USCellular is one of the mobile network operators that protect its customer’s privacy and strictly follows all its protection policies. But, recently, the USCelluar has encountered a data breach in which the hackers managed to get access to its CRM and customers’ accounts. USCellualar is taking all its steps to safeguard the personal information of […]
The post USCellular Hacked – Hackers Gained access to its CRM Software appeared first on Cyber Security News.
https://cybersecuritynews.com/uscellular-hacked-hackers-gained-access-to-its-crm-software/?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 31, 2021
Saturday, January 30, 2021
Bonobos – 2,811,929 breached accounts
Read the original article: Bonobos – 2,811,929 breached accounts In August 2020, the clothing store Bonobos suffered a data breach that exposed almost 70GB of data containing 2.8 million unique email addresses. The breach also exposed names, physical and IP…
Read more → The post Bonobos – 2,811,929 breached accounts first appeared on IT Security News.
https://www.itsecuritynews.info/bonobos-2811929-breached-accounts/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/bonobos-2811929-breached-accounts/?utm_source=dlvr.it&utm_medium=blogger
The Privacy Feud Between Facebook And Apple Is Heating Up
Read the original article: The Privacy Feud Between Facebook And Apple Is Heating Up The post The Privacy Feud Between Facebook And Apple Is Heating Up appeared first on Facecrooks. In recent months, Facebook and Apple have been locked in…
Read more → The post The Privacy Feud Between Facebook And Apple Is Heating Up first appeared on IT Security News.
https://www.itsecuritynews.info/the-privacy-feud-between-facebook-and-apple-is-heating-up/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-privacy-feud-between-facebook-and-apple-is-heating-up/?utm_source=dlvr.it&utm_medium=blogger
Week in security with Tony Anscombe
Read the original article: Week in security with Tony Anscombe Law enforcement disrupts Emotet – Wormable Android malware spreading via WhatsApp – Three iOS zero-day bugs squashed The post Week in security with Tony Anscombe appeared first on WeLiveSecurity …
Read more → The post Week in security with Tony Anscombe first appeared on IT Security News.
https://www.itsecuritynews.info/week-in-security-with-tony-anscombe-102/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/week-in-security-with-tony-anscombe-102/?utm_source=dlvr.it&utm_medium=blogger
Friday, January 29, 2021
New Malware Campaign Targeting Security Researchers Who is Working in Vulnerability Research
The Threat Analysis Group has recently detected an ongoing campaign targeting the security researchers who are working on vulnerability analysis and development at separate companies and organizations. According to the Google report, this campaign was well organized across various online platforms, that includes drive-by browser accommodations from booby-trapped websites. In the report, Google affirmed that […]
The post New Malware Campaign Targeting Security Researchers Who is Working in Vulnerability Research appeared first on Cyber Security News.
https://cybersecuritynews.com/new-malware-campaign-targeting-security-researchers/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/new-malware-campaign-targeting-security-researchers/?utm_source=dlvr.it&utm_medium=blogger
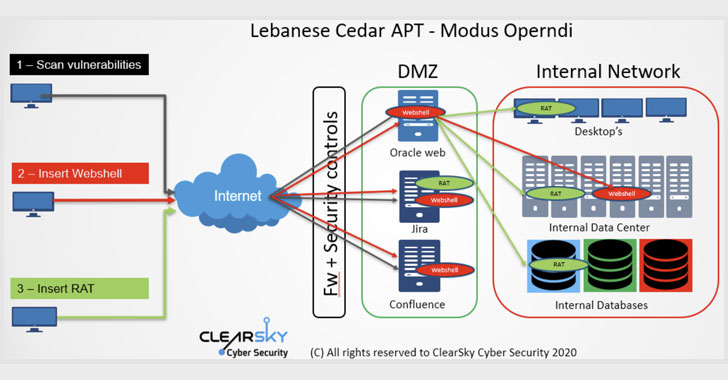
Hezbollah Hacker Group Targeted Telecoms, Hosting, ISPs Worldwide
A "persistent attacker group" with alleged ties to Hezbollah has retooled its malware arsenal with a new version of a remote access Trojan (RAT) to break into companies worldwide and extract valuable information. In a new report published by the ClearSky research team on Thursday, the Israeli cybersecurity firm said it identified at least 250 public-facing web servers since early 2020 that have
https://thehackernews.com/2021/01/hezbollah-hacker-group-targeted.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/hezbollah-hacker-group-targeted.html?utm_source=dlvr.it&utm_medium=blogger
Rocke Group’s Malware Now Has Worm Capabilities
Read the original article: Rocke Group’s Malware Now Has Worm Capabilities This post doesn’t have text content, please click on the link below to view the original article. Rocke Group’s Malware Now Has Worm Capabilities Become a supporter of…
Read more → The post Rocke Group’s Malware Now Has Worm Capabilities first appeared on IT Security News.
https://www.itsecuritynews.info/rocke-groups-malware-now-has-worm-capabilities-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/rocke-groups-malware-now-has-worm-capabilities-2/?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 28, 2021
NSW taskforce wants Australia-wide cyber standards harmony
Read the original article: NSW taskforce wants Australia-wide cyber standards harmony Report has called for industry and all governments to follow the same standards to ‘build a more secure Australia’. Become a supporter of IT Security News and help…
Read more → The post NSW taskforce wants Australia-wide cyber standards harmony first appeared on IT Security News.
https://www.itsecuritynews.info/nsw-taskforce-wants-australia-wide-cyber-standards-harmony/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/nsw-taskforce-wants-australia-wide-cyber-standards-harmony/?utm_source=dlvr.it&utm_medium=blogger
Sending the All Clear Signal: The Implications of WhatsApp’s New Data Privacy Policy
Read the original article: Sending the All Clear Signal: The Implications of WhatsApp’s New Data Privacy Policy Popular messaging app WhatsApp announced new data privacy policy changes set to debut on February 8, much to the chagrin of its massive…
Read more → The post Sending the All Clear Signal: The Implications of WhatsApp’s New Data Privacy Policy first appeared on IT Security News.
https://www.itsecuritynews.info/sending-the-all-clear-signal-the-implications-of-whatsapps-new-data-privacy-policy/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/sending-the-all-clear-signal-the-implications-of-whatsapps-new-data-privacy-policy/?utm_source=dlvr.it&utm_medium=blogger
Authorities Seize Dark-Web Site Linked to the Netwalker Ransomware
U.S. and Bulgarian authorities this week took control of the dark web site used by the NetWalker ransomware cybercrime group to publish data stolen from its victims. "We are striking back against the growing threat of ransomware by not only bringing criminal charges against the responsible actors, but also disrupting criminal online infrastructure and, wherever possible, recovering ransom
https://thehackernews.com/2021/01/authorities-seize-dark-web-site-linked.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/authorities-seize-dark-web-site-linked.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, January 27, 2021
HPE awarded $35+M to build supercomputer using its end-to-end HPC technologies for the NCAR
Read the original article: HPE awarded $35+M to build supercomputer using its end-to-end HPC technologies for the NCAR Hewlett Packard Enterprise (HPE) announced it was awarded a $35+ million contract to build a new supercomputer using its end-to-end high performance…
Read more → The post HPE awarded $35+M to build supercomputer using its end-to-end HPC technologies for the NCAR first appeared on IT Security News.
