This article has been indexed from Security Affairs Threat actors that hacked Electronic Arts in June have leaked full data dump stolen from the company after the failure of the negotiation with the victim. In June, hackers have compromised the…
Read more → The post Threat actors leaked data stolen from EA, including FIFA code first appeared on IT Security News.
https://www.itsecuritynews.info/threat-actors-leaked-data-stolen-from-ea-including-fifa-code/?utm_source=dlvr.it&utm_medium=blogger
Saturday, July 31, 2021
Top 10 Open Source Cloud Security Tools to Protect Data from Hackers
By seeing the heading of this article, you might be wondering what all about open source cloud? It is a service or solution which got developed by using open source software and technology. These Cloud Security Tools are useful for any public and private models like SaaS, PaaS, laaS, etc. This is completely built and […]
The post Top 10 Open Source Cloud Security Tools to Protect Data from Hackers appeared first on Cyber Security News.
https://cybersecuritynews.com/cloud-security-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cloud-security-tools/?utm_source=dlvr.it&utm_medium=blogger
Oscorp – New Android Credential Stealing Malware Actively Attack in the Wild
Recently, security researchers have found an android malware, and it has been dubbed as Vulture that is a Remote Access Trojan (RAT). According to the report, this malware is violating accessibility services on the targeted devices, so that the attackers can hijack user credentials for European banking. However, this malware is quite dangerous, as it […]
The post Oscorp – New Android Credential Stealing Malware Actively Attack in the Wild appeared first on Cyber Security News.
https://cybersecuritynews.com/oscorp/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/oscorp/?utm_source=dlvr.it&utm_medium=blogger
Friday, July 30, 2021
BehavioSec extends its behavioral biometrics platform into a SOC/ISO compliant SaaS version
This article has been indexed from Help Net Security BehavioSec announced that it has extended its patented technology and BehavioSense platform into a SOC/ISO compliant, hosted-version and a cloud-native, SaaS version. These new versions will help more organizations meet compliance…
Read more → The post BehavioSec extends its behavioral biometrics platform into a SOC/ISO compliant SaaS version first appeared on IT Security News.
https://www.itsecuritynews.info/behaviosec-extends-its-behavioral-biometrics-platform-into-a-soc-iso-compliant-saas-version/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/behaviosec-extends-its-behavioral-biometrics-platform-into-a-soc-iso-compliant-saas-version/?utm_source=dlvr.it&utm_medium=blogger
Beware!! Phone Call Centers Trick Windows Users to Install Malware For Data Exfiltration & Credential Theft
Security researchers from Microsoft observed a new tricks users by attackers to download the BazaLoader malware on windows Users computers through fraudulent call centers, and exfiltrate the sensitive data, credential theft and install the ransomware after 48 hours from the time of initial compromise. The campaign named “BazaCall” also comes with backdoor capabilities, and the […]
The post Beware!! Phone Call Centers Trick Windows Users to Install Malware For Data Exfiltration & Credential Theft appeared first on Cyber Security News.
