This article has been indexed from Help Net Security Fujitsu is collaborating with the Telecom Infra Project (TIP) OpenRAN Project Group to accelerate adoption of open radio access network infrastructure, helping service providers speed new 5G services to market at…
Read more → The post Fujitsu and Telecom Infra Project deliver Open RAN-compliant multi-band 5G radios first appeared on IT Security News.
https://www.itsecuritynews.info/fujitsu-and-telecom-infra-project-deliver-open-ran-compliant-multi-band-5g-radios/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, June 30, 2021
[Webinar] How Cyber Attack Groups Are Spinning a Larger Ransomware Web
Organizations today already have an overwhelming number of dangers and threats to look out for, from spam to phishing attempts to new infiltration and ransomware tactics. There is no chance to rest, since attack groups are constantly looking for more effective means of infiltrating and infecting systems. Today, there are hundreds of groups devoted to infiltrating almost every industry,
https://thehackernews.com/2021/06/webinar-how-cyber-attack-groups-are.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/webinar-how-cyber-attack-groups-are.html?utm_source=dlvr.it&utm_medium=blogger
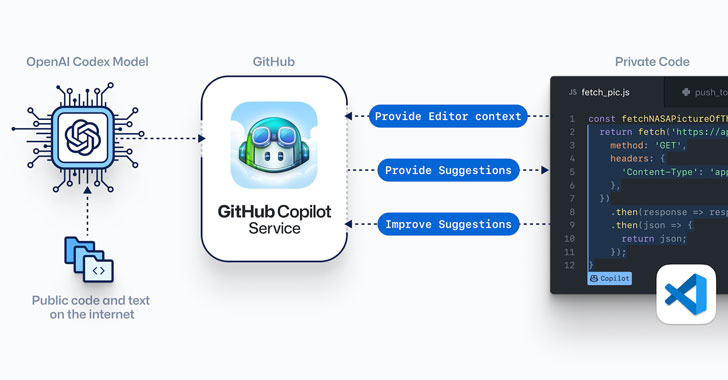
GitHub Launches 'Copilot' — AI-Powered Code Completion Tool
GitHub on Tuesday launched a technical preview of a new AI-powered pair programming tool that aims to help software developers write better code across a variety of programming languages, including Python, JavaScript, TypeScript, Ruby, and Go. Copilot, as the code synthesizer is called, has been developed in collaboration with OpenAI, and leverages Codex, a new AI system that's trained on
https://thehackernews.com/2021/06/github-launches-copilot-ai-powered-code.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/github-launches-copilot-ai-powered-code.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, June 29, 2021
JFrog to acquire Vdoo to expand its end-to-end DevOps platform offering
This article has been indexed from Help Net Security JFrog announced that it has entered into a definitive agreement to acquire Vdoo Connected Trust in a cash and stock-based deal valued at approximately $300 million. JFrog has accelerated its efforts…
Read more → The post JFrog to acquire Vdoo to expand its end-to-end DevOps platform offering first appeared on IT Security News.
https://www.itsecuritynews.info/jfrog-to-acquire-vdoo-to-expand-its-end-to-end-devops-platform-offering/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/jfrog-to-acquire-vdoo-to-expand-its-end-to-end-devops-platform-offering/?utm_source=dlvr.it&utm_medium=blogger
Data of Over 700M LinkedIn Users Posted on Hacker Forum For Sale
700 Million LinkedIn Records For Sale on Hacker Forum, June 22nd 2021! LinkedIn has again hit with massive data breaches and user data of over 700 million of LinkedIn’s users has been scraped from the platform and posted online for sale. This is encountered the second time after the first breach which was disclosed in […]
The post Data of Over 700M LinkedIn Users Posted on Hacker Forum For Sale appeared first on Cyber Security News.
https://cybersecuritynews.com/700m-linkedin-users/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/700m-linkedin-users/?utm_source=dlvr.it&utm_medium=blogger
What is Pretexting? Simple & Effective Social Engineering Attack
Before you know about pretexting, you must understand that it is one type of social engineering attack. Now, are you wondering what social engineering attack is? It mainly accounts for the massive portion of cyberattacks where studies show that the attack always rising. Most of the 90% of hacks start from the social engineering attack. What […]
The post What is Pretexting? Simple & Effective Social Engineering Attack appeared first on Cyber Security News.
