This article has been indexed from MacRumors: Mac News and Rumors – Front Page Apple plans to adopt OLED display technology in “some” iPad models next year, following the recent adoption of mini-LED technology in its highest-end 12.9-inch iPad Pro,…
Read more → The post Apple Rumored to Adopt OLED Displays in ‘Some’ iPad Models Starting Next Year first appeared on IT Security News.
https://www.itsecuritynews.info/apple-rumored-to-adopt-oled-displays-in-some-ipad-models-starting-next-year/?utm_source=dlvr.it&utm_medium=blogger
Monday, May 31, 2021
SolarWinds Hackers Targets Individual Accounts Across 150 Organizations Worldwide
Microsoft said that Nobelium, a Russian-based hacking group, launched the phishing campaign by gaining access to a marketing account of the U.S. Agency for International Development. These SolarWinds hackers targeted 150 organizations with phishing. Microsoft’s Insights on this Phishing Attack The SolarWinds hackers have launched a campaign and appear to target government agencies. Microsoft said […]
The post SolarWinds Hackers Targets Individual Accounts Across 150 Organizations Worldwide appeared first on Cyber Security News.
https://cybersecuritynews.com/solarwinds-nobelium-hacker-group/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/solarwinds-nobelium-hacker-group/?utm_source=dlvr.it&utm_medium=blogger
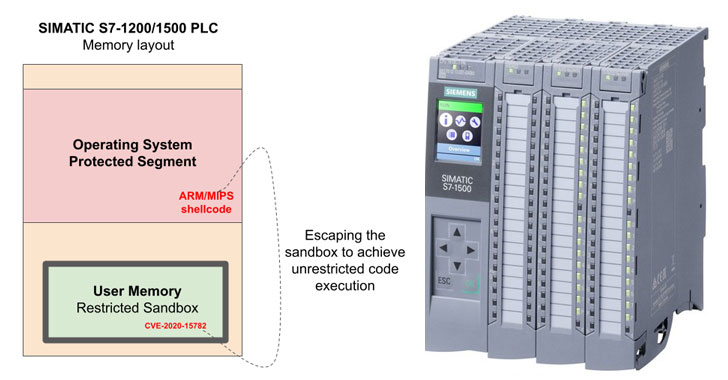
A New Bug in Siemens PLCs Could Let Hackers Run Malicious Code Remotely
Siemens on Friday shipped firmware updates to address a severe vulnerability in SIMATIC S7-1200 and S7-1500 programmable logic controllers (PLCs) that could be exploited by a malicious actor to remotely gain access to protected areas of the memory and achieve unrestricted and undetected code execution, in what the researchers describe as an attacker's "holy grail." The memory protection bypass
https://thehackernews.com/2021/05/a-new-bug-in-siemens-plcs-could-let.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/a-new-bug-in-siemens-plcs-could-let.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, May 30, 2021
BSides Canberra 2021 – Sean Yeoh’s, Patrick Mortensen’s, Michael Gianarakis’ And Shubham Shah’s ‘Context Aware Content Discovery: The Natural Evolution’
This article has been indexed from Security Boulevard Thanks to BSides Canberra for publishing their outstanding videos on the organization’s YouTube channel. Enjoy! Permalink The post BSides Canberra 2021 – Sean Yeoh’s, Patrick Mortensen’s, Michael Gianarakis’ And Shubham Shah’s ‘Context…
Read more → The post BSides Canberra 2021 – Sean Yeoh’s, Patrick Mortensen’s, Michael Gianarakis’ And Shubham Shah’s ‘Context Aware Content Discovery: The Natural Evolution’ first appeared on IT Security News.
https://www.itsecuritynews.info/bsides-canberra-2021-sean-yeohs-patrick-mortensens-michael-gianarakis-and-shubham-shahs-context-aware-content-discovery-the-natural-evolution/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/bsides-canberra-2021-sean-yeohs-patrick-mortensens-michael-gianarakis-and-shubham-shahs-context-aware-content-discovery-the-natural-evolution/?utm_source=dlvr.it&utm_medium=blogger
Apple’s M1 Chip Has a Fascinating Flaw
This article has been indexed from Security Latest The covert channel bug demonstrates a fundamental fact of CPUs: even new ones have vulnerabilities. Read the original article: Apple’s M1 Chip Has a Fascinating Flaw
Read more → The post Apple’s M1 Chip Has a Fascinating Flaw first appeared on IT Security News.
