The Cofense Phishing Defense Center (PDC) has revealed a phishing campaign that targets Office 365 users and includes a convincing SharePoint document claiming to urgently need an email signature. This new phishing campaign found in an environment protected by Microsoft’s secure email gateway (SEG). Since thousands of individuals still required to telework, hackers lure their […]
The post New Phishing Campaign Found in Microsoft’s own Secure Email Gateway (SEG) Uses SharePoint Documents appeared first on Cyber Security News.
https://cybersecuritynews.com/phishing-campaign-sharepoint-documents/?utm_source=dlvr.it&utm_medium=blogger
Friday, April 30, 2021
Microsoft Finds 'BadAlloc' Flaws Affecting Wide-Range of IoT and OT Devices
Microsoft researchers on Thursday disclosed two dozen vulnerabilities affecting a wide range of Internet of Things (IoT) and Operational Technology (OT) devices used in industrial, medical, and enterprise networks that could be abused by adversaries to execute arbitrary code and even cause critical systems to crash. "These remote code execution (RCE) vulnerabilities cover more than 25 CVEs and
https://thehackernews.com/2021/04/microsoft-finds-badalloc-flaws.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/microsoft-finds-badalloc-flaws.html?utm_source=dlvr.it&utm_medium=blogger
Passwordstate Warns of Ongoing Phishing Attacks Following Data Breach
Click Studios, the Australian software firm which confirmed a supply chain attack affecting its Passwordstate password management application, has warned customers of an ongoing phishing attack by an unknown threat actor. "We have been advised a bad actor has commenced a phishing attack with a small number of customers having received emails requesting urgent action," the company said in an
https://thehackernews.com/2021/04/passwordstate-warns-of-ongoing-phishing.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/passwordstate-warns-of-ongoing-phishing.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, April 29, 2021
Learn how to mitigate container security issues
Read the original article: Learn how to mitigate container security issues This post doesn’t have text content, please click on the link below to view the original article. Read the original article: Learn how to mitigate container security issues
Read more → The post Learn how to mitigate container security issues first appeared on IT Security News.
https://www.itsecuritynews.info/learn-how-to-mitigate-container-security-issues/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/learn-how-to-mitigate-container-security-issues/?utm_source=dlvr.it&utm_medium=blogger
Researchers Uncover Stealthy Linux Malware That Went Undetected for 3 Years
A previously undocumented Linux malware with backdoor capabilities has managed to stay under the radar for about three years, allowing the threat actor behind to harvest and exfiltrate sensitive information from infected systems. Dubbed "RotaJakiro" by researchers from Qihoo 360 NETLAB, the backdoor targets Linux X64 machines, and is so named after the fact that "the family uses rotate
https://thehackernews.com/2021/04/researchers-uncover-stealthy-linux.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/researchers-uncover-stealthy-linux.html?utm_source=dlvr.it&utm_medium=blogger
Top 10 Password Less Authentication Tools for Better Application Security
Password is a headache for those who use them and also who manage them. We as a user make many passwords, so it becomes easy for us to lose those and keep the track of them. That time it becomes a problem so password less authentication can be feasible for doing safe business. Now, you […]
The post Top 10 Password Less Authentication Tools for Better Application Security appeared first on Cyber Security News.
https://cybersecuritynews.com/password-less-authentication/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/password-less-authentication/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, April 28, 2021
Groups & User Right Management
Read the original article: Groups & User Right Management Organizations are diverse and as organizations grow, they end up owning multiple web assets that need protection. At Indusface, we have customers who end up using our AppTrana solution for. The…
Read more → The post Groups & User Right Management first appeared on IT Security News.
https://www.itsecuritynews.info/groups-user-right-management/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/groups-user-right-management/?utm_source=dlvr.it&utm_medium=blogger
Linux kernel Bug Let Attackers Insert Malicious Code into the Kernel Address Space
Address Space Layout Randomization (ASLR) is a computer security technique that involves randomly positioning the base address of an executable and the position of libraries, heap, and stack, in a process’s address space. Linux has long had ASLR for user-space programs, researcher Kees Cook has applied to the kernel itself as well. Linux kernel Bug […]
The post Linux kernel Bug Let Attackers Insert Malicious Code into the Kernel Address Space appeared first on Cyber Security News.
