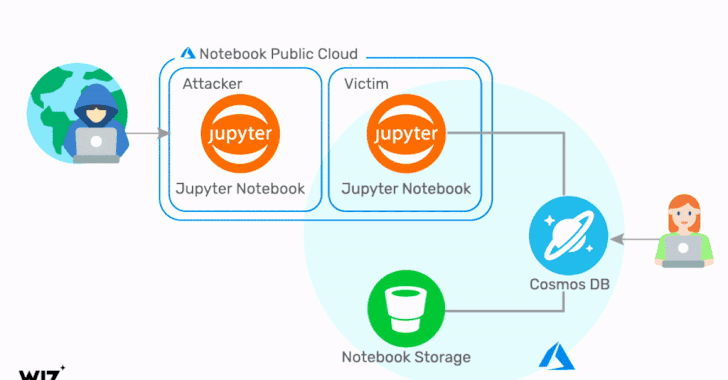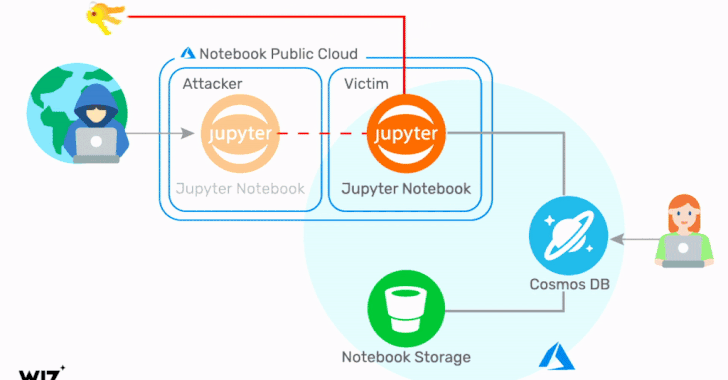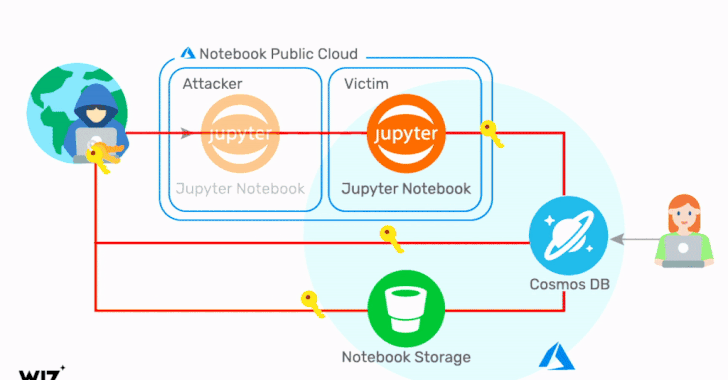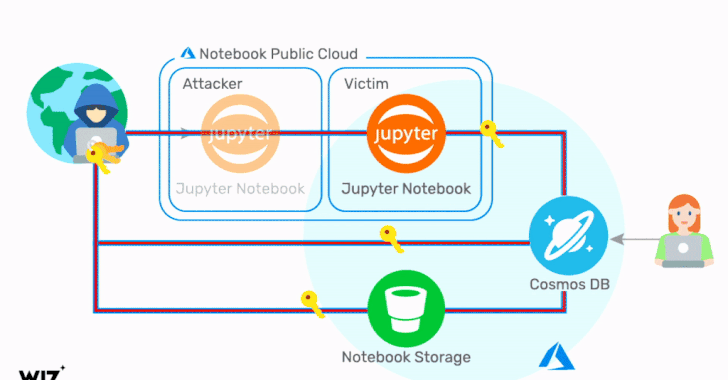
Critical Cosmos Database Flaw Affected Thousands of Microsoft Azure Customers
Cloud infrastructure security company Wiz on Thursday revealed details of a now-fixed Azure Cosmos database vulnerability that could have been potentially exploited to grant any Azure user full admin access to other customers' database instances without any authorization. The flaw, which grants read, write, and delete privileges, has been dubbed "ChaosDB," with Wiz researchers noting that "the
https://thehackernews.com/2021/08/critical-cosmos-database-flaw-affected.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/critical-cosmos-database-flaw-affected.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, August 26, 2021
Clear and present danger: Why business leaders must prioritize cybersecurity
This article has been indexed from Security – VentureBeat In the last few months, we’ve seen cyberattacks of unprecedented scale. But your employees won’t get serious about security until you do. Read the original article: Clear and present danger: Why…
Read more → The post Clear and present danger: Why business leaders must prioritize cybersecurity first appeared on IT Security News.