https://cybersecuritynews.com/pretexting/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/pretexting/?utm_source=dlvr.it&utm_medium=blogger
Monday, June 28, 2021
Cisco flaw under attack after researchers publish exploit PoC
This article has been indexed from HITBSecNews – Keeping Knowledge Free for Over a Decade Cisco flaw under attack after researchers publish exploit PoC l33tdawg Tue, 06/29/2021 – 00:08 Read the original article: Cisco flaw under attack after researchers publish…
Read more → The post Cisco flaw under attack after researchers publish exploit PoC first appeared on IT Security News.
https://www.itsecuritynews.info/cisco-flaw-under-attack-after-researchers-publish-exploit-poc/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cisco-flaw-under-attack-after-researchers-publish-exploit-poc/?utm_source=dlvr.it&utm_medium=blogger
SolarWinds Hackers Breach Microsoft Customer Support to Target its Customers
In yet another sign that the Russian hackers who breached SolarWinds network monitoring software to compromise a slew of entities never really went away, Microsoft said the threat actor behind the malicious cyber activities used password spraying and brute-force attacks in an attempt to guess passwords and gain access to its customer accounts. "This recent activity was mostly unsuccessful, and
https://thehackernews.com/2021/06/solarwinds-hackers-breach-microsoft.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/solarwinds-hackers-breach-microsoft.html?utm_source=dlvr.it&utm_medium=blogger
Cyber Workforce: Gender Diversity Challenges
This article has been indexed from The State of Security Over the years, there have been many news headlines, policy reports, white papers, and corporate newsletters that have highlighted cybersecurity workforce challenges; namely, the global shortage of cybersecurity professionals. Some of…
Read more → The post Cyber Workforce: Gender Diversity Challenges first appeared on IT Security News.
https://www.itsecuritynews.info/cyber-workforce-gender-diversity-challenges/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cyber-workforce-gender-diversity-challenges/?utm_source=dlvr.it&utm_medium=blogger
Sunday, June 27, 2021
IT Security News Daily Summary 2021-06-27
DIY CD/DVD Destruction, (Sun, Jun 27th) How the United States Can Compete with Chinese Influence in Southeast Asia NOBELIUM Hackers Gain Access To The Microsoft Networks via Hacked Employee Computer The Case for Open XDR – X Means Everything How…
Read more → The post IT Security News Daily Summary 2021-06-27 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-06-27/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-06-27/?utm_source=dlvr.it&utm_medium=blogger
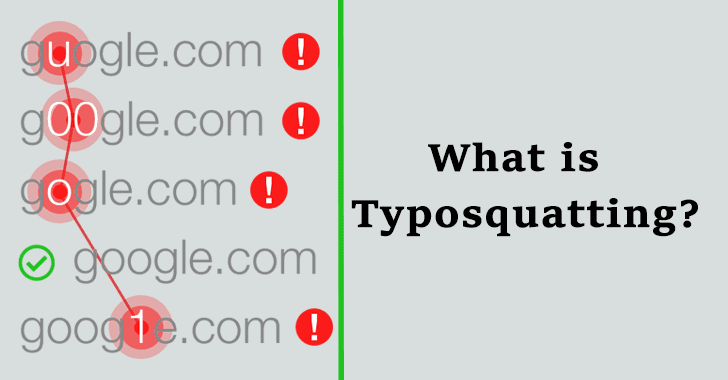
What is Typosquatting? Simple & Effective Hacking Technique
Before you know about typosquatting, you need to make sure that you have enough knowledge about social engineering. This is a technological defenses which cybercriminals are using for transferring money, collecting sensitive information, and other activity. This can be used in both ways online and offline. Typosquatting is the social engineering attack that targets the […]
The post What is Typosquatting? Simple & Effective Hacking Technique appeared first on Cyber Security News.
