Read the original article: Cyber Security Roundup for January 2021 A suspected nation-state sophisticated cyber-attack of SolarWinds which led to the distribution of a tainted version the SolarWinds Orion network monitoring tool, compromising their customers, dominated the cyber headlines in…
Read more → The post Cyber Security Roundup for January 2021 first appeared on IT Security News.
https://www.itsecuritynews.info/cyber-security-roundup-for-january-2021/?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 31, 2020
Microsoft Reveals That Russian Attackers Accessed Some of Its Source Code
Read the original article: Microsoft Reveals That Russian Attackers Accessed Some of Its Source Code Malicious SolarWinds Orion backdoor installed in Microsoft’s network led to the attackers viewing some of its source code. Become a supporter of IT Security…
Read more → The post Microsoft Reveals That Russian Attackers Accessed Some of Its Source Code first appeared on IT Security News.
https://www.itsecuritynews.info/microsoft-reveals-that-russian-attackers-accessed-some-of-its-source-code/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/microsoft-reveals-that-russian-attackers-accessed-some-of-its-source-code/?utm_source=dlvr.it&utm_medium=blogger
Ticketmaster Pays $10m DoJ Fine For Accessing Rival’s Computer
Read the original article: Ticketmaster Pays $10m DoJ Fine For Accessing Rival’s Computer Criminal computer intrusion fine imposed on Ticketmaster by the US DoJ, after it repeatedly accessed computer system of a rival Become a supporter of IT Security…
Read more → The post Ticketmaster Pays $10m DoJ Fine For Accessing Rival’s Computer first appeared on IT Security News.
https://www.itsecuritynews.info/ticketmaster-pays-10m-doj-fine-for-accessing-rivals-computer/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ticketmaster-pays-10m-doj-fine-for-accessing-rivals-computer/?utm_source=dlvr.it&utm_medium=blogger
Wednesday, December 30, 2020
T-Mobile data breach: CPNI (Customer Proprietary Network Information) exposed
Read the original article: T-Mobile data breach: CPNI (Customer Proprietary Network Information) exposed T-Mobile has disclosed a data breach that exposed customers’ network information (CPNI), including phone numbers and calls records. T-Mobile has disclosed a data breach exposing customers’ account’s…
Read more → The post T-Mobile data breach: CPNI (Customer Proprietary Network Information) exposed first appeared on IT Security News.
https://www.itsecuritynews.info/t-mobile-data-breach-cpni-customer-proprietary-network-information-exposed/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/t-mobile-data-breach-cpni-customer-proprietary-network-information-exposed/?utm_source=dlvr.it&utm_medium=blogger
Kawasaki Security Breach – Unauthorized Access to a Server from an Overseas Location
Kawasaki Heavy Industries, Ltd. is a Japanese public multinational corporation primarily known as a manufacturer of motorcycles, engines, heavy equipment, aerospace and defense equipment, rolling stock and ships. The company declared that it was subject to unauthorized access from outside the company. As a result of a thorough investigation, the company have discovered that some […]
The post Kawasaki Security Breach – Unauthorized Access to a Server from an Overseas Location appeared first on Cyber Security News.
https://cybersecuritynews.com/kawasaki-security-breach/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/kawasaki-security-breach/?utm_source=dlvr.it&utm_medium=blogger
Multi-platform Credit Card SKimmer hits Shopify, Bigcommerce, and Others
Security experts from SanSec, warn of a multi-platform credit card skimmer that targets online stores running on Shopify, BigCommerce, Zencart, and Woocommerce. This new skimmer can also target the hosted platforms like BigCommerce and Shopify even though it does not allow custom Javascript on checkout pages. Expert says that this skimmer shows a fake payment […]
The post Multi-platform Credit Card SKimmer hits Shopify, Bigcommerce, and Others appeared first on Cyber Security News.
https://cybersecuritynews.com/multi-platform-credit-card-skimmer/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/multi-platform-credit-card-skimmer/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, December 29, 2020
FBI: Pranksters are hijacking smart devices to live-stream swatting incidents
Read the original article: FBI: Pranksters are hijacking smart devices to live-stream swatting incidents The FBI said it’s working with smart device makers to address the issue. Become a supporter of IT Security News and help us remove the…
Read more → The post FBI: Pranksters are hijacking smart devices to live-stream swatting incidents first appeared on IT Security News.
https://www.itsecuritynews.info/fbi-pranksters-are-hijacking-smart-devices-to-live-stream-swatting-incidents/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/fbi-pranksters-are-hijacking-smart-devices-to-live-stream-swatting-incidents/?utm_source=dlvr.it&utm_medium=blogger
Op-ed: What nobody else will say about the new cybersecurity crisis
Read the original article: Op-ed: What nobody else will say about the new cybersecurity crisis The culprit is said to be Russia, but equal responsibility lies much closer to home. Become a supporter of IT Security News and help…
Read more → The post Op-ed: What nobody else will say about the new cybersecurity crisis first appeared on IT Security News.