https://cybersecuritynews.com/linux-kernel-bug/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/linux-kernel-bug/?utm_source=dlvr.it&utm_medium=blogger
‘FluBot’ Malware Delivery Via SMS Texts Targets Android Devices
A text message scam that infects Android phones is spreading across the UK, warns the country’s National Cyber Security Centre. The message which pretends to be from a package delivery firm, prompts users to install a tracking app – but is a malicious piece of spyware. A malicious piece of spyware, known as ‘FluBot’ is […]
The post ‘FluBot’ Malware Delivery Via SMS Texts Targets Android Devices appeared first on Cyber Security News.
https://cybersecuritynews.com/flubot-android-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/flubot-android-malware/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, April 27, 2021
Understanding and Protecting Against Ransomware Attacks
Damage caused by ransomware attacks reached $20 Billion in the year 2020, doubling from $11 Billion in 2019, and is still getting worse. The number of organizations targeted is swelling rapidly each month rendering enormous impacts on victims who had to suffer the loss of worth millions of dollars. Only a few companies can bear […]
The post Understanding and Protecting Against Ransomware Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/understanding-and-protecting-against-ransomware-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/understanding-and-protecting-against-ransomware-attacks/?utm_source=dlvr.it&utm_medium=blogger
Twelve South Launches ‘Forte’ MagSafe Charger Stand
Read the original article: Twelve South Launches ‘Forte’ MagSafe Charger Stand Twelve South today announced the launch of the Forté, a charging stand that is compatible with Apple’s MagSafe Charger. The stand is designed to house the Apple-designed MagSafe charger,…
Read more → The post Twelve South Launches ‘Forte’ MagSafe Charger Stand first appeared on IT Security News.
https://www.itsecuritynews.info/twelve-south-launches-forte-magsafe-charger-stand/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/twelve-south-launches-forte-magsafe-charger-stand/?utm_source=dlvr.it&utm_medium=blogger
Top 10 DNS Filtering Solutions to Stay Protected From Cyber Attacks
Before you know about DNS Filtering Solutions, you need to understand that it is a concept that comes in the first place. In this digital world, cybersecurity is essential, and this is a big concern now. Cyber-attacks are happening everywhere in the world, so you not only need to save your company, even you need […]
The post Top 10 DNS Filtering Solutions to Stay Protected From Cyber Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/dns-filtering-solutions/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/dns-filtering-solutions/?utm_source=dlvr.it&utm_medium=blogger
Monday, April 26, 2021
BigBasket Data Leak – Over 20 Million Personal Information and Hashed Passwords Published on a Hacking Forum
A database of about 20 million alleged BigBasket users has leaked on a well-known cybercrime forum. BigBasket is a popular Indian online grocery delivery service that allows people to shop online for food and deliver it to their homes. A threat actor has leaked approximately 20 million BigBasket user records containing personal information and hashed […]
The post BigBasket Data Leak – Over 20 Million Personal Information and Hashed Passwords Published on a Hacking Forum appeared first on Cyber Security News.