https://www.itsecuritynews.info/hpe-awarded-35m-to-build-supercomputer-using-its-end-to-end-hpc-technologies-for-the-ncar/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hpe-awarded-35m-to-build-supercomputer-using-its-end-to-end-hpc-technologies-for-the-ncar/?utm_source=dlvr.it&utm_medium=blogger
New Docker Container Escape Bug Affects Microsoft Azure Functions
Cybersecurity researcher Paul Litvak today disclosed an unpatched vulnerability in Microsoft Azure Functions that could be used by an attacker to escalate privileges and escape the Docker container used for hosting them. The findings come as part of Intezer Lab's investigations into the Azure compute infrastructure. Following disclosure to Microsoft, the Windows maker is said to have "determined
https://thehackernews.com/2021/01/new-docker-container-escape-bug-affects.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/new-docker-container-escape-bug-affects.html?utm_source=dlvr.it&utm_medium=blogger
In the Wake of the SolarWinds Hack, Here's How Businesses Should Respond
Throughout 2020, businesses, in general, have had their hands full with IT challenges. They had to rush to accommodate a sudden shift to remote work. Then they had to navigate a rapid adoption of automation technologies. And as the year came to a close, more businesses began trying to assemble the safety infrastructure required to return to some semblance of normal in 2021. But at the end of the
https://thehackernews.com/2021/01/in-wake-of-solarwinds-hack-heres-how.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/in-wake-of-solarwinds-hack-heres-how.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 26, 2021
Quantum unveils H2000 Series, a line of hybrid storage arrays
Read the original article: Quantum unveils H2000 Series, a line of hybrid storage arrays Quantum announced the launch of the H2000 Series of hybrid storage arrays to provide customers with cost-effective performance, ease of use, and scalability for data-intensive workflows.…
Read more → The post Quantum unveils H2000 Series, a line of hybrid storage arrays first appeared on IT Security News.
https://www.itsecuritynews.info/quantum-unveils-h2000-series-a-line-of-hybrid-storage-arrays/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/quantum-unveils-h2000-series-a-line-of-hybrid-storage-arrays/?utm_source=dlvr.it&utm_medium=blogger
Google releases alarming report about North Korean hackers posing as security analysts
Read the original article: Google releases alarming report about North Korean hackers posing as security analysts Google said the attackers were targeting security researchers by using fake LinkedIn and Twitter profiles and asking to collaborate. Become a supporter of…
Read more → The post Google releases alarming report about North Korean hackers posing as security analysts first appeared on IT Security News.
https://www.itsecuritynews.info/google-releases-alarming-report-about-north-korean-hackers-posing-as-security-analysts/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/google-releases-alarming-report-about-north-korean-hackers-posing-as-security-analysts/?utm_source=dlvr.it&utm_medium=blogger
Hackers Can Exploit Windows RDP Servers to Amplify DDoS Attacks
These days, Windows Remote Desktop Protocol (RDP) servers are being exploited by DDoS-for-hire services to expand Distributed Denial of Service (DDoS) attacks. However, we all know that Microsoft is one of the latest major tech firms to check that all its resources are being ill-treated as part of a DDoS attack. Cybersecurity researchers have recently […]
The post Hackers Can Exploit Windows RDP Servers to Amplify DDoS Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/hackers-can-exploit-windows-rdp-servers-to-amplify-ddos-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/hackers-can-exploit-windows-rdp-servers-to-amplify-ddos-attacks/?utm_source=dlvr.it&utm_medium=blogger
Monday, January 25, 2021
Part Two: Secure Coding Urban Myths
Read the original article: Part Two: Secure Coding Urban Myths In part one of this two-part series, we dug into a few urban myths about the security of open source code and trusting your favorite developer tools. While the myths…
Read more → The post Part Two: Secure Coding Urban Myths first appeared on IT Security News.
https://www.itsecuritynews.info/part-two-secure-coding-urban-myths/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/part-two-secure-coding-urban-myths/?utm_source=dlvr.it&utm_medium=blogger
IT Security News Daily Summary 2021-01-25
2.28M MeetMindful Daters Compromised in Data Breach Outgoing FCC Chair Issues Final Security Salvo Against China Breaking Down Joe Biden’s $10B Cybersecurity ‘Down Payment’ Deloitte & Touche Buys Threat-Hunting Firm Is Biden’s Peloton Bike an IoT Cybersecurity Risk? Ransomware attack…
Read more → The post IT Security News Daily Summary 2021-01-25 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-01-25/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-01-25/?utm_source=dlvr.it&utm_medium=blogger
Pen Testing By Numbers: Tracking Pen Testing Trends and Challenges
Over the years, penetration testing has had to change and adapt alongside the IT environments and technology that need to be assessed. Broad cybersecurity issues often influence the strategy and growth of pen-testing. In such a fast-paced field, organizations get real value from learning about others' penetration testing experiences, identifying trends, and the role they play in today's threat
https://thehackernews.com/2021/01/pen-testing-by-numbers-tracking-pen.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/pen-testing-by-numbers-tracking-pen.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 24, 2021
How to Protect Your IoT Devices From Botnet Attacks
IoT devices allow us to connect everything and make our environment smart. However, the technology has always been marred by insecurity, with manufacturers and security organizations still unable to ensure the safety of these devices. According to a report by Nozomi networks, the continued growth of IoT in 2020 was also mirrored by growing categories […]
The post How to Protect Your IoT Devices From Botnet Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/how-to-protect-your-iot-devices-from-botnet-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/how-to-protect-your-iot-devices-from-botnet-attacks/?utm_source=dlvr.it&utm_medium=blogger
Chinese Hacker Group Abusing Cloud Services to Steal Passenger Data From the Airline Industry
According to the recent threat report of the cybersecurity researchers at Fox-IT, there is a hacking group from China that has been attacking nearly all airline companies for the past few years. The experts have also claimed in their report that the main purpose behind the campaign was to collect all passenger data so that […]
The post Chinese Hacker Group Abusing Cloud Services to Steal Passenger Data From the Airline Industry appeared first on Cyber Security News.
https://cybersecuritynews.com/chinese-hacker-group-abusing-cloud-services/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/chinese-hacker-group-abusing-cloud-services/?utm_source=dlvr.it&utm_medium=blogger
Multilingual Cybersecurity Awareness Training adapted for your needs
Technology alone cannot protect you from everything. Because the online world is so interconnected, everyone is a target, no matter if you are an individual, small business or huge enterprise. Cybersecurity awareness training teaches your employees – to spot fake…
Read more → The post Multilingual Cybersecurity Awareness Training adapted for your needs first appeared on IT Security News.