https://www.itsecuritynews.info/op-ed-what-nobody-else-will-say-about-the-new-cybersecurity-crisis/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/op-ed-what-nobody-else-will-say-about-the-new-cybersecurity-crisis/?utm_source=dlvr.it&utm_medium=blogger
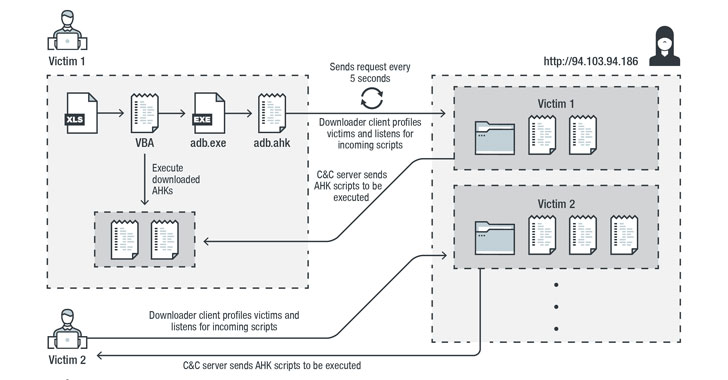
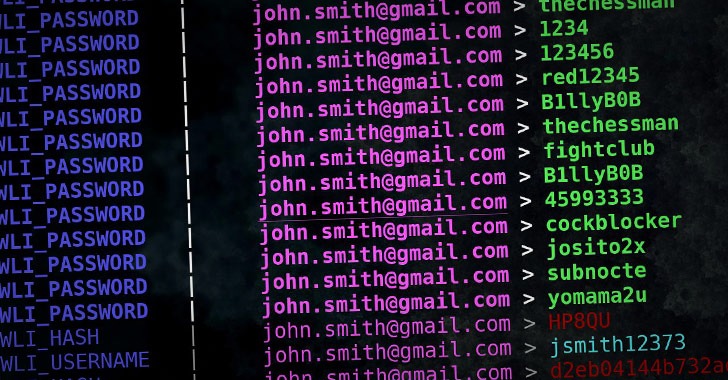
AutoHotkey-Based Password Stealer Targeting US, Canadian Banking Users
Threat actors have been discovered distributing a new credential stealer written in AutoHotkey (AHK) scripting language as part of an ongoing campaign that started early 2020. Customers of financial institutions in the US and Canada are among the primary targets for credential exfiltration, with a specific focus on banks such as Scotiabank, Royal Bank of Canada, HSBC, Alterna Bank, Capital One,
https://thehackernews.com/2020/12/autohotkey-based-password-stealer.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/autohotkey-based-password-stealer.html?utm_source=dlvr.it&utm_medium=blogger
Monday, December 28, 2020
Threat actor is selling a dump allegedly including 2,5M customers of service provider Ho Mobile
Read the original article: Threat actor is selling a dump allegedly including 2,5M customers of service provider Ho Mobile Threat intelligence analyst discovered a threat actor that is selling a database of the Italian mobile service provider Ho mobile. Threat…
Read more → The post Threat actor is selling a dump allegedly including 2,5M customers of service provider Ho Mobile first appeared on IT Security News.
https://www.itsecuritynews.info/threat-actor-is-selling-a-dump-allegedly-including-25m-customers-of-service-provider-ho-mobile/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/threat-actor-is-selling-a-dump-allegedly-including-25m-customers-of-service-provider-ho-mobile/?utm_source=dlvr.it&utm_medium=blogger
Apple Hearing Study Bug Results in Accidental Historical Data Collection From Participants
Read the original article: Apple Hearing Study Bug Results in Accidental Historical Data Collection From Participants Apple device owners who participated in the Apple Hearing Study that Apple is conducting with the University of Michigan School of Public Health are…
Read more → The post Apple Hearing Study Bug Results in Accidental Historical Data Collection From Participants first appeared on IT Security News.
https://www.itsecuritynews.info/apple-hearing-study-bug-results-in-accidental-historical-data-collection-from-participants/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-hearing-study-bug-results-in-accidental-historical-data-collection-from-participants/?utm_source=dlvr.it&utm_medium=blogger
Beyond the Technical – Advise for those starting in Infosec
Read the original article: Beyond the Technical – Advise for those starting in Infosec One question I get on a regular basis is “I want to start a career in infosec where do I start?” and when I ask in…
Read more → The post Beyond the Technical – Advise for those starting in Infosec first appeared on IT Security News.
https://www.itsecuritynews.info/beyond-the-technical-advise-for-those-starting-in-infosec/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/beyond-the-technical-advise-for-those-starting-in-infosec/?utm_source=dlvr.it&utm_medium=blogger
Sunday, December 27, 2020
2020-12-24 (Thursday) – Dridex infection example
Read the original article: 2020-12-24 (Thursday) – Dridex infection example This post doesn’t have text content, please click on the link below to view the original article. 2020-12-24 (Thursday) – Dridex infection example Become a supporter of IT Security…
Read more → The post 2020-12-24 (Thursday) – Dridex infection example first appeared on IT Security News.
https://www.itsecuritynews.info/2020-12-24-thursday-dridex-infection-example/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/2020-12-24-thursday-dridex-infection-example/?utm_source=dlvr.it&utm_medium=blogger
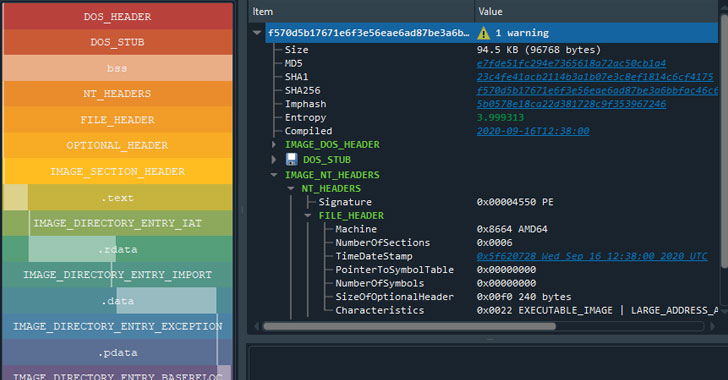
A New SolarWinds Flaw Likely Had Let Hackers Install SUPERNOVA Malware
An authentication bypass vulnerability in the SolarWinds Orion software may have been leveraged by adversaries as zero-day to deploy the SUPERNOVA malware in target environments. According to an advisory published yesterday by the CERT Coordination Center, the SolarWinds Orion API that's used to interface with all other Orion system monitoring and management products suffers from a security flaw
https://thehackernews.com/2020/12/a-new-solarwinds-flaw-likely-had-let.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/a-new-solarwinds-flaw-likely-had-let.html?utm_source=dlvr.it&utm_medium=blogger
CYBERSECURITY CONSULTANT: ARE MORE CISSPS EMBRACING THE GIG ECONOMY?