https://cybersecuritynews.com/beware-phone-call-centers-trick-windows-users-to-install-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/beware-phone-call-centers-trick-windows-users-to-install-malware/?utm_source=dlvr.it&utm_medium=blogger
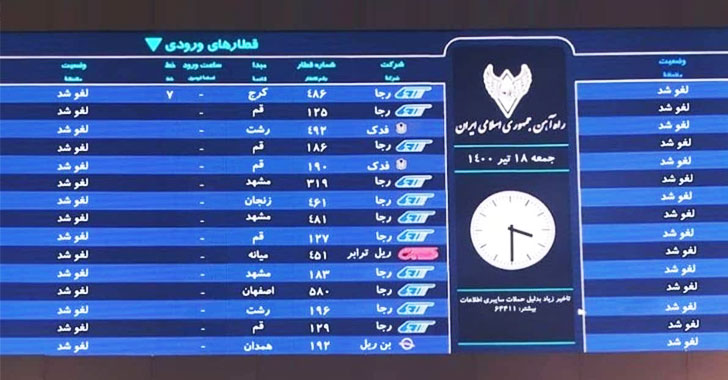
A New Wiper Malware Was Behind Recent Cyberattack On Iranian Train System
A cyber attack that derailed websites of Iran's transport ministry and its national railway system earlier this month, causing widespread disruptions in train services, was the result of a never-before-seen reusable wiper malware called "Meteor." The campaign — dubbed "MeteorExpress" — has not been linked to any previously identified threat group or to additional attacks, making it the first
https://thehackernews.com/2021/07/a-new-wiper-malware-was-behind-recent.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/a-new-wiper-malware-was-behind-recent.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, July 29, 2021
Best Practices to Thwart Business Email Compromise (BEC) Attacks
Business email compromise (BEC) refers to all types of email attacks that do not have payloads. Although there are numerous types, there are essentially two main mechanisms through which attackers penetrate organizations utilizing BEC techniques, spoofing and account take-over attacks. In a recent study, 71% of organizations acknowledged they had seen a business email compromise (BEC) attack
https://thehackernews.com/2021/07/best-practices-to-thwart-business-email_29.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/best-practices-to-thwart-business-email_29.html?utm_source=dlvr.it&utm_medium=blogger
What is a Supply Chain Attack? How Attackers Use that to Compromise Organization Security
You might be wondering how the supply chain attack works? First, let us tell you that this is one type of cyber-attack that targets the organization by focusing on its weaker link. This network includes all the organization, technology, individual, resources, many other things. All are involved in creating and selling the product. This supply […]
The post What is a Supply Chain Attack? How Attackers Use that to Compromise Organization Security appeared first on Cyber Security News.
https://cybersecuritynews.com/supply-chain-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/supply-chain-attack/?utm_source=dlvr.it&utm_medium=blogger
LG To Sell Apple iPhones In Stores, After Phone Exit
This article has been indexed from Silicon UK Two months after it made its last ever smartphone, LG Electronics will begin selling Apple iPhones in its South Korean stores Read the original article: LG To Sell Apple iPhones In Stores,…
Read more → The post LG To Sell Apple iPhones In Stores, After Phone Exit first appeared on IT Security News.
https://www.itsecuritynews.info/lg-to-sell-apple-iphones-in-stores-after-phone-exit/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/lg-to-sell-apple-iphones-in-stores-after-phone-exit/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, July 28, 2021
New Flaw Let Hackers Take Over Zimbra Server Sending Malicious Email
Zimbra offers the most innovative messaging experience, connecting end-users to the information and activity in personal clouds. It is used by over 200,000 businesses and over a thousand government & financial institutions to exchange emails between millions of users every day. Experts from SonarSource have disclosed two vulnerabilities in the open-source Zimbra code. These vulnerabilities […]
The post New Flaw Let Hackers Take Over Zimbra Server Sending Malicious Email appeared first on Cyber Security News.
https://cybersecuritynews.com/zimbra-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/zimbra-flaw/?utm_source=dlvr.it&utm_medium=blogger
UBEL is the New Oscorp — Android Credential Stealing Malware Active in the Wild
An Android malware that was observed abusing accessibility services in the device to hijack user credentials from European banking applications has morphed into an entirely new botnet as part of a renewed campaign that began in May 2021. Italy's CERT-AGID, in late January, disclosed details about Oscorp, a mobile malware developed to attack multiple financial targets with the goal of stealing
https://thehackernews.com/2021/07/ubel-is-new-oscorp-android-credential.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/ubel-is-new-oscorp-android-credential.html?utm_source=dlvr.it&utm_medium=blogger
What is Access Control and its Importance in Cyber Security?
Are you wondering what access control is? Then here, you will get the answer. This is the security technique that minimizes the risk of the organization in a computing environment. Access control can work in two types, physical and logical. Physical access control is limited with campus, rooms, buildings, physical IT assets, etc. Logical limits […]
The post What is Access Control and its Importance in Cyber Security? appeared first on Cyber Security News.
