Cybersecurity researchers on Tuesday disclosed details of a sophisticated campaign that deploys malicious backdoors for the purpose of exfiltrating information from a number of industry sectors located in Japan. Dubbed "A41APT" by Kaspersky researchers, the findings delve into a new slew of attacks undertaken by APT10 (aka Stone Panda or Cicada) using previously undocumented malware to deliver
https://thehackernews.com/2021/03/hackers-are-implanting-multiple.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, March 31, 2021
Decided to move on from your NGAV/EDR? A Guide for Small Security Teams to What’s Next
Read the original article: Decided to move on from your NGAV/EDR? A Guide for Small Security Teams to What’s Next You’re fully aware of the need to stop threats at the front door and then hunt any that got through…
Read more → The post Decided to move on from your NGAV/EDR? A Guide for Small Security Teams to What’s Next first appeared on IT Security News.
https://www.itsecuritynews.info/decided-to-move-on-from-your-ngav-edr-a-guide-for-small-security-teams-to-whats-next/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/decided-to-move-on-from-your-ngav-edr-a-guide-for-small-security-teams-to-whats-next/?utm_source=dlvr.it&utm_medium=blogger
Nearly 40% of new ransomware families use both data encryption and data theft in attacks
Read the original article: Nearly 40% of new ransomware families use both data encryption and data theft in attacks Data-stealing ransomware attacks, information harvesting malware, and supply chain attacks are among the critical threats to organizations, according to F-Secure. One…
Read more → The post Nearly 40% of new ransomware families use both data encryption and data theft in attacks first appeared on IT Security News.
https://www.itsecuritynews.info/nearly-40-of-new-ransomware-families-use-both-data-encryption-and-data-theft-in-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/nearly-40-of-new-ransomware-families-use-both-data-encryption-and-data-theft-in-attacks/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, March 30, 2021
Ghost Users Haunt Healthcare Firms
Read the original article: Ghost Users Haunt Healthcare Firms Data security hygiene severely lacking among healthcare firms, new research shows. Become a supporter of IT Security News and help us remove the ads. Read the original article: Ghost Users…
Read more → The post Ghost Users Haunt Healthcare Firms first appeared on IT Security News.
https://www.itsecuritynews.info/ghost-users-haunt-healthcare-firms/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ghost-users-haunt-healthcare-firms/?utm_source=dlvr.it&utm_medium=blogger
PHP Git Server Hacked – Attackers Insert Secret Backdoor to Its Source Code
Threat actors have recently managed to gain control of PHP’s Git repository by implementing two back doors to the code. However, the analysts have reported that till now, there is no information on how the attack took place or performed. PHP is an open-source general-purpose computer manuscript language, which is especially suitable for web development […]
The post PHP Git Server Hacked – Attackers Insert Secret Backdoor to Its Source Code appeared first on Cyber Security News.
https://cybersecuritynews.com/php-git-server-hacked/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/php-git-server-hacked/?utm_source=dlvr.it&utm_medium=blogger
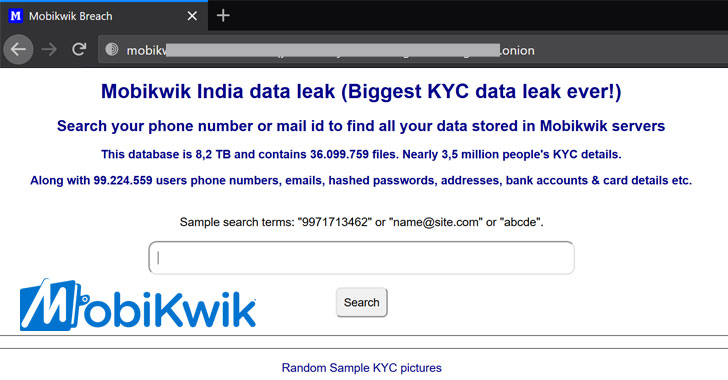
MobiKwik Suffers Major Breach — KYC Data of 3.5 Million Users Exposed
Popular Indian mobile payments service MobiKwik on Monday came under fire after 8.2 terabytes (TB) of data belonging to millions of its users began circulating on the dark web in the aftermath of a major data breach that came to light earlier this month. The leaked data includes sensitive personal information such as:customer names,hashed passwords,email addresses,residential addresses,GPS
https://thehackernews.com/2021/03/mobikwik-suffers-major-breach-kyc-data.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/mobikwik-suffers-major-breach-kyc-data.html?utm_source=dlvr.it&utm_medium=blogger
Monday, March 29, 2021
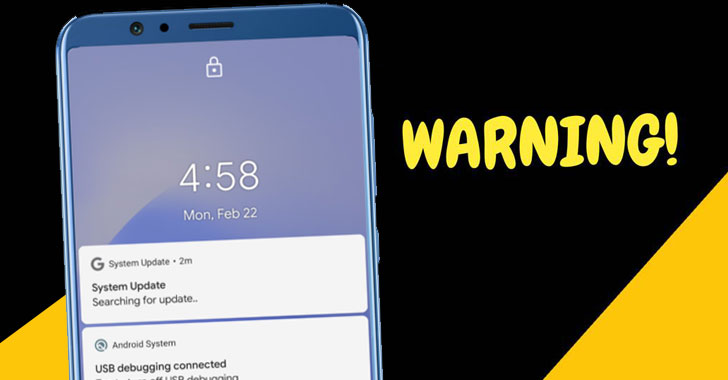
New Advanced Android Malware Poses as “System Update” to Steal Messages, Images and Taking Control of Android Phones
Zimperium zLabs researchers revealed unsecured cloud configurations exposing information in thousands of legitimate iOS and Android apps. zLabs is warning Android users about a sophisticated new malicious app. The new malware disguises itself as a System Update application, and is stealing data, messages, images and taking control of Android phones. Once in control, hackers can […]
The post New Advanced Android Malware Poses as “System Update” to Steal Messages, Images and Taking Control of Android Phones appeared first on Cyber Security News.