Read the original article: CYBERSECURITY CONSULTANT: ARE MORE CISSPS EMBRACING THE GIG ECONOMY? This post was originally published by (ISC)² Management. The gig economy has grown rapidly in recent years and now includes more than one third of U.S. workers…
Read more → The post CYBERSECURITY CONSULTANT: ARE MORE CISSPS EMBRACING THE GIG ECONOMY? first appeared on IT Security News.
https://www.itsecuritynews.info/cybersecurity-consultant-are-more-cissps-embracing-the-gig-economy-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/cybersecurity-consultant-are-more-cissps-embracing-the-gig-economy-2/?utm_source=dlvr.it&utm_medium=blogger
Saturday, December 26, 2020
The U.S. Internet Is Being Starved of Its Potential: 2020 in Review
Read the original article: The U.S. Internet Is Being Starved of Its Potential: 2020 in Review Over a year ago, EFF raised the desperate need for the United States to have a universal fiber infrastructure plan in order to ensure…
Read more → The post The U.S. Internet Is Being Starved of Its Potential: 2020 in Review first appeared on IT Security News.
https://www.itsecuritynews.info/the-u-s-internet-is-being-starved-of-its-potential-2020-in-review/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-u-s-internet-is-being-starved-of-its-potential-2020-in-review/?utm_source=dlvr.it&utm_medium=blogger
TruKno TTP based Threat Intelligence Platform
Read the original article: TruKno TTP based Threat Intelligence Platform TruKno’s ThreatBoard is a platform that helps security professionals uncover the root causes behind emerging cyber-attacks, Improving proactive defense postures.. TTP Based Threat Intelligence Trukno, a Community-based Threat Intelligence Platform…
Read more → The post TruKno TTP based Threat Intelligence Platform first appeared on IT Security News.
https://www.itsecuritynews.info/trukno-ttp-based-threat-intelligence-platform/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/trukno-ttp-based-threat-intelligence-platform/?utm_source=dlvr.it&utm_medium=blogger
Police Arrest 21 WeLeakInfo Customers Who Bought Breached Personal Data
21 people have been arrested across the UK as part of a nationwide cyber crackdown targeting customers of WeLeakInfo[.]com, a now-defunct online service that had been previously selling access to data hacked from other websites. The suspects used stolen personal credentials to commit further cyber and fraud offences, the NCA said. Of the 21 arrested—all men aged between 18 and 38— nine have been
https://thehackernews.com/2020/12/police-arrest-21-weleakinfo-customers.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/police-arrest-21-weleakinfo-customers.html?utm_source=dlvr.it&utm_medium=blogger
Friday, December 25, 2020
Apple Setup Issues: Apple Watch Verification Failed, HomePod Stuck on Configuring
Read the original article: Apple Setup Issues: Apple Watch Verification Failed, HomePod Stuck on Configuring Apple’s status page shows an ongoing issue with “iCloud Account and Sign In” since early Christmas morning. The issue seems likely to be related to…
Read more → The post Apple Setup Issues: Apple Watch Verification Failed, HomePod Stuck on Configuring first appeared on IT Security News.
https://www.itsecuritynews.info/apple-setup-issues-apple-watch-verification-failed-homepod-stuck-on-configuring/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-setup-issues-apple-watch-verification-failed-homepod-stuck-on-configuring/?utm_source=dlvr.it&utm_medium=blogger
The software-defined home: IoT sensors can help build healthier and greener housing
Read the original article: The software-defined home: IoT sensors can help build healthier and greener housing Creating an oasis of health in your home is getting easier with the help of sensors and IoT devices. Become a supporter of…
Read more → The post The software-defined home: IoT sensors can help build healthier and greener housing first appeared on IT Security News.
https://www.itsecuritynews.info/the-software-defined-home-iot-sensors-can-help-build-healthier-and-greener-housing/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-software-defined-home-iot-sensors-can-help-build-healthier-and-greener-housing/?utm_source=dlvr.it&utm_medium=blogger
Attackers Abusing Citrix NetScaler Devices to Launch Amplified DDoS Attacks
Citrix has issued an emergency advisory warning its customers of a security issue affecting its NetScaler application delivery controller (ADC) devices that attackers are abusing to launch amplified distributed denial-of-service (DDoS) attacks against several targets. "An attacker or bots can overwhelm the Citrix ADC [Datagram Transport Layer Security] network throughput, potentially leading to
https://thehackernews.com/2020/12/citrix-adc-ddos-attack.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/citrix-adc-ddos-attack.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 24, 2020
SUNBURST Additional Technical Details
Read the original article: SUNBURST Additional Technical Details FireEye has discovered additional details about the SUNBURST backdoor since our initial publication on Dec. 13, 2020. Before diving into the technical depth of this malware, we recommend readers familiarize themselves with…
Read more → The post SUNBURST Additional Technical Details first appeared on IT Security News.
https://www.itsecuritynews.info/sunburst-additional-technical-details/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/sunburst-additional-technical-details/?utm_source=dlvr.it&utm_medium=blogger
Why AI and security pros need to work together to fight cybercrime
Read the original article: Why AI and security pros need to work together to fight cybercrime Cybercriminals sometimes use AI to their benefit. In order to defeat these cyber bad guys, security pros and AI should focus on what they…
Read more → The post Why AI and security pros need to work together to fight cybercrime first appeared on IT Security News.