https://www.itsecuritynews.info/clear-and-present-danger-why-business-leaders-must-prioritize-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/clear-and-present-danger-why-business-leaders-must-prioritize-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
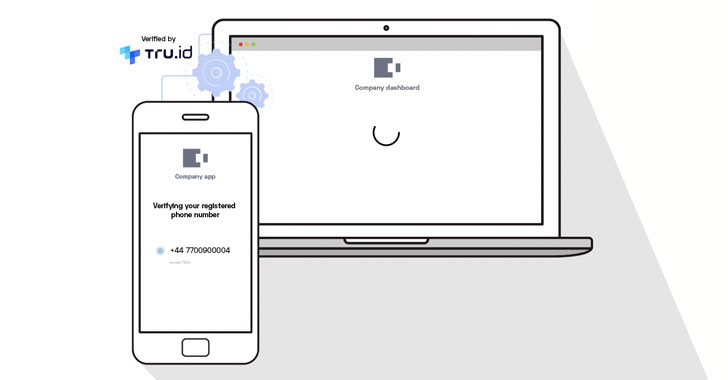
New Passwordless Verification API Uses SIM Security for Zero Trust Remote Access
Forget watercooler conspiracies or boardroom battles. There's a new war in the office. As companies nudge their staff to return to communal workspaces, many workers don't actually want to – more than 50 percent of employees would rather quit, according to research by EY. While HR teams worry over the hearts and minds of staff, IT security professionals have a different battle plan to draft –
https://thehackernews.com/2021/08/new-passwordless-verification-api-uses.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/new-passwordless-verification-api-uses.html?utm_source=dlvr.it&utm_medium=blogger
Critical Flaw Discovered in Cisco APIC for Switches — Patch Released
Cisco Systems on Wednesday issued patches to address a critical security vulnerability affecting the Application Policy Infrastructure Controller (APIC) interface used in its Nexus 9000 Series Switches that could be potentially abused to read or write arbitrary files on a vulnerable system. Tracked as CVE-2021-1577 (CVSS score: 9.1), the issue — which is due to improper access control — could
https://thehackernews.com/2021/08/critical-flaw-discovered-in-cisco-apic.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/critical-flaw-discovered-in-cisco-apic.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, August 25, 2021
Beware!! New Modified Version of WhatsApp Install Malware on Your Device & Steal SMS Data
The Kaspersky Lab has recently discovered the Trojan Triada, in one of the versions of the mod for the WhatsApp messenger – FMWhatsapp16.80.0. This malware can easily download and operate other malicious modules, exhibit ads, and subscribe. However, in this version, the threat actors have configured the download of a malicious request by an application […]
The post Beware!! New Modified Version of WhatsApp Install Malware on Your Device & Steal SMS Data appeared first on Cyber Security News.
https://cybersecuritynews.com/new-modified-version-of-whatsapp-install-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/new-modified-version-of-whatsapp-install-malware/?utm_source=dlvr.it&utm_medium=blogger
4 New Emerging Ransomware Groups That Can a Serious Threat To Enterprises And Critical Infrastructure
Palo Alto Networks’ Unit 42 threat intelligence team observed four emerging ransomware groups that are currently affecting organizations and show signs of having the potential to become more widespread in the future. AvosLocker Ransomware It is ransomware as a service (RaaS) that is utilizing a blue beetle logo to identify itself in communications with victims […]
The post 4 New Emerging Ransomware Groups That Can a Serious Threat To Enterprises And Critical Infrastructure appeared first on Cyber Security News.