https://cybersecuritynews.com/bigbasket-data-leak/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/bigbasket-data-leak/?utm_source=dlvr.it&utm_medium=blogger
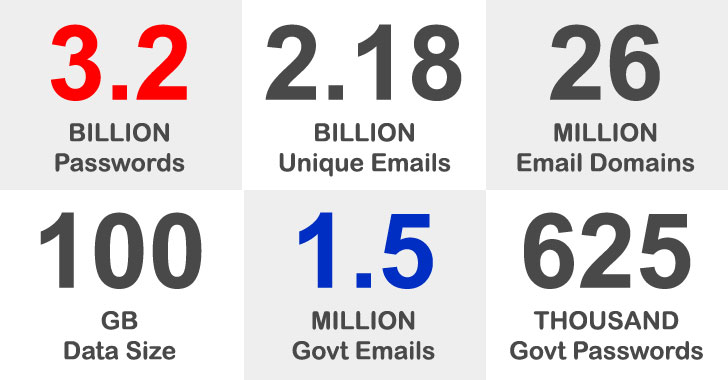
3.2 Billion Leaked Passwords Contain 1.5 Million Records with Government Emails
A staggering number of 3.28 billion passwords linked to 2.18 billion unique email addresses were exposed in what's one of the largest data dumps of breached usernames and passwords. In addition, the leak includes 1,502,909 passwords associated with email addresses from government domains across the world, with the U.S. government alone taking up 625,505 of the exposed passwords, followed by the
https://thehackernews.com/2021/04/32-billion-leaked-passwords-contain-15.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/32-billion-leaked-passwords-contain-15.html?utm_source=dlvr.it&utm_medium=blogger
Instagram Anti-Abuse Tool, Apple Advertiser Restrictions, Terrible Passwords
Read the original article: Instagram Anti-Abuse Tool, Apple Advertiser Restrictions, Terrible Passwords Instagram is rolling out new features to help block spam and abusive messages, Apple releases iOS 14.5 to restrict tracking by advertisers, and a discussion about why people…
Read more → The post Instagram Anti-Abuse Tool, Apple Advertiser Restrictions, Terrible Passwords first appeared on IT Security News.
https://www.itsecuritynews.info/instagram-anti-abuse-tool-apple-advertiser-restrictions-terrible-passwords/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/instagram-anti-abuse-tool-apple-advertiser-restrictions-terrible-passwords/?utm_source=dlvr.it&utm_medium=blogger
Sunday, April 25, 2021
CYBER THREATS: THE FINANCIAL SYSTEM’S TOP RISK
Read the original article: CYBER THREATS: THE FINANCIAL SYSTEM’S TOP RISK This post was originally published by (ISC)² Management. With cyber attacks against financial and banking institutions now a daily occurrence, cyber threats have become the biggest risk to the…
Read more → The post CYBER THREATS: THE FINANCIAL SYSTEM’S TOP RISK first appeared on IT Security News.
https://www.itsecuritynews.info/cyber-threats-the-financial-systems-top-risk-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cyber-threats-the-financial-systems-top-risk-2/?utm_source=dlvr.it&utm_medium=blogger
Web Application Attacks – Types, Impact & Mitigation – Part-4
Read the original article: Web Application Attacks – Types, Impact & Mitigation – Part-4 With this article, we list some of the common web application attacks, impacts, and possible mitig […]Content was cut in order to protect the source.Please visit…
Read more → The post Web Application Attacks – Types, Impact & Mitigation – Part-4 first appeared on IT Security News.
https://www.itsecuritynews.info/web-application-attacks-types-impact-mitigation-part-4-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/web-application-attacks-types-impact-mitigation-part-4-2/?utm_source=dlvr.it&utm_medium=blogger
Top 10 Open Source Cloud Security Tools to Protect Data from Hackers
By seeing the heading of this article, you might be wondering what all about open source cloud? It is a service or solution which got developed by using open source software and technology. These Cloud Security Tools are useful for any public and private models like SaaS, PaaS, laaS, etc. This is completely built and […]
The post Top 10 Open Source Cloud Security Tools to Protect Data from Hackers appeared first on Cyber Security News.
https://cybersecuritynews.com/cloud-security-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cloud-security-tools/?utm_source=dlvr.it&utm_medium=blogger
Saturday, April 24, 2021
Ransomware Strain Qlocker Targeting QNAP NAS Flaws – Patch It!
A new ransomware strain called Qlocker is infecting hundreds of QNAP NAS devices every day and demanding a $550 ransom payment. The first reports of the infections emerged on April 20, with the adversaries behind the operations demanding a bitcoin payment (0.01 bitcoins or about $500.57) to receive the decryption key. QNAP Systems, Inc. (QNAP), […]
The post Ransomware Strain Qlocker Targeting QNAP NAS Flaws – Patch It! appeared first on Cyber Security News.
https://cybersecuritynews.com/ransomware-strain-qlocker/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/ransomware-strain-qlocker/?utm_source=dlvr.it&utm_medium=blogger
Is AI as Dangerous as Nuclear Tech?