https://cybersecuritynews.com/access-control/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/access-control/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, July 27, 2021
Apple Releases Urgent 0-Day Bug Patch for Mac, iPhone and iPad Devices
Apple on Monday rolled out an urgent security update for iOS, iPadOS, and macOS to address a zero-day flaw that it said may have been actively exploited, making it the thirteenth such vulnerability Apple has patched since the start of this year. The updates, which arrive less than a week after the company released iOS 14.7, iPadOS 14.7, and macOS Big Sur 11.5 to the public, fixes a memory
https://thehackernews.com/2021/07/apple-releases-urgent-0-day-bug-patch.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/apple-releases-urgent-0-day-bug-patch.html?utm_source=dlvr.it&utm_medium=blogger
CODESYS Patches Dozen Vulnerabilities in Industrial Automation Products
This article has been indexed from SecurityWeek RSS Feed Industrial automation software provider CODESYS this month informed customers about a dozen vulnerabilities affecting various products. More than half of these flaws were discovered by Cisco Talos and their details were…
Read more → The post CODESYS Patches Dozen Vulnerabilities in Industrial Automation Products first appeared on IT Security News.
https://www.itsecuritynews.info/codesys-patches-dozen-vulnerabilities-in-industrial-automation-products/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/codesys-patches-dozen-vulnerabilities-in-industrial-automation-products/?utm_source=dlvr.it&utm_medium=blogger
What is Kerberos Authentication, How it Works, and its Advantages?
Kerberos authentication is a cryptography-based protocol that is used to secure logins. The Kerberos is a mythological three-headed Greek creature. It guards the gates to prevent the soul from escaping. Due to this inspection, the Massachusetts Institute of Technology has developed a protocol to protect their project. Their main idea behind the Kerberos is to […]
The post What is Kerberos Authentication, How it Works, and its Advantages? appeared first on Cyber Security News.
https://cybersecuritynews.com/kerberos-authentication/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/kerberos-authentication/?utm_source=dlvr.it&utm_medium=blogger
Monday, July 26, 2021
Black Hat USA & DEFCON 2021 Coverage on LinuxSecurity: What You Need to Know>
This article has been indexed from LinuxSecurity.com – Hybrid RSS To say that it’s an exciting time in the cybersecurity community is an understatement! Two of the most prestigious cybersecurity conferences – Black Hat USA 2021 and DEF CON –…
Read more → The post Black Hat USA & DEFCON 2021 Coverage on LinuxSecurity: What You Need to Know> first appeared on IT Security News.
https://www.itsecuritynews.info/black-hat-usa-defcon-2021-coverage-on-linuxsecurity-what-you-need-to-know/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/black-hat-usa-defcon-2021-coverage-on-linuxsecurity-what-you-need-to-know/?utm_source=dlvr.it&utm_medium=blogger
What is an Evil Twin Attack – Example, Procedure, and Preventive Methods
By listing this name, you might have thought that Evil twin is some staff of the horror movies, but this is not the thing, it is a thing of the online world, where they try to steal your sensitive details while browsing something in public Wi-Fi. In this article, you will know what is all […]
The post What is an Evil Twin Attack – Example, Procedure, and Preventive Methods appeared first on Cyber Security News.
https://cybersecuritynews.com/evil-twin/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/evil-twin/?utm_source=dlvr.it&utm_medium=blogger
New PetitPotam NTLM Relay Attack Lets Hackers Take Over Windows Domains
A newly uncovered security flaw in the Windows operating system can be exploited to coerce remote Windows servers, including Domain Controllers, to authenticate with a malicious destination, thereby allowing an adversary to stage an NTLM relay attack and completely take over a Windows domain. The issue, dubbed "PetitPotam," was discovered by security researcher Gilles Lionel, who shared
https://thehackernews.com/2021/07/new-petitpotam-ntlm-relay-attack-lets.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/new-petitpotam-ntlm-relay-attack-lets.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, July 25, 2021
AST New 100% Mobile Friendly Magazine Now Live (Multi-Video)
This article has been indexed from Cyber Security – American Security Today American Security Today is pleased to announce their newest 100% mobile-friendly Digital Magazine is ready for viewing, and includes the following featured articles: Why CAMERAS MAY NOT BE…
Read more → The post AST New 100% Mobile Friendly Magazine Now Live (Multi-Video) first appeared on IT Security News.