https://cybersecuritynews.com/emerging-ransomware-groups/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/emerging-ransomware-groups/?utm_source=dlvr.it&utm_medium=blogger
New SideWalk Backdoor Targets U.S.-based Computer Retail Business
A computer retail company based in the U.S. was the target of a previously undiscovered implant called SideWalk as part of a recent campaign undertaken by a Chinese advanced persistent threat group primarily known for singling out entities in East and Southeast Asia. Slovak cybersecurity firm ESET attributed the malware to an advanced persistent threat it tracks under the moniker SparklingGoblin
https://thehackernews.com/2021/08/new-sidewalk-backdoor-targets-us-based.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/new-sidewalk-backdoor-targets-us-based.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, August 24, 2021
Nokia Subsidiary Discloses Data Breach After Conti Ransomware Attack
SAC Wireless that operates as a wholly-owned subsidiary of Nokia suffered a data breach following a Conti Ransomware incident. The company helps customers design, build and upgrade cellular networks, including 5G, 4G LTE, small cell, and FirstNet. According to the company’s data breach notification, the company became aware that certain aspects of our internal technology […]
The post Nokia Subsidiary Discloses Data Breach After Conti Ransomware Attack appeared first on Cyber Security News.
https://cybersecuritynews.com/nokia-subsidiary-data-breach/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/nokia-subsidiary-data-breach/?utm_source=dlvr.it&utm_medium=blogger
Protect Your Enterprise From ShinyHunters APT Hackers Group That Responsible for Notable Cyber Attacks
The security researchers of Intel 471 have recently detected a cybercriminal group ShinyHunters that is continuously trying to collect all essential data of the enterprises. The cybercriminal group ShinyHunters are searching for all large enterprises so that they can conduct larger-scale attacks. The experts have started analyzing this vulnerability and came to know that the […]
The post Protect Your Enterprise From ShinyHunters APT Hackers Group That Responsible for Notable Cyber Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/protect-your-enterprise-from-shinyhunters-apt-hackers/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/protect-your-enterprise-from-shinyhunters-apt-hackers/?utm_source=dlvr.it&utm_medium=blogger
Google bans the following cryptocurrency apps for data security
This article has been indexed from Cybersecurity Insiders If you are a cryptocurrency enthusiast and are using any of the mining apps to earn more, then this article needs your interest. Google has issued a warning to all users of…
Read more → The post Google bans the following cryptocurrency apps for data security first appeared on IT Security News.
https://www.itsecuritynews.info/google-bans-the-following-cryptocurrency-apps-for-data-security/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/google-bans-the-following-cryptocurrency-apps-for-data-security/?utm_source=dlvr.it&utm_medium=blogger
Monday, August 23, 2021
ACLU Advocate Reining in Government Use of Face Surveillance, Champion of Privacy Rights Research, and Data Security Trainer Protecting Black Communities Named Recipients of EFF’s Pioneer Award
This article has been indexed from Deeplinks Virtual Ceremony September 16 Will Honor Kade Crockford, Pam Dixon, and Matt Mitchell San Francisco – The Electronic Frontier Foundation (EFF) is honored to announce that Kade Crockford, Director of the Technology for…
Read more → The post ACLU Advocate Reining in Government Use of Face Surveillance, Champion of Privacy Rights Research, and Data Security Trainer Protecting Black Communities Named Recipients of EFF’s Pioneer Award first appeared on IT Security News.
