Read the original article: Axonius raises $100 million to protect IoT devices from cyberattack Axonius, a cybersecurity startup focused on the IoT sector, has raised $100 million at a $1 billion valuation. Become a supporter of IT Security News…
Read more → The post Axonius raises $100 million to protect IoT devices from cyberattack first appeared on IT Security News.
https://www.itsecuritynews.info/axonius-raises-100-million-to-protect-iot-devices-from-cyberattack/?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 28, 2021
Penetration testing
Penetration testing is the technical analysis of the safety level of IT systems and networks. We offer a complete investigation of the hardware / software systems for security vulnerabilities. If you have at least one online service, then you must…
Read more → The post Penetration testing first appeared on IT Security News.
https://www.itsecuritynews.info/penetration-testing-16/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/penetration-testing-16/?utm_source=dlvr.it&utm_medium=blogger
Lazarus hacker Group Attack Defence Industries with custom-made Malware ThreatNeedle
Read the original article: Lazarus hacker Group Attack Defence Industries with custom-made Malware ThreatNeedle Lazarus has now added the defence industry to its growing list of victims. Lazarus is a North Korean hacking group that has been active since 2009.…
Read more → The post Lazarus hacker Group Attack Defence Industries with custom-made Malware ThreatNeedle first appeared on IT Security News.
https://www.itsecuritynews.info/lazarus-hacker-group-attack-defence-industries-with-custom-made-malware-threatneedle/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/lazarus-hacker-group-attack-defence-industries-with-custom-made-malware-threatneedle/?utm_source=dlvr.it&utm_medium=blogger
Saturday, February 27, 2021
Steris Corporation, The Latest Victim of Ransomware Gang Called ‘Clop’.
Read the original article: Steris Corporation, The Latest Victim of Ransomware Gang Called ‘Clop’. Data related to a customer of a recently targeted California-based private cloud solutions firm Accellion is being published online for sale by threat actors. Accellion…
Read more → The post Steris Corporation, The Latest Victim of Ransomware Gang Called ‘Clop’. first appeared on IT Security News.
https://www.itsecuritynews.info/steris-corporation-the-latest-victim-of-ransomware-gang-called-clop/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/steris-corporation-the-latest-victim-of-ransomware-gang-called-clop/?utm_source=dlvr.it&utm_medium=blogger
Review: Perlroth’s book on the cyberarms market
Read the original article: Review: Perlroth’s book on the cyberarms market New York Times reporter Nicole Perlroth has written a book on zero-days and nation-state hacking entitled “This Is How They Tell Me The World Ends”. Here is my review.…
Read more → The post Review: Perlroth’s book on the cyberarms market first appeared on IT Security News.
https://www.itsecuritynews.info/review-perlroths-book-on-the-cyberarms-market-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/review-perlroths-book-on-the-cyberarms-market-2/?utm_source=dlvr.it&utm_medium=blogger
Critical Vulnerability in Cisco Systems allows a Remote Attacker to Bypass Authentication
A critical vulnerability in Cisco Systems’ intersite policy manager software could allow a remote attacker to bypass authentication. Three critical flaws fixed by Cisco this week. The vulnerabilities exist in Cisco’s ACI Multi-Site Orchestrator (ACI MSO) this is Cisco’s management software for businesses, which allows them to monitor the health of all interconnected policy-management sites. […]
The post Critical Vulnerability in Cisco Systems allows a Remote Attacker to Bypass Authentication appeared first on Cyber Security News.
https://cybersecuritynews.com/critical-cisco-flaw/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/critical-cisco-flaw/?utm_source=dlvr.it&utm_medium=blogger
Friday, February 26, 2021
The hidden business costs of working remotely
Read the original article: The hidden business costs of working remotely The benefits of working remotely are numerous, but studies are finding there are significant hidden costs that need to be factored in. Become a supporter of IT Security…
Read more → The post The hidden business costs of working remotely first appeared on IT Security News.
https://www.itsecuritynews.info/the-hidden-business-costs-of-working-remotely/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-hidden-business-costs-of-working-remotely/?utm_source=dlvr.it&utm_medium=blogger
February 2021 Web Server Survey
Read the original article: February 2021 Web Server Survey In the February 2021 survey we received responses from 1,204,252,411 sites across 263,042,054 unique domains and 10,766,606 web-facing computers. This reflects a gain of 6,270,052 sites, 92,829 domains, and 116,789 computers.…
Read more → The post February 2021 Web Server Survey first appeared on IT Security News.
https://www.itsecuritynews.info/february-2021-web-server-survey/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/february-2021-web-server-survey/?utm_source=dlvr.it&utm_medium=blogger
Cybercrime groups are selling their hacking skills. Some countries are buying
Read the original article: Cybercrime groups are selling their hacking skills. Some countries are buying Nation-state hacking groups don’t need to do the work themselves anymore: they can hire criminal gangs to breach targets for them – with the added…
Read more → The post Cybercrime groups are selling their hacking skills. Some countries are buying first appeared on IT Security News.
https://www.itsecuritynews.info/cybercrime-groups-are-selling-their-hacking-skills-some-countries-are-buying/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cybercrime-groups-are-selling-their-hacking-skills-some-countries-are-buying/?utm_source=dlvr.it&utm_medium=blogger
Thursday, February 25, 2021
Integrated Risk Management for Your Business
Read the original article: Integrated Risk Management for Your Business For today’s security professionals, managing risk is arguably the most critical and challenging part of their job–and quite … Read More The post Integrated Risk Management for Your Business appeared…
Read more → The post Integrated Risk Management for Your Business first appeared on IT Security News.