Read the original article: Is AI as Dangerous as Nuclear Tech? Saying nuclear power is the safest energy seems wildly inaccurate and misleading, yet often I see people make this claim. It’s always based on wild assumptions about quality control,…
Read more → The post Is AI as Dangerous as Nuclear Tech? first appeared on IT Security News.
https://www.itsecuritynews.info/is-ai-as-dangerous-as-nuclear-tech/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/is-ai-as-dangerous-as-nuclear-tech/?utm_source=dlvr.it&utm_medium=blogger
Passwordstate Password Manager Update Hijacked to Install Backdoor on Thousands of PCs
Click Studios, the Australian software company behind the Passwordstate password management application, has notified customers to reset their passwords following a software supply chain attack. The Adelaide-based firm said a bad actor used sophisticated techniques to compromise the software's update mechanism and used it to drop malware on user computers. The breach is said to have occurred
https://thehackernews.com/2021/04/passwordstate-password-manager-update.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/passwordstate-password-manager-update.html?utm_source=dlvr.it&utm_medium=blogger
Friday, April 23, 2021
Casey’s General Stores Announces Security and Retail Leader Paul Suarez Joins Company as Chief Information Security Officer
Read the original article: Casey’s General Stores Announces Security and Retail Leader Paul Suarez Joins Company as Chief Information Security Officer ANKENY, Iowa–(BUSINESS WIRE)–Casey’s General Stores, Inc. (NASDAQ: CASY), today announced that Paul Suarez has joined the company as chief…
Read more → The post Casey’s General Stores Announces Security and Retail Leader Paul Suarez Joins Company as Chief Information Security Officer first appeared on IT Security News.
https://www.itsecuritynews.info/caseys-general-stores-announces-security-and-retail-leader-paul-suarez-joins-company-as-chief-information-security-officer/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/caseys-general-stores-announces-security-and-retail-leader-paul-suarez-joins-company-as-chief-information-security-officer/?utm_source=dlvr.it&utm_medium=blogger
Top 10 SMTP Test Tools to Detect Server Issues and to Test Email Security
The SMTP test tool is one type of tool which checks your SMTP server’s health status. First, it connects SMTP server then it sends an email. As we all know, for doing B2B business, email is the third most essential thing for conveying any information. The majority is not much concerned about mail, and many […]
The post Top 10 SMTP Test Tools to Detect Server Issues and to Test Email Security appeared first on Cyber Security News.
https://cybersecuritynews.com/smtp-test-tools/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/smtp-test-tools/?utm_source=dlvr.it&utm_medium=blogger
Facebook Busts Palestinian Hackers' Operation Spreading Mobile Spyware
Facebook on Wednesday said it took steps to dismantle malicious activities perpetrated by two state-sponsored hacking groups operating out of Palestine that abused its platform to distribute malware. The social media giant attributed the attacks to a network connected to the Preventive Security Service (PSS), the security apparatus of the State of Palestine, and another threat actor known as
https://thehackernews.com/2021/04/facebook-busts-palestinian-hackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/facebook-busts-palestinian-hackers.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, April 22, 2021
Do CASBs and Cloud SWGs Compete?
Read the original article: Do CASBs and Cloud SWGs Compete? I’m frequently asked whether Secure Web Gateways (SWGs) and Cloud Access Security Brokers (CASBs) compete. After all, they’re both proxies, they both offer data & threat protection, they’re both cloud-based…
Read more → The post Do CASBs and Cloud SWGs Compete? first appeared on IT Security News.
https://www.itsecuritynews.info/do-casbs-and-cloud-swgs-compete/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/do-casbs-and-cloud-swgs-compete/?utm_source=dlvr.it&utm_medium=blogger
WhatsApp Pink – Beware of this New Malware that Takes Control of Your Device
A malware is found that sends automated replies to messages on WhatsApp and other major chat apps. Eager to know what it is? Yes, as the name suggests, it is Whatsapp Pink! What is Whatsapp Pink? “WhatsApp Pink is an updated version of the WhatsApp auto-reply worm we wrote about in January. The Trojan’s updated […]
The post WhatsApp Pink – Beware of this New Malware that Takes Control of Your Device appeared first on Cyber Security News.