https://www.itsecuritynews.info/aclu-advocate-reining-in-government-use-of-face-surveillance-champion-of-privacy-rights-research-and-data-security-trainer-protecting-black-communities-named-recipients-of-effs-pioneer-awa/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/aclu-advocate-reining-in-government-use-of-face-surveillance-champion-of-privacy-rights-research-and-data-security-trainer-protecting-black-communities-named-recipients-of-effs-pioneer-awa/?utm_source=dlvr.it&utm_medium=blogger
Top 15 Vulnerabilities Attackers Exploited Millions of Times to Hack Linux Systems
Close to 14 million Linux-based systems are directly exposed to the Internet, making them a lucrative target for an array of real-world attacks that could result in the deployment of malicious web shells, coin miners, ransomware, and other trojans. That's according to an in-depth look at the Linux threat landscape published by U.S.-Japanese cybersecurity firm Trend Micro, detailing the top
https://thehackernews.com/2021/08/top-15-vulnerabilities-attackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/top-15-vulnerabilities-attackers.html?utm_source=dlvr.it&utm_medium=blogger
Top 10 Kubernetes Container Scanner to Detect Security Vulnerability and Misconfiguration
Before you read this topic, you may be wondering what Kubernetes is? Let us tell you; it is an extensible, portable, and open-source platform that manages containerized workload and services. It provides two facilities like automation and declarative configuration. In this article, we detail the top 10 Kubernetes Container Scanner. It has the ability to […]
The post Top 10 Kubernetes Container Scanner to Detect Security Vulnerability and Misconfiguration appeared first on Cyber Security News.
https://cybersecuritynews.com/kubernetes-container-scanner/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/kubernetes-container-scanner/?utm_source=dlvr.it&utm_medium=blogger
Sunday, August 22, 2021
Multilingual Cybersecurity Awareness Training adapted for your needs
Technology alone cannot protect you from everything. Because the online world is so interconnected, everyone is a target, no matter if you are an individual, small business or huge enterprise. Cybersecurity awareness training teaches your employees – to spot fake…
Read more → The post Multilingual Cybersecurity Awareness Training adapted for your needs first appeared on IT Security News.
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-39/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-39/?utm_source=dlvr.it&utm_medium=blogger
WARNING: Microsoft Exchange Under Attack With ProxyShell Flaws
The U.S. Cybersecurity and Infrastructure Security Agency is warning of active exploitation attempts that leverage the latest line of "ProxyShell" Microsoft Exchange vulnerabilities that were patched earlier this May, including deploying LockFile ransomware on compromised systems. Tracked as CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207, the vulnerabilities enable adversaries to bypass ACL
https://thehackernews.com/2021/08/microsoft-exchange-under-attack-with.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/microsoft-exchange-under-attack-with.html?utm_source=dlvr.it&utm_medium=blogger
Identity management org Sailpoint unveils no-code tool
This article has been indexed from Security – VentureBeat SailPoint adds no-code tool to make it easier for IT teams to manage workflows based on employee identities. Read the original article: Identity management org Sailpoint unveils no-code tool
Read more → The post Identity management org Sailpoint unveils no-code tool first appeared on IT Security News.
https://www.itsecuritynews.info/identity-management-org-sailpoint-unveils-no-code-tool/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/identity-management-org-sailpoint-unveils-no-code-tool/?utm_source=dlvr.it&utm_medium=blogger
Saturday, August 21, 2021
Largest HTTP DDoS Attack That Peaking At 17.2 Million Requests Per Second
Cloudflare stated that it mitigated a 17.2 million request-per-second (rps) DDoS attack, an attack about three times larger than any previous one that was recorded so far. This attack took place earlier last month, targeted one of Cloudflare’s customers in the financial industry. The company said that a threat actor used a botnet of more […]
The post Largest HTTP DDoS Attack That Peaking At 17.2 Million Requests Per Second appeared first on Cyber Security News.
https://cybersecuritynews.com/http-ddos-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/http-ddos-attack/?utm_source=dlvr.it&utm_medium=blogger
Hacker Rewarded with $500,000 and a CSA Job by Poly Network
This article has been indexed from E Hacking News – Latest Hacker News and IT Security News Lately, it has been a turbulence-filled time for Poly Networks. The company creates software to handle the exchange between different blockchains for…
Read more → The post Hacker Rewarded with $500,000 and a CSA Job by Poly Network first appeared on IT Security News.