https://www.itsecuritynews.info/integrated-risk-management-for-your-business/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/integrated-risk-management-for-your-business/?utm_source=dlvr.it&utm_medium=blogger
The Top Free Tools for Sysadmins in 2021
It's no secret that sysadmins have plenty on their plates. Managing, troubleshooting, and updating software or hardware is a tedious task. Additionally, admins must grapple with complex webs of permissions and security. This can quickly become overwhelming without the right tools. If you're a sysadmin seeking to simplify your workflows, you're in luck. We've gathered some excellent software
https://thehackernews.com/2021/02/the-top-free-tools-for-sysadmins-in-2021.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/the-top-free-tools-for-sysadmins-in-2021.html?utm_source=dlvr.it&utm_medium=blogger
Russian Hackers Targeted Ukraine Authorities With Supply-Chain Malware Attack
Ukraine is formally pointing fingers at Russian hackers for hacking into one of its government systems and attempting to plant and distribute malicious documents that would install malware on target systems of public authorities. "The purpose of the attack was the mass contamination of information resources of public authorities, as this system is used for the circulation of documents in most
https://thehackernews.com/2021/02/russian-hackers-targeted-ukraine.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/russian-hackers-targeted-ukraine.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, February 24, 2021
Experts Warns of Notable Increase in QuickBooks Data Files Theft Attacks
New research has uncovered a significant increase in QuickBooks file data theft using social engineering tricks to deliver malware and exploit the accounting software. "A majority of the time, the attack involves basic malware that is often signed, making it hard to detect using antivirus or other threat detection software," researchers from ThreatLocker said in an analysis shared today with The
https://thehackernews.com/2021/02/experts-warns-of-notable-increase-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/experts-warns-of-notable-increase-in.html?utm_source=dlvr.it&utm_medium=blogger
Everything You Need to Know About Evolving Threat of Ransomware
The cybersecurity world is constantly evolving to new forms of threats and vulnerabilities. But ransomware proves to be a different animal—most destructive, persistent, notoriously challenging to prevent, and is showing no signs of slowing down. Falling victim to a ransomware attack can cause significant data loss, data breach, operational downtime, costly recovery, legal consequences, and
https://thehackernews.com/2021/02/everything-you-need-to-know-about.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/everything-you-need-to-know-about.html?utm_source=dlvr.it&utm_medium=blogger
Critical RCE Flaws Affect VMware ESXi and vSphere Client — Patch Now
VMware has addressed multiple critical remote code execution (RCE) vulnerabilities in VMware ESXi and vSphere Client virtual infrastructure management platform that may allow attackers to execute arbitrary commands and take control of affected systems. "A malicious actor with network access to port 443 may exploit this issue to execute commands with unrestricted privileges on the underlying
https://thehackernews.com/2021/02/critical-rce-flaw-affects-vmware.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/critical-rce-flaw-affects-vmware.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, February 23, 2021
Experts Find a Way to Learn What You're Typing During Video Calls
A new attack framework aims to infer keystrokes typed by a target user at the opposite end of a video conference call by simply leveraging the video feed to correlate observable body movements to the text being typed. The research was undertaken by Mohd Sabra, and Murtuza Jadliwala from the University of Texas at San Antonio and Anindya Maiti from the University of Oklahoma, who say the attack
https://thehackernews.com/2021/02/experts-find-way-to-learn-what-youre.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/experts-find-way-to-learn-what-youre.html?utm_source=dlvr.it&utm_medium=blogger
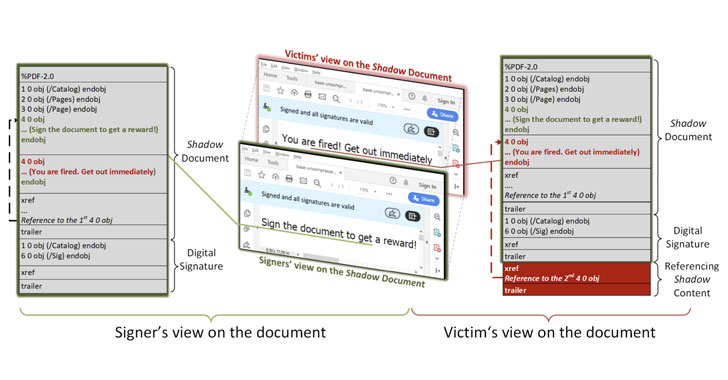
Shadow Attacks Let Attackers Replace Content in Digitally Signed PDFs
Researchers have demonstrated a novel class of attacks that could allow a bad actor to potentially circumvent existing countermeasures and break the integrity protection of digitally signed PDF documents. Called "Shadow attacks" by academics from Ruhr-University Bochum, the technique uses the "enormous flexibility provided by the PDF specification so that shadow documents remain
https://thehackernews.com/2021/02/shadow-attacks-let-attackers-replace.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/shadow-attacks-let-attackers-replace.html?utm_source=dlvr.it&utm_medium=blogger
Hackers Exploit Accellion Zero-Days in Recent Data Theft and Extortion Attacks
Cybersecurity researchers on Monday tied a string of attacks targeting Accellion File Transfer Appliance (FTA) servers over the past two months to data theft and extortion campaign orchestrated by a cybercrime group called UNC2546. The attacks, which began in mid-December 2020, involved exploiting multiple zero-day vulnerabilities in the legacy FTA software to install a new web shell named
https://thehackernews.com/2021/02/hackers-exploit-accellion-zero-days-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/hackers-exploit-accellion-zero-days-in.html?utm_source=dlvr.it&utm_medium=blogger
Monday, February 22, 2021
Attacks Targeting Accellion Product Linked to FIN11 Cybercrime Group
Read the original article: Attacks Targeting Accellion Product Linked to FIN11 Cybercrime Group The hacking group behind the recent cyber-attack targeting Accellion’s FTA file transfer service appears to be linked to a threat actor known as FIN11, security researchers with…
Read more → The post Attacks Targeting Accellion Product Linked to FIN11 Cybercrime Group first appeared on IT Security News.
https://www.itsecuritynews.info/attacks-targeting-accellion-product-linked-to-fin11-cybercrime-group/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/attacks-targeting-accellion-product-linked-to-fin11-cybercrime-group/?utm_source=dlvr.it&utm_medium=blogger
Chinese Hackers Had Access to a U.S. Hacking Tool Years Before It Was Leaked Online
On August 13, 2016, a hacking unit calling itself "The Shadow Brokers" announced that it had stolen malware tools and exploits used by the Equation Group, a sophisticated threat actor believed to be affiliated to the Tailored Access Operations (TAO) unit of the U.S. National Security Agency (NSA). Although the group has since signed off following the unprecedented disclosures, new "conclusive"
https://thehackernews.com/2021/02/chinese-hackers-had-access-to-us.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/chinese-hackers-had-access-to-us.html?utm_source=dlvr.it&utm_medium=blogger
New 'Silver Sparrow' Malware Infected Nearly 30,000 Apple Macs
Days after the first malware targeting Apple M1 chips was discovered in the wild, researchers have disclosed yet another previously undetected piece of malicious software that was found in about 30,000 Macs running Intel x86_64 and the iPhone maker's M1 processors. However, the ultimate goal of the operation remains something of a conundrum, what with the lack of a next-stage or final payload
https://thehackernews.com/2021/02/new-silver-sparrow-malware-infected.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/new-silver-sparrow-malware-infected.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 21, 2021
Criminals leveraging shift to remote work to develop targeted attacks
Read the original article: Criminals leveraging shift to remote work to develop targeted attacks Malwarebytes announced the findings of its report which explores how the global pandemic forced many employees to quickly become a remote workforce and confined consumers to…
Read more → The post Criminals leveraging shift to remote work to develop targeted attacks first appeared on IT Security News.