https://www.itsecuritynews.info/apples-m1-chip-has-a-fascinating-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apples-m1-chip-has-a-fascinating-flaw/?utm_source=dlvr.it&utm_medium=blogger
Growing Log Management Platform Logit.io Launches Dedicated UK Data Centre
Leading log management and metrics company Logit.io is pleased to announce that they have expanded their offering to include a new dedicated UK data center. Logit.io has had a number of dedicated data centres across the EMEA & US regions for some time making the addition of their UK data centre the latest example of […]
The post Growing Log Management Platform Logit.io Launches Dedicated UK Data Centre appeared first on Cyber Security News.
https://cybersecuritynews.com/growing-log-management-platform-logit-io-launches-dedicated-uk-data-centre/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/growing-log-management-platform-logit-io-launches-dedicated-uk-data-centre/?utm_source=dlvr.it&utm_medium=blogger
Saturday, May 29, 2021
Cryptocurrency trading bots: Strengthening Cybersecurity and minimizing risks
This article has been indexed from Cybersecurity Insiders This blog was written by an independent guest blogger. A staggering $1.9 billion in cryptocurrency was stolen by criminals in 2020, a recent report by Finaria reveals. Fortunately, despite the growth of the crypto…
Read more → The post Cryptocurrency trading bots: Strengthening Cybersecurity and minimizing risks first appeared on IT Security News.
https://www.itsecuritynews.info/cryptocurrency-trading-bots-strengthening-cybersecurity-and-minimizing-risks-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cryptocurrency-trading-bots-strengthening-cybersecurity-and-minimizing-risks-2/?utm_source=dlvr.it&utm_medium=blogger
A New Malware Campaign Deliver Weaponized AnyDesk Installer via Targeted Google ad Searches
Security experts have uncovered a complicated malvertising campaign (malware advertising) distributing the weaponized AnyDesk installer via targeted Google ad searches for the keyword “Anydesk.” According to a security investigation from CrowdStrike Falcon Complete team, cybercriminals are spreading a malicious file “AnyDeskSetup.exe” masquerading as a legitimate AnyDesk Remote Desktop application. What is Anydesk? AnyDesk is a remote desktop application that provides […]
The post A New Malware Campaign Deliver Weaponized AnyDesk Installer via Targeted Google ad Searches appeared first on Cyber Security News.
https://cybersecuritynews.com/weaponized-anydesk-installer/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/weaponized-anydesk-installer/?utm_source=dlvr.it&utm_medium=blogger
Researchers Demonstrate 2 New Hacks to Modify Certified PDF Documents
Cybersecurity researchers have disclosed two new attack techniques on certified PDF documents that could potentially enable an attacker to alter a document's visible content by displaying malicious content over the certified content without invalidating its signature. "The attack idea exploits the flexibility of PDF certification, which allows signing or adding annotations to certified documents
https://thehackernews.com/2021/05/researchers-demonstrate-2-new-hacks-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/researchers-demonstrate-2-new-hacks-to.html?utm_source=dlvr.it&utm_medium=blogger
Friday, May 28, 2021
The Various Ways in Which Someone Can Remotely Monitor Your Android Device
Monitor Your Android Device Technology today is so advanced that one always needs to be careful about the kind of information they share and store on their smartphones. While some people are comfortable keeping a manual record of their passwords and bank account details, others tend to have all their lives stored away on their […]
The post The Various Ways in Which Someone Can Remotely Monitor Your Android Device appeared first on Cyber Security News.
https://cybersecuritynews.com/the-various-ways-in-which-someone-can-remotely-monitor-your-android-device/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/the-various-ways-in-which-someone-can-remotely-monitor-your-android-device/?utm_source=dlvr.it&utm_medium=blogger
Chinese Cyber Espionage Hackers Continue to Target Pulse Secure VPN Devices
Cybersecurity researchers from FireEye unmasked additional tactics, techniques, and procedures (TTPs) adopted by Chinese threat actors who were recently found abusing Pulse Secure VPN devices to drop malicious web shells and exfiltrate sensitive information from enterprise networks. FireEye's Mandiant threat intelligence team, which is tracking the cyberespionage activity under two threat
https://thehackernews.com/2021/05/chinese-cyber-espionage-hackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/chinese-cyber-espionage-hackers.html?utm_source=dlvr.it&utm_medium=blogger
SolarWinds Hackers Target Think Tanks With New 'NativeZone' Backdoor
Microsoft on Thursday disclosed that the threat actor behind the SolarWinds supply chain hack returned to the threat landscape to target government agencies, think tanks, consultants, and non-governmental organizations located across 24 countries, including the U.S. "This wave of attacks targeted approximately 3,000 email accounts at more than 150 different organizations," Tom Burt, Microsoft's
https://thehackernews.com/2021/05/solarwinds-hackers-target-think-tanks.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/solarwinds-hackers-target-think-tanks.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, May 27, 2021
Identity, credentials and behavior are critical to network protection
This article has been indexed from GCN: News, Explainers, Insights In a post-pandemic economy with employees outside the firewall, agencies must embrace the idea that identity is the new perimeter. Read the original article: Identity, credentials and behavior are critical…
Read more → The post Identity, credentials and behavior are critical to network protection first appeared on IT Security News.