https://www.itsecuritynews.info/hacker-rewarded-with-500000-and-a-csa-job-by-poly-network/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hacker-rewarded-with-500000-and-a-csa-job-by-poly-network/?utm_source=dlvr.it&utm_medium=blogger
Hackers swipe almost $100 million from major cryptocurrency exchange
This article has been indexed from WeLiveSecurity Japanese cryptocurrency exchange Liquid suspends cryptocurrency deposits and withdrawals and moves its assets into cold storage The post Hackers swipe almost $100 million from major cryptocurrency exchange appeared first on WeLiveSecurity Read the…
Read more → The post Hackers swipe almost $100 million from major cryptocurrency exchange first appeared on IT Security News.
https://www.itsecuritynews.info/hackers-swipe-almost-100-million-from-major-cryptocurrency-exchange/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hackers-swipe-almost-100-million-from-major-cryptocurrency-exchange/?utm_source=dlvr.it&utm_medium=blogger
Friday, August 20, 2021
MacRumors Giveaway: Win a Jackery Explorer 500 Portable Power Station
This article has been indexed from MacRumors: Mac News and Rumors – Front Page For this week’s giveaway, we’ve once again teamed up with Jackery to offer MacRumors readers a chance to win a Jackery Explorer 500 Portable Power Station…
Read more → The post MacRumors Giveaway: Win a Jackery Explorer 500 Portable Power Station first appeared on IT Security News.
https://www.itsecuritynews.info/macrumors-giveaway-win-a-jackery-explorer-500-portable-power-station/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/macrumors-giveaway-win-a-jackery-explorer-500-portable-power-station/?utm_source=dlvr.it&utm_medium=blogger
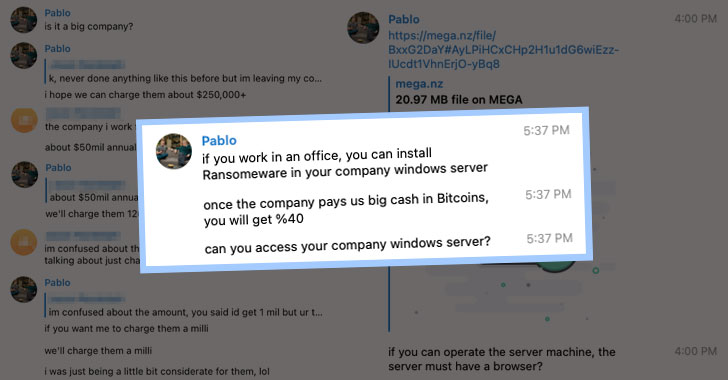
Cybercrime Group Asking Insiders for Help in Planting Ransomware
A Nigerian threat actor has been observed attempting to recruit employees by offering them to pay $1 million in bitcoins to deploy Black Kingdom ransomware on companies' networks as part of an insider threat scheme. "The sender tells the employee that if they're able to deploy ransomware on a company computer or Windows server, then they would be paid $1 million in bitcoin, or 40% of the
https://thehackernews.com/2021/08/cybercrime-group-asking-insiders-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/cybercrime-group-asking-insiders-for.html?utm_source=dlvr.it&utm_medium=blogger
Critical Flaw Found in Older Cisco Small Business Routers Won't Be Fixed
A critical vulnerability in Cisco Small Business Routers will not be patched by the networking equipment giant, since the devices reached end-of-life in 2019. Tracked as CVE-2021-34730 (CVSS score: 9.8), the issue resides in the routers' Universal Plug-and-Play (UPnP) service, enabling an unauthenticated, remote attacker to execute arbitrary code or cause an affected device to restart
https://thehackernews.com/2021/08/critical-flaw-found-in-older-cisco.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/critical-flaw-found-in-older-cisco.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, August 19, 2021
Tencent Security Keen Lab: Experimental Security Assessment of Mercedes-Benz Cars
This article has been indexed from Keen Security Lab Blog MBUX, Mercedes-Benz User Experience is the infotainment system in Mercedes-Benz cockpits. Mercedes-Benz first introduced MBUX in the new A-Class back in 2018, and is adopting MBUX in their entire vehicle…
Read more → The post Tencent Security Keen Lab: Experimental Security Assessment of Mercedes-Benz Cars first appeared on IT Security News.