https://www.itsecuritynews.info/criminals-leveraging-shift-to-remote-work-to-develop-targeted-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/criminals-leveraging-shift-to-remote-work-to-develop-targeted-attacks/?utm_source=dlvr.it&utm_medium=blogger
Penetration testing
Penetration testing is the technical analysis of the safety level of IT systems and networks. We offer a complete investigation of the hardware / software systems for security vulnerabilities. If you have at least one online service, then you must…
Read more → The post Penetration testing first appeared on IT Security News.
https://www.itsecuritynews.info/penetration-testing-15/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/penetration-testing-15/?utm_source=dlvr.it&utm_medium=blogger
Multilingual Cybersecurity Awareness Training adapted for your needs
Technology alone cannot protect you from everything. Because the online world is so interconnected, everyone is a target, no matter if you are an individual, small business or huge enterprise. Cybersecurity awareness training teaches your employees – to spot fake…
Read more → The post Multilingual Cybersecurity Awareness Training adapted for your needs first appeared on IT Security News.
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-14/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-14/?utm_source=dlvr.it&utm_medium=blogger
Saturday, February 20, 2021
Privacy Bug in Brave Browser Exposes Dark-Web Browsing History of Its Users
Brave has fixed a privacy issue in its browser that sent queries for .onion domains to public internet DNS resolvers rather than routing them through Tor nodes, thus exposing users' visits to dark web websites. The bug was addressed in a hotfix release (V1.20.108) made available yesterday. Brave ships with a built-in feature called "Private Window with Tor" that integrates the Tor anonymity
https://thehackernews.com/2021/02/privacy-bug-in-brave-browser-exposes.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/privacy-bug-in-brave-browser-exposes.html?utm_source=dlvr.it&utm_medium=blogger
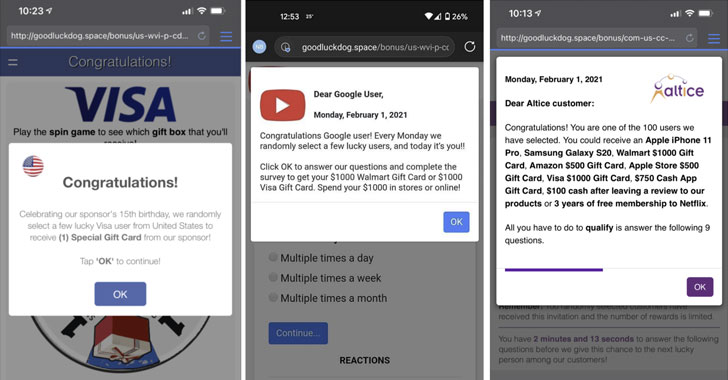
ScamClub Malvertiser Exploited WebKit Zero-Day To Redirect Users To Shady Sites
Read the original article: ScamClub Malvertiser Exploited WebKit Zero-Day To Redirect Users To Shady Sites Another malicious ad campaign is in the wild targeting iOS users this time. Reportedly, the… ScamClub Malvertiser Exploited WebKit Zero-Day To Redirect Users To Shady…
Read more → The post ScamClub Malvertiser Exploited WebKit Zero-Day To Redirect Users To Shady Sites first appeared on IT Security News.
https://www.itsecuritynews.info/scamclub-malvertiser-exploited-webkit-zero-day-to-redirect-users-to-shady-sites/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/scamclub-malvertiser-exploited-webkit-zero-day-to-redirect-users-to-shady-sites/?utm_source=dlvr.it&utm_medium=blogger
‘Build’ or ‘Buy’ your own antivirus product
We can help you decide if you should build your own antivirus product or if you should license an OEM or whitelabel product Both options come with advantages and disadvantages, it depends on the needs of the customer, on the…
Read more → The post ‘Build’ or ‘Buy’ your own antivirus product first appeared on IT Security News.