https://www.itsecuritynews.info/identity-credentials-and-behavior-are-critical-to-network-protection/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/identity-credentials-and-behavior-are-critical-to-network-protection/?utm_source=dlvr.it&utm_medium=blogger
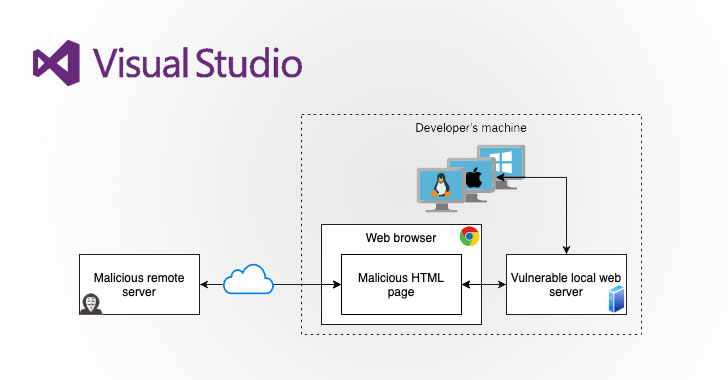
Newly Discovered Bugs in VSCode Extensions Could Lead to Supply Chain Attacks
Severe security flaws uncovered in popular Visual Studio Code extensions could enable attackers to compromise local machines as well as build and deployment systems through a developer's integrated development environment (IDE). The vulnerable extensions could be exploited to run arbitrary code on a developer's system remotely, in what could ultimately pave the way for supply chain attacks. Some
https://thehackernews.com/2021/05/newly-discovered-bugs-in-vscode.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/newly-discovered-bugs-in-vscode.html?utm_source=dlvr.it&utm_medium=blogger
Hackers Using Fake Foundations to Target Uyghur Minority in China
The Uyghur community located in China and Pakistan has been the subject of an ongoing espionage campaign aiming to trick the targets into downloading a Windows backdoor to amass sensitive information from their systems. "Considerable effort was put into disguising the payloads, whether by creating delivery documents that appear to be originating from the United Nations using up to date related
https://thehackernews.com/2021/05/hackers-using-fake-foundations-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/hackers-using-fake-foundations-to.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, May 26, 2021
How user experience is shaping verifiable credentials and identity
This article has been indexed from Microsoft Security Since 2017, Microsoft has been working with the identity community on two groundbreaking technologies designed from the ground up to make digital privacy convenient and practical: decentralized identifiers and verifiable credentials. We…
Read more → The post How user experience is shaping verifiable credentials and identity first appeared on IT Security News.
https://www.itsecuritynews.info/how-user-experience-is-shaping-verifiable-credentials-and-identity/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-user-experience-is-shaping-verifiable-credentials-and-identity/?utm_source=dlvr.it&utm_medium=blogger
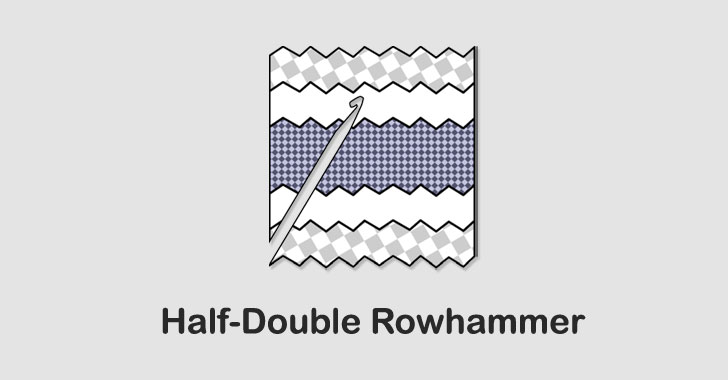
Google Researchers Discover A New Variant of Rowhammer Attack
A team of security researchers from Google has demonstrated yet another variant of the Rowhammer attack that bypasses all current defenses to tamper with data stored in memory. Dubbed "Half-Double," the new hammering technique hinges on the weak coupling between two memory rows that are not immediately adjacent to each other but one row removed. "Unlike TRRespass, which exploits the blind spots
https://thehackernews.com/2021/05/google-researchers-discover-new-variant.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/google-researchers-discover-new-variant.html?utm_source=dlvr.it&utm_medium=blogger
Critical RCE Vulnerability Found in VMware vCenter Server — Patch Now!