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-10/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/multilingual-cybersecurity-awareness-training-adapted-for-your-needs-10/?utm_source=dlvr.it&utm_medium=blogger
Saturday, January 23, 2021
iPhone 13
Read the original article: iPhone 13 It’s early to talk about the 2021 iPhone, but rumors are already buzzing about what to expect from the so called iPhone 13. Here’s what we know so far. Click to read our iPhone…
Read more → The post iPhone 13 first appeared on IT Security News.
https://www.itsecuritynews.info/iphone-13/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/iphone-13/?utm_source=dlvr.it&utm_medium=blogger
AirPods 3: Everything We Know So Far
Read the original article: AirPods 3: Everything We Know So Far Apple is working on a third-generation version of the AirPods, and for this updated version rumored to be launching in 2021, we could see some design changes for the…
Read more → The post AirPods 3: Everything We Know So Far first appeared on IT Security News.
https://www.itsecuritynews.info/airpods-3-everything-we-know-so-far/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/airpods-3-everything-we-know-so-far/?utm_source=dlvr.it&utm_medium=blogger
Beware! Fully-Functional Released Online for SAP Solution Manager Flaw
Cybersecurity researchers have warned of a publicly available fully-functional exploit that could be used to target SAP enterprise software. The exploit leverages a vulnerability, tracked as CVE-2020-6207, that stems from a missing authentication check in SAP Solution Manager (SolMan) version 7.2 SAP SolMan is an application management and administration solution that offers end-to-end
https://thehackernews.com/2021/01/beware-fully-functional-released-online.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/beware-fully-functional-released-online.html?utm_source=dlvr.it&utm_medium=blogger
Friday, January 22, 2021
Statistics-Based OWASP Top 10 2021 Proposal
Read the original article: Statistics-Based OWASP Top 10 2021 Proposal Everybody knows the OWASP Top 10 as well as the fact that it gets updated only every other 3-4 years. With the last update published in 2017, it’s no surprise…
Read more → The post Statistics-Based OWASP Top 10 2021 Proposal first appeared on IT Security News.
https://www.itsecuritynews.info/statistics-based-owasp-top-10-2021-proposal/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/statistics-based-owasp-top-10-2021-proposal/?utm_source=dlvr.it&utm_medium=blogger
Samsung Galaxy Buds Pro vs. Apple AirPods Pro
Read the original article: Samsung Galaxy Buds Pro vs. Apple AirPods Pro Samsung in January unveiled new flagship Galaxy S21 smartphones and alongside the new phones, introduced the $200 Galaxy Buds Pro, which are priced at $199 and offer Active…
Read more → The post Samsung Galaxy Buds Pro vs. Apple AirPods Pro first appeared on IT Security News.
https://www.itsecuritynews.info/samsung-galaxy-buds-pro-vs-apple-airpods-pro/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/samsung-galaxy-buds-pro-vs-apple-airpods-pro/?utm_source=dlvr.it&utm_medium=blogger
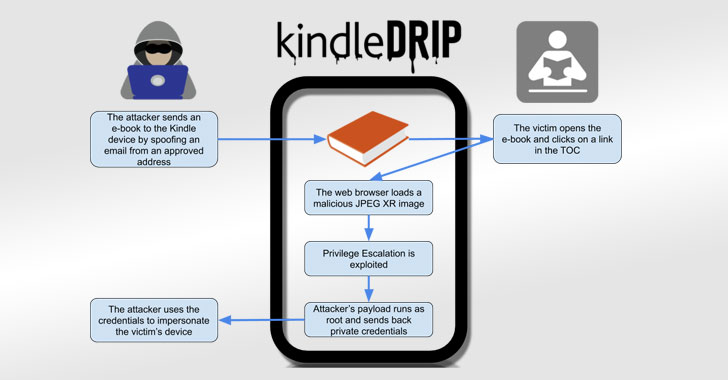
Sharing eBook With Your Kindle Could Have Let Hackers Hijack Your Account
Amazon has addressed a number of flaws in its Kindle e-reader platform that could have allowed an attacker to take control of victims' devices by simply sending them a malicious e-book. Dubbed "KindleDrip," the exploit chain takes advantage of a feature called "Send to Kindle" to send a malware-laced document to a Kindle device that, when opened, could be leveraged to remotely execute arbitrary
https://thehackernews.com/2021/01/sharing-ebook-with-your-kindle-could.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/sharing-ebook-with-your-kindle-could.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 21, 2021
EFF’s Top Recommendations for the Biden Administration
Read the original article: EFF’s Top Recommendations for the Biden Administration At noon on January 20, 2021, Joseph R. Biden, Jr. was sworn in as the 46th President of the United States, and he and his staff took over the…
Read more → The post EFF’s Top Recommendations for the Biden Administration first appeared on IT Security News.
https://www.itsecuritynews.info/effs-top-recommendations-for-the-biden-administration/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/effs-top-recommendations-for-the-biden-administration/?utm_source=dlvr.it&utm_medium=blogger
MrbMiner Crypto-Mining Malware Links to Iranian Software Company
A relatively new crypto-mining malware that surfaced last year and infected thousands of Microsoft SQL Server (MSSQL) databases has now been linked to a small software development company based in Iran. The attribution was made possible due to an operational security oversight, said researchers from cybersecurity firm Sophos, that led to the company's name inadvertently making its way into the
https://thehackernews.com/2021/01/mrbminer-crypto-mining-malware-links-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/mrbminer-crypto-mining-malware-links-to.html?utm_source=dlvr.it&utm_medium=blogger
Importance of Application Security and Customer Data Protection to a Startup
When you are a startup, there are umpteen things that demand your attention. You must give your hundred percent (probably even more!) to work effectively and efficiently with the limited resources. Understandably, the application security importance may be pushed at the bottom of your things-to-do list. One other reason to ignore web application protectioncould be your belief that only large
https://thehackernews.com/2021/01/importance-of-application-security-and.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/importance-of-application-security-and.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, January 20, 2021
QSC unveils Professional Tier feature set for Q-SYS Reflect Enterprise Manager
Read the original article: QSC unveils Professional Tier feature set for Q-SYS Reflect Enterprise Manager QSC announced the availability of the new Professional Tier feature set for Q-SYS Reflect Enterprise Manager remote monitoring and management service. This advanced feature set…
Read more → The post QSC unveils Professional Tier feature set for Q-SYS Reflect Enterprise Manager first appeared on IT Security News.
https://www.itsecuritynews.info/qsc-unveils-professional-tier-feature-set-for-q-sys-reflect-enterprise-manager/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/qsc-unveils-professional-tier-feature-set-for-q-sys-reflect-enterprise-manager/?utm_source=dlvr.it&utm_medium=blogger
Bugs in Facebook, Google chat, JioChat Let Attackers Spy on the Users
Google’s Project Zero security researcher, Natalie Silvanovich discovered a serious vulnerability in Group FaceTime which allowed an attacker to call a target and force the call to connect without user interaction from the target, allowing the attacker to listen to the target’s surroundings without their knowledge or consent. The bug was remarkable in both its […]
The post Bugs in Facebook, Google chat, JioChat Let Attackers Spy on the Users appeared first on Cyber Security News.
https://cybersecuritynews.com/messaging-apps-bug/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/messaging-apps-bug/?utm_source=dlvr.it&utm_medium=blogger
Google Discloses Flaws in Signal, FB Messenger, JioChat Messaging Apps
In January 2019, a critical flaw was reported in Apple's FaceTime group chats feature that made it possible for users to initiate a FaceTime video call and eavesdrop on targets by adding their own number as a third person in a group chat even before the person on the other end accepted the incoming call. The vulnerability was deemed so severe that the iPhone maker removed the FaceTime group
https://thehackernews.com/2021/01/google-discloses-flaws-in-signal-fb.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/google-discloses-flaws-in-signal-fb.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 19, 2021
New OCC Rule Is a Win in the Fight Against Financial Censorship
Read the original article: New OCC Rule Is a Win in the Fight Against Financial Censorship On Thursday, the Office of the Comptroller of the Currency finalized its Fair Access to Financial Services rule, which will prevent banks from refusing…
Read more → The post New OCC Rule Is a Win in the Fight Against Financial Censorship first appeared on IT Security News.