https://cybersecuritynews.com/android-malware-poses-as-system-update/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/android-malware-poses-as-system-update/?utm_source=dlvr.it&utm_medium=blogger
PHP's Git Server Hacked to Insert Secret Backdoor to Its Source code
In yet another instance of a software supply chain attack, unidentified actors hacked the official Git server of the PHP programming language and pushed unauthorized updates to insert a secret backdoor into its source code. The two malicious commits were pushed to the self-hosted "php-src" repository hosted on the git.php.net server, illicitly using the names of Rasmus Lerdorf, the author of the
https://thehackernews.com/2021/03/phps-git-server-hacked-to-insert-secret.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/phps-git-server-hacked-to-insert-secret.html?utm_source=dlvr.it&utm_medium=blogger
SpaceX Engineer Pleads Guilty for Insider Trading on the Dark Web
A SpaceX engineer pleaded guilty for exchanging insider trading tips on the dark web. James Roland Jones, aged 33, of Hermosa Beach, California, has pleaded guilty to conspiracy to commit securities fraud. Jones faces a maximum penalty of five years in federal prison. A sentencing date has not yet been set. According to the plea […]
The post SpaceX Engineer Pleads Guilty for Insider Trading on the Dark Web appeared first on Cyber Security News.
https://cybersecuritynews.com/spacex-engineer-pleads-guilty/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/spacex-engineer-pleads-guilty/?utm_source=dlvr.it&utm_medium=blogger
Sunday, March 28, 2021
Over 62,000 Microsoft Exchange Servers, Still Left unpatched
Microsoft has recently published a very new, one-click mitigation tool, as Microsoft has recently identified various 0-day exploits that are generally being used by different threat actors to target the on-premises version of Microsoft Exchange Servers. This Microsoft Exchange On-Premises Mitigation Tool generally enables the customers to address the vulnerabilities immediately that are being exploited […]
The post Over 62,000 Microsoft Exchange Servers, Still Left unpatched appeared first on Cyber Security News.
https://cybersecuritynews.com/over-62000-microsoft-exchange-servers-still-left-unpatched/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/over-62000-microsoft-exchange-servers-still-left-unpatched/?utm_source=dlvr.it&utm_medium=blogger
Multilingual Cybersecurity Awareness Training adapted for your needs
Technology alone cannot protect you from everything. Because the online world is so interconnected, everyone is a target, no matter if you are an individual, small business or huge enterprise. Cybersecurity awareness training teaches your employees – to spot fake…
Read more → The post Multilingual Cybersecurity Awareness Training adapted for your needs first appeared on IT Security News.
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-19/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-19/?utm_source=dlvr.it&utm_medium=blogger
Experts spotted a new advanced Android spyware posing as “System Update”
Read the original article: Experts spotted a new advanced Android spyware posing as “System Update” Researchers spotted a sophisticated Android spyware that implements exfiltration capabilities and surveillance features, including recording audio and phone calls. Experts from security firm Zimperium have…
Read more → The post Experts spotted a new advanced Android spyware posing as “System Update” first appeared on IT Security News.
https://www.itsecuritynews.info/experts-spotted-a-new-advanced-android-spyware-posing-as-system-update/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/experts-spotted-a-new-advanced-android-spyware-posing-as-system-update/?utm_source=dlvr.it&utm_medium=blogger
Saturday, March 27, 2021
Future Focused: A Safer Way to Expose Private Server Names
Read the original article: Future Focused: A Safer Way to Expose Private Server Names Working to stay ahead of bad actors and keep our costumers secure is our priority, that’s why we’re exploring a safer way to publicly advertise private…
Read more → The post Future Focused: A Safer Way to Expose Private Server Names first appeared on IT Security News.
https://www.itsecuritynews.info/future-focused-a-safer-way-to-expose-private-server-names/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/future-focused-a-safer-way-to-expose-private-server-names/?utm_source=dlvr.it&utm_medium=blogger
Watch Out! That Android System Update May Contain A Powerful Spyware
Researchers have discovered a new information-stealing trojan, which targets Android devices with an onslaught of data-exfiltration capabilities — from collecting browser searches to recording audio and phone calls. While malware on Android has previously taken the guise of copycat apps, which go under names similar to legitimate pieces of software, this sophisticated new malicious app
https://thehackernews.com/2021/03/watch-out-that-android-system-update.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/watch-out-that-android-system-update.html?utm_source=dlvr.it&utm_medium=blogger
Apple Issues Urgent Patch Update for Another Zero‑Day Under Attack
Merely weeks after releasing out-of-band patches for iOS, iPadOS, macOS and watchOS, Apple has released yet another security update for iPhone, iPad, Apple Watch to fix a critical zero-day weakness that it says is being actively exploited in the wild. Tracked as CVE-2021-1879, the vulnerability relates to a WebKit flaw that could enable adversaries to process maliciously crafted web content that
https://thehackernews.com/2021/03/apple-issues-urgent-patch-update-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/apple-issues-urgent-patch-update-for.html?utm_source=dlvr.it&utm_medium=blogger
Friday, March 26, 2021
OpenSSL Releases Patches for 2 High-Severity Security Vulnerabilities
The maintainers of OpenSSL have released a fix for two high-severity security flaws in its software that could be exploited to carry out denial-of-service (DoS) attacks and bypass certificate verification. Tracked as CVE-2021-3449 and CVE-2021-3450, both the vulnerabilities have been resolved in an update (version OpenSSL 1.1.1k) released on Thursday. While CVE-2021-3449 affects all OpenSSL
https://thehackernews.com/2021/03/openssl-releases-patches-for-2-high.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/openssl-releases-patches-for-2-high.html?utm_source=dlvr.it&utm_medium=blogger
As Blinken Visits Europe, China Retaliates Against U.S., EU Xinjiang Sanctions
Read the original article: As Blinken Visits Europe, China Retaliates Against U.S., EU Xinjiang Sanctions Secretary of State Antony Blinken met with China's top diplomat Yan Jiechi in Anchorage, Alaska on March 18, 2021. (State Department photo by Ron Przysucha)…
Read more → The post As Blinken Visits Europe, China Retaliates Against U.S., EU Xinjiang Sanctions first appeared on IT Security News.