VMware has rolled out patches to address a critical security vulnerability in vCenter Server that could be leveraged by an adversary to execute arbitrary code on the server. Tracked as CVE-2021-21985 (CVSS score 9.8), the issue stems from a lack of input validation in the Virtual SAN (vSAN) Health Check plug-in, which is enabled by default in the vCenter Server. "A malicious actor with network
https://thehackernews.com/2021/05/critical-rce-vulnerability-found-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/critical-rce-vulnerability-found-in.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, May 25, 2021
Who are you? Rising to the data protection challenge
This article has been indexed from GCN: News, Explainers, Insights Mainframes allow agencies to implement zero trust, multifactor authentication and privileged user access as standard practices, without requiring additional capacity. Read the original article: Who are you? Rising to the…
Read more → The post Who are you? Rising to the data protection challenge first appeared on IT Security News.
https://www.itsecuritynews.info/who-are-you-rising-to-the-data-protection-challenge/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/who-are-you-rising-to-the-data-protection-challenge/?utm_source=dlvr.it&utm_medium=blogger
New Bluetooth Flaws Let Attackers Impersonate Legitimate Devices
Adversaries could exploit newly discovered security weaknesses in Bluetooth Core and Mesh Profile Specifications to masquerade as legitimate devices and carry out man-in-the-middle (MitM) attacks. "Devices supporting the Bluetooth Core and Mesh Specifications are vulnerable to impersonation attacks and AuthValue disclosure that could allow an attacker to impersonate a legitimate device during
https://thehackernews.com/2021/05/new-bluetooth-flaws-let-attackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/new-bluetooth-flaws-let-attackers.html?utm_source=dlvr.it&utm_medium=blogger
Apple Issues Patches to Combat Ongoing 0-Day Attacks on macOS, tvOS
Apple on Monday rolled out security updates for iOS, macOS, tvOS, watchOS, and Safari web browser to fix multiple vulnerabilities, including an actively exploited zero-day flaw in macOS Big Sur and expand patches for two previously disclosed zero-day flaws. Tracked as CVE-2021-30713, the zero-day concerns a permissions issue in Apple's Transparency, Consent, and Control (TCC) framework in macOS
https://thehackernews.com/2021/05/apple-issues-patches-to-combat-ongoing.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/apple-issues-patches-to-combat-ongoing.html?utm_source=dlvr.it&utm_medium=blogger
Monday, May 24, 2021
We’re Hiring! Come be Our New Fellow on Cybersecurity
This article has been indexed from Lawfare We’re excited to announce that we’re now accepting applications for a new position at both Lawfare and the Brookings Institution: a Lawfare senior editor and Brookings fellow who will take on recently departed…
Read more → The post We’re Hiring! Come be Our New Fellow on Cybersecurity first appeared on IT Security News.
https://www.itsecuritynews.info/were-hiring-come-be-our-new-fellow-on-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/were-hiring-come-be-our-new-fellow-on-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
What To Do When Your Business Is Hacked
As businesses move to a remote workforce, hackers have increased their activity to capitalize on new security holes. Cybercriminals often use unsophisticated methods that continue to be extremely successful. These include phishing emails to harvest credentials and gain easy access to business-critical environments. Hackers are also using ransomware to hold your data hostage, demanding a ransom
https://thehackernews.com/2021/05/what-to-do-when-your-business-is-hacked.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/what-to-do-when-your-business-is-hacked.html?utm_source=dlvr.it&utm_medium=blogger
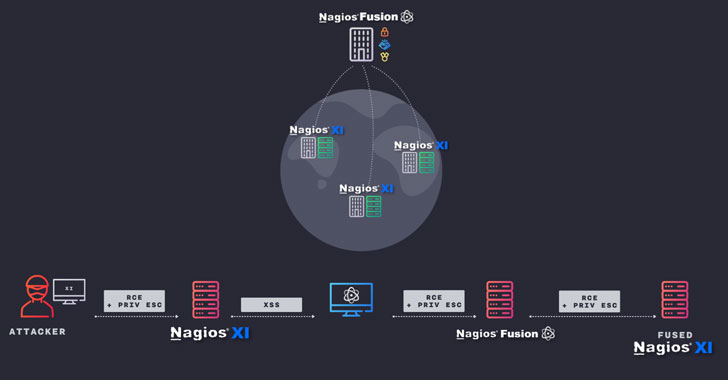
Details Disclosed On Critical Flaws Affecting Nagios IT Monitoring Software
Cybersecurity researchers disclosed details about 13 vulnerabilities in the Nagios network monitoring application that could be abused by an adversary to hijack the infrastructure without any operator intervention. "In a telco setting, where a telco is monitoring thousands of sites, if a customer site is fully compromised, an attacker can use the vulnerabilities to compromise the telco, and then
https://thehackernews.com/2021/05/details-disclosed-on-critical-flaws.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/details-disclosed-on-critical-flaws.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, May 23, 2021
CPDP 2021 – Moderator: Seda Gürses ‘Connecting The Dots: Privacy, Data, Racial Justice’
This article has been indexed from Security Boulevard Speakers: Yasmine Boudiaf, Sarah Chander, Nakeema Stefflbauer, Nani Jansen Reventlow, Seeta Peña Gangadharan Our sincere thanks to CPDP 2021 – Computers, Privacy & Data Protection Conference for publishing their well-crafted videos on…
Read more → The post CPDP 2021 – Moderator: Seda Gürses ‘Connecting The Dots: Privacy, Data, Racial Justice’ first appeared on IT Security News.