https://cybersecuritynews.com/whatsapp-pink/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/whatsapp-pink/?utm_source=dlvr.it&utm_medium=blogger
Deep Analysis: FormBook New Variant Delivered in Phishing Campaign – Part II
Read the original article: Deep Analysis: FormBook New Variant Delivered in Phishing Campaign – Part II FortiGuard Labs captured a phishing campaign sending a PowerPoint document as an email attachment to spread a new variant of the FormBook malware. In…
Read more → The post Deep Analysis: FormBook New Variant Delivered in Phishing Campaign – Part II first appeared on IT Security News.
https://www.itsecuritynews.info/deep-analysis-formbook-new-variant-delivered-in-phishing-campaign-part-ii/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/deep-analysis-formbook-new-variant-delivered-in-phishing-campaign-part-ii/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, April 21, 2021
Malicious App in Google Play Store Hijack SMS Message Notifications to Commit Billing Fraud
Many fraudulent apps have made their way to the Google Play store, targeting Android users in Southwest Asia and the Arabian Peninsula to the tune of more than 700,000 downloads. These malicious App in Google Play Store hijack SMS message notifications to commit Billing Fraud. What are these Fraudulent apps up to?: Pretending as photo […]
The post Malicious App in Google Play Store Hijack SMS Message Notifications to Commit Billing Fraud appeared first on Cyber Security News.
https://cybersecuritynews.com/malicious-app-in-google-play-store/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/malicious-app-in-google-play-store/?utm_source=dlvr.it&utm_medium=blogger
WARNING: Hackers Exploit Unpatched Pulse Secure 0-Day to Breach Organizations
If the Pulse Connect Secure gateway is part of your organization network, you need to be aware of a newly discovered critical zero-day authentication bypass vulnerability (CVE-2021-22893) that is currently being exploited in the wild and for which there is no patch yet. At least two threat actors have been behind a series of intrusions targeting defense, government, and financial organizations
https://thehackernews.com/2021/04/warning-hackers-exploit-unpatched-pulse.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/warning-hackers-exploit-unpatched-pulse.html?utm_source=dlvr.it&utm_medium=blogger
Cryptocurrency-stealing Malware Dubbed HackBoss Stolen over $560,000 USD from the Victims
With the rapid rise in the value of cryptocurrencies such as Bitcoin and Dogecoin, more and more people are fascinated and drawn towards cryptocurrencies. The flip side to this being that even people with malicious intentions are drawn towards it. There are several malware that has been deployed that are specifically targeted at cryptocurrencies. HackBoss […]
The post Cryptocurrency-stealing Malware Dubbed HackBoss Stolen over $560,000 USD from the Victims appeared first on Cyber Security News.
https://cybersecuritynews.com/hackboss-cryptocurrency-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackboss-cryptocurrency-malware/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, April 20, 2021
Beware of New Monero Mining Campaign that Uses ProxyLogon Exploit to Compromise Exchange Servers
Microsoft already released details about a serious vulnerability affecting their Exchange mail server software, a range of threat actors have been targeting exploitable servers with a variety of malware, from webshells to ransomware. SophosLabs researchers say that “those aren’t the only payloads we’ve seen directed at Exchange servers: An unknown attacker has been attempting to […]
The post Beware of New Monero Mining Campaign that Uses ProxyLogon Exploit to Compromise Exchange Servers appeared first on Cyber Security News.
https://cybersecuritynews.com/monero-mining-campaign-exchange/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/monero-mining-campaign-exchange/?utm_source=dlvr.it&utm_medium=blogger
Armis and UK’s Eseye partner to secure connected devices on any cellular network
Read the original article: Armis and UK’s Eseye partner to secure connected devices on any cellular network Global connectivity specialist Eseye and leading agentless device security platform provider Armis, today announced a strategic partnership and joint solution that enables organisations…
Read more → The post Armis and UK’s Eseye partner to secure connected devices on any cellular network first appeared on IT Security News.