https://www.itsecuritynews.info/as-blinken-visits-europe-china-retaliates-against-u-s-eu-xinjiang-sanctions/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/as-blinken-visits-europe-china-retaliates-against-u-s-eu-xinjiang-sanctions/?utm_source=dlvr.it&utm_medium=blogger
Another Critical RCE Flaw Discovered in SolarWinds Orion Platform
IT infrastructure management provider SolarWinds on Thursday released a new update to its Orion networking monitoring tool with fixes for four security vulnerabilities, counting two weaknesses that could be exploited by an authenticated attacker to achieve remote code execution (RCE). Chief among them is a JSON deserialization flaw that allows an authenticated user to execute arbitrary code via
https://thehackernews.com/2021/03/solarwinds-orion-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/solarwinds-orion-vulnerability.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, March 25, 2021
A Former IT Consultant Hacked a Company and Deleted 1,200 User Accounts
An IT Contractor, Deepanshu Kher was sentenced to two years in prison for accessing the server of a Carlsbad Company and deleting over 1,200 over the company’s 1,500 Microsoft User Accounts. According to court documents, Kher was employed by an information technology consulting firm from 2017 through May 2018. In 2017, the consulting firm was […]
The post A Former IT Consultant Hacked a Company and Deleted 1,200 User Accounts appeared first on Cyber Security News.
https://cybersecuritynews.com/it-contractor-sentenced/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/it-contractor-sentenced/?utm_source=dlvr.it&utm_medium=blogger
Chinese Hackers Used Facebook to Hack Uighur Muslims Living Abroad
Facebook may be banned in China, but the company on Wednesday said it has disrupted a network of bad actors using its platform to target the Uyghur community and lure them into downloading malicious software that would allow surveillance of their devices. "They targeted activists, journalists and dissidents predominantly among Uyghurs from Xinjiang in China primarily living abroad in Turkey,
https://thehackernews.com/2021/03/chinese-hackers-used-facebook-to-hack.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/chinese-hackers-used-facebook-to-hack.html?utm_source=dlvr.it&utm_medium=blogger
Cloudflare Launches zero-trust Tool Designed to Help Protect Remote Employees from Cyberattacks
Cloudflare is excited to announce that Cloudflare Browser Isolation is now available within Cloudflare for Teams suite of zero trust security and secure web browsing services as an add-on. Teams of any size from startups to large enterprises can benefit from reliable and safe browsing without changing their preferred web browser or setting up complex […]
The post Cloudflare Launches zero-trust Tool Designed to Help Protect Remote Employees from Cyberattacks appeared first on Cyber Security News.
https://cybersecuritynews.com/cloudflare-zero-trust-tool/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cloudflare-zero-trust-tool/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, March 24, 2021
FCC sees data as key to closing digital divide
Read the original article: FCC sees data as key to closing digital divide To ensure Americans have reliable access to high-speed internet, the Federal Communications Commission aims to build a comprehensive, user-friendly dataset on broadband availability. Become a supporter…
Read more → The post FCC sees data as key to closing digital divide first appeared on IT Security News.
https://www.itsecuritynews.info/fcc-sees-data-as-key-to-closing-digital-divide/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/fcc-sees-data-as-key-to-closing-digital-divide/?utm_source=dlvr.it&utm_medium=blogger
5G network slicing vulnerability leaves enterprises exposed to cyberattacks
Read the original article: 5G network slicing vulnerability leaves enterprises exposed to cyberattacks AdaptiveMobile Security today publicly disclosed details of a major security flaw in the architecture of 5G network slicing and virtualized network functions. The fundamental vulnerability has the…
Read more → The post 5G network slicing vulnerability leaves enterprises exposed to cyberattacks first appeared on IT Security News.
https://www.itsecuritynews.info/5g-network-slicing-vulnerability-leaves-enterprises-exposed-to-cyberattacks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/5g-network-slicing-vulnerability-leaves-enterprises-exposed-to-cyberattacks/?utm_source=dlvr.it&utm_medium=blogger
Purple Fox Rootkit Can Now Spread Itself to Other Windows Computers
Purple Fox, a Windows malware previously known for infecting machines by using exploit kits and phishing emails, has now added a new technique to its arsenal that gives it worm-like propagation capabilities. The ongoing campaign makes use of a "novel spreading technique via indiscriminate port scanning and exploitation of exposed SMB services with weak passwords and hashes," according to
https://thehackernews.com/2021/03/purple-fox-rootkit-can-now-spread.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/purple-fox-rootkit-can-now-spread.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, March 23, 2021
Critical Flaws Affecting GE's Universal Relay Pose Threat to Electric Utilities
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has warned of critical security shortcomings in GE's Universal Relay (UR) family of power management devices. "Successful exploitation of these vulnerabilities could allow an attacker to access sensitive information, reboot the UR, gain privileged access, or cause a denial-of-service condition," the agency said in an advisory
https://thehackernews.com/2021/03/critical-flaws-affecting-ges-universal.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/critical-flaws-affecting-ges-universal.html?utm_source=dlvr.it&utm_medium=blogger
‘Half’ Of Exchange Servers Left Unpatched As Attacks Continue
Read the original article: ‘Half’ Of Exchange Servers Left Unpatched As Attacks Continue Only half of Exchange servers have been patched so far, security firm estimates, as it detects tens of thousands of new hacks per day Become a…
Read more → The post ‘Half’ Of Exchange Servers Left Unpatched As Attacks Continue first appeared on IT Security News.