https://www.itsecuritynews.info/build-or-buy-your-own-antivirus-product-23/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/build-or-buy-your-own-antivirus-product-23/?utm_source=dlvr.it&utm_medium=blogger
Friday, February 19, 2021
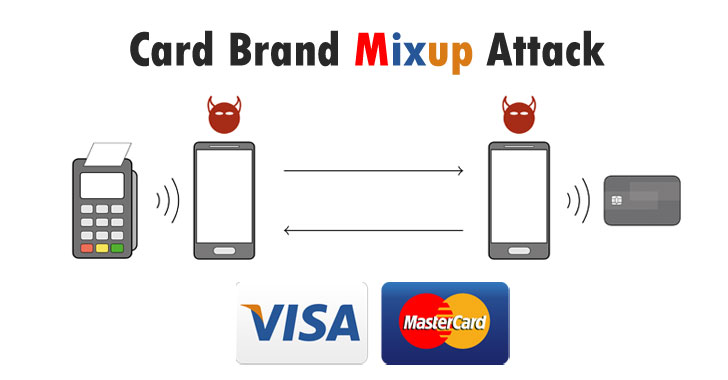
New Hack Lets Attackers Bypass MasterCard PIN by Using Them As Visa Card
Cybersecurity researchers have disclosed a novel attack that could allow criminals to trick a point of sale terminal into transacting with a victim's Mastercard contactless card while believing it to be a Visa card. The research, published by a group of academics from the ETH Zurich, builds on a study detailed last September that delved into a PIN bypass attack, permitting bad actors to leverage
https://thehackernews.com/2021/02/new-hack-lets-attackers-bypass.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/new-hack-lets-attackers-bypass.html?utm_source=dlvr.it&utm_medium=blogger
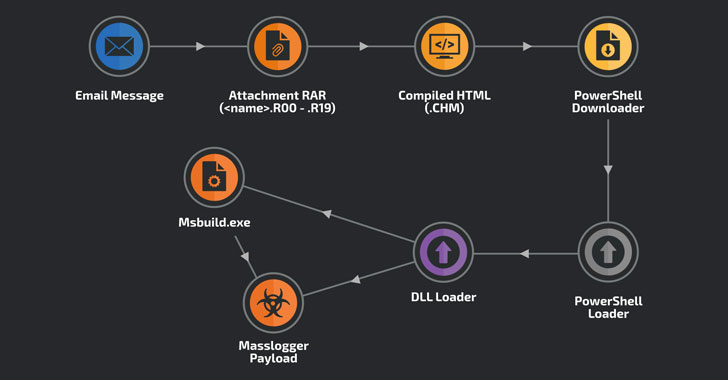
Masslogger Trojan Upgraded to Steal All Your Outlook, Chrome Credentials
A credential stealer infamous for targeting Windows systems has resurfaced in a new phishing campaign that aims to steal credentials from Microsoft Outlook, Google Chrome, and instant messenger apps. Primarily directed against users in Turkey, Latvia, and Italy starting mid-January, the attacks involve the use of MassLogger — a .NET-based malware with capabilities to hinder static analysis —
https://thehackernews.com/2021/02/masslogger-trojan-upgraded-to-steal-all.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/masslogger-trojan-upgraded-to-steal-all.html?utm_source=dlvr.it&utm_medium=blogger
SolarWinds Hackers Stole Some Source Code for Microsoft Azure, Exchange, Intune
Microsoft on Thursday said it concluded its probe into the SolarWinds hack, finding that the attackers stole some source code but confirmed there's no evidence that they abused its internal systems to target other companies or gained access to production services or customer data. The disclosure builds upon an earlier update on December 31, 2020, that uncovered a compromise of its own network to
https://thehackernews.com/2021/02/solarwinds-hackers-stole-some-source.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/solarwinds-hackers-stole-some-source.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, February 18, 2021
How To Know if a Website Is Safe To Use
Some aspects of the web are a mystery to many users around the world. Even though we are using our computers daily, we still do not know everything about them. After all, we do not have to understand how all the tools that we use work. Moreover, it seems that all that matters to us […]
The post How To Know if a Website Is Safe To Use appeared first on Cyber Security News.
https://cybersecuritynews.com/how-to-know-if-a-website-is-safe-to-use/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/how-to-know-if-a-website-is-safe-to-use/?utm_source=dlvr.it&utm_medium=blogger
First Malware Designed for Apple M1 Chip Discovered in the Wild
One of the first malware samples tailored to run natively on Apple's M1 chips has been discovered, suggesting a new development that indicates that bad actors have begun adapting malicious software to target the company's latest generation of Macs powered by its own processors. While the transition to Apple silicon has necessitated developers to build new versions of their apps to ensure better
https://thehackernews.com/2021/02/first-malware-designed-for-apple-m1.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/first-malware-designed-for-apple-m1.html?utm_source=dlvr.it&utm_medium=blogger
U.S. Charges 3 North Korean Hackers Over $1.3 Billion Cryptocurrency Heist
The U.S. Department of Justice (DoJ) on Wednesday indicted three suspected North Korean hackers for allegedly conspiring to steal and extort over $1.3 billion in cash and cryptocurrencies from financial institutions and businesses. The three defendants — Jon Chang Hyok, 31; Kim Il, 27; and Park Jin Hyok, 36 — are said to be members of the Reconnaissance General Bureau, a military intelligence
https://thehackernews.com/2021/02/us-charges-3-north-korean-hackers-over.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/us-charges-3-north-korean-hackers-over.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, February 17, 2021
What’s Going on With Apple’s iOS Security Flaws?
Apple is usually known for how much it values user privacy, and the lengths it goes to secure their data. Which is why pretty much everyone was surprised to hear that iOS actually had some serious vulnerabilities which hackers could have easily exploited. If this is the first time you’re hearing about this, we’ll tell […]
The post What’s Going on With Apple’s iOS Security Flaws? appeared first on Cyber Security News.
https://cybersecuritynews.com/whats-going-on-with-apples-ios-security-flaws/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/whats-going-on-with-apples-ios-security-flaws/?utm_source=dlvr.it&utm_medium=blogger
Researchers Unmask Hackers Behind APOMacroSploit Malware Builder
Cybersecurity researchers have disclosed a new kind of Office malware distributed as part of a malicious email campaign that targeted more than 80 customers worldwide in an attempt to control victim machines and steal information remotely. The tool — dubbed "APOMacroSploit" — is a macro exploit generator that allows the user to create an Excel document capable of bypassing antivirus software,
https://thehackernews.com/2021/02/researchers-unmask-hackers-behind.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/researchers-unmask-hackers-behind.html?utm_source=dlvr.it&utm_medium=blogger
Malvertisers Exploited WebKit 0-Day to Redirect Browser Users to Scam Sites
A malvertising group known as "ScamClub" exploited a zero-day vulnerability in WebKit-based browsers to inject malicious payloads that redirected users to fraudulent websites gift card scams. The attacks, first spotted by ad security firm Confiant in late June 2020, leveraged a bug (CVE-2021–1801) that allowed malicious parties to bypass the iframe sandboxing policy in the browser engine that
https://thehackernews.com/2021/02/malvertisers-exploited-webkit-0-day-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/malvertisers-exploited-webkit-0-day-to.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, February 16, 2021
Unpatched ShareIT Android App Flaw Could Let Hackers Inject Malware
Multiple unpatched vulnerabilities have been discovered in SHAREit, a popular app with over one billion downloads, that could be abused to leak a user's sensitive data, execute arbitrary code, and possibly lead to remote code execution. The findings come from cybersecurity firm Trend Micro's analysis of the Android version of the app, which allows users to share or transfer files between devices
https://thehackernews.com/2021/02/unpatched-shareit-android-app-flaw.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/unpatched-shareit-android-app-flaw.html?utm_source=dlvr.it&utm_medium=blogger
Hacker Group APT Confucius Employees two New Spyware to Target Military and Nuclear Entities
The cybersecurity experts of the Threat Intelligence firm have recently discovered two new spyware named Hornbill and SunBird. These two variants of Android spyware are related to the pro-India advanced persistent threat (APT) group. The experts affirmed that these two malware strains had been linked to Confucius; however, it was first detected in 2013 as […]
The post Hacker Group APT Confucius Employees two New Spyware to Target Military and Nuclear Entities appeared first on Cyber Security News.