https://www.itsecuritynews.info/ast-new-100-mobile-friendly-magazine-now-live-multi-video/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ast-new-100-mobile-friendly-magazine-now-live-multi-video/?utm_source=dlvr.it&utm_medium=blogger
Fraud-as-a-Service – 2 Hackers Arrested by Dutch Cops for Sells & Rents Sophisticated Phishing Kits
Recently, the Dutch cops in the association of Group-IB have arrested two hackers for their testified association in a phishing fraud-as-a-service scheme. The report also claims that these two hackers have been selling and renting all complex phishing frameworks. After detecting the attack, the police claimed that one of the suspects is a 24-year-old software […]
The post Fraud-as-a-Service – 2 Hackers Arrested by Dutch Cops for Sells & Rents Sophisticated Phishing Kits appeared first on Cyber Security News.
https://cybersecuritynews.com/fraud-as-a-service/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/fraud-as-a-service/?utm_source=dlvr.it&utm_medium=blogger
Cybersecurity Professionals to Newcomers: Focus on Vendor-Neutral Certifications
This article has been indexed from Cybersecurity Insiders Cybersecurity professionals are far more likely to hold vendor-specific certificates than certifications from a vendor-neutral association or standards-based organization, according to the (ISC)² Cybersecurity Career Pursuers Study. But when asked which qualifications…
Read more → The post Cybersecurity Professionals to Newcomers: Focus on Vendor-Neutral Certifications first appeared on IT Security News.
https://www.itsecuritynews.info/cybersecurity-professionals-to-newcomers-focus-on-vendor-neutral-certifications-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cybersecurity-professionals-to-newcomers-focus-on-vendor-neutral-certifications-2/?utm_source=dlvr.it&utm_medium=blogger
Saturday, July 24, 2021
IT Security News Daily Summary 2021-07-24
XKCD ‘Immune Factory’ BSides Vancouver 2021 – Marek Mikita’s ‘Sysmon Monitoring Different Way’ macOS Malware Added New Weapons to Its Arsenal To Attack Google Chrome & Telegram Japanese computers hit by a wiper malware ahead of 2021 Tokyo Olympics CISSPs…
Read more → The post IT Security News Daily Summary 2021-07-24 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-07-24/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-07-24/?utm_source=dlvr.it&utm_medium=blogger
Porn Showed Upon on Legit News Sites Thanks to Internet Rot
This article has been indexed from Security Latest Plus: China’s pipeline probing, a Chromebook debacle, and more of the week’s top security news. Read the original article: Porn Showed Upon on Legit News Sites Thanks to Internet Rot
Read more → The post Porn Showed Upon on Legit News Sites Thanks to Internet Rot first appeared on IT Security News.
https://www.itsecuritynews.info/porn-showed-upon-on-legit-news-sites-thanks-to-internet-rot/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/porn-showed-upon-on-legit-news-sites-thanks-to-internet-rot/?utm_source=dlvr.it&utm_medium=blogger
Girl Scouts Safeguards Data with BlackFog
This article has been indexed from Security Boulevard Girl Scouts North Carolina Coastal Pines serves 35,000+ girls and volunteers in 41 counties in central and eastern North Carolina, During the evaluation phase they quickly discovered that BlackFog was filling a…
Read more → The post Girl Scouts Safeguards Data with BlackFog first appeared on IT Security News.
https://www.itsecuritynews.info/girl-scouts-safeguards-data-with-blackfog/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/girl-scouts-safeguards-data-with-blackfog/?utm_source=dlvr.it&utm_medium=blogger
Friday, July 23, 2021
Flashpoint collaborates with Cybermerc to enhance its threat intelligence solution
This article has been indexed from Help Net Security Flashpoint announces a partnership with the Australian threat intelligence services provider Cybermerc. The partnership features a joint solution making Flashpoint’s advanced threat intelligence available in Cybermerc service offerings and acts as…
Read more → The post Flashpoint collaborates with Cybermerc to enhance its threat intelligence solution first appeared on IT Security News.