https://www.itsecuritynews.info/cpdp-2021-moderator-seda-gurses-connecting-the-dots-privacy-data-racial-justice/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cpdp-2021-moderator-seda-gurses-connecting-the-dots-privacy-data-racial-justice/?utm_source=dlvr.it&utm_medium=blogger
Security Affairs newsletter Round 315
This article has been indexed from Security Affairs A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. Avaddon Ransomware gang hacked France-based Acer Finance…
Read more → The post Security Affairs newsletter Round 315 first appeared on IT Security News.
https://www.itsecuritynews.info/security-affairs-newsletter-round-315/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/security-affairs-newsletter-round-315/?utm_source=dlvr.it&utm_medium=blogger
India’s National Carrier Says Hack Leaked Passengers’ Data
This article has been indexed from SecurityWeek RSS Feed Personal data of an unspecified number of travelers has been compromised after a company that serves India’s national carrier was hacked, Air India said. The hackers were able to access 10…
Read more → The post India’s National Carrier Says Hack Leaked Passengers’ Data first appeared on IT Security News.
https://www.itsecuritynews.info/indias-national-carrier-says-hack-leaked-passengers-data/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/indias-national-carrier-says-hack-leaked-passengers-data/?utm_source=dlvr.it&utm_medium=blogger
Saturday, May 22, 2021
Foreign hackers breached Russian federal agencies, said FSB
This article has been indexed from Security Affairs FSB National Coordination Center for Computer Incidents (NKTsKI) revealed that foreign hackers have breached networks of Russian federal agencies. A joint report published by Rostelecom-Solar and the FSB National Coordination Center for…
Read more → The post Foreign hackers breached Russian federal agencies, said FSB first appeared on IT Security News.
https://www.itsecuritynews.info/foreign-hackers-breached-russian-federal-agencies-said-fsb/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/foreign-hackers-breached-russian-federal-agencies-said-fsb/?utm_source=dlvr.it&utm_medium=blogger
FBI Warns Conti Ransomware Hit 16 U.S. Health and Emergency Services
The adversary behind Conti ransomware targeted no fewer than 16 healthcare and first responder networks in the U.S. within the past year, totally victimizing over 400 organizations worldwide, 290 of which are situated in the country. That's according to a new flash alert issued by the U.S. Federal Bureau of Investigation (FBI) on Thursday. "The FBI identified at least 16 Conti ransomware attacks
https://thehackernews.com/2021/05/fbi-warns-conti-ransomware-hit-16-us.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/fbi-warns-conti-ransomware-hit-16-us.html?utm_source=dlvr.it&utm_medium=blogger
Air India Hack Exposes Credit Card and Passport Info of 4.5 Million Passengers
India's flag carrier airline, Air India, has disclosed a data breach affecting 4.5 million of its customers over a period stretching nearly 10 years after its Passenger Service System (PSS) provider SITA fell victim to a cyber attack earlier this year. The breach involves personal data registered between Aug. 26, 2011 and Feb. 3, 2021, including details such as names, dates of birth, contact
https://thehackernews.com/2021/05/indias-flag-carrier-airline-air-india.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/indias-flag-carrier-airline-air-india.html?utm_source=dlvr.it&utm_medium=blogger
Friday, May 21, 2021
Shining a Light on DARKSIDE Ransomware Operations
This article has been indexed from Threat Research Update (May 14): Mandiant has observed multiple actors cite a May 13 announcement that appeared to be shared with DARKSIDE RaaS affiliates by the operators of the service. This announcement stated that they…
Read more → The post Shining a Light on DARKSIDE Ransomware Operations first appeared on IT Security News.