https://cybersecuritynews.com/typosquatting/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/typosquatting/?utm_source=dlvr.it&utm_medium=blogger
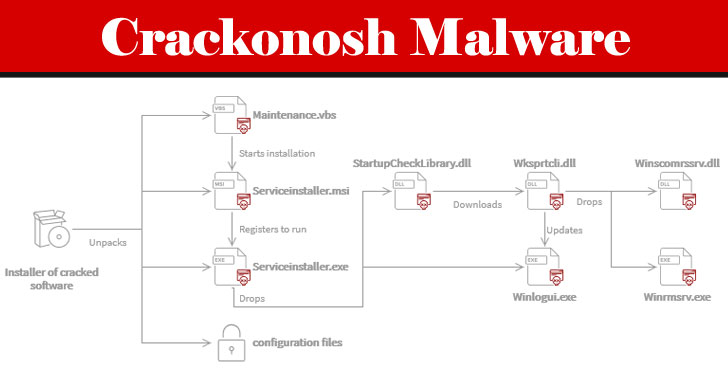
222,000 Computers Worldwide Hacked To Mine Monero Cryptocurrency
Researchers from Avast say the “Crackonosh” malware has been living in the 222,000 computers worldwide, which have installed the cracked version of the games from Torrent. Some of them are “Grand Theft Auto V” and “NBA 2k19.” Crackonosh is distributed along with illegal, cracked copies of popular software and searches for and disables many popular […]
The post 222,000 Computers Worldwide Hacked To Mine Monero Cryptocurrency appeared first on Cyber Security News.
https://cybersecuritynews.com/crackonosh-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/crackonosh-malware/?utm_source=dlvr.it&utm_medium=blogger
Saturday, June 26, 2021
SolarWinds backdoor gang now pwns Microsoft support agent to turn sights on customers
This article has been indexed from The Register – Security Plus: Amazon gobbles Wickr, automakers cough to privacy blunders, and more In Brief The spies who backdoored SolarWinds’ Orion software also infiltrated Microsoft’s support desk systems last month to obtain…
Read more → The post SolarWinds backdoor gang now pwns Microsoft support agent to turn sights on customers first appeared on IT Security News.
https://www.itsecuritynews.info/solarwinds-backdoor-gang-now-pwns-microsoft-support-agent-to-turn-sights-on-customers/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/solarwinds-backdoor-gang-now-pwns-microsoft-support-agent-to-turn-sights-on-customers/?utm_source=dlvr.it&utm_medium=blogger
What are Red Teaming, Tactics & How Does it Works?
You might have heard about Red Teaming, but you might be wondering what it is all about? It is a practice of security testing for your system through which you can try to hack. The red team can be externally contracted in a group of pen tester in your organization. The red teaming central role […]
The post What are Red Teaming, Tactics & How Does it Works? appeared first on Cyber Security News.
https://cybersecuritynews.com/red-teaming/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/red-teaming/?utm_source=dlvr.it&utm_medium=blogger
Critical Flaws In The Atlassian Project Let Attackers Take Over Control Of Accounts And Apps
Check Point Research (CPR) revealed critical vulnerabilities in the Atlassian project that allow attackers to take over control of accounts and Atlassian apps through single sign-on (SSO) capability. Atlassian develops products for software developers, project managers, and other software-related teams that use the platform for data collaboration and information sharing. Affected Domains jira.atlassian.com confluence.atlassian.com getsupport.atlassian.com […]
The post Critical Flaws In The Atlassian Project Let Attackers Take Over Control Of Accounts And Apps appeared first on Cyber Security News.
https://cybersecuritynews.com/critical-flaws-atlassian-project/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/critical-flaws-atlassian-project/?utm_source=dlvr.it&utm_medium=blogger
Friday, June 25, 2021
AWS launches BugBust contest: Help fix a $100m problem for a $12 tshirt
This article has been indexed from The Register – Security Did we mention you’ll soon be paying to play in 30 days, too? AWS has set up a competition for its customers’ developers to find and fix one million bugs.……
Read more → The post AWS launches BugBust contest: Help fix a $100m problem for a $12 tshirt first appeared on IT Security News.