https://www.itsecuritynews.info/half-of-exchange-servers-left-unpatched-as-attacks-continue/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/half-of-exchange-servers-left-unpatched-as-attacks-continue/?utm_source=dlvr.it&utm_medium=blogger
WARNING: A New Android Zero-Day Vulnerability Is Under Active Attack
Google has disclosed that a now-patched vulnerability affecting Android devices that use Qualcomm chipsets is being weaponized by attackers to launch targeted attacks. Tracked as CVE-2020-11261 (CVSS score 8.4), the flaw concerns an "improper input validation" issue in Qualcomm's Graphics component that could be exploited to trigger memory corruption when an attacker-engineered app requests
https://thehackernews.com/2021/03/warning-new-android-zero-day.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/warning-new-android-zero-day.html?utm_source=dlvr.it&utm_medium=blogger
Monday, March 22, 2021
Zoom’s screen-sharing Feature Bug Leaks Sensitive Data
Zoom is a video conferencing and messaging software with support for many different devices. A glitch in Zoom’s display-sharing characteristic exhibits elements of presenters’ screens that they did not intend to share – possibly leaking email messages or passwords. Zoom’s screen-sharing Feature Bug The flaw tracked as (CVE-2021-28133) stems from a glitch in the screen […]
The post Zoom’s screen-sharing Feature Bug Leaks Sensitive Data appeared first on Cyber Security News.
https://cybersecuritynews.com/zooms-screen-sharing-feature-bug/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/zooms-screen-sharing-feature-bug/?utm_source=dlvr.it&utm_medium=blogger
Critical RCE Vulnerability Found in Apache OFBiz ERP Software—Patch Now
The Apache Software Foundation on Friday addressed a high severity vulnerability in Apache OFBiz that could have allowed an unauthenticated adversary to remotely seize control of the open-source enterprise resource planning (ERP) system. Tracked as CVE-2021-26295, the flaw affects all versions of the software prior to 17.12.06 and employs an "unsafe deserialization" as an attack vector to permit
https://thehackernews.com/2021/03/critical-rce-vulnerability-found-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/critical-rce-vulnerability-found-in.html?utm_source=dlvr.it&utm_medium=blogger
Popular remote lesson monitoring program could be exploited to attack student PCs
Read the original article: Popular remote lesson monitoring program could be exploited to attack student PCs The vulnerabilities allowed attackers full and unfettered access to student PCs. Become a supporter of IT Security News and help us remove the…
Read more → The post Popular remote lesson monitoring program could be exploited to attack student PCs first appeared on IT Security News.
https://www.itsecuritynews.info/popular-remote-lesson-monitoring-program-could-be-exploited-to-attack-student-pcs/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/popular-remote-lesson-monitoring-program-could-be-exploited-to-attack-student-pcs/?utm_source=dlvr.it&utm_medium=blogger
Sunday, March 21, 2021
Tech Gaint Acer Hit by a REvil Ransomware – Attackers Demanding $50,000,000 Ransom
Taiwanese computer manufacturer Acer has been hit by a REvil ransomware attack where the threat actors are demanding the largest known ransom to date, $50,000,000. Acer is the world’s 6th-largest PC vendor by unit sales as of January 2021 and well-known for laptops, desktops, and monitors. Who is REvil? A Computer Weekly report calls REvil […]
The post Tech Gaint Acer Hit by a REvil Ransomware – Attackers Demanding $50,000,000 Ransom appeared first on Cyber Security News.
https://cybersecuritynews.com/acer-hit-by-revil-ransomware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/acer-hit-by-revil-ransomware/?utm_source=dlvr.it&utm_medium=blogger
E-Sim Fraud and Prevention
Read the original article: E-Sim Fraud and Prevention Some mobile service providers have eSIM-enabled cell phones which don’t need an actual SIM card. They have a little chip inside the phone and the data on this eSIM is rewritable…
Read more → The post E-Sim Fraud and Prevention first appeared on IT Security News.
https://www.itsecuritynews.info/e-sim-fraud-and-prevention/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/e-sim-fraud-and-prevention/?utm_source=dlvr.it&utm_medium=blogger
USENIX Enigma 2021 – Nicole Fern’s ‘Hardware: A Double-Edged Sword For Security’
Read the original article: USENIX Enigma 2021 – Nicole Fern’s ‘Hardware: A Double-Edged Sword For Security’ Many thanks to USENIX Enigma 2021 for publishing these outstanding conference videos on the YouTube USENIX Channel; don’t miss this erudite 27 video information…
Read more → The post USENIX Enigma 2021 – Nicole Fern’s ‘Hardware: A Double-Edged Sword For Security’ first appeared on IT Security News.
https://www.itsecuritynews.info/usenix-enigma-2021-nicole-ferns-hardware-a-double-edged-sword-for-security/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/usenix-enigma-2021-nicole-ferns-hardware-a-double-edged-sword-for-security/?utm_source=dlvr.it&utm_medium=blogger
Saturday, March 20, 2021
Critical F5 BIG-IP Bug Under Active Attacks After PoC Exploit Posted Online
Almost 10 days after application security company F5 Networks released patches for critical vulnerabilities in its BIG-IP and BIG-IQ products, adversaries have begun opportunistically mass scanning and targeting exposed and unpatched networking devices to break into enterprise networks. News of in the wild exploitation development comes on the heels of a proof-of-concept exploit code that
https://thehackernews.com/2021/03/latest-f5-big-ip-bug-under-active.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/latest-f5-big-ip-bug-under-active.html?utm_source=dlvr.it&utm_medium=blogger
Magecart Hackers Hide the Credit Card Data in Image Files
Nowadays the cybercriminals are mainly focusing on credit card theft, as they always try their best to find different methods to successfully execute such thefts. The cybersecurity researchers at website security company Sucuri have discovered the new exfiltration method while investigating a compromised online shop that was initially running version 2 of the open-source Magento […]
The post Magecart Hackers Hide the Credit Card Data in Image Files appeared first on Cyber Security News.
https://cybersecuritynews.com/magecart-hackers-hide-credit-card-data/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/magecart-hackers-hide-credit-card-data/?utm_source=dlvr.it&utm_medium=blogger
Microsoft Bug Deleting the Downloaded Files from Microsoft Teams and SharePoint files
Microsoft SharePoint and Microsoft Teams users report that the downloaded files are missing or moved to the Recycle Bin. Microsoft Sharepoint administrators look into the issue, they find the SharePoint folder structure to be intact, but all of the files are missing. Ultimately, they noticed that the files have been deleted and are now located […]
The post Microsoft Bug Deleting the Downloaded Files from Microsoft Teams and SharePoint files appeared first on Cyber Security News.