https://www.itsecuritynews.info/why-ai-and-security-pros-need-to-work-together-to-fight-cybercrime/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/why-ai-and-security-pros-need-to-work-together-to-fight-cybercrime/?utm_source=dlvr.it&utm_medium=blogger
North Korean Hackers Trying to Steal COVID-19 Vaccine Research
Threat actors such as the notorious Lazarus group are continuing to tap into the ongoing COVID-19 vaccine research to steal sensitive information to speed up their countries' vaccine-development efforts. Cybersecurity firm Kaspersky detailed two incidents at a pharmaceutical company and a government ministry in September and October leveraging different tools and techniques but exhibiting
https://thehackernews.com/2020/12/north-korean-hackers-trying-to-steal.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/north-korean-hackers-trying-to-steal.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, December 23, 2020
FireEye shares jump back to pre-hack levels
Read the original article: FireEye shares jump back to pre-hack levels Andrew Nowinski, D.A. Davidson, on FireEye's recovery, post-hack. With CNBC's Melissa Lee and the Fast Money traders, Guy Adami, Tim Seymour, Dan Nathan and Nadine Terman. Become a…
Read more → The post FireEye shares jump back to pre-hack levels first appeared on IT Security News.
https://www.itsecuritynews.info/fireeye-shares-jump-back-to-pre-hack-levels/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/fireeye-shares-jump-back-to-pre-hack-levels/?utm_source=dlvr.it&utm_medium=blogger
Google Faces its 3rd Major Antitrust Lawsuit for Using Monopolistic Powers to Control Pricing
Recently Google faced the 3rd antitrust lawsuit, and it’s one of the major lawsuits for using Monopolistic powers to control different pricing. In this lawsuit, more than 30 states joined Google’s mushrooming legal miseries. We have recently reported that Google Faces a $5 billion Lawsuit in the U.S. for Tracking When Users Browsing via “Incognito” […]
The post Google Faces its 3rd Major Antitrust Lawsuit for Using Monopolistic Powers to Control Pricing appeared first on Cyber Security News.
https://cybersecuritynews.com/google-faces-its-3rd-major-antitrust-lawsuit/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/google-faces-its-3rd-major-antitrust-lawsuit/?utm_source=dlvr.it&utm_medium=blogger
New Critical Flaws in Treck TCP/IP Stack Affect Millions of IoT Devices
The US Cybersecurity Infrastructure and Security Agency (CISA) has warned of critical vulnerabilities in a low-level TCP/IP software library developed by Treck that, if weaponized, could allow remote attackers to run arbitrary commands and mount denial-of-service (DoS) attacks. The four flaws affect Treck TCP/IP stack version 6.0.1.67 and earlier and were reported to the company by Intel. Two of
https://thehackernews.com/2020/12/new-critical-flaws-in-treck-tcpip-stack.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/new-critical-flaws-in-treck-tcpip-stack.html?utm_source=dlvr.it&utm_medium=blogger
Tuesday, December 22, 2020
Don’t let a data breach sink your business: Here’s what you need to know
Read the original article: Don’t let a data breach sink your business: Here’s what you need to know Experts offer insights about the legal and financial hits, as well as the devastating loss of reputation, your business might suffer if…
Read more → The post Don’t let a data breach sink your business: Here’s what you need to know first appeared on IT Security News.
https://www.itsecuritynews.info/dont-let-a-data-breach-sink-your-business-heres-what-you-need-to-know/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/dont-let-a-data-breach-sink-your-business-heres-what-you-need-to-know/?utm_source=dlvr.it&utm_medium=blogger
Cybercriminals' Favorite Bulletproof VPN Service Shuts Down In Global Action
Law enforcement agencies from the US, Germany, Netherlands, Switzerland, France, along with Europol's European Cybercrime Centre (EC3), announced today the coordinated takedown of Safe-Inet, a popular virtual private network (VPN) service that was used to facilitate criminal activity. The three domains in question — insorg[.]org, safe-inet[.]com, and safe-inet[.]net — were shut down, and their
https://thehackernews.com/2020/12/cybercriminals-favorite-bulletproof-vpn.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/cybercriminals-favorite-bulletproof-vpn.html?utm_source=dlvr.it&utm_medium=blogger
A Second Hacker Group May Have Also Breached SolarWinds, Microsoft Says
As the probe into the SolarWinds supply chain attack continues, new digital forensic evidence has brought to light that a separate threat actor may have been abusing the IT infrastructure provider's Orion software to drop a similar persistent backdoor on target systems. "The investigation of the whole SolarWinds compromise led to the discovery of an additional malware that also affects the
https://thehackernews.com/2020/12/a-second-hacker-group-may-have-also.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/a-second-hacker-group-may-have-also.html?utm_source=dlvr.it&utm_medium=blogger
Monday, December 21, 2020
May Mitchell joins iboss as Senior Vice President of Marketing
Read the original article: May Mitchell joins iboss as Senior Vice President of Marketing iboss announces that May Mitchell has joined the firm as Senior Vice President of Marketing. In her new role, Mitchell will oversee sales and marketing of the…
Read more → The post \May Mitchell joins iboss as Senior Vice President of Marketing\ first appeared on \IT Security News\.
https://www.itsecuritynews.info/may-mitchell-joins-iboss-as-senior-vice-president-of-marketing/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/may-mitchell-joins-iboss-as-senior-vice-president-of-marketing/?utm_source=dlvr.it&utm_medium=blogger
Two Critical Flaws — CVSS Score 10 — Affect Dell Wyse Thin Client Devices
A team of researchers today unveils two critical security vulnerabilities it discovered in Dell Wyse Thin clients that could have potentially allowed attackers to remotely execute malicious code and access arbitrary files on affected devices. The flaws, which were uncovered by healthcare cybersecurity provider CyberMDX and reported to Dell in June 2020, affects all devices running ThinOS
https://thehackernews.com/2020/12/two-critical-flaws-cvss-score-10-affect.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/two-critical-flaws-cvss-score-10-affect.html?utm_source=dlvr.it&utm_medium=blogger
iPhones of 36 Journalists Hacked Using iMessage Zero-Click Exploit
Three dozen journalists working for Al Jazeera had their iPhones stealthily compromised via a zero-click exploit to install spyware as part of a Middle East cyberespionage campaign. In a new report published yesterday by University of Toronto's Citizen Lab, researchers said personal phones of 36 journalists, producers, anchors, and executives at Al Jazeera, and a journalist at London-based Al
https://thehackernews.com/2020/12/iphones-of-36-journalists-hacked-using.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/iphones-of-36-journalists-hacked-using.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, December 20, 2020
Trump administration says Russia behind SolarWinds hack.Trump himself begs to differ
Read the original article: Trump administration says Russia behind SolarWinds hack.Trump himself begs to differ Microsoft’s analysis of hack details next-level ‘DLL hell’ after likely developer pipeline compromise United States secretary of state Mike Pompeo has laid the blame for…
Read more →
The post Trump administration says Russia behind SolarWinds hack.Trump himself begs to differ first appeared on IT Security News.