https://www.itsecuritynews.info/shining-a-light-on-darkside-ransomware-operations-3/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/shining-a-light-on-darkside-ransomware-operations-3/?utm_source=dlvr.it&utm_medium=blogger
Microsoft Warns of Data Stealing Malware That Pretends to Be Ransomware
Microsoft on Thursday warned of a "massive email campaign" that's pushing a Java-based STRRAT malware to steal confidential data from infected systems while disguising itself as a ransomware infection. "This RAT is infamous for its ransomware-like behavior of appending the file name extension .crimson to files without actually encrypting them," the Microsoft Security Intelligence team said in a
https://thehackernews.com/2021/05/microsoft-warns-of-data-stealing.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/microsoft-warns-of-data-stealing.html?utm_source=dlvr.it&utm_medium=blogger
Over 150 Flaws in 58 Stalkerware Apps Let Attackers Steal Control and Carry out Malicious Activities
Spouseware. Nope! Not the term used when your spouse troubles you! It is a mobile monitoring software, also known as mobile stalkerware. This is installed by the stalker onto a victim’s phone without their knowledge. A stalker usually requires to have physical access to the victim’s device. Due to this, the stalker is usually a […]
The post Over 150 Flaws in 58 Stalkerware Apps Let Attackers Steal Control and Carry out Malicious Activities appeared first on Cyber Security News.
https://cybersecuritynews.com/58-stalkerware-apps/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/58-stalkerware-apps/?utm_source=dlvr.it&utm_medium=blogger
Thursday, May 20, 2021
How your personal data may be exposed by misconfigured mobile apps
This article has been indexed from Security on TechRepublic App developers are failing to properly set up and secure access to third-party services, putting user data at risk, says Check Point Research. Read the original article: How your personal data…
Read more → The post How your personal data may be exposed by misconfigured mobile apps first appeared on IT Security News.
https://www.itsecuritynews.info/how-your-personal-data-may-be-exposed-by-misconfigured-mobile-apps/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-your-personal-data-may-be-exposed-by-misconfigured-mobile-apps/?utm_source=dlvr.it&utm_medium=blogger
Watering Hole Attack Was Used to Target Florida Water Utilities
An investigation undertaken in the aftermath of the Oldsmar water plant hack earlier this year has revealed that an infrastructure contractor in the U.S. state of Florida hosted malicious code on its website in what's known as a watering hole attack. "This malicious code seemingly targeted water utilities, particularly in Florida, and more importantly, was visited by a browser from the city of
https://thehackernews.com/2021/05/watering-hole-attack-was-used-to-target.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/watering-hole-attack-was-used-to-target.html?utm_source=dlvr.it&utm_medium=blogger
Android Issues Patches for 4 New Zero-Day Bugs Exploited in the Wild
Google on Wednesday updated its May 2021 Android Security Bulletin to disclose that four of the security vulnerabilities that were patched earlier this month by Arm and Qualcomm may have been exploited in the wild as zero-days. "There are indications that CVE-2021-1905, CVE-2021-1906, CVE-2021-28663 and CVE-2021-28664 may be under limited, targeted exploitation," the search giant said in an
https://thehackernews.com/2021/05/android-issues-patches-for-4-new-zero.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/android-issues-patches-for-4-new-zero.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, May 19, 2021
A New Unique RAT Heavily Uses The Autohotkey Scripting Language On An Ongoing Malware Campaign
The Morphisec Labs team has tracked a unique and ongoing RAT delivery campaign that heavily uses the AutoHotKey scripting language, a fork of the AutoIt language that is frequently used for testing purposes. Researchers identified at least four versions of the RAT delivery campaign, each of which includes multiple advancements and adaptations over the past […]
The post A New Unique RAT Heavily Uses The Autohotkey Scripting Language On An Ongoing Malware Campaign appeared first on Cyber Security News.