https://cybersecuritynews.com/malware-sunbird-and-hornbill/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/malware-sunbird-and-hornbill/?utm_source=dlvr.it&utm_medium=blogger
Managed Service Provider? Watch This Video to Learn about Autonomous XDR
As managed security service providers, you're always on the lookout for new platforms. One that can generate further business, enables you to scale easily without investing in more human resources and provides that value immediately. In the meanwhile, your clients are constantly demanding more security for a lesser cost. Cynet recently published an 8-min video detailing their platform, the Cynet
https://thehackernews.com/2021/02/managed-service-provider-watch-this.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/managed-service-provider-watch-this.html?utm_source=dlvr.it&utm_medium=blogger
Monday, February 15, 2021
A Sticker Sent On Telegram Could Have Exposed Your Secret Chats
Cybersecurity researchers on Monday disclosed details of a now-patched flaw in the Telegram messaging app that could have exposed users' secret messages, photos, and videos to remote malicious actors. The issues were discovered by Italy-based Shielder in iOS, Android, and macOS versions of the app. Following responsible disclosure, Telegram addressed them in a series of patches on September 30
https://thehackernews.com/2021/02/a-sticker-sent-on-telegram-could-have.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/a-sticker-sent-on-telegram-could-have.html?utm_source=dlvr.it&utm_medium=blogger
Let’s Encrypt completes huge upgrade, can now rip and replace 200 million security certs in ‘worst case scenario’
Read the original article: Let’s Encrypt completes huge upgrade, can now rip and replace 200 million security certs in ‘worst case scenario’ Plus: SentinelOne picks up Scalyr, fatal flaws in TCP, and a view on Supermicro In brief Internet Security…
Read more → The post Let’s Encrypt completes huge upgrade, can now rip and replace 200 million security certs in ‘worst case scenario’ first appeared on IT Security News.
https://www.itsecuritynews.info/lets-encrypt-completes-huge-upgrade-can-now-rip-and-replace-200-million-security-certs-in-worst-case-scenario/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/lets-encrypt-completes-huge-upgrade-can-now-rip-and-replace-200-million-security-certs-in-worst-case-scenario/?utm_source=dlvr.it&utm_medium=blogger
Apple will proxy Safe Browsing requests to hide iOS users' IP from Google
Apple's upcoming iOS 14.5 update will come with a new feature that will redirect all fraudulent website checks through its own proxy servers as a workaround to preserve user privacy and prevent leaking IP addresses to Google. A built-in security-focused feature in the Safari browser, "Fraudulent Website Warning," alerts users about dangerous websites that have been reported as deceptive,
https://thehackernews.com/2021/02/apple-will-proxy-safe-browsing-requests.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/apple-will-proxy-safe-browsing-requests.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 14, 2021
Rampant password reuse puts companies and customers at risk
Read the original article: Rampant password reuse puts companies and customers at risk 25.9 million business account credentials and over 543 million breach assets tied to employees in the Fortune 1000 are readily available on the criminal underground, SpyCloud reveals.…
Read more → The post Rampant password reuse puts companies and customers at risk first appeared on IT Security News.
https://www.itsecuritynews.info/rampant-password-reuse-puts-companies-and-customers-at-risk/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/rampant-password-reuse-puts-companies-and-customers-at-risk/?utm_source=dlvr.it&utm_medium=blogger
Multilingual Cybersecurity Awareness Training adapted for your needs
Technology alone cannot protect you from everything. Because the online world is so interconnected, everyone is a target, no matter if you are an individual, small business or huge enterprise. Cybersecurity awareness training teaches your employees – to spot fake…
Read more → The post Multilingual Cybersecurity Awareness Training adapted for your needs first appeared on IT Security News.
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-13/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-13/?utm_source=dlvr.it&utm_medium=blogger
Apple’s Heart Month Activity Challenge Requires 60 Minutes of Exercise on Valentine’s Day
Read the original article: Apple’s Heart Month Activity Challenge Requires 60 Minutes of Exercise on Valentine’s Day Today only, Apple Watch owners can complete a new Apple Watch activity challenge in celebration of Heart Month, which is aimed at promoting…
Read more → The post Apple’s Heart Month Activity Challenge Requires 60 Minutes of Exercise on Valentine’s Day first appeared on IT Security News.
https://www.itsecuritynews.info/apples-heart-month-activity-challenge-requires-60-minutes-of-exercise-on-valentines-day/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apples-heart-month-activity-challenge-requires-60-minutes-of-exercise-on-valentines-day/?utm_source=dlvr.it&utm_medium=blogger
Saturday, February 13, 2021
Computer Malware Fraudster Gets 2 Years in Prison
Read the original article: Computer Malware Fraudster Gets 2 Years in Prison A man who played a key role in a computer malware scam has been sentenced to two years in prison, federal prosecutors say. read more Become a…
Read more → The post Computer Malware Fraudster Gets 2 Years in Prison first appeared on IT Security News.
https://www.itsecuritynews.info/computer-malware-fraudster-gets-2-years-in-prison/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/computer-malware-fraudster-gets-2-years-in-prison/?utm_source=dlvr.it&utm_medium=blogger
Weekly Update 230
Read the original article: Weekly Update 230 Presently sponsored by: Credential stuffing is currently the biggest threat to organisations, find out how you can protect your network right now with safepass.me This week has seen a lot of my time…
Read more → The post Weekly Update 230 first appeared on IT Security News.
https://www.itsecuritynews.info/weekly-update-230/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/weekly-update-230/?utm_source=dlvr.it&utm_medium=blogger
‘Build’ or ‘Buy’ your own antivirus product
We can help you decide if you should build your own antivirus product or if you should license an OEM or whitelabel product Both options come with advantages and disadvantages, it depends on the needs of the customer, on the…
Read more → The post ‘Build’ or ‘Buy’ your own antivirus product first appeared on IT Security News.