https://www.itsecuritynews.info/trump-administration-says-russia-behind-solarwinds-hack-trump-himself-begs-to-differ/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/trump-administration-says-russia-behind-solarwinds-hack-trump-himself-begs-to-differ/?utm_source=dlvr.it&utm_medium=blogger
Apple Offers Solution for ‘Pairing Canceled’ Error When Using Apple Fitness+ on Apple TV
Read the original article: Apple Offers Solution for ‘Pairing Canceled’ Error When Using Apple Fitness+ on Apple TV Some customers attempting to use the new Apple Fitness+ workout service on their Apple TVs have been encountering a “pairing canceled” error…
Read more →
The post Apple Offers Solution for 'Pairing Canceled' Error When Using Apple Fitness+ on Apple TV first appeared on IT Security News.
https://www.itsecuritynews.info/apple-offers-solution-for-pairing-canceled-error-when-using-apple-fitness-on-apple-tv/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-offers-solution-for-pairing-canceled-error-when-using-apple-fitness-on-apple-tv/?utm_source=dlvr.it&utm_medium=blogger
Zero-Hour Phishing Attack on Google’s App Engine Targeting Office 365 Users Pushes Holiday Spike Above 100%
Read the original article: Zero-Hour Phishing Attack on Google’s App Engine Targeting Office 365 Users Pushes Holiday Spike Above 100% As we write this post, SlashNext Threat Labs is witnessing an active attack on Google’s App Engine service via Appspot.com…
Read more →
The post Zero-Hour Phishing Attack on Google’s App Engine Targeting Office 365 Users Pushes Holiday Spike Above 100% first appeared on IT Security News.
https://www.itsecuritynews.info/zero-hour-phishing-attack-on-googles-app-engine-targeting-office-365-users-pushes-holiday-spike-above-100/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/zero-hour-phishing-attack-on-googles-app-engine-targeting-office-365-users-pushes-holiday-spike-above-100/?utm_source=dlvr.it&utm_medium=blogger
Saturday, December 19, 2020
What’s Next for the Western Sahara Conflict?
Read the original article: What’s Next for the Western Sahara Conflict? A Sahrawi refugee camp in Tindouf, Algeria. (EU Civil Protection & Humanitarian Aid, https://flic.kr/p/bxuHsR; CC BY-SA 2.0, https://creativecommons.org/licenses/by-sa/2.0/deed.en) On Dec. 10, Morocco scored a long-dreamed-of foreign policy victory. After…
Read more →
The post What’s Next for the Western Sahara Conflict? first appeared on IT Security News.
https://www.itsecuritynews.info/whats-next-for-the-western-sahara-conflict-2/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/whats-next-for-the-western-sahara-conflict-2/?utm_source=dlvr.it&utm_medium=blogger
Secure Communication using TLS in Elasticsearch, (Sat, Dec 19th)
Read the original article: Secure Communication using TLS in Elasticsearch, (Sat, Dec 19th) In the past, I have published a couple diaries on Elasticsearch for pihole and tcp-honeypot to parse and report on the data capture by those applications. …
Read more →
The post Secure Communication using TLS in Elasticsearch, (Sat, Dec 19th) first appeared on IT Security News.
https://www.itsecuritynews.info/secure-communication-using-tls-in-elasticsearch-sat-dec-19th/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/secure-communication-using-tls-in-elasticsearch-sat-dec-19th/?utm_source=dlvr.it&utm_medium=blogger
The European Commission added VKontakte and Telegram to the list of pirate sites
Read the original article: The European Commission added VKontakte and Telegram to the list of pirate sites VKontakte is surprised by the decision of the European Commission to include the social network in the list of resources that contribute to…
Read more →
The post The European Commission added VKontakte and Telegram to the list of pirate sites first appeared on IT Security News.
https://www.itsecuritynews.info/the-european-commission-added-vkontakte-and-telegram-to-the-list-of-pirate-sites/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/the-european-commission-added-vkontakte-and-telegram-to-the-list-of-pirate-sites/?utm_source=dlvr.it&utm_medium=blogger
Friday, December 18, 2020
Microsoft Says Its Systems Were Also Breached in Massive SolarWinds Hack
The massive state-sponsored espionage campaign that compromised software maker SolarWinds also targeted Microsoft, as the unfolding investigation into the hacking spree reveals the incident may have been far more wider in scope, sophistication, and impact than previously thought. News of Microsoft's compromise was first reported by Reuters, which also said the company's own products were then
https://thehackernews.com/2020/12/microsoft-says-its-systems-were-also.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/microsoft-says-its-systems-were-also.html?utm_source=dlvr.it&utm_medium=blogger
IT Security News Daily Summary 2020-12-18
Securely managing the IT workload: In-house or outsource? T-Mobile: Massive BYOD growth raises huge enterprise security risks Apple, Google, Microsoft, and Mozilla ban Kazakhstan’s MitM HTTPS certificate VERT Alert: SolarWinds Supply Chain Attack Cloud is King: 9 Software Security Trends…
Read more →
The post IT Security News Daily Summary 2020-12-18 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2020-12-18/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2020-12-18/?utm_source=dlvr.it&utm_medium=blogger
Massive Fraud Operation Facilitated By Evil Mobile Emulator Steals Millions From Banks
Read the original article: Massive Fraud Operation Facilitated By Evil Mobile Emulator Steals Millions From Banks Threat actors behind an ongoing worldwide mobile banking fraud campaign were able to steal millions from multiple US and EU banks, needing just a…
Read more →
The post Massive Fraud Operation Facilitated By Evil Mobile Emulator Steals Millions From Banks first appeared on IT Security News.