https://cybersecuritynews.com/microsoft-bug-deleting-the-downloaded-files-from-microsoft-teams-and-sharepoint-files/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/microsoft-bug-deleting-the-downloaded-files-from-microsoft-teams-and-sharepoint-files/?utm_source=dlvr.it&utm_medium=blogger
Friday, March 19, 2021
Hackers Infecting Apple App Developers With Trojanized Xcode Projects
Cybersecurity researchers on Thursday disclosed a new attack wherein threat actors are leveraging Xcode as an attack vector to compromise Apple platform developers with a backdoor, adding to a growing trend that involves targeting developers and researchers with malicious attacks. Dubbed "XcodeSpy," the trojanized Xcode project is a tainted version of a legitimate, open-source project available
https://thehackernews.com/2021/03/hackers-infecting-apple-app-developers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/hackers-infecting-apple-app-developers.html?utm_source=dlvr.it&utm_medium=blogger
Facial recognition ID with a twist: Smiles, winks and other facial movements for access
Read the original article: Facial recognition ID with a twist: Smiles, winks and other facial movements for access Concurrent Two-Factor Identity Verification requires both one’s facial identity and a specific facial motion to gain access. To set it up, a…
Read more → The post Facial recognition ID with a twist: Smiles, winks and other facial movements for access first appeared on IT Security News.
https://www.itsecuritynews.info/facial-recognition-id-with-a-twist-smiles-winks-and-other-facial-movements-for-access/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/facial-recognition-id-with-a-twist-smiles-winks-and-other-facial-movements-for-access/?utm_source=dlvr.it&utm_medium=blogger
New Zoom Screen-Sharing Bug Lets Other Users Access Restricted Apps
A newly discovered glitch in Zoom's screen sharing feature can accidentally leak sensitive information to other attendees in a call, according to the latest findings. Tracked as CVE-2021-28133, the unpatched security vulnerability makes it possible to reveal contents of applications that are not shared, but only briefly, thereby making it harder to exploit it in the wild. It's worth pointing out
https://thehackernews.com/2021/03/new-zoom-screen-sharing-bug-lets-other.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/new-zoom-screen-sharing-bug-lets-other.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, March 18, 2021
Critical RCE Flaw Reported in MyBB Forum Software—Patch Your Sites
A pair of critical vulnerabilities in a popular bulletin board software called MyBB could have been chained together to achieve remote code execution (RCE) without the need for prior access to a privileged account. The flaws, which were discovered by independent security researchers Simon Scannell and Carl Smith, were reported to the MyBB Team on February 22, following which it released an
https://thehackernews.com/2021/03/critical-rce-flaw-reported-in-mybb.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/critical-rce-flaw-reported-in-mybb.html?utm_source=dlvr.it&utm_medium=blogger
Flaws in Two Popular WordPress Plugins Affect Over 7 Million Websites
Researchers have disclosed vulnerabilities in multiple WordPress plugins that, if successfully exploited, could allow an attacker to run arbitrary code and take over a website in certain scenarios. The flaws were uncovered in Elementor, a website builder plugin used on more than seven million sites, and WP Super Cache, a tool used to serve cached pages of a WordPress site. According to Wordfence
https://thehackernews.com/2021/03/flaws-in-two-popular-wordpress-plugins.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/flaws-in-two-popular-wordpress-plugins.html?utm_source=dlvr.it&utm_medium=blogger
Passwords that have been hacked over 50,000 times
Read the original article: Passwords that have been hacked over 50,000 times Media has been trying its best to create awareness among online users about the need to go for passwords that are difficult to guess or hack. Despite that,…
Read more → The post Passwords that have been hacked over 50,000 times first appeared on IT Security News.
https://www.itsecuritynews.info/passwords-that-have-been-hacked-over-50000-times/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/passwords-that-have-been-hacked-over-50000-times/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, March 17, 2021
New Mirai Variant Targeting IoT & Network Security Devices
Unit 42 researchers observed a new Mirai variant targeting IoT and network security devices. They discovered attacks leveraging several vulnerabilities, including: VisualDoor (a SonicWall SSL-VPN exploit). CVE-2020-25506 (a D-Link DNS-320 firewall exploit). CVE-2020-26919 (a Netgear ProSAFE Plus exploit). Possibly CVE-2019-19356 (a Netis WF2419 wireless router exploit). Three other IoT vulnerabilities yet to be identified. The […]
The post New Mirai Variant Targeting IoT & Network Security Devices appeared first on Cyber Security News.
https://cybersecuritynews.com/new-mirai-variant-iot/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/new-mirai-variant-iot/?utm_source=dlvr.it&utm_medium=blogger
Apple May Start Delivering Security Patches Separately From Other OS Updates
Apple may be changing the way it delivers security patches to its devices running iOS and iPadOS mobile operating systems. According to code spotted in iOS 14.5, the iPhone maker is reportedly working on a method for delivering security fixes independently of other OS updates. The changes were first reported by the 9to5Mac website. While Google's Android has had monthly security
https://thehackernews.com/2021/03/apple-may-start-delivering-security.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/apple-may-start-delivering-security.html?utm_source=dlvr.it&utm_medium=blogger
How to ensure security and trust in connected cars
Read the original article: How to ensure security and trust in connected cars The cars we drive today have become truly connected objects, capable of a variety of functionalities that both users and manufacturers could have only dreamed of in…
Read more → The post How to ensure security and trust in connected cars first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-ensure-security-and-trust-in-connected-cars/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-to-ensure-security-and-trust-in-connected-cars/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, March 16, 2021
Latest Mirai Variant Targets SonicWall, D-Link and IoT Devices
Read the original article: Latest Mirai Variant Targets SonicWall, D-Link and IoT Devices A new Mirai variant is targeting known flaws in D-Link, Netgear and SonicWall devices, as well as newly-discovered flaws in unknown IoT devices. Become a supporter…
Read more → The post Latest Mirai Variant Targets SonicWall, D-Link and IoT Devices first appeared on IT Security News.