https://www.itsecuritynews.info/new-occ-rule-is-a-win-in-the-fight-against-financial-censorship/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/new-occ-rule-is-a-win-in-the-fight-against-financial-censorship/?utm_source=dlvr.it&utm_medium=blogger
Researchers Discover Raindrop — 4th Malware Linked to the SolarWinds Attack
Cybersecurity researchers have unearthed a fourth new malware strain—designed to spread the malware onto other computers in victims' networks—which was deployed as part of the SolarWinds supply chain attack disclosed late last year. Dubbed "Raindrop" by Broadcom-owned Symantec, the malware joins the likes of other malicious implants such as Sunspot, Sunburst (or Solorigate), and Teardrop that
https://thehackernews.com/2021/01/researchers-discover-raindrop-4th.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/researchers-discover-raindrop-4th.html?utm_source=dlvr.it&utm_medium=blogger
New Educational Video Series for CISOs with Small Security Teams
Cybersecurity is hard. For a CISO that faces the cyber threat landscape with a small security team, the challenge is compounded. Compared to CISOs at large enterprises, CISOs small to medium-sized enterprises (SMEs) have smaller teams with less expertise, smaller budgets for technology and outside services, and are more involved in day-to-day protection activities. CISOs at SMEs are
https://thehackernews.com/2021/01/new-educational-video-series-for-cisos.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/new-educational-video-series-for-cisos.html?utm_source=dlvr.it&utm_medium=blogger
Monday, January 18, 2021
CI Security appoints Steve Sedlock as CRO and Kristoffer Turner as VP of Security Operations
Read the original article: CI Security appoints Steve Sedlock as CRO and Kristoffer Turner as VP of Security Operations CI Security announced the addition of Steve Sedlock as the company’s Chief Revenue Officer (CRO) and the promotion of Kristoffer Turner…
Read more → The post CI Security appoints Steve Sedlock as CRO and Kristoffer Turner as VP of Security Operations first appeared on IT Security News.
https://www.itsecuritynews.info/ci-security-appoints-steve-sedlock-as-cro-and-kristoffer-turner-as-vp-of-security-operations/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ci-security-appoints-steve-sedlock-as-cro-and-kristoffer-turner-as-vp-of-security-operations/?utm_source=dlvr.it&utm_medium=blogger
Hackers Leaked 22 Million Records on the Dark Web in 2020
Read the original article: Hackers Leaked 22 Million Records on the Dark Web in 2020 Hackers leaked over 22 million records on the Dark Web in 2020, putting your business in danger of cyberattacks. Here’s how to mitigate it. The…
Read more → The post Hackers Leaked 22 Million Records on the Dark Web in 2020 first appeared on IT Security News.
https://www.itsecuritynews.info/hackers-leaked-22-million-records-on-the-dark-web-in-2020/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hackers-leaked-22-million-records-on-the-dark-web-in-2020/?utm_source=dlvr.it&utm_medium=blogger
Joker’s Stash, the Largest Underground Carding Marketplace, Shuts Down
Security experts from the FBI and Interpol have recently seized several servers of the large carder site, Joker’s Stash, temporarily disrupted the site’s operation. According to the reports, a coordinated police operation is still ongoing, but security officials have declined to comment further on the matter. Special sources informed the seizure of domains that appeared […]
The post Joker’s Stash, the Largest Underground Carding Marketplace, Shuts Down appeared first on Cyber Security News.
https://cybersecuritynews.com/jokers-stash-shuts-down/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/jokers-stash-shuts-down/?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 17, 2021
D-Link announces official implementation of the IEC 62443-4-1 industry security standard certification
Read the original article: D-Link announces official implementation of the IEC 62443-4-1 industry security standard certification D-Link announced their official implementation of the IEC 62443-4-1 industry security standard, which was certified by internationally recognized certification organization TÜV NORD. From design…
Read more → The post D-Link announces official implementation of the IEC 62443-4-1 industry security standard certification first appeared on IT Security News.
https://www.itsecuritynews.info/d-link-announces-official-implementation-of-the-iec-62443-4-1-industry-security-standard-certification/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/d-link-announces-official-implementation-of-the-iec-62443-4-1-industry-security-standard-certification/?utm_source=dlvr.it&utm_medium=blogger
Apple Extends 13-Inch MacBook Pro Backlight Repair Program
Read the original article: Apple Extends 13-Inch MacBook Pro Backlight Repair Program Apple this week extended its worldwide 13-inch MacBook Pro Display Backlight Service Program, authorizing coverage for eligible notebooks for up to five years after the original purchase date…
Read more → The post Apple Extends 13-Inch MacBook Pro Backlight Repair Program first appeared on IT Security News.
https://www.itsecuritynews.info/apple-extends-13-inch-macbook-pro-backlight-repair-program/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-extends-13-inch-macbook-pro-backlight-repair-program/?utm_source=dlvr.it&utm_medium=blogger
Penetration testing
Penetration testing is the technical analysis of the safety level of IT systems and networks. We offer a complete investigation of the hardware / software systems for security vulnerabilities. If you have at least one online service, then you must…
Read more → The post Penetration testing first appeared on IT Security News.
https://www.itsecuritynews.info/penetration-testing-10/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/penetration-testing-10/?utm_source=dlvr.it&utm_medium=blogger
Saturday, January 16, 2021
Pcaps and the Tools That Love Them Part 1 of ???
Read the original article: Pcaps and the Tools That Love Them Part 1 of ??? There are many pcap tools available and which ones you use really depends on what you’re using them for. Some are very good at just…
Read more → The post Pcaps and the Tools That Love Them Part 1 of ??? first appeared on IT Security News.
https://www.itsecuritynews.info/pcaps-and-the-tools-that-love-them-part-1-of/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/pcaps-and-the-tools-that-love-them-part-1-of/?utm_source=dlvr.it&utm_medium=blogger
Joker's Stash, The Largest Carding Marketplace, Announces Shutdown
Joker's Stash, the largest dark web marketplace notorious for selling compromised payment card data, has announced plans to shut down its operations on February 15, 2021. In a message board post on a Russian-language underground cybercrime forum, the operator of the site — who goes by the name "JokerStash" — said "it's time for us to leave forever" and that "we will never ever open again,"
https://thehackernews.com/2021/01/jokers-stash-largest-carding.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/jokers-stash-largest-carding.html?utm_source=dlvr.it&utm_medium=blogger
Iconic BugTraq security mailing list shuts down after 27 years
Read the original article: Iconic BugTraq security mailing list shuts down after 27 years BugTraq launched in November 1993 and it was one of the first mailing lists dedicated to disclosing vulnerabilities. Become a supporter of IT Security News…
Read more → The post Iconic BugTraq security mailing list shuts down after 27 years first appeared on IT Security News.