https://www.itsecuritynews.info/build-or-buy-your-own-antivirus-product-22/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/build-or-buy-your-own-antivirus-product-22/?utm_source=dlvr.it&utm_medium=blogger
Friday, February 12, 2021
Yandex Employee Caught Selling Access to Users' Email Inboxes
Russian Dutch-domiciled search engine, ride-hailing and email service provider Yandex on Friday disclosed a data breach that compromised 4,887 email accounts of its users. The company blamed the incident on an unnamed employee who had been providing unauthorized access to the users' mailboxes for personal gain. "The employee was one of three system administrators with the necessary access
https://thehackernews.com/2021/02/yandex-employee-caught-selling-access.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/yandex-employee-caught-selling-access.html?utm_source=dlvr.it&utm_medium=blogger
Sensor Tower: iOS Users Spent $10.3 billion on Top 100 Subscription Apps in 2020, Up 32% Year-on-Year
Read the original article: Sensor Tower: iOS Users Spent $10.3 billion on Top 100 Subscription Apps in 2020, Up 32% Year-on-Year Consumer spending on the top 100 non-game subscription-based apps across mobile platforms grew 34% year-on-year from $9.7 billion in…
Read more → The post Sensor Tower: iOS Users Spent $10.3 billion on Top 100 Subscription Apps in 2020, Up 32% Year-on-Year first appeared on IT Security News.
https://www.itsecuritynews.info/sensor-tower-ios-users-spent-10-3-billion-on-top-100-subscription-apps-in-2020-up-32-year-on-year/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/sensor-tower-ios-users-spent-10-3-billion-on-top-100-subscription-apps-in-2020-up-32-year-on-year/?utm_source=dlvr.it&utm_medium=blogger
Secret Chat in Telegram Left Self-Destructing Media Files On Devices
Popular messaging app Telegram fixed a privacy-defeating bug in its macOS app that made it possible to access self-destructing audio and video messages long after they disappeared from secret chats. The vulnerability was discovered by security researcher Dhiraj Mishra in version 7.3 of the app, who disclosed his findings to Telegram on December 26, 2020. The issue has since been resolved in
https://thehackernews.com/2021/02/secret-chat-in-telegram-left-self.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/secret-chat-in-telegram-left-self.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, February 11, 2021
Researchers Uncover Android Spying Campaign Targeting Pakistan Officials
Two new Android surveillanceware families have been found to target military, nuclear, and election entities in Pakistan and Kashmir as part of a pro-India, state-sponsored hacking campaign. Dubbed Hornbill and Sunbird, the malware impersonates legitimate or seemingly innocuous services to cover its tracks, only to stealthily collect SMS, encrypted messaging app content, and geolocation, among
https://thehackernews.com/2021/02/researchers-uncover-android-spying.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/researchers-uncover-android-spying.html?utm_source=dlvr.it&utm_medium=blogger
Iranian Hackers Utilize ScreenConnect to Spy On UAE, Kuwait Government Agencies
UAE and Kuwait government agencies are targets of a new cyberespionage campaign potentially carried out by Iranian threat actors, according to new research. Attributing the operation to be the work of Static Kitten (aka MERCURY or MuddyWater), Anomali said the "objective of this activity is to install a remote management tool called ScreenConnect (acquired by ConnectWise 2015) with unique launch
https://thehackernews.com/2021/02/iranian-hackers-utilize-screenconnect.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/iranian-hackers-utilize-screenconnect.html?utm_source=dlvr.it&utm_medium=blogger
Researchers Hacked into Microsoft, Apple, more in Novel Supply Chain Attack
Ethical hacker, Alex Birsan, has demonstrated that it is possible to breach the systems of tech giants by utilizing a novel supply chain attack by exploiting public, open-source developer tools. These tech companies include giants such as Microsoft, Apple, PayPal, Shopify, Netflix, Tesla and Uber. The attack injects malicious code into common tools for installing […]
The post Researchers Hacked into Microsoft, Apple, more in Novel Supply Chain Attack appeared first on Cyber Security News.
https://cybersecuritynews.com/novel-supply-chain-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/novel-supply-chain-attack/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, February 10, 2021
Sentropy Protect helps tackle online hate and harassment from abusive Twitter accounts
Read the original article: Sentropy Protect helps tackle online hate and harassment from abusive Twitter accounts Sentropy announced its first consumer product – and third product overall – Sentropy Protect, which enables Twitter users to proactively identify and protect themselves…
Read more → The post Sentropy Protect helps tackle online hate and harassment from abusive Twitter accounts first appeared on IT Security News.
https://www.itsecuritynews.info/sentropy-protect-helps-tackle-online-hate-and-harassment-from-abusive-twitter-accounts/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/sentropy-protect-helps-tackle-online-hate-and-harassment-from-abusive-twitter-accounts/?utm_source=dlvr.it&utm_medium=blogger
YouTube Website’s Picture-in-Picture Works Again in iOS 14.5 Beta
Read the original article: YouTube Website’s Picture-in-Picture Works Again in iOS 14.5 Beta YouTube’s website appears to support picture-in-picture (PiP) again in the latest iOS 14.5 beta for iPhone, although how long it will continue to work for is anybody’s…
Read more → The post YouTube Website’s Picture-in-Picture Works Again in iOS 14.5 Beta first appeared on IT Security News.
https://www.itsecuritynews.info/youtube-websites-picture-in-picture-works-again-in-ios-14-5-beta/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/youtube-websites-picture-in-picture-works-again-in-ios-14-5-beta/?utm_source=dlvr.it&utm_medium=blogger
mHealth App APIs Vulnerable To Attacks Exposing PII & PHI – Experts Insight
Read the original article: mHealth App APIs Vulnerable To Attacks Exposing PII & PHI – Experts Insight New findings in the research report “All That We Let In” (press release and study link) show that fully 100% of the 30 popular mHealth apps…
Read more → The post mHealth App APIs Vulnerable To Attacks Exposing PII & PHI – Experts Insight first appeared on IT Security News.
https://www.itsecuritynews.info/mhealth-app-apis-vulnerable-to-attacks-exposing-pii-phi-experts-insight/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/mhealth-app-apis-vulnerable-to-attacks-exposing-pii-phi-experts-insight/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, February 9, 2021
Enormous Growth in RDP Attacks as Hackers Targeting Employees Working From Home
Nowadays, there is a vast increase in cybercriminal attacks, and the RDP attacks are at the top of these attacks list in 2020. As cybercriminals are continuously implementing new attack methods by exploiting remote login credentials. The attack rate has increased over the last year, as many employees started to work from home due to […]
The post Enormous Growth in RDP Attacks as Hackers Targeting Employees Working From Home appeared first on Cyber Security News.