https://www.itsecuritynews.info/latest-mirai-variant-targets-sonicwall-d-link-and-iot-devices/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/latest-mirai-variant-targets-sonicwall-d-link-and-iot-devices/?utm_source=dlvr.it&utm_medium=blogger
New Mirai Variant and ZHtrap Botnet Malware Emerge in the Wild
Cybersecurity researchers on Monday disclosed a new wave of ongoing attacks exploiting multiple vulnerabilities to deploy Mirai variants on compromised systems. "Upon successful exploitation, the attackers try to download a malicious shell script, which contains further infection behaviors such as downloading and executing Mirai variants and brute-forcers," Palo Alto Networks' Unit 42 Threat
https://thehackernews.com/2021/03/new-mirai-variant-and-zhtrap-botnet.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/new-mirai-variant-and-zhtrap-botnet.html?utm_source=dlvr.it&utm_medium=blogger
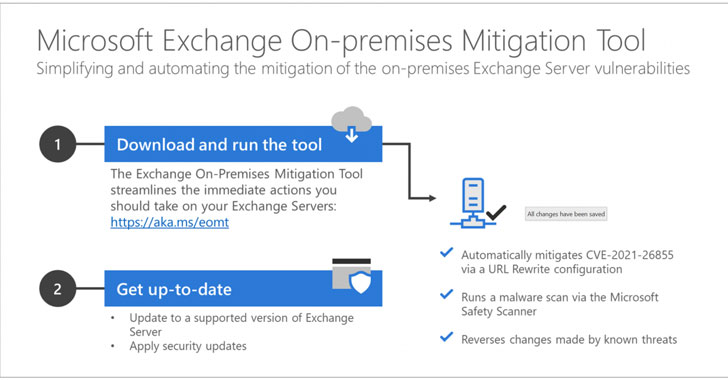
Use This One-Click Mitigation Tool from Microsoft to Prevent Exchange Attacks
Microsoft on Monday released a one-click mitigation software that applies all the necessary countermeasures to secure vulnerable environments against the ongoing widespread ProxyLogon Exchange Server cyberattacks. Called Exchange On-premises Mitigation Tool (EOMT), the PowerShell-based script serves to mitigate against current known attacks using CVE-2021-26855, scan the Exchange Server using
https://thehackernews.com/2021/03/use-this-one-click-mitigation-tool-from.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/use-this-one-click-mitigation-tool-from.html?utm_source=dlvr.it&utm_medium=blogger
Monday, March 15, 2021
A Tip For Easy SQL-based Big Data Analysis: Use a Temporary Dataset
Read the original article: A Tip For Easy SQL-based Big Data Analysis: Use a Temporary Dataset Every once in a while we’re required to analyze big data on a wide time range. Here’s a common example: “Can you analyze what…
Read more → The post A Tip For Easy SQL-based Big Data Analysis: Use a Temporary Dataset first appeared on IT Security News.
https://www.itsecuritynews.info/a-tip-for-easy-sql-based-big-data-analysis-use-a-temporary-dataset/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/a-tip-for-easy-sql-based-big-data-analysis-use-a-temporary-dataset/?utm_source=dlvr.it&utm_medium=blogger
CEO of Encrypted Chat Platform Indicted for Aiding Organised Criminals
The U.S. Department of Justice (DoJ) on Friday announced an indictment against Jean-Francois Eap, the CEO of encrypted messaging company Sky Global, and an associate for wilfully participating in a criminal enterprise to help international drug traffickers avoid law enforcement. Eap (also known as "888888") and Thomas Herdman, a former high-level distributor of Sky Global devices, have been
https://thehackernews.com/2021/03/ceo-of-encrypted-chat-platform-indicted.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/ceo-of-encrypted-chat-platform-indicted.html?utm_source=dlvr.it&utm_medium=blogger
Biden administration reveals probe into government security has found holes, wants more private sector collaboration as the cure
Read the original article: Biden administration reveals probe into government security has found holes, wants more private sector collaboration as the cure Plans include replicating Singapore’s consumer tech security ratings scheme The Biden administration has revealed that its probe into…
Read more → The post Biden administration reveals probe into government security has found holes, wants more private sector collaboration as the cure first appeared on IT Security News.
https://www.itsecuritynews.info/biden-administration-reveals-probe-into-government-security-has-found-holes-wants-more-private-sector-collaboration-as-the-cure/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/biden-administration-reveals-probe-into-government-security-has-found-holes-wants-more-private-sector-collaboration-as-the-cure/?utm_source=dlvr.it&utm_medium=blogger
Sunday, March 14, 2021
Judge Rules Google Must Face Lawsuit Alleging Chrome Tracks Users in Incognito Mode
Read the original article: Judge Rules Google Must Face Lawsuit Alleging Chrome Tracks Users in Incognito Mode A judge in California has ruled that Google must face a class action lawsuit alleging that it secretly tracks the online activity of…
Read more → The post Judge Rules Google Must Face Lawsuit Alleging Chrome Tracks Users in Incognito Mode first appeared on IT Security News.
https://www.itsecuritynews.info/judge-rules-google-must-face-lawsuit-alleging-chrome-tracks-users-in-incognito-mode/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/judge-rules-google-must-face-lawsuit-alleging-chrome-tracks-users-in-incognito-mode/?utm_source=dlvr.it&utm_medium=blogger
Penetration testing
Penetration testing is the technical analysis of the safety level of IT systems and networks. We offer a complete investigation of the hardware / software systems for security vulnerabilities. If you have at least one online service, then you must…
Read more → The post Penetration testing first appeared on IT Security News.
https://www.itsecuritynews.info/penetration-testing-18/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/penetration-testing-18/?utm_source=dlvr.it&utm_medium=blogger
Saturday, March 13, 2021
BSides Huntsville 2021 – Joanna Burkey’s ‘Keynote – Cybersecurity As An Ecosystem’
Read the original article: BSides Huntsville 2021 – Joanna Burkey’s ‘Keynote – Cybersecurity As An Ecosystem’ Many thanks to BSides Huntsville 2021 for publishing their tremendous conference videos on the organization’s YouTube channel; one of the best BSides for this…
Read more → The post BSides Huntsville 2021 – Joanna Burkey’s ‘Keynote – Cybersecurity As An Ecosystem’ first appeared on IT Security News.