https://cybersecuritynews.com/rat-uses-autohotkey/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/rat-uses-autohotkey/?utm_source=dlvr.it&utm_medium=blogger
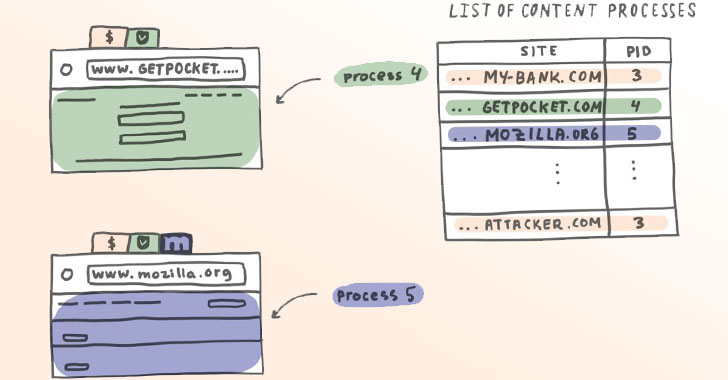
Mozilla Begins Rolling Out 'Site Isolation' Security Feature to Firefox Browser
Mozilla has begun rolling out a new security feature for its Firefox browser in nightly and beta channels that aims to protect users against a new class of side-channel attacks from malicious sites. Called "Site Isolation," the implementation loads each website separately in its own operating system process and, as a result, prevents untrusted code from a rogue website from accessing
https://thehackernews.com/2021/05/mozilla-begins-rolling-out-site.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/mozilla-begins-rolling-out-site.html?utm_source=dlvr.it&utm_medium=blogger
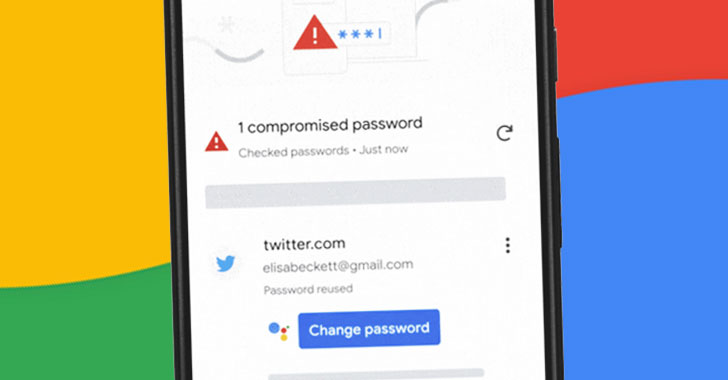
A Simple 1-Click Compromised Password Reset Feature Coming to Chrome Browser
Google on Tuesday announced a new feature to its password manager that could be used to change a stolen password automatically with a single tap. Automated password changes build on the tool's ability to check the safety of saved passwords. Thus when Chrome finds a password that may have been compromised as part of a data breach, it will prompt users with an alert containing a "Change Password"
https://thehackernews.com/2021/05/a-simple-1-click-compromised-password.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/a-simple-1-click-compromised-password.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, May 18, 2021
Hackers Abuse Microsoft Build Engine to Deliver Password-Stealing Malware Filelessly
Anomali Threat Research recognized a campaign in which threat actors used Microsoft Build Engine (MSBuild) to filelessly deliver Remcos remote access tool (RAT) and password-stealing malware commonly known as RedLine Stealer. Threat actors used MSBuild, a tool used for building apps and gives users an XML schema “that controls how the build platform processes and […]
The post Hackers Abuse Microsoft Build Engine to Deliver Password-Stealing Malware Filelessly appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-abuse-microsoft-build-engine/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-abuse-microsoft-build-engine/?utm_source=dlvr.it&utm_medium=blogger
Experts Reveal Over 150 Ways to Steal Control of 58 Android Stalkerware Apps
A total of 158 privacy and security issues have been identified in 58 Android stalkware apps from various vendors that could enable a malicious actor to take control of a victim's device, hijack a stalker's account, intercept data, achieve remote code execution, and even frame the victim by uploading fabricated evidence. The new findings, which come from an analysis of 86 stalkerware apps for
https://thehackernews.com/2021/05/experts-reveal-over-150-ways-to-steal.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/experts-reveal-over-150-ways-to-steal.html?utm_source=dlvr.it&utm_medium=blogger
70 European and South American Banks Under Attack By Bizarro Banking Malware
A financially motivated cybercrime gang has unleashed a previously undocumented banking trojan, which can steal credentials from customers of 70 banks located in various European and South American countries. Dubbed "Bizarro" by Kaspersky researchers, the Windows malware is "using affiliates or recruiting money mules to operationalize their attacks, cashing out or simply to helping [sic] with
https://thehackernews.com/2021/05/70-european-and-south-american-banks.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/70-european-and-south-american-banks.html?utm_source=dlvr.it&utm_medium=blogger
Monday, May 17, 2021
Apple Building Developer Center at Apple Park Campus
This article has been indexed from MacRumors: Mac News and Rumors – Front Page Apple is working to build a dedicated Developer Center on its Apple Park campus, Apple Fellow Phil Schiller said today during his testimony in the ongoing…
Read more → The post Apple Building Developer Center at Apple Park Campus first appeared on IT Security News.