https://www.itsecuritynews.info/flashpoint-collaborates-with-cybermerc-to-enhance-its-threat-intelligence-solution/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/flashpoint-collaborates-with-cybermerc-to-enhance-its-threat-intelligence-solution/?utm_source=dlvr.it&utm_medium=blogger
Nasty macOS Malware XCSSET Now Targets Google Chrome, Telegram Software
A malware known for targeting macOS operating system has been updated once again to add more features to its toolset that allows it to amass and exfiltrate sensitive data stored in a variety of apps, including apps such as Google Chrome and Telegram, as part of further "refinements in its tactics." XCSSET was uncovered in August 2020, when it was found targeting Mac developers using an unusual
https://thehackernews.com/2021/07/nasty-macos-malware-xcsset-now-targets.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/nasty-macos-malware-xcsset-now-targets.html?utm_source=dlvr.it&utm_medium=blogger
Top 10 Cyber Attack Maps to See Digital Threats 2021
With the help of Bromium, we get to know that digital crime result has increased to 1.5 trillion dollars yearly in illegal earnings. In this article, we list the Cyber Attack Maps. Now many of you might be thinking that what Bromium is? Let me tell you guys that it is a startup company that […]
The post Top 10 Cyber Attack Maps to See Digital Threats 2021 appeared first on Cyber Security News.
https://cybersecuritynews.com/cyber-attack-maps/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cyber-attack-maps/?utm_source=dlvr.it&utm_medium=blogger
Thursday, July 22, 2021
GTT’s portal feature provides expanded visibility into network security and performance
This article has been indexed from Help Net Security GTT Communications has announced the addition of the Secure Co-Manage feature to its EtherVision portal to provide customers with enhanced network security visibility and the ability to make real-time changes to…
Read more → The post GTT’s portal feature provides expanded visibility into network security and performance first appeared on IT Security News.
https://www.itsecuritynews.info/gtts-portal-feature-provides-expanded-visibility-into-network-security-and-performance/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/gtts-portal-feature-provides-expanded-visibility-into-network-security-and-performance/?utm_source=dlvr.it&utm_medium=blogger
Pegasus Project investigation uncovers the reach and implications of NSO Group spyware
This article has been indexed from Security Boulevard On Sunday, the first reports were published under the banner of the Pegasus Project, revealing the results of an investigation into how NSO Group’s military-grade spyware has been used to hack the…
Read more → The post Pegasus Project investigation uncovers the reach and implications of NSO Group spyware first appeared on IT Security News.
https://www.itsecuritynews.info/pegasus-project-investigation-uncovers-the-reach-and-implications-of-nso-group-spyware/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/pegasus-project-investigation-uncovers-the-reach-and-implications-of-nso-group-spyware/?utm_source=dlvr.it&utm_medium=blogger
Another Hacker Arrested for 2020 Twitter Hack and Massive Bitcoin Scam
A U.K. citizen has been arrested in the Spanish town of Estepona over his alleged involvement in the July 2020 hack of Twitter, resulting in the compromise of 130 high-profile accounts. Joseph O'Connor, 22, has been charged with intentionally accessing a computer without authorization and obtaining information from a protected computer, as well as for making extortive communications. The Spanish
https://thehackernews.com/2021/07/another-hacker-arrested-for-2020.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/another-hacker-arrested-for-2020.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, July 21, 2021
16-Year-Old Security Bug Affects Millions of HP, Samsung, Xerox Printers
Details have emerged about a high severity security vulnerability affecting a software driver used in HP, Xerox, and Samsung printers that has remained undetected since 2005. Tracked as CVE-2021-3438 (CVSS score: 8.8), the issue concerns a buffer overflow in a print driver installer package named "SSPORT.SYS" that can enable remote privilege and arbitrary code execution. Hundreds of millions of
https://thehackernews.com/2021/07/16-year-old-security-bug-affects.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/16-year-old-security-bug-affects.html?utm_source=dlvr.it&utm_medium=blogger
New to GovCloud: Falcon Managed Detection and Response Transforms Government Security
This article has been indexed from https://www.crowdstrike.com/blog/feed Public sector organizations continue to deal with a threat landscape unlike any we’ve seen before. They’re being targeted in increasingly stealthy and sophisticated cyberattacks from both nation-state and eCrime adversaries. And at the…
Read more → The post New to GovCloud: Falcon Managed Detection and Response Transforms Government Security first appeared on IT Security News.