https://www.itsecuritynews.info/bsides-huntsville-2021-joanna-burkeys-keynote-cybersecurity-as-an-ecosystem/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/bsides-huntsville-2021-joanna-burkeys-keynote-cybersecurity-as-an-ecosystem/?utm_source=dlvr.it&utm_medium=blogger
How to Export Your Passwords From LastPass
Read the original article: How to Export Your Passwords From LastPass The popular security service is severely limiting its free tier starting March 16. If you’d like to move your passwords to another manager, here’s how. Become a supporter…
Read more → The post How to Export Your Passwords From LastPass first appeared on IT Security News.
https://www.itsecuritynews.info/how-to-export-your-passwords-from-lastpass/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-to-export-your-passwords-from-lastpass/?utm_source=dlvr.it&utm_medium=blogger
CompTIA Security Certification Prep — Lifetime Access for just $30
At long last, top companies are starting to take cybersecurity seriously. As a consequence, technical recruiters are looking for people with hacking skills and certifications to prove it. CompTIA is seen as the gold standard when it comes to cybersecurity exams, with several certifications to choose from. If you would like to scoop them all, The CompTIA Security Infrastructure Expert Bundle is
https://thehackernews.com/2021/03/comptia-security-certification-prep.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/comptia-security-certification-prep.html?utm_source=dlvr.it&utm_medium=blogger
Friday, March 12, 2021
Vulnerability in Million Times Downloaded iPhone app Let Attacker Listen to any User’s Call Recording
The “Automatic call recorder” application is one of the popular applications used by iPhone users to record their calls. The app is among top-grossing in the Business category of App Store currently #15 in the downloads in the Business Category worldwide. PingSafe AI, a security company that monitors multiple breaches in real-time, has uncovered a […]
The post Vulnerability in Million Times Downloaded iPhone app Let Attacker Listen to any User’s Call Recording appeared first on Cyber Security News.
https://cybersecuritynews.com/automatic-call-recorder-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/automatic-call-recorder-flaw/?utm_source=dlvr.it&utm_medium=blogger
NimzaLoader Malware Developed Using a Rare Programming Language to Avoid Detection
The research team from Proofpoint observed an interesting email campaign by a threat actor and tracked it as ‘TA800’. The TA800 threat group is distributing a malware loader, which researchers call NimzaLoader, via ongoing, highly-targeted spear-phishing emails. This actor has predominantly used BazaLoader since April of 2020, but on February 3rd, 2021 they distributed a […]
The post NimzaLoader Malware Developed Using a Rare Programming Language to Avoid Detection appeared first on Cyber Security News.
https://cybersecuritynews.com/nimzaloader-malware-developed-using-a-rare-programming/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/nimzaloader-malware-developed-using-a-rare-programming/?utm_source=dlvr.it&utm_medium=blogger
Hackers Are Targeting Microsoft Exchange Servers With Ransomware
It didn't take long. Intelligence agencies and cybersecurity researchers had been warning that unpatched Exchange Servers could open the pathway for ransomware infections in the wake of swift escalation of the attacks since last week. Now it appears that threat actors have caught up. According to the latest reports, cybercriminals are leveraging the heavily exploited ProxyLogon Exchange Server
https://thehackernews.com/2021/03/icrosoft-exchange-ransomware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/icrosoft-exchange-ransomware.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, March 11, 2021
Does a VPN Protect You From Hackers?
A VPN does indeed protect you from hackers along with a myriad of other benefits. This is the cheapest, yet essential, form of security you can add to your everyday life. A VPN enhances security and privacy even from your internet service provider. A VPN will encrypt all traffic between you and your server making […]
The post Does a VPN Protect You From Hackers? appeared first on Cyber Security News.
https://cybersecuritynews.com/does-a-vpn-protect-you-from-hackers/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/does-a-vpn-protect-you-from-hackers/?utm_source=dlvr.it&utm_medium=blogger
Fixing the Weakest Link — The Passwords — in Cybersecurity Today
Password security has long been an issue for businesses and their cybersecurity standards. Account passwords are often the weakest link in the overall security posture for many organizations. Many companies have used Microsoft's default password policies for decades. While these can be customized, businesses often accept the default values for their organization. The Windows default password
https://thehackernews.com/2021/03/fixing-weakest-link-passwords-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/fixing-weakest-link-passwords-in.html?utm_source=dlvr.it&utm_medium=blogger
Cryptomining Botnet z0Miner Targeting ElasticSearch and Jenkins RCE Vulnerabilities
A crypto mining botnet spotted in the previous year is currently targeting and attempting to take control of Jenkins and ElasticSearch servers to mine for Monero (XMR) cryptocurrency. z0Miner is a malicious mining family that spotted active by Tencent Security Team. When z0Miner was initially active, it used Weblogic’s unauthorized command execution vulnerability to spread. […]
The post Cryptomining Botnet z0Miner Targeting ElasticSearch and Jenkins RCE Vulnerabilities appeared first on Cyber Security News.
https://cybersecuritynews.com/cryptomining-botnet-z0miner/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/cryptomining-botnet-z0miner/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, March 10, 2021
Critical Pre-Auth RCE Flaw Found in F5 Big-IP Platform — Patch ASAP!