https://www.itsecuritynews.info/aws-launches-bugbust-contest-help-fix-a-100m-problem-for-a-12-tshirt/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/aws-launches-bugbust-contest-help-fix-a-100m-problem-for-a-12-tshirt/?utm_source=dlvr.it&utm_medium=blogger
Crackonosh virus mined $2 million of Monero from 222,000 hacked computers
A previously undocumented Windows malware has infected over 222,000 systems worldwide since at least June 2018, yielding its developer no less than 9,000 Moneros ($2 million) in illegal profits. Dubbed "Crackonosh," the malware is distributed via illegal, cracked copies of popular software, only to disable antivirus programs installed in the machine and install a coin miner package called XMRig
https://thehackernews.com/2021/06/crackonosh-virus-mined-2-million-of.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/crackonosh-virus-mined-2-million-of.html?utm_source=dlvr.it&utm_medium=blogger
Clop Gang Partners Laundered $500 Million in Ransomware Payments
The cybercrime ring that was apprehended last week in connection with Clop (aka Cl0p) ransomware attacks against dozens of companies in the last few months helped launder money totaling $500 million for several malicious actors through a plethora of illegal activities. "The group — also known as FANCYCAT — has been running multiple criminal activities: distributing cyber attacks; operating a
https://thehackernews.com/2021/06/clop-gang-members-laundered-500-million.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/clop-gang-members-laundered-500-million.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, June 24, 2021
Coast Guard confronts harassment and retaliation in the ranks
This article has been indexed from FCW: The business of federal technology The U.S. Coast Guard wants to build out its cyber workforce, but will have to contend with budget restraints and culture issues surrounding sexual harassment and retaliation. Read…
Read more → The post Coast Guard confronts harassment and retaliation in the ranks first appeared on IT Security News.
https://www.itsecuritynews.info/coast-guard-confronts-harassment-and-retaliation-in-the-ranks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/coast-guard-confronts-harassment-and-retaliation-in-the-ranks/?utm_source=dlvr.it&utm_medium=blogger
Antivirus Pioneer John McAfee Found Dead in Spanish Jail
Controversial mogul and antivirus pioneer John McAfee on Wednesday died by suicide in a jail cell in Barcelona, hours after reports that he would be extradited to face federal charges in the U.S. McAfee was 75. He is said to have died by hanging "as his nine months in prison brought him to despair," according to McAfee's lawyer Javier Villalba, Reuters reported. Security personnel at the Brians
https://thehackernews.com/2021/06/antivirus-pioneer-john-mcafee-found.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/antivirus-pioneer-john-mcafee-found.html?utm_source=dlvr.it&utm_medium=blogger
What is a Dictionary Attack? How the Attack works and How to Prevent the Dictionary Attack
A Dictionary attack is one of the ways through which the attackers try to gain access to the keys of the reign. Bad actors take advantage of people using common dictionary words as their passwords. A study has proved how the majority of people like to reuse their passwords or use common phrases that are […]
The post What is a Dictionary Attack? How the Attack works and How to Prevent the Dictionary Attack appeared first on Cyber Security News.
https://cybersecuritynews.com/dictionary-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/dictionary-attack/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, June 23, 2021
Three things that have vanished: $3.6bn in Bitcoin, a crypto investment biz, and the two brothers who ran it
This article has been indexed from The Register – Security We got hacked and we’ll be right back, duo said … two months ago Up to $3.6bn in Bitcoin has disappeared from a South African cryptocurrency investment outfit as well…
Read more → The post Three things that have vanished: $3.6bn in Bitcoin, a crypto investment biz, and the two brothers who ran it first appeared on IT Security News.
https://www.itsecuritynews.info/three-things-that-have-vanished-3-6bn-in-bitcoin-a-crypto-investment-biz-and-the-two-brothers-who-ran-it/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/three-things-that-have-vanished-3-6bn-in-bitcoin-a-crypto-investment-biz-and-the-two-brothers-who-ran-it/?utm_source=dlvr.it&utm_medium=blogger
Top 10 Best Android Password Managers – 2021
Android Password Manager is very essential utility to secure your credentials from cybercriminals and store it in an isolated environment. One of the main recommendations when creating secure passwords is not to use them in different services, as it would be almost impossible to remember all of them, but don’t worry, as there are applications […]
The post Top 10 Best Android Password Managers – 2021 appeared first on Cyber Security News.