https://www.itsecuritynews.info/iconic-bugtraq-security-mailing-list-shuts-down-after-27-years/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/iconic-bugtraq-security-mailing-list-shuts-down-after-27-years/?utm_source=dlvr.it&utm_medium=blogger
Friday, January 15, 2021
The 2021 NDAA, White Supremacy and Domestic Extremism
Read the original article: The 2021 NDAA, White Supremacy and Domestic Extremism The U.S. Capitol with security fencing after the Jan 6. insurrection (Victoria Pickering, https://tinyurl.com/y6o8t29m; CC BY-NC-ND 2.0, https://creativecommons.org/licenses/by-nc-nd/2.0/). In early January, Congress overcame a presidential veto and enacted…
Read more → The post The 2021 NDAA, White Supremacy and Domestic Extremism first appeared on IT Security News.
https://www.itsecuritynews.info/the-2021-ndaa-white-supremacy-and-domestic-extremism/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-2021-ndaa-white-supremacy-and-domestic-extremism/?utm_source=dlvr.it&utm_medium=blogger
How law enforcement gets around your smartphone’s encryption
Read the original article: How law enforcement gets around your smartphone’s encryption How law enforcement gets around your smartphone’s encryption l33tdawg Fri, 01/15/2021 – 22:50 Become a supporter of IT Security News and help us remove the ads. Read…
Read more → The post How law enforcement gets around your smartphone’s encryption first appeared on IT Security News.
https://www.itsecuritynews.info/how-law-enforcement-gets-around-your-smartphones-encryption-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/how-law-enforcement-gets-around-your-smartphones-encryption-2/?utm_source=dlvr.it&utm_medium=blogger
Researchers Disclose Undocumented Chinese Malware Used in Recent Attacks
Cybersecurity researchers have disclosed a series of attacks by a threat actor of Chinese origin that has targeted organizations in Russia and Hong Kong with malware — including a previously undocumented backdoor. Attributing the campaign to Winnti (or APT41), Positive Technologies dated the first attack to May 12, 2020, when the APT used LNK shortcuts to extract and run the malware payload. A
https://thehackernews.com/2021/01/researchers-disclose-undocumented.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/researchers-disclose-undocumented.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 14, 2021
Xiaomi added to US list of alleged Communist Chinese military companies
Read the original article: Xiaomi added to US list of alleged Communist Chinese military companies Device maker joins a list that includes Huawei, Hikvision, Inspur, Panda Electronics, and Semiconductor Manufacturing International Corporation. Become a supporter of IT Security News…
Read more → The post Xiaomi added to US list of alleged Communist Chinese military companies first appeared on IT Security News.
https://www.itsecuritynews.info/xiaomi-added-to-us-list-of-alleged-communist-chinese-military-companies/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/xiaomi-added-to-us-list-of-alleged-communist-chinese-military-companies/?utm_source=dlvr.it&utm_medium=blogger
New Malware That Uses WiFi BSSID to Determine the Victim’s Location
The cybersecurity researchers at SANS Internet Storm Center’s Xavier Mertens recently recognized malware that utilizes an exciting method to discover the victim’s possible location. One of the interesting facts of this malware is that it does not use various GeoIP API services. The experts affirmed that this malware usually assembles an infected user’s Basic Service […]
The post New Malware That Uses WiFi BSSID to Determine the Victim’s Location appeared first on Cyber Security News.
https://cybersecuritynews.com/new-malware-that-uses-wifi-bssid-to-determine-the-victims-location/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/new-malware-that-uses-wifi-bssid-to-determine-the-victims-location/?utm_source=dlvr.it&utm_medium=blogger
Experts Uncover Malware Attacks Against Colombian Government and Companies
Cybersecurity researchers took the wraps off an ongoing surveillance campaign directed against Colombian government institutions and private companies in the energy and metallurgical industries. In a report published by ESET on Tuesday, the Slovak internet security company said the attacks — dubbed "Operation Spalax" — began in 2020, with the modus operandi sharing some similarities to an APT
https://thehackernews.com/2021/01/experts-uncover-malware-attacks-against.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/experts-uncover-malware-attacks-against.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, January 13, 2021
HITRUST announces organizational changes in the form of new leadership appointments
Read the original article: HITRUST announces organizational changes in the form of new leadership appointments HITRUST announced strategic organizational changes in the form of new leadership appointments as well as new and expanded responsibilities for existing executive management. The changes…
Read more → The post HITRUST announces organizational changes in the form of new leadership appointments first appeared on IT Security News.
https://www.itsecuritynews.info/hitrust-announces-organizational-changes-in-the-form-of-new-leadership-appointments/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/hitrust-announces-organizational-changes-in-the-form-of-new-leadership-appointments/?utm_source=dlvr.it&utm_medium=blogger
Multiple Flaws With Fortinet FortiWeb WAF Would Allow Attackers to Hack Corporate Networks
The cybersecurity researchers of Positives Technologies have detected some severe flaws in the Fortinet FotiWeb web application firewall. According to the security experts, the threat actors could easily hack the corporate networks with these flaws. The Fortinet FortiWeb web application firewall (WAF) is generally created to shield servers from web-based attacks, but it got vulnerable […]
The post Multiple Flaws With Fortinet FortiWeb WAF Would Allow Attackers to Hack Corporate Networks appeared first on Cyber Security News.
https://cybersecuritynews.com/fortinet-fortiweb-waf/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/fortinet-fortiweb-waf/?utm_source=dlvr.it&utm_medium=blogger
Microsoft Issues Patches for Defender Zero-Day and 82 Other Windows Flaws
For the first patch Tuesday of 2021, Microsoft released security updates addressing a total of 83 flaws spanning as many as 11 products and services, including an actively exploited zero-day vulnerability. The latest security patches cover Microsoft Windows, Edge browser, ChakraCore, Office and Microsoft Office Services, and Web Apps, Visual Studio, Microsoft Malware Protection Engine, .NET Core
https://thehackernews.com/2021/01/microsoft-issues-patches-for-defender.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/microsoft-issues-patches-for-defender.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 12, 2021
Juspay Hacked – Over 100 Million Users Data Leaked in Dark web
The cybersecurity researchers have recently detected a data breach of Juspay’s servers. And according to the experts’ report, in this data breach, nearly 10 Crore of debit and credit cardholders’ data was compromised and the threat actors have leaked them on Dark Web. Later, this news was confirmed by one of the cybersecurity researchers, Rajaharai; […]
The post Juspay Hacked – Over 100 Million Users Data Leaked in Dark web appeared first on Cyber Security News.
https://cybersecuritynews.com/juspay-hacked-over-100-million-users-data-leaked-in-dark-web/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/juspay-hacked-over-100-million-users-data-leaked-in-dark-web/?utm_source=dlvr.it&utm_medium=blogger
Unveiled: SUNSPOT Malware Was Used to Inject SolarWinds Backdoor
As the investigation into the SolarWinds supply-chain attack continues, cybersecurity researchers have disclosed a third malware strain that was deployed into the build environment to inject the backdoor into the company's Orion network monitoring platform. Called "Sunspot," the malignant tool adds to a growing list of previously disclosed malicious software such as Sunburst and Teardrop. "This
https://thehackernews.com/2021/01/unveiled-sunspot-malware-was-used-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/unveiled-sunspot-malware-was-used-to.html?utm_source=dlvr.it&utm_medium=blogger
Parler Hack: Platform’s Role in U.S. Insurrection
Read the original article: Parler Hack: Platform’s Role in U.S. Insurrection After rioters stormed the U.S. Capitol last Wednesday, a hacker on Twitter archived the Trump supporters’ posts on Parler to piece together the role the platform played in the insurgency.…
Read more → The post Parler Hack: Platform’s Role in U.S. Insurrection first appeared on IT Security News.