https://www.itsecuritynews.info/massive-fraud-operation-facilitated-by-evil-mobile-emulator-steals-millions-from-banks/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/massive-fraud-operation-facilitated-by-evil-mobile-emulator-steals-millions-from-banks/?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 17, 2020
iFixit Starts Tearing Down AirPods Max
Read the original article: iFixit Starts Tearing Down AirPods Max iFixit today began disassembling Apple’s new AirPods Max headphones for one of its traditional device teardowns, with the aim of determining whether the AirPods Max are repairable to any degree…
Read more →
The post iFixit Starts Tearing Down AirPods Max first appeared on IT Security News.
https://www.itsecuritynews.info/ifixit-starts-tearing-down-airpods-max/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/ifixit-starts-tearing-down-airpods-max/?utm_source=dlvr.it&utm_medium=blogger
IT Security News Daily Summary 2020-12-17
Streamlining AI workflows with the NetApp Data Science Toolkit Three Upcoming Security Regulations Automotive Companies Need to Know How using tactical literacy makes it harder for cybercriminals to fool end users Facebook Again Slams Apple Over Privacy Concerns 5 million…
Read more →
The post IT Security News Daily Summary 2020-12-17 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2020-12-17/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2020-12-17/?utm_source=dlvr.it&utm_medium=blogger
Software Supply-Chain Attack Hits Vietnam Government Certification Authority
Cybersecurity researchers today disclosed a new supply-chain attack targeting the Vietnam Government Certification Authority (VGCA) that compromised the agency's digital signature toolkit to install a backdoor on victim systems. Uncovered by Slovak internet security company ESET early this month, the "SignSight" attack involved modifying software installers hosted on the CA's website ("ca.gov.vn
https://thehackernews.com/2020/12/software-supply-chain-attack-hits.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/software-supply-chain-attack-hits.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, December 16, 2020
Focus of OT and IoT Cybersecurity in Australia’s Critical Infrastructure
Read the original article: Focus of OT and IoT Cybersecurity in Australia’s Critical Infrastructure The Australian Government’s approach to OT/IoT security is a significant step forward, but great challenges still exist for critical infrastructure. The post Focus of OT and…
Read more →
The post Focus of OT and IoT Cybersecurity in Australia’s Critical Infrastructure first appeared on IT Security News.
https://www.itsecuritynews.info/focus-of-ot-and-iot-cybersecurity-in-australias-critical-infrastructure/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/focus-of-ot-and-iot-cybersecurity-in-australias-critical-infrastructure/?utm_source=dlvr.it&utm_medium=blogger
Most businesses are tracking customers yet don’t tell them
Read the original article: Most businesses are tracking customers yet don’t tell them Apple is cracking down on apps that track users without their permission, but a new survey shows this type of consumer data privacy abuse is also happening…
Read more →
The post Most businesses are tracking customers yet don’t tell them first appeared on IT Security News.
https://www.itsecuritynews.info/most-businesses-are-tracking-customers-yet-dont-tell-them/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/most-businesses-are-tracking-customers-yet-dont-tell-them/?utm_source=dlvr.it&utm_medium=blogger
Gmail suffers two outages in one day
Read the original article: Gmail suffers two outages in one day Gmail has suffered two outages in 24 hours, as users have been unable to send emails to other Gmail users, while others have experienced unexpected behaviour. However, users are…
Read more →
The post Gmail suffers two outages in one day first appeared on IT Security News.
https://www.itsecuritynews.info/gmail-suffers-two-outages-in-one-day/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/gmail-suffers-two-outages-in-one-day/?utm_source=dlvr.it&utm_medium=blogger
Tuesday, December 15, 2020
Adrozek Malware Silently Hijacks Microsoft Edge, Google Chrome, Yandex & Firefox Browsers
Recently, Microsoft 365 Defender Research affirmed that they had recorded a new malware that has been continuously attacking popular browsers like Google Chrome, Firefox, Microsoft Edge, and Yandex. The malware is named Adrozek Malware, and it is specifically created to inject ads into search engine results pages. Since May 2020, this malware has been on […]
The post Adrozek Malware Silently Hijacks Microsoft Edge, Google Chrome, Yandex & Firefox Browsers appeared first on Cyber Security News.
https://cybersecuritynews.com/adrozek-malware/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/adrozek-malware/?utm_source=dlvr.it&utm_medium=blogger
Molerats APT: New Malware and Techniques in Middle East Espionage Campaign
Read the original article: Molerats APT: New Malware and Techniques in Middle East Espionage Campaign Security researchers observed a politically motivated APT called “Molerats” using three new malware variants to conduct espionage in the Middle East. The post Molerats APT:…
Read more →
The post Molerats APT: New Malware and Techniques in Middle East Espionage Campaign first appeared on IT Security News.
https://www.itsecuritynews.info/molerats-apt-new-malware-and-techniques-in-middle-east-espionage-campaign/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/molerats-apt-new-malware-and-techniques-in-middle-east-espionage-campaign/?utm_source=dlvr.it&utm_medium=blogger
Exfiltrating Data from Air-Gapped Computers via Wi-Fi Signals (Without Wi-Fi Hardware)
A security researcher has demonstrated that sensitive data could be exfiltrated from air-gapped computers via a novel technique that leverages Wi-Fi signals as a covert channel—surprisingly, without requiring the presence of Wi-Fi hardware on the targeted systems. Dubbed "AIR-FI," the attack hinges on deploying a specially designed malware in a compromised system that exploits "DDR SDRAM buses
https://thehackernews.com/2020/12/exfiltrating-data-from-air-gapped.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/exfiltrating-data-from-air-gapped.html?utm_source=dlvr.it&utm_medium=blogger
Monday, December 14, 2020
5 building blocks of a well-developed security culture
Read the original article: 5 building blocks of a well-developed security culture A defined security culture is helping the financial industry, though the fundamentals should apply to any business. Become a supporter of IT Security News and help us…
Read more →
The post 5 building blocks of a well-developed security culture first appeared on IT Security News.