https://cybersecuritynews.com/android-password-manager/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/android-password-manager/?utm_source=dlvr.it&utm_medium=blogger
SonicWall Left a VPN Flaw Partially Unpatched Amidst 0-Day Attacks
A critical vulnerability in SonicWall VPN appliances that was believed to have been patched last year has been now found to be "botched," with the company leaving a memory leak flaw unaddressed, until now, that could permit a remote attacker to gain access to sensitive information. The shortcoming was rectified in an update rolled out to SonicOS on June 22. Tracked as CVE-2021-20019 (CVSS score
https://thehackernews.com/2021/06/sonicwall-left-vpn-flaw-partially.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/sonicwall-left-vpn-flaw-partially.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, June 22, 2021
Wormable DarkRadiation Ransomware Targets Linux and Docker Instances
Cybersecurity researchers have disclosed a new ransomware strain called "DarkRadiation" that's implemented entirely in Bash and targets Linux and Docker cloud containers, while banking on messaging service Telegram for command-and-control (C2) communications. "The ransomware is written in Bash script and targets Red Hat/CentOS and Debian Linux distributions," researchers from Trend Micro said in
https://thehackernews.com/2021/06/wormable-darkradiation-ransomware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/wormable-darkradiation-ransomware.html?utm_source=dlvr.it&utm_medium=blogger
How to Create a Simulated Phishing Attack Across Your Company
This article has been indexed from Blog Email is one of the many weapons at the disposal of bad actors on the Internet, and your employees are in the firing line. Attackers try to hide behind a trusted entity, sometimes…
Read more → The post How to Create a Simulated Phishing Attack Across Your Company first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-create-a-simulated-phishing-attack-across-your-company/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-to-create-a-simulated-phishing-attack-across-your-company/?utm_source=dlvr.it&utm_medium=blogger
NVIDIA Jetson Chipsets Found Vulnerable to High-severity Flaws
U.S. graphics chip specialist NVIDIA has released software updates to address a total of 26 vulnerabilities impacting its Jetson system-on-module (SOM) series that could be abused by adversaries to escalate privileges and even lead to denial-of-service and information disclosure. Tracked from CVE‑2021‑34372 through CVE‑2021‑34397, the flaws affect products Jetson TX1, TX2 series,
https://thehackernews.com/2021/06/nvidia-jetson-chipsets-found-vulnerable.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/nvidia-jetson-chipsets-found-vulnerable.html?utm_source=dlvr.it&utm_medium=blogger
Monday, June 21, 2021
Wikimedia Bans Administrator of the Croatian version of Wikipedia
Croatian language Wikipedia was created on February 16, 2003, alongside Serbian language Wikipedia. Serbo-Croatian is a commonly intelligible pluricentric language in Southeastern Europe, written in both Cyrillic and Latin scripts and presently covered by four different Wikipedia language versions: Bosnian, Croatian, Serbian, and the original Serbo-Croatian language Wikipedia that was temporarily archived for a couple […]
The post Wikimedia Bans Administrator of the Croatian version of Wikipedia appeared first on Cyber Security News.
https://cybersecuritynews.com/wikimedia-bans-administrator/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/wikimedia-bans-administrator/?utm_source=dlvr.it&utm_medium=blogger
DroidMorph Shows Popular Android Antivirus Fail to Detect Cloned Malicious Apps
A new research published by a group of academics has found that anti-virus programs for Android continue to remain vulnerable against different permutations of malware, in what could pose a serious risk as malicious actors evolve their toolsets to better evade analysis. "Malware writers use stealthy mutations (morphing/obfuscations) to continuously develop malware clones, thwarting detection by
https://thehackernews.com/2021/06/droidmorph-shows-popular-android.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/droidmorph-shows-popular-android.html?utm_source=dlvr.it&utm_medium=blogger
What is a Cyber Security Ontology and How to get a Cyber-ontology Job?