https://www.itsecuritynews.info/parler-hack-platforms-role-in-u-s-insurrection/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/parler-hack-platforms-role-in-u-s-insurrection/?utm_source=dlvr.it&utm_medium=blogger
Monday, January 11, 2021
Igal Elbaz re-elected to serve as Chairman of the 5G Americas Board of Governors
Read the original article: Igal Elbaz re-elected to serve as Chairman of the 5G Americas Board of Governors Wireless cellular industry trade association, 5G Americas, announced Igal Elbaz, Senior Vice President, Wireless and Access Technology of AT&T has been re-elected…
Read more → The post Igal Elbaz re-elected to serve as Chairman of the 5G Americas Board of Governors first appeared on IT Security News.
https://www.itsecuritynews.info/igal-elbaz-re-elected-to-serve-as-chairman-of-the-5g-americas-board-of-governors/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/igal-elbaz-re-elected-to-serve-as-chairman-of-the-5g-americas-board-of-governors/?utm_source=dlvr.it&utm_medium=blogger
IT Security News Daily Summary 2021-01-11
The first Patch Tuesday of ’21; time to delay updates Did Trump shrink the government? Not according to the Plum Book USAID seeks remote sensing, analytics platform to track location, condition of aid DISA takes on DOD cloud operations The…
Read more → The post IT Security News Daily Summary 2021-01-11 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-01-11/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2021-01-11/?utm_source=dlvr.it&utm_medium=blogger
Russian Hacker Gets 12-Years Prison for Massive JP Morgan Chase Hack
A U.S. court on Thursday sentenced a 37-year-old Russian to 12 years in prison for perpetrating an international hacking campaign that resulted in the heist of a trove of personal information from several financial institutions, brokerage firms, financial news publishers, and other American companies. Andrei Tyurin was charged with computer intrusion, wire fraud, bank fraud, and illegal online
https://thehackernews.com/2021/01/russian-hacker-gets-12-years-prison-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/russian-hacker-gets-12-years-prison-for.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 10, 2021
4 Things to Know About FISMA
Read the original article: 4 Things to Know About FISMA Recently we wrote about the top cybersecurity frameworks to reduce cybersecurity risk, and the Federal Information Security Management Act (FISMA) certainly belongs in that list. But what is FISMA? Who…
Read more → The post 4 Things to Know About FISMA first appeared on IT Security News.
https://www.itsecuritynews.info/4-things-to-know-about-fisma/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/4-things-to-know-about-fisma/?utm_source=dlvr.it&utm_medium=blogger
Apple and Hyundai to Sign Apple Car Deal by March With Production Beginning in 2024
Read the original article: Apple and Hyundai to Sign Apple Car Deal by March With Production Beginning in 2024 Apple and Hyundai will reach a partnership agreement for the upcoming Apple Car by March, according to a new report shared…
Read more → The post Apple and Hyundai to Sign Apple Car Deal by March With Production Beginning in 2024 first appeared on IT Security News.
https://www.itsecuritynews.info/apple-and-hyundai-to-sign-apple-car-deal-by-march-with-production-beginning-in-2024/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-and-hyundai-to-sign-apple-car-deal-by-march-with-production-beginning-in-2024/?utm_source=dlvr.it&utm_medium=blogger
Streaming Wars as a Hotbed for Cybercriminals: Scope and Attacks
Time and again, Cybercriminals have forayed into the digital space, mostly convoyed with newer strategies to breach, attack, and plunder us of our confidentiality. Slithering into the unsuspicious segments, these threats make the most of our ignorance about the cybersecurity standards. If the diverse aspects of the digital domain weren’t enough for the cybercriminals to […]
The post Streaming Wars as a Hotbed for Cybercriminals: Scope and Attacks appeared first on Cyber Security News.
https://cybersecuritynews.com/streaming-wars-as-a-hotbed-for-cybercriminals-scope-and-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/streaming-wars-as-a-hotbed-for-cybercriminals-scope-and-attacks/?utm_source=dlvr.it&utm_medium=blogger
Saturday, January 9, 2021
Executive Branch Legal Process and the Self-Pardon
Read the original article: Executive Branch Legal Process and the Self-Pardon President Donald J. Trump disembarks Air Force One in New York State (Official White House Photo by Shealah Craighead/https://flic.kr/p/2khg4ds/Public Domain) It remains a possibility that President Trump will pardon…
Read more → The post Executive Branch Legal Process and the Self-Pardon first appeared on IT Security News.
https://www.itsecuritynews.info/executive-branch-legal-process-and-the-self-pardon/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/executive-branch-legal-process-and-the-self-pardon/?utm_source=dlvr.it&utm_medium=blogger
What is next gen antivirus? NGAV explained
Read the original article: What is next gen antivirus? NGAV explained This blog was written by a third party author. What is next gen antivirus (NGAV) and how does it work? In contrast to legacy antivirus technology, next generation antivirus…
Read more → The post What is next gen antivirus? NGAV explained first appeared on IT Security News.
https://www.itsecuritynews.info/what-is-next-gen-antivirus-ngav-explained/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/what-is-next-gen-antivirus-ngav-explained/?utm_source=dlvr.it&utm_medium=blogger
FBI Warns of Egregor Ransomware Targets Businesses Worldwide
Egregor Ransomware targets businesses worldwide, attempting to extort businesses by publicly releasing Exfiltrated Data. The US Federal Bureau of Investigation (FBI) first observed Egregor Ransomware in September 2020. The threat actors behind this ransomware variant claim to have compromised more than 150 victims worldwide until now. What is Egregor Ransomware? Egregor ransomware is operating as […]
The post FBI Warns of Egregor Ransomware Targets Businesses Worldwide appeared first on Cyber Security News.
https://cybersecuritynews.com/egregor-ransomware-attacks/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/egregor-ransomware-attacks/?utm_source=dlvr.it&utm_medium=blogger
Friday, January 8, 2021
California City’s Effort to Punish Journalists For Publishing Documents Widely Available Online is Dangerous and Chilling, EFF Brief Argues
Read the original article: California City’s Effort to Punish Journalists For Publishing Documents Widely Available Online is Dangerous and Chilling, EFF Brief Argues As part of their jobs, journalists routinely dig through government websites to find newsworthy documents and share…
Read more → The post California City’s Effort to Punish Journalists For Publishing Documents Widely Available Online is Dangerous and Chilling, EFF Brief Argues first appeared on IT Security News.
https://www.itsecuritynews.info/california-citys-effort-to-punish-journalists-for-publishing-documents-widely-available-online-is-dangerous-and-chilling-eff-brief-argues/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/california-citys-effort-to-punish-journalists-for-publishing-documents-widely-available-online-is-dangerous-and-chilling-eff-brief-argues/?utm_source=dlvr.it&utm_medium=blogger
New Attack Could Let Hackers Clone Your Google Titan 2FA Security Keys
Hardware security keys—such as those from Google and Yubico—are considered the most secure means to protect accounts from phishing and takeover attacks. But a new research published on Thursday demonstrates how an adversary in possession of such a two-factor authentication (2FA) device can clone it by exploiting an electromagnetic side-channel in the chip embedded in it. The vulnerability (
https://thehackernews.com/2021/01/new-attack-could-let-hackers-clone-your.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/new-attack-could-let-hackers-clone-your.html?utm_source=dlvr.it&utm_medium=blogger
ALERT: North Korean hackers targeting South Korea with RokRat Trojan
A North Korean hacking group has been found deploying the RokRat Trojan in a new spear-phishing campaign targeting the South Korean government. Attributing the attack to APT37 (aka Starcruft, Ricochet Chollima, or Reaper), Malwarebytes said it identified a malicious document last December that, when opened, executes a macro in memory to install the aforementioned remote access tool (RAT). "The
https://thehackernews.com/2021/01/alert-north-korean-hackers-targeting.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/alert-north-korean-hackers-targeting.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, January 7, 2021
RansomExx newer variants adapted to Attack Linux servers
RansomExx is a ransomware variant responsible for several high-profile attacks in 2020 and has revealed signs of further development and unhampered activity. It includes the use of trojanized software to deliver malicious payloads and an overall short and fastest attack. The most recently reported development involves the use of newer variants adapted for Linux servers […]
The post RansomExx newer variants adapted to Attack Linux servers appeared first on Cyber Security News.
https://cybersecuritynews.com/ransomexx-attacks-linux-servers/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/ransomexx-attacks-linux-servers/?utm_source=dlvr.it&utm_medium=blogger
Farewell Flash, Forevermore
Read the original article: Farewell Flash, Forevermore Dear Flash, You helped us get our coding legs with Dreamweaver on sites like MySpace and the early web, but you were easily overtaken and hackable. The security and performance holes in your…
Read more → The post Farewell Flash, Forevermore first appeared on IT Security News.
https://www.itsecuritynews.info/farewell-flash-forevermore/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/farewell-flash-forevermore/?utm_source=dlvr.it&utm_medium=blogger
SolarWinds Hackers Also Accessed U.S. Justice Department's Email Server
The U.S. Department of Justice on Wednesday became the latest government agency in the country to admit its internal network was compromised as part of the SolarWinds supply chain attack. "On December 24, 2020, the Department of Justice's Office of the Chief Information Officer (OCIO) learned of previously unknown malicious activity linked to the global SolarWinds incident that has affected
https://thehackernews.com/2021/01/solarwinds-hackers-also-accessed-us.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/solarwinds-hackers-also-accessed-us.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, January 6, 2021
Greg Nicastro joins SmartBear as EVP/GM of Products and Technology
Read the original article: Greg Nicastro joins SmartBear as EVP/GM of Products and Technology SmartBear announced Greg Nicastro has joined the company as EVP/GM of Products and Technology. He was previously Chief Product Officer at cloud cost management leader, CloudHealth…
Read more → The post Greg Nicastro joins SmartBear as EVP/GM of Products and Technology first appeared on IT Security News.
https://www.itsecuritynews.info/greg-nicastro-joins-smartbear-as-evp-gm-of-products-and-technology/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/greg-nicastro-joins-smartbear-as-evp-gm-of-products-and-technology/?utm_source=dlvr.it&utm_medium=blogger
FBI Warn Hackers are Using Hijacked Home Security Devices
The U.S. Federal Bureau of Investigation has recently reported that the threat actors are hacking home security systems and applying them to place fake calls to emergency services. The F.B.I. has issued an announcement to warn all the users of smart home devices with cameras and voice skills to apply all kinds of complex, unique […]
The post FBI Warn Hackers are Using Hijacked Home Security Devices appeared first on Cyber Security News.
https://cybersecuritynews.com/fbi-warn-hackers-are-using-hijacked-home-security-devices/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/fbi-warn-hackers-are-using-hijacked-home-security-devices/?utm_source=dlvr.it&utm_medium=blogger
FBI, CISA, NSA Officially Blame Russia for SolarWinds Cyber Attack
The U.S. government on Tuesday formally pointed fingers at the Russian government for orchestrating the massive SolarWinds supply chain attack that came to light early last month. "This work indicates that an Advanced Persistent Threat (APT) actor, likely Russian in origin, is responsible for most or all of the recently discovered, ongoing cyber compromises of both government and
https://thehackernews.com/2021/01/fbi-cisa-nsa-officially-blames-russia.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/fbi-cisa-nsa-officially-blames-russia.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, January 5, 2021
Vertiv appoints Stephanie Gill as Chief Legal Counsel and Corporate Secretary
Read the original article: Vertiv appoints Stephanie Gill as Chief Legal Counsel and Corporate Secretary Vertiv named Stephanie Gill, Esq., the company’s new Chief Legal Counsel and Corporate Secretary. She will report directly to Chief Executive Officer, Rob Johnson, effective…
Read more → The post Vertiv appoints Stephanie Gill as Chief Legal Counsel and Corporate Secretary first appeared on IT Security News.
https://www.itsecuritynews.info/vertiv-appoints-stephanie-gill-as-chief-legal-counsel-and-corporate-secretary/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/vertiv-appoints-stephanie-gill-as-chief-legal-counsel-and-corporate-secretary/?utm_source=dlvr.it&utm_medium=blogger
Warning: Cross-Platform ElectroRAT Malware Targeting Cryptocurrency Users
Cybersecurity researchers today revealed a wide-ranging scam targeting cryptocurrency users that began as early as January last year to distribute trojanized applications to install a previously undetected remote access tool on target systems. Called ElectroRAT by Intezer, the RAT is written from ground-up in Golang and designed to target multiple operating systems such as Windows, Linux, and
https://thehackernews.com/2021/01/warning-cross-platform-electrorat.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/warning-cross-platform-electrorat.html?utm_source=dlvr.it&utm_medium=blogger
Google Speech-to-Text API Can Help Attackers Easily Bypass Google reCAPTCHA
A three-year-old attack technique to bypass Google's audio reCAPTCHA by using its own Speech-to-Text API has been found to still work with 97% accuracy. Researcher Nikolai Tschacher disclosed his findings in a proof-of-concept (PoC) of the attack on January 2. "The idea of the attack is very simple: You grab the MP3 file of the audio reCAPTCHA and you submit it to Google's own speech-to-text API
https://thehackernews.com/2021/01/google-speech-to-text-api-can-help.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/google-speech-to-text-api-can-help.html?utm_source=dlvr.it&utm_medium=blogger
Monday, January 4, 2021
Microsoft Source Code Exposed: What We Know & What It Means
Read the original article: Microsoft Source Code Exposed: What We Know & What It Means Microsoft says there is no increase in security risk; however, experts say access to source code could make some steps easier for attackers. Become…
Read more → The post Microsoft Source Code Exposed: What We Know & What It Means first appeared on IT Security News.
https://www.itsecuritynews.info/microsoft-source-code-exposed-what-we-know-what-it-means/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/microsoft-source-code-exposed-what-we-know-what-it-means/?utm_source=dlvr.it&utm_medium=blogger
Secret Backdoor Found in Zyxel Firewall and AP Controllers
The Niels Teusink of Dutch cybersecurity firm EYE has recently revealed a secret backdoor official account in the latest “4.60 patch 0” for some Zyxel devices. Nearly 100,000 Zyxel devices got vulnerable to a hidden backdoor (CVE-2020-29583) that has been caused by hardcoded credentials, which are used to update firewall and AP controllers’ firmware. We […]
The post Secret Backdoor Found in Zyxel Firewall and AP Controllers appeared first on Cyber Security News.
https://cybersecuritynews.com/secret-backdoor-found-in-zyxel-firewall-and-ap-controllers/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/secret-backdoor-found-in-zyxel-firewall-and-ap-controllers/?utm_source=dlvr.it&utm_medium=blogger
British Court Rejects U.S. Request to Extradite WikiLeaks' Julian Assange
A British court has rejected the U.S. government's request to extradite Wikileaks founder Julian Assange to the country on charges pertaining to illegally obtaining and sharing classified material related to national security. In a hearing at Westminster Magistrates' Court today, Judge Vanessa Baraitser denied the extradition on the grounds that Assange is a suicide risk and extradition to the
https://thehackernews.com/2021/01/british-court-rejects-us-request-to.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/british-court-rejects-us-request-to.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, January 3, 2021
StrongPity APT Extends CyberAttack WorldWide with it’s New Infrastructure
StrongPity or Promethium APT, also referred to as APT-C-41, has been active since 2012. It had been first publicly reported in October 2016, after cyberattacks against users in Belgium and Italy during which it used the watering-hole attack technique to deliver malicious versions of WinRAR and the TrueCrypt file encryption software. The group mainly uses […]
The post StrongPity APT Extends CyberAttack WorldWide with it’s New Infrastructure appeared first on Cyber Security News.
https://cybersecuritynews.com/strongpity-apt-extends-cyberattack/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/strongpity-apt-extends-cyberattack/?utm_source=dlvr.it&utm_medium=blogger
A Smorgasbord of Bad Takedowns: 2020 Year in Review
Read the original article: A Smorgasbord of Bad Takedowns: 2020 Year in Review Here at EFF, we take particular notice of the way that intellectual property law leads to expression being removed from the Internet. We document the worst examples…
Read more → The post A Smorgasbord of Bad Takedowns: 2020 Year in Review first appeared on IT Security News.
https://www.itsecuritynews.info/a-smorgasbord-of-bad-takedowns-2020-year-in-review/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/a-smorgasbord-of-bad-takedowns-2020-year-in-review/?utm_source=dlvr.it&utm_medium=blogger
Booz Allen Leads New Frost & Sullivan Security Report
Read the original article: Booz Allen Leads New Frost & Sullivan Security Report MCLEAN, Va.–(BUSINESS WIRE)–Frost & Sullivan, a leading market research and strategy firm, ranked Booz Allen Hamilton (NYSE: BAH) as holding the largest single market share in Managed…
Read more → The post Booz Allen Leads New Frost & Sullivan Security Report first appeared on IT Security News.
https://www.itsecuritynews.info/booz-allen-leads-new-frost-sullivan-security-report/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/booz-allen-leads-new-frost-sullivan-security-report/?utm_source=dlvr.it&utm_medium=blogger
Saturday, January 2, 2021
DNS, DoH, and ODoH, Oh My: Year-in-Review 2020
Read the original article: DNS, DoH, and ODoH, Oh My: Year-in-Review 2020 Government knowledge of what sites activists have visited can put them at risk of serious injury, arrest, or even death. This makes it a vitally important priority to…
Read more → The post DNS, DoH, and ODoH, Oh My: Year-in-Review 2020 first appeared on IT Security News.
https://www.itsecuritynews.info/dns-doh-and-odoh-oh-my-year-in-review-2020/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/dns-doh-and-odoh-oh-my-year-in-review-2020/?utm_source=dlvr.it&utm_medium=blogger
Ticketmaster To Pay $10 Million Fine For Hacking A Rival Company
Ticketmaster has agreed to pay a $10 million fine after being charged with illegally accessing computer systems of a competitor repeatedly between 2013 and 2015 in an attempt to "cut [the company] off at the knees." A subsidiary of Live Nation, the California-based ticket sales and distribution company used the stolen information to gain an advantage over CrowdSurge — which merged with Songkick
https://thehackernews.com/2021/01/ticketmaster-to-pay-10-million-fine-for.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2021/01/ticketmaster-to-pay-10-million-fine-for.html?utm_source=dlvr.it&utm_medium=blogger
Backdoor account discovered in more than 100,000 Zyxel firewalls, VPN gateways
Read the original article: Backdoor account discovered in more than 100,000 Zyxel firewalls, VPN gateways The username and password (zyfwp/PrOw!aN_fXp) were visible in one of the Zyxel firmware binaries. Become a supporter of IT Security News and help us…
Read more → The post Backdoor account discovered in more than 100,000 Zyxel firewalls, VPN gateways first appeared on IT Security News.
https://www.itsecuritynews.info/backdoor-account-discovered-in-more-than-100000-zyxel-firewalls-vpn-gateways/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/backdoor-account-discovered-in-more-than-100000-zyxel-firewalls-vpn-gateways/?utm_source=dlvr.it&utm_medium=blogger
Friday, January 1, 2021
Expert found a secret backdoor in Zyxel firewall and VPN
Read the original article: Expert found a secret backdoor in Zyxel firewall and VPN Zyxel addressed a critical flaw in its firmware, tracked as CVE-2020-29583, related to the presence of a hardcoded undocumented secret account. The Taiwanese vendor Zyxel has addressed…
Read more → The post Expert found a secret backdoor in Zyxel firewall and VPN first appeared on IT Security News.
https://www.itsecuritynews.info/expert-found-a-secret-backdoor-in-zyxel-firewall-and-vpn/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/expert-found-a-secret-backdoor-in-zyxel-firewall-and-vpn/?utm_source=dlvr.it&utm_medium=blogger
Microsoft Says SolarWinds Hackers Accessed Some of Its Source Code
Microsoft on Thursday revealed that the threat actors behind the SolarWinds supply chain attack were able to gain access to a small number of internal accounts and escalate access inside its internal network. The "very sophisticated nation-state actor" used the unauthorized access to view, but not modify, the source code present in its repositories, the company said. "We detected
https://thehackernews.com/2020/12/microsoft-says-solarwinds-hackers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/microsoft-says-solarwinds-hackers.html?utm_source=dlvr.it&utm_medium=blogger
Online frauds increased by 70% because of Corona Virus
Read the original article: Online frauds increased by 70% because of Corona Virus Online Frauds such as shopping, dating and finance related have increased by 70% in 2020 says a research carried out by Action fraud. The intelligence unit of…
Read more → The post Online frauds increased by 70% because of Corona Virus first appeared on IT Security News.
https://www.itsecuritynews.info/online-frauds-increased-by-70-because-of-corona-virus/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/online-frauds-increased-by-70-because-of-corona-virus/?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)