https://www.itsecuritynews.info/new-to-govcloud-falcon-managed-detection-and-response-transforms-government-security/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/new-to-govcloud-falcon-managed-detection-and-response-transforms-government-security/?utm_source=dlvr.it&utm_medium=blogger
Phone Of France’s Macron Targetted By NSO Pegasus – Report
This article has been indexed from Silicon UK French President Emmanuel Macron among world leaders whose phones were allegedly targetted by NSO Group’s Pegasus ‘spyware’ Read the original article: Phone Of France’s Macron Targetted By NSO Pegasus – Report
Read more → The post Phone Of France’s Macron Targetted By NSO Pegasus – Report first appeared on IT Security News.
https://www.itsecuritynews.info/phone-of-frances-macron-targetted-by-nso-pegasus-report/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/phone-of-frances-macron-targetted-by-nso-pegasus-report/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, July 20, 2021
Massive Data Leak Exposed a Pegasus spyware Used to Hack Cellphones of Journalists Globally
Recently, in a serious investigation, several security experts from the Guardian and The Washington Post along with Amnesty International and Forbidden Stories have detected traces of Pegasus spyware in journalists’ cellphones, that was being produced by the Israeli company NSO Group. After the investigation, the experts have found that the Pegasus spyware has generated a […]
The post Massive Data Leak Exposed a Pegasus spyware Used to Hack Cellphones of Journalists Globally appeared first on Cyber Security News.
https://cybersecuritynews.com/massive-data-leak-exposed-a-pegasus-spyware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/massive-data-leak-exposed-a-pegasus-spyware/?utm_source=dlvr.it&utm_medium=blogger
Supply chain attacks: Top 5 things to know
This article has been indexed from Security on TechRepublic Worried about supply chain attacks? Tom Merritt has answers for you. Read the original article: Supply chain attacks: Top 5 things to know
Read more → The post Supply chain attacks: Top 5 things to know first appeared on IT Security News.
https://www.itsecuritynews.info/supply-chain-attacks-top-5-things-to-know/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/supply-chain-attacks-top-5-things-to-know/?utm_source=dlvr.it&utm_medium=blogger
This New Malware Hides Itself Among Windows Defender Exclusions to Evade Detection
Cybersecurity researchers on Tuesday lifted the lid on a previously undocumented malware strain dubbed "MosaicLoader" that singles out individuals searching for cracked software as part of a global campaign. "The attackers behind MosaicLoader created a piece of malware that can deliver any payload on the system, making it potentially profitable as a delivery service," Bitdefender researchers
https://thehackernews.com/2021/07/this-new-malware-hides-itself-among.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/this-new-malware-hides-itself-among.html?utm_source=dlvr.it&utm_medium=blogger
Monday, July 19, 2021
Fast Radius merges with ECP Environmental Growth Opportunities to become a publicly-listed company
This article has been indexed from Help Net Security Fast Radius and ECP Environmental Growth Opportunities (ENNV) have entered into a definitive agreement that will result in Fast Radius becoming a publicly-listed company. Purpose-built software and technology firm fostering sustainable…
Read more → The post Fast Radius merges with ECP Environmental Growth Opportunities to become a publicly-listed company first appeared on IT Security News.
https://www.itsecuritynews.info/fast-radius-merges-with-ecp-environmental-growth-opportunities-to-become-a-publicly-listed-company/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/fast-radius-merges-with-ecp-environmental-growth-opportunities-to-become-a-publicly-listed-company/?utm_source=dlvr.it&utm_medium=blogger
Researchers Warn of Linux Cryptojacking Attackers Operating from Romania
A threat group likely based in Romania and active since at least 2020 has been behind an active cryptojacking campaign targeting Linux-based machines with a previously undocumented SSH brute-forcer written in Golang. Dubbed "Diicot brute," the password cracking tool is alleged to be distributed via a software-as-a-service model, with each threat actor furnishing their own unique API keys to
https://thehackernews.com/2021/07/researchers-warn-of-linux-cryptojacking.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/researchers-warn-of-linux-cryptojacking.html?utm_source=dlvr.it&utm_medium=blogger
D-Link Critical Flaw Let Attackers Execute Arbitrary Code And Obtain Sensitive Information
Cisco Talos, the threat intelligence research team of Cisco has recently identified and uncovered several critical security flaws in the router of D-LINK, DIR-3040, it’s an AC3000-based wireless internet router. By exploiting the detected bugs, an attacker can easily execute arbitrary code to gain access to the confidential data, and not only that even also […]
The post D-Link Critical Flaw Let Attackers Execute Arbitrary Code And Obtain Sensitive Information appeared first on Cyber Security News.