Before you know the Cyber Security Ontology, you need to know what is Cyber Security? This is the practice which defends the computers, mobile device, servers, network, electronic system, etc. from malicious attack. This is also well-known as an information security technology. Now is the time to know what is all about Cyber Security Ontology, […]
The post What is a Cyber Security Ontology and How to get a Cyber-ontology Job? appeared first on Cyber Security News.
https://cybersecuritynews.com/cyber-security-ontology/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cyber-security-ontology/?utm_source=dlvr.it&utm_medium=blogger
Sunday, June 20, 2021
IT Security News Daily Summary 2021-06-20
Multilingual Cybersecurity Awareness Training adapted for your needs Penetration testing IT Security News Daily Summary 2021-06-19 ‘Build’ or ‘Buy’ your own antivirus product Generated on 2021-06-20 23:55:16.422919
Read more → The post IT Security News Daily Summary 2021-06-20 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-06-20/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-06-20/?utm_source=dlvr.it&utm_medium=blogger
Penetration testing
Penetration testing is the technical analysis of the safety level of IT systems and networks. We offer a complete investigation of the hardware / software systems for security vulnerabilities. If you have at least one online service, then you must…
Read more → The post Penetration testing first appeared on IT Security News.
https://www.itsecuritynews.info/penetration-testing-33/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/penetration-testing-33/?utm_source=dlvr.it&utm_medium=blogger
Saturday, June 19, 2021
IT Security News Daily Summary 2021-06-19
‘Build’ or ‘Buy’ your own antivirus product IT Security News Daily Summary 2021-06-18 Ransomware Actors Evolved Their Operations in 2020 Texan Admits Data Center Bomb Plot Colorado Passes New Privacy Act New Jersey Councilor Charged with Cyber-harassment Google Spices Up…
Read more → The post IT Security News Daily Summary 2021-06-19 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-06-19/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-06-19/?utm_source=dlvr.it&utm_medium=blogger
‘Build’ or ‘Buy’ your own antivirus product
We can help you decide if you should build your own antivirus product or if you should license an OEM or whitelabel product Both options come with advantages and disadvantages, it depends on the needs of the customer, on the…
Read more → The post ‘Build’ or ‘Buy’ your own antivirus product first appeared on IT Security News.
https://www.itsecuritynews.info/build-or-buy-your-own-antivirus-product-40/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/build-or-buy-your-own-antivirus-product-40/?utm_source=dlvr.it&utm_medium=blogger
North Korea Exploited VPN Flaw to Hack South's Nuclear Research Institute
South Korea's state-run Korea Atomic Energy Research Institute (KAERI) on Friday disclosed that its internal network was infiltrated by suspected attackers operating out of its northern counterpart. The intrusion is said to have taken place on May 14 through a vulnerability in an unnamed virtual private network (VPN) vendor and involved a total of 13 IP addresses, one of which — "27.102.114[.]89
https://thehackernews.com/2021/06/north-korea-exploited-vpn-flaw-to-hack.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/north-korea-exploited-vpn-flaw-to-hack.html?utm_source=dlvr.it&utm_medium=blogger
Friday, June 18, 2021
Want your endpoint security product in the ‘Microsoft Consumer Antivirus Providers for Windows’ ?
You need to meet some serious performance and functionality requirements. Don’t try to do this yourself because you will need a long time and a lot of attempts. We have helped a lot of companies develop their product, enter MVI,…
Read more → The post Want your endpoint security product in the ‘Microsoft Consumer Antivirus Providers for Windows’ ? first appeared on IT Security News.