https://www.itsecuritynews.info/tencent-security-keen-lab-experimental-security-assessment-of-mercedes-benz-cars-10/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/tencent-security-keen-lab-experimental-security-assessment-of-mercedes-benz-cars-10/?utm_source=dlvr.it&utm_medium=blogger
Researchers Find New Evidence Linking Diavol Ransomware to TrickBot Gang
Cybersecurity researchers have disclosed details about an early development version of a nascent ransomware strain called Diavol that has been linked to threat actors behind the infamous TrickBot syndicate. The latest findings from IBM X-Force show that the ransomware sample shares similarities to other malware that has been attributed to the cybercrime gang, thus establishing a clearer
https://thehackernews.com/2021/08/researchers-find-new-evidence-linking.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/researchers-find-new-evidence-linking.html?utm_source=dlvr.it&utm_medium=blogger
How Hackers Break Two-Factor Authentication Security By Intercepting SMS and Voice Calls
The latest findings state that more than 80% of all hacking-related breaches happen due to compromised and weak credentials, with three billion username/password combinations stolen in 2016 alone. Two-factor authentication (2FA), referred to as two-step verification or dual-factor authentication, is a security process in which users provide two different authentication factors to verify themselves. […]
The post How Hackers Break Two-Factor Authentication Security By Intercepting SMS and Voice Calls appeared first on Cyber Security News.
https://cybersecuritynews.com/two-factor-authentication/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/two-factor-authentication/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, August 18, 2021
What are Residential Proxies? – Pros & Cons
Proxy is an intermediate server of the Internet connection between the user and an Internet website. Such a connection scheme helps avoid the direct connection between the user and the Internet; this solution decreases digital fingerprints. A proxy server has an IP address like any other Internet user. It includes information regarding user location, provider, […]
The post What are Residential Proxies? – Pros & Cons appeared first on Cyber Security News.
https://cybersecuritynews.com/what-are-residential-proxies-pros-cons/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/what-are-residential-proxies-pros-cons/?utm_source=dlvr.it&utm_medium=blogger
Does a VPN Protect You from Hackers?
A virtual private network (VPN) is the perfect solution for a lot of issues you might experience online- accessing blocked sites, hiding your browsing activity, getting rid of internet throttling, finding better deals, and much more. But does a VPN protect you from hackers? Is your private information and files safer on the internet with a VPN? How much of a difference does it make in terms of
https://thehackernews.com/2021/08/does-vpn-protect-you-from-hackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/does-vpn-protect-you-from-hackers.html?utm_source=dlvr.it&utm_medium=blogger
STARTTLS Flaws in Email Clients Let Hackers Steak The Credentials From Apple Mail, Gmail, Mozilla Thunderbird
Nearly 40 different vulnerabilities were exposed lately by security researchers that are correlated with an opportunistic encryption mechanism in mail clients and servers. These servers could open the gateway to targeted man-in-the-middle (MitM) attacks, enabling an attackers to trick the mailbox contents and to steal all the important credentials. The experts have detected the flaw […]
The post STARTTLS Flaws in Email Clients Let Hackers Steak The Credentials From Apple Mail, Gmail, Mozilla Thunderbird appeared first on Cyber Security News.
https://cybersecuritynews.com/starttls-flaw-affects-email-clients/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/starttls-flaw-affects-email-clients/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, August 17, 2021
Intezer Analyze Detects MITRE D3FEND™ Techniques
This article has been indexed from Intezer The MITRE Corporation recently released MITRE D3FEND™, a complementary framework to its industry acclaimed MITRE ATT&CK® matrix. D3FEND provides defense techniques that security teams can apply to protect their environments against cyber threats.…
Read more → The post Intezer Analyze Detects MITRE D3FEND™ Techniques first appeared on IT Security News.