https://cybersecuritynews.com/d-link-critical-flaw-let-attackers-execute-arbitrary-code/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/d-link-critical-flaw-let-attackers-execute-arbitrary-code/?utm_source=dlvr.it&utm_medium=blogger
Sunday, July 18, 2021
Top 10 Best Free Penetration Testing Tools 2021
When we talk about the penetration Testing tools, we all know very well that the first thing that comes up to our mind is the threat. As we all know very well that we use penetration testing and hacking tools for recognizing security vulnerabilities in a network, server, or in a web application. Generally, all […]
The post Top 10 Best Free Penetration Testing Tools 2021 appeared first on Cyber Security News.
https://cybersecuritynews.com/penetration-testing-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/penetration-testing-tools/?utm_source=dlvr.it&utm_medium=blogger
Chinese government issues new vulnerability disclosure regulations
This article has been indexed from Security Affairs Cyberspace Administration of China (CAC) issued new vulnerability disclosure regulations that oblige experts to report zero-days to the government. The Cyberspace Administration of China (CAC) has issued a new exacerbated vulnerability disclosure…
Read more → The post Chinese government issues new vulnerability disclosure regulations first appeared on IT Security News.
https://www.itsecuritynews.info/chinese-government-issues-new-vulnerability-disclosure-regulations/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/chinese-government-issues-new-vulnerability-disclosure-regulations/?utm_source=dlvr.it&utm_medium=blogger
Experts: the volume of cryptocurrency fraud in the world has reached $1 billion in a year
This article has been indexed from E Hacking News – Latest Hacker News and IT Security News In the last year, at least $1 billion worth of digital currency was stolen worldwide. The number of extortion cases since the beginning…
Read more → The post Experts: the volume of cryptocurrency fraud in the world has reached $1 billion in a year first appeared on IT Security News.
https://www.itsecuritynews.info/experts-the-volume-of-cryptocurrency-fraud-in-the-world-has-reached-1-billion-in-a-year/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/experts-the-volume-of-cryptocurrency-fraud-in-the-world-has-reached-1-billion-in-a-year/?utm_source=dlvr.it&utm_medium=blogger
Saturday, July 17, 2021
Larry Prior joins Shift5 Board of Directors
This article has been indexed from Help Net Security Shift5 announces Larry Prior joins as the latest addition to their Board of Directors. Larry Prior currently serves as an Operating Executive for The Carlyle Group, where he is focused on…
Read more → The post Larry Prior joins Shift5 Board of Directors first appeared on IT Security News.
https://www.itsecuritynews.info/larry-prior-joins-shift5-board-of-directors/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/larry-prior-joins-shift5-board-of-directors/?utm_source=dlvr.it&utm_medium=blogger
CloudFlare CDNJS Bug Could Have Led to Widespread Supply-Chain Attacks
Web infrastructure and website security company Cloudflare last month fixed a critical vulnerability in its CDNJS library that's used by 12.7% of all websites on the internet. CDNJS is a free and open-source content delivery network (CDN) that serves about 4,041 JavaScript and CSS libraries, making it the second most popular CDN for JavaScript after Google Hosted Libraries. The weakness
https://thehackernews.com/2021/07/cloudflare-cdnjs-bug-could-have-led-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/cloudflare-cdnjs-bug-could-have-led-to.html?utm_source=dlvr.it&utm_medium=blogger
New Unpatched Windows Print Spooler Bug Let Hackers Exploit The Elevation of Privilege
Microsoft issued a new security warning about the unpatched Windows Print Spooler Elevation of privilege vulnerability that allows attackers to execute an arbitrary code with the system privileges’. “The print spooler service is a service that is running on each computer that participates in the Print Services system. The print spooler service implements the print client and print server roles, by […]
The post New Unpatched Windows Print Spooler Bug Let Hackers Exploit The Elevation of Privilege appeared first on Cyber Security News.