https://www.itsecuritynews.info/armis-and-uks-eseye-partner-to-secure-connected-devices-on-any-cellular-network/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/armis-and-uks-eseye-partner-to-secure-connected-devices-on-any-cellular-network/?utm_source=dlvr.it&utm_medium=blogger
Lazarus APT Hackers are now using BMP images to hide RAT malware
A spear-phishing attack operated by a North Korean threat actor targeting its southern counterpart has been found to conceal its malicious code within a bitmap (.BMP) image file to drop a remote access trojan (RAT) capable of stealing sensitive information. Attributing the attack to the Lazarus Group based on similarities to prior tactics adopted by the adversary, researchers from Malwarebytes
https://thehackernews.com/2021/04/lazarus-apt-hackers-are-now-using-bmp.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/lazarus-apt-hackers-are-now-using-bmp.html?utm_source=dlvr.it&utm_medium=blogger
Monday, April 19, 2021
System Admin of FIN7 Hacking Group Sentenced to Ten Years in Prison
Fedir Hladyr, 35, a Ukrainian national, served as a high-level manager and systems administrator for FIN7. He was arrested in Dresden, Germany, in 2018 at the request of U.S. law enforcement and was extradited to Seattle. In September 2019, he pleaded guilty to conspiracy to commit wire fraud and one count of conspiracy to commit […]
The post System Admin of FIN7 Hacking Group Sentenced to Ten Years in Prison appeared first on Cyber Security News.
https://cybersecuritynews.com/system-admin-of-fin7-hacking-group/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/system-admin-of-fin7-hacking-group/?utm_source=dlvr.it&utm_medium=blogger
What is Cyber Terrorism and Ways to Protect Yourself from Cyberattacks?
Cyberterrorism mainly happens because of the massive use of the internet. As a result, you get threaten, data loss, bodily harm, and other dangerous things. They give threaten and intimidation the victim. This process is also called internet terrorism where many terrorist activities happen by hacking personal computers. In this COVID-19 pandemic situation, many computers […]
The post What is Cyber Terrorism and Ways to Protect Yourself from Cyberattacks? appeared first on Cyber Security News.
https://cybersecuritynews.com/cyber-terrorism/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cyber-terrorism/?utm_source=dlvr.it&utm_medium=blogger
Critical Bugs in EtherNet/IP Stack Expose Industrial Systems to DoS, Data Leaks, and RCE Attacks
Critical Bugs in EtherNet/IP stack expose Industrial systems to DoS, data leaks, and RCE Attacks The OpENer EtherNet/IP stack implements the ENIP and CIP protocols that run in many commercial products. This is very popular among the significant SCADA vendors that use it to find security vulnerabilities before threat actors can exploit them. The Claroty Research Team […]
The post Critical Bugs in EtherNet/IP Stack Expose Industrial Systems to DoS, Data Leaks, and RCE Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/critical-bugs-in-ethernet-ip-stack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/critical-bugs-in-ethernet-ip-stack/?utm_source=dlvr.it&utm_medium=blogger
Sunday, April 18, 2021
Whistleblower: Facebook Loophole Allows For Fake Engagement And Inauthentic Activity
Read the original article: Whistleblower: Facebook Loophole Allows For Fake Engagement And Inauthentic Activity The post Whistleblower: Facebook Loophole Allows For Fake Engagement And Inauthentic Activity appeared first on Facecrooks. This week, The Guardian published a bombshell report and interview…
Read more → The post Whistleblower: Facebook Loophole Allows For Fake Engagement And Inauthentic Activity first appeared on IT Security News.
https://www.itsecuritynews.info/whistleblower-facebook-loophole-allows-for-fake-engagement-and-inauthentic-activity/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=whistleblower-facebook-loophole-allows-for-fake-engagement-and-inauthentic-activity
https://www.itsecuritynews.info/whistleblower-facebook-loophole-allows-for-fake-engagement-and-inauthentic-activity/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=whistleblower-facebook-loophole-allows-for-fake-engagement-and-inauthentic-activity
7 Common Cybersecurity Challenges Organizations Struggle With
You don’t have to look far to find news about a data breach in these pandemic-driven days. It’s unfortunate but true that cybersecurity is on every business’s mind while the damage from data breaches and malicious attacks continues to escalate. Even today, organizations are struggling to treat cybersecurity as a grave business threat. The ones […]
The post 7 Common Cybersecurity Challenges Organizations Struggle With appeared first on Cyber Security News.