https://www.itsecuritynews.info/intezer-analyze-detects-mitre-d3fend-techniques/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/intezer-analyze-detects-mitre-d3fend-techniques/?utm_source=dlvr.it&utm_medium=blogger
Solution Providers Can Now Add Incident Response to Their Services Portfolio For Free
The Incident Response (IR) services market is in accelerated growth due to the rise in cyberattacks that result in breaches. More and more organizations, across all sizes and verticals, choose to outsource IR to 3rd party service providers over handling security incidents in-house. Cynet is now launching a first-of-its-kind offering, enabling any Managed Security Provider (MSP) or Security
https://thehackernews.com/2019/09/msp-incident-response.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2019/09/msp-incident-response.html?utm_source=dlvr.it&utm_medium=blogger
Multiple Flaws Affecting Realtek Wi-Fi SDKs Impact Nearly a Million IoT Devices
Taiwanese chip designer Realtek is warning of four security vulnerabilities in three software development kits (SDKs) accompanying its WiFi modules, which are used in almost 200 IoT devices made by at least 65 vendors. The flaws, which affect Realtek SDK v2.x, Realtek "Jungle" SDK v3.0/v3.1/v3.2/v3.4.x/v3.4T/v3.4T-CT, and Realtek "Luna" SDK up to version 1.3.2, could be abused by attackers to
https://thehackernews.com/2021/08/multiple-flaws-affecting-realtek-wi-fi.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/multiple-flaws-affecting-realtek-wi-fi.html?utm_source=dlvr.it&utm_medium=blogger
Monday, August 16, 2021
A week in security (August 9 – August 15)
This article has been indexed from Malwarebytes Labs
Read more → The post A week in security (August 9 – August 15) first appeared on IT Security News.
https://www.itsecuritynews.info/a-week-in-security-august-9-august-15/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/a-week-in-security-august-9-august-15/?utm_source=dlvr.it&utm_medium=blogger
Strengthening Your WAF Through Manual Penetration Testing
A penetration test, also sometimes referred to as a pen test or a vulnerability assessment, is the term given to a simulated cyber-attack on a computer system that is intended to test out potential vulnerabilities that could be exploited by hackers. Penetration testing is often used for the purpose of augmenting web application firewalls regarding […]
The post Strengthening Your WAF Through Manual Penetration Testing appeared first on Cyber Security News.
https://cybersecuritynews.com/strengthening-your-waf/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/strengthening-your-waf/?utm_source=dlvr.it&utm_medium=blogger
New AdLoad Variant Bypasses Apple's Security Defenses to Target macOS Systems
A new wave of attacks involving a notorious macOS adware family has evolved to leverage around 150 unique samples in the wild in 2021 alone, some of which have slipped past Apple's on-device malware scanner and even signed by its own notarization service, highlighting the malicious software ongoing attempts to adapt and evade detection. "AdLoad," as the malware is known, is one of several
https://thehackernews.com/2021/08/new-adload-variant-bypasses-apples.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/08/new-adload-variant-bypasses-apples.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, August 15, 2021
This Week in Security News – August 13, 2021
This article has been indexed from Trend Micro Simply Security This Week in Security News: Hackers Steal $600 million in Largest Ever Cryptocurrency Heist and Cybersecurity is the New ‘Great Game’ Read the original article: This Week in Security News…
Read more → The post This Week in Security News – August 13, 2021 first appeared on IT Security News.
https://www.itsecuritynews.info/this-week-in-security-news-august-13-2021/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/this-week-in-security-news-august-13-2021/?utm_source=dlvr.it&utm_medium=blogger
Facebook Added an End-to-End Encrypted for Messengers Audio & Video Call
Nowadays the communication over digital mediums are becoming more common, whether it’s for work, personal, or education. And that’s why the users always seek for secure means to keep all their data private. So, to make users feel more secure during their conversations, Facebook has recently announced that it will now start encrypting the voice […]
The post Facebook Added an End-to-End Encrypted for Messengers Audio & Video Call appeared first on Cyber Security News.
https://cybersecuritynews.com/facebook-added-an-end-to-end-encrypted-for-messengers-audio-video-call/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/facebook-added-an-end-to-end-encrypted-for-messengers-audio-video-call/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)