https://cybersecuritynews.com/new-unpatched-windows-print-spooler-bug/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/new-unpatched-windows-print-spooler-bug/?utm_source=dlvr.it&utm_medium=blogger
Friday, July 16, 2021
Amazon asked Apple to remove an app that spots fake reviews, and Apple agreed
This article has been indexed from Cybersecurity Fakespot is a well-known app used to help shoppers detect fraudulent reviews on Amazon. Read the original article: Amazon asked Apple to remove an app that spots fake reviews, and Apple agreed
Read more → The post Amazon asked Apple to remove an app that spots fake reviews, and Apple agreed first appeared on IT Security News.
https://www.itsecuritynews.info/amazon-asked-apple-to-remove-an-app-that-spots-fake-reviews-and-apple-agreed/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/amazon-asked-apple-to-remove-an-app-that-spots-fake-reviews-and-apple-agreed/?utm_source=dlvr.it&utm_medium=blogger
The Definitive RFP Templates for EDR/EPP and APT Protection
Advanced Persistent Threats groups were once considered a problem that concerns Fortune 100 companies only. However, the threat landscape of the recent years tells otherwise—in fact, every organization, regardless of vertical and size is at risk, whether as a direct target, supply chain or collateral damage. The vast majority of security decision-makers acknowledge they need to address the APT
https://thehackernews.com/2019/09/rfp-templates-for-edr-epp.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2019/09/rfp-templates-for-edr-epp.html?utm_source=dlvr.it&utm_medium=blogger
Update Your Chrome Browser to Patch New Zero‑Day Bug Exploited in the Wild
Google has pushed out a new security update to Chrome browser for Windows, Mac, and Linux with multiple fixes, including a zero-day that it says is being exploited in the wild. The latest patch resolves a total of eight issues, one of which concerns a type confusion issue in its V8 open-source and JavaScript engine (CVE-2021-30563). The search giant credited an anonymous researcher for reporting
https://thehackernews.com/2021/07/update-your-chrome-browser-to-patch-new.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/update-your-chrome-browser-to-patch-new.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, July 15, 2021
The Tower of Babel: How Public Interest Internet is Trying to Save Messaging and Banish Big Social Media
This article has been indexed from Deeplinks This blog post is part of a series, looking at the public interest internet—the parts of the internet that don’t garner the headlines of Facebook or Google, but quietly provide public goods and…
Read more → The post The Tower of Babel: How Public Interest Internet is Trying to Save Messaging and Banish Big Social Media first appeared on IT Security News.
https://www.itsecuritynews.info/the-tower-of-babel-how-public-interest-internet-is-trying-to-save-messaging-and-banish-big-social-media/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-tower-of-babel-how-public-interest-internet-is-trying-to-save-messaging-and-banish-big-social-media/?utm_source=dlvr.it&utm_medium=blogger
China's Cyberspies Targeting Southeast Asian Government Entities
A sweeping and "highly active campaign" that originally set its sights on Myanmar has broadened its focus to strike a number of targets located in the Philippines, according to new research. Russian cybersecurity firm Kaspersky, which first spotted the infections in October 2020, attributed them to a threat actor it tracks as "LuminousMoth," which it connected with medium to high confidence to a
https://thehackernews.com/2021/07/chinas-cyberspies-targeting-southeast.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/07/chinas-cyberspies-targeting-southeast.html?utm_source=dlvr.it&utm_medium=blogger
Romanian Hackers Actively Attacking Linux-based Machines With Weak SSH Credentials
Researchers uncovered a new active crypto-jacking attack from the APT threat group targeting Linux-based machines by taking advantage of the weak SSH credentials to deploy the crypto-malware to mine Monero cryptocurrency. To mine cryptocurrency, attackers targeting third-party home computers or work computers are compromised and hijacked to utilize their resources known as a crypto-jacking attack. […]
The post Romanian Hackers Actively Attacking Linux-based Machines With Weak SSH Credentials appeared first on Cyber Security News.
https://cybersecuritynews.com/romanian-hackers-actively-attacking-linux-based-machines/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/romanian-hackers-actively-attacking-linux-based-machines/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)