https://www.itsecuritynews.info/want-your-endpoint-security-product-in-the-microsoft-consumer-antivirus-providers-for-windows-68/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/want-your-endpoint-security-product-in-the-microsoft-consumer-antivirus-providers-for-windows-68/?utm_source=dlvr.it&utm_medium=blogger
Hackers are Selling Audi, Volkswagen Customer Data on a Hacking Forum
Audi, Volkswagen disclosed a data breach last week Friday, the hacker said that they have stolen more than 3.3 million customers and interested buyers’ details from an exposed Azure BLOB container. A hacker who goes by the name [000] listed the data on hacking forums, according to the post the data contains more than 5 […]
The post Hackers are Selling Audi, Volkswagen Customer Data on a Hacking Forum appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-audi-volkswagen/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-audi-volkswagen/?utm_source=dlvr.it&utm_medium=blogger
Update Your Chrome Browser to Patch Yet Another 0-Day Exploited in-the-Wild
Google has rolled out yet another update to Chrome browser for Windows, Mac, and Linux to fix four security vulnerabilities, including one zero-day flaw that's being exploited in the wild. Tracked as CVE-2021-30554, the high severity flaw concerns a use after free vulnerability in WebGL (aka Web Graphics Library), a JavaScript API for rendering interactive 2D and 3D graphics within the browser.
https://thehackernews.com/2021/06/update-your-chrome-browser-to-patch-yet.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/update-your-chrome-browser-to-patch-yet.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, June 17, 2021
Ukraine Police Arrested Clop Ransomware Gang And Disrupted Infrastructure
Members of the Clop ransomware gang arrested by the Ukrainian police in conjunction with Interpol and law enforcement from the US and South Korea. With the help of the malicious program “Clop”, the defendants encrypted the data on the media of companies in the Republic of Korea and the United States. Later on, they demanded […]
The post Ukraine Police Arrested Clop Ransomware Gang And Disrupted Infrastructure appeared first on Cyber Security News.
https://cybersecuritynews.com/clop-ransomware-gang/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/clop-ransomware-gang/?utm_source=dlvr.it&utm_medium=blogger
60% of Businesses Would Consider Paying a Ransomware Demand
This article has been indexed from http://www.infosecurity-magazine.com/rss/news/76/application-security/ One in five businesses are also prepared to spend 20% or more of their annual revenue Read the original article: 60% of Businesses Would Consider Paying a Ransomware Demand
Read more → The post 60% of Businesses Would Consider Paying a Ransomware Demand first appeared on IT Security News.
https://www.itsecuritynews.info/60-of-businesses-would-consider-paying-a-ransomware-demand/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/60-of-businesses-would-consider-paying-a-ransomware-demand/?utm_source=dlvr.it&utm_medium=blogger
Researchers Uncover 'Process Ghosting' — A New Malware Evasion Technique
Cybersecurity researchers have disclosed a new executable image tampering attack dubbed "Process Ghosting" that could be potentially abused by an attacker to circumvent protections and stealthily run malicious code on a Windows system. "With this technique, an attacker can write a piece of malware to disk in such a way that it's difficult to scan or delete it — and where it then executes the
https://thehackernews.com/2021/06/researchers-uncover-process-ghosting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/researchers-uncover-process-ghosting.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, June 16, 2021
IT Security News Daily Summary 2021-06-16
US Convicts Russian Malware-masker Deloitte Acquires Terbium Labs IAB Tech Lab Accused of “World’s Largest Data Breach” Members of Clop Ransomware Gang Arrested in Ukraine NHS Test and Trace Bolsters its Cybersecurity A Conversation with Arielle McKee on the Meaning…
Read more → The post IT Security News Daily Summary 2021-06-16 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-06-16/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-06-16/?utm_source=dlvr.it&utm_medium=blogger
Noxplayer Supply-Chain Attack Targets Governments, Religious Organizations, Electronics Manufacturers and Universities
Researchers from ESET in recent times linked a stealthy cyberespionage group, active since 2014 known as Gelsemium. It is believed that Gelsemium is responsible for the Supply-Chain attack against BigNox, previously reported as Operation NightScout. The victims of these campaigns are located in East Asia as well as the Middle East and include governments, religious […]
The post Noxplayer Supply-Chain Attack Targets Governments, Religious Organizations, Electronics Manufacturers and Universities appeared first on Cyber Security News.