https://www.itsecuritynews.info/5-building-blocks-of-a-well-developed-security-culture/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/5-building-blocks-of-a-well-developed-security-culture/?utm_source=dlvr.it&utm_medium=blogger
SoReL-20M: A Huge Dataset of 20 Million Malware Samples Released Online
Cybersecurity firms Sophos and ReversingLabs on Monday jointly released the first-ever production-scale malware research dataset to be made available to the general public that aims to build effective defenses and drive industry-wide improvements in security detection and response. "SoReL-20M" (short for Sophos-ReversingLabs – 20 Million), as it's called, is a dataset containing metadata, labels
https://thehackernews.com/2020/12/sorel-20m-huge-dataset-of-20-million.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/sorel-20m-huge-dataset-of-20-million.html?utm_source=dlvr.it&utm_medium=blogger
US Agencies and FireEye Were Hacked Using SolarWinds Software Backdoor
State-sponsored actors allegedly working for Russia have targeted the US Treasury, the Commerce Department's National Telecommunications and Information Administration (NTIA), and other government agencies to monitor internal email traffic as part of a widespread cyberespionage campaign. The Washington Post, citing unnamed sources, said the latest attacks were the work of APT29 or Cozy Bear, the
https://thehackernews.com/2020/12/us-agencies-and-fireeye-were-hacked.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/us-agencies-and-fireeye-were-hacked.html?utm_source=dlvr.it&utm_medium=blogger
Sunday, December 13, 2020
IT Security News Daily Summary 2020-12-13
Pay2Key hackers stole data from Intel’s Habana Labs Steam vulnerabilities allowed remote take over of users’ computers Third parties: The Risk Management Blind Spot The Comforting… DEF CON 28 Safe Mode Aerospace Village – Jay Angus’ ‘Checklist For Aviation Vulnerability…
Read more →
The post IT Security News Daily Summary 2020-12-13 first appeared on IT Security News.
https://www.itsecuritynews.info/it-security-news-daily-summary-2020-12-13/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/it-security-news-daily-summary-2020-12-13/?utm_source=dlvr.it&utm_medium=blogger
Why You Need to Take Care of Your Cybersecurity
Technology has become an integral part of modern society. In fact, the average person spends around 11 hours each day for many forms of social media interaction. Whether it may be the smartphone you carry around everywhere you go or your personal computer containing important documents, people have come to rely on technology. With this […]
The post Why You Need to Take Care of Your Cybersecurity appeared first on Cyber Security News.
https://cybersecuritynews.com/why-you-need-to-take-care-of-your-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/why-you-need-to-take-care-of-your-cybersecurity/?utm_source=dlvr.it&utm_medium=blogger
Amnesia:33 – 33 Vulnerabilities That Impact Four Open-source TCP/IP Stacks Affects Millions of IoT Devices
The cybersecurity researchers have been warning regarding a set of very severe vulnerabilities that are continuously affecting TCP/IP stacks let hackers attack Millions of IoT, OT and IT Devices. The revelation of 33 TCP/IP stacks Zero-Day Vulnerabilities attacking all the smart devices produced by over 150 different tech firms and has again delivered the spotlight […]
The post Amnesia:33 – 33 Vulnerabilities That Impact Four Open-source TCP/IP Stacks Affects Millions of IoT Devices appeared first on Cyber Security News.
https://cybersecuritynews.com/amnesia33/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/amnesia33/?utm_source=dlvr.it&utm_medium=blogger
Saturday, December 12, 2020
DEF CON 28 Safe Mode Aerospace Village – Panel: ‘Building Connections Across The Aviation Ecosystem’
Read the original article: DEF CON 28 Safe Mode Aerospace Village – Panel: ‘Building Connections Across The Aviation Ecosystem’ Many thanks to DEF CON and Panel Speakers (Randy Talley’s (CISA), Sidd Gejji’s (FAA), Al Burke’s (DoD), Jen Ellis’ (Rapid7), Jeff…
Read more →
The post DEF CON 28 Safe Mode Aerospace Village – Panel: ‘Building Connections Across The Aviation Ecosystem’ first appeared on IT Security News.
https://www.itsecuritynews.info/def-con-28-safe-mode-aerospace-village-panel-building-connections-across-the-aviation-ecosystem/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/def-con-28-safe-mode-aerospace-village-panel-building-connections-across-the-aviation-ecosystem/?utm_source=dlvr.it&utm_medium=blogger
What is the Different Between VPN and Proxy – A Complete Guide
Both the VPN and proxy are used to facilitate the connection between the client and server by hiding it’s IP address and they are slightly different in the way it handles the data. In the modern cyber world, we have faced a lot of concerns about our privacy, both the VPNs and proxy handle it […]
The post What is the Different Between VPN and Proxy – A Complete Guide appeared first on Cyber Security News.
https://cybersecuritynews.com/vpn-and-proxy/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/vpn-and-proxy/?utm_source=dlvr.it&utm_medium=blogger
WinZip 24 Insecure Communication Let Hackers Drop Malware
In the process of checking for updates on the WinZip network communications, the experts have found that the WinZip archiver was vulnerable to several attacks through the unsecured http. Any threat actor can easily exploit this by granting a rogue “update.” WinZip is currently at version 25, but shortly after it releases, check the server […]
The post WinZip 24 Insecure Communication Let Hackers Drop Malware appeared first on Cyber Security News.