https://cybersecuritynews.com/7-common-cybersecurity-challenges-organizations-struggle-with/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/7-common-cybersecurity-challenges-organizations-struggle-with/?utm_source=dlvr.it&utm_medium=blogger
Popular Desktop Apps Including Telegram, VLC, Wireshark, & others Affected With 1-click Code Execution Vulnerabilities
Popular Desktop Apps Including Telegram, VLC, Libre-/OpenOffice, Wireshark, and others are affected with 1-click code execution vulnerabilities. These desktop applications are often vulnerable to code execution with user interaction. Let’s further see about code execution vulnerabilities in numerous desktop applications. Everything is with the same root cause, i.e: insufficient validation of user input that is later […]
The post Popular Desktop Apps Including Telegram, VLC, Wireshark, & others Affected With 1-click Code Execution Vulnerabilities appeared first on Cyber Security News.
https://cybersecuritynews.com/popular-desktop-app-flaws/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/popular-desktop-app-flaws/?utm_source=dlvr.it&utm_medium=blogger
Saturday, April 17, 2021
The New Russia Sanctions Resolve a Mystery That Mueller Left Unanswered
Read the original article: The New Russia Sanctions Resolve a Mystery That Mueller Left Unanswered
Read more → The post The New Russia Sanctions Resolve a Mystery That Mueller Left Unanswered first appeared on IT Security News.
https://www.itsecuritynews.info/the-new-russia-sanctions-resolve-a-mystery-that-mueller-left-unanswered/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=the-new-russia-sanctions-resolve-a-mystery-that-mueller-left-unanswered
https://www.itsecuritynews.info/the-new-russia-sanctions-resolve-a-mystery-that-mueller-left-unanswered/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=the-new-russia-sanctions-resolve-a-mystery-that-mueller-left-unanswered
What are the different roles within cybersecurity?
People talk about the cybersecurity job market like it's a monolith, but there are a number of different roles within cybersecurity, depending not only on your skill level and experience but on what you like to do. In fact, Cybercrime Magazine came up with a list of 50 cybersecurity job titles, while CyberSN, a recruiting organization, came up with its own list of 45 cybersecurity job categories
https://thehackernews.com/2021/04/what-are-different-roles-within.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/what-are-different-roles-within.html?utm_source=dlvr.it&utm_medium=blogger
Week in security with Tony Anscombe
Read the original article: Week in security with Tony Anscombe FBI cleans up compromised Exchange servers – Data of Clubhouse users scraped and posted online – WhatsApp bug alert The post Week in security with Tony Anscombe appeared first on…
Read more → The post Week in security with Tony Anscombe first appeared on IT Security News.
https://www.itsecuritynews.info/week-in-security-with-tony-anscombe-113/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=week-in-security-with-tony-anscombe-113
https://www.itsecuritynews.info/week-in-security-with-tony-anscombe-113/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=week-in-security-with-tony-anscombe-113
Friday, April 16, 2021
Swedish Authorities Say Russia Is to Blame for Sports Confederation Hack
Read the original article: Swedish Authorities Say Russia Is to Blame for Sports Confederation Hack
Read more → The post Swedish Authorities Say Russia Is to Blame for Sports Confederation Hack first appeared on IT Security News.
https://www.itsecuritynews.info/swedish-authorities-say-russia-is-to-blame-for-sports-confederation-hack/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=swedish-authorities-say-russia-is-to-blame-for-sports-confederation-hack
https://www.itsecuritynews.info/swedish-authorities-say-russia-is-to-blame-for-sports-confederation-hack/?utm_source=dlvr.it&utm_medium=blogger&utm_campaign=swedish-authorities-say-russia-is-to-blame-for-sports-confederation-hack
Hackers Used 100,000 Google Sites to Install SolarMarket RAT on Victims Device
Several professionals who had searched the internet for professional forms such as invoices, questionnaires, and receipts were lured into downloading a RAT to their system. It has been found that over 100,000 unique pages contain the terms “template”, “invoice”, “receipt”, “questionnaire”, and “resume”. RAT stands for Remote Access Trojan. A RAT is a malware program […]
The post Hackers Used 100,000 Google Sites to Install SolarMarket RAT on Victims Device appeared first on Cyber Security News.
https://cybersecuritynews.com/google-sites-to-install-solarmarket-rat/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/google-sites-to-install-solarmarket-rat/?utm_source=dlvr.it&utm_medium=blogger
Data Encryption: Why Is It So Important?