https://cybersecuritynews.com/noxplayer-supply-chain-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/noxplayer-supply-chain-attack/?utm_source=dlvr.it&utm_medium=blogger
Critical ThroughTek Flaw Opens Millions of Connected Cameras to Eavesdropping
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday issued an advisory regarding a critical software supply-chain flaw impacting ThroughTek's software development kit (SDK) that could be abused by an adversary to gain improper access to audio and video streams. "Successful exploitation of this vulnerability could permit unauthorized access to sensitive information, such
https://thehackernews.com/2021/06/critical-throughtek-flaw-opens-millions.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/critical-throughtek-flaw-opens-millions.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, June 15, 2021
Syniverse and AlefEdge support enterprises in creating their own 5G edge networks
This article has been indexed from Help Net Security Syniverse and AlefEdge announced a collaboration to enable global enterprises and their developers to create their own 5G Edge networks and launch 5G Edge applications and services in minutes. The combination…
Read more → The post Syniverse and AlefEdge support enterprises in creating their own 5G edge networks first appeared on IT Security News.
https://www.itsecuritynews.info/syniverse-and-alefedge-support-enterprises-in-creating-their-own-5g-edge-networks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/syniverse-and-alefedge-support-enterprises-in-creating-their-own-5g-edge-networks/?utm_source=dlvr.it&utm_medium=blogger
What is a SOC Framework, Elements & Benefits of Security Operation Centre
Security Operation Centre is always the heart of the organization in cybersecurity. When other groups mainly focus on the architecture and strategy, SOC Framework works as rubber meets to implement those strategies. As per the research, it has proven that in this world 68% organization has SOC, and they are the successful organization. Moreover, a […]
The post What is a SOC Framework, Elements & Benefits of Security Operation Centre appeared first on Cyber Security News.
https://cybersecuritynews.com/soc-framework/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/soc-framework/?utm_source=dlvr.it&utm_medium=blogger
Apple Issues Urgent Patches for 2 Zero-Day Flaws Exploited in the Wild
Apple on Monday shipped out-of-band security patches to address two zero-day vulnerabilities in iOS 12.5.3 that it says are being actively exploited in the wild. The latest update, iOS 12.5.4, comes with fixes for three security bugs, including a memory corruption issue in ASN.1 decoder (CVE-2021-30737) and two flaws concerning its WebKit browser engine that could be abused to
https://thehackernews.com/2021/06/apple-issues-urgent-patches-for-2-zero.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/apple-issues-urgent-patches-for-2-zero.html?utm_source=dlvr.it&utm_medium=blogger
Monday, June 14, 2021
VPN Attacks Surged in First Quarter
This article has been indexed from Dark Reading: But volume of malware, botnet, and other exploit activity declined because of the Emotet botnet takedown. Read the original article: VPN Attacks Surged in First Quarter
Read more → The post VPN Attacks Surged in First Quarter first appeared on IT Security News.
https://www.itsecuritynews.info/vpn-attacks-surged-in-first-quarter/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/vpn-attacks-surged-in-first-quarter/?utm_source=dlvr.it&utm_medium=blogger
Credential Theft, O365 Lures Dominate Corporate Inboxes in Q1
This article has been indexed from The PhishLabs Blog Read the original article: Credential Theft, O365 Lures Dominate Corporate Inboxes in Q1
Read more → The post Credential Theft, O365 Lures Dominate Corporate Inboxes in Q1 first appeared on IT Security News.
https://www.itsecuritynews.info/credential-theft-o365-lures-dominate-corporate-inboxes-in-q1/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/credential-theft-o365-lures-dominate-corporate-inboxes-in-q1/?utm_source=dlvr.it&utm_medium=blogger
Cybersecurity Executive Order 2021: What It Means for Cloud and SaaS Security
In response to malicious actors targeting US federal IT systems and their supply chain, the President released the "Executive Order on Improving the Nation’s Cybersecurity (Executive Order)." Although directed at Federal departments and agencies, the Executive Order will likely have a ripple effect through the Federal technology supply stream. Private companies and enterprises will look to the
https://thehackernews.com/2021/06/cybersecurity-executive-order-2021-what.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/06/cybersecurity-executive-order-2021-what.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)