https://cybersecuritynews.com/rdp-attacks-as-hackers-targeting-employees-working-from-home/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/rdp-attacks-as-hackers-targeting-employees-working-from-home/?utm_source=dlvr.it&utm_medium=blogger
Ukrainian Police Arrest Author of World's Largest Phishing Service U-Admin
Law enforcement officials in Ukraine, in coordination with authorities from the U.S. and Australia, last week shut down one of the world's largest phishing services that were used to attack financial institutions in 11 countries, causing tens of millions of dollars in losses. The Ukrainian attorney general's office said it worked with the National Police and its Main Investigation Department to
https://thehackernews.com/2021/02/ukrainian-police-arrest-author-of.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/ukrainian-police-arrest-author-of.html?utm_source=dlvr.it&utm_medium=blogger
Hacker Tried Poisoning Water Supply After Breaking Into Florida's Treatment System
Hackers successfully infiltrated the computer system controlling a water treatment facility in the U.S. state of Florida and remotely changed a setting that drastically altered the levels of sodium hydroxide (NaOH) in the water. During a press conference held yesterday, Pinellas County Sheriff Bob Gualtieri said an operator managed to catch the manipulation in real-time and restored the
https://thehackernews.com/2021/02/hacker-tried-poisoning-water-supply.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/hacker-tried-poisoning-water-supply.html?utm_source=dlvr.it&utm_medium=blogger
Monday, February 8, 2021
New Botnet Reuse the Mirai Framework to Perform DDoS Attack on Android Devices
Recently, the Chinese security firm Qihoo 360’s networking security division Netlab has discovered a nascent malware campaign. This campaign has been spotted co-opting the Android devices into a botnet along with the principal objective of carrying out distributed denial-of-service (DDoS) attacks. The botnet malware that has been detected by the researchers at Qihoo 360’s Netlab […]
The post New Botnet Reuse the Mirai Framework to Perform DDoS Attack on Android Devices appeared first on Cyber Security News.
https://cybersecuritynews.com/new-botnet-reuse-the-mirai-framework/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/new-botnet-reuse-the-mirai-framework/?utm_source=dlvr.it&utm_medium=blogger
Detailed: Here's How Iran Spies on Dissidents with the Help of Hackers
Twin cyber operations conducted by state-sponsored Iranian threat actors demonstrate their continued focus on compiling detailed dossiers on Iranian citizens that could threaten the stability of the Islamic Republic, including dissidents, opposition forces, and ISIS supporters, and Kurdish natives. Tracing the extensive espionage operations to two advanced Iranian cyber-groups Domestic Kitten (
https://thehackernews.com/2021/02/researchers-reveal-how-iran-spies-on.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/researchers-reveal-how-iran-spies-on.html?utm_source=dlvr.it&utm_medium=blogger
Top 5 Bug Bounty Programs to Watch in 2021
While Gartner does not have a dedicated Magic Quadrant for Bug Bounties or Crowd Security Testing yet, Gartner Peer Insights already lists 24 vendors in the "Application Crowdtesting Services" category. We have compiled the top 5 most promising bug bounty platforms for those of you who are looking to enhance your existing software testing arsenal with knowledge and expertise from international
https://thehackernews.com/2021/02/top-5-bug-bounty-programs-to-watch-in.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/top-5-bug-bounty-programs-to-watch-in.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, February 7, 2021
Cisco AppDynamics strengthens security posture while achieving peak app performance
Read the original article: Cisco AppDynamics strengthens security posture while achieving peak app performance AppDynamics announced Cisco Secure Application, a solution to drastically simplify vulnerability management, defend against attacks and protect applications – from the inside-out. Co-innovated with the Cisco…
Read more → The post Cisco AppDynamics strengthens security posture while achieving peak app performance first appeared on IT Security News.
https://www.itsecuritynews.info/cisco-appdynamics-strengthens-security-posture-while-achieving-peak-app-performance/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cisco-appdynamics-strengthens-security-posture-while-achieving-peak-app-performance/?utm_source=dlvr.it&utm_medium=blogger
Penetration testing
Penetration testing is the technical analysis of the safety level of IT systems and networks. We offer a complete investigation of the hardware / software systems for security vulnerabilities. If you have at least one online service, then you must…
Read more → The post Penetration testing first appeared on IT Security News.
https://www.itsecuritynews.info/penetration-testing-13/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/penetration-testing-13/?utm_source=dlvr.it&utm_medium=blogger
Multilingual Cybersecurity Awareness Training adapted for your needs
Technology alone cannot protect you from everything. Because the online world is so interconnected, everyone is a target, no matter if you are an individual, small business or huge enterprise. Cybersecurity awareness training teaches your employees – to spot fake…
Read more → The post Multilingual Cybersecurity Awareness Training adapted for your needs first appeared on IT Security News.