No one would have imagined a few years ago that cybercrime would become such a big concern as it is today. Billions of attacks are launched against individual devices and entire company networks each passing day with many of them leading to data breaches. Data encryption is touted as one of the best defenses against […]
The post Data Encryption: Why Is It So Important? appeared first on Cyber Security News.
https://cybersecuritynews.com/data-encryption-why-is-it-so-important/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/data-encryption-why-is-it-so-important/?utm_source=dlvr.it&utm_medium=blogger
Thursday, April 15, 2021
US Sanctions Russia and Expels 10 Diplomats Over SolarWinds Cyberattack
The U.S. and U.K. on Thursday formally attributed the supply chain attack of IT infrastructure management company SolarWinds with "high confidence" to government operatives working for Russia's Foreign Intelligence Service (SVR). "Russia's pattern of malign behaviour around the world – whether in cyberspace, in election interference or in the aggressive operations of their intelligence services
https://thehackernews.com/2021/04/us-sanctions-russia-and-expels-10.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/us-sanctions-russia-and-expels-10.html?utm_source=dlvr.it&utm_medium=blogger
YIKES! Hackers flood the web with 100,000 pages offering malicious PDFs
Cybercriminals are resorting to search engine poisoning techniques to lure business professionals into seemingly legitimate Google sites that install a Remote Access Trojan (RAT) capable of carrying out a wide range of attacks. The attack works by leveraging searches for business forms such as invoices, templates, questionnaires, and receipts as a stepping stone toward infiltrating the systems.
https://thehackernews.com/2021/04/yikes-cybercriminals-flood-intrenet.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/yikes-cybercriminals-flood-intrenet.html?utm_source=dlvr.it&utm_medium=blogger
Critical WhatsApp Flaw Let Attackers Hack the Victim Device Remotely
CENSUS identified two vulnerabilities in the popular WhatsApp messenger app for Android. The first of these was independently reported to Facebook and was found to be patched in recent versions, while the second one was communicated by CENSUS to Facebook and was tracked as CVE-2021-24027. At present, both vulnerabilities have been patched. Researchers have explained how […]
The post Critical WhatsApp Flaw Let Attackers Hack the Victim Device Remotely appeared first on Cyber Security News.
https://cybersecuritynews.com/critical-whatsapp-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/critical-whatsapp-flaw/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, April 14, 2021
New WhatsApp Bugs Could've Let Attackers Hack Your Phone Remotely
Facebook-owned WhatsApp recently addressed two security vulnerabilities in its messaging app for Android that could have been exploited to execute malicious code remotely on the device and even compromise encrypted communications. The flaws take aim at devices running Android versions up to and including Android 9 by carrying out what's known as a "man-in-the-disk" attack that makes it possible
https://thehackernews.com/2021/04/new-whatsapp-bug-couldve-let-attackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/new-whatsapp-bug-couldve-let-attackers.html?utm_source=dlvr.it&utm_medium=blogger
New JavaScript Exploit Can Now Carry Out DDR4 Rowhammer Attacks
Academics from Vrije University in Amsterdam and ETH Zurich have published a new research paper describing yet another variation of the Rowhammer attack. Dubbed SMASH (Synchronized MAny-Sided Hammering), the technique can be used to successfully trigger the attack from JavaScript on modern DDR4 RAM cards, notwithstanding extensive mitigations that have been put in place by manufacturers over the
https://thehackernews.com/2021/04/new-javascript-exploit-can-now-carry.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/04/new-javascript-exploit-can-now-carry.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)