https://www.itsecuritynews.info/apple-building-developer-center-at-apple-park-campus/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-building-developer-center-at-apple-park-campus/?utm_source=dlvr.it&utm_medium=blogger
Why Password Hygiene Needs a Reboot
In today's digital world, password security is more important than ever. While biometrics, one-time passwords (OTP), and other emerging forms of authentication are often touted as replacements to the traditional password, today, this concept is more marketing hype than anything else. But just because passwords aren't going anywhere anytime soon doesn't mean that organizations don’t need to
https://thehackernews.com/2021/05/why-password-hygiene-needs-reboot.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/why-password-hygiene-needs-reboot.html?utm_source=dlvr.it&utm_medium=blogger
Experts Warn About Ongoing AutoHotkey-Based Malware Attacks
Cybersecurity researchers have uncovered an ongoing malware campaign that heavily relies on AutoHotkey (AHK) scripting language to deliver multiple remote access trojans (RAT) such as Revenge RAT, LimeRAT, AsyncRAT, Houdini, and Vjw0rm on target Windows systems. At least four different versions of the campaign have been spotted starting February 2021, according to researchers from Morphisec Labs
https://thehackernews.com/2021/05/experts-warn-about-ongoing-autohotkey.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/05/experts-warn-about-ongoing-autohotkey.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, May 16, 2021
Avaddon Ransomware gang hacked France-based Acer Finance and AXA Asia
This article has been indexed from Security Affairs Avaddon ransomware gang has breached the France-based financial consultancy firm Acer Finance. Avaddon ransomware gang made the headlines again, the cybercrime gang has breached the France-based financial consultancy firm Acer Finance. Acer…
Read more → The post Avaddon Ransomware gang hacked France-based Acer Finance and AXA Asia first appeared on IT Security News.
https://www.itsecuritynews.info/avaddon-ransomware-gang-hacked-france-based-acer-finance-and-axa-asia/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/avaddon-ransomware-gang-hacked-france-based-acer-finance-and-axa-asia/?utm_source=dlvr.it&utm_medium=blogger
What is Command and Control(C2) Server – A Detailed Overview
Like a regular system holder, you might be wondering why is your system running slower than usual? Always you are getting random messages like pop-up, something got added as an extension in your browser and you have never used this. Your browser cannot load the page, internet connectivity is slow, and even the computer is […]
The post What is Command and Control(C2) Server – A Detailed Overview appeared first on Cyber Security News.
https://cybersecuritynews.com/command-and-controlc2-server/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/command-and-controlc2-server/?utm_source=dlvr.it&utm_medium=blogger
Popular Russian Hacking Forum XSS Bans all the Topics Promoting Ransomware
XSS, the Russian-speaking hacker forums have banned all topics publicizing ransomware to prevent unwanted attention and to share knowledge about exploits, vulnerabilities, malware, and network penetration. An Insight on the Announcement: U.S. fuel pipeline’s operation, law enforcement and security researchers have been increasingly scrutinizing the ransomware gang and sites that promote it for a couple […]
The post Popular Russian Hacking Forum XSS Bans all the Topics Promoting Ransomware appeared first on Cyber Security News.
https://cybersecuritynews.com/hacking-forum-xss/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hacking-forum-xss/?utm_source=dlvr.it&utm_medium=blogger
Saturday, May 15, 2021
Priority on people – An argument against the excessive use of Cybersecurity technology
This article has been indexed from Cybersecurity Insiders Introduction Despite what many advertisements and salespeople would like you to think, you don’t need to (and in many cases shouldn’t) spend a fortune on security tools to achieve a robust cybersecurity…
Read more →
The post Priority on people – An argument against the excessive use of Cybersecurity technology appeared first on IT Security News.
https://www.itsecuritynews.info/priority-on-people-an-argument-against-the-excessive-use-of-cybersecurity-technology-3/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/priority-on-people-an-argument-against-the-excessive-use-of-cybersecurity-technology-3/?utm_source=dlvr.it&utm_medium=blogger
Cisco has Fixed a six-month-Old Zero-day Vulnerability Found in the Cisco AnyConnect
This article has been indexed from GBHackers On Security The Cisco Product Security Incident Response Team (PSIRT) has recently fixed a six-month-old zero-day vulnerability that is tracked as “CVE-2020-3556” in Cisco AnyConnect Security Client. This zero-day flaw allows any attackers…
Read more → The post Cisco has Fixed a six-month-Old Zero-day Vulnerability Found in the Cisco AnyConnect first appeared on IT Security News.
https://www.itsecuritynews.info/cisco-has-fixed-a-six-month-old-zero-day-vulnerability-found-in-the-cisco-anyconnect/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cisco-has-fixed-a-six-month-old-zero-day-vulnerability-found-in-the-cisco-anyconnect/?utm_source=dlvr.it&utm_medium=blogger
Rapid7 has Disclosed that Some Code Repositories were Accessed in Codecov Supply-Chain Attack
Cybersecurity vendor Rapid7 disclosed it was among the victims of the Codecov software supply chain attack and warned that data for a subset of its customers were accessed in the breach. Codecov Supply-Chain Attack On April 15, 2021, the software company Codecov, a provider of code coverage solutions, announced a supply chain incident in which […]
The post Rapid7 has Disclosed that Some Code Repositories were Accessed in Codecov Supply-Chain Attack appeared first on Cyber Security News.
https://cybersecuritynews.com/rapid7-cyber-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/rapid7-cyber-attack/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)