Application security company F5 Networks on Wednesday published an advisory warning of four critical vulnerabilities impacting multiple products that could result in a denial of service (DoS) attack and even unauthenticated remote code execution on target networks. The patches concern a total of seven related flaws (from CVE-2021-22986 through CVE-2021-22992), two of which were discovered and
https://thehackernews.com/2021/03/critical-pre-auth-rce-flaw-found-in-f5.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/critical-pre-auth-rce-flaw-found-in-f5.html?utm_source=dlvr.it&utm_medium=blogger
Researchers Unveil New Linux Malware Linked to Chinese Hackers
Cybersecurity researchers on Wednesday shed light on a new sophisticated backdoor targeting Linux endpoints and servers that's believed to be the work of Chinese nation-state actors. Dubbed "RedXOR" by Intezer, the backdoor masquerades as a polkit daemon, with similarities found between the malware and those previously associated with the Winnti Umbrella (or Axiom) threat group such as PWNLNX,
https://thehackernews.com/2021/03/researchers-unveil-new-linux-malware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/researchers-unveil-new-linux-malware.html?utm_source=dlvr.it&utm_medium=blogger
FIN8 Hackers Return With More Powerful Version of BADHATCH PoS Malware
Threat actors known for keeping a low profile do so by ceasing operations for prolonged periods in between to evade attracting any attention as well as constantly refining their toolsets to fly below the radar of many detection technologies. One such group is FIN8, a financially motivated threat actor that's back in action after a year-and-a-half hiatus with a powerful version of a backdoor with
https://thehackernews.com/2021/03/fin8-hackers-return-with-more-powerful.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/fin8-hackers-return-with-more-powerful.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, March 9, 2021
Microsoft Issues Security Patches for 82 Flaws — IE 0-Day Under Active Attacks
Microsoft plugged as many as 89 security flaws as part of its monthly Patch Tuesday updates released today, including fixes for an actively exploited zero-day in Internet Explorer that could permit an attacker to run arbitrary code on target machines. Of these flaws, 14 are listed as Critical, and 75 are listed as Important in severity, out of which two of the bugs are described as publicly
https://thehackernews.com/2021/03/microsoft-issues-security-patches-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/microsoft-issues-security-patches-for.html?utm_source=dlvr.it&utm_medium=blogger
McAfee Sells its Enterprise Business to Symphony Technology Group in $4.0 Billion Deal
McAfee Corp., the device-to-cloud cybersecurity company has disclosed it has entered into a definitive agreement to sell its Enterprise business to a consortium led by Symphony Technology Group (STG) in an all-cash transaction for $4.0 billion. McAfee’s Enterprise business has set the pace and standard within the cybersecurity industry for more than 30 years and […]
The post McAfee Sells its Enterprise Business to Symphony Technology Group in $4.0 Billion Deal appeared first on Cyber Security News.
https://cybersecuritynews.com/mcafee-sells-its-enterprise-business/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/mcafee-sells-its-enterprise-business/?utm_source=dlvr.it&utm_medium=blogger
Microsoft Exchange Hackers Also Breached European Banking Authority
The European Banking Authority (EBA) on Sunday said it had been a victim of a cyberattack targeting its Microsoft Exchange Servers, forcing it to temporarily take its email systems offline as a precautionary measure. "As the vulnerability is related to the EBA's email servers, access to personal data through emails held on that servers may have been obtained by the attacker," the Paris-based
https://thehackernews.com/2021/03/microsoft-exchange-hackers-also.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/microsoft-exchange-hackers-also.html?utm_source=dlvr.it&utm_medium=blogger
Monday, March 8, 2021
Apple Issues Patch for Remote Hacking Bug Affecting Billions of its Devices
Apple has released out-of-band patches for iOS, macOS, watchOS, and Safari browsers to address a security flaw that could allow attackers to run arbitrary code on devices via malicious web content. Tracked as CVE-2021-1844, the vulnerability was discovered and reported to the company by Clément Lecigne of Google's Threat Analysis Group and Alison Huffman of Microsoft Browser Vulnerability
https://thehackernews.com/2021/03/apple-issues-patch-for-remote-hacking.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/apple-issues-patch-for-remote-hacking.html?utm_source=dlvr.it&utm_medium=blogger
Why Data Privacy Should Be on President Biden’s Agenda for His First 100 Days
Read the original article: Why Data Privacy Should Be on President Biden’s Agenda for His First 100 Days The new administration is in an excellent position to make significant progress on data privacy — not just because it’s needed, but…
Read more → The post Why Data Privacy Should Be on President Biden’s Agenda for His First 100 Days first appeared on IT Security News.
https://www.itsecuritynews.info/why-data-privacy-should-be-on-president-bidens-agenda-for-his-first-100-days/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/why-data-privacy-should-be-on-president-bidens-agenda-for-his-first-100-days/?utm_source=dlvr.it&utm_medium=blogger
Malware Can Exploit New Flaw in Intel CPUs to Launch Side-Channel Attacks
A new research has yielded yet another means to pilfer sensitive data by exploiting what's the first "on-chip, cross-core" side-channel in Intel Coffee Lake and Skylake processors. Published by a group of academics from the University of Illinois at Urbana-Champaign, the findings are expected to be presented at the USENIX Security Symposium coming this August. While information leakage attacks
https://thehackernews.com/2021/03/malware-can-exploit-new-flaw-in-intel.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/03/malware-can-exploit-new-flaw-in-intel.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, March 7, 2021
US National Security Council urges review of Exchange Servers in wake of Hafnium attack
Read the original article: US National Security Council urges review of Exchange Servers in wake of Hafnium attack Don’t just patch, check for p0wnage, says top natsec team The Biden administration has urged users of Microsoft’s Exchange mail and messaging…
Read more → The post US National Security Council urges review of Exchange Servers in wake of Hafnium attack first appeared on IT Security News.
https://www.itsecuritynews.info/us-national-security-council-urges-review-of-exchange-servers-in-wake-of-hafnium-attack/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/us-national-security-council-urges-review-of-exchange-servers-in-wake-of-hafnium-attack/?utm_source=dlvr.it&utm_medium=blogger
Creator of McAfee Antivirus Software Charged For Conspiracy?
Read the original article: Creator of McAfee Antivirus Software Charged For Conspiracy? Creator of McAfee antivirus software, Businessman John McAfee is charged under a conspiracy to commit fraud and money laundering in the U.S. McAfee and his bodyguard Jimmy…
Read more → The post Creator of McAfee Antivirus Software Charged For Conspiracy? first appeared on IT Security News.
https://www.itsecuritynews.info/creator-of-mcafee-antivirus-software-charged-for-conspiracy/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/creator-of-mcafee-antivirus-software-charged-for-conspiracy/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)