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-12/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-12/?utm_source=dlvr.it&utm_medium=blogger
Saturday, February 6, 2021
Hackers Abusing Google Chrome Extension to Exfiltrating Data & Using That Channel for C&C Communication
Recently, an IT cybersecurity researcher, Bojan Zdrnja, has published its research exposing that the threat actors are using Google Chrome’s Sync feature for Command and Control communication by exfiltrating data. However, Zdrnja declares that the threat actors used compelling features to exploit the Chrome browser. As Google Chrome’s Sync feature could be exploited by several […]
The post Hackers Abusing Google Chrome Extension to Exfiltrating Data & Using That Channel for C&C Communication appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-abusing-google-chrome-extension-to-exfiltrating-data/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-abusing-google-chrome-extension-to-exfiltrating-data/?utm_source=dlvr.it&utm_medium=blogger
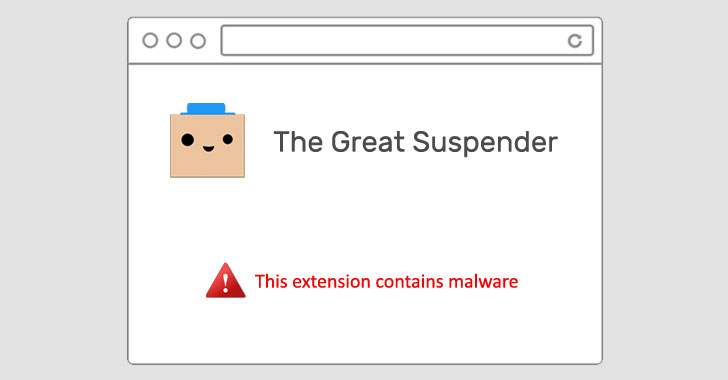
WARNING — Hugely Popular 'The Great Suspender' Chrome Extension Contains Malware
Google on Thursday removed The Great Suspender, a popular Chrome extension used by millions of users, from its Chrome Web Store for containing malware. It also took the unusual step of deactivating it from users' computers. "This extension contains malware," read a terse notification from Google, but it has since emerged that the add-on stealthily added features that could be exploited to
https://thehackernews.com/2021/02/warning-hugely-popular-great-suspender.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/warning-hugely-popular-great-suspender.html?utm_source=dlvr.it&utm_medium=blogger
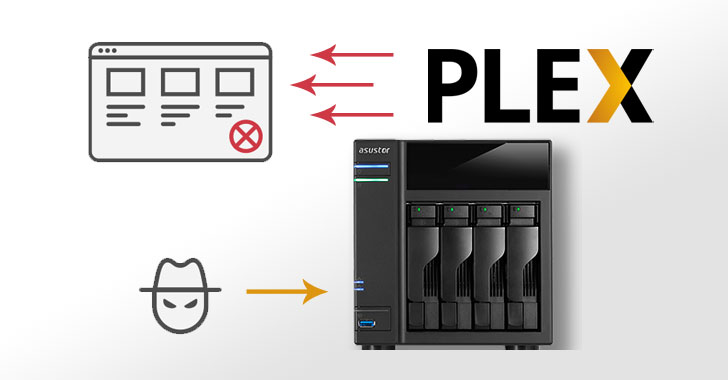
Cybercriminals Now Using Plex Media Servers to Amplify DDoS Attacks
A new distributed denial-of-service attack (DDoS) vector has ensnared Plex Media Server systems to amplify malicious traffic against targets to take them offline. "Plex's startup processes unintentionally expose a Plex UPnP-enabled service registration responder to the general Internet, where it can be abused to generate reflection/amplification DDoS attacks," Netscout researchers said in a
https://thehackernews.com/2021/02/cybercriminals-now-using-plex-media.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/cybercriminals-now-using-plex-media.html?utm_source=dlvr.it&utm_medium=blogger
Friday, February 5, 2021
What is SYN Attack? How the Attack works and How to Prevent the SYN Attack
TCP SYN Flood attacks are the most popular ones amongst the DDOS attacks. Here we are going to discuss in detail, the basis of the TCP SYN attack and to stop before it reaches those servers. It’s been more than two decades when the first DDOS attack was attempted at the University of Minnesota which […]
The post What is SYN Attack? How the Attack works and How to Prevent the SYN Attack appeared first on Cyber Security News.
https://cybersecuritynews.com/syn-attack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/syn-attack/?utm_source=dlvr.it&utm_medium=blogger
Critical Flaws Reported in Cisco VPN Routers for Businesses—Patch ASAP
Cisco has rolled out fixes for multiple critical vulnerabilities in the web-based management interface of Small Business routers that could potentially allow an unauthenticated, remote attacker to execute arbitrary code as the root user on an affected device. The flaws — tracked from CVE-2021-1289 through CVE-2021-1295 (CVSS score 9.8) — impact RV160, RV160W, RV260, RV260P, and RV260W VPN
https://thehackernews.com/2021/02/critical-flaws-reported-in-cisco-vpn.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/critical-flaws-reported-in-cisco-vpn.html?utm_source=dlvr.it&utm_medium=blogger
New Chrome Browser 0-day Under Active Attack—Update Immediately!
Google has patched a zero-day vulnerability in Chrome web browser for desktop that it says is being actively exploited in the wild. The company released 88.0.4324.150 for Windows, Mac, and Linux, with a fix for a heap buffer overflow flaw (CVE-2021-21148) in its V8 JavaScript rendering engine. "Google is aware of reports that an exploit for CVE-2021-21148 exists in the wild," the company said in
https://thehackernews.com/2021/02/new-chrome-browser-0-day-under-active.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/new-chrome-browser-0-day-under-active.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, February 4, 2021
ISC Stormcast For Friday, February 5th, 2021 https://isc.sans.edu/podcastdetail.html?id=7360, (Fri, Feb 5th)
Read the original article: ISC Stormcast For Friday, February 5th, 2021 https://isc.sans.edu/podcastdetail.html?id=7360, (Fri, Feb 5th) This post doesn’t have text content, please click on the link below to view the original article. ISC Stormcast For Friday, February 5th, 2021 https://isc.sans.edu/podcastdetail.html?id=7360,…
Read more → The post ISC Stormcast For Friday, February 5th, 2021 https://isc.sans.edu/podcastdetail.html?id=7360, (Fri, Feb 5th) first appeared on IT Security News.
https://www.itsecuritynews.info/isc-stormcast-for-friday-february-5th-2021-https-isc-sans-edu-podcastdetail-htmlid7360-fri-feb-5th/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/isc-stormcast-for-friday-february-5th-2021-https-isc-sans-edu-podcastdetail-htmlid7360-fri-feb-5th/?utm_source=dlvr.it&utm_medium=blogger
Why Human Error is #1 Cyber Security Threat to Businesses in 2021
Phishing and Malware Among the major cyber threats, the malware remains a significant danger. The 2017 WannaCry outbreak that cost businesses worldwide up to $4 billion is still in recent memory, and other new strains of malware are discovered on a daily basis. Phishing has also seen a resurgence in the last few years, with many new scams being invented to take advantage of unsuspecting
https://thehackernews.com/2021/02/why-human-error-is-1-cyber-security.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/why-human-error-is-1-cyber-security.html?utm_source=dlvr.it&utm_medium=blogger
Critical Bugs Found in Popular Realtek Wi-Fi Module for Embedded Devices
Major vulnerabilities have been discovered in the Realtek RTL8195A Wi-Fi module that could have been exploited to gain root access and take complete control of a device's wireless communications. The six flaws were reported by researchers from Israeli IoT security firm Vdoo. The Realtek RTL8195A module is a standalone, low-power-consumption Wi-Fi hardware module targeted at embedded devices used
https://thehackernews.com/2021/02/critical-bugs-found-in-popular-realtek.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/02/critical-bugs-found-in-popular-realtek.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)