https://cybersecuritynews.com/winzip-24-insecure-communication/?utm_source=dlvr.it&utm_medium=blogger
https://cybersecuritynews.com/winzip-24-insecure-communication/?utm_source=dlvr.it&utm_medium=blogger
Friday, December 11, 2020
Rethinking computing for next-level problems
Read the original article: Rethinking computing for next-level problems With current computer systems struggling to keep pace with ever more complex workloads, intelligence and defense agencies are looking for new approaches to solving data-intensive problems. Become a supporter of…
Read more →
The post Rethinking computing for next-level problems first appeared on IT Security News.
https://www.itsecuritynews.info/rethinking-computing-for-next-level-problems/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/rethinking-computing-for-next-level-problems/?utm_source=dlvr.it&utm_medium=blogger
Mount Locker Ransomware Offering Double Extortion Scheme to Other Hackers
A relatively new ransomware strain behind a series of breaches on corporate networks has developed new capabilities that allow it to broaden the scope of its targeting and evade security software—as well as with ability for its affiliates to launch double extortion attacks. The MountLocker ransomware, which only began making the rounds in July 2020, has already gained notoriety for stealing
https://thehackernews.com/2020/12/mount-locker-ransomware-offering-double.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/mount-locker-ransomware-offering-double.html?utm_source=dlvr.it&utm_medium=blogger
Facebook Tracks APT32 OceanLotus Hackers to IT Company in Vietnam
Cybersecurity researchers from Facebook today formally linked the activities of a Vietnamese threat actor to an IT company in the country after the group was caught abusing its platform to hack into people's accounts and distribute malware. Tracked as APT32 (or Bismuth, OceanLotus, and Cobalt Kitty), the state-aligned operatives affiliated with the Vietnam government have been known for
https://thehackernews.com/2020/12/facebook-tracks-apt32-oceanlotus.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/facebook-tracks-apt32-oceanlotus.html?utm_source=dlvr.it&utm_medium=blogger
Thursday, December 10, 2020
Apple Developing In-House Modem That Will Eventually Replace Qualcomm Chips
Read the original article: Apple Developing In-House Modem That Will Eventually Replace Qualcomm Chips Apple is now developing its own cellular modem that will be used in future devices and that will eventually replace modem components sourced from Qualcomm, reports…
Read more →
The post Apple Developing In-House Modem That Will Eventually Replace Qualcomm Chips first appeared on IT Security News.
https://www.itsecuritynews.info/apple-developing-in-house-modem-that-will-eventually-replace-qualcomm-chips/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/apple-developing-in-house-modem-that-will-eventually-replace-qualcomm-chips/?utm_source=dlvr.it&utm_medium=blogger
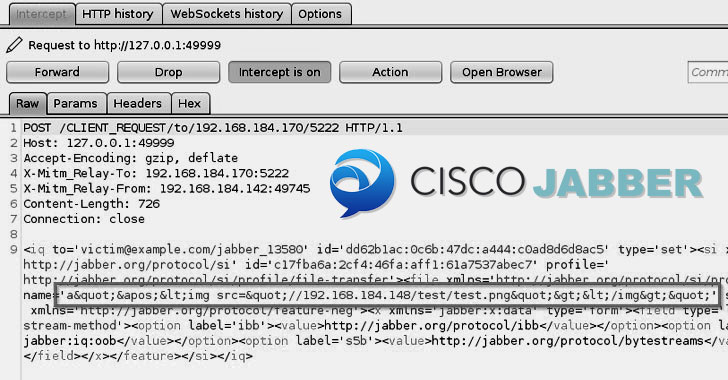
Cisco Reissues Patches for Critical Bugs in Jabber Video Conferencing Software
Cisco has once again fixed four previously disclosed critical bugs in its Jabber video conferencing and messaging app that were inadequately addressed, leaving its users susceptible to remote attacks. The vulnerabilities, if successfully exploited, could allow an authenticated, remote attacker to execute arbitrary code on target systems by sending specially-crafted chat messages in group
https://thehackernews.com/2020/12/cisco-reissues-patches-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/cisco-reissues-patches-for-critical.html?utm_source=dlvr.it&utm_medium=blogger
48 U.S. States and FTC are suing Facebook for illegal monopolization
The US Federal Trade Commission and a coalition of 48 state attorneys general on Wednesday filed a pair of sweeping antitrust suits against Facebook, alleging that the company abused its power in the marketplace to neutralize competitors through its acquisitions of Instagram and WhatsApp and depriving users of better privacy-friendly alternatives. "Facebook has engaged in a systematic strategy —
https://thehackernews.com/2020/12/48-us-states-and-ftc-are-suing-facebook.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/48-us-states-and-ftc-are-suing-facebook.html?utm_source=dlvr.it&utm_medium=blogger
Wednesday, December 9, 2020
RPA takes root as agencies use cases grow
Read the original article: RPA takes root as agencies use cases grow Maturity of federal robotic process automation programs grew 70% in the last year, according to a recent report. Become a supporter of IT Security News and help…
Read more →
The post RPA takes root as agencies use cases grow first appeared on IT Security News.
https://www.itsecuritynews.info/rpa-takes-root-as-agencies-use-cases-grow/?utm_source=dlvr.it&utm_medium=blogger
https://www.itsecuritynews.info/rpa-takes-root-as-agencies-use-cases-grow/?utm_source=dlvr.it&utm_medium=blogger
Russian APT28 Hackers Using COVID-19 as Bait to Deliver Zebrocy Malware
A Russian threat actor known for its malware campaigns has reappeared in the threat landscape with yet another attack leveraging COVID-19 as phishing lures, once again indicating how adversaries are adept at repurposing the current world events to their advantage. Linking the operation to a sub-group of APT28 (aka Sofacy, Sednit, Fancy Bear, or STRONTIUM), cybersecurity firm Intezer said the
https://thehackernews.com/2020/12/russian-apt28-hackers-using-covid-19-as.html?utm_source=dlvr.it&utm_medium=blogger
https://thehackernews.com/2020/12/russian-apt28-hackers-using-covid-19-as.html?utm_source=dlvr.it&utm_medium=blogger
Subscribe to:
